Data Governance, Risk Assessment, and Security Plan for Private-Match
VerifiedAdded on 2023/01/17
|26
|5829
|25
Report
AI Summary
This report provides a comprehensive data governance plan for the dating agency "Private Match." It begins with a risk assessment of IT services and data security, identifying vulnerabilities like malicious AI use, lack of cybersecurity policies, data theft, and improper security training, along with mitigation recommendations. A business continuity plan is outlined, emphasizing resilience, recovery, and contingency strategies. The report then details steps to enhance operational and environmental security, including developing security and change management policies, data policies, and security awareness programs. A guide for staff concerning ethical, legal, and regulatory compliance is also included, addressing potential financial and reputational losses due to breaches, stakeholder responsibilities, staff training, incident reporting, and relevant laws and industry best practices. Finally, the report includes a disaster recovery A4 electronic poster. The document aims to ensure data protection and operational security within the organization.

Running head: INFORMATION GOVERANCE
Private-Match (PM)
Name of the Student
Name of the University
Author’s Note
Private-Match (PM)
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
INFORMATION GOVERANCE
Table of Contents
Introduction......................................................................................................................................2
1.1 Risk assessment relating to IT services and data security with proper recommendations....2
1.2 Business continuity plan........................................................................................................8
1.3 Steps for enhancing operational and environmental security................................................9
2. Guide for the staff concerning ethical, legal and regulatory compliance..................................11
2.1 Potential financial as well as reputational loss that would occur due to breach..................11
2.2 Responsibilities of the involved stakeholders......................................................................12
2.3 Training facility to the staffs................................................................................................13
2.4 Steps for reporting any suspicious incident.........................................................................14
2.5 Clear information about the laws and industry best practices.............................................16
3. A4 electronic poster for Disaster Recovery...............................................................................18
Conclusion.....................................................................................................................................19
References......................................................................................................................................20
INFORMATION GOVERANCE
Table of Contents
Introduction......................................................................................................................................2
1.1 Risk assessment relating to IT services and data security with proper recommendations....2
1.2 Business continuity plan........................................................................................................8
1.3 Steps for enhancing operational and environmental security................................................9
2. Guide for the staff concerning ethical, legal and regulatory compliance..................................11
2.1 Potential financial as well as reputational loss that would occur due to breach..................11
2.2 Responsibilities of the involved stakeholders......................................................................12
2.3 Training facility to the staffs................................................................................................13
2.4 Steps for reporting any suspicious incident.........................................................................14
2.5 Clear information about the laws and industry best practices.............................................16
3. A4 electronic poster for Disaster Recovery...............................................................................18
Conclusion.....................................................................................................................................19
References......................................................................................................................................20

2
INFORMATION GOVERANCE
Introduction
The paper mainly reflects on the organization “Private Match” which is a national dating
agency. It is found that currently the company has six offices within the country with one head
office. The PM administer their matching services with the help of websites as well as mobile
applications and matching is generally done with the help of AI algorithms. In order to make
matching, lots of personal data of the customers are asked and therefore data protection is one of
the keys for the entire company. Presently, the organization is facing a number of struggles in
order to properly understand the complexities for implementing new data as well as protection
regulations properly. In order to avoid such issues, the company generally decided to implement
a full risk assessment for the IT services as well as different types of related data, proper disaster
management and recovery plan. In addition to this, the company also wants to set proper
enhanced IT policies that generally include data protection, backup policy as well as staff
training policies effectively for maintaining proper operational as well as environmental security
of the company.
1. Proposal to the board of directors
1.1 Risk assessment relating to IT services and data security with proper recommendations
The risk assessment that is done on the IT services as well as data security mainly
determines the hazard, risk factors and analyzes proper ways for eliminating the risks that are
associated with the IT services as well as data security.
