Professional Issues Assignment: Analysis of IT Scenarios and Factors
VerifiedAdded on 2022/09/11
|13
|3373
|31
Report
AI Summary
This report examines professional issues within the IT industry, focusing on two distinct scenarios. The first scenario involves a quality assurance engineer facing pressure to ship potentially defective servers, leading to discussions around legal factors such as breach of privacy and potential data loss, as well as ethical considerations related to honesty and public interest. The second scenario addresses a software developer who copies code, raising copyright infringement concerns and professional conduct issues. The analysis delves into legal, professional, employment, social, personal, and intrinsic factors for both scenarios, prioritizing the key issues and providing a decision based on the ethical implications. The report emphasizes the importance of ethical practices, adherence to legal frameworks, and the impact of personal and organizational values in the IT field.

Student Name
Student No.
7101ICT
Trimester n, 202n
Professional Issues Assignment 1
<For the postgrad version of this course, your assignment should be 2500 words
(plus or minus 10%) – word count is calculated as everything from the Introduction to
the Conclusion – it doesn’t include the Table of Contents, or References – delete this
advice before submitting>
Due Date: time, dd/mm/yy
Lecturer: David Tuffley
Campus (NA, LG, GC):
Student No.
7101ICT
Trimester n, 202n
Professional Issues Assignment 1
<For the postgrad version of this course, your assignment should be 2500 words
(plus or minus 10%) – word count is calculated as everything from the Introduction to
the Conclusion – it doesn’t include the Table of Contents, or References – delete this
advice before submitting>
Due Date: time, dd/mm/yy
Lecturer: David Tuffley
Campus (NA, LG, GC):
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Professional Issues Assignment Introduction
Contents
1. Introduction 2
2. Analysis 3
2.1. Legal factors...............................................................................3
2.1.1. Scenario 1.1.........................................................................3
2.1.2. Scenario 1.2.........................................................................3
2.2. Professional factors....................................................................3
2.2.1. Scenario 1.1.........................................................................3
2.2.2. Scenario 1.2.........................................................................3
2.3. Employment and Social factors..................................................3
2.3.1. Scenario 1.1.........................................................................4
2.3.2. Scenario 1.2.........................................................................4
2.4. Personal factors..........................................................................4
2.4.1. Scenario 1.1.........................................................................4
2.4.2. Scenario 1.2.........................................................................4
2.5. Intrinsic factors............................................................................4
2.5.1. Scenario 1.1.........................................................................4
2.5.2. Scenario 1.2.........................................................................4
2.6. Prioritisation................................................................................5
2.6.1. Scenario 1.1.........................................................................5
2.6.1. Scenario 1.2.........................................................................5
2.7. Decision......................................................................................6
2.7.1. Scenario 1.1.........................................................................6
2.7.2. Scenario 1.2.........................................................................6
3. Discussion 7
3.1.1. Scenario 1.1.........................................................................7
3.1.2. Scenario 1.2.........................................................................7
4. Conclusion 7
4.1.1. Scenario 1.1.........................................................................7
4.1.2. Scenario 1.2.........................................................................7
(Student Name, Course, Semester, Year)0 Page 1
Contents
1. Introduction 2
2. Analysis 3
2.1. Legal factors...............................................................................3
2.1.1. Scenario 1.1.........................................................................3
2.1.2. Scenario 1.2.........................................................................3
2.2. Professional factors....................................................................3
2.2.1. Scenario 1.1.........................................................................3
2.2.2. Scenario 1.2.........................................................................3
2.3. Employment and Social factors..................................................3
2.3.1. Scenario 1.1.........................................................................4
2.3.2. Scenario 1.2.........................................................................4
2.4. Personal factors..........................................................................4
2.4.1. Scenario 1.1.........................................................................4
2.4.2. Scenario 1.2.........................................................................4
2.5. Intrinsic factors............................................................................4
2.5.1. Scenario 1.1.........................................................................4
2.5.2. Scenario 1.2.........................................................................4
2.6. Prioritisation................................................................................5
2.6.1. Scenario 1.1.........................................................................5
2.6.1. Scenario 1.2.........................................................................5
2.7. Decision......................................................................................6
2.7.1. Scenario 1.1.........................................................................6
2.7.2. Scenario 1.2.........................................................................6
3. Discussion 7
3.1.1. Scenario 1.1.........................................................................7
3.1.2. Scenario 1.2.........................................................................7
4. Conclusion 7
4.1.1. Scenario 1.1.........................................................................7
4.1.2. Scenario 1.2.........................................................................7
(Student Name, Course, Semester, Year)0 Page 1

Professional Issues Assignment Introduction
1. Introduction
The professional issues in the information technology address the legal,
social, financial, organization and ethical issues in the IT industry. The report
discusses about the two scenarios where one scenario discusses about the non-
ethical way of conducting business and the second one discusses about the
copyright laws and the importance of copyright laws in the IT industry. Therefore,
before doing anything, the employees of the company must know about the
professional and the social issues so that they can maintain ethics while doing their
work in the company.
