Improving Security: A Project on Python Code Vulnerability Detection
VerifiedAdded on 2022/01/17
|31
|6112
|125
Project
AI Summary
This project delves into the critical domain of software security, specifically focusing on detecting and analyzing vulnerabilities within Python code. The core objective is to identify and evaluate various tools suitable for security testing, encompassing both static and dynamic analysis techniques. The project aims to compare the effectiveness of these tools across different operating systems, namely Linux and Windows, to provide a comprehensive understanding of their capabilities. The methodology involves selecting Python code samples that are known to contain vulnerabilities, and then systematically testing them using the chosen tools. The findings will be presented in an analytical report, detailing the types of vulnerabilities detected, the performance of each tool, and a comparative analysis of the results. Furthermore, the project seeks to propose improvements and potentially design a customized tool based on the insights gained from the evaluation process. The literature review explores existing research on cyberattacks, vulnerability detection, and security testing models, providing a theoretical foundation for the project's practical investigations. The project aims to enhance the security of software development and contribute to the ongoing efforts to mitigate the risks associated with software vulnerabilities.

An Analytical Approach for
Obtaining the Improvised Tool for
Security Testing
Abstract
Obtaining the Improvised Tool for
Security Testing
Abstract
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

List of Figures

List of Tables
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

List of Abbreviations
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser


TABLE OF CONTENTS
Chapter-1 Introduction.......................................................................................................................6
Chapter-2 Literature Review..............................................................................................................6
Chapter-3 Methodology......................................................................................................................6
Chapter-4 Experimental Procedure...................................................................................................6
Chapter-5 Analysis and Result...........................................................................................................6
Chapter-6 Discussion...........................................................................................................................6
Chapter-7 Conclusion..........................................................................................................................6
References............................................................................................................................................6
Chapter-1 Introduction.......................................................................................................................6
Chapter-2 Literature Review..............................................................................................................6
Chapter-3 Methodology......................................................................................................................6
Chapter-4 Experimental Procedure...................................................................................................6
Chapter-5 Analysis and Result...........................................................................................................6
Chapter-6 Discussion...........................................................................................................................6
Chapter-7 Conclusion..........................................................................................................................6
References............................................................................................................................................6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1 CHAPTER-1 INTRODUCTION
In the field of software development, different types of programming languages are used for the
designing of the software. In most cases, the developer chooses such a programming language that is
not open-source. However, not all of those kinds of software are eligible for creating the software.
Thus, in most cases, for the purpose of software development, Java, C and Python are used. This is
because all are eligible for creating the executable files. However, the executable files or software are
mostly sensitive to be attacked by the cybercriminals as for the vulnerability issues in it (Li, 2010).
Thus, after creating or designing software, security and functional testing are done to make sure about
the quality and health of the software.
Generally, open-source code is considered as less secured as it is using the open-source libraries as
well which are developed by some third party who do not disclose the internal operations of those
libraries. This is because, those kinds of codes can be easily hacked by the attackers as they will try to
penetrate into the code surface and will steal all the valuable and confidential information from the
code and server (Jinan et al., 2017). The sensitive issues are found in web frameworks and software
applications. Most of the web framework is done using Java and Python (Flask or Django) which is
open source. The backend of the database is designed based on the required data storage.
Thus, the identification and detection of vulnerability are essential for those software or backend
coding. There are different tools that are available which are used to check the vulnerabilities in a
source code. In this project, some tolls will be identified through which the codes will be tested for
vulnerabilities.
1.1 VULNERABILITIES
Software vulnerabilities in a certain code are the flaws or weaknesses that are present in that code.
These are often caused by the flaw, glitch or weakness that are present in the software through which
the code has been written (Hou et al., 2018). To write and design a sophisticated code, the flaws
thatare the vulnerabilities should be prevented. However, to prevent the code from vulnerabilities, the
reason and behaviour of all of the possible vulnerabilities need to be identified. The finding of the
code vulnerabilities can be done both manually and with the application of tools. However, all of the
vulnerabilities cannot be found through a manual search. Thus, the tools are required through which
the vulnerabilities can be found. There are different vulnerabilities present in Python which is an
In the field of software development, different types of programming languages are used for the
designing of the software. In most cases, the developer chooses such a programming language that is
not open-source. However, not all of those kinds of software are eligible for creating the software.
Thus, in most cases, for the purpose of software development, Java, C and Python are used. This is
because all are eligible for creating the executable files. However, the executable files or software are
mostly sensitive to be attacked by the cybercriminals as for the vulnerability issues in it (Li, 2010).
Thus, after creating or designing software, security and functional testing are done to make sure about
the quality and health of the software.
Generally, open-source code is considered as less secured as it is using the open-source libraries as
well which are developed by some third party who do not disclose the internal operations of those
libraries. This is because, those kinds of codes can be easily hacked by the attackers as they will try to
penetrate into the code surface and will steal all the valuable and confidential information from the
code and server (Jinan et al., 2017). The sensitive issues are found in web frameworks and software
applications. Most of the web framework is done using Java and Python (Flask or Django) which is
open source. The backend of the database is designed based on the required data storage.
Thus, the identification and detection of vulnerability are essential for those software or backend
coding. There are different tools that are available which are used to check the vulnerabilities in a
source code. In this project, some tolls will be identified through which the codes will be tested for
vulnerabilities.
1.1 VULNERABILITIES
Software vulnerabilities in a certain code are the flaws or weaknesses that are present in that code.
These are often caused by the flaw, glitch or weakness that are present in the software through which
the code has been written (Hou et al., 2018). To write and design a sophisticated code, the flaws
thatare the vulnerabilities should be prevented. However, to prevent the code from vulnerabilities, the
reason and behaviour of all of the possible vulnerabilities need to be identified. The finding of the
code vulnerabilities can be done both manually and with the application of tools. However, all of the
vulnerabilities cannot be found through a manual search. Thus, the tools are required through which
the vulnerabilities can be found. There are different vulnerabilities present in Python which is an
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

