Project Management: Network Security for E-Commerce Business
VerifiedAdded on 2020/04/01
|15
|2758
|34
Project
AI Summary
This project management assignment addresses the development of a secure network for an e-commerce business. The assignment begins with an executive summary and table of contents, followed by an introduction that highlights the growing importance of network security in the e-commerce sector. The core of the assignment is the project planning document, which outlines project goals, objectives, requirements (functional and non-functional), and team roles. It includes a detailed work breakdown structure (WBS), project duration, and a comprehensive resource allocation plan. The assignment uses MS Project to create a Gantt chart and network diagram, along with a cost estimate based on a bottom-up estimation method, including a 10% management reserve. A quality plan, stakeholder analysis, communications plan, risk management plan, and deployment plan are also included. The assignment concludes with a project handover section, post-project review, and recommendations for future maintenance and training.

BN205
Trimester 2, 2017 - Project Management
Assignment 2
Name of University
Name of Professor:
Student’s Name
Dated:
Trimester 2, 2017 - Project Management
Assignment 2
Name of University
Name of Professor:
Student’s Name
Dated:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Trimester 2, 2017 - Project Management
Executive Summary
The planning document is the necessity of all the kind of projects. Moreover the security is also become
must require features of any e-commerce business. In current report these two items shall be merged
together to develop the report.
This report deals with the requirement of a project, which should be documented first in the form of this
report below and detailed planning is done using the renowned software the MS Project to analyze
time, cost and resources. Resources considered for the case are manpower and material both are
assigned to all the applicable activities using MS Project software.
Page 2 of 15
Executive Summary
The planning document is the necessity of all the kind of projects. Moreover the security is also become
must require features of any e-commerce business. In current report these two items shall be merged
together to develop the report.
This report deals with the requirement of a project, which should be documented first in the form of this
report below and detailed planning is done using the renowned software the MS Project to analyze
time, cost and resources. Resources considered for the case are manpower and material both are
assigned to all the applicable activities using MS Project software.
Page 2 of 15

Trimester 2, 2017 - Project Management
Table of Contents
Introduction.................................................................................................................................................4
Project Planning Document.........................................................................................................................4
Conclusion.................................................................................................................................................12
References.................................................................................................................................................12
Appendices................................................................................................................................................12
Page 3 of 15
Table of Contents
Introduction.................................................................................................................................................4
Project Planning Document.........................................................................................................................4
Conclusion.................................................................................................................................................12
References.................................................................................................................................................12
Appendices................................................................................................................................................12
Page 3 of 15
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Trimester 2, 2017 - Project Management
Introduction
Business world has become very competitive now a days, every business requires smart work and strong
network system. To develop the customer network and maintain the relationship the e-commerce
business concept has grown like anything. As more and more businesses are conducting through e-
commerce platform, the concern regarding maintain the network security has also increased. The more
sophisticated IT Networks are being developed for the business, parallel to it the more complex security
threats are also growing. So developing the exact Network Security for any business has become the
necessity for the organization. The current project is to develop a strong network security system for a
new e-commerce business organization.
This report shall discuss regarding the project planning document being developed for the above
conceptualized project and shall cover the entire aspects of the project by using the renowned planning
software like MS Project.
Project Planning Document
Project Title: Network Security for E-Commerce Business
Start Date: 18th September 2017 Finish Date: 28th March 2018
Goals of the Project: the main goal of the project is to develop a strong and secured network for
conducting safe e-commerce business transactions and maintaining database without fear of getting
cyber attacked
Objectives of the Project: the objective is to design and implement the secured network for e-
commerce business by first of all gathering the requirements by conducting SWOT analysis and then
accordingly design, procure and implement the system for fearless transactions.
Project requirements:
Functional:
The user of the system should always be asked for the first time registration on portal
The network needs to be secured enough by asking for passwords for accessing every
time
Page 4 of 15
Introduction
Business world has become very competitive now a days, every business requires smart work and strong
network system. To develop the customer network and maintain the relationship the e-commerce
business concept has grown like anything. As more and more businesses are conducting through e-
commerce platform, the concern regarding maintain the network security has also increased. The more
sophisticated IT Networks are being developed for the business, parallel to it the more complex security
threats are also growing. So developing the exact Network Security for any business has become the
necessity for the organization. The current project is to develop a strong network security system for a
new e-commerce business organization.
This report shall discuss regarding the project planning document being developed for the above
conceptualized project and shall cover the entire aspects of the project by using the renowned planning
software like MS Project.
Project Planning Document
Project Title: Network Security for E-Commerce Business
Start Date: 18th September 2017 Finish Date: 28th March 2018
Goals of the Project: the main goal of the project is to develop a strong and secured network for
conducting safe e-commerce business transactions and maintaining database without fear of getting
cyber attacked
Objectives of the Project: the objective is to design and implement the secured network for e-
commerce business by first of all gathering the requirements by conducting SWOT analysis and then
accordingly design, procure and implement the system for fearless transactions.
