Industry Project Plan: Protecting ChekRite Data from Unmanaged Devices
VerifiedAdded on 2022/08/22
|13
|2351
|21
Project
AI Summary
This Industry Project Plan addresses the critical need for enhanced data security within ChekRite, a data capturing company, particularly focusing on their Android application and the challenges posed by Bring Your Own Device (BYOD) policies. The project aims to improve the security and usability of the Android app, proposing strategies to protect business data from unmanaged devices. The plan outlines project objectives, scope, and functional/non-functional requirements, including the creation of user profiles, inspection functionalities, and secure data storage. The project adopts an agile methodology, specifically the scrum framework, for efficient development, detailing sprint planning, work breakdown structures, and Gantt charts. Communication and risk management strategies are also included, covering potential threats like scope creep and lack of time management. The plan provides a comprehensive overview of the project's lifecycle, from initial planning to implementation, emphasizing the importance of a secure and user-friendly application to store data securely in the cloud.

Running head: INDUSTRY PROJECT PLAN
Industry Project Plan
Name of Student-
Name of University-
Author’s Note-
Industry Project Plan
Name of Student-
Name of University-
Author’s Note-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INDUSTRY PROJECT PLAN
Title: Strategies for Protecting Business Data from Unmanaged Devices
Introduction
Background
The organization that is included in this report is ChekRite. This is a data capturing
company that helps to store the data of the user securely. The main goal of ChekRite is creating a
safer, efficient and productive working environment and this is done by eliminating the admin,
recovering costs, and prioritize the risks. ChekRite helps to conduct digital inspections by
providing checklists, and can collect detailed information by asking clear questions, and annotate
photos and also enables the users to record notes over voice. After completion of the inspection,
ChekRite helps to sign, share and submit the inspection with single check. ChekRite has security
with the interface that they provide and they have secured iOS platform. But after expanding to
Android application, the security and usability of the app is to be increased. There are many
companies that has Bring Your Own Devices (BYOD) policies and for those companies
ChekRite needs to provide more secured interface.
Aim of project
The aim of this research project is to increase the security and usability of the android
mobile application provided by ChekRite and implement strategies to protect the business data
from some unmanaged devices. The android based application is not as secured as iOS
application and ChekRite needs to secure the information that are captured by the android
application.
Objective of the project
The objectives of this research project are
Title: Strategies for Protecting Business Data from Unmanaged Devices
Introduction
Background
The organization that is included in this report is ChekRite. This is a data capturing
company that helps to store the data of the user securely. The main goal of ChekRite is creating a
safer, efficient and productive working environment and this is done by eliminating the admin,
recovering costs, and prioritize the risks. ChekRite helps to conduct digital inspections by
providing checklists, and can collect detailed information by asking clear questions, and annotate
photos and also enables the users to record notes over voice. After completion of the inspection,
ChekRite helps to sign, share and submit the inspection with single check. ChekRite has security
with the interface that they provide and they have secured iOS platform. But after expanding to
Android application, the security and usability of the app is to be increased. There are many
companies that has Bring Your Own Devices (BYOD) policies and for those companies
ChekRite needs to provide more secured interface.
Aim of project
The aim of this research project is to increase the security and usability of the android
mobile application provided by ChekRite and implement strategies to protect the business data
from some unmanaged devices. The android based application is not as secured as iOS
application and ChekRite needs to secure the information that are captured by the android
application.
Objective of the project
The objectives of this research project are

2INDUSTRY PROJECT PLAN
To study the current state of the unmanageable devices that are used in the business.
To speared technical knowledge, risk awareness and the data threat exposure to the users
using the unmanageable devices.
To specify different approaches that the software companies should take so that they can
manage the risk of the unmanaged devices and includes cost implications of those
approaches.
To provide technical solution in application design so that the data of the company can be
protected from unmanaged android devices.
Potential Impact
By developing this research project, the businesses using BYOD policies can store the
data securely in their businesses. There will be potential growth in the business as because they
will be able to store the data securely in the cloud.
Describe Project Scope
In-Scope
The in-scope of this research project includes
The technical solution for the android application will be provided in this research so that
the companies can protect their data.
Proper training will be provided to the employees of the companies to use the android
application as all the employees are not tech savvy.
Includes risk awareness for using the non-manageable devices in the organization.
To study the current state of the unmanageable devices that are used in the business.
To speared technical knowledge, risk awareness and the data threat exposure to the users
using the unmanageable devices.
To specify different approaches that the software companies should take so that they can
manage the risk of the unmanaged devices and includes cost implications of those
approaches.