Risk Description Impact Probability Mitigation
/recommendation
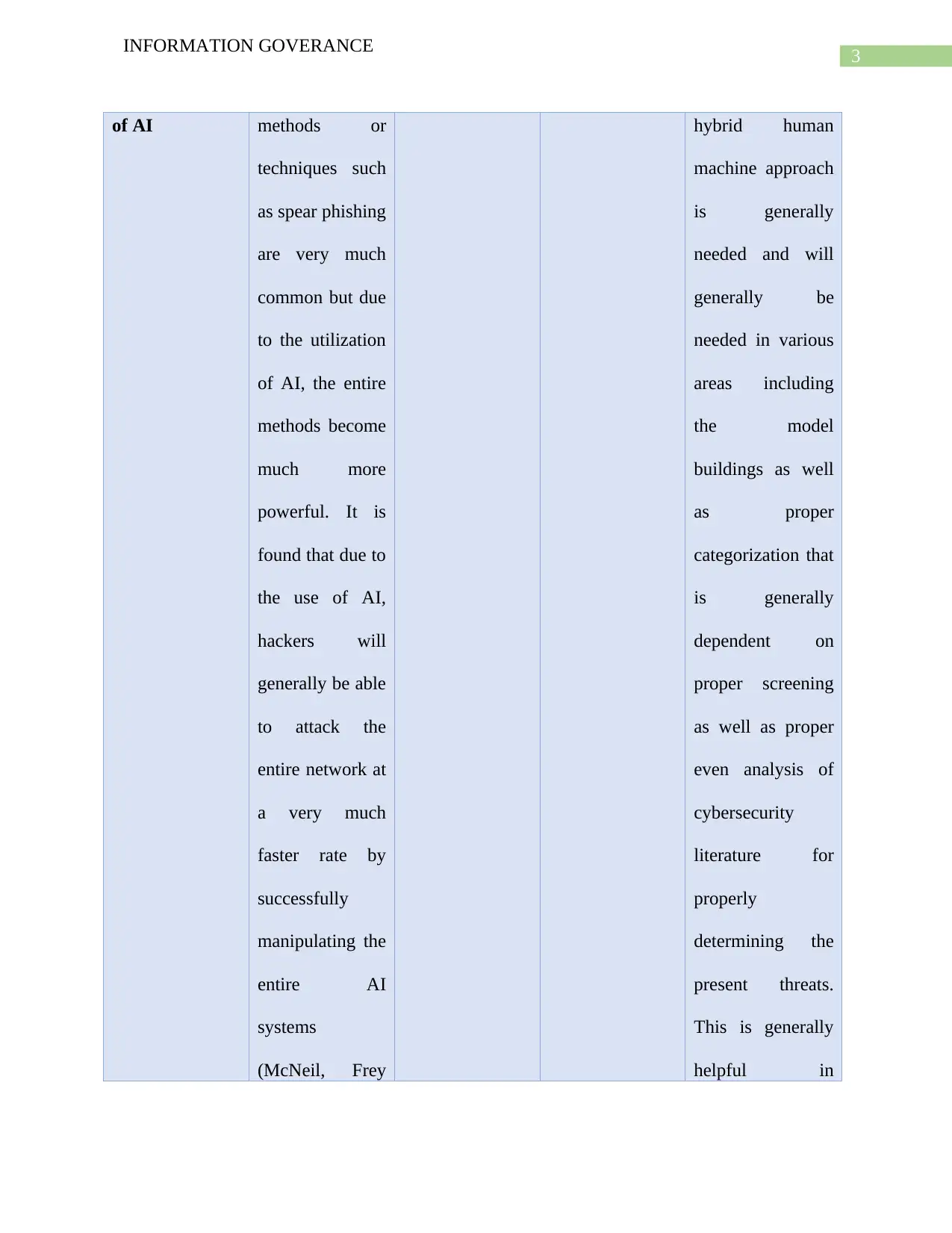
Malicious use Cyberhacking High High It is found that
INFORMATION GOVERANCE
Introduction
The paper mainly reflects on the organization “Private Match” which is a national dating
agency. It is found that currently the company has six offices within the country with one head
office. The PM administer their matching services with the help of websites as well as mobile
applications and matching is generally done with the help of AI algorithms. In order to make
matching, lots of personal data of the customers are asked and therefore data protection is one of
the keys for the entire company. Presently, the organization is facing a number of struggles in
order to properly understand the complexities for implementing new data as well as protection
regulations properly. In order to avoid such issues, the company generally decided to implement
a full risk assessment for the IT services as well as different types of related data, proper disaster
management and recovery plan. In addition to this, the company also wants to set proper
enhanced IT policies that generally include data protection, backup policy as well as staff
training policies effectively for maintaining proper operational as well as environmental security
of the company.
1. Proposal to the board of directors
1.1 Risk assessment relating to IT services and data security with proper recommendations
The risk assessment that is done on the IT services as well as data security mainly
determines the hazard, risk factors and analyzes proper ways for eliminating the risks that are
associated with the IT services as well as data security.
Risk Description Impact Probability Mitigation
/recommendation
Malicious use Cyberhacking High High It is found that
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
INFORMATION GOVERANCE
of AI methods or
techniques such
as spear phishing
are very much
common but due
to the utilization
of AI, the entire
methods become
much more
powerful. It is
found that due to
the use of AI,
hackers will
generally be able
to attack the
entire network at
a very much
faster rate by
successfully
manipulating the
entire AI
systems
(McNeil, Frey
hybrid human
machine approach
is generally
needed and will
generally be
needed in various
areas including
the model
buildings as well
as proper
categorization that
is generally
dependent on
proper screening
as well as proper
even analysis of
cybersecurity
literature for
properly
determining the
present threats.