Project requirements:
Functional:
The user of the system should always be asked for the first time registration on portal
The network needs to be secured enough by asking for passwords for accessing every
time
Page 4 of 15
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Trimester 2, 2017 - Project Management
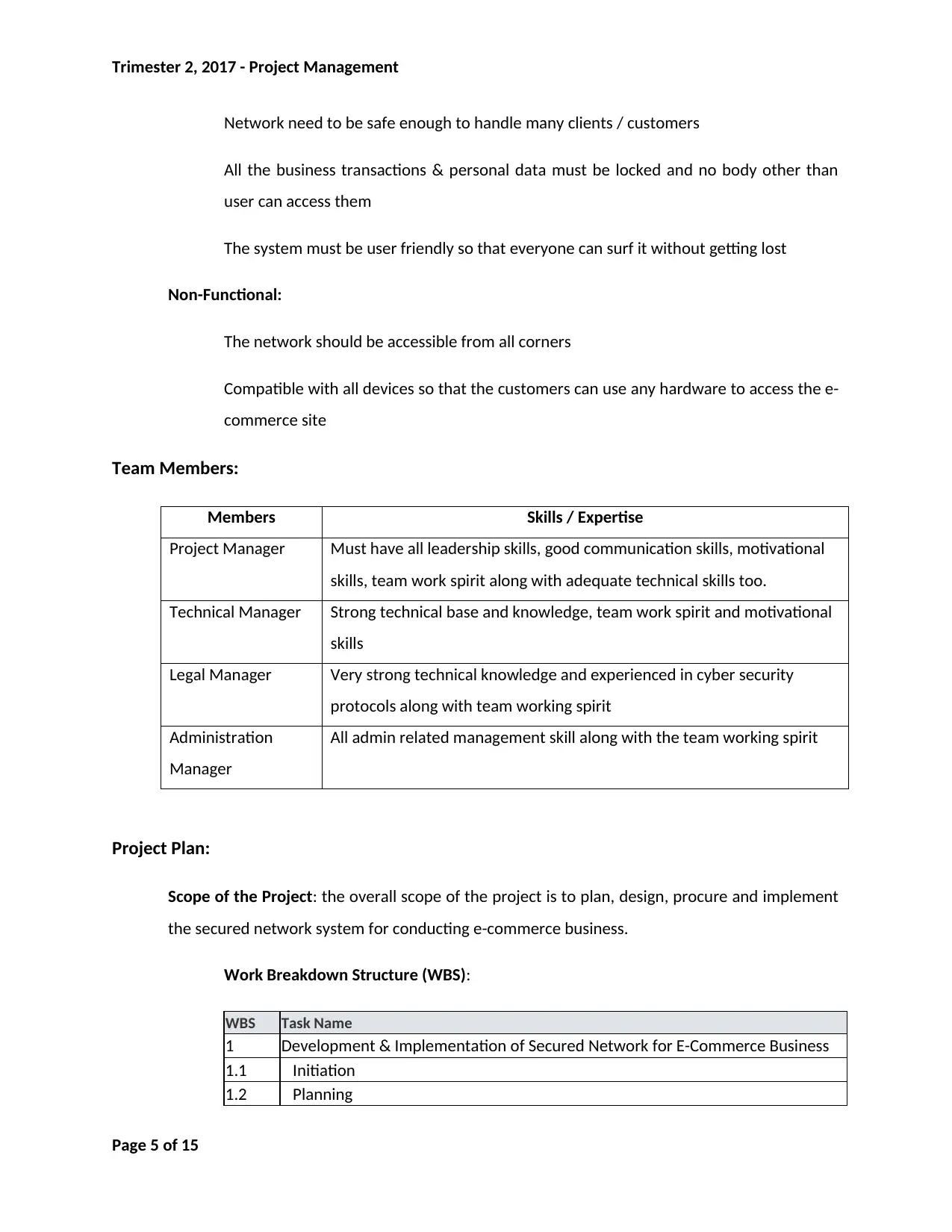
Network need to be safe enough to handle many clients / customers
All the business transactions & personal data must be locked and no body other than
user can access them
The system must be user friendly so that everyone can surf it without getting lost
Non-Functional:
The network should be accessible from all corners
Compatible with all devices so that the customers can use any hardware to access the e-
commerce site
Team Members:
Members Skills / Expertise
Project Manager Must have all leadership skills, good communication skills, motivational
skills, team work spirit along with adequate technical skills too.
Technical Manager Strong technical base and knowledge, team work spirit and motivational
skills
Legal Manager Very strong technical knowledge and experienced in cyber security
protocols along with team working spirit
Administration
Manager
All admin related management skill along with the team working spirit
Project Plan:
Scope of the Project: the overall scope of the project is to plan, design, procure and implement
the secured network system for conducting e-commerce business.
Work Breakdown Structure (WBS):
WBS Task Name
1 Development & Implementation of Secured Network for E-Commerce Business
1.1 Initiation
1.2 Planning
Page 5 of 15
Network need to be safe enough to handle many clients / customers
All the business transactions & personal data must be locked and no body other than
user can access them
The system must be user friendly so that everyone can surf it without getting lost
Non-Functional:
The network should be accessible from all corners
Compatible with all devices so that the customers can use any hardware to access the e-
commerce site
Team Members:
Members Skills / Expertise
Project Manager Must have all leadership skills, good communication skills, motivational
skills, team work spirit along with adequate technical skills too.
Technical Manager Strong technical base and knowledge, team work spirit and motivational
skills
Legal Manager Very strong technical knowledge and experienced in cyber security
protocols along with team working spirit
Administration
Manager
All admin related management skill along with the team working spirit
Project Plan:
Scope of the Project: the overall scope of the project is to plan, design, procure and implement
the secured network system for conducting e-commerce business.
Work Breakdown Structure (WBS):
WBS Task Name
1 Development & Implementation of Secured Network for E-Commerce Business
1.1 Initiation
1.2 Planning
Page 5 of 15
Trimester 2, 2017 - Project Management
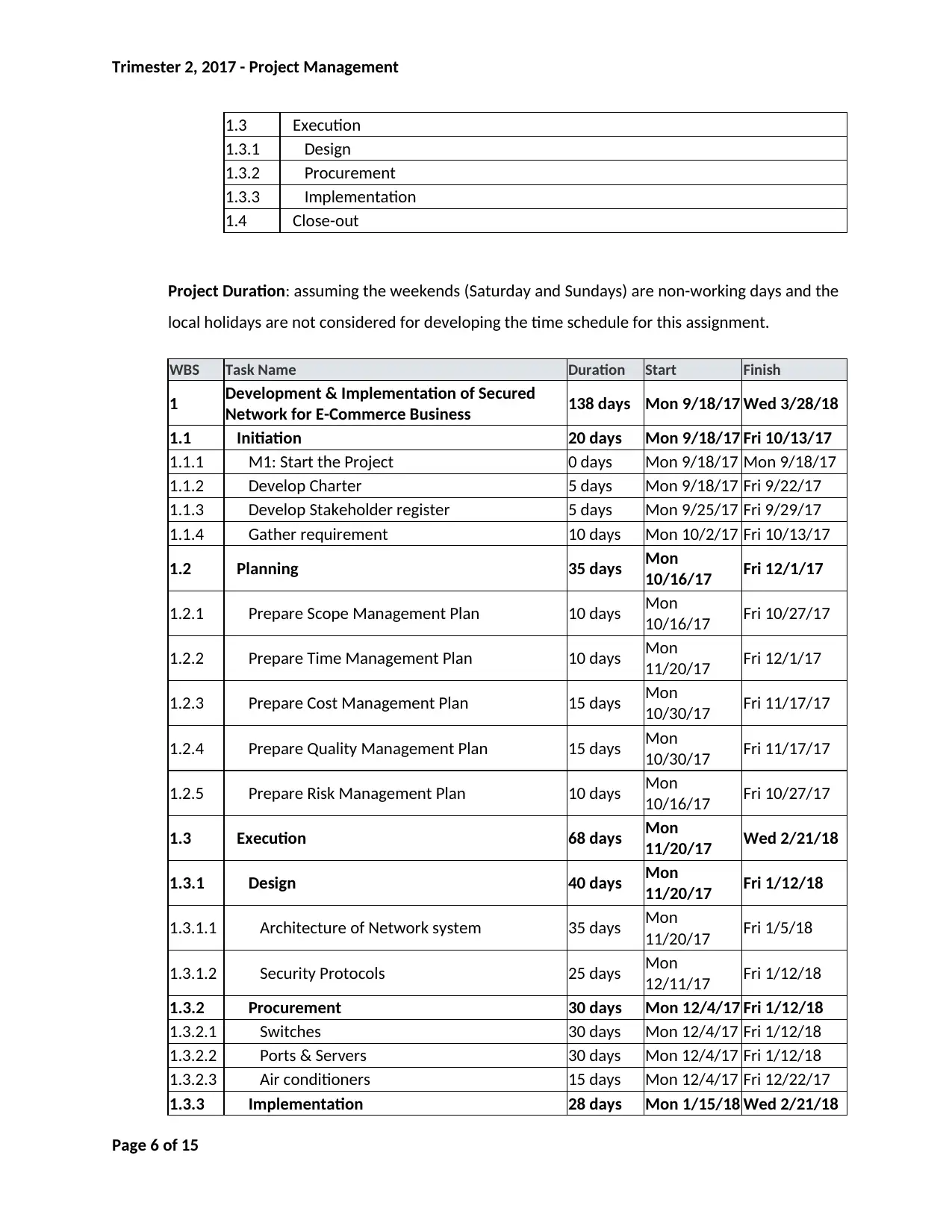
1.3 Execution
1.3.1 Design
1.3.2 Procurement
1.3.3 Implementation
1.4 Close-out
Project Duration: assuming the weekends (Saturday and Sundays) are non-working days and the
local holidays are not considered for developing the time schedule for this assignment.