To provide technical solution in application design so that the data of the company can be
protected from unmanaged android devices.
Potential Impact
By developing this research project, the businesses using BYOD policies can store the
data securely in their businesses. There will be potential growth in the business as because they
will be able to store the data securely in the cloud.
Describe Project Scope
In-Scope
The in-scope of this research project includes
The technical solution for the android application will be provided in this research so that
the companies can protect their data.
Proper training will be provided to the employees of the companies to use the android
application as all the employees are not tech savvy.
Includes risk awareness for using the non-manageable devices in the organization.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INDUSTRY PROJECT PLAN
Out-Scope
Any documentation for the training that are provided to the employee will not be
included in this research project.
Security policies will not be provided the users using the application.
The application intend to protect the data under some particular constraints and if data
breach occurs outside those constraints, that is not included in this research project.
Functional Requirements
ChekRite will help to create a profile for the users who uses the android application.
There will be option for the users to select that is they want to do inspection, pre-start or
can select the uncategorized option.
The users will be able to start the checking for a particular asset and they will be able to
calculate the price of the widgets that are used in the organization.
The customers will also have the accessibility to record the “to do tasks” so that they gets
reminded at the time to do the work.
The customers will have security and proper user interface to access the application.
Non-Functional Requirements
The application will have a user interface that is easy to use and users who are not tech
savvy can also use the application.
The application will have security so that the data can be stored safely in the application.
The application will be available 24 hours and will be robust and reliable for the users.
The application is capable of handling any exception error in the application.
The application will be able to support many concurrent users and the response time of
the interface is very less.
Out-Scope
Any documentation for the training that are provided to the employee will not be
included in this research project.
Security policies will not be provided the users using the application.
The application intend to protect the data under some particular constraints and if data
breach occurs outside those constraints, that is not included in this research project.
Functional Requirements
ChekRite will help to create a profile for the users who uses the android application.
There will be option for the users to select that is they want to do inspection, pre-start or
can select the uncategorized option.
The users will be able to start the checking for a particular asset and they will be able to
calculate the price of the widgets that are used in the organization.
The customers will also have the accessibility to record the “to do tasks” so that they gets
reminded at the time to do the work.
The customers will have security and proper user interface to access the application.
Non-Functional Requirements
The application will have a user interface that is easy to use and users who are not tech
savvy can also use the application.
The application will have security so that the data can be stored safely in the application.
The application will be available 24 hours and will be robust and reliable for the users.
The application is capable of handling any exception error in the application.
The application will be able to support many concurrent users and the response time of
the interface is very less.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INDUSTRY PROJECT PLAN
The application has supportability because more security patch can be added in the
application after the development of the system.
Project Management
Project Management Approach
The method of agile project management helps to complete the project more efficiently
and with more flexibility. The methodology includes iterative approach to develop the
application and the work is divided in to sprints and all the sprints are considered as small
projects to be completed on time (Santos et al., 2016). The sprints in the agile methodology
includes project design, project implementation, testing as well as deployment of the project that
are defined in the scope of the application development. The agile methodology that will be used
for creating the application is adaptive to business change and provides the clients to add, change
as well as remove the requirements in the ongoing project.
The technique of agile methodology that will be used for developing a secured android
application is scrum methodology (Flora, 2018). This method includes interlocking steps as well
as include components that are required in the development process. Scrum includes a
development strategy that combines the software developers as team and helps to reach the goal
of the project. The application development with scrum technology actually starts with a wish
list including product backlog. The team of product backlog includes backlog, the work that is
needed to be completed and the time that they will take to complete the project. The scrum
method includes sprints and sprints are the time period that is used for software development.
Sprint in scrum lasts for more than weeks and this helps to create saleable products.
The application has supportability because more security patch can be added in the
application after the development of the system.
Project Management
Project Management Approach
The method of agile project management helps to complete the project more efficiently
and with more flexibility. The methodology includes iterative approach to develop the
application and the work is divided in to sprints and all the sprints are considered as small
projects to be completed on time (Santos et al., 2016). The sprints in the agile methodology
includes project design, project implementation, testing as well as deployment of the project that
are defined in the scope of the application development. The agile methodology that will be used
for creating the application is adaptive to business change and provides the clients to add, change
as well as remove the requirements in the ongoing project.
The technique of agile methodology that will be used for developing a secured android
application is scrum methodology (Flora, 2018). This method includes interlocking steps as well
as include components that are required in the development process. Scrum includes a
development strategy that combines the software developers as team and helps to reach the goal
of the project. The application development with scrum technology actually starts with a wish
list including product backlog. The team of product backlog includes backlog, the work that is
needed to be completed and the time that they will take to complete the project. The scrum
method includes sprints and sprints are the time period that is used for software development.
