Public Key Cryptography: RSA Algorithm and Mathematical Concepts
VerifiedAdded on 2022/01/21
|44
|2675
|91
Homework Assignment
AI Summary
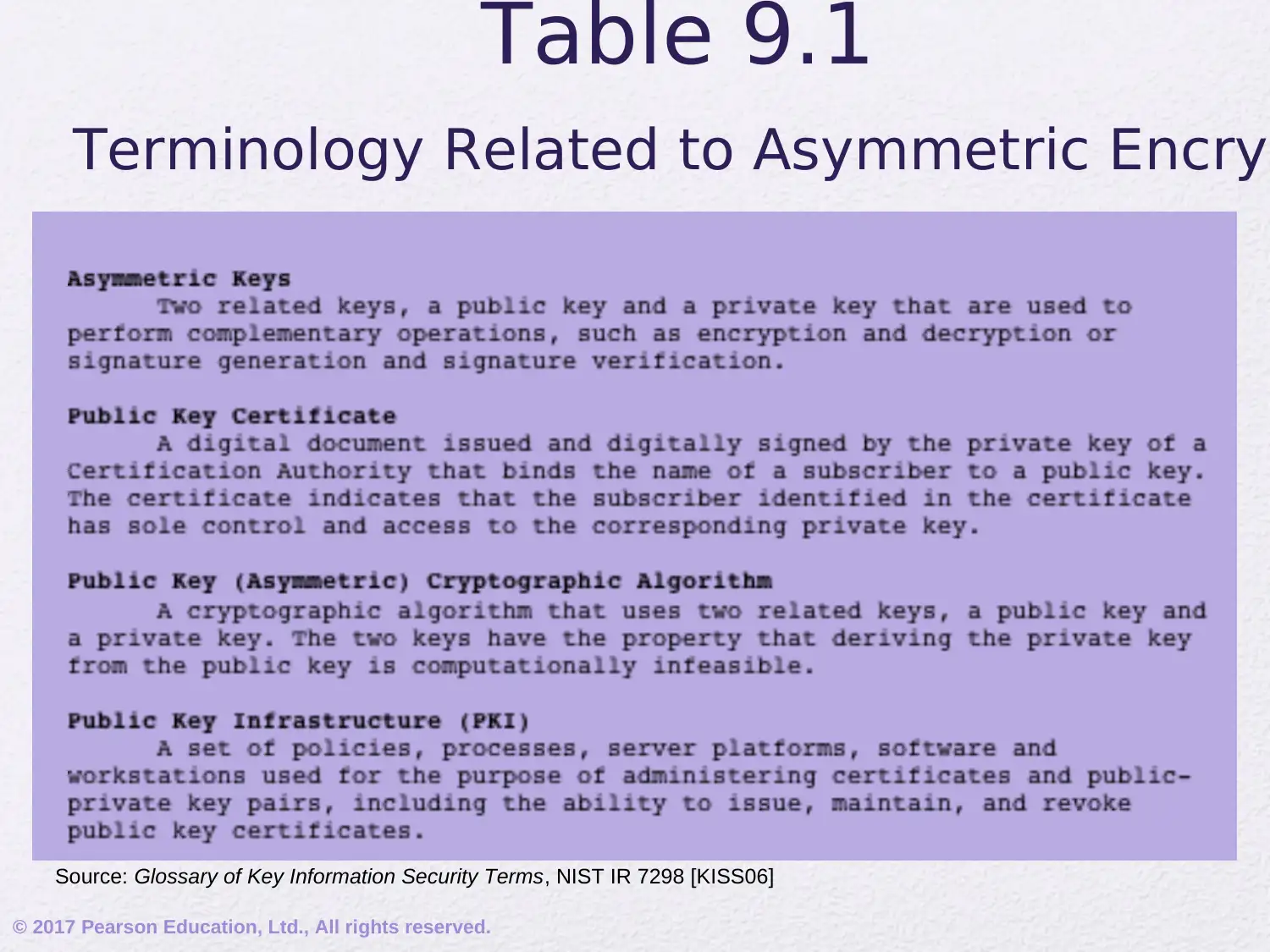
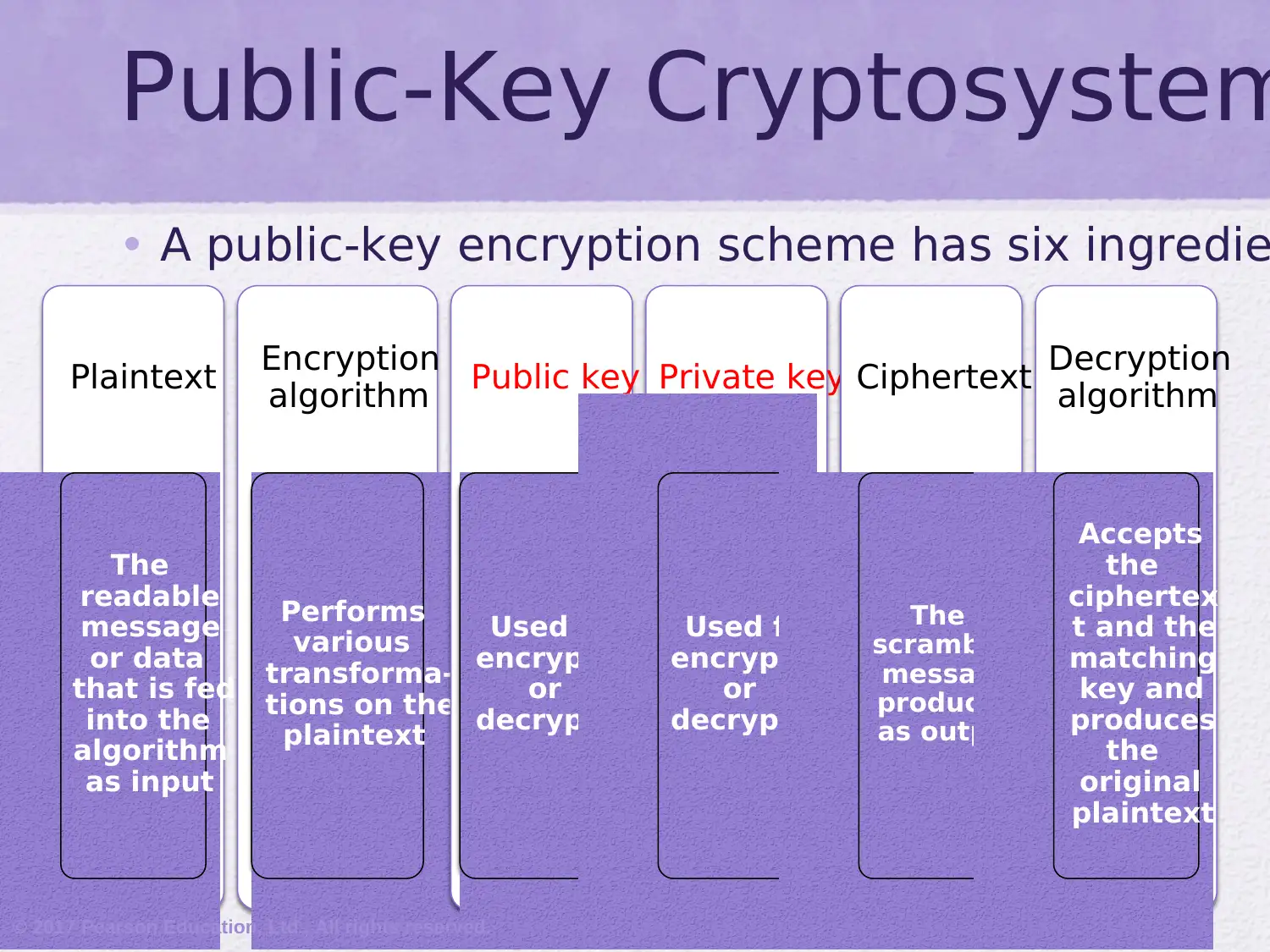
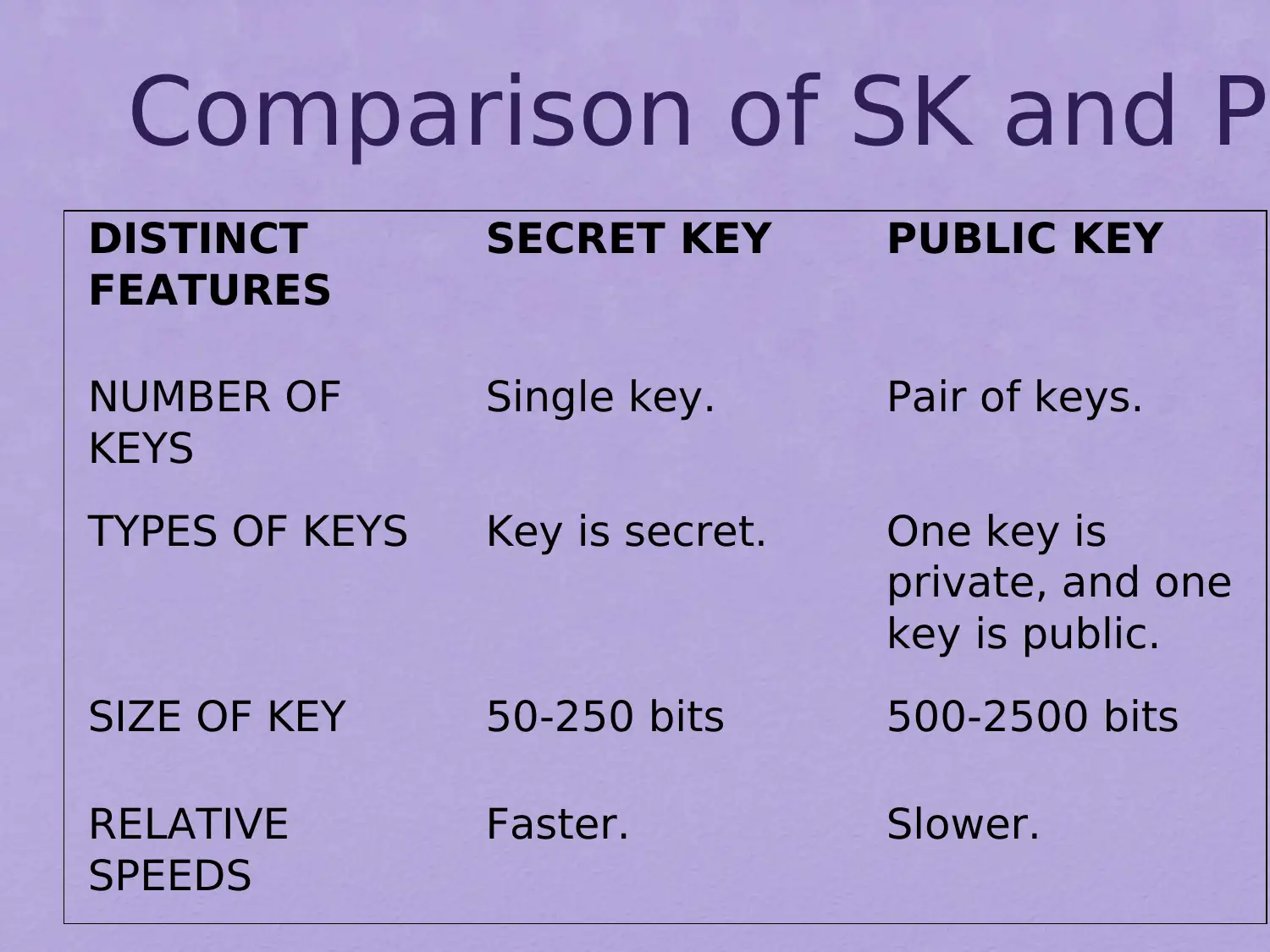
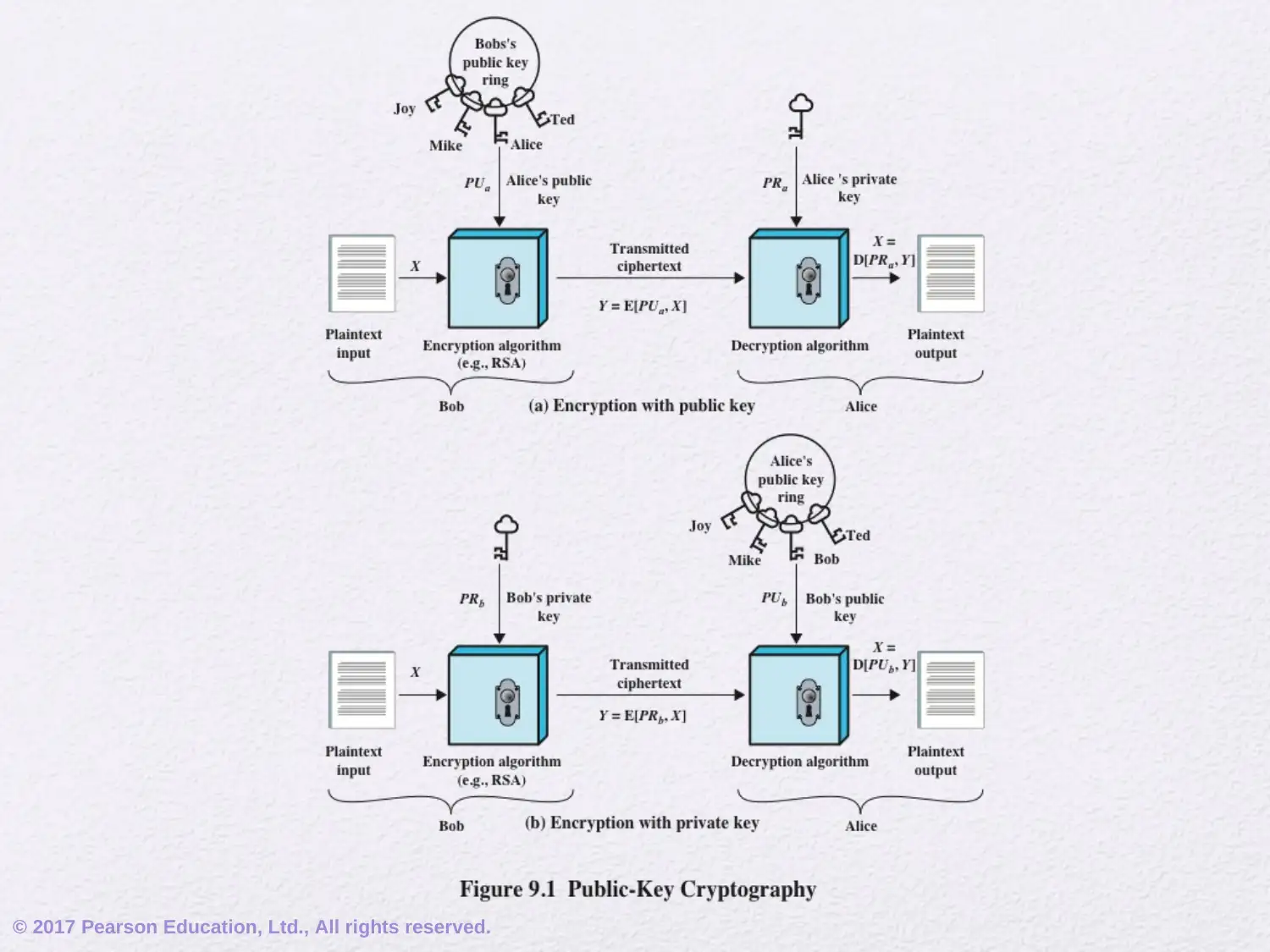
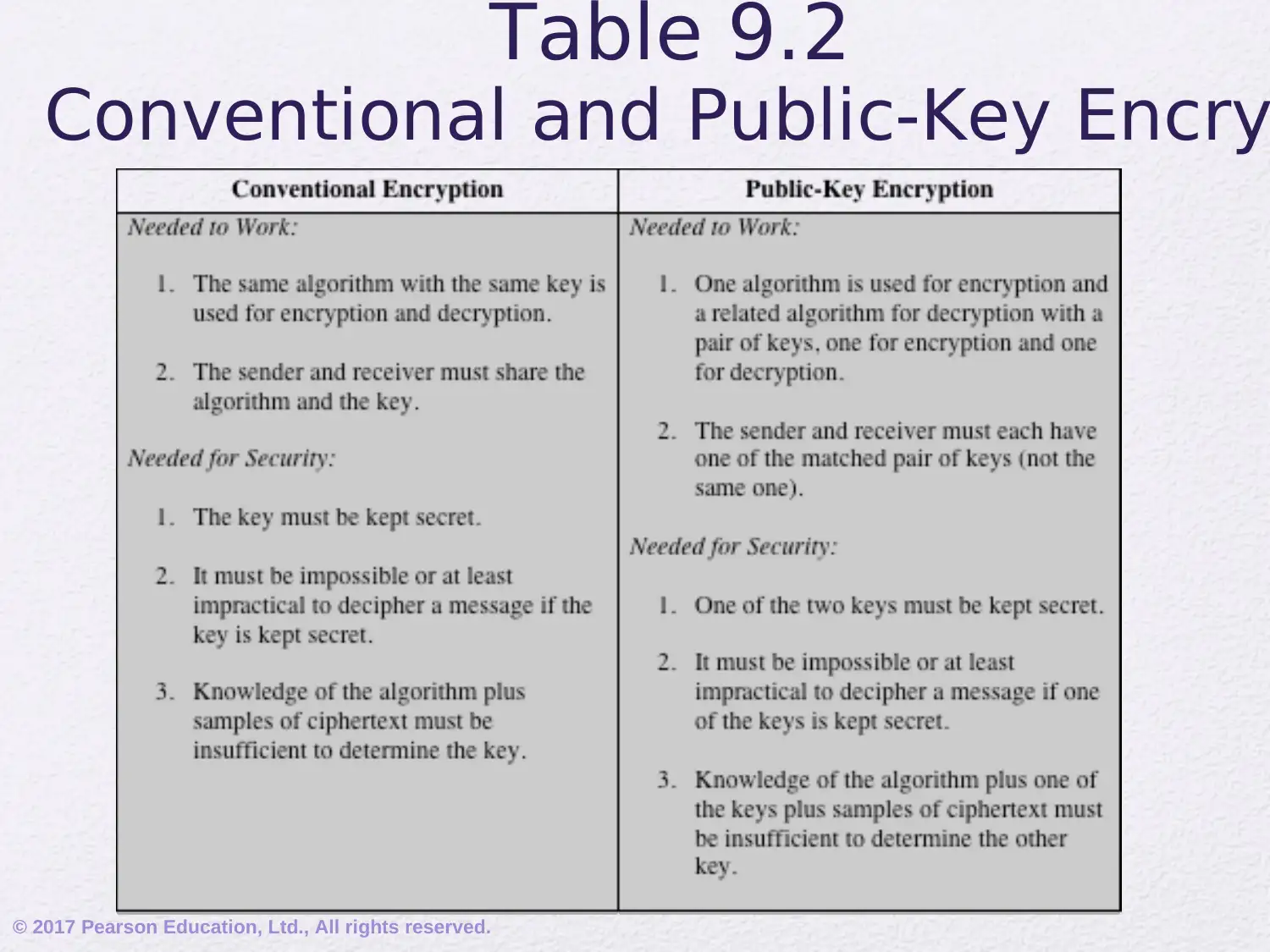
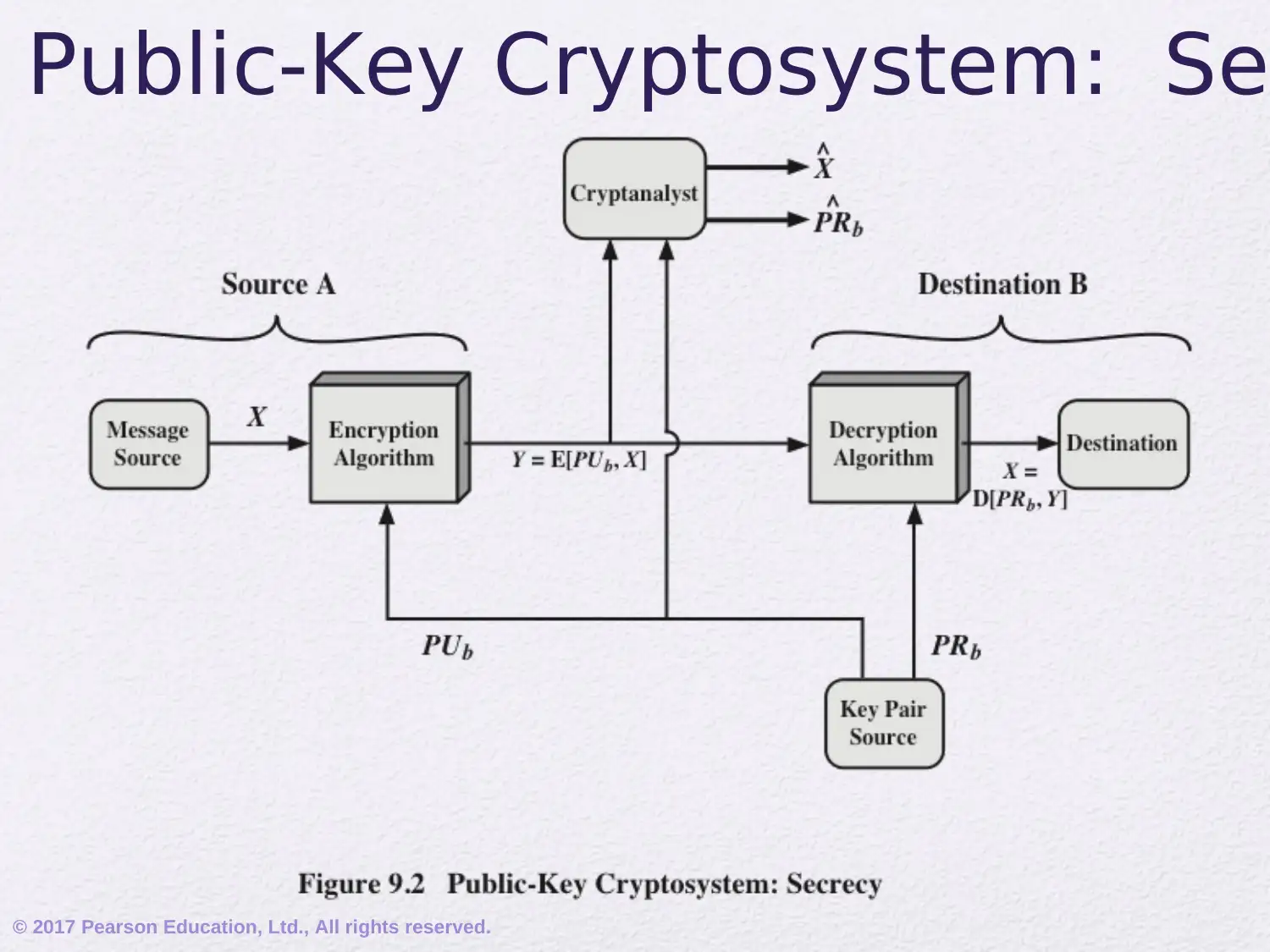
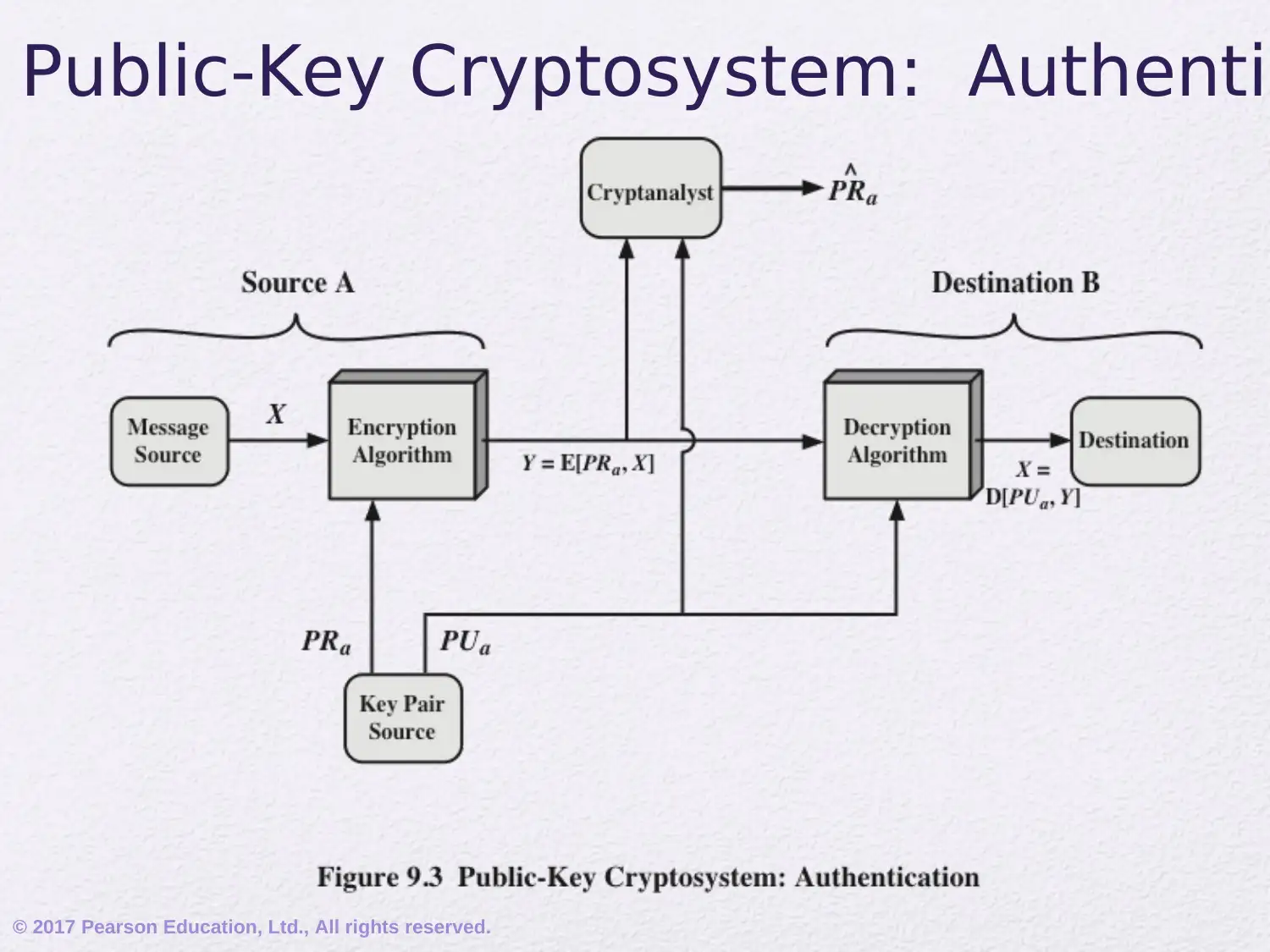
