Professional Skills for ICT - Melbourne Software Company Report
VerifiedAdded on 2019/11/26
|14
|3708
|144
Report
AI Summary
This report analyzes the professional skills essential for success in the Information and Communication Technology (ICT) field, specifically focusing on a small software company based in Melbourne. It delves into the importance of network security, exploring various threats such as viruses, malware, and ransomware, and the strategies to mitigate these risks. The report highlights the significance of updated antivirus software, firewalls, and intrusion detection systems. It also addresses ethical and social dilemmas, emphasizing the need for strong passwords, VPNs, data backup, and multi-factor authentication. The report outlines the potential opportunities for business development in the market, discussing the use of cloud computing and the expansion of the company. Finally, it identifies the risks associated with insufficient policies, cloud attacks, and the use of external devices like USB drives, providing recommendations for enhancing the company's security posture and ethical practices.

Running head: PROFESSIONAL SKILLS FOR INFORMATION AND COMMUNICATION
TECHNOLOGY
Professional skills for Information and Communication Technology
Name of the Student
Name of the University
Author’s Note
TECHNOLOGY
Professional skills for Information and Communication Technology
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1PROFESSIONAL SKILLS FOR INFORMATION AND COMMUNICATION TECHNOLOGY
Executive Summary
This report focuses on the potential open doors in the market for the advancement of the
organization in the market. Diverse advances and updates in the organization have been
discussed about in report. This report concentrates on the Information security over the web. The
reason for the report is to distinguish the risks engaged with the online information and data of
the organization. This report concentrates on the procedures utilized for moderating the digital
issues in the organization. This report manages the moral and social difficulties of the association
in the market. There are ethical issues discussed in the official administration group taking part
in the life cycle of the business association.
Executive Summary
This report focuses on the potential open doors in the market for the advancement of the
organization in the market. Diverse advances and updates in the organization have been
discussed about in report. This report concentrates on the Information security over the web. The
reason for the report is to distinguish the risks engaged with the online information and data of
the organization. This report concentrates on the procedures utilized for moderating the digital
issues in the organization. This report manages the moral and social difficulties of the association
in the market. There are ethical issues discussed in the official administration group taking part
in the life cycle of the business association.

2PROFESSIONAL SKILLS FOR INFORMATION AND COMMUNICATION TECHNOLOGY
Table of Contents
Introduction......................................................................................................................................4
Network Security.............................................................................................................................5
Risks and Issues...............................................................................................................................8
Insufficient policies.........................................................................................................................9
Conclusion.....................................................................................................................................10
Recommendations..........................................................................................................................10
References......................................................................................................................................13
Table of Contents
Introduction......................................................................................................................................4
Network Security.............................................................................................................................5
Risks and Issues...............................................................................................................................8
Insufficient policies.........................................................................................................................9
Conclusion.....................................................................................................................................10
Recommendations..........................................................................................................................10
References......................................................................................................................................13
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3PROFESSIONAL SKILLS FOR INFORMATION AND COMMUNICATION TECHNOLOGY
Introduction
The ICT has been evolving in the business organization in the recent years. This
organization is a small software based company established five years ago in Melbourne. It used
to develop and customize applications in the information and networking field. The company is
looking for expanding its business in different parts of the country. It is assumed that the
company has a good customer base in the market but still not using the cloud computing services
in their business (Stallings & Tahiliani, 2014). It is assumed that the company is not upgraded to
the latest technologies available in the market. There are various internet issues including the
cyber-attacks with the help of viruses, malwares and ransomware. This have been a big issue for
the company to secure their data and information from these attacks.
This report deals with the potential opportunities in the market for the development of the
company in the market. Different technologies and updates in the industries have been discussed
in report. This report focuses on the Information security over the internet. The purpose of the
report is to identify the risks involved in the online data and information of the company. This
report focuses on the strategies used for mitigating the cyber issues in the company. This report
deals with the ethical and social dilemmas of the organization in the market. There are ethical
issues in the executive management team engaging in the life cycle of the business organization.
This report outlines the methodology to be used for the development of the company in
the market. This report depicts the strategies to be used to mitigate the ethical and social issues of
the company in the market. This report also provide some recommendations that helps in
resolving the challenges faced by the company in the market. The report focuses on the security
and their technological aspects of the security to identify appropriate solutions to overcome the
risks involved.