Sprint in scrum lasts for more than weeks and this helps to create saleable products.

5INDUSTRY PROJECT PLAN
Justification for the chosen approach
The sprint of scrum process includes good enough development that mainly results in
saleable product even when the project is on process. So, this technique of project management
helps to lessen the time in the market and can provide high revenue in the market. All the sprints
in the scrum methodology are reviewed at first before going to the next sprint and testing process
is conducted throughout the project process (Ashishdeep, Bhatia & Varma, 2016). This allows
the change in the project and the scope of the project can be altered at any point of the project.
So, the scrum technique in agile methodology is the most suitable approach to conduct this
research study.
Implementation of PM Approach
For developing the application for ChekRite, certain steps were followed to implement
the scrum methodology in this project. The steps that were used are:
1. Proper definition of scrum elements: All the elements in scrum such as product owner,
work team, scrum master and scrum duration are mentioned in the project. With proper
definition, the project scrum works properly.
2. Prioritize the objectives and backlog: Project backlog is to be defined in the project as
the list of tasks that are included in the project and backlog of the project is known as the project
roadmap and includes list of functionalities, and the activities that are pending.
3. Planning the sprint: The sprints that are included in the scrum are to be planned prior to
carry out the project details and important information in the project are included in the project
backlog (Jacob, 2019). All estimations regarding the project, and commitments that are to be
included in the performance includes large number of project tasks and stories.
Justification for the chosen approach
The sprint of scrum process includes good enough development that mainly results in
saleable product even when the project is on process. So, this technique of project management
helps to lessen the time in the market and can provide high revenue in the market. All the sprints
in the scrum methodology are reviewed at first before going to the next sprint and testing process
is conducted throughout the project process (Ashishdeep, Bhatia & Varma, 2016). This allows
the change in the project and the scope of the project can be altered at any point of the project.
So, the scrum technique in agile methodology is the most suitable approach to conduct this
research study.
Implementation of PM Approach
For developing the application for ChekRite, certain steps were followed to implement
the scrum methodology in this project. The steps that were used are:
1. Proper definition of scrum elements: All the elements in scrum such as product owner,
work team, scrum master and scrum duration are mentioned in the project. With proper
definition, the project scrum works properly.
2. Prioritize the objectives and backlog: Project backlog is to be defined in the project as
the list of tasks that are included in the project and backlog of the project is known as the project
roadmap and includes list of functionalities, and the activities that are pending.
3. Planning the sprint: The sprints that are included in the scrum are to be planned prior to
carry out the project details and important information in the project are included in the project
backlog (Jacob, 2019). All estimations regarding the project, and commitments that are to be
included in the performance includes large number of project tasks and stories.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6INDUSTRY PROJECT PLAN
4. Making work and daily meeting visible: The progress of the project is to be made
visible to the team and project update should be updated from time to time.
5. Reviewing the sprints: This methodology is an iterative process and review of each
methodology is to be carried out in the product progress. This helps to make progress with the
expectation of the project.
Project Schedule
Work Breakdown Structure
Figure 1: Work Breakdown Structure
(Source: Created by Author)
Developing of android
mobile app
Project Initiation
Develop the
business case
Assign project
manager
Develop project
charter
Implement project
management
technique
Project Planning
Primary Planning
Develop WBS for
the project
Plan Schedule for
the porject
Plan project
Resource
Plan project Budget
Perform Supply Plan
Plan Risk
management
Plan communication
management
Plan Change
management and
cost Management
Design and analysis
phase
Developing
application design
Develop functional
and non-functional
requirement
Design Use case
Design front end
interface
Design back end
interface
User interface of
application
Perform security
analysis
Test phase
Test all subsystem
Integrate
Sub-systems
Test Integrated
system
Testing
documentation
Project Closure
Documenting
project closure
Project Signoff
4. Making work and daily meeting visible: The progress of the project is to be made
visible to the team and project update should be updated from time to time.
5. Reviewing the sprints: This methodology is an iterative process and review of each
methodology is to be carried out in the product progress. This helps to make progress with the
expectation of the project.