This is generally
helpful in
INFORMATION GOVERANCE
of AI methods or
techniques such
as spear phishing
are very much
common but due
to the utilization
of AI, the entire
methods become
much more
powerful. It is
found that due to
the use of AI,
hackers will
generally be able
to attack the
entire network at
a very much
faster rate by
successfully
manipulating the
entire AI
systems
(McNeil, Frey
hybrid human
machine approach
is generally
needed and will
generally be
needed in various
areas including
the model
buildings as well
as proper
categorization that
is generally
dependent on
proper screening
as well as proper
even analysis of
cybersecurity
literature for
properly
determining the
present threats.
This is generally
helpful in
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
INFORMATION GOVERANCE
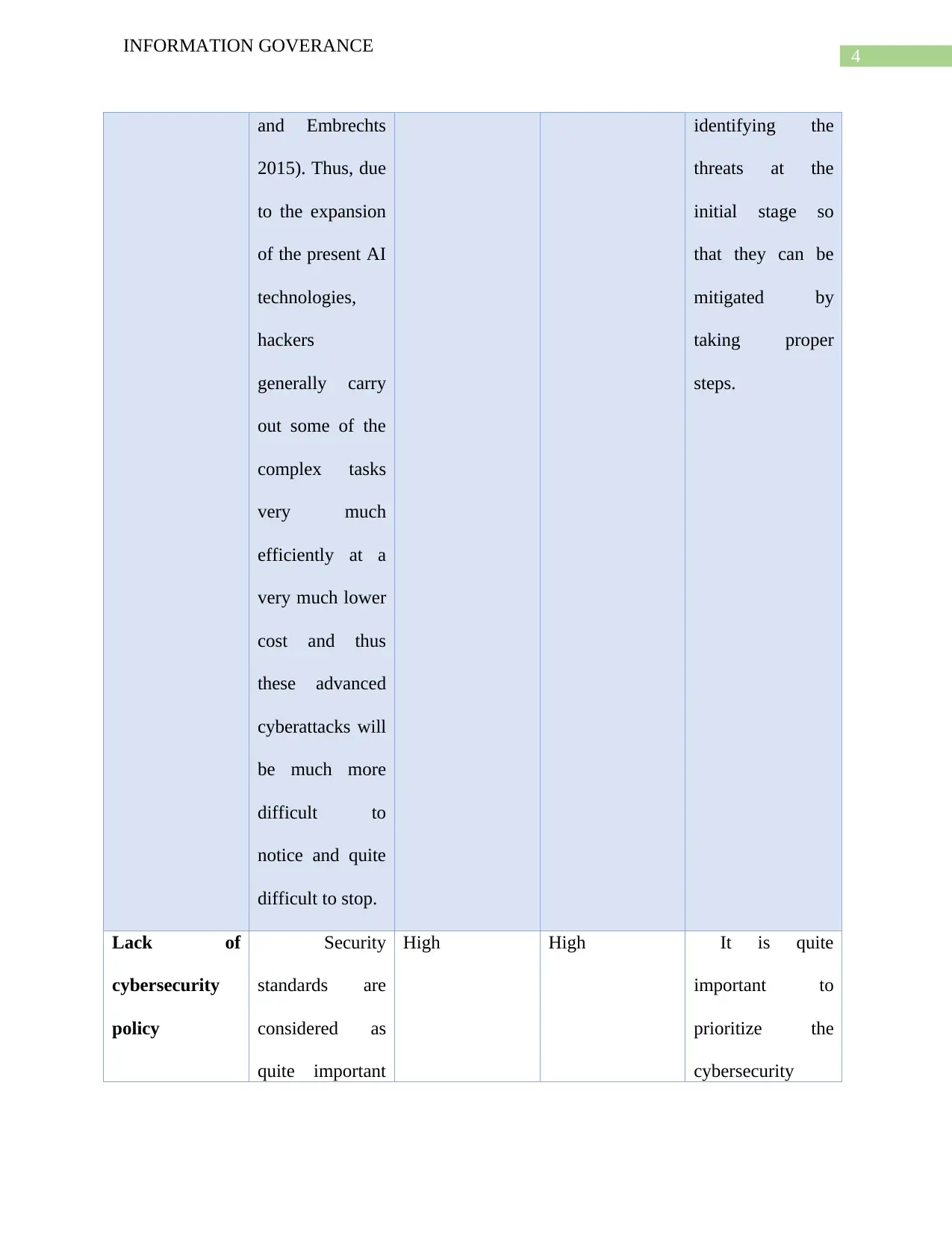
and Embrechts
2015). Thus, due
to the expansion
of the present AI
technologies,
hackers
generally carry
out some of the
complex tasks
very much
efficiently at a
very much lower
cost and thus
these advanced
cyberattacks will
be much more
difficult to
notice and quite
difficult to stop.
identifying the
threats at the
initial stage so
that they can be
mitigated by
taking proper
steps.