Network Security
The security to the network of an organization from other intruders over the Internet is
termed as network security (Perlman, Kaufman & Speciner, 2016). System security is the
security gave to a system from unapproved access and dangers. It is the obligation of system
managers to embrace preventive measures to shield their systems from potential security dangers
(Kahate, 2013).
Introduction
The ICT has been evolving in the business organization in the recent years. This
organization is a small software based company established five years ago in Melbourne. It used
to develop and customize applications in the information and networking field. The company is
looking for expanding its business in different parts of the country. It is assumed that the
company has a good customer base in the market but still not using the cloud computing services
in their business (Stallings & Tahiliani, 2014). It is assumed that the company is not upgraded to
the latest technologies available in the market. There are various internet issues including the
cyber-attacks with the help of viruses, malwares and ransomware. This have been a big issue for
the company to secure their data and information from these attacks.
This report deals with the potential opportunities in the market for the development of the
company in the market. Different technologies and updates in the industries have been discussed
in report. This report focuses on the Information security over the internet. The purpose of the
report is to identify the risks involved in the online data and information of the company. This
report focuses on the strategies used for mitigating the cyber issues in the company. This report
deals with the ethical and social dilemmas of the organization in the market. There are ethical
issues in the executive management team engaging in the life cycle of the business organization.
This report outlines the methodology to be used for the development of the company in
the market. This report depicts the strategies to be used to mitigate the ethical and social issues of
the company in the market. This report also provide some recommendations that helps in
resolving the challenges faced by the company in the market. The report focuses on the security
and their technological aspects of the security to identify appropriate solutions to overcome the
risks involved.
Network Security
The security to the network of an organization from other intruders over the Internet is
termed as network security (Perlman, Kaufman & Speciner, 2016). System security is the
security gave to a system from unapproved access and dangers. It is the obligation of system
managers to embrace preventive measures to shield their systems from potential security dangers
(Kahate, 2013).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4PROFESSIONAL SKILLS FOR INFORMATION AND COMMUNICATION TECHNOLOGY
PC organizes that are engaged with customary exchanges and correspondence inside the
administration, people, or business require security. The most widely recognized and basic
method for ensuring a system asset is by allocating it a special name and a relating secret word.
The business organization have been operating over the internet to increase their business in the
market. Therefore, the security of the data and information over the internet is an important part
for the business organization (Knapp & Langill, 2014). The goals and objectives of the business
organization have to be fulfilled with the help of security of information.
Various network security applications are currently used in the market by the business
organization including Antiviruses, Firewalls and Intrusion Detection Systems. The utilization of
the distributed computing helps in putting away critical information and data over the web. The
utilization of a refreshed antivirus and firewalls confine the establishment of some critical
programming and application in the framework. These security applications help in controlling
the cyber-attacks in the business organization. For example, Norton Security is an antivirus
software that protect data and information from the being breached. This application provides
Anti-Spam, Anti-Virus, Email Attachment Protection, Spyware Removal and Web Threat
Management to the users (Pierson & DeHaan, 2015). These features help in providing a secured
environment for the information over the internet. It helps in detecting harmful viruses and
malwares over the internet.
PC organizes that are engaged with customary exchanges and correspondence inside the
administration, people, or business require security. The most widely recognized and basic
method for ensuring a system asset is by allocating it a special name and a relating secret word.
The business organization have been operating over the internet to increase their business in the
market. Therefore, the security of the data and information over the internet is an important part
for the business organization (Knapp & Langill, 2014). The goals and objectives of the business
organization have to be fulfilled with the help of security of information.
Various network security applications are currently used in the market by the business
organization including Antiviruses, Firewalls and Intrusion Detection Systems. The utilization of
the distributed computing helps in putting away critical information and data over the web. The
utilization of a refreshed antivirus and firewalls confine the establishment of some critical
programming and application in the framework. These security applications help in controlling
the cyber-attacks in the business organization. For example, Norton Security is an antivirus
software that protect data and information from the being breached. This application provides
Anti-Spam, Anti-Virus, Email Attachment Protection, Spyware Removal and Web Threat
Management to the users (Pierson & DeHaan, 2015). These features help in providing a secured
environment for the information over the internet. It helps in detecting harmful viruses and
malwares over the internet.