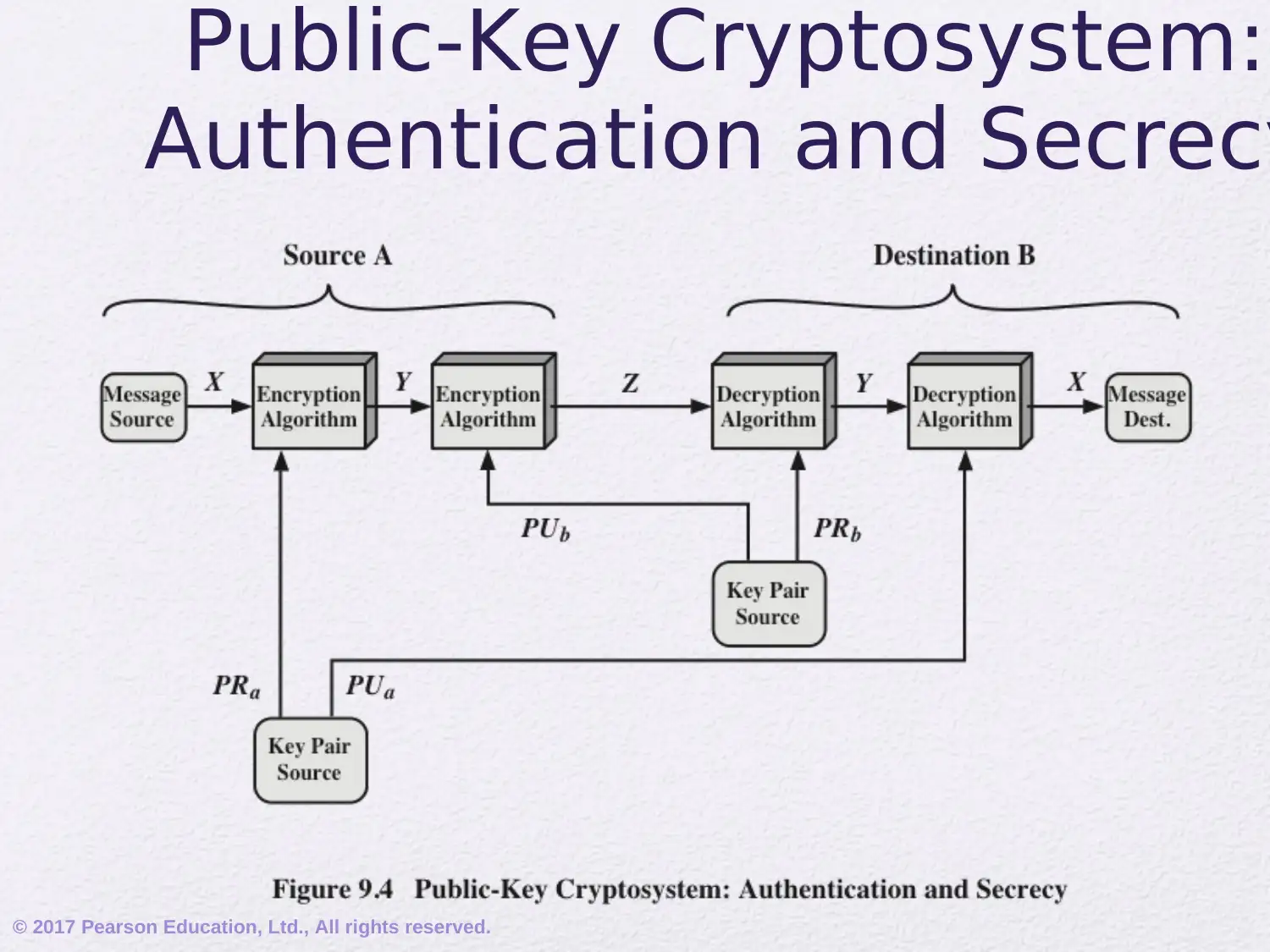
This assignment delves into the realm of public-key cryptography, focusing on the RSA algorithm. It begins by addressing common misconceptions and outlining the principles of public-key cryptosystems, including key distribution and digital signatures. The document elucidates the components of a public-key encryption scheme, differentiating between secret key and public key characteristics, and exploring applications such as encryption/decryption, digital signatures, and key exchange. It also covers the requirements for public-key algorithms, emphasizing the role of trapdoor one-way functions. Furthermore, the assignment provides a detailed exploration of the mathematical ideas underlying RSA, including prime numbers, factorization, the greatest common divisor, modular arithmetic, and Euler's theorem. It then explains the RSA algorithm, its requirements, and provides a worked example, illustrating the encryption and decryption processes. This comprehensive overview provides a solid foundation for understanding the principles and practical applications of public-key cryptography.
1 out of 44









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)