Lack of
cybersecurity
policy
Security
standards are
considered as
quite important
High High It is quite
important to
prioritize the
cybersecurity
INFORMATION GOVERANCE
and Embrechts
2015). Thus, due
to the expansion
of the present AI
technologies,
hackers
generally carry
out some of the
complex tasks
very much
efficiently at a
very much lower
cost and thus
these advanced
cyberattacks will
be much more
difficult to
notice and quite
difficult to stop.
identifying the
threats at the
initial stage so
that they can be
mitigated by
taking proper
steps.
Lack of
cybersecurity
policy
Security
standards are
considered as
quite important
High High It is quite
important to
prioritize the
cybersecurity
5
INFORMATION GOVERANCE
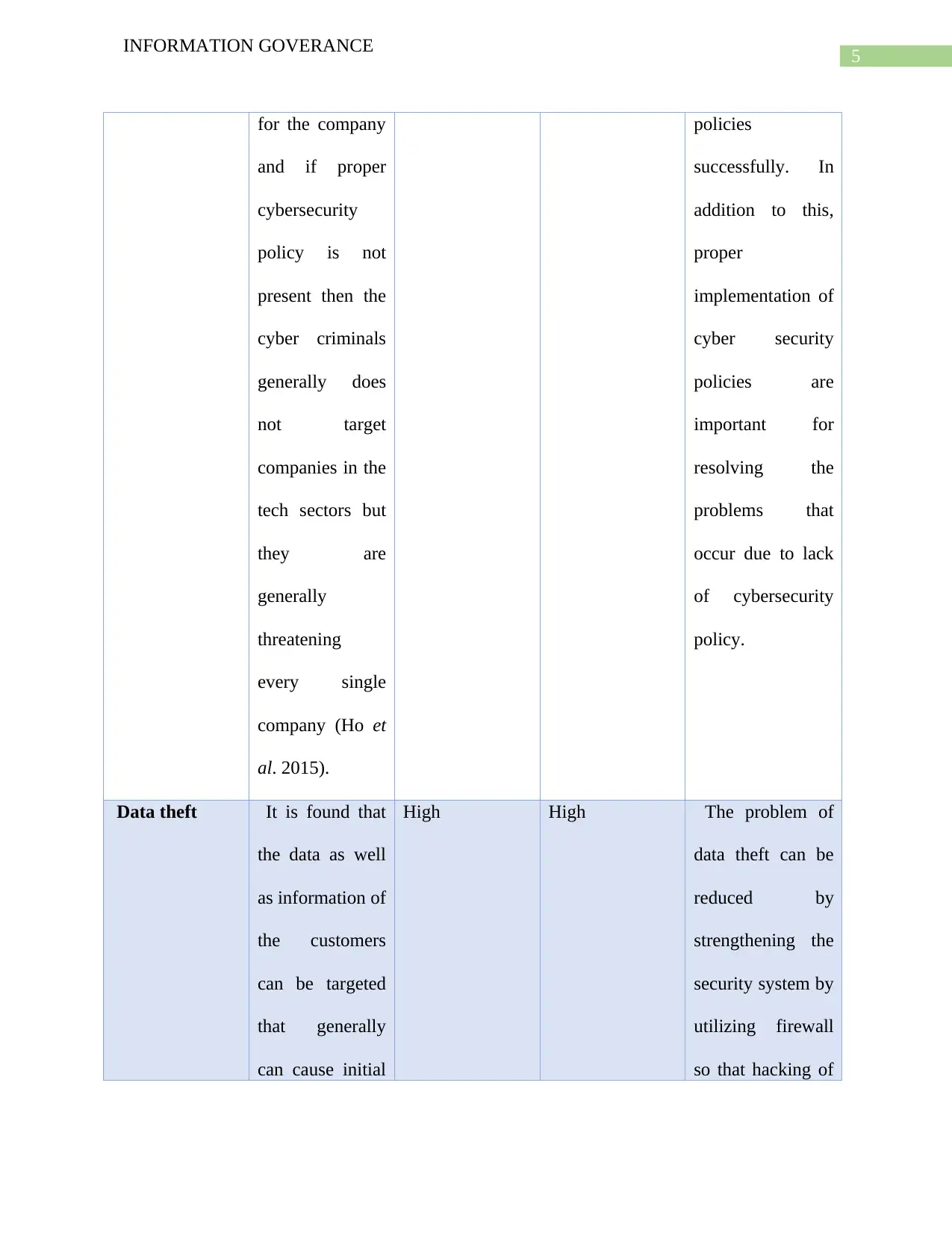
for the company
and if proper
cybersecurity
policy is not
present then the
cyber criminals
generally does
not target
companies in the
tech sectors but
they are
generally
threatening
every single
company (Ho et
al. 2015).