Scenario 1 says discusses about Rachel who is a quality assurance. The
Company she works for provides servers to its customers. However, the company
have less time to test the servers after they are manufactured. Rachel also did not
test the servers and she would ships the server as if she does not the competitor of
the company would ship it resulting in loss of profit and loss of customers
Scenario 2 discusses about William who works as a software developer in a
company. He was asked to developed a code that he has already developed while
he was working in a start up. He copies the code and the makes the software run, but
he did not know that he has breached the copyright laws and the code is an
intellectual property of the start up.
Both the scenario deals with some professional issues and ethical issues in
the IT companies which will be discussed in detail in this report.
2. Analysis
It is important to know about the several factors that can help the
company to know the professional and the social issues in the IT industry so
that they know about the issues do their work ethically. The various factors
include the legal factors, professional factors, social factors, intrinsic factors
and many more factors.
3. Legal factors
There are various legal factors that should be taken into consideration
by Rachel and William.
(Student Name, Course, Semester, Year)0 Page 2
1. Introduction
The professional issues in the information technology address the legal,
social, financial, organization and ethical issues in the IT industry. The report
discusses about the two scenarios where one scenario discusses about the non-
ethical way of conducting business and the second one discusses about the
copyright laws and the importance of copyright laws in the IT industry. Therefore,
before doing anything, the employees of the company must know about the
professional and the social issues so that they can maintain ethics while doing their
work in the company.
Scenario 1 says discusses about Rachel who is a quality assurance. The
Company she works for provides servers to its customers. However, the company
have less time to test the servers after they are manufactured. Rachel also did not
test the servers and she would ships the server as if she does not the competitor of
the company would ship it resulting in loss of profit and loss of customers
Scenario 2 discusses about William who works as a software developer in a
company. He was asked to developed a code that he has already developed while
he was working in a start up. He copies the code and the makes the software run, but
he did not know that he has breached the copyright laws and the code is an
intellectual property of the start up.
Both the scenario deals with some professional issues and ethical issues in
the IT companies which will be discussed in detail in this report.
2. Analysis
It is important to know about the several factors that can help the
company to know the professional and the social issues in the IT industry so
that they know about the issues do their work ethically. The various factors
include the legal factors, professional factors, social factors, intrinsic factors
and many more factors.
3. Legal factors
There are various legal factors that should be taken into consideration
by Rachel and William.
(Student Name, Course, Semester, Year)0 Page 2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Professional Issues Assignment Introduction
3.1.1. Scenario 1.1
In scenario 1, it is seen that Rachel knows about the bad quality of the
servers that the company provides to its customers. The company gets little
time to test the servers but if they do not provide the customers with the
servers, then the competitor of the company will provide the servers and the
customer will go out of their hands (WARREN, JUSTICE & SUPREME 2018).
Therefore, she has decided that she will ship the product that has higher
probability of failure that can lead to data loss. It is breach in privacy act that
after knowing that the servers are not adequately tested, she will ship the
server knowing that it has problems in them. The customers that have the
server will suffer a data loss. Therefore, it is against the laws to deliver the
products those are defected
3.1.2. Scenario 1.2
In scenario 2, it is seen that William has been hired for a company and
he does the job of software engineer. He previously worked for a start up
where he developed a same code that is given here. Therefore, he copies the
code here. However, legal issue here is that they have breached the copyright
laws. The code is the intellectual property of the start up that William used to
work. Therefore, the start up can file a case against the company in order to
breach the copyright laws and use their code that was copyrighted. It is
important to know about the laws before copying the code. This could have
led to serious trouble for the company if the start up had files a case against
this company that William works. The ethical thing that they can do is to
apologise to the start up company and try to buy the intellectual property from
as the start up company does not exist (Hall & Melvin 2017).