WBS Task Name Duration Start Finish
1 Development & Implementation of Secured
Network for E-Commerce Business 138 days Mon 9/18/17 Wed 3/28/18
1.1 Initiation 20 days Mon 9/18/17 Fri 10/13/17
1.1.1 M1: Start the Project 0 days Mon 9/18/17 Mon 9/18/17
1.1.2 Develop Charter 5 days Mon 9/18/17 Fri 9/22/17
1.1.3 Develop Stakeholder register 5 days Mon 9/25/17 Fri 9/29/17
1.1.4 Gather requirement 10 days Mon 10/2/17 Fri 10/13/17
1.2 Planning 35 days Mon
10/16/17 Fri 12/1/17
1.2.1 Prepare Scope Management Plan 10 days Mon
10/16/17 Fri 10/27/17
1.2.2 Prepare Time Management Plan 10 days Mon
11/20/17 Fri 12/1/17
1.2.3 Prepare Cost Management Plan 15 days Mon
10/30/17 Fri 11/17/17
1.2.4 Prepare Quality Management Plan 15 days Mon
10/30/17 Fri 11/17/17
1.2.5 Prepare Risk Management Plan 10 days Mon
10/16/17 Fri 10/27/17
1.3 Execution 68 days Mon
11/20/17 Wed 2/21/18
1.3.1 Design 40 days Mon
11/20/17 Fri 1/12/18
1.3.1.1 Architecture of Network system 35 days Mon
11/20/17 Fri 1/5/18
1.3.1.2 Security Protocols 25 days Mon
12/11/17 Fri 1/12/18
1.3.2 Procurement 30 days Mon 12/4/17 Fri 1/12/18
1.3.2.1 Switches 30 days Mon 12/4/17 Fri 1/12/18
1.3.2.2 Ports & Servers 30 days Mon 12/4/17 Fri 1/12/18
1.3.2.3 Air conditioners 15 days Mon 12/4/17 Fri 12/22/17
1.3.3 Implementation 28 days Mon 1/15/18 Wed 2/21/18
Page 6 of 15
1.3 Execution
1.3.1 Design
1.3.2 Procurement
1.3.3 Implementation
1.4 Close-out
Project Duration: assuming the weekends (Saturday and Sundays) are non-working days and the
local holidays are not considered for developing the time schedule for this assignment.
WBS Task Name Duration Start Finish
1 Development & Implementation of Secured
Network for E-Commerce Business 138 days Mon 9/18/17 Wed 3/28/18
1.1 Initiation 20 days Mon 9/18/17 Fri 10/13/17
1.1.1 M1: Start the Project 0 days Mon 9/18/17 Mon 9/18/17
1.1.2 Develop Charter 5 days Mon 9/18/17 Fri 9/22/17
1.1.3 Develop Stakeholder register 5 days Mon 9/25/17 Fri 9/29/17
1.1.4 Gather requirement 10 days Mon 10/2/17 Fri 10/13/17
1.2 Planning 35 days Mon
10/16/17 Fri 12/1/17
1.2.1 Prepare Scope Management Plan 10 days Mon
10/16/17 Fri 10/27/17
1.2.2 Prepare Time Management Plan 10 days Mon
11/20/17 Fri 12/1/17
1.2.3 Prepare Cost Management Plan 15 days Mon
10/30/17 Fri 11/17/17
1.2.4 Prepare Quality Management Plan 15 days Mon
10/30/17 Fri 11/17/17
1.2.5 Prepare Risk Management Plan 10 days Mon
10/16/17 Fri 10/27/17
1.3 Execution 68 days Mon
11/20/17 Wed 2/21/18
1.3.1 Design 40 days Mon
11/20/17 Fri 1/12/18
1.3.1.1 Architecture of Network system 35 days Mon
11/20/17 Fri 1/5/18
1.3.1.2 Security Protocols 25 days Mon
12/11/17 Fri 1/12/18
1.3.2 Procurement 30 days Mon 12/4/17 Fri 1/12/18
1.3.2.1 Switches 30 days Mon 12/4/17 Fri 1/12/18
1.3.2.2 Ports & Servers 30 days Mon 12/4/17 Fri 1/12/18
1.3.2.3 Air conditioners 15 days Mon 12/4/17 Fri 12/22/17
1.3.3 Implementation 28 days Mon 1/15/18 Wed 2/21/18
Page 6 of 15
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Trimester 2, 2017 - Project Management
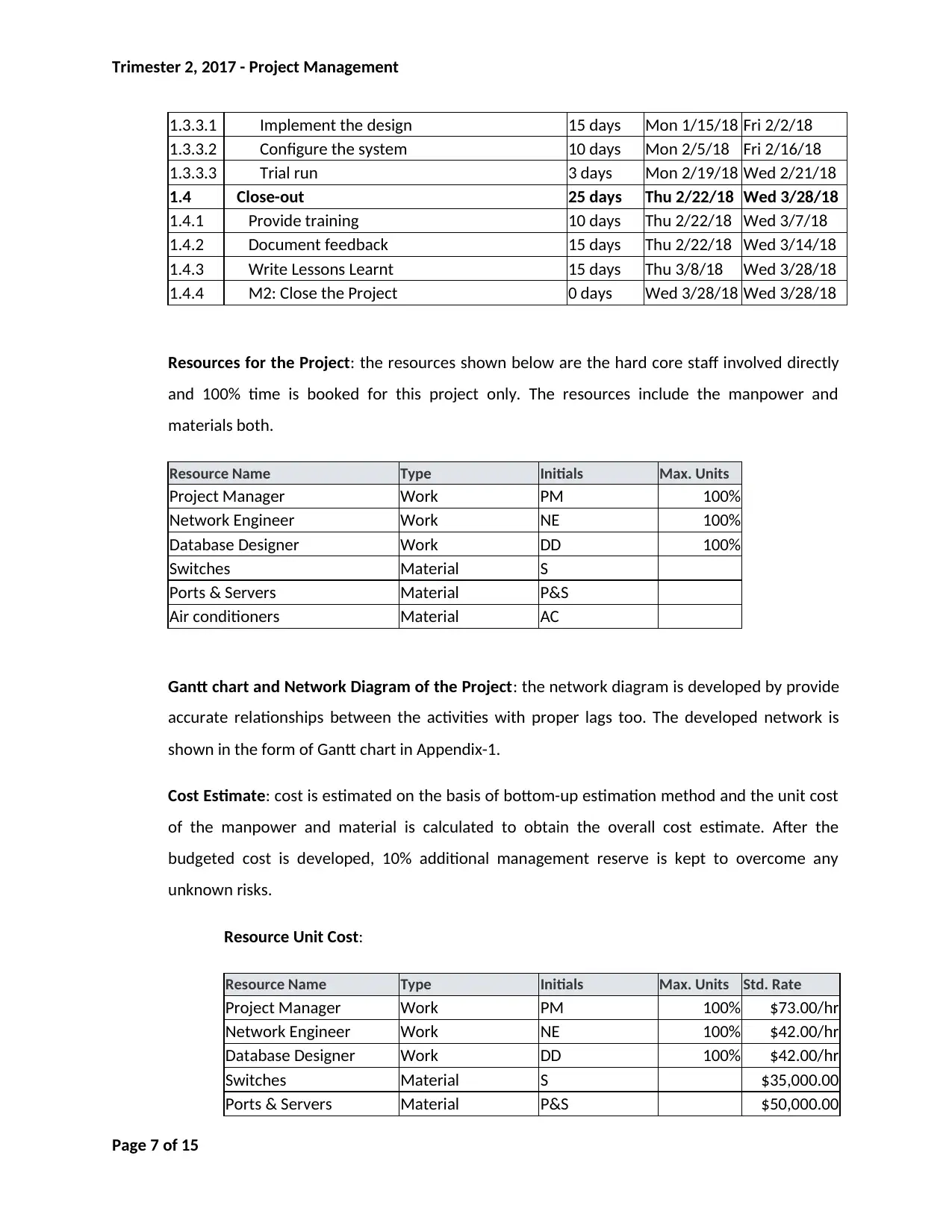