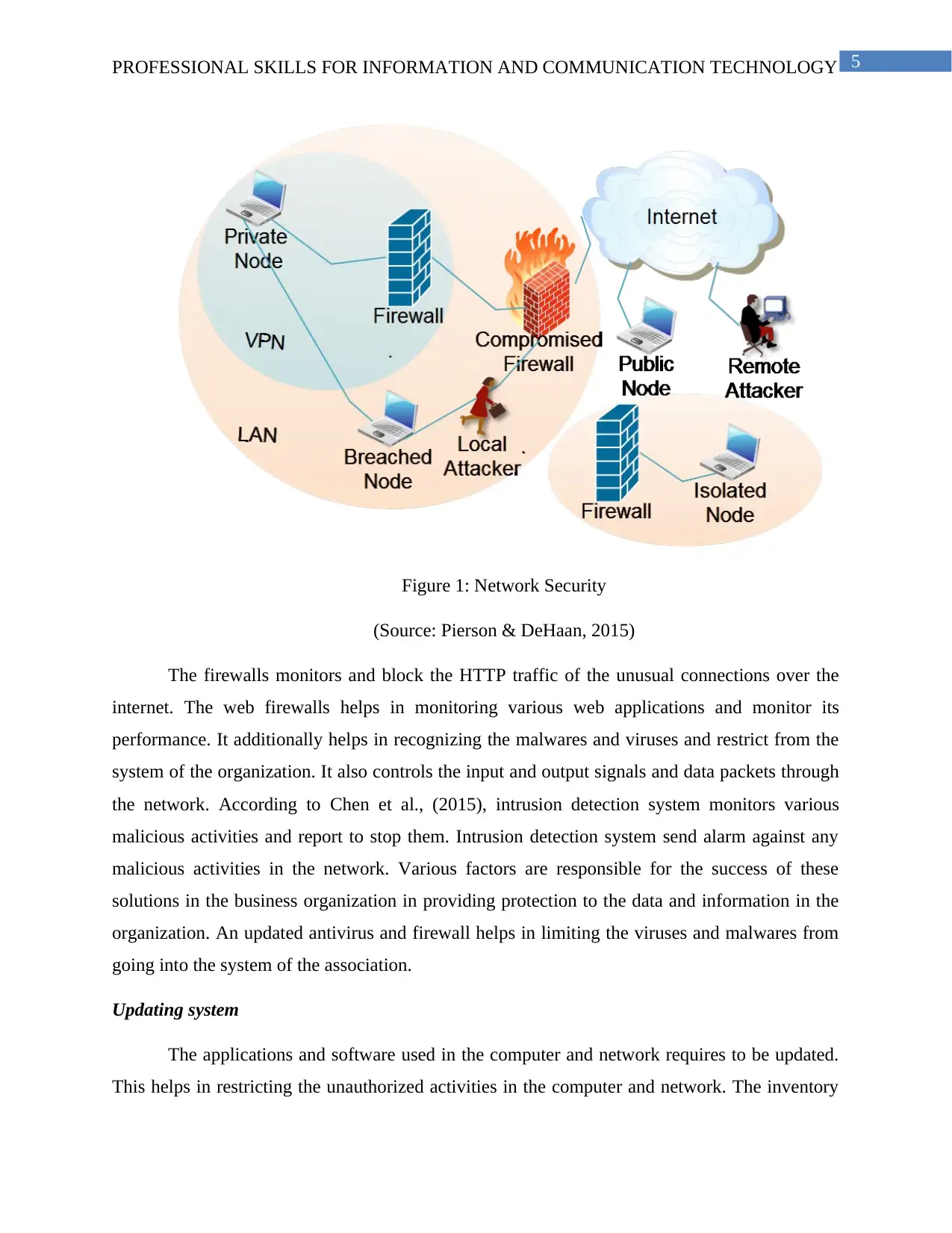
5PROFESSIONAL SKILLS FOR INFORMATION AND COMMUNICATION TECHNOLOGY
Figure 1: Network Security
(Source: Pierson & DeHaan, 2015)
The firewalls monitors and block the HTTP traffic of the unusual connections over the
internet. The web firewalls helps in monitoring various web applications and monitor its
performance. It additionally helps in recognizing the malwares and viruses and restrict from the
system of the organization. It also controls the input and output signals and data packets through
the network. According to Chen et al., (2015), intrusion detection system monitors various
malicious activities and report to stop them. Intrusion detection system send alarm against any
malicious activities in the network. Various factors are responsible for the success of these
solutions in the business organization in providing protection to the data and information in the
organization. An updated antivirus and firewall helps in limiting the viruses and malwares from
going into the system of the association.