3.2. Professional factors
The professional factors are very important and should be kept in mind
by William and Rachel as they are professionals and they do well for the
public interest and not do anything for their own interest. They are serving the
clients and must keep in mind the code of ethics that says that the public
interest must be kept above all personal, business or sectional interest.
(Student Name, Course, Semester, Year)0 Page 3
3.1.1. Scenario 1.1
In scenario 1, it is seen that Rachel knows about the bad quality of the
servers that the company provides to its customers. The company gets little
time to test the servers but if they do not provide the customers with the
servers, then the competitor of the company will provide the servers and the
customer will go out of their hands (WARREN, JUSTICE & SUPREME 2018).
Therefore, she has decided that she will ship the product that has higher
probability of failure that can lead to data loss. It is breach in privacy act that
after knowing that the servers are not adequately tested, she will ship the
server knowing that it has problems in them. The customers that have the
server will suffer a data loss. Therefore, it is against the laws to deliver the
products those are defected
3.1.2. Scenario 1.2
In scenario 2, it is seen that William has been hired for a company and
he does the job of software engineer. He previously worked for a start up
where he developed a same code that is given here. Therefore, he copies the
code here. However, legal issue here is that they have breached the copyright
laws. The code is the intellectual property of the start up that William used to
work. Therefore, the start up can file a case against the company in order to
breach the copyright laws and use their code that was copyrighted. It is
important to know about the laws before copying the code. This could have
led to serious trouble for the company if the start up had files a case against
this company that William works. The ethical thing that they can do is to
apologise to the start up company and try to buy the intellectual property from
as the start up company does not exist (Hall & Melvin 2017).
3.2. Professional factors
The professional factors are very important and should be kept in mind
by William and Rachel as they are professionals and they do well for the
public interest and not do anything for their own interest. They are serving the
clients and must keep in mind the code of ethics that says that the public
interest must be kept above all personal, business or sectional interest.
(Student Name, Course, Semester, Year)0 Page 3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Professional Issues Assignment Introduction
3.2.1. Scenario 1.1
In the first scenario, it is seen that Rachel is dishonest with her work
and she is shipping the servers that has the probability of failure because if
her company does not do so, the competitor of the company will ship them
and they take away their customers. She is keeping her business interest first.
However she should keep the public interest in the first priority according to
the code of ethics. She should also try to upgrade the quality of life of those
are affected by her work. However, she is not doing so in this case, she is
shipping the defected server to their clients due to the profit of the company
(Brooks, Riemenschneider & Armstrong 2019). The defected server can lead
to data loss of the company and she is not enhancing the quality of life but
degrading the life of them. His is breach in the code of ethics and she must
not do so.
3.2.2. Scenario 1.2
In the second scenario, it is seen that William is copying the code that
he developed for another start up and it is the intellectual property of the start
up. Therefore, he is not showing enough professionalism in this case. He is
keeping his personal interest in this case as he will be rewarded by the
company as the code is running quite well. He is not honest in representation
of skills and knowledge towards his profession and he is stealing codes from
other’s. Therefore, he is breaching the ACS code of ethics. According to the
ACS code of ethics, a person must work competently and diligently for his
stakeholders (Tavani, 2016). However, in this case, William is not working at
all. He is stealing codes and breaking the copyright laws. Because of this,
Company could have been in great trouble. He is not working for the
enhancement of the company but degrading them and that is not at all good
for the company. William is not showing enough professionalism by breaching
the ACS code of ethics.
4. Employment and Social factors
The employment and the social factors are important as they contribute
as much as the legal and the legal and the professional factors.
(Student Name, Course, Semester, Year)0 Page 4
3.2.1. Scenario 1.1
In the first scenario, it is seen that Rachel is dishonest with her work
and she is shipping the servers that has the probability of failure because if
her company does not do so, the competitor of the company will ship them
and they take away their customers. She is keeping her business interest first.
However she should keep the public interest in the first priority according to
the code of ethics. She should also try to upgrade the quality of life of those
are affected by her work. However, she is not doing so in this case, she is
shipping the defected server to their clients due to the profit of the company
(Brooks, Riemenschneider & Armstrong 2019). The defected server can lead
to data loss of the company and she is not enhancing the quality of life but
degrading the life of them. His is breach in the code of ethics and she must
not do so.