1.3.3.1 Implement the design 15 days Mon 1/15/18 Fri 2/2/18
1.3.3.2 Configure the system 10 days Mon 2/5/18 Fri 2/16/18
1.3.3.3 Trial run 3 days Mon 2/19/18 Wed 2/21/18
1.4 Close-out 25 days Thu 2/22/18 Wed 3/28/18
1.4.1 Provide training 10 days Thu 2/22/18 Wed 3/7/18
1.4.2 Document feedback 15 days Thu 2/22/18 Wed 3/14/18
1.4.3 Write Lessons Learnt 15 days Thu 3/8/18 Wed 3/28/18
1.4.4 M2: Close the Project 0 days Wed 3/28/18 Wed 3/28/18
Resources for the Project: the resources shown below are the hard core staff involved directly
and 100% time is booked for this project only. The resources include the manpower and
materials both.
Resource Name Type Initials Max. Units
Project Manager Work PM 100%
Network Engineer Work NE 100%
Database Designer Work DD 100%
Switches Material S
Ports & Servers Material P&S
Air conditioners Material AC
Gantt chart and Network Diagram of the Project: the network diagram is developed by provide
accurate relationships between the activities with proper lags too. The developed network is
shown in the form of Gantt chart in Appendix-1.
Cost Estimate: cost is estimated on the basis of bottom-up estimation method and the unit cost
of the manpower and material is calculated to obtain the overall cost estimate. After the
budgeted cost is developed, 10% additional management reserve is kept to overcome any
unknown risks.
Resource Unit Cost:
Resource Name Type Initials Max. Units Std. Rate
Project Manager Work PM 100% $73.00/hr
Network Engineer Work NE 100% $42.00/hr
Database Designer Work DD 100% $42.00/hr
Switches Material S $35,000.00
Ports & Servers Material P&S $50,000.00
Page 7 of 15
1.3.3.1 Implement the design 15 days Mon 1/15/18 Fri 2/2/18
1.3.3.2 Configure the system 10 days Mon 2/5/18 Fri 2/16/18
1.3.3.3 Trial run 3 days Mon 2/19/18 Wed 2/21/18
1.4 Close-out 25 days Thu 2/22/18 Wed 3/28/18
1.4.1 Provide training 10 days Thu 2/22/18 Wed 3/7/18
1.4.2 Document feedback 15 days Thu 2/22/18 Wed 3/14/18
1.4.3 Write Lessons Learnt 15 days Thu 3/8/18 Wed 3/28/18
1.4.4 M2: Close the Project 0 days Wed 3/28/18 Wed 3/28/18
Resources for the Project: the resources shown below are the hard core staff involved directly
and 100% time is booked for this project only. The resources include the manpower and
materials both.
Resource Name Type Initials Max. Units
Project Manager Work PM 100%
Network Engineer Work NE 100%
Database Designer Work DD 100%
Switches Material S
Ports & Servers Material P&S
Air conditioners Material AC
Gantt chart and Network Diagram of the Project: the network diagram is developed by provide
accurate relationships between the activities with proper lags too. The developed network is
shown in the form of Gantt chart in Appendix-1.
Cost Estimate: cost is estimated on the basis of bottom-up estimation method and the unit cost
of the manpower and material is calculated to obtain the overall cost estimate. After the
budgeted cost is developed, 10% additional management reserve is kept to overcome any
unknown risks.