Updating system
The applications and software used in the computer and network requires to be updated.
This helps in restricting the unauthorized activities in the computer and network. The inventory
Figure 1: Network Security
(Source: Pierson & DeHaan, 2015)
The firewalls monitors and block the HTTP traffic of the unusual connections over the
internet. The web firewalls helps in monitoring various web applications and monitor its
performance. It additionally helps in recognizing the malwares and viruses and restrict from the
system of the organization. It also controls the input and output signals and data packets through
the network. According to Chen et al., (2015), intrusion detection system monitors various
malicious activities and report to stop them. Intrusion detection system send alarm against any
malicious activities in the network. Various factors are responsible for the success of these
solutions in the business organization in providing protection to the data and information in the
organization. An updated antivirus and firewall helps in limiting the viruses and malwares from
going into the system of the association.
Updating system
The applications and software used in the computer and network requires to be updated.
This helps in restricting the unauthorized activities in the computer and network. The inventory
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6PROFESSIONAL SKILLS FOR INFORMATION AND COMMUNICATION TECHNOLOGY
of the applications and software have to be updated for allowing installation of proper patches
and updates.
Strong Passwords
The passwords and other user credentials requires keeping at safe place. The difficulty
level of the passwords ca be increase by using combination of alphabets, numbers and symbols
(Zaalouk et al., 2014). This provide security of the data and information stored in the packet.
Securing VPN
Information encryption and personality verification are particularly critical to securing a
VPN. Any open system association is a weakness programmers can adventure to sneak onto your
system. Besides, information is especially defenseless while it is going over the Internet. Survey
the documentation for your server and VPN programming to ensure that the most grounded
conceivable conventions for encryption and confirmation are being used (Anwar et al., 2014).
The utilization of the VPN helps sequestered from everything the IP address of the frameworks
associated in the system. Then again, there are a few inconveniences of these arrangements in the
system.
Multi-factor validation is the most secure character confirmation strategy. The more
strides your clients must take to demonstrate their personality, the better. For instance,
notwithstanding a secret word, clients could be required to enter a PIN (Shin et al., 2013). On the
other hand, an irregular numerical code produced by a key-coxcomb authenticator like
clockwork could be utilized as a part of conjunction with a PIN or secret word. The utilization of
the VPN in the system gives additional security to the system.
Backing up Data
The data and information are backed up for recovery. The system back up and disaster
recovery helps in maintaining the backup data and information. In the case of data loss due to
any kind of cyber-attack and data breach, the lost data can be recovered easily.
In this case, the organization is looking for expansion in the market. Therefore, the data
and information regarding business have to be secured. The use of these applications might help
in managing the security and protection of the data and information in the organization (He et al.,
of the applications and software have to be updated for allowing installation of proper patches
and updates.
Strong Passwords
The passwords and other user credentials requires keeping at safe place. The difficulty
level of the passwords ca be increase by using combination of alphabets, numbers and symbols
(Zaalouk et al., 2014). This provide security of the data and information stored in the packet.
Securing VPN
Information encryption and personality verification are particularly critical to securing a
VPN. Any open system association is a weakness programmers can adventure to sneak onto your
system. Besides, information is especially defenseless while it is going over the Internet. Survey
the documentation for your server and VPN programming to ensure that the most grounded
conceivable conventions for encryption and confirmation are being used (Anwar et al., 2014).
The utilization of the VPN helps sequestered from everything the IP address of the frameworks
associated in the system. Then again, there are a few inconveniences of these arrangements in the
system.
Multi-factor validation is the most secure character confirmation strategy. The more
strides your clients must take to demonstrate their personality, the better. For instance,
notwithstanding a secret word, clients could be required to enter a PIN (Shin et al., 2013). On the
other hand, an irregular numerical code produced by a key-coxcomb authenticator like
clockwork could be utilized as a part of conjunction with a PIN or secret word. The utilization of
the VPN in the system gives additional security to the system.