3.2.2. Scenario 1.2
In the second scenario, it is seen that William is copying the code that
he developed for another start up and it is the intellectual property of the start
up. Therefore, he is not showing enough professionalism in this case. He is
keeping his personal interest in this case as he will be rewarded by the
company as the code is running quite well. He is not honest in representation
of skills and knowledge towards his profession and he is stealing codes from
other’s. Therefore, he is breaching the ACS code of ethics. According to the
ACS code of ethics, a person must work competently and diligently for his
stakeholders (Tavani, 2016). However, in this case, William is not working at
all. He is stealing codes and breaking the copyright laws. Because of this,
Company could have been in great trouble. He is not working for the
enhancement of the company but degrading them and that is not at all good
for the company. William is not showing enough professionalism by breaching
the ACS code of ethics.
4. Employment and Social factors
The employment and the social factors are important as they contribute
as much as the legal and the legal and the professional factors.
(Student Name, Course, Semester, Year)0 Page 4

Professional Issues Assignment Introduction
4.1.1. Scenario 1.1
From the scenario 1, it is seen that the company cannot have enough
time for the test and quality assurance of the servers. As Rachel is a quality
assurance engineer, she has to the test the quality of the servers. However, in
this case, she has not done and will ship the servers without testing them
otherwise the competitor of the company would have shipped their servers
and take their customers. The company will not say anything to this as their
customers will be taken away. Therefore, from the scenario it can be said that
the organization has no ethical practices and their values are unprofessional
and questionable (Hussain, Wark & Ryan 2018). They have shipped the
servers knowing that it has the highest probability to fail and will lead to data
loss. The customer will be in grave danger if it leads to data loss.
4.1.2. Scenario 1.2
In scenario 2, it can be seen that William has copied a code that he has
developed in a start up that he used to work earlier and the company did not
know anything about this. They were happy that the code is giving them
suitable results but they did check about the code. In this scenario, William
does not do any ethical work and he did not do the work maintaining the
ethics. From here it can be said that he does not have any ethical practices
and his values are unprofessional and questionable. He unethical work could
have led the company in danger and the start up could have filed as case
against the company (Balasubramanian, 2019).
5. Personal factors
The personal factors are also important in the IT industry. The personal
factors must be properly analysed in order to see the unethical behaviour of
Rachel and William
5.1.1. Scenario 1.1
In scenario 1, it is seen that Rachel is doing the work of a quality
assurance engineer and it is her work to test the servers but due to some
factors that can be personal gain from the company or profit of the company
she has not tested the servers properly and will ship the products that have
the probability to fail leading to data loss (Öğütçü, Testik & Chouseinoglou
2016).
(Student Name, Course, Semester, Year)0 Page 5
4.1.1. Scenario 1.1
From the scenario 1, it is seen that the company cannot have enough
time for the test and quality assurance of the servers. As Rachel is a quality
assurance engineer, she has to the test the quality of the servers. However, in
this case, she has not done and will ship the servers without testing them
otherwise the competitor of the company would have shipped their servers
and take their customers. The company will not say anything to this as their
customers will be taken away. Therefore, from the scenario it can be said that
the organization has no ethical practices and their values are unprofessional
and questionable (Hussain, Wark & Ryan 2018). They have shipped the
servers knowing that it has the highest probability to fail and will lead to data
loss. The customer will be in grave danger if it leads to data loss.
4.1.2. Scenario 1.2
In scenario 2, it can be seen that William has copied a code that he has
developed in a start up that he used to work earlier and the company did not
know anything about this. They were happy that the code is giving them
suitable results but they did check about the code. In this scenario, William
does not do any ethical work and he did not do the work maintaining the
ethics. From here it can be said that he does not have any ethical practices
and his values are unprofessional and questionable. He unethical work could
have led the company in danger and the start up could have filed as case
against the company (Balasubramanian, 2019).
5. Personal factors
The personal factors are also important in the IT industry. The personal
factors must be properly analysed in order to see the unethical behaviour of
Rachel and William
5.1.1. Scenario 1.1
In scenario 1, it is seen that Rachel is doing the work of a quality
assurance engineer and it is her work to test the servers but due to some
factors that can be personal gain from the company or profit of the company
she has not tested the servers properly and will ship the products that have
the probability to fail leading to data loss (Öğütçü, Testik & Chouseinoglou
2016).