policies
successfully. In
addition to this,
proper
implementation of
cyber security
policies are
important for
resolving the
problems that
occur due to lack
of cybersecurity
policy.
Data theft It is found that
the data as well
as information of
the customers
can be targeted
that generally
can cause initial
High High The problem of
data theft can be
reduced by
strengthening the
security system by
utilizing firewall
so that hacking of
INFORMATION GOVERANCE
for the company
and if proper
cybersecurity
policy is not
present then the
cyber criminals
generally does
not target
companies in the
tech sectors but
they are
generally
threatening
every single
company (Ho et
al. 2015).
policies
successfully. In
addition to this,
proper
implementation of
cyber security
policies are
important for
resolving the
problems that
occur due to lack
of cybersecurity
policy.
Data theft It is found that
the data as well
as information of
the customers
can be targeted
that generally
can cause initial
High High The problem of
data theft can be
reduced by
strengthening the
security system by
utilizing firewall
so that hacking of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
INFORMATION GOVERANCE
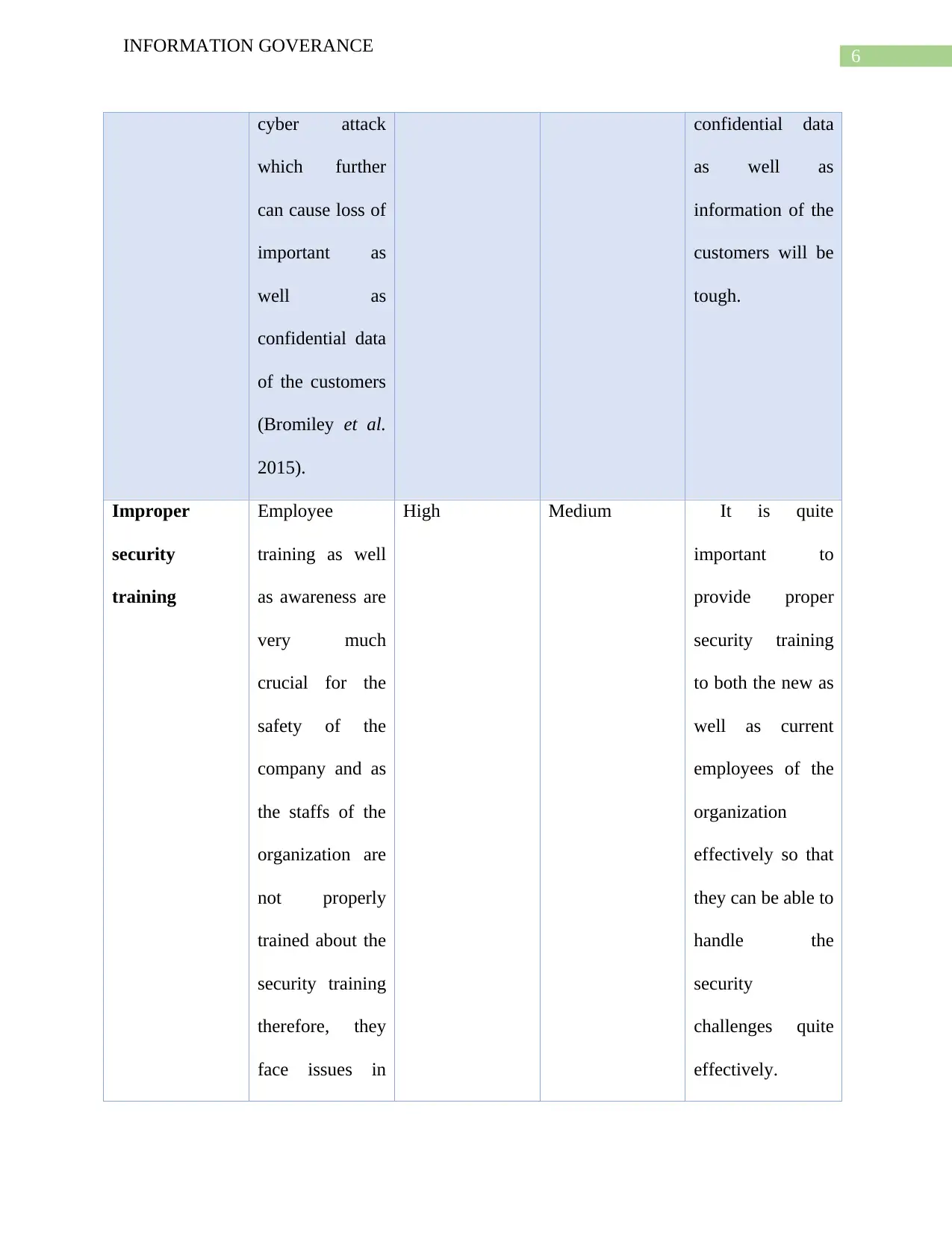
cyber attack
which further
can cause loss of
important as
well as
confidential data
of the customers
(Bromiley et al.