open-source coding language (Dhivvya et al., 2019). Some of the important vulnerabilities in python
code are listed below:
Insufficient Logging and Monitoring: This is one of the dangerous vulnerabilities which
causes the breach or tampering with the data that are accessed by python and stored in the
backend database.
Injection Flaws: It occurs when untrusted data is sent as part of a command or query to the
remote location or port. The cybercriminals then try to attack by applying the sophisticated
trick to the targeted system using unintended commands (Klyokta et al., 2019).
Sensitive Data Exposure: The flaws regarding credential management like the username and
password will incur a significant loss to the user.
Cross-Site Scripting Flaws: This is a type of risk in the web script through which
cybercriminals use to target a web page and steal all the data from there and create a new web
page. On that new web page, the same content will be replicated which distract the users
(Katole et al., 2018).
Broken Authentication: This is another type of vulnerability through which the user
credentials can be stolen as the code does not provide the integral measure to save the
credentials securely.
1.2 SOFTWARE SYSTEM VULNERABILITIES
<1000 WORDS>
USE THIS LINK FOR REF: https://www.compuquip.com/blog/computer-security-vulnerabilities
1.2.1 Types of Security Vulnerability
Hidden Backdoor Programs
Admin Account Privileges
Automated Running of Scripts
Unknown Security Bugs in Software
code are listed below:
Insufficient Logging and Monitoring: This is one of the dangerous vulnerabilities which
causes the breach or tampering with the data that are accessed by python and stored in the
backend database.
Injection Flaws: It occurs when untrusted data is sent as part of a command or query to the
remote location or port. The cybercriminals then try to attack by applying the sophisticated
trick to the targeted system using unintended commands (Klyokta et al., 2019).
Sensitive Data Exposure: The flaws regarding credential management like the username and
password will incur a significant loss to the user.
Cross-Site Scripting Flaws: This is a type of risk in the web script through which
cybercriminals use to target a web page and steal all the data from there and create a new web
page. On that new web page, the same content will be replicated which distract the users
(Katole et al., 2018).
Broken Authentication: This is another type of vulnerability through which the user
credentials can be stolen as the code does not provide the integral measure to save the
credentials securely.
1.2 SOFTWARE SYSTEM VULNERABILITIES
<1000 WORDS>
USE THIS LINK FOR REF: https://www.compuquip.com/blog/computer-security-vulnerabilities
1.2.1 Types of Security Vulnerability
Hidden Backdoor Programs
Admin Account Privileges
Automated Running of Scripts
Unknown Security Bugs in Software