Backing up Data
The data and information are backed up for recovery. The system back up and disaster
recovery helps in maintaining the backup data and information. In the case of data loss due to
any kind of cyber-attack and data breach, the lost data can be recovered easily.
In this case, the organization is looking for expansion in the market. Therefore, the data
and information regarding business have to be secured. The use of these applications might help
in managing the security and protection of the data and information in the organization (He et al.,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7PROFESSIONAL SKILLS FOR INFORMATION AND COMMUNICATION TECHNOLOGY
2014). These factors also help in developing the organization in the market. The proper
management of important data and essential is important for the success of the company in the
market. The growth of the company depends in the security of the data and information in the
market. The security of the details of employees and customers is important to be maintained by
the company for future use. This also helps in enhancing the quality of the services provided to
the customers. This software company is currently working in an off the-shelf application.
Figure 2: Triple-R Framework
(Source: Created by author)
Presently, the customers of the company is limited to different regions of Australia. The
implementation of the off the-shelf application have allowed to connect the company with the
internet and collect many clients all over the world (DeLoach et al., 2014). The use of the online
business helps in gathering the clients from various regions of the world other than Australia.
Therefore, the expansion of the business becomes rapid for the company. Meanwhile, the
customer base of the company is increased with the use of the online business of the IT
applications.
There are various advantages and disadvantages of the solutions of the network security.
The use of the firewalls and antivirus helps in protecting the data and information of the
company. The use of the cloud computing in the management of the company helps in protecting
the data and information over the cloud. The use of the cloud computing helps in storing
Roles
Regulation
Responsibilities
2014). These factors also help in developing the organization in the market. The proper
management of important data and essential is important for the success of the company in the
market. The growth of the company depends in the security of the data and information in the
market. The security of the details of employees and customers is important to be maintained by
the company for future use. This also helps in enhancing the quality of the services provided to
the customers. This software company is currently working in an off the-shelf application.
Figure 2: Triple-R Framework
(Source: Created by author)
Presently, the customers of the company is limited to different regions of Australia. The
implementation of the off the-shelf application have allowed to connect the company with the
internet and collect many clients all over the world (DeLoach et al., 2014). The use of the online
business helps in gathering the clients from various regions of the world other than Australia.
Therefore, the expansion of the business becomes rapid for the company. Meanwhile, the
customer base of the company is increased with the use of the online business of the IT
applications.
There are various advantages and disadvantages of the solutions of the network security.
The use of the firewalls and antivirus helps in protecting the data and information of the
company. The use of the cloud computing in the management of the company helps in protecting
the data and information over the cloud. The use of the cloud computing helps in storing
Roles
Regulation
Responsibilities

8PROFESSIONAL SKILLS FOR INFORMATION AND COMMUNICATION TECHNOLOGY
important data and information over the internet (Moreno, Pudjianto & Strbac, 2013). An
updated antivirus and firewall helps in restricting the viruses and malwares from entering into the
network of the organization. It also helps in detecting the malwares and virus and remove from
the network of the company. The use of the VPN in the network provides extra security to the
network. The use of the VPN helps in hiding the IP address of the systems connected in the
network (Scott-Hayward, O'Callaghan & Sezer, 2013). On the other hand, there are some
disadvantages of these solutions in the network. The use of an updated antivirus and firewalls
restrict the installation of some important software and application in the system. This might
cause loss to the company regarding the use of the application in the system. The use of firewall
restricts some data packets from entering the network that are useful for the company in the
market (Daya, 2013). The technological aspects of the network security have been prevailing in
the company that helps in maintaining the security of the data and information.
Risks and Issues
Various risks and issues are prevailing in the company related to the network security.
The data and information of the company transferred in the network can be traced. There are
various risks involved in the network security of the company over internet.
USB and external devices
The use of the USB drives and other external media poses various risks to the network of
the company. The harmful virus and malwares can enter into the system connected in the
network with the help of the USB and external drives (Beberlein et al., 2017). The users of the
laptops and mobile computing are more prone to the risk of data loss with USBs.
