University Database Application Report: ACCT6001 Project Management
VerifiedAdded on 2020/04/15
|7
|774
|268
Report
AI Summary
This report presents a database application designed for a project management company, addressing the need for efficient data tracking and management. It begins by justifying the use of a database to handle project details, employee assignments, and material information. The core of the report includes an Entity-Relationship (ER) diagram and a relational schema to illustrate the database structure. Furthermore, it outlines necessary IT controls to ensure data security and integrity, covering aspects like access controls and data encryption. The report also discusses critical ethical, privacy, and security issues related to database implementation, such as data breaches and unauthorized access. Finally, it provides a bibliography of relevant sources supporting the analysis and design of the database application, demonstrating the student's understanding of database principles and practical application within a business context.

Running head: DATABASE APPLICATION
ACCT6001 Accounting Information Systems
Student Name:
University Name:
ACCT6001 Accounting Information Systems
Student Name:
University Name:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1DATABASE APPLICATION
Table of Contents
1. Introduction..................................................................................................................................2
2. Justification of the use of database..............................................................................................2
3. Database Design: E-R Diagram...................................................................................................3
3.1 ER Diagram...........................................................................................................................3
3.2 Relational Schema.................................................................................................................4
4. IT controls needed.......................................................................................................................4
5. Ethical, privacy and security issues.............................................................................................5
Bibliography....................................................................................................................................7
Table of Contents
1. Introduction..................................................................................................................................2
2. Justification of the use of database..............................................................................................2
3. Database Design: E-R Diagram...................................................................................................3
3.1 ER Diagram...........................................................................................................................3
3.2 Relational Schema.................................................................................................................4
4. IT controls needed.......................................................................................................................4
5. Ethical, privacy and security issues.............................................................................................5
Bibliography....................................................................................................................................7

2DATABASE APPLICATION
1. Introduction
The aim of this paper is to demonstrate the ability of solving problems related to business
with the help of database design tool and software. This paper also focuses on illustrating the
impacts of using IT (Information Technology) in business and reflecting the key issues. There is
a need of accurate recording, updating and tracking of data by various businesses so that the
employees can access the data with the help of database. Hence, in this paper a database is
designed in context to a project management company for tracking its commercial projects,
employee and the employees’ participation in each project.
2. Justification of the use of database
The project management company handles various ongoing projects at a same time hence
it is essential for project leaders to know the team members who are associated with a particular
project. The database to be will help to keep track of the data on each employee that is associated
with a project or employees that have not been assigned to any project. The database will also
help to record each project being undertaken by the company along with the activities that are
associated with the project. The description of project will comprise of the list of associated
activities and each activity will require some materials so that information will be also stored in
the database. The supplier information of materials will be also recorded in the database to keep
track of which materials are being delivered by which supplier. Hence, there is a need for
database to keep track of every information that is associated with each project.
1. Introduction
The aim of this paper is to demonstrate the ability of solving problems related to business
with the help of database design tool and software. This paper also focuses on illustrating the
impacts of using IT (Information Technology) in business and reflecting the key issues. There is
a need of accurate recording, updating and tracking of data by various businesses so that the
employees can access the data with the help of database. Hence, in this paper a database is
designed in context to a project management company for tracking its commercial projects,
employee and the employees’ participation in each project.
