Proactive Network Defence: Case Study and Analysis
VerifiedAdded on 2023/04/21
|19
|5232
|130
Report
AI Summary
This report focuses on proactive network defense, starting with an executive summary that outlines the key areas covered. It includes a data flow decomposition diagram to identify threats and vulnerabilities across corporate workstations, control system workstations, and engineering workstations. A detailed threat modeling approach is used to analyze passive and active attacks, including masquerade, replay, distributed, insider, close-in, hijack, and denial-of-service attacks. The report explores threats related to wireless LANs. The report then provides threat mitigation plans and examines security controls in accordance with policy and regulatory compliance frameworks. It concludes with recommendations for enhancing the resilience of examined systems.

Running head: PROACTIVE NETWORK DEFENCE
PROACTIVE NETWORK DEFENCE
Name of student:
Name of university:
Author’s note:
PROACTIVE NETWORK DEFENCE
Name of student:
Name of university:
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
PROACTIVE NETWORK DEFENCE
Executive summary
The aim of this report is to discuss on the topic Proactive network defence. A data flow
decomposition diagram of the current infrastructure is provided in this report. A threat
modelling approach for identifying the threats and the vulnerabilities of the trust domains are
provided in this report. A detailed derivation of the threat mitigation plans for the identified
trust domains are provided in this report and appropriate actions and options are developed
for enhancing the resiliency of the examined systems is provided in this report. The controls
that are used in the threat mitigation plans is examined according to the policy and the
frameworks of the regulatory compliance is discussed in this report. Finally, the report settles
with a suitable conclusion for this report. The data flow decomposition diagram helps in the
identification of the threats and the probable vulnerabilities of the complete infrastructure and
implement appropriate controls for enhancing the security of the systems.
PROACTIVE NETWORK DEFENCE
Executive summary
The aim of this report is to discuss on the topic Proactive network defence. A data flow
decomposition diagram of the current infrastructure is provided in this report. A threat
modelling approach for identifying the threats and the vulnerabilities of the trust domains are
provided in this report. A detailed derivation of the threat mitigation plans for the identified
trust domains are provided in this report and appropriate actions and options are developed
for enhancing the resiliency of the examined systems is provided in this report. The controls
that are used in the threat mitigation plans is examined according to the policy and the
frameworks of the regulatory compliance is discussed in this report. Finally, the report settles
with a suitable conclusion for this report. The data flow decomposition diagram helps in the
identification of the threats and the probable vulnerabilities of the complete infrastructure and
implement appropriate controls for enhancing the security of the systems.