1.3 AIM AND OBJECTIVES
This dissertation aims to detect the vulnerabilities in a code. In this context, python has been selected
as the coding which will be tested for vulnerabilities. This detection of the vulnerabilities will be done
through the application of tools that will be chosen in this context. To fulfil the aim, the following
objectives have been taken:
1. In this research, primarily some tools will be identified which are used for checking the
source code vulnerabilities. The tools will be chosen such that some of those can work in
Linux operating system and some others will be operated in Windows as well. So, the source
code testing will be done in both two operating systems (Penta et al., 2008).
2. After the choice of tools, the source code will be collected in the domain of Python which
may include the vulnerabilities. This selected code will be checked for vulnerability in those
selected tools.
3. There may be some vulnerability that may not be detected using a certain tool but is detected
using another tool. So, the check for the vulnerability will be done using all of the selected
tools (Zimmermann et al., 2010).
4. Next, the vulnerability will be checked and compared in Windows Operating System and
Linux Operating System (Kanashiro et al., 2017).
5. Finally, the tool will be designed by taking the operating idea of the used tools to detect the
vulnerability of source codes.
With those aims, the project will be conducted with in-depth analysis to check for the vulnerability
and to fix them using multiple tools.
1.4 RESEARCH QUESTIONS
The research questions that have been taken into consideration in this research are:
RQ1:What is the best way to detect security vulnerabilities in source code that is selected to be under
test
RQ2:How to rank software security testing tools from the list of tools selected for research for
selected source code?
RQ3:How can one identify critical types of vulnerabilities in a python written system using static code
analysis?
This dissertation aims to detect the vulnerabilities in a code. In this context, python has been selected
as the coding which will be tested for vulnerabilities. This detection of the vulnerabilities will be done
through the application of tools that will be chosen in this context. To fulfil the aim, the following
objectives have been taken:
1. In this research, primarily some tools will be identified which are used for checking the
source code vulnerabilities. The tools will be chosen such that some of those can work in
Linux operating system and some others will be operated in Windows as well. So, the source
code testing will be done in both two operating systems (Penta et al., 2008).
2. After the choice of tools, the source code will be collected in the domain of Python which
may include the vulnerabilities. This selected code will be checked for vulnerability in those
selected tools.
3. There may be some vulnerability that may not be detected using a certain tool but is detected
using another tool. So, the check for the vulnerability will be done using all of the selected
tools (Zimmermann et al., 2010).
4. Next, the vulnerability will be checked and compared in Windows Operating System and
Linux Operating System (Kanashiro et al., 2017).
5. Finally, the tool will be designed by taking the operating idea of the used tools to detect the
vulnerability of source codes.
With those aims, the project will be conducted with in-depth analysis to check for the vulnerability
and to fix them using multiple tools.
1.4 RESEARCH QUESTIONS
The research questions that have been taken into consideration in this research are:
RQ1:What is the best way to detect security vulnerabilities in source code that is selected to be under