Project Schedule
Work Breakdown Structure
Figure 1: Work Breakdown Structure
(Source: Created by Author)
Developing of android
mobile app
Project Initiation
Develop the
business case
Assign project
manager
Develop project
charter
Implement project
management
technique
Project Planning
Primary Planning
Develop WBS for
the project
Plan Schedule for
the porject
Plan project
Resource
Plan project Budget
Perform Supply Plan
Plan Risk
management
Plan communication
management
Plan Change
management and
cost Management
Design and analysis
phase
Developing
application design
Develop functional
and non-functional
requirement
Design Use case
Design front end
interface
Design back end
interface
User interface of
application
Perform security
analysis
Test phase
Test all subsystem
Integrate
Sub-systems
Test Integrated
system
Testing
documentation
Project Closure
Documenting
project closure
Project Signoff
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
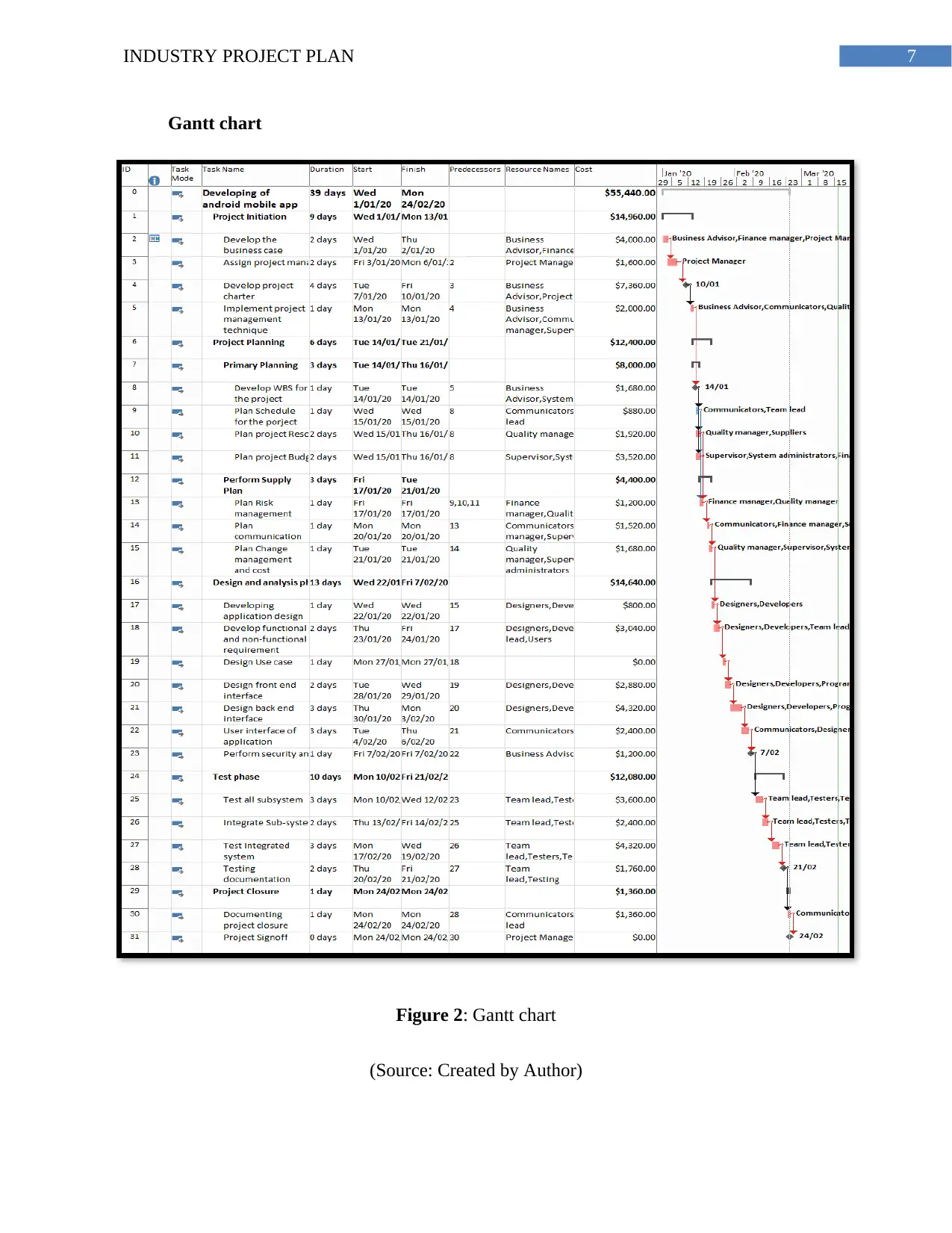
7INDUSTRY PROJECT PLAN
Gantt chart
Figure 2: Gantt chart
(Source: Created by Author)
Gantt chart
Figure 2: Gantt chart
(Source: Created by Author)