2. Justification of the use of database
The project management company handles various ongoing projects at a same time hence
it is essential for project leaders to know the team members who are associated with a particular
project. The database to be will help to keep track of the data on each employee that is associated
with a project or employees that have not been assigned to any project. The database will also
help to record each project being undertaken by the company along with the activities that are
associated with the project. The description of project will comprise of the list of associated
activities and each activity will require some materials so that information will be also stored in
the database. The supplier information of materials will be also recorded in the database to keep
track of which materials are being delivered by which supplier. Hence, there is a need for
database to keep track of every information that is associated with each project.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3DATABASE APPLICATION
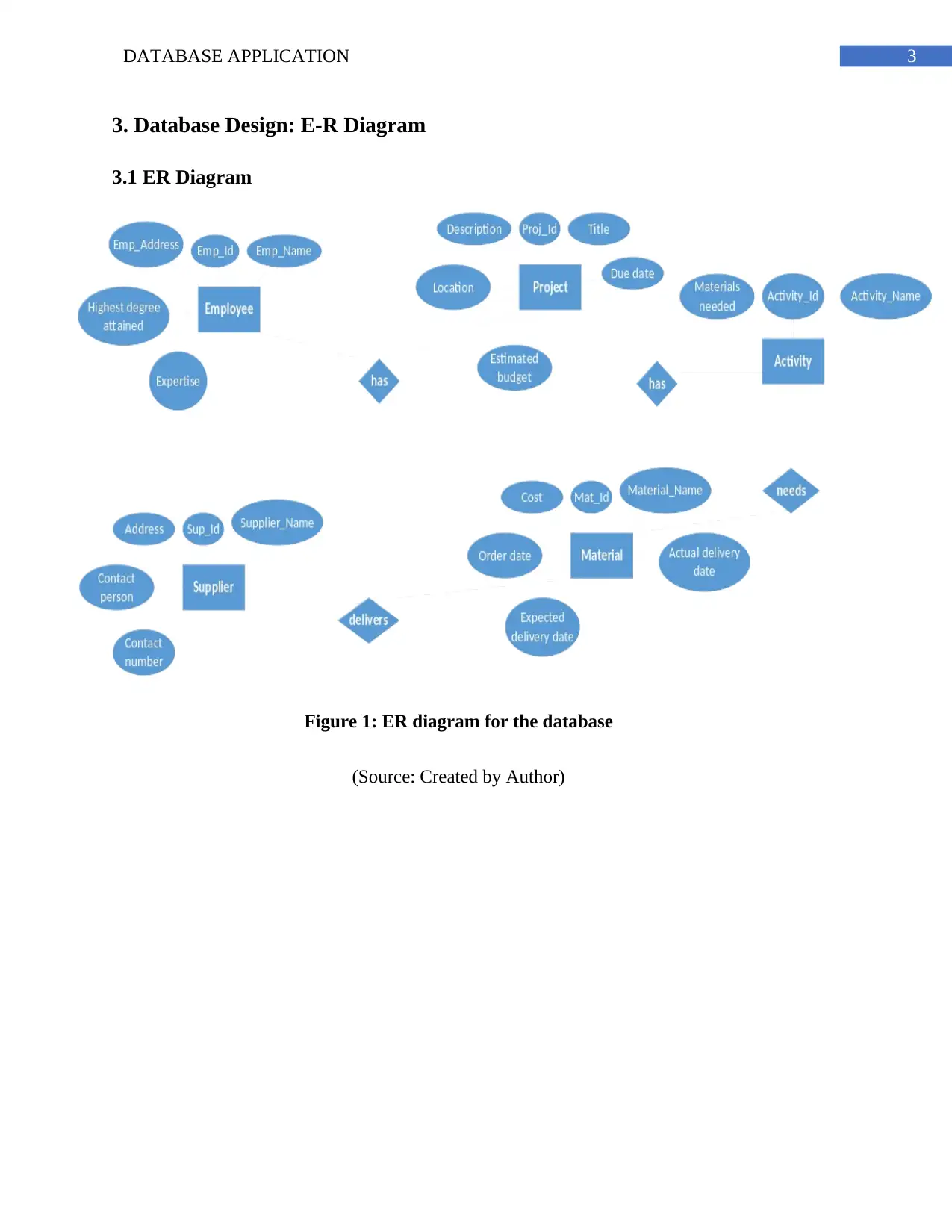
3. Database Design: E-R Diagram
3.1 ER Diagram
Figure 1: ER diagram for the database
(Source: Created by Author)
3. Database Design: E-R Diagram
3.1 ER Diagram
Figure 1: ER diagram for the database
(Source: Created by Author)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4DATABASE APPLICATION
3.2 Relational Schema
Figure 2: Relational schema of the database
(Source: Created by Author)
4. IT controls needed
The IT controls that are needed for implementation of database in the organization are
listed as below:
Foundation: A stable and functioning operating environment have to be maintained for
users as well as application systems so that is available 24 hours for 7 days in a week1. Proper
security measures have to be adopted for protecting information and transactions being carried
out over the internet or any insecure environment.