(Student Name, Course, Semester, Year)0 Page 5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Professional Issues Assignment Introduction
5.1.2. Scenario 1.2
In this case also, due to personal gain William have copied the code of
the start up and did not inform the manager of the company. Because of his
unethical behaviour company could have been in danger and if the company
cannot find the start up then they have rewrite the code and it can lead to the
delay in releasing the product (Smith, & Wong 2016)
6. Intrinsic factors
6.1.1. Scenario 1.1
In scenario 1, it is seen that Rachel is seen shipping defected products
to its customers and it can lead to data loss. Therefore it can be said that she
is self centred due to which she does this in order to increase the profit of the
company and also her profit (Shroff & Keyes 2017). This is unethical and
should not be done by Rachel as the customers depend on them for their
products
6.1.2. Scenario 1.2
In Scenario 2, it is seen that William is copying codes from other
company and using in this company so that he gets some reward. William
might have been doing unethical jobs from childhood and this why he has
done it here also
(Student Name, Course, Semester, Year)0 Page 6
5.1.2. Scenario 1.2
In this case also, due to personal gain William have copied the code of
the start up and did not inform the manager of the company. Because of his
unethical behaviour company could have been in danger and if the company
cannot find the start up then they have rewrite the code and it can lead to the
delay in releasing the product (Smith, & Wong 2016)
6. Intrinsic factors
6.1.1. Scenario 1.1
In scenario 1, it is seen that Rachel is seen shipping defected products
to its customers and it can lead to data loss. Therefore it can be said that she
is self centred due to which she does this in order to increase the profit of the
company and also her profit (Shroff & Keyes 2017). This is unethical and
should not be done by Rachel as the customers depend on them for their
products
6.1.2. Scenario 1.2
In Scenario 2, it is seen that William is copying codes from other
company and using in this company so that he gets some reward. William
might have been doing unethical jobs from childhood and this why he has
done it here also
(Student Name, Course, Semester, Year)0 Page 6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Professional Issues Assignment Introduction
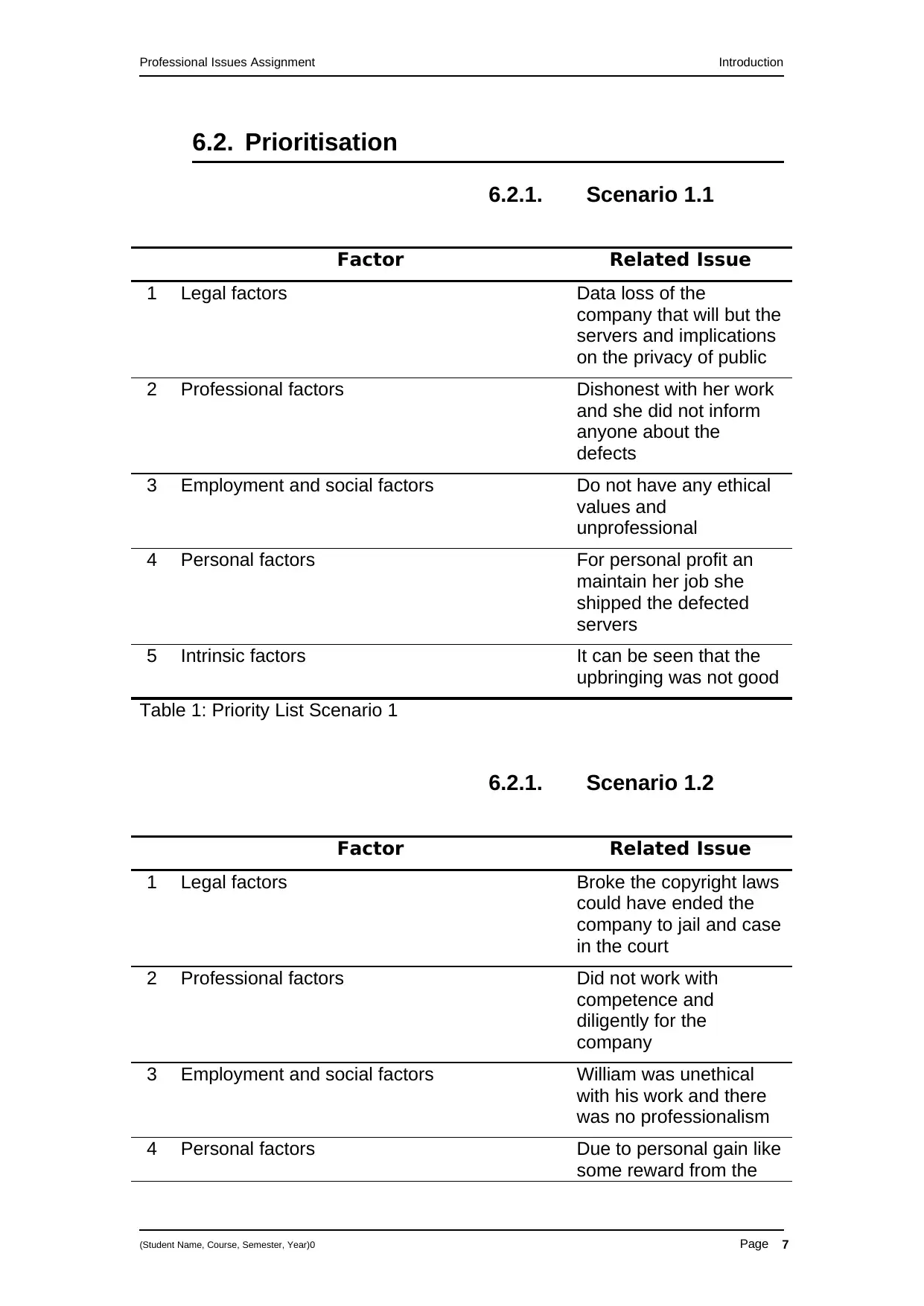
6.2. Prioritisation
6.2.1. Scenario 1.1
Factor Related Issue
1 Legal factors Data loss of the
company that will but the
servers and implications
on the privacy of public
2 Professional factors Dishonest with her work
and she did not inform
anyone about the
defects
3 Employment and social factors Do not have any ethical
values and
unprofessional
4 Personal factors For personal profit an
maintain her job she
shipped the defected
servers
5 Intrinsic factors It can be seen that the