Insufficient policies
The use of emails and other internet facilities in the organization by the employees have
to be educated with the correct use of the system. This helps in maintaining the security of the
systems from being attacked. The risk is involved in the ethical status of the company regarding
the security of the network over internet. There are various social issues of using the network
security regarding g the use of the social websites. These websites are prone to the attack of the
virus and malwares over internet.
important data and information over the internet (Moreno, Pudjianto & Strbac, 2013). An
updated antivirus and firewall helps in restricting the viruses and malwares from entering into the
network of the organization. It also helps in detecting the malwares and virus and remove from
the network of the company. The use of the VPN in the network provides extra security to the
network. The use of the VPN helps in hiding the IP address of the systems connected in the
network (Scott-Hayward, O'Callaghan & Sezer, 2013). On the other hand, there are some
disadvantages of these solutions in the network. The use of an updated antivirus and firewalls
restrict the installation of some important software and application in the system. This might
cause loss to the company regarding the use of the application in the system. The use of firewall
restricts some data packets from entering the network that are useful for the company in the
market (Daya, 2013). The technological aspects of the network security have been prevailing in
the company that helps in maintaining the security of the data and information.
Risks and Issues
Various risks and issues are prevailing in the company related to the network security.
The data and information of the company transferred in the network can be traced. There are
various risks involved in the network security of the company over internet.
USB and external devices
The use of the USB drives and other external media poses various risks to the network of
the company. The harmful virus and malwares can enter into the system connected in the
network with the help of the USB and external drives (Beberlein et al., 2017). The users of the
laptops and mobile computing are more prone to the risk of data loss with USBs.
Insufficient policies
The use of emails and other internet facilities in the organization by the employees have
to be educated with the correct use of the system. This helps in maintaining the security of the
systems from being attacked. The risk is involved in the ethical status of the company regarding
the security of the network over internet. There are various social issues of using the network
security regarding g the use of the social websites. These websites are prone to the attack of the
virus and malwares over internet.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
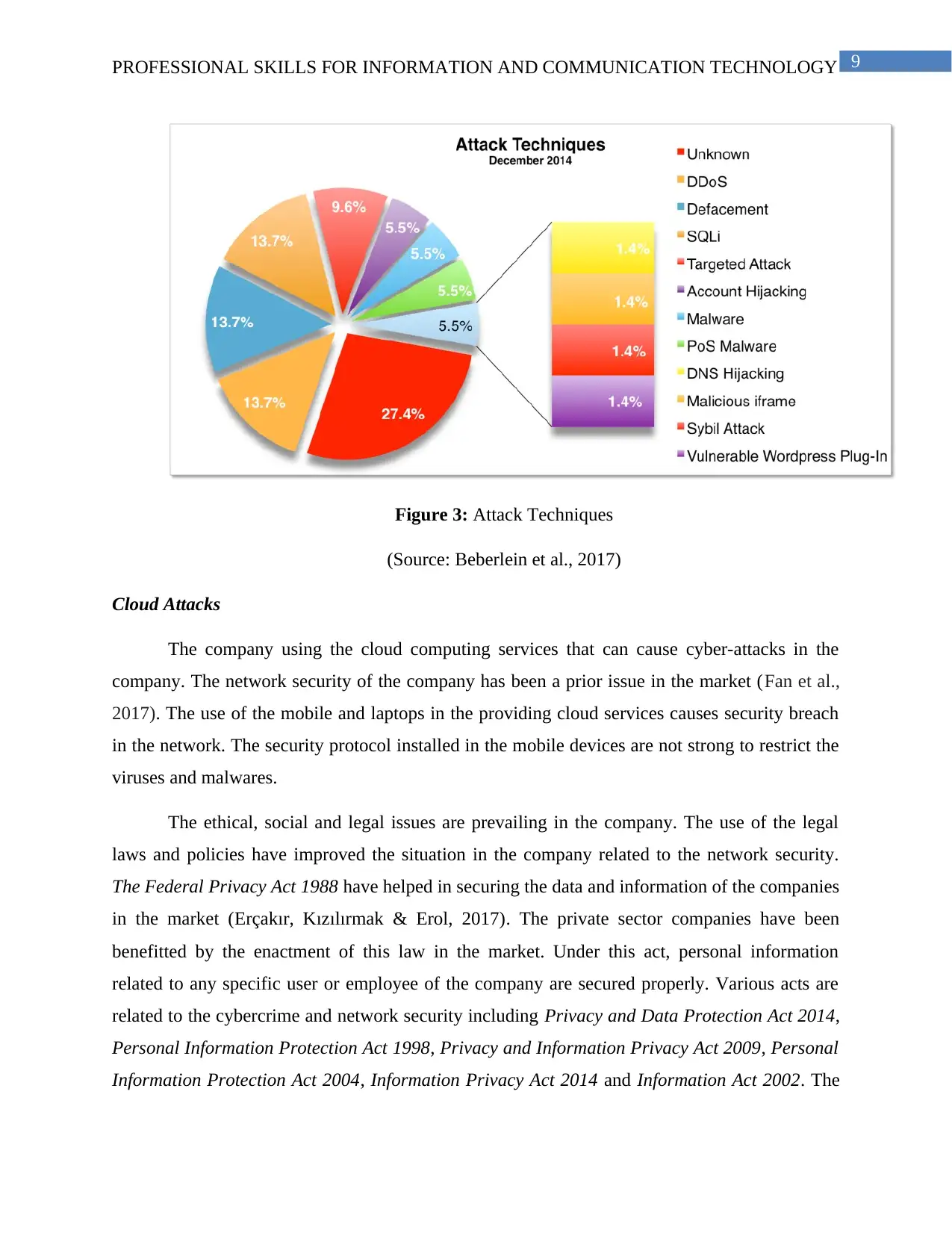
9PROFESSIONAL SKILLS FOR INFORMATION AND COMMUNICATION TECHNOLOGY
Figure 3: Attack Techniques
(Source: Beberlein et al., 2017)
Cloud Attacks
The company using the cloud computing services that can cause cyber-attacks in the
company. The network security of the company has been a prior issue in the market (Fan et al.,
2017). The use of the mobile and laptops in the providing cloud services causes security breach