Resource Unit Cost:
Resource Name Type Initials Max. Units Std. Rate
Project Manager Work PM 100% $73.00/hr
Network Engineer Work NE 100% $42.00/hr
Database Designer Work DD 100% $42.00/hr
Switches Material S $35,000.00
Ports & Servers Material P&S $50,000.00
Page 7 of 15
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Trimester 2, 2017 - Project Management
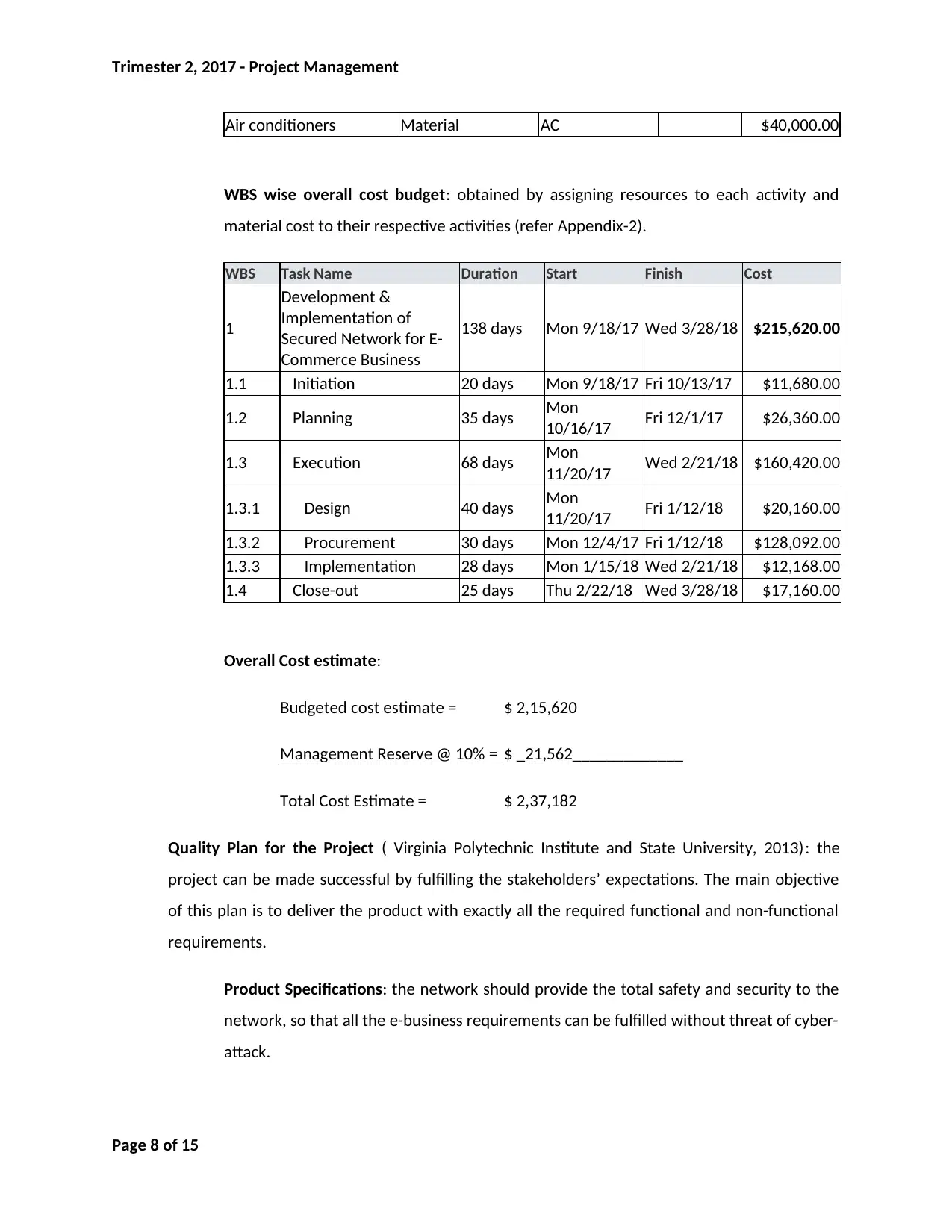
Air conditioners Material AC $40,000.00
WBS wise overall cost budget: obtained by assigning resources to each activity and
material cost to their respective activities (refer Appendix-2).
WBS Task Name Duration Start Finish Cost
1
Development &
Implementation of
Secured Network for E-
Commerce Business
138 days Mon 9/18/17 Wed 3/28/18 $215,620.00
1.1 Initiation 20 days Mon 9/18/17 Fri 10/13/17 $11,680.00
1.2 Planning 35 days Mon
10/16/17 Fri 12/1/17 $26,360.00
1.3 Execution 68 days Mon
11/20/17 Wed 2/21/18 $160,420.00
1.3.1 Design 40 days Mon
11/20/17 Fri 1/12/18 $20,160.00
1.3.2 Procurement 30 days Mon 12/4/17 Fri 1/12/18 $128,092.00
1.3.3 Implementation 28 days Mon 1/15/18 Wed 2/21/18 $12,168.00
1.4 Close-out 25 days Thu 2/22/18 Wed 3/28/18 $17,160.00
Overall Cost estimate:
Budgeted cost estimate = $ 2,15,620
Management Reserve @ 10% = $ _21,562_____________
Total Cost Estimate = $ 2,37,182
Quality Plan for the Project ( Virginia Polytechnic Institute and State University, 2013): the
project can be made successful by fulfilling the stakeholders’ expectations. The main objective
of this plan is to deliver the product with exactly all the required functional and non-functional
requirements.
Product Specifications: the network should provide the total safety and security to the
network, so that all the e-business requirements can be fulfilled without threat of cyber-
attack.
Page 8 of 15
Air conditioners Material AC $40,000.00
WBS wise overall cost budget: obtained by assigning resources to each activity and
material cost to their respective activities (refer Appendix-2).
WBS Task Name Duration Start Finish Cost
1
Development &
Implementation of
Secured Network for E-
Commerce Business
138 days Mon 9/18/17 Wed 3/28/18 $215,620.00
1.1 Initiation 20 days Mon 9/18/17 Fri 10/13/17 $11,680.00
1.2 Planning 35 days Mon
10/16/17 Fri 12/1/17 $26,360.00
1.3 Execution 68 days Mon
11/20/17 Wed 2/21/18 $160,420.00
1.3.1 Design 40 days Mon
11/20/17 Fri 1/12/18 $20,160.00
1.3.2 Procurement 30 days Mon 12/4/17 Fri 1/12/18 $128,092.00
1.3.3 Implementation 28 days Mon 1/15/18 Wed 2/21/18 $12,168.00
1.4 Close-out 25 days Thu 2/22/18 Wed 3/28/18 $17,160.00
Overall Cost estimate:
Budgeted cost estimate = $ 2,15,620
Management Reserve @ 10% = $ _21,562_____________
Total Cost Estimate = $ 2,37,182
Quality Plan for the Project ( Virginia Polytechnic Institute and State University, 2013): the
project can be made successful by fulfilling the stakeholders’ expectations. The main objective
of this plan is to deliver the product with exactly all the required functional and non-functional
requirements.
Product Specifications: the network should provide the total safety and security to the
network, so that all the e-business requirements can be fulfilled without threat of cyber-
attack.
Page 8 of 15
Trimester 2, 2017 - Project Management
Quality Assurance: the required standards of the network security must be met at the
end of the project life cycle, for which all the network designs need to be done with
accurate analytical analysis.
Quality Control: all the applicable check points are required to be developed with
measurable matrices of the standards.