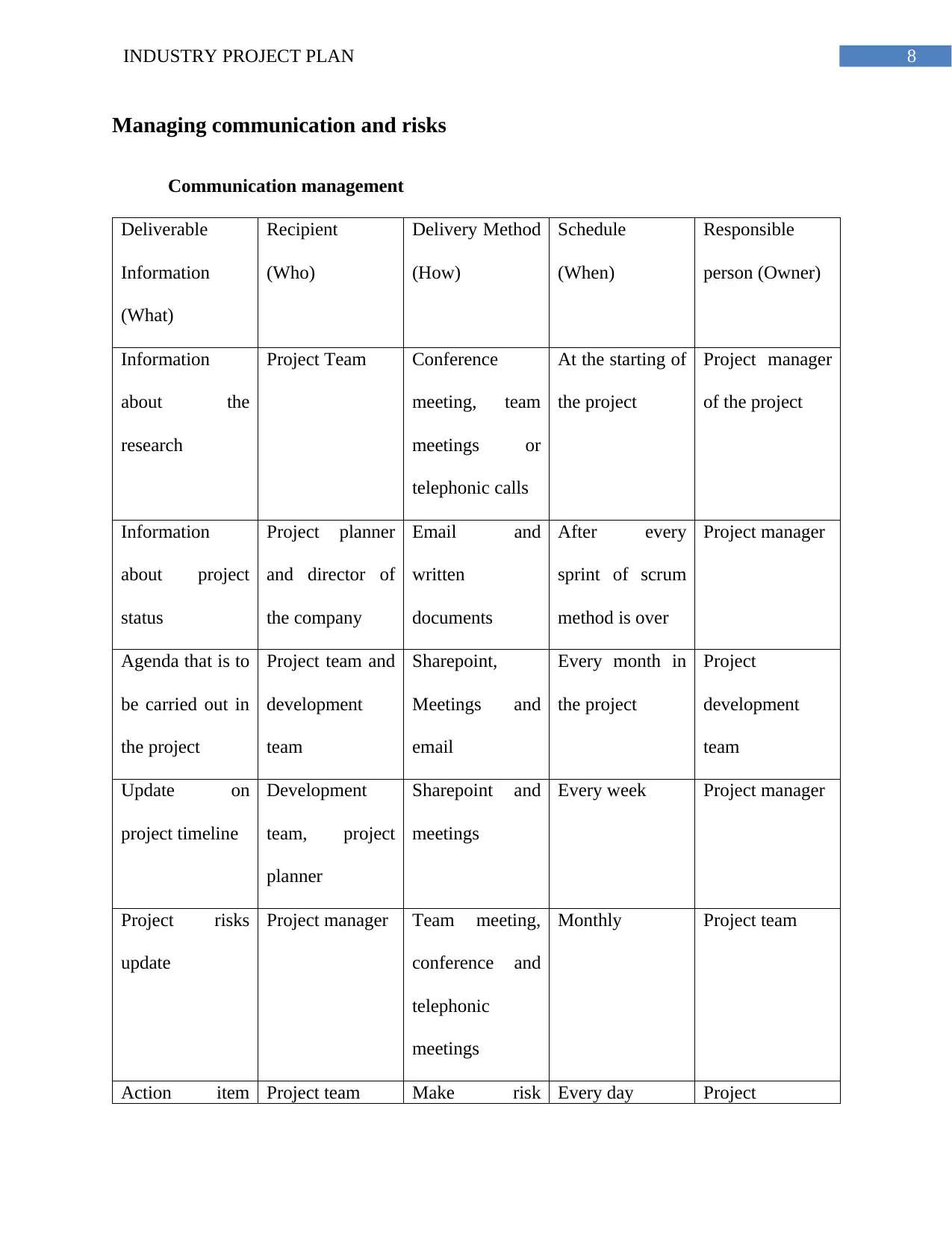
8INDUSTRY PROJECT PLAN
Managing communication and risks
Communication management
Deliverable
Information
(What)
Recipient
(Who)
Delivery Method
(How)
Schedule
(When)
Responsible
person (Owner)
Information
about the
research
Project Team Conference
meeting, team
meetings or
telephonic calls
At the starting of
the project
Project manager
of the project
Information
about project
status
Project planner
and director of
the company
Email and
written
documents
After every
sprint of scrum
method is over
Project manager
Agenda that is to
be carried out in
the project
Project team and
development
team
Sharepoint,
Meetings and
email
Every month in
the project
Project
development
team
Update on
project timeline
Development
team, project
planner
Sharepoint and
meetings
Every week Project manager
Project risks
update
Project manager Team meeting,
conference and
telephonic
meetings
Monthly Project team
Action item Project team Make risk Every day Project
Managing communication and risks
Communication management
Deliverable
Information
(What)
Recipient
(Who)
Delivery Method
(How)
Schedule
(When)
Responsible