upbringing was not good
Table 1: Priority List Scenario 1
6.2.1. Scenario 1.2
Factor Related Issue
1 Legal factors Broke the copyright laws
could have ended the
company to jail and case
in the court
2 Professional factors Did not work with
competence and
diligently for the
company
3 Employment and social factors William was unethical
with his work and there
was no professionalism
4 Personal factors Due to personal gain like
some reward from the
(Student Name, Course, Semester, Year)0 Page 7
6.2. Prioritisation
6.2.1. Scenario 1.1
Factor Related Issue
1 Legal factors Data loss of the
company that will but the
servers and implications
on the privacy of public
2 Professional factors Dishonest with her work
and she did not inform
anyone about the
defects
3 Employment and social factors Do not have any ethical
values and
unprofessional
4 Personal factors For personal profit an
maintain her job she
shipped the defected
servers
5 Intrinsic factors It can be seen that the
upbringing was not good
Table 1: Priority List Scenario 1
6.2.1. Scenario 1.2
Factor Related Issue
1 Legal factors Broke the copyright laws
could have ended the
company to jail and case
in the court
2 Professional factors Did not work with
competence and
diligently for the
company
3 Employment and social factors William was unethical
with his work and there
was no professionalism
4 Personal factors Due to personal gain like
some reward from the
(Student Name, Course, Semester, Year)0 Page 7

Professional Issues Assignment Introduction
manager of the company
5 Intrinsic factors Fraudulent acts from
childhood that is why he
did this
Table 2: Priority List Scenario 2
7. Decision
7.1.1. Scenario 1.1
From the above table for scenario 1 it can be said that legal issue
should always be prioritised. The company should face legal issues because
they have provided the customers with defected products and it has the
highest probability to fail. The fail of the server means that the data will be
lost. The data can consist of sensitive information of clients and customers of
the company. There are various people that can take advantage of this. It can
have serious implications on the privacy of public. Therefore, the Company
must face legal issue due to this as they are not adequately testing the
Company and Rachel due to her personal interest and increasing the profit of
the company, she is also shipping the products.
7.1.2. Scenario 1.2
In this scenario, the legal issue should always be prioritized as it is an
important factor. The legal issue in this scenario is that the copyright laws
have been broken by Williams and the start up filed a case against the
company as it was their intellectual rights. It is the priority of the company to
mitigate this issue by apologising to the company and try to buy the
intellectual property from the start up otherwise the company would have to
rewrite the code again and the release of their product will be delayed.
