Project on Cybersecurity Laws: The Impact of EU and UK Regulations
VerifiedAdded on 2023/06/11
|9
|1398
|350
Project
AI Summary
This project examines the significance of cybersecurity laws, focusing on the roles of the European Union and the United Kingdom in shaping these regulations. It identifies the research objectives, questions, and problems related to cybersecurity, emphasizing the importance of EU and UK involvement. The methodology employs quantitative analysis, gathering data from primary and secondary sources, and uses project management tools like Gantt charts and budget planning to address potential risks. The study reviews existing literature to understand the legal landscape of cybersecurity, the challenges faced in formulating effective laws, and the importance of protecting data and information in the digital age. The project concludes by highlighting the crucial role of cybersecurity laws in ensuring data protection and security.

Proposal
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction.................................................................................................................................................3
Research Objectives:...............................................................................................................................3
Research Questions.................................................................................................................................3
Research problem....................................................................................................................................3
Rational for the research..........................................................................................................................3
Literature Review........................................................................................................................................4
Methodology...............................................................................................................................................4
Project management................................................................................................................................5
Conclusion...................................................................................................................................................8
References...................................................................................................................................................9
Introduction.................................................................................................................................................3
Research Objectives:...............................................................................................................................3
Research Questions.................................................................................................................................3
Research problem....................................................................................................................................3
Rational for the research..........................................................................................................................3
Literature Review........................................................................................................................................4
Methodology...............................................................................................................................................4
Project management................................................................................................................................5
Conclusion...................................................................................................................................................8
References...................................................................................................................................................9

Topic: The importance of the European Union and United Kingdom on cybersecurity laws”
Introduction
Cyber security is highly important to protect the data and information. For this purpose,
various cyber security acts have been formulated by the European countries and the UK. These
acts are helpful in protecting the confidential information in an appropriate way(Syafrizal,
Selamat and Zakaria, 2020). The present research work will be conducted on the significance of
European union and united kingdom on cybersecurity laws.
Research Objectives:
To develop knowledge regarding cybersecurity laws.
To understand the importance of European Union and United kingdom on cybersecurity
laws.
To identify the challenges faced by European Union and United Kingdom while
preparing laws related to cybersecurity.
Research Questions
Discuss knowledge regarding cybersecurity laws?
What is the importance of European Union and United kingdom on cybersecurity laws?
What are the challenges faced by European Union and United Kingdom while preparing
laws related to cybersecurity?
Research problem
In the present research, the main focus is on resolving the issues related to cyber security
that is being faced by the UK and European countries.
Rational for the research
The main aim of conducting the research on the given topic is to develop the knowledge
base regarding cybersecurity laws. It will help the researcher in terms of developing significant
knowledge laws of cybersecurity. Apart from this, it is also helpful in enhancement of various
skills such as communication, presentation and more.
Introduction
Cyber security is highly important to protect the data and information. For this purpose,
various cyber security acts have been formulated by the European countries and the UK. These
acts are helpful in protecting the confidential information in an appropriate way(Syafrizal,
Selamat and Zakaria, 2020). The present research work will be conducted on the significance of
European union and united kingdom on cybersecurity laws.
Research Objectives:
To develop knowledge regarding cybersecurity laws.
To understand the importance of European Union and United kingdom on cybersecurity
laws.
To identify the challenges faced by European Union and United Kingdom while
preparing laws related to cybersecurity.
Research Questions
Discuss knowledge regarding cybersecurity laws?
What is the importance of European Union and United kingdom on cybersecurity laws?
What are the challenges faced by European Union and United Kingdom while preparing
laws related to cybersecurity?
Research problem
In the present research, the main focus is on resolving the issues related to cyber security
that is being faced by the UK and European countries.
Rational for the research
The main aim of conducting the research on the given topic is to develop the knowledge
base regarding cybersecurity laws. It will help the researcher in terms of developing significant
knowledge laws of cybersecurity. Apart from this, it is also helpful in enhancement of various
skills such as communication, presentation and more.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Literature Review
According to Mylrea, (2017), cyber security refers to the area of laws that deals with the
internet’s relationship with different components such as technological elements, computer,
hardware, software and more. Cyber law also refers as the internet law. Additionally, cyberlaw
reduces damage related to cyber criminal activities by protecting the information from
unnecessary access, communications, IP and more. In the present time, the increasing use of
internet is enhancing of legal issues such across the world.