in the network. The security protocol installed in the mobile devices are not strong to restrict the
viruses and malwares.
The ethical, social and legal issues are prevailing in the company. The use of the legal
laws and policies have improved the situation in the company related to the network security.
The Federal Privacy Act 1988 have helped in securing the data and information of the companies
in the market (Erçakır, Kızılırmak & Erol, 2017). The private sector companies have been
benefitted by the enactment of this law in the market. Under this act, personal information
related to any specific user or employee of the company are secured properly. Various acts are
related to the cybercrime and network security including Privacy and Data Protection Act 2014,
Personal Information Protection Act 1998, Privacy and Information Privacy Act 2009, Personal
Information Protection Act 2004, Information Privacy Act 2014 and Information Act 2002. The
Figure 3: Attack Techniques
(Source: Beberlein et al., 2017)
Cloud Attacks
The company using the cloud computing services that can cause cyber-attacks in the
company. The network security of the company has been a prior issue in the market (Fan et al.,
2017). The use of the mobile and laptops in the providing cloud services causes security breach
in the network. The security protocol installed in the mobile devices are not strong to restrict the
viruses and malwares.
The ethical, social and legal issues are prevailing in the company. The use of the legal
laws and policies have improved the situation in the company related to the network security.
The Federal Privacy Act 1988 have helped in securing the data and information of the companies
in the market (Erçakır, Kızılırmak & Erol, 2017). The private sector companies have been
benefitted by the enactment of this law in the market. Under this act, personal information
related to any specific user or employee of the company are secured properly. Various acts are
related to the cybercrime and network security including Privacy and Data Protection Act 2014,
Personal Information Protection Act 1998, Privacy and Information Privacy Act 2009, Personal
Information Protection Act 2004, Information Privacy Act 2014 and Information Act 2002. The
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10PROFESSIONAL SKILLS FOR INFORMATION AND COMMUNICATION TECHNOLOGY
proper implementation of these acts and policies helps in strengthening the security protocols of
the company (Kaur & Singh, 2017).
Conclusion
It can be concluded that the security of the data and information in the organization is an
integral part of their operational management system. The data and information of the company
is stored and transferred online. Therefore, there is a huge risk of data breach during transferring
data. This IT Company is looking for expansion in the market. There are various solutions
provided in the report that helps in maintaining risks and issues in the company. There are
various risks discussed in the report related to the network security in the company. These risks
and issues in the security of the data and information has been mentioned in the report. The
various laws and acts have helped in maintaining the malicious activities over the internet. There
are proper recommendations provided in the end of the report to analyses the solution for
network security issues.