(Student Name, Course, Semester, Year)0 Page 8
manager of the company
5 Intrinsic factors Fraudulent acts from
childhood that is why he
did this
Table 2: Priority List Scenario 2
7. Decision
7.1.1. Scenario 1.1
From the above table for scenario 1 it can be said that legal issue
should always be prioritised. The company should face legal issues because
they have provided the customers with defected products and it has the
highest probability to fail. The fail of the server means that the data will be
lost. The data can consist of sensitive information of clients and customers of
the company. There are various people that can take advantage of this. It can
have serious implications on the privacy of public. Therefore, the Company
must face legal issue due to this as they are not adequately testing the
Company and Rachel due to her personal interest and increasing the profit of
the company, she is also shipping the products.
7.1.2. Scenario 1.2
In this scenario, the legal issue should always be prioritized as it is an
important factor. The legal issue in this scenario is that the copyright laws
have been broken by Williams and the start up filed a case against the
company as it was their intellectual rights. It is the priority of the company to
mitigate this issue by apologising to the company and try to buy the
intellectual property from the start up otherwise the company would have to
rewrite the code again and the release of their product will be delayed.
(Student Name, Course, Semester, Year)0 Page 8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Professional Issues Assignment Introduction
8. Discussion
8.1.1. Scenario 1.1
From scenario 1, it can be said that the thing Rachel did was not at all
good and ethical. She should have thought about the implications of the bad
servers and the data loss and can compromise the privacy of pubic. However,
due to the personal interest and profit of the company and in order to maintain
her job she did this unethical job. It can be due to the fact that she has been
raised this way and this is the reason she has done this. The legal issues
must be prioritized as the privacy of the people are important and anybody
can take advantage of the personal details of the public. The decision that is
taken is that the company should face legal issues due to their dishonesty in
their work.
8.1.2.Scenario 1.2
From the second scenario, it can be said that William has showed an example
of unprofessionalism and unethical behaviour. He has copied the code that
developed in the start up and used in this company. He has used the intellectual
property of other company. He has broken the copyright laws and must be fined
for these and must be kept in prison for this behaviour. The thing that the
company should do is buy the intellectual property from the start up otherwise
they have to rewrite the code and their product launch will be delayed due to the
mistake of William.
9. Conclusion
9.1.1. Scenario 1.1
From the scenario 1, it can be inferred that Rachel has showed
dishonesty and unprofessionalism in her work. Due to her personal gain,
maintain her job and profit of the company she has shipped the defected
servers to their customers. The defected servers can lead to data loss and the
data can contain the data of the public. Therefore, the privacy of the public
can be compromised due to this. Rachel must have properly tested the quality
of servers and should not ship the products those are defected in order to
keep her ethics intact. It can be said that the company has unethical practices
and their values are unprofessional and questionable.
(Student Name, Course, Semester, Year)0 Page 9
8. Discussion
8.1.1. Scenario 1.1
From scenario 1, it can be said that the thing Rachel did was not at all
good and ethical. She should have thought about the implications of the bad
servers and the data loss and can compromise the privacy of pubic. However,
due to the personal interest and profit of the company and in order to maintain
her job she did this unethical job. It can be due to the fact that she has been
raised this way and this is the reason she has done this. The legal issues
must be prioritized as the privacy of the people are important and anybody
can take advantage of the personal details of the public. The decision that is
taken is that the company should face legal issues due to their dishonesty in
their work.
8.1.2.Scenario 1.2
From the second scenario, it can be said that William has showed an example
of unprofessionalism and unethical behaviour. He has copied the code that
developed in the start up and used in this company. He has used the intellectual
property of other company. He has broken the copyright laws and must be fined
for these and must be kept in prison for this behaviour. The thing that the
company should do is buy the intellectual property from the start up otherwise
they have to rewrite the code and their product launch will be delayed due to the
mistake of William.
9. Conclusion
9.1.1. Scenario 1.1
From the scenario 1, it can be inferred that Rachel has showed
dishonesty and unprofessionalism in her work. Due to her personal gain,
maintain her job and profit of the company she has shipped the defected
servers to their customers. The defected servers can lead to data loss and the
data can contain the data of the public. Therefore, the privacy of the public
can be compromised due to this. Rachel must have properly tested the quality
of servers and should not ship the products those are defected in order to
keep her ethics intact. It can be said that the company has unethical practices
and their values are unprofessional and questionable.