2
PROACTIVE NETWORK DEFENCE
Table of Contents
Data flow diagram..........................................................................................................3
Threat modelling approach............................................................................................3
Threat mitigation plans..................................................................................................9
Legal and ethical considerations..................................................................................12
Conclusion....................................................................................................................13
References....................................................................................................................14
Appendix......................................................................................................................18
PROACTIVE NETWORK DEFENCE
Table of Contents
Data flow diagram..........................................................................................................3
Threat modelling approach............................................................................................3
Threat mitigation plans..................................................................................................9
Legal and ethical considerations..................................................................................12
Conclusion....................................................................................................................13
References....................................................................................................................14
Appendix......................................................................................................................18
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
PROACTIVE NETWORK DEFENCE
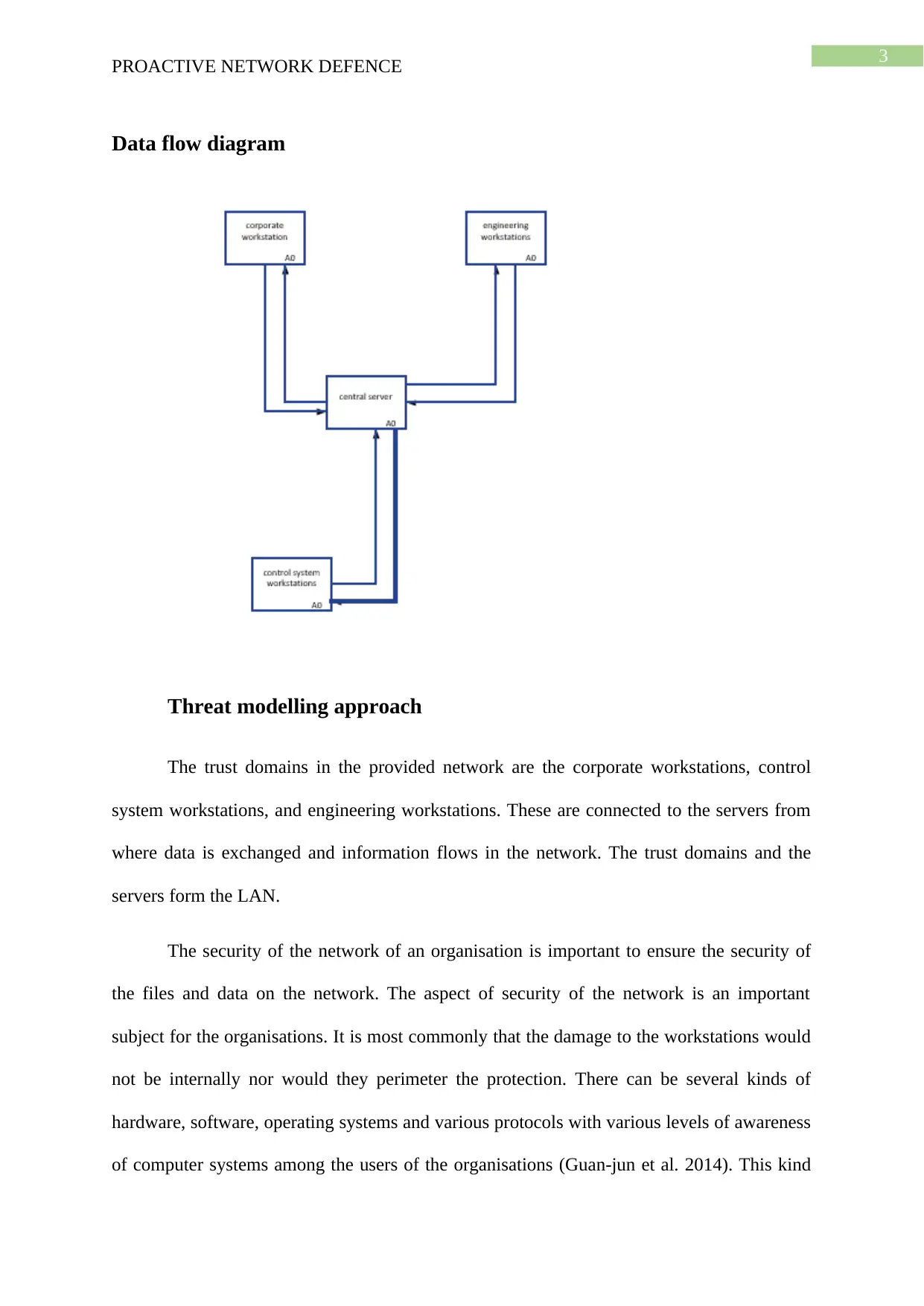
Data flow diagram
Threat modelling approach
The trust domains in the provided network are the corporate workstations, control
system workstations, and engineering workstations. These are connected to the servers from
where data is exchanged and information flows in the network. The trust domains and the
servers form the LAN.
The security of the network of an organisation is important to ensure the security of
the files and data on the network. The aspect of security of the network is an important
subject for the organisations. It is most commonly that the damage to the workstations would
not be internally nor would they perimeter the protection. There can be several kinds of
hardware, software, operating systems and various protocols with various levels of awareness
of computer systems among the users of the organisations (Guan-jun et al. 2014). This kind
PROACTIVE NETWORK DEFENCE
Data flow diagram
Threat modelling approach
The trust domains in the provided network are the corporate workstations, control
system workstations, and engineering workstations. These are connected to the servers from
where data is exchanged and information flows in the network. The trust domains and the
servers form the LAN.