According to Schünemann and Baumann, (2017), it is analyzed that cybersecurity laws
play an important role in protecting the information appropriately. For this purpose, the
European countries have been formulated several laws that are important in order to manage the
data & information significantly. It is monitored that cyber security is helpful in order to
strengthen the EU agency for cybersecurity. Also, it establishes a proper cybersecurity
certification framework for several products & services.
According Didenko, (2020), there are ample of challenges faced by the European
countries and UK while structuring the laws related to cybersecurity. In this regard, the
authorities need to analyze various components like security and more. In addition to this, they
also face significant issues in terms of data breaches and cloud threats. It is analyzed that the
authorities are required to take several significant steps before formulating the cybersecurity laws
significantly.
Methodology
Research methodology refers to collect, analyze as well as interpret the information
significantly. It included various significant steps to reach at meaningful decisions in significant
manner. In this context, research methodology is mentioned below:
Quantitative analysis: This method is associated with collection of numerical
information. Here statistical and mathematical tools are used to gather as well as analyze the
According to Mylrea, (2017), cyber security refers to the area of laws that deals with the
internet’s relationship with different components such as technological elements, computer,
hardware, software and more. Cyber law also refers as the internet law. Additionally, cyberlaw
reduces damage related to cyber criminal activities by protecting the information from
unnecessary access, communications, IP and more. In the present time, the increasing use of
internet is enhancing of legal issues such across the world.
According to Schünemann and Baumann, (2017), it is analyzed that cybersecurity laws
play an important role in protecting the information appropriately. For this purpose, the
European countries have been formulated several laws that are important in order to manage the
data & information significantly. It is monitored that cyber security is helpful in order to
strengthen the EU agency for cybersecurity. Also, it establishes a proper cybersecurity
certification framework for several products & services.
According Didenko, (2020), there are ample of challenges faced by the European
countries and UK while structuring the laws related to cybersecurity. In this regard, the
authorities need to analyze various components like security and more. In addition to this, they
also face significant issues in terms of data breaches and cloud threats. It is analyzed that the
authorities are required to take several significant steps before formulating the cybersecurity laws
significantly.
Methodology
Research methodology refers to collect, analyze as well as interpret the information
significantly. It included various significant steps to reach at meaningful decisions in significant
manner. In this context, research methodology is mentioned below:
Quantitative analysis: This method is associated with collection of numerical
information. Here statistical and mathematical tools are used to gather as well as analyze the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

information appropriately. This method is useful in collecting authentic information to get
appropriate results in the future period of time (Mukherjee, 2019).
Qualitative analysis: It is also an imperative method of data analysis. It is related to
collection and analysis of non-numerical information. There are various sources utilized to
collect non-numerical information such as focus group, case study, group discussion and more.
By utilizing such sources, it is possible to collect in-depth & detailed information in an efficient
manner.
In context of the present research work, quantitative analysis is taken into consideration
as it will help in collecting numerical data & information for future success of the research
work.
Data collection: Data collection is an important part of the research study. To complete a
research successfully, the data is collected from several sources like primary, secondary and
more. In primary, the information is taken out from raw sources. On other side, the secondary
information is gathered from different sources like websites, articles, journals and more (Säfsten
and Gustavsson, 2020).
Data analysis: While carrying out the research on a particular topic, it is important to
analyze the data significantly. In current context, the information has been analyzed using
various tools & techniques. For this purpose, the researcher has been used various graphs, tables
to make appropriate interpretation of the data.
Project management
Risks: In context of the given study, there are several risks in terms of lack of funds,
resources and other equipments (Bigorra Puente, 2017). These risks could be addressed by taking
suitable steps in an efficient manner.