(Student Name, Course, Semester, Year)0 Page 9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Professional Issues Assignment Introduction
9.1.2. Scenario 1.2
From the second scenario, it can be inferred that William has showed
an example of unethical and unprofessional behaviour. He is dishonest with
his work. He has breached the copyright laws and copied the code of a start
up and pasted in this company due to personal gain. He could have been
taken to jail and fined due to this issue. The company is in danger due to this
because they have needed to buy the intellectual property else their product
launch will be delayed due to the mistake of the company. It can be said that,
William must be honest with his work and must not these things as ethics is
important in the IT industry. They should work for the public interest and not
for personal or business interest.
(Student Name, Course, Semester, Year)0 Page 10
9.1.2. Scenario 1.2
From the second scenario, it can be inferred that William has showed
an example of unethical and unprofessional behaviour. He is dishonest with
his work. He has breached the copyright laws and copied the code of a start
up and pasted in this company due to personal gain. He could have been
taken to jail and fined due to this issue. The company is in danger due to this
because they have needed to buy the intellectual property else their product
launch will be delayed due to the mistake of the company. It can be said that,
William must be honest with his work and must not these things as ethics is
important in the IT industry. They should work for the public interest and not
for personal or business interest.
(Student Name, Course, Semester, Year)0 Page 10

Professional Issues Assignment Introduction
10. References
Balasubramanian, D. (2019). Occupational stress on employees in
information technology organizations-a study. research journal of social
sciences, 10(3). Retrieved from
(http://www.aensi.in/assets/uploads/doc/b19b5-220-230.14503.pdf)
Brooks, N. G., Riemenschneider, C. K., & Armstrong, D. J. (2019). The
Information Technology Professional: A Two-wave Study of Factors Impacting
Commitment and Satisfaction. Communications of the Association for
Information Systems, 44(1), 29. Retrieved From
(https://aisel.aisnet.org/cais/vol44/iss1/29/)
Hall, M. D., & Melvin, M. L. (2017). CSC 403-D1 Social, Ethical and
Professional Issues. Retrieved From
(http://152.6.15.92/Documents/macsc/syllabus/Fall/CSC/CSC403.pdf)
Hussain, R., Wark, S., & Ryan, P. (2018). Caregiving, Employment and Social
Isolation: Challenges for Rural Carers in Australia. International journal of
environmental research and public health, 15(10), 2267. Retrieved From
(https://www.mdpi.com/1660-4601/15/10/2267)
Öğütçü, G., Testik, Ö. M., & Chouseinoglou, O. (2016). Analysis of personal
information security behavior and awareness. Computers & Security, 56, 83-
93. Retrieved From
(https://www.sciencedirect.com/science/article/pii/S0167404815001406)
(Student Name, Course, Semester, Year)0 Page 11
10. References
Balasubramanian, D. (2019). Occupational stress on employees in
information technology organizations-a study. research journal of social
sciences, 10(3). Retrieved from
(http://www.aensi.in/assets/uploads/doc/b19b5-220-230.14503.pdf)
Brooks, N. G., Riemenschneider, C. K., & Armstrong, D. J. (2019). The
Information Technology Professional: A Two-wave Study of Factors Impacting
Commitment and Satisfaction. Communications of the Association for
Information Systems, 44(1), 29. Retrieved From
(https://aisel.aisnet.org/cais/vol44/iss1/29/)
Hall, M. D., & Melvin, M. L. (2017). CSC 403-D1 Social, Ethical and
Professional Issues. Retrieved From
(http://152.6.15.92/Documents/macsc/syllabus/Fall/CSC/CSC403.pdf)
Hussain, R., Wark, S., & Ryan, P. (2018). Caregiving, Employment and Social
Isolation: Challenges for Rural Carers in Australia. International journal of
environmental research and public health, 15(10), 2267. Retrieved From
(https://www.mdpi.com/1660-4601/15/10/2267)
Öğütçü, G., Testik, Ö. M., & Chouseinoglou, O. (2016). Analysis of personal
information security behavior and awareness. Computers & Security, 56, 83-
93. Retrieved From
(https://www.sciencedirect.com/science/article/pii/S0167404815001406)
(Student Name, Course, Semester, Year)0 Page 11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