The security of the network of an organisation is important to ensure the security of
the files and data on the network. The aspect of security of the network is an important
subject for the organisations. It is most commonly that the damage to the workstations would
not be internally nor would they perimeter the protection. There can be several kinds of
hardware, software, operating systems and various protocols with various levels of awareness
of computer systems among the users of the organisations (Guan-jun et al. 2014). This kind
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
PROACTIVE NETWORK DEFENCE
of unsecured network grows to be a target for any kind of attack that holds and alters the
sensitive information and it presents the vulnerabilities. The security of the network starts
from the authentication of any user for accessing information in the network most commonly
using the password and username that is provided to them. Once the process of authentication
is completed, the firewall implements the policies of accessing like the services that are
allowed to be accessed by the users (Xingang, Jiaoli and Bei 2013). Even though the firewall
protects the unauthorised use of any explicit use of services, it fails to check the threats due to
worms or viruses. Trojans and viruses can be inserted in the network through the firewalls.
The intrusion system that is implemented in the network helps in detecting and inhibiting the
actions of several kinds of malware in the network. The anomaly based intrusion detection
system detects the anomalies in the network and prevents further damage to the network of
any organisation. The communication among two host that are using a network can be
encrypted for maintaining the privacy of the communication. As the creation of the several
huge open networks, the threats to security amplified with the expansion of the business
(Waliullah and Gan 2014).
If proper security plans are not implemented for the network and the data, they
become vulnerable to attacks. These attacks can be active or passive, passive denotes to the
monitoring of information and any other is active denotes that the alteration of the
information is being done for corrupting or destroying the data or the network (Duric et al.
2016). Commonly, data is sent in plain text which is considered to be an unsecured way that
allows any attacker for gaining permission to data paths in the network for eavesdropping or
gaining enhanced access to network of the organisation. Some basic threats that are related to
the trust domains in the network are:
Passive attack: This attack tries to gain knowledge or utilise the information that is
available from the system from any isolated place but it does not affects the resources of the
PROACTIVE NETWORK DEFENCE
of unsecured network grows to be a target for any kind of attack that holds and alters the
sensitive information and it presents the vulnerabilities. The security of the network starts
from the authentication of any user for accessing information in the network most commonly
using the password and username that is provided to them. Once the process of authentication
is completed, the firewall implements the policies of accessing like the services that are
allowed to be accessed by the users (Xingang, Jiaoli and Bei 2013). Even though the firewall
protects the unauthorised use of any explicit use of services, it fails to check the threats due to
worms or viruses. Trojans and viruses can be inserted in the network through the firewalls.
The intrusion system that is implemented in the network helps in detecting and inhibiting the
actions of several kinds of malware in the network. The anomaly based intrusion detection
system detects the anomalies in the network and prevents further damage to the network of
any organisation. The communication among two host that are using a network can be
encrypted for maintaining the privacy of the communication. As the creation of the several
huge open networks, the threats to security amplified with the expansion of the business
(Waliullah and Gan 2014).
If proper security plans are not implemented for the network and the data, they
become vulnerable to attacks. These attacks can be active or passive, passive denotes to the
monitoring of information and any other is active denotes that the alteration of the
information is being done for corrupting or destroying the data or the network (Duric et al.
2016). Commonly, data is sent in plain text which is considered to be an unsecured way that
allows any attacker for gaining permission to data paths in the network for eavesdropping or
gaining enhanced access to network of the organisation. Some basic threats that are related to
the trust domains in the network are:
Passive attack: This attack tries to gain knowledge or utilise the information that is
available from the system from any isolated place but it does not affects the resources of the

5
PROACTIVE NETWORK DEFENCE
systems. This means the attacker can obtain the information of the system but they cannot
gain access to the resources of the system. Passive attack are commonly considered as
eavesdropping or observing the transmission of the information. The main aim of the
unauthorised user is to gain all the information, which is transmitting from one point to
another (Yao et al. 2014). It is significantly problematic in detecting the passive attacks as
there is no kind of alteration of data. Commonly, in the passive attacks the traffic of the
message is not sent and it is received in normal order and the receiver and the sender does not
have any knowledge that the messages have been read by any third party individual or have
monitored the pattern of traffic that is used by the media of transmission. Moreover, it is
commonly possible to avert the success of these kinds of attacks by the utilisation of
encryption of the informations (Tucker et al. 2015). Therefore, focus is more on the
prevention than it is on the detection during any passive attacks.