2015).
confidential data
as well as
information of the
customers will be
tough.
Improper
security
training
Employee
training as well
as awareness are
very much
crucial for the
safety of the
company and as
the staffs of the
organization are
not properly
trained about the
security training
therefore, they
face issues in
High Medium It is quite
important to
provide proper
security training
to both the new as
well as current
employees of the
organization
effectively so that
they can be able to
handle the
security
challenges quite
effectively.
INFORMATION GOVERANCE
cyber attack
which further
can cause loss of
important as
well as
confidential data
of the customers
(Bromiley et al.
2015).
confidential data
as well as
information of the
customers will be
tough.
Improper
security
training
Employee
training as well
as awareness are
very much
crucial for the
safety of the
company and as
the staffs of the
organization are
not properly
trained about the
security training
therefore, they
face issues in
High Medium It is quite
important to
provide proper
security training
to both the new as
well as current
employees of the
organization
effectively so that
they can be able to
handle the
security
challenges quite
effectively.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
INFORMATION GOVERANCE
determining the
issues as well as
resolving them
(Wiengarten et
al. 2016).
Lack of proper
recovery plan
It is found that
proper planning
for the security
attack is only
possible with the
help of a plan for
preventing the
cyberattack and
as the
organization
does not have a
proper recovery
plan therefore,
they face a lot of
cybersecurity
related incidents
(Cole, Gine and
Vickery 2017).
Medium Medium Implementation
of proper recovery
plan is generally
important for
dealing different
types of critical
situations that are
generally
associated with
the cyberattack.
INFORMATION GOVERANCE
determining the
issues as well as
resolving them
(Wiengarten et
al. 2016).
Lack of proper
recovery plan
It is found that
proper planning
for the security
attack is only
possible with the
help of a plan for
preventing the
cyberattack and
as the
organization
does not have a
proper recovery
plan therefore,
they face a lot of
cybersecurity
related incidents
(Cole, Gine and
Vickery 2017).
Medium Medium Implementation
of proper recovery
plan is generally
important for
dealing different
types of critical
situations that are
generally
associated with
the cyberattack.

8
INFORMATION GOVERANCE
1.2 Business continuity plan
The organization “Private Match” uses a proper business continuity plan in order to give
overview about the operation of the business if something generally goes wrong. According to
Wallace and Webber (2017) business continuity is defined as one of the abilities of an
organization for maintaining the proper functions during or after the occurrence of the disaster. It
is found that the business continuity planning generally helps in establishing proper risk
management processes as well as procedures that generally aims to properly prevent
interruptions as well as proper re-establishment of full function to the entire organization as
quickly as possible. The three key elements of the business continuity plan that is prepared is
generally reflected below:
Resilience
The company “private match” generally increases its resilience by successfully designing
the various critical functions as well as infrastructures with different types of disaster-based
possibilities in mind including proper staff rotations, data redundancy as well as effective
maintenance of surplus of capacity (Kato and Charoenrat 2018). It is found that proper insurance
of resilience against the various types of scenarios generally helps the business for properly
maintaining the proper services on off-site as well as location without effective interruption.