person (Owner)
Information
about the
research
Project Team Conference
meeting, team
meetings or
telephonic calls
At the starting of
the project
Project manager
of the project
Information
about project
status
Project planner
and director of
the company
Email and
written
documents
After every
sprint of scrum
method is over
Project manager
Agenda that is to
be carried out in
the project
Project team and
development
team
Sharepoint,
Meetings and
Every month in
the project
Project
development
team
Update on
project timeline
Development
team, project
planner
Sharepoint and
meetings
Every week Project manager
Project risks
update
Project manager Team meeting,
conference and
telephonic
meetings
Monthly Project team
Action item Project team Make risk Every day Project
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9INDUSTRY PROJECT PLAN
status for project
update
document and
organize
meetings
development
team
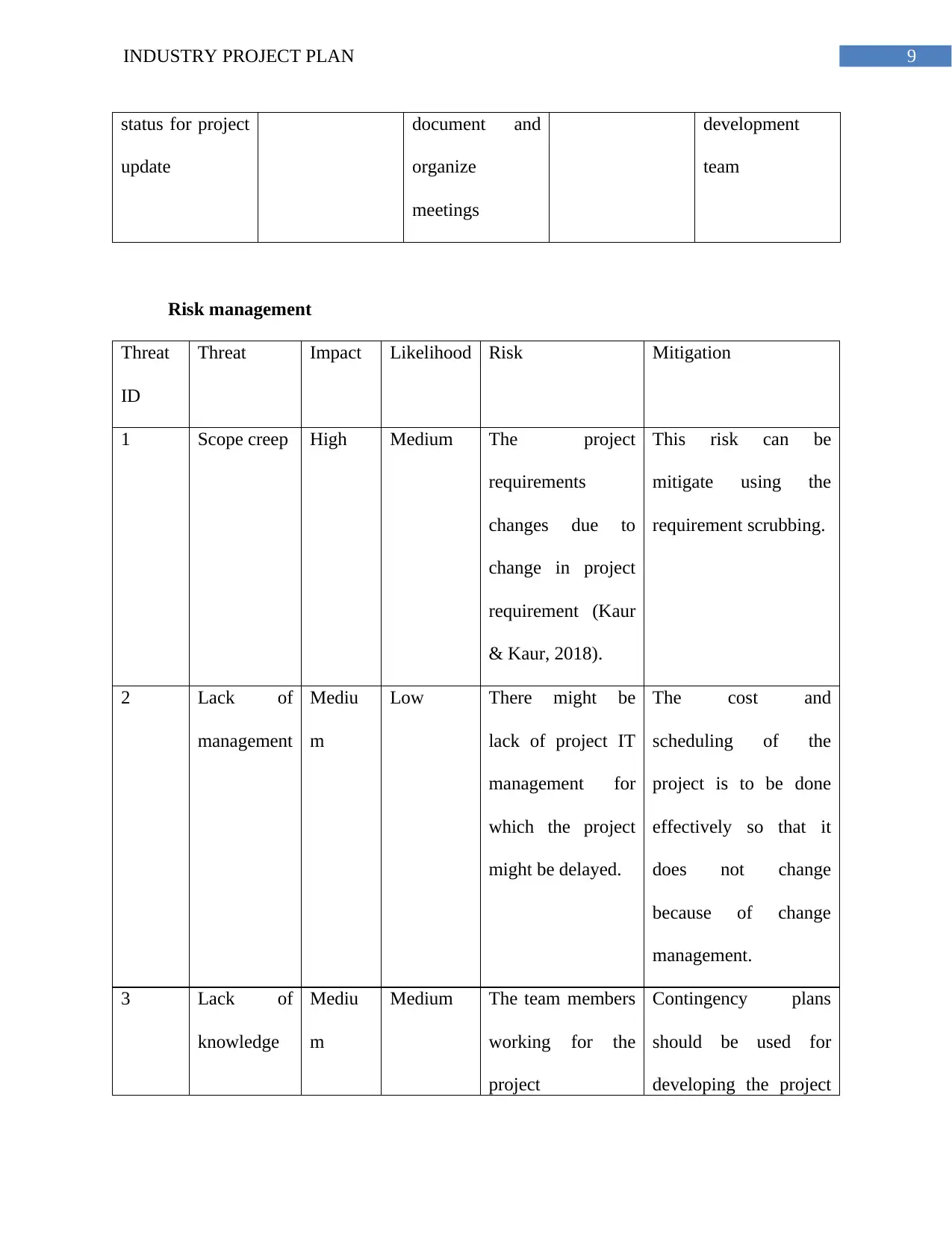
Risk management
Threat
ID
Threat Impact Likelihood Risk Mitigation
1 Scope creep High Medium The project
requirements
changes due to
change in project
requirement (Kaur
& Kaur, 2018).