Active attacks: The active attacks comprises several alteration and the alteration of
data stream or formation of the stream of false data and it can be grouped in four sections:
a. Masquerade: this happens when the behaviour of an entity is same as another
entity. This part involves the sequences of authentication can be replayed and
captured when any valid authentication sequence has occurred and thus allowing
the authorised entity with several privileges for obtaining the additional privileges
by the personification of any entity that contains the privileges.
b. Replay: This phase contains the passive data stream capture and the consequent
retransmission for producing any unauthorised effect by any third party.
Distributed attacks: Any distributed attacks involves the introduction of the code
like back-door program or Trojan Horse for the trusted software that would later by circulated
to several other companies and the users of the companies (Han et al. 2015). The distribution
PROACTIVE NETWORK DEFENCE
systems. This means the attacker can obtain the information of the system but they cannot
gain access to the resources of the system. Passive attack are commonly considered as
eavesdropping or observing the transmission of the information. The main aim of the
unauthorised user is to gain all the information, which is transmitting from one point to
another (Yao et al. 2014). It is significantly problematic in detecting the passive attacks as
there is no kind of alteration of data. Commonly, in the passive attacks the traffic of the
message is not sent and it is received in normal order and the receiver and the sender does not
have any knowledge that the messages have been read by any third party individual or have
monitored the pattern of traffic that is used by the media of transmission. Moreover, it is
commonly possible to avert the success of these kinds of attacks by the utilisation of
encryption of the informations (Tucker et al. 2015). Therefore, focus is more on the
prevention than it is on the detection during any passive attacks.
Active attacks: The active attacks comprises several alteration and the alteration of
data stream or formation of the stream of false data and it can be grouped in four sections:
a. Masquerade: this happens when the behaviour of an entity is same as another
entity. This part involves the sequences of authentication can be replayed and
captured when any valid authentication sequence has occurred and thus allowing
the authorised entity with several privileges for obtaining the additional privileges
by the personification of any entity that contains the privileges.
b. Replay: This phase contains the passive data stream capture and the consequent
retransmission for producing any unauthorised effect by any third party.
Distributed attacks: Any distributed attacks involves the introduction of the code
like back-door program or Trojan Horse for the trusted software that would later by circulated
to several other companies and the users of the companies (Han et al. 2015). The distribution
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
PROACTIVE NETWORK DEFENCE
attacks emphasises on malicious variation and alteration of the software or hardware during
the distribution. These attacks majorly introduces the malicious code like the back door for
any product for gaining authorisation of accessing of the information or to any function of the
system later.
Insider attacks: the insider attacks consists of someone from inside like any
authorised employee, attacking the network. This kind of attack can be malicious or no
malicious. Any insider attack is considered to be a malicious attack when it is intended to
damage the network of the organisation and it is carried out by any person with authorised
access to the system (Singh, Mishra and Barwal 2014). The insider attackers hold a distinct
advantage over the attackers without any authorised access as the insider attackers possess all
the protocols and the design of the network.
Close in attack: any close in attack implicates any individual trying in getting
physically close to the data on the network, the systems and the components for learning
about the network. The close-in attack consists of unvarying individuals managing nearby
physical vicinity to the systems, networks, or the facilities for collecting and altering or
disagreeing the access to the information. The close physical vicinity is obtained with the
surreptitious entry in the network or open access (Chang 2013). The most common practise
of the close in attack is the social engineering. Any social engineering attack involves the
compromise of the system or the network with the social interaction with any person, with
any phone or email.
Hijack attacks: In any hijack attack, any hacker possess over any session among the
innocent user as well as the server and then disengages the other individuals from the
medium of communication.
PROACTIVE NETWORK DEFENCE
attacks emphasises on malicious variation and alteration of the software or hardware during
the distribution. These attacks majorly introduces the malicious code like the back door for
any product for gaining authorisation of accessing of the information or to any function of the
system later.