Recovery
In context to business continuity plan, the organization utilizes rapid recovery for
restoring the business functions after a disaster or risk occurrence. It is identified that setting
proper time of recovery for the different types of systems, networks as well as applications are
generally considered to be helpful in properly prioritizing the elements that requires to be
INFORMATION GOVERANCE
1.2 Business continuity plan
The organization “Private Match” uses a proper business continuity plan in order to give
overview about the operation of the business if something generally goes wrong. According to
Wallace and Webber (2017) business continuity is defined as one of the abilities of an
organization for maintaining the proper functions during or after the occurrence of the disaster. It
is found that the business continuity planning generally helps in establishing proper risk
management processes as well as procedures that generally aims to properly prevent
interruptions as well as proper re-establishment of full function to the entire organization as
quickly as possible. The three key elements of the business continuity plan that is prepared is
generally reflected below:
Resilience
The company “private match” generally increases its resilience by successfully designing
the various critical functions as well as infrastructures with different types of disaster-based
possibilities in mind including proper staff rotations, data redundancy as well as effective
maintenance of surplus of capacity (Kato and Charoenrat 2018). It is found that proper insurance
of resilience against the various types of scenarios generally helps the business for properly
maintaining the proper services on off-site as well as location without effective interruption.
Recovery
In context to business continuity plan, the organization utilizes rapid recovery for
restoring the business functions after a disaster or risk occurrence. It is identified that setting
proper time of recovery for the different types of systems, networks as well as applications are
generally considered to be helpful in properly prioritizing the elements that requires to be
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
INFORMATION GOVERANCE
recovered first. Moreover, the various types of recovery strategies generally include different
types of resource inventories agreements as well as third parties within a company for various
types of mission- based functions.
Contingency
After then, a contingency plan is used that is considered as one of the procedures that
generally uses different varieties of external scenarios which further include chain of command
which further distributes different types of responsibilities within the entire organization
(Sahebjamnia, Torabi and Mansouri 2015). The various types of responsibilities generally
include proper hardware replacement, leasing the office spaces, damage assessment as well as
proper contracting with the third-party vendors in order to get effective help from them.
1.3 Steps for enhancing operational and environmental security
The organization “Private Match” can be able to achieve both operational as well as
environmental security with the help of proper policies as well as procedures that further assists
in guiding the user’s interaction with the help of data as well as effective data processing systems
(Blos, Hoeflich and Miyagi 2015). It is found that development as well as alignment of the
efforts with the goals of the business is considered as one of the crucial parts for the development
of proper operational as well as environmental security programs. The steps that are needed to be
followed are generally elaborated below:
Development of security policies: Security policies are generally defined as high level
statements that is generally produced by the senior management that generally outlines both what
is generally security meant for the organization and the organization’s goals for providing proper
security. The main security policy can generally be broken into number of policies that are linked
with security. In addition to this, the policies are generally related with the access control, the
INFORMATION GOVERANCE
recovered first. Moreover, the various types of recovery strategies generally include different
types of resource inventories agreements as well as third parties within a company for various
types of mission- based functions.
Contingency
After then, a contingency plan is used that is considered as one of the procedures that
generally uses different varieties of external scenarios which further include chain of command
which further distributes different types of responsibilities within the entire organization
(Sahebjamnia, Torabi and Mansouri 2015). The various types of responsibilities generally
include proper hardware replacement, leasing the office spaces, damage assessment as well as
proper contracting with the third-party vendors in order to get effective help from them.
1.3 Steps for enhancing operational and environmental security
The organization “Private Match” can be able to achieve both operational as well as
environmental security with the help of proper policies as well as procedures that further assists
in guiding the user’s interaction with the help of data as well as effective data processing systems
(Blos, Hoeflich and Miyagi 2015). It is found that development as well as alignment of the
efforts with the goals of the business is considered as one of the crucial parts for the development
of proper operational as well as environmental security programs. The steps that are needed to be
followed are generally elaborated below:
Development of security policies: Security policies are generally defined as high level
statements that is generally produced by the senior management that generally outlines both what
is generally security meant for the organization and the organization’s goals for providing proper
security. The main security policy can generally be broken into number of policies that are linked
with security. In addition to this, the policies are generally related with the access control, the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
INFORMATION GOVERANCE
organizations security policy which must include proper policies and all policies should be
effectively reviewed on proper basis as per requirement.
Change management policy: The main purpose of the change management is to make
sure that effective procedures are generally followed when effective modifications are generally
needed within the IT infrastructures. The modifications should be properly prompted with the
help of a number of events including proper legislation, updated hardware as well as software as
well as effective improvements within the infrastructure (Graham and Kaye 2015). It is found
that proper change management procedures should include different stages including the method
of requesting to the change within the infrastructure as well as review as well as approval
procedure for the request.
Data policies: Proper system integration within third parties generally involves with the
data sharing. It is found that the data can generally be shared for the effective purpose of
processing. Effective control over data is important for avoiding challenges as well as issues
related with unauthorized data sharing (Fisher, Norman and Klett 2017). In addition to this, data
ownership requirements generally need proper backup responsibilities that generally includes
proper determination of the backup responsibilities as well as development of effective
operational procedures for making sure that proper backup generally occur as they are generally
important for various security elements.