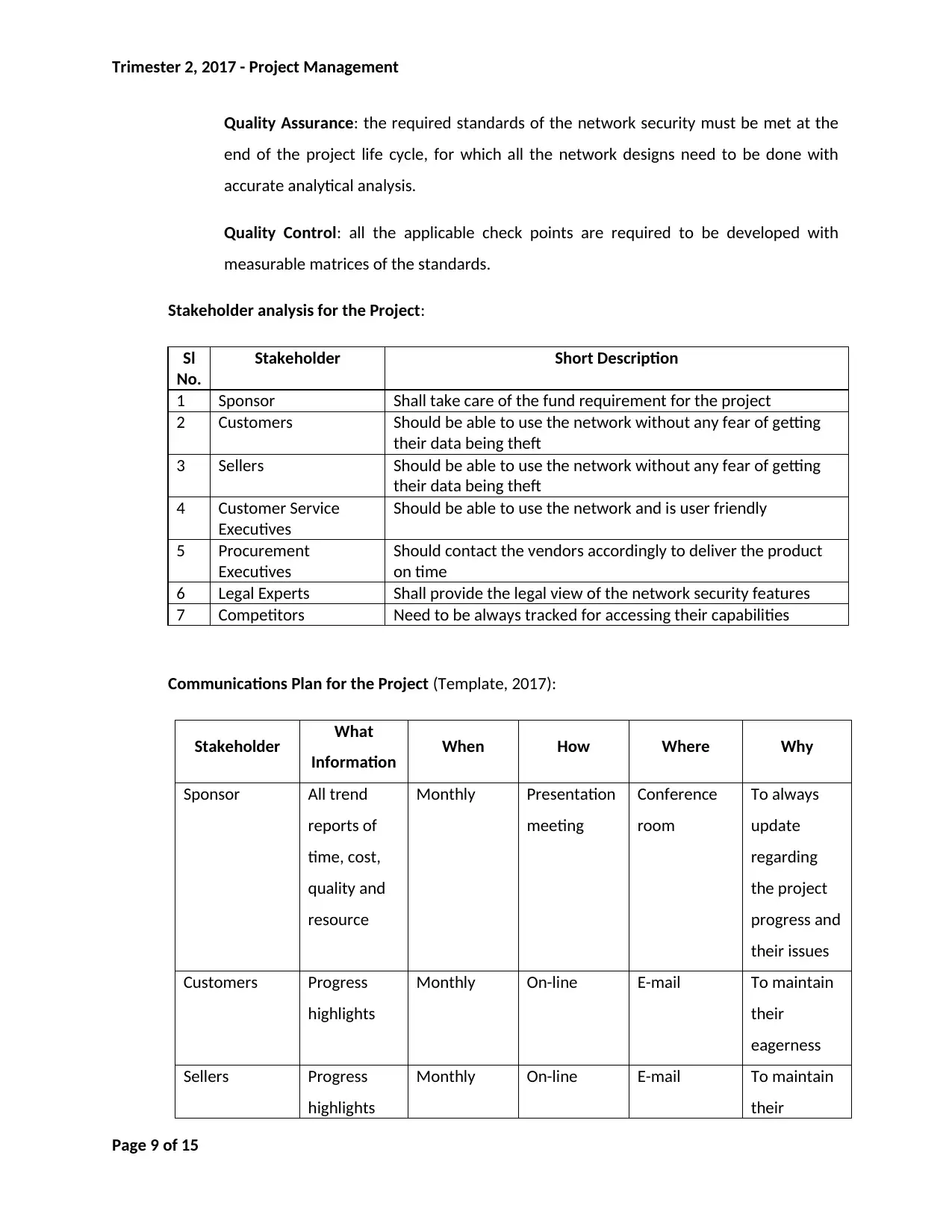
Stakeholder analysis for the Project:
Sl
No.
Stakeholder Short Description
1 Sponsor Shall take care of the fund requirement for the project
2 Customers Should be able to use the network without any fear of getting
their data being theft
3 Sellers Should be able to use the network without any fear of getting
their data being theft
4 Customer Service
Executives
Should be able to use the network and is user friendly
5 Procurement
Executives
Should contact the vendors accordingly to deliver the product
on time
6 Legal Experts Shall provide the legal view of the network security features
7 Competitors Need to be always tracked for accessing their capabilities
Communications Plan for the Project (Template, 2017):
Stakeholder What
Information When How Where Why
Sponsor All trend
reports of
time, cost,
quality and
resource
Monthly Presentation
meeting
Conference
room
To always
update
regarding
the project
progress and
their issues
Customers Progress
highlights
Monthly On-line E-mail To maintain
their
eagerness
Sellers Progress
highlights
Monthly On-line E-mail To maintain
their
Page 9 of 15
Quality Assurance: the required standards of the network security must be met at the
end of the project life cycle, for which all the network designs need to be done with
accurate analytical analysis.
Quality Control: all the applicable check points are required to be developed with
measurable matrices of the standards.
Stakeholder analysis for the Project:
Sl
No.
Stakeholder Short Description
1 Sponsor Shall take care of the fund requirement for the project
2 Customers Should be able to use the network without any fear of getting
their data being theft
3 Sellers Should be able to use the network without any fear of getting
their data being theft
4 Customer Service
Executives
Should be able to use the network and is user friendly
5 Procurement
Executives
Should contact the vendors accordingly to deliver the product
on time
6 Legal Experts Shall provide the legal view of the network security features
7 Competitors Need to be always tracked for accessing their capabilities
Communications Plan for the Project (Template, 2017):
Stakeholder What
Information When How Where Why
Sponsor All trend
reports of
time, cost,
quality and
resource
Monthly Presentation
meeting
Conference
room
To always
update
regarding
the project
progress and
their issues
Customers Progress
highlights
Monthly On-line E-mail To maintain
their
eagerness
Sellers Progress
highlights
Monthly On-line E-mail To maintain