Insider attacks: the insider attacks consists of someone from inside like any
authorised employee, attacking the network. This kind of attack can be malicious or no
malicious. Any insider attack is considered to be a malicious attack when it is intended to
damage the network of the organisation and it is carried out by any person with authorised
access to the system (Singh, Mishra and Barwal 2014). The insider attackers hold a distinct
advantage over the attackers without any authorised access as the insider attackers possess all
the protocols and the design of the network.
Close in attack: any close in attack implicates any individual trying in getting
physically close to the data on the network, the systems and the components for learning
about the network. The close-in attack consists of unvarying individuals managing nearby
physical vicinity to the systems, networks, or the facilities for collecting and altering or
disagreeing the access to the information. The close physical vicinity is obtained with the
surreptitious entry in the network or open access (Chang 2013). The most common practise
of the close in attack is the social engineering. Any social engineering attack involves the
compromise of the system or the network with the social interaction with any person, with
any phone or email.
Hijack attacks: In any hijack attack, any hacker possess over any session among the
innocent user as well as the server and then disengages the other individuals from the
medium of communication.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
PROACTIVE NETWORK DEFENCE
Denial of services attacks: The denial of service attacks involves the attack on the
network that is intended in damaging the network by the flooding of excess traffic. In the
computing network, the DoS attacks is any attempt for making the network or the machine
resources unavailable for the envisioned users for indefinitely or temporarily interrupt or
suspend services of the host that is connected to internet (Ding et al. 2014). The DoS attacks
can be originated in several methods, such as transmission failure, traffic redirection, DNS
attacks or the connection flooding.
Some other threats associated with the network of the trust domains are as follows:
The wireless LANs have obtained significant importance than the wired networks as
the cost-effectiveness and flexibility and the simplicity of the installation. Moreover, the
increase in the disposition of the WLAN represents the cracker or the hacker with increased
prospects (Huang et al. 2014). Unlike the networks with wired technologies, the WLANs
transmits data through the medium of air by using the infrared radio or frequency
transmission. The present wireless technology provides the opportunity to any attacker for
monitoring any network wireless methods and in the worst case it can affect the data
integrity. In recent times, many issues of security that grants the IT security professional and
the administrator of system who are working to secure the network with major complications
(Le et al. 2013). The major threats to the WLAN is due to the fact that the WLAN utilises the
radio frequency for the transmission of the information and thus making it very prone to
attacks. These attacks are commonly focused on the damaging or interrupting the functioning
of the network. The attacks can be classified in two segments:
Passive attacks: These kinds of attacks on the WLAN are intended in obtaining the
transmitted information or the received information by the network. The detection of these
PROACTIVE NETWORK DEFENCE
Denial of services attacks: The denial of service attacks involves the attack on the
network that is intended in damaging the network by the flooding of excess traffic. In the
computing network, the DoS attacks is any attempt for making the network or the machine
resources unavailable for the envisioned users for indefinitely or temporarily interrupt or
suspend services of the host that is connected to internet (Ding et al. 2014). The DoS attacks
can be originated in several methods, such as transmission failure, traffic redirection, DNS
attacks or the connection flooding.
Some other threats associated with the network of the trust domains are as follows:
The wireless LANs have obtained significant importance than the wired networks as
the cost-effectiveness and flexibility and the simplicity of the installation. Moreover, the
increase in the disposition of the WLAN represents the cracker or the hacker with increased
prospects (Huang et al. 2014). Unlike the networks with wired technologies, the WLANs
transmits data through the medium of air by using the infrared radio or frequency
transmission. The present wireless technology provides the opportunity to any attacker for
monitoring any network wireless methods and in the worst case it can affect the data
integrity. In recent times, many issues of security that grants the IT security professional and
the administrator of system who are working to secure the network with major complications
(Le et al. 2013). The major threats to the WLAN is due to the fact that the WLAN utilises the
radio frequency for the transmission of the information and thus making it very prone to
attacks. These attacks are commonly focused on the damaging or interrupting the functioning
of the network. The attacks can be classified in two segments:
Passive attacks: These kinds of attacks on the WLAN are intended in obtaining the
transmitted information or the received information by the network. The detection of these

8
PROACTIVE NETWORK DEFENCE
kinds of attack is considerably difficult as the modification of the contents is not done by the
attackers (Farina et al. 2016)
Active attacks: The active attacks are the kind of attacks where any attacker obtains
access to all the information on the network and they alters the information on the network or
produce the false information on the network (Zhang, Cho and Shieh 2015). This kind of
malicious attacks results in the immense loss of the organisation. Some of the active attacks
on the LAN of the organisations can be categorised as:
A. Confidentiality attacks: This type of attacks involves the attempts of intruders to seize
the valuable or the sensitive information, which is being transmitted over the wireless
connection either with encryption or without any encryption of the information. The
passive attacks that threatens the confidentiality of the information on WLAN are
Man-in-the-middle attacks, Eavesdropping, traffic analysis (Kizza 2013). The active
attacks consists of the evil twin AP, the AP phishing and WEP key crackin.