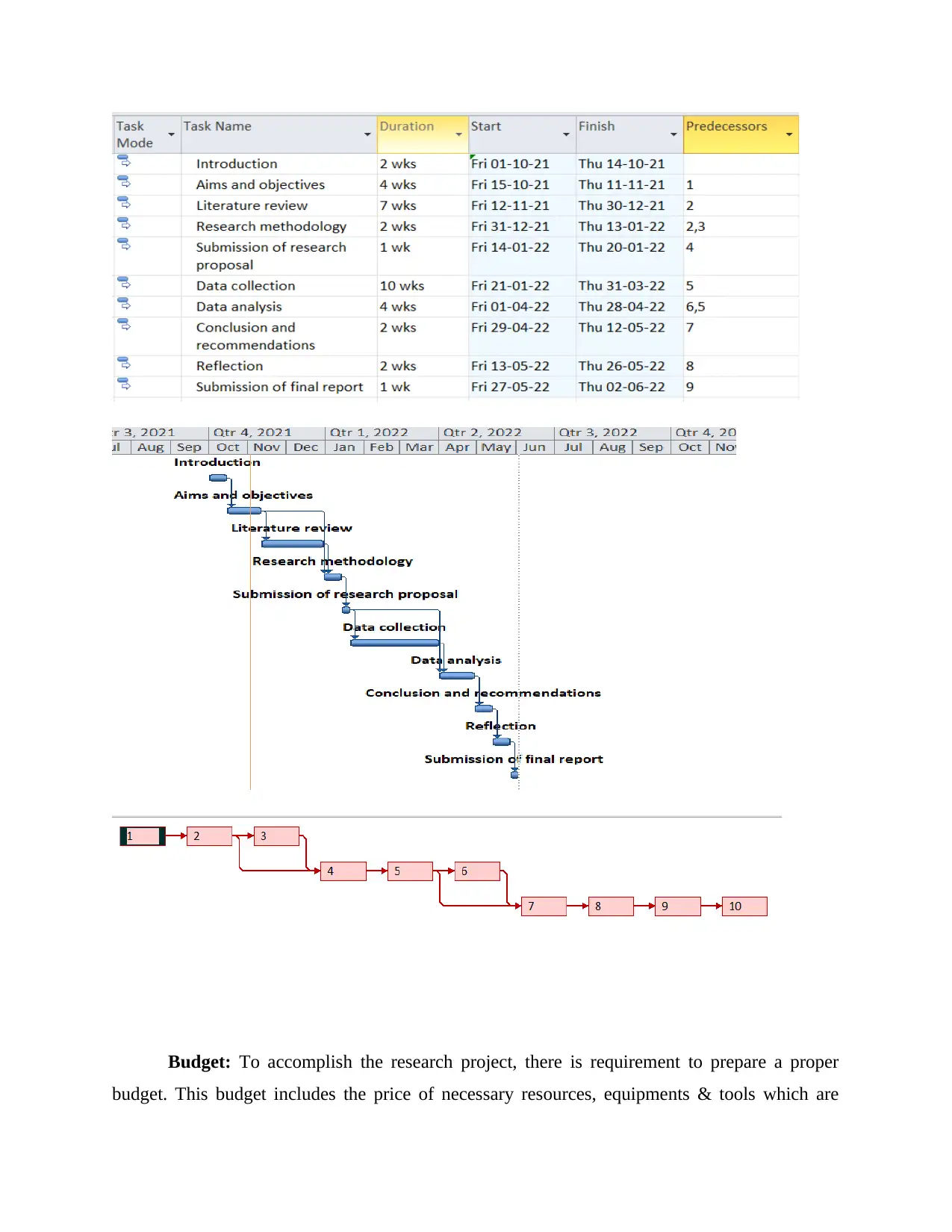
Gantt chart: For the purpose of current study, gantt chart is given below:
appropriate results in the future period of time (Mukherjee, 2019).
Qualitative analysis: It is also an imperative method of data analysis. It is related to
collection and analysis of non-numerical information. There are various sources utilized to
collect non-numerical information such as focus group, case study, group discussion and more.
By utilizing such sources, it is possible to collect in-depth & detailed information in an efficient
manner.
In context of the present research work, quantitative analysis is taken into consideration
as it will help in collecting numerical data & information for future success of the research
work.
Data collection: Data collection is an important part of the research study. To complete a
research successfully, the data is collected from several sources like primary, secondary and
more. In primary, the information is taken out from raw sources. On other side, the secondary
information is gathered from different sources like websites, articles, journals and more (Säfsten
and Gustavsson, 2020).
Data analysis: While carrying out the research on a particular topic, it is important to
analyze the data significantly. In current context, the information has been analyzed using
various tools & techniques. For this purpose, the researcher has been used various graphs, tables
to make appropriate interpretation of the data.