their
Page 9 of 15
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Trimester 2, 2017 - Project Management
eagerness
Customer
Service
Executives
Progress
highlights
Monthly Meeting Presentation To keep
informed
about the
project
stages
Procurement
Executives
Procurement
status
Weekly E-mail,
report
Reports To PM for
update
regarding
the project
Legal Experts Procurement
status
Weekly E-mail,
report
Reports To PM for
update
regarding
the project
Competitors Their reports
must be
tracked
closely
As and when
available
Internal
group
meeting
Reports To get
updated
about what
others are
doing
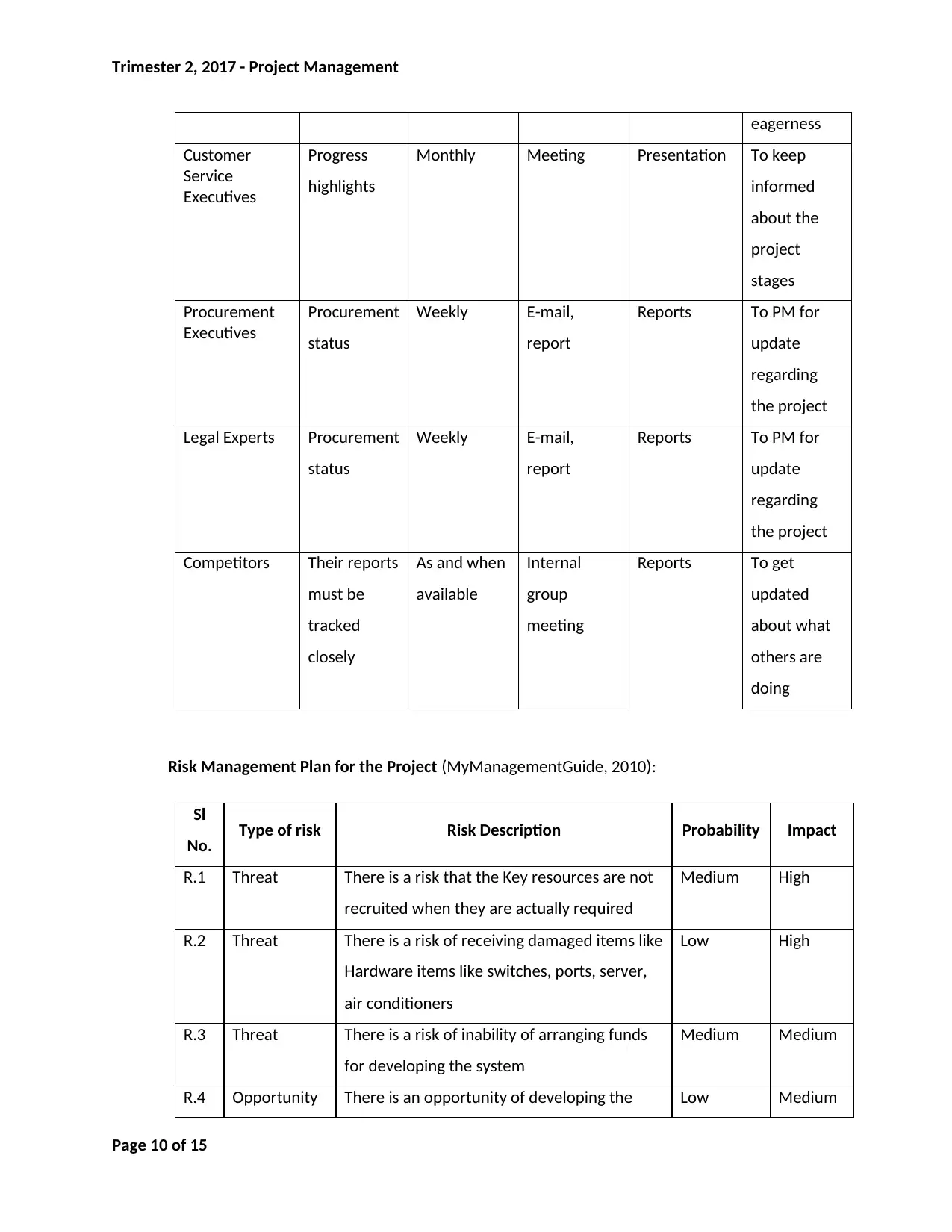
Risk Management Plan for the Project (MyManagementGuide, 2010):
Sl
No. Type of risk Risk Description Probability Impact
R.1 Threat There is a risk that the Key resources are not
recruited when they are actually required
Medium High
R.2 Threat There is a risk of receiving damaged items like
Hardware items like switches, ports, server,
air conditioners
Low High
R.3 Threat There is a risk of inability of arranging funds
for developing the system
Medium Medium
R.4 Opportunity There is an opportunity of developing the Low Medium
Page 10 of 15
eagerness
Customer
Service
Executives
Progress
highlights
Monthly Meeting Presentation To keep
informed
about the
project
stages
Procurement
Executives
Procurement
status
Weekly E-mail,
report
Reports To PM for
update
regarding
the project
Legal Experts Procurement
status
Weekly E-mail,
report
Reports To PM for
update
regarding
the project
Competitors Their reports
must be
tracked
closely
As and when
available
Internal
group
meeting
Reports To get
updated
about what
others are
doing
Risk Management Plan for the Project (MyManagementGuide, 2010):
Sl
No. Type of risk Risk Description Probability Impact
R.1 Threat There is a risk that the Key resources are not
recruited when they are actually required
Medium High
R.2 Threat There is a risk of receiving damaged items like
Hardware items like switches, ports, server,
air conditioners
Low High
R.3 Threat There is a risk of inability of arranging funds
for developing the system
Medium Medium
R.4 Opportunity There is an opportunity of developing the Low Medium
Page 10 of 15
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Trimester 2, 2017 - Project Management
system before e the schedule and it can save
from getting any LDs
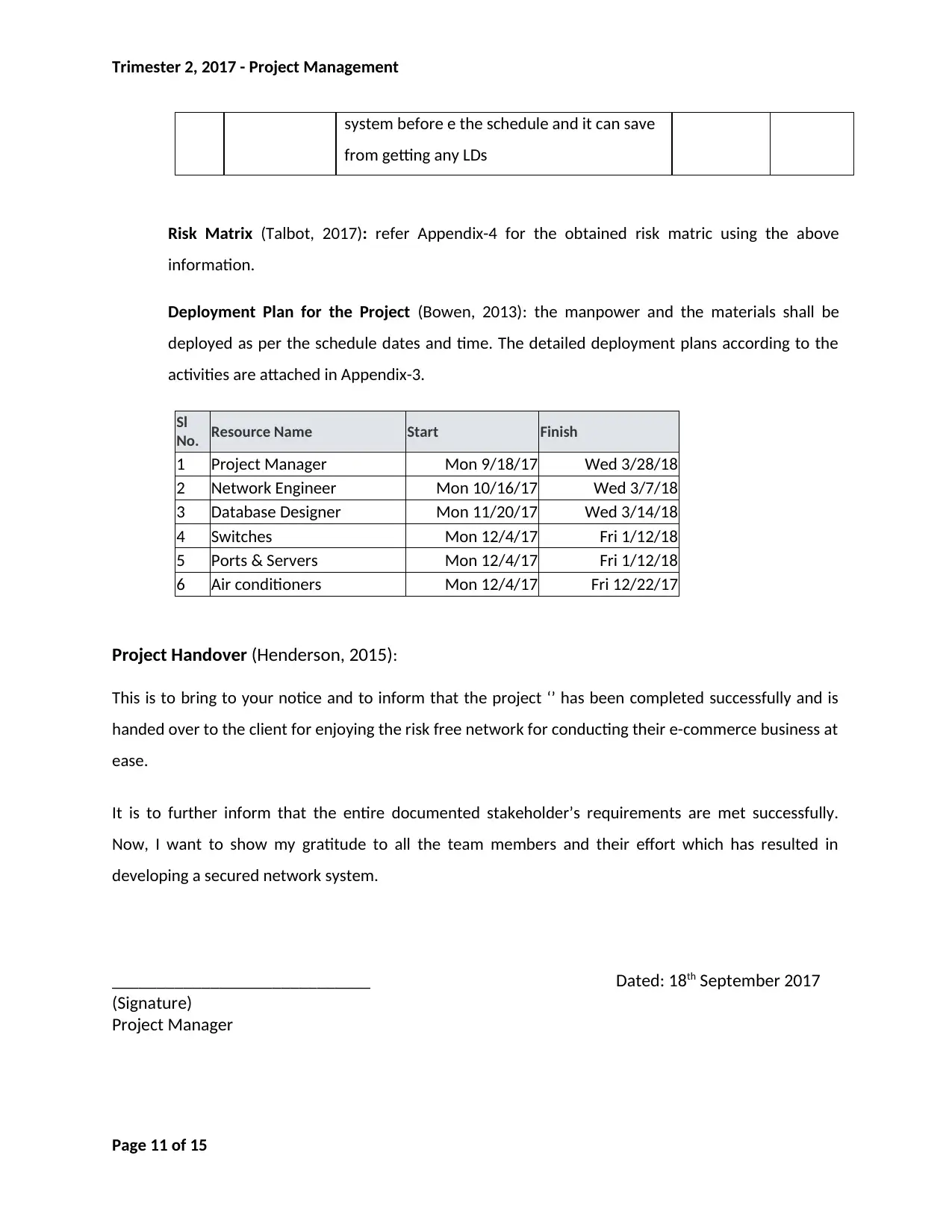
Risk Matrix (Talbot, 2017): refer Appendix-4 for the obtained risk matric using the above
information.