test
RQ2:How to rank software security testing tools from the list of tools selected for research for
selected source code?
RQ3:How can one identify critical types of vulnerabilities in a python written system using static code
analysis?
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2 CHAPTER-2 LITERATURE REVIEW
as stated by (Núñez et al., 2020), a large number of cyberattacks happen each day. The
disclosure of weak systems accelerates the spread of computer assaults with catastrophic
repercussions, mainly when directed at critical infrastructures, industrial activities, or Internet
of Things devices. Traditional software development methods take a proactive strategy,
delegating security tasks to the later phases of the programme life cycle. Nonetheless,
software development models should incorporate functionality as well as aggressive
responses to security issues. Such techniques take into account security operations that span
the entire software development phase. The figure below compares all of the models'
commonalities and contrasts using a Venn Euler diagram.
as stated by (Núñez et al., 2020), a large number of cyberattacks happen each day. The
disclosure of weak systems accelerates the spread of computer assaults with catastrophic
repercussions, mainly when directed at critical infrastructures, industrial activities, or Internet
of Things devices. Traditional software development methods take a proactive strategy,
delegating security tasks to the later phases of the programme life cycle. Nonetheless,
software development models should incorporate functionality as well as aggressive
responses to security issues. Such techniques take into account security operations that span
the entire software development phase. The figure below compares all of the models'
commonalities and contrasts using a Venn Euler diagram.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
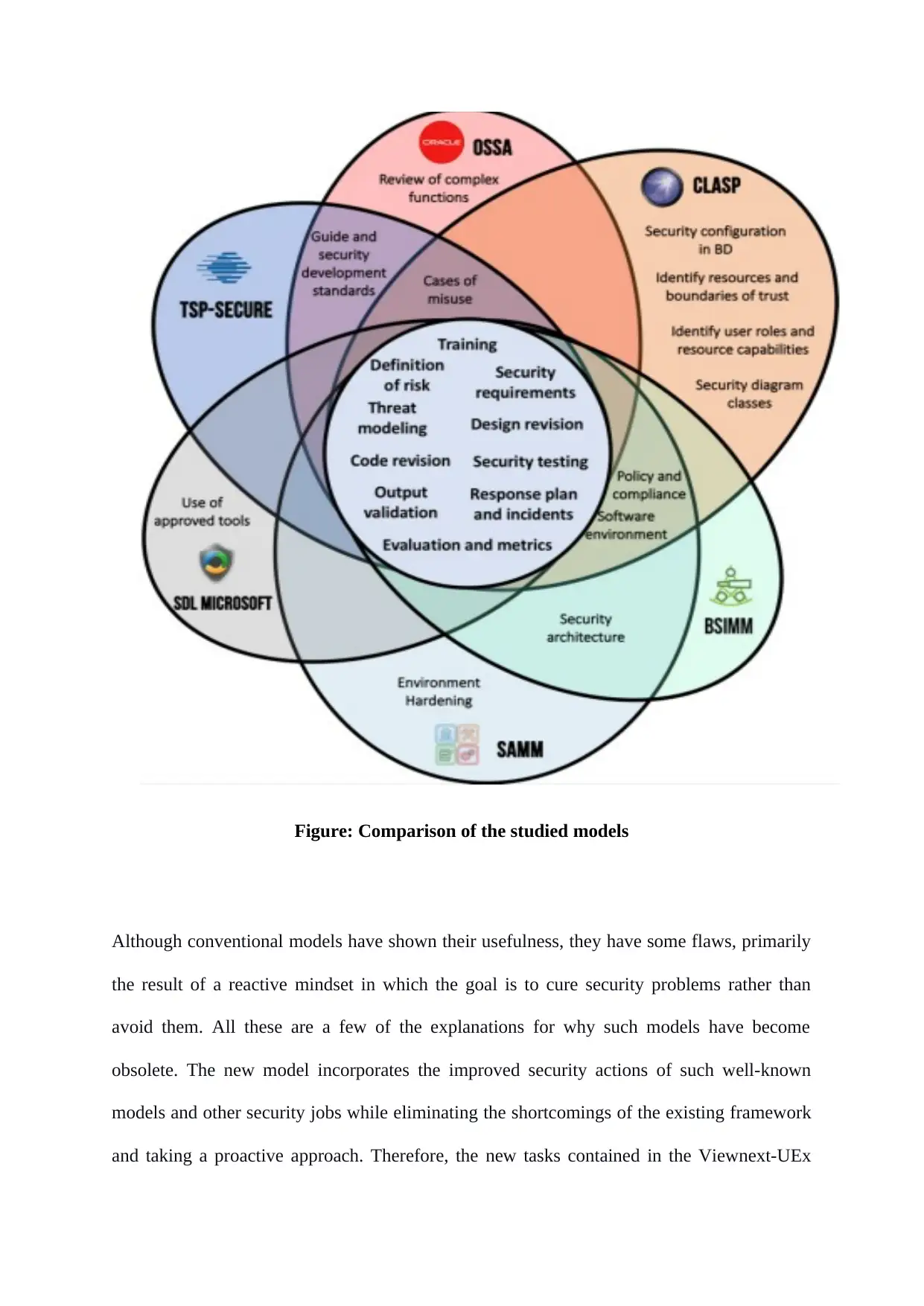
Figure: Comparison of the studied models
Although conventional models have shown their usefulness, they have some flaws, primarily
the result of a reactive mindset in which the goal is to cure security problems rather than
avoid them. All these are a few of the explanations for why such models have become
obsolete. The new model incorporates the improved security actions of such well-known
models and other security jobs while eliminating the shortcomings of the existing framework
and taking a proactive approach. Therefore, the new tasks contained in the Viewnext-UEx
Although conventional models have shown their usefulness, they have some flaws, primarily
the result of a reactive mindset in which the goal is to cure security problems rather than
avoid them. All these are a few of the explanations for why such models have become
obsolete. The new model incorporates the improved security actions of such well-known
models and other security jobs while eliminating the shortcomings of the existing framework
and taking a proactive approach. Therefore, the new tasks contained in the Viewnext-UEx

model allow for the avoidance of weaknesses, the performance of empirical reporting, and
the tracking of the software's security state mostly during the development phase. The
Viewnext-UEx model has been validated using real-world data. According to the research
study, the amount of identified weaknesses has decreased by 66percent. Vulnerabilities' risk
level is also significantly reduced. This results in noticeable cost savings and delays, which
are especially apparent in the later development stages. The security and reliability of
programming are improved, as is development efficