IT Project Management Report: Authentication, Methodologies, and Scope
VerifiedAdded on 2022/10/04
|7
|1042
|20
Report
AI Summary
This report delves into key aspects of IT project management, beginning with network security and authentication protocols, specifically examining two-way and three-way handshakes. It then explores Rapid Application Development (RAD) and Agile methodologies, comparing their advantages and disadvantages in software development. The report further addresses project scope management, emphasizing the importance of clearly defined scopes to mitigate scope creep. Finally, it touches upon the broader concept of project management, illustrating its application through the example of a Real-Time Glucose Monitoring (RTGM) system and the methods for gathering requirements such as surveys and interviews. The report concludes by highlighting the significance of effective communication and planning in IT projects.
Running Head: IT Project Management 0
IT Project management
Report
Student name
IT Project management
Report
Student name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
IT Project management 1
Q - 1
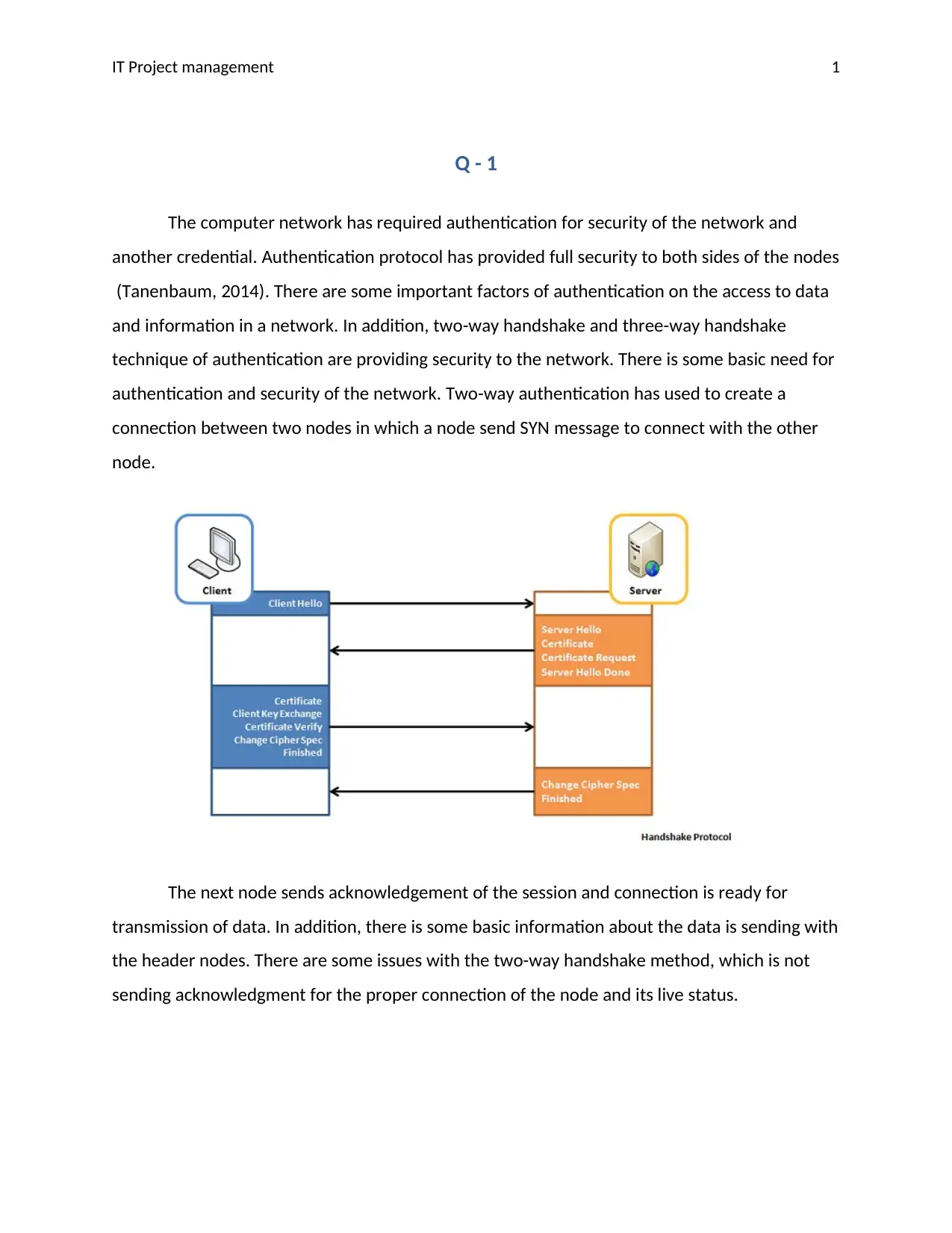
The computer network has required authentication for security of the network and
another credential. Authentication protocol has provided full security to both sides of the nodes
(Tanenbaum, 2014). There are some important factors of authentication on the access to data
and information in a network. In addition, two-way handshake and three-way handshake
technique of authentication are providing security to the network. There is some basic need for
authentication and security of the network. Two-way authentication has used to create a
connection between two nodes in which a node send SYN message to connect with the other
node.
The next node sends acknowledgement of the session and connection is ready for
transmission of data. In addition, there is some basic information about the data is sending with
the header nodes. There are some issues with the two-way handshake method, which is not
sending acknowledgment for the proper connection of the node and its live status.
Q - 1
The computer network has required authentication for security of the network and
another credential. Authentication protocol has provided full security to both sides of the nodes
(Tanenbaum, 2014). There are some important factors of authentication on the access to data
and information in a network. In addition, two-way handshake and three-way handshake
technique of authentication are providing security to the network. There is some basic need for
authentication and security of the network. Two-way authentication has used to create a
connection between two nodes in which a node send SYN message to connect with the other
node.
The next node sends acknowledgement of the session and connection is ready for
transmission of data. In addition, there is some basic information about the data is sending with
the header nodes. There are some issues with the two-way handshake method, which is not
sending acknowledgment for the proper connection of the node and its live status.

IT Project management 2
Moreover, the three-way handshake protocol has provided three segments for creating
a connection between server and client. In addition, there is three-segment, which are SYN,
SYN=ACK, and ACK.
All these segments have used for showing a proper connection and guarantee of that
connection. A client sends a request for the connection from the server using SYN menace. The
server sends an ACK to confirm the connection and server have required the ACK from the
client for confirmation of the client.
There are many benefits of the 3-way handshake protocol in favor of security of the
network. In addition, there are some basic concepts of security, which includes authentication
of the users as well. It is the best way for more security from hackers. However, it has created
high level of traffic in the network form ACK segments, which is not necessary.
Q- 2
Rapid Application Development (RAD) is a new approach to software development in which
development process has stabled from various objectives to complete the project in the given
time (Peltola, Melchels, Grijpma, & Kellomäki, 2008). There is some important factor of the
Moreover, the three-way handshake protocol has provided three segments for creating
a connection between server and client. In addition, there is three-segment, which are SYN,
SYN=ACK, and ACK.
All these segments have used for showing a proper connection and guarantee of that
connection. A client sends a request for the connection from the server using SYN menace. The
server sends an ACK to confirm the connection and server have required the ACK from the
client for confirmation of the client.
There are many benefits of the 3-way handshake protocol in favor of security of the
network. In addition, there are some basic concepts of security, which includes authentication
of the users as well. It is the best way for more security from hackers. However, it has created
high level of traffic in the network form ACK segments, which is not necessary.
Q- 2
Rapid Application Development (RAD) is a new approach to software development in which
development process has stabled from various objectives to complete the project in the given
time (Peltola, Melchels, Grijpma, & Kellomäki, 2008). There is some important factor of the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IT Project management 3
RAD methodology has provided many benefits to the company as well as customers. These are
some benefits of the RAD methodology, which areas,
1. Great designs of the project
2. Rapid prototyping
3. Fast speed of development
4. High-level quality
In addition, RAD methodology has some disadvantages, which makes huge impacts on the
development processes (Meredith, Mantel Jr, & Shafer, 2017). these are some drawback of this
technology, which areas,
1. A short amount of time
2. Reduced scalability
3. Fewer benefits
Answer - 3
Agile is the latest methodology for project management for small scale projects. In
addition, there are some basic advantages of this technology, which makes it different from
other methodologies (Highsmith, 2009). These are some features of agile methodologies, which
areas:
Advantages of agile mythologies:
1. It makes a strong bond between the client and the company, which provides a high level
of customer satisfaction.
2. It provides reports of the development phase to the clients and it implement desired
changes in the project in a given time to improve the performance and reduces time
from the delivery of the project.
RAD methodology has provided many benefits to the company as well as customers. These are
some benefits of the RAD methodology, which areas,
1. Great designs of the project
2. Rapid prototyping
3. Fast speed of development
4. High-level quality
In addition, RAD methodology has some disadvantages, which makes huge impacts on the
development processes (Meredith, Mantel Jr, & Shafer, 2017). these are some drawback of this
technology, which areas,
1. A short amount of time
2. Reduced scalability
3. Fewer benefits
Answer - 3
Agile is the latest methodology for project management for small scale projects. In
addition, there are some basic advantages of this technology, which makes it different from
other methodologies (Highsmith, 2009). These are some features of agile methodologies, which
areas:
Advantages of agile mythologies:
1. It makes a strong bond between the client and the company, which provides a high level
of customer satisfaction.