This risk can be
mitigate using the
requirement scrubbing.
2 Lack of
management
Mediu
m
Low There might be
lack of project IT
management for
which the project
might be delayed.
The cost and
scheduling of the
project is to be done
effectively so that it
does not change
because of change
management.
3 Lack of
knowledge
Mediu
m
Medium The team members
working for the
project
Contingency plans
should be used for
developing the project
status for project
update
document and
organize
meetings
development
team
Risk management
Threat
ID
Threat Impact Likelihood Risk Mitigation
1 Scope creep High Medium The project
requirements
changes due to
change in project
requirement (Kaur
& Kaur, 2018).
This risk can be
mitigate using the
requirement scrubbing.
2 Lack of
management
Mediu
m
Low There might be
lack of project IT
management for
which the project
might be delayed.
The cost and
scheduling of the
project is to be done
effectively so that it
does not change
because of change
management.
3 Lack of
knowledge
Mediu
m
Medium The team members
working for the
project
Contingency plans
should be used for
developing the project
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10INDUSTRY PROJECT PLAN
development might
not be skilled
enough to handle
the project
development
scope and automated
version control tools
should be implemented
in the project (Volkov,
Semin & Semin, 2019).
4 Lack of time
and cost
management
High High The project might
be delayed because
of having no
control on the
project.
Proper scheduling
tracking of the project
is done so that the
project manager can
track the project
progress.
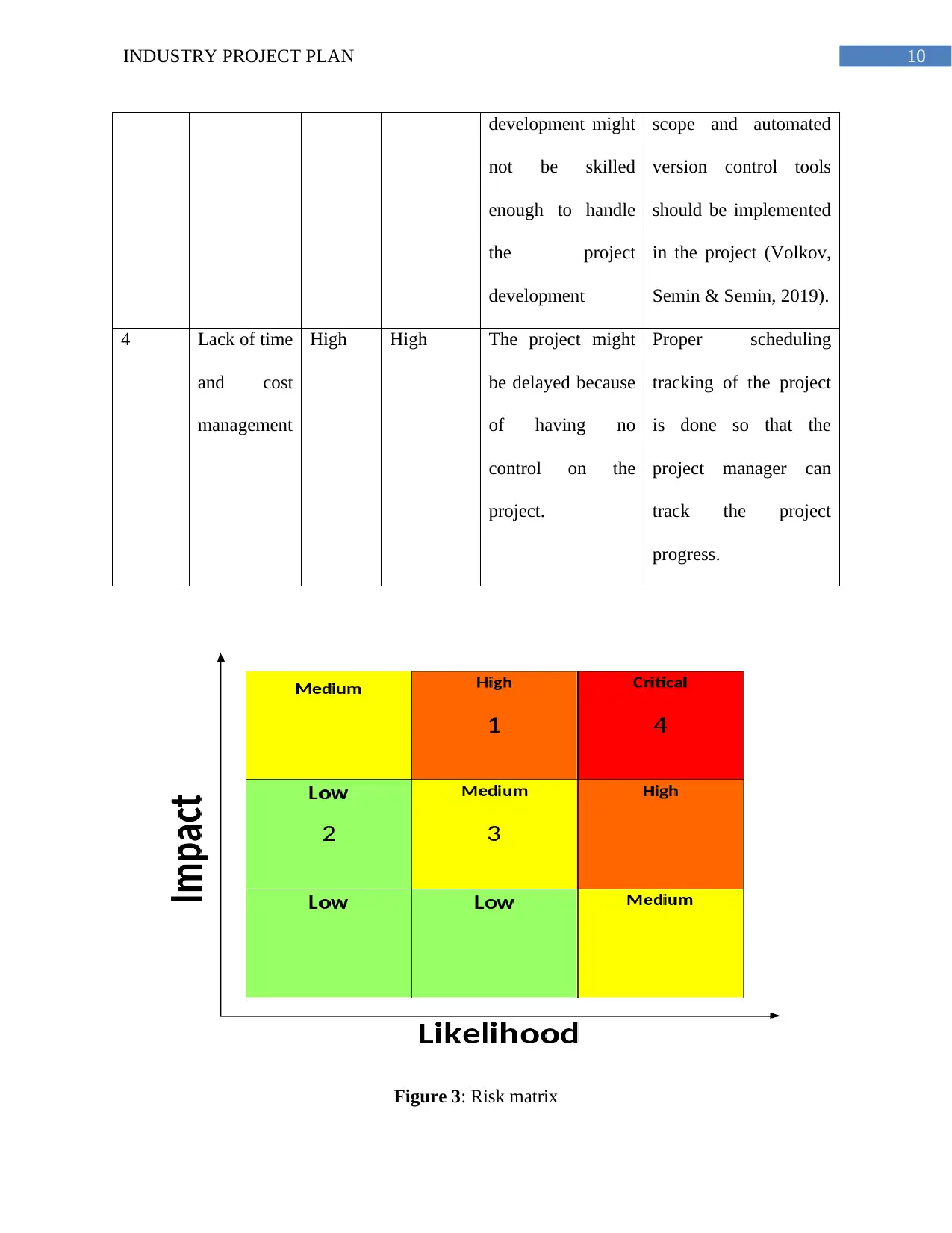
Figure 3: Risk matrix
development might
not be skilled
enough to handle
the project
development
scope and automated
version control tools
should be implemented
in the project (Volkov,
Semin & Semin, 2019).