1 Erez Shmueli and others, 'Implementing A Database Encryption Solution, Design And Implementation
Issues' (2014) 44 Computers & Security.
3.2 Relational Schema
Figure 2: Relational schema of the database
(Source: Created by Author)
4. IT controls needed
The IT controls that are needed for implementation of database in the organization are
listed as below:
Foundation: A stable and functioning operating environment have to be maintained for
users as well as application systems so that is available 24 hours for 7 days in a week1. Proper
security measures have to be adopted for protecting information and transactions being carried
out over the internet or any insecure environment.
1 Erez Shmueli and others, 'Implementing A Database Encryption Solution, Design And Implementation
Issues' (2014) 44 Computers & Security.

5DATABASE APPLICATION
Access controls: Specific users should be provided with separate access to data
individually as per requirement or role of user. Proper authentication measures have to be
implemented within the organization so that unauthorized access to sensitive data or information
is prevented.
Data Encryption: An additional security measure to prevent data breach is to encrypt the
data being stored or during transmission2. Proper encryption and decryption method have to be
followed so that the data is secure from external threat.
5. Ethical, privacy and security issues
Ethical issues: This issue relates to information that must be stored or not in a database3.
Such as some sensitive information that is not required to be stored in the database goes into
wrong hands then it may hamper security of the organization.
Privacy issues: This issue relates to the identity theft such as there may be data leakage
of the employee or supplier information. Further, the project information may be also leaked if
the database is accessed by external threat.
Security issues: The information of customers or clients is a valuable asset for any
organization and if an attacker can get into the database system then the sensitive information
may be leaked4.
2 Elisa Bertino, 'Editorial: Introduction To Data Security And Privacy' (2016) 1 Data Science and
Engineering.
3 S Balamurugan and S Charanyaa, Principles Of Database Security (Scholars' Press 2014).
4 Ben Densham, 'Three Cyber-Security Strategies To Mitigate The Impact Of A Data Breach' (2015) 2015
Network Security.
Access controls: Specific users should be provided with separate access to data
individually as per requirement or role of user. Proper authentication measures have to be
implemented within the organization so that unauthorized access to sensitive data or information
is prevented.
Data Encryption: An additional security measure to prevent data breach is to encrypt the
data being stored or during transmission2. Proper encryption and decryption method have to be
followed so that the data is secure from external threat.
5. Ethical, privacy and security issues
Ethical issues: This issue relates to information that must be stored or not in a database3.
Such as some sensitive information that is not required to be stored in the database goes into
wrong hands then it may hamper security of the organization.
Privacy issues: This issue relates to the identity theft such as there may be data leakage
of the employee or supplier information. Further, the project information may be also leaked if
the database is accessed by external threat.
Security issues: The information of customers or clients is a valuable asset for any
organization and if an attacker can get into the database system then the sensitive information
may be leaked4.
2 Elisa Bertino, 'Editorial: Introduction To Data Security And Privacy' (2016) 1 Data Science and
Engineering.
3 S Balamurugan and S Charanyaa, Principles Of Database Security (Scholars' Press 2014).
4 Ben Densham, 'Three Cyber-Security Strategies To Mitigate The Impact Of A Data Breach' (2015) 2015
Network Security.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6DATABASE APPLICATION
Bibliography
Balamurugan S and Charanyaa S, Principles Of Database Security (Scholars' Press 2014)
Bertino E, 'Editorial: Introduction To Data Security And Privacy' (2016) 1 Data Science and
Engineering
Densham B, 'Three Cyber-Security Strategies To Mitigate The Impact Of A Data Breach' (2015)
2015 Network Security
Shmueli E and others, 'Implementing A Database Encryption Solution, Design And
Implementation Issues' (2014) 44 Computers & Security
Bibliography
Balamurugan S and Charanyaa S, Principles Of Database Security (Scholars' Press 2014)
Bertino E, 'Editorial: Introduction To Data Security And Privacy' (2016) 1 Data Science and
Engineering
Densham B, 'Three Cyber-Security Strategies To Mitigate The Impact Of A Data Breach' (2015)
2015 Network Security
Shmueli E and others, 'Implementing A Database Encryption Solution, Design And
Implementation Issues' (2014) 44 Computers & Security
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