Project management
Risks: In context of the given study, there are several risks in terms of lack of funds,
resources and other equipments (Bigorra Puente, 2017). These risks could be addressed by taking
suitable steps in an efficient manner.
Gantt chart: For the purpose of current study, gantt chart is given below:
Budget: To accomplish the research project, there is requirement to prepare a proper
budget. This budget includes the price of necessary resources, equipments & tools which are
budget. This budget includes the price of necessary resources, equipments & tools which are
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

used for the completion of research work (Cicmil and et. al., 2017). In case of current research
the overall budet is 90 Euros.
Resources: For the accomplishment of research study, there is requirement of ample of
resources. These resources are funds, staff, equipments and more.
Skills: Research is carried out by ample of people. For successful completion of project
work, there is requirement to have necessary skills in terms of communication, presentation, time
management, decision-making and so on.
Health & safety: During the research study, there is requirement to take care of health & safety
requirements to get meaningful results in an efficient manner.
the overall budet is 90 Euros.
Resources: For the accomplishment of research study, there is requirement of ample of
resources. These resources are funds, staff, equipments and more.
Skills: Research is carried out by ample of people. For successful completion of project
work, there is requirement to have necessary skills in terms of communication, presentation, time
management, decision-making and so on.
Health & safety: During the research study, there is requirement to take care of health & safety
requirements to get meaningful results in an efficient manner.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Conclusion
From the above-mentioned study, it is analyzed that cybersecurity laws are crucial for
the purpose of protection & security of data. The above-study is based on the significance of
European countries and UK on cybersecurity laws.
From the above-mentioned study, it is analyzed that cybersecurity laws are crucial for
the purpose of protection & security of data. The above-study is based on the significance of
European countries and UK on cybersecurity laws.

References
Books and journals
Bigorra Puente, D., 2017. Project management plan of the creation of a travellers-oriented
mobile application (Master's thesis, Universitat Politècnica de Catalunya).
Cicmil and et. al., 2017, April. Exploring the complexity of projects: Implications of complexity
theory for project management practice. Project Management Institute.
Didenko, A.N., 2020. Cybersecurity regulation in the financial sector: prospects of legal
harmonization in the European Union and beyond. Uniform Law Review, 25(1), pp.125-
167.
Mukherjee, S.P., 2019. A guide to research methodology: An overview of research problems,
tasks and methods. CRC Press.
Mylrea, M., 2017. Smart energy-internet-of-things opportunities require smart treatment of legal,
privacy and cybersecurity challenges. The Journal of World Energy Law &
Business, 10(2), pp.147-158.
Säfsten, K. and Gustavsson, M., 2020. Research methodology: for engineers and other problem-
solvers.
Schünemann, W.J. and Baumann, M.O. eds., 2017. Privacy, data protection and cybersecurity in
Europe. Springer International Publishing.
Syafrizal, M., Selamat, S.R. and Zakaria, N.A., 2020. Analysis of cybersecurity standard and
framework components. International Journal of Communication Networks and
Information Security, 12(3), pp.417-432.
Books and journals
Bigorra Puente, D., 2017. Project management plan of the creation of a travellers-oriented
mobile application (Master's thesis, Universitat Politècnica de Catalunya).
Cicmil and et. al., 2017, April. Exploring the complexity of projects: Implications of complexity
theory for project management practice. Project Management Institute.
Didenko, A.N., 2020. Cybersecurity regulation in the financial sector: prospects of legal
harmonization in the European Union and beyond. Uniform Law Review, 25(1), pp.125-
167.
Mukherjee, S.P., 2019. A guide to research methodology: An overview of research problems,
tasks and methods. CRC Press.
Mylrea, M., 2017. Smart energy-internet-of-things opportunities require smart treatment of legal,
privacy and cybersecurity challenges. The Journal of World Energy Law &
Business, 10(2), pp.147-158.
Säfsten, K. and Gustavsson, M., 2020. Research methodology: for engineers and other problem-
solvers.
Schünemann, W.J. and Baumann, M.O. eds., 2017. Privacy, data protection and cybersecurity in
Europe. Springer International Publishing.
Syafrizal, M., Selamat, S.R. and Zakaria, N.A., 2020. Analysis of cybersecurity standard and
framework components. International Journal of Communication Networks and
Information Security, 12(3), pp.417-432.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