Security awareness and training: Security awareness as well as training programs are
generally helpful in properly enhancing the security of the programs. It is quite important to train
the employees with proper objectives so that they can be capable of handling the security
challenges effectively. As the security policies are considered as very much high-level directive
which further helps in setting the entire support as well as proper execution of the direction with
INFORMATION GOVERANCE
organizations security policy which must include proper policies and all policies should be
effectively reviewed on proper basis as per requirement.
Change management policy: The main purpose of the change management is to make
sure that effective procedures are generally followed when effective modifications are generally
needed within the IT infrastructures. The modifications should be properly prompted with the
help of a number of events including proper legislation, updated hardware as well as software as
well as effective improvements within the infrastructure (Graham and Kaye 2015). It is found
that proper change management procedures should include different stages including the method
of requesting to the change within the infrastructure as well as review as well as approval
procedure for the request.
Data policies: Proper system integration within third parties generally involves with the
data sharing. It is found that the data can generally be shared for the effective purpose of
processing. Effective control over data is important for avoiding challenges as well as issues
related with unauthorized data sharing (Fisher, Norman and Klett 2017). In addition to this, data
ownership requirements generally need proper backup responsibilities that generally includes
proper determination of the backup responsibilities as well as development of effective
operational procedures for making sure that proper backup generally occur as they are generally
important for various security elements.
Security awareness and training: Security awareness as well as training programs are
generally helpful in properly enhancing the security of the programs. It is quite important to train
the employees with proper objectives so that they can be capable of handling the security
challenges effectively. As the security policies are considered as very much high-level directive
which further helps in setting the entire support as well as proper execution of the direction with

11
INFORMATION GOVERANCE
respect to proper security. In addition to this, second level policies including policies, access as
well as information handling generally utilizes proper policies that needs to be effectively
designed as well as understood.
Fire suppressions: Fires are generally considered as one of the disasters that generally
can create negative impact on the organizational environment by using proper equipment. It is
found that proper fire detection as well as fire suppression are generally considered as two
important devices for successfully addressing the threat. Proper suppression system generally
come in different varieties including the gas-based system as well as sprinkler-based system
(Conti, Dargahi and Dehghantanha 2018).
2. Guide for the staff concerning ethical, legal and regulatory compliance
2.1 Potential financial as well as reputational loss that would occur due to breach
It is found that if any data breach or security issue occur within the organization “Private
Match” then it would generally create negative impact on the financial as well as reputational
status of the organization. As the organization “PM” generally administers their matching
services with the help of either website or with the help of mobile applications. It is found that
the customers generally need to sign off by utilizing their personal details, information related
with debit and credit card as well as with the help of proper text-based information (Samtani et
al. 2017). However, if any type of security breach occurs within the organization then the
confidential or personal information related with the customers gets leaked that causes a number
of ethical as well as financial issues. If the details of the credit or debit card get hacked then it
will generally create a huge financial impact on both the organization as well as on the customers
that further creates negative impact on the reputation of the organization (Williams et al. 2018).
Thus, it is found that both the financial as well as reputational status of the organization gets
INFORMATION GOVERANCE
respect to proper security. In addition to this, second level policies including policies, access as
well as information handling generally utilizes proper policies that needs to be effectively
designed as well as understood.
Fire suppressions: Fires are generally considered as one of the disasters that generally
can create negative impact on the organizational environment by using proper equipment. It is
found that proper fire detection as well as fire suppression are generally considered as two
important devices for successfully addressing the threat. Proper suppression system generally
come in different varieties including the gas-based system as well as sprinkler-based system
(Conti, Dargahi and Dehghantanha 2018).
2. Guide for the staff concerning ethical, legal and regulatory compliance
2.1 Potential financial as well as reputational loss that would occur due to breach
It is found that if any data breach or security issue occur within the organization “Private
Match” then it would generally create negative impact on the financial as well as reputational
status of the organization. As the organization “PM” generally administers their matching
services with the help of either website or with the help of mobile applications. It is found that
the customers generally need to sign off by utilizing their personal details, information related
with debit and credit card as well as with the help of proper text-based information (Samtani et
al. 2017). However, if any type of security breach occurs within the organization then the
confidential or personal information related with the customers gets leaked that causes a number
of ethical as well as financial issues. If the details of the credit or debit card get hacked then it
will generally create a huge financial impact on both the organization as well as on the customers
that further creates negative impact on the reputation of the organization (Williams et al. 2018).
Thus, it is found that both the financial as well as reputational status of the organization gets
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 26
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