Deployment Plan for the Project (Bowen, 2013): the manpower and the materials shall be
deployed as per the schedule dates and time. The detailed deployment plans according to the
activities are attached in Appendix-3.
Sl
No. Resource Name Start Finish
1 Project Manager Mon 9/18/17 Wed 3/28/18
2 Network Engineer Mon 10/16/17 Wed 3/7/18
3 Database Designer Mon 11/20/17 Wed 3/14/18
4 Switches Mon 12/4/17 Fri 1/12/18
5 Ports & Servers Mon 12/4/17 Fri 1/12/18
6 Air conditioners Mon 12/4/17 Fri 12/22/17
Project Handover (Henderson, 2015):
This is to bring to your notice and to inform that the project ‘’ has been completed successfully and is
handed over to the client for enjoying the risk free network for conducting their e-commerce business at
ease.
It is to further inform that the entire documented stakeholder’s requirements are met successfully.
Now, I want to show my gratitude to all the team members and their effort which has resulted in
developing a secured network system.
_____________________________ Dated: 18th September 2017
(Signature)
Project Manager
Page 11 of 15
system before e the schedule and it can save
from getting any LDs
Risk Matrix (Talbot, 2017): refer Appendix-4 for the obtained risk matric using the above
information.
Deployment Plan for the Project (Bowen, 2013): the manpower and the materials shall be
deployed as per the schedule dates and time. The detailed deployment plans according to the
activities are attached in Appendix-3.
Sl
No. Resource Name Start Finish
1 Project Manager Mon 9/18/17 Wed 3/28/18
2 Network Engineer Mon 10/16/17 Wed 3/7/18
3 Database Designer Mon 11/20/17 Wed 3/14/18
4 Switches Mon 12/4/17 Fri 1/12/18
5 Ports & Servers Mon 12/4/17 Fri 1/12/18
6 Air conditioners Mon 12/4/17 Fri 12/22/17
Project Handover (Henderson, 2015):
This is to bring to your notice and to inform that the project ‘’ has been completed successfully and is
handed over to the client for enjoying the risk free network for conducting their e-commerce business at
ease.
It is to further inform that the entire documented stakeholder’s requirements are met successfully.
Now, I want to show my gratitude to all the team members and their effort which has resulted in
developing a secured network system.
_____________________________ Dated: 18th September 2017
(Signature)
Project Manager
Page 11 of 15

Trimester 2, 2017 - Project Management
Post project review and recommendations: after the project cycle is completed with the formal
project handover process is completed, then we shall also provide one year maintenance free of any
charges for the built network and its hardware systems too. Proper training plan is also required to be
developed so that all newly joined in the client’s organization for the operating and maintaining of the
system.
Further a feedback session is also planned to be scheduled for receiving the actual feedback of the
whole system and the steps taken to implement the secured network and the future happening and all
kind of supports shall be provided by us (chargeable basis).
Conclusion
After conducting the total review of the project to develop and implement the network security system
project, it can be concluded that the project is a success and more such systems have become the
necessity of the time. As all the businesses and its transactions are being done using internet services
only, so developing a strong network system to avoid any attack from outside is very much required.
This project features and management plan has provided a consolidated overview of the major tasks
which are required to be conducted for delivering the right quality product and none of the item or the
information were left pending. This project is always advisable and can be used as a learning for the
future development too.
References
Virginia Polytechnic Institute and State University. (2013). Project Quality Management Plan. Retrieved
September 17, 2017, from www.itplanning.org:
http://www.itplanning.org.vt.edu/pm/qualitymgmtplan.html
Bowen, R. (2013, May 20). Instituting a Project Deployment Plan. Retrieved September 17, 2017, from
brighthubpm.com: http://www.brighthubpm.com/project-planning/62273-how-to-create-a-
project-deployment-plan/
Henderson, R. (2015, July 3). Project Sign-off. Retrieved September 17, 2017, from LinkedIn Corporation:
https://www.slideshare.net/RayHenderson2/project-signoff
MyManagementGuide. (2010, May). Retrieved September 17, 2017, from 2. Risk management plan for a
project: Definition, Purpose, Software, Content and Approaches:
Page 12 of 15
Post project review and recommendations: after the project cycle is completed with the formal
project handover process is completed, then we shall also provide one year maintenance free of any
charges for the built network and its hardware systems too. Proper training plan is also required to be
developed so that all newly joined in the client’s organization for the operating and maintaining of the
system.
Further a feedback session is also planned to be scheduled for receiving the actual feedback of the
whole system and the steps taken to implement the secured network and the future happening and all
kind of supports shall be provided by us (chargeable basis).
Conclusion
After conducting the total review of the project to develop and implement the network security system
project, it can be concluded that the project is a success and more such systems have become the
necessity of the time. As all the businesses and its transactions are being done using internet services
only, so developing a strong network system to avoid any attack from outside is very much required.
This project features and management plan has provided a consolidated overview of the major tasks
which are required to be conducted for delivering the right quality product and none of the item or the
information were left pending. This project is always advisable and can be used as a learning for the
future development too.
References
Virginia Polytechnic Institute and State University. (2013). Project Quality Management Plan. Retrieved
September 17, 2017, from www.itplanning.org:
http://www.itplanning.org.vt.edu/pm/qualitymgmtplan.html
Bowen, R. (2013, May 20). Instituting a Project Deployment Plan. Retrieved September 17, 2017, from
brighthubpm.com: http://www.brighthubpm.com/project-planning/62273-how-to-create-a-
project-deployment-plan/
Henderson, R. (2015, July 3). Project Sign-off. Retrieved September 17, 2017, from LinkedIn Corporation:
https://www.slideshare.net/RayHenderson2/project-signoff
MyManagementGuide. (2010, May). Retrieved September 17, 2017, from 2. Risk management plan for a
project: Definition, Purpose, Software, Content and Approaches:
Page 12 of 15
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