Recommendations
There are different risks and issues are discussed in the report that are prevailing related
to the network security in the company. There are some recommendation provides that might
help in minimizing the cyber-attacks on the network security.
Encryption
The company needs to use the encryption technique that helps in encrypting the packets
of data transferred. The encryption technique can be used that acquires a locking system with a
key. The key or password is known to only transmitter and receiver. This helps in sage transfer
of data and information between customer and company.
Layered Security architecture
The company have to install a layered architecture that helps in providing security to the
inner architecture where data and information is stored. The layered architecture helps in
maintaining the security protocol of the company in the market. It becomes difficult for the
hackers to enter into the inner layer of the architecture.
proper implementation of these acts and policies helps in strengthening the security protocols of
the company (Kaur & Singh, 2017).
Conclusion
It can be concluded that the security of the data and information in the organization is an
integral part of their operational management system. The data and information of the company
is stored and transferred online. Therefore, there is a huge risk of data breach during transferring
data. This IT Company is looking for expansion in the market. There are various solutions
provided in the report that helps in maintaining risks and issues in the company. There are
various risks discussed in the report related to the network security in the company. These risks
and issues in the security of the data and information has been mentioned in the report. The
various laws and acts have helped in maintaining the malicious activities over the internet. There
are proper recommendations provided in the end of the report to analyses the solution for
network security issues.
Recommendations
There are different risks and issues are discussed in the report that are prevailing related
to the network security in the company. There are some recommendation provides that might
help in minimizing the cyber-attacks on the network security.
Encryption
The company needs to use the encryption technique that helps in encrypting the packets
of data transferred. The encryption technique can be used that acquires a locking system with a
key. The key or password is known to only transmitter and receiver. This helps in sage transfer
of data and information between customer and company.
Layered Security architecture
The company have to install a layered architecture that helps in providing security to the
inner architecture where data and information is stored. The layered architecture helps in
maintaining the security protocol of the company in the market. It becomes difficult for the
hackers to enter into the inner layer of the architecture.

11PROFESSIONAL SKILLS FOR INFORMATION AND COMMUNICATION TECHNOLOGY
Use of strong password
The running applications of the company have to use a strong password that helps in
minimizing the chances of the hacking of the network. The server of the company have to use
strong password that disables the entry of the malicious users in the network. The password must
be at least eight characters long. The combination of capital and small letters, numbers and
special characters are helpful in creating strong passwords for the network servers. The company
needs to update the passwords regularly. This decreases the chances of matching the passwords
by the hackers.
Using a secured back up plan
The backup plan is a secured strategy for any IT infrastructure. There can be any kind of
data and information loss in the company that can cause huge loss to the company in the market
therefore, the use of the backup helps in recovering the lost data. The backup data and
information is stored in a secured and remote place away from the regular place of business. This
helps in protecting data from both physical and cyber-attacks.
The company might look for the use of the robotics science in the organization. The use
of the robotics helps in minimizing the workload on the employees of the company. The
advancement in the technological aspect of the company might drove the company towards the
success in the market.
Use of strong password
The running applications of the company have to use a strong password that helps in
minimizing the chances of the hacking of the network. The server of the company have to use
strong password that disables the entry of the malicious users in the network. The password must
be at least eight characters long. The combination of capital and small letters, numbers and
special characters are helpful in creating strong passwords for the network servers. The company
needs to update the passwords regularly. This decreases the chances of matching the passwords
by the hackers.
Using a secured back up plan
The backup plan is a secured strategy for any IT infrastructure. There can be any kind of
data and information loss in the company that can cause huge loss to the company in the market
therefore, the use of the backup helps in recovering the lost data. The backup data and
information is stored in a secured and remote place away from the regular place of business. This
helps in protecting data from both physical and cyber-attacks.
The company might look for the use of the robotics science in the organization. The use
of the robotics helps in minimizing the workload on the employees of the company. The
advancement in the technological aspect of the company might drove the company towards the
success in the market.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