1. Traffic analysis: It is also referred as the foot printing and this is the first stage
involved in the executing further attacks. In the phase, the communication load,
the packets number, the packet size and the destination and the sources of the
packets that is being received and transmitted over the network is determined
(Waliullah and Gan 2014).
2. Eavesdropping: Any eavesdrop attack allows the attacker in gaining the access to
the traffic of the network and it reads the contents of any message that is being
transferred over the network. Wireless session and the payload is closely
monitored by the attacker. If the encryption of the message is done, then the
attacker can obtain the message that is encrypted (Upadhyay and Shukla 2013).
The information regarding the packets, particularly the destination size, source
and the number and the time of the transmission can be obtained by the attacker.
PROACTIVE NETWORK DEFENCE
kinds of attack is considerably difficult as the modification of the contents is not done by the
attackers (Farina et al. 2016)
Active attacks: The active attacks are the kind of attacks where any attacker obtains
access to all the information on the network and they alters the information on the network or
produce the false information on the network (Zhang, Cho and Shieh 2015). This kind of
malicious attacks results in the immense loss of the organisation. Some of the active attacks
on the LAN of the organisations can be categorised as:
A. Confidentiality attacks: This type of attacks involves the attempts of intruders to seize
the valuable or the sensitive information, which is being transmitted over the wireless
connection either with encryption or without any encryption of the information. The
passive attacks that threatens the confidentiality of the information on WLAN are
Man-in-the-middle attacks, Eavesdropping, traffic analysis (Kizza 2013). The active
attacks consists of the evil twin AP, the AP phishing and WEP key crackin.
1. Traffic analysis: It is also referred as the foot printing and this is the first stage
involved in the executing further attacks. In the phase, the communication load,
the packets number, the packet size and the destination and the sources of the
packets that is being received and transmitted over the network is determined
(Waliullah and Gan 2014).
2. Eavesdropping: Any eavesdrop attack allows the attacker in gaining the access to
the traffic of the network and it reads the contents of any message that is being
transferred over the network. Wireless session and the payload is closely
monitored by the attacker. If the encryption of the message is done, then the
attacker can obtain the message that is encrypted (Upadhyay and Shukla 2013).
The information regarding the packets, particularly the destination size, source
and the number and the time of the transmission can be obtained by the attacker.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
PROACTIVE NETWORK DEFENCE
Significantly, there are several manoeuvring antennas that are accessible in the
market that can be used for detecting the malicious transmissions.
3. Man-in-the-middle attack: This kind of attack can be utilised for reading the
private data from any session or for modifying them and therefore breaching the
integrity and the confidentiality of data. The indirect data confidentiality of broken
by this kind of attack (Waliullah, Moniruzzaman and Rahman 2015). Moreover,
any organisation could implement several security mechanisms like IPsec or VPN
that simply provides protection against the confidentiality attacks on data.
B. Access control attacks: These kinds of attacks are targeted for penetrating the network
by dodging the firewalls and the filters for gaining unauthorised access, rogue access
points, war driving and unauthorised access.
C. Integrity attacks: Any integrity attack modifies the data during the transmission of the
data. This attack consists of the alteration, adding or deleting the frames or data of the
management by the intruder that means the forged control packets to network, that can
deceive the recipient or facilitate alternative kind of attack (Youssef et al. 2016). The
DoS attack is the most common kind of attack which is different than data replay,
session hijacking, frame injection, replay attacks and the data deletion.