2. It provides reports of the development phase to the clients and it implement desired
changes in the project in a given time to improve the performance and reduces time
from the delivery of the project.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT Project management 4
There are some disadvantages of the agile methodology, which are not good for the large scale
projects, which areas:
1. Agile methodology has used the large scale of documentation and feedback processes
that takes huge time in large-scale projects.
2. This methodology has included clients in the development and designing processes,
which take huge time and change the project main objectives as well.
Answer - 4
The project should have a proper scope and it should share between all the team
members to avoid any confusing statement (Haworth, 2018). It is necessary to reduce scope
creep for project success. It is beneficial for project management. It is very good feature of
project management. These are some basic needs of a project to reduce the scope creep, which
areas:
1. Scope of the project must know by the whole team
2. No pressure for decision making
3. The budget should be proper
Answer - 5
Project Management is a large process, which was based on various requirements and
decisions (Portny, 2017). The Real-Time Glucose Monitoring (RTGM) system will provide
benefits to the various people using technology and medial sector innovation.
In addition, Bluetooth technology is the best way to improve the efficiency of the
measurement and provide proper information. There are various methods for collecting
information and requirements for the RTGM, which are surveys, feedback, and interview. There
are three basic methods for gathering requirements, which are users, buyers, and suppliers'
feedbacks.
There are some disadvantages of the agile methodology, which are not good for the large scale
projects, which areas:
1. Agile methodology has used the large scale of documentation and feedback processes
that takes huge time in large-scale projects.
2. This methodology has included clients in the development and designing processes,
which take huge time and change the project main objectives as well.
Answer - 4
The project should have a proper scope and it should share between all the team
members to avoid any confusing statement (Haworth, 2018). It is necessary to reduce scope
creep for project success. It is beneficial for project management. It is very good feature of
project management. These are some basic needs of a project to reduce the scope creep, which
areas:
1. Scope of the project must know by the whole team
2. No pressure for decision making
3. The budget should be proper
Answer - 5
Project Management is a large process, which was based on various requirements and
decisions (Portny, 2017). The Real-Time Glucose Monitoring (RTGM) system will provide
benefits to the various people using technology and medial sector innovation.
In addition, Bluetooth technology is the best way to improve the efficiency of the
measurement and provide proper information. There are various methods for collecting
information and requirements for the RTGM, which are surveys, feedback, and interview. There
are three basic methods for gathering requirements, which are users, buyers, and suppliers'
feedbacks.

IT Project management 5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IT Project management 6
References
Haworth, S. (2018, October 1). Identify And Avoid Project Scope Creep. Retrieved from
https://thedigitalprojectmanager.com: https://thedigitalprojectmanager.com/scope-creep/
Highsmith, J. R. (2009). Agile project management: creating innovative products. New York: Pearson
Education.
LaBarre, O. (2019). Project Management. Retrieved June 22, 2019, from
https://www.investopedia.com/terms/p/project-management.asp
Meredith, J., Mantel Jr, S., & Shafer, S. (2017). Project management: a managerial approach. John Wiley
& Sons.
Peltola, S. M., Melchels, F. P., Grijpma, D. W., & Kellomäki, M. (2008). A review of rapid prototyping
techniques for tissue engineering purposes. Annals of medicine 40, 40(4), 268-280.
Portny, S. E. (2017). Project management for dummies (1st ed.). New York: John Wiley & Sons.
References
Haworth, S. (2018, October 1). Identify And Avoid Project Scope Creep. Retrieved from
https://thedigitalprojectmanager.com: https://thedigitalprojectmanager.com/scope-creep/
Highsmith, J. R. (2009). Agile project management: creating innovative products. New York: Pearson
Education.
LaBarre, O. (2019). Project Management. Retrieved June 22, 2019, from
https://www.investopedia.com/terms/p/project-management.asp
Meredith, J., Mantel Jr, S., & Shafer, S. (2017). Project management: a managerial approach. John Wiley
& Sons.
Peltola, S. M., Melchels, F. P., Grijpma, D. W., & Kellomäki, M. (2008). A review of rapid prototyping
techniques for tissue engineering purposes. Annals of medicine 40, 40(4), 268-280.
Portny, S. E. (2017). Project management for dummies (1st ed.). New York: John Wiley & Sons.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