4 Lack of time
and cost
management
High High The project might
be delayed because
of having no
control on the
project.
Proper scheduling
tracking of the project
is done so that the
project manager can
track the project
progress.
Figure 3: Risk matrix

11INDUSTRY PROJECT PLAN
(Source: Created by Author)
Bibliography
Ahmad, A., Li, K., Feng, C., Asim, S. M., Yousif, A., & Ge, S. (2018). An empirical study of
investigating mobile applications development challenges. IEEE Access, 6, 17711-17728.
Ashishdeep, A., Bhatia, J., & Varma, K. (2016). Software process models for mobile application
development: A review. Computer Science and Electronic Journal, 7(1), 150-153.
Dar, H., Lali, M. I., Ashraf, H., Ramzan, M., Amjad, T., & Shahzad, B. (2018). A systematic
study on software requirements elicitation techniques and its challenges in mobile
application development. IEEE Access, 6, 63859-63867.
Delía, L., Galdamez, N., Corbalan, L., Pesado, P., & Thomas, P. (2017, July). Approaches to
mobile application development: comparative performance analysis. In 2017 Computing
Conference (pp. 652-659). IEEE.
Flora, H. K. (2018). Adopting an agile approach for the development of mobile applications.
Jacob, N. M. (2019). A Review of Mobile Application Development in the Agile Software
Development Environment. Global Journal of Computer Science and Technology.
Kaur, A., & Kaur, K. (2018). Effort Estimation in Traditional and Agile Mobile Application
Development & Testing. Indonesian Journal of Electrical Engineering and Computer
Science, 12(3), 1265-1272.
Kumar, N. A., Krishna, K. H., & Manjula, R. (2016). Challenges and best practices in mobile
application development. Imperial Journal of Interdisciplinary Research, 2, 12.
(Source: Created by Author)
Bibliography
Ahmad, A., Li, K., Feng, C., Asim, S. M., Yousif, A., & Ge, S. (2018). An empirical study of
investigating mobile applications development challenges. IEEE Access, 6, 17711-17728.
Ashishdeep, A., Bhatia, J., & Varma, K. (2016). Software process models for mobile application
development: A review. Computer Science and Electronic Journal, 7(1), 150-153.
Dar, H., Lali, M. I., Ashraf, H., Ramzan, M., Amjad, T., & Shahzad, B. (2018). A systematic
study on software requirements elicitation techniques and its challenges in mobile
application development. IEEE Access, 6, 63859-63867.
Delía, L., Galdamez, N., Corbalan, L., Pesado, P., & Thomas, P. (2017, July). Approaches to
mobile application development: comparative performance analysis. In 2017 Computing
Conference (pp. 652-659). IEEE.
Flora, H. K. (2018). Adopting an agile approach for the development of mobile applications.
Jacob, N. M. (2019). A Review of Mobile Application Development in the Agile Software
Development Environment. Global Journal of Computer Science and Technology.
Kaur, A., & Kaur, K. (2018). Effort Estimation in Traditional and Agile Mobile Application
Development & Testing. Indonesian Journal of Electrical Engineering and Computer
Science, 12(3), 1265-1272.
Kumar, N. A., Krishna, K. H., & Manjula, R. (2016). Challenges and best practices in mobile
application development. Imperial Journal of Interdisciplinary Research, 2, 12.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