D. Availability attacks: This kind of attacks averts or it forbids the authentic clients by
restricting the access to all the information that is requested by them on the network
(Xing, Lan and Hu 2013). The DoS attack is considered to be the most common attack
that makes renders the network unusable.
E. Authentication attack: Any intruder steals all the identities of te legitimates user and
the credentials for gaining access to the private or the public WLAN or the services.
The dictionary attacks are the brute force attacks are most common methods of
executing this attacks (Runxi 2013). As soon as the information is obtained by the
PROACTIVE NETWORK DEFENCE
Significantly, there are several manoeuvring antennas that are accessible in the
market that can be used for detecting the malicious transmissions.
3. Man-in-the-middle attack: This kind of attack can be utilised for reading the
private data from any session or for modifying them and therefore breaching the
integrity and the confidentiality of data. The indirect data confidentiality of broken
by this kind of attack (Waliullah, Moniruzzaman and Rahman 2015). Moreover,
any organisation could implement several security mechanisms like IPsec or VPN
that simply provides protection against the confidentiality attacks on data.
B. Access control attacks: These kinds of attacks are targeted for penetrating the network
by dodging the firewalls and the filters for gaining unauthorised access, rogue access
points, war driving and unauthorised access.
C. Integrity attacks: Any integrity attack modifies the data during the transmission of the
data. This attack consists of the alteration, adding or deleting the frames or data of the
management by the intruder that means the forged control packets to network, that can
deceive the recipient or facilitate alternative kind of attack (Youssef et al. 2016). The
DoS attack is the most common kind of attack which is different than data replay,
session hijacking, frame injection, replay attacks and the data deletion.
D. Availability attacks: This kind of attacks averts or it forbids the authentic clients by
restricting the access to all the information that is requested by them on the network
(Xing, Lan and Hu 2013). The DoS attack is considered to be the most common attack
that makes renders the network unusable.
E. Authentication attack: Any intruder steals all the identities of te legitimates user and
the credentials for gaining access to the private or the public WLAN or the services.
The dictionary attacks are the brute force attacks are most common methods of
executing this attacks (Runxi 2013). As soon as the information is obtained by the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
PROACTIVE NETWORK DEFENCE
attacker, the attacker then impersonates as the authorised user and gains all the
authorised privileges in the network.
Threat mitigation plans
The threat mitigation plans for eliminating the above mentioned threats are as follows:
It is essential to implement proper security measuring for ensuring the safe and secured
transmission of information through the network. Prevention from the threats of WLAN
must be measured all through the advancement lifecycle of the WLAN, which starts from
the early design and the stage of deployment with the maintenance, implementation, and
the observing the security measures. The utilisation of robust encryption standards
protects the WLAN from the worse threats.
Another method that can be used for securing the WLAN of the organisations is
disabling the SSID, which hides the point of access. It means the user need to manually
configure the name of the network and the password for accessing the WLAN (Noor and
Hassan 2013). The captive portal is another method that is used in several organisations
for effective transmission of data on a secured network.
The VLAN or Virtual Local Area Network is a method that can be used for securing the
WLAN of the organisations. It is most used for corporation of the wireless network for
enforcing the security policy (Khan et al. 2016). The VLANs work by the tagging of
frames of LAN that is allocated to various workgroups. Tags commonly determines the
received frames place and where it can and cannot enter in the network.
A wireless intrusion prevention and detection system can be utilised for the identification
of the intrusions and then informing the system administrator about the attacks. The
passive sniffing of the network cannot be stopped using the conventional firewalls (Puthal
et al. 2016). Due to this, the WIPS/WIDS could be installed for acting as the regulator for
PROACTIVE NETWORK DEFENCE
attacker, the attacker then impersonates as the authorised user and gains all the
authorised privileges in the network.
Threat mitigation plans
The threat mitigation plans for eliminating the above mentioned threats are as follows:
It is essential to implement proper security measuring for ensuring the safe and secured
transmission of information through the network. Prevention from the threats of WLAN
must be measured all through the advancement lifecycle of the WLAN, which starts from
the early design and the stage of deployment with the maintenance, implementation, and
the observing the security measures. The utilisation of robust encryption standards
protects the WLAN from the worse threats.
Another method that can be used for securing the WLAN of the organisations is
disabling the SSID, which hides the point of access. It means the user need to manually
configure the name of the network and the password for accessing the WLAN (Noor and
Hassan 2013). The captive portal is another method that is used in several organisations
for effective transmission of data on a secured network.
The VLAN or Virtual Local Area Network is a method that can be used for securing the
WLAN of the organisations. It is most used for corporation of the wireless network for
enforcing the security policy (Khan et al. 2016). The VLANs work by the tagging of
frames of LAN that is allocated to various workgroups. Tags commonly determines the
received frames place and where it can and cannot enter in the network.
A wireless intrusion prevention and detection system can be utilised for the identification
of the intrusions and then informing the system administrator about the attacks. The
passive sniffing of the network cannot be stopped using the conventional firewalls (Puthal
et al. 2016). Due to this, the WIPS/WIDS could be installed for acting as the regulator for

11
PROACTIVE NETWORK DEFENCE
detecting and preventing threats and any kind of spiteful activities. VPN is commonly
used with the WIDS/WIPS can offer a robust security mechanism by the active observing
of the network for identifying the irregularities in the network.
NAC or Network Access Control is considered to be another method that can used by the
organisations for authentication technology and it provides an extra security measures.
Instead of the filtering of the traffic based on the port numbers and the IP addresses, the
NAC regulates the permission of accessing of the user to the resources of the network
based on the authentic user identity of the sender, the condition of the device of the user
and the configured policy (Singh, Mishra and Barwal 2014). With the NAC, the devices
on the network like the Aps, routers, Ethernet switches, and the firewalls can control the
access but are enforcing the decisions that are created by the NAC.
The threat mitigation plans for the network can be implemented using several methods.
A protocol can be implemented for the fake route detection and it also adopts the
measures of prevention against the nodes of wormhole from reappearing in the phase of
route discovery. This can be achieved with the use of monitoring method of the neighbour
node of each node and the detection method of wormhole route of the source node on
selected route (Gomzin 2014). This mechanism has been implemented on the basis of the
DSR protocol.
A trust based model can be implemented that is based on the identification and the
isolation of the nodes that creates a wormhole in the network deprived of engagement of
any means of cryptography. This method includes the derivation of the trust levels in the
neighbouring nodes on the basis on the sincerity in the execution of the protocol of
routing. The use of this derived trust is done for influencing the decisions of routing, that
guides a node for avoiding the communication through the wormholes. The major
advantages of using this method is the reduction of the packet dropping without the use of
PROACTIVE NETWORK DEFENCE
detecting and preventing threats and any kind of spiteful activities. VPN is commonly
used with the WIDS/WIPS can offer a robust security mechanism by the active observing
of the network for identifying the irregularities in the network.
NAC or Network Access Control is considered to be another method that can used by the
organisations for authentication technology and it provides an extra security measures.
Instead of the filtering of the traffic based on the port numbers and the IP addresses, the
NAC regulates the permission of accessing of the user to the resources of the network
based on the authentic user identity of the sender, the condition of the device of the user
and the configured policy (Singh, Mishra and Barwal 2014). With the NAC, the devices
on the network like the Aps, routers, Ethernet switches, and the firewalls can control the
access but are enforcing the decisions that are created by the NAC.
The threat mitigation plans for the network can be implemented using several methods.
A protocol can be implemented for the fake route detection and it also adopts the
measures of prevention against the nodes of wormhole from reappearing in the phase of
route discovery. This can be achieved with the use of monitoring method of the neighbour
node of each node and the detection method of wormhole route of the source node on
selected route (Gomzin 2014). This mechanism has been implemented on the basis of the
DSR protocol.
A trust based model can be implemented that is based on the identification and the
isolation of the nodes that creates a wormhole in the network deprived of engagement of
any means of cryptography. This method includes the derivation of the trust levels in the
neighbouring nodes on the basis on the sincerity in the execution of the protocol of
routing. The use of this derived trust is done for influencing the decisions of routing, that
guides a node for avoiding the communication through the wormholes. The major
advantages of using this method is the reduction of the packet dropping without the use of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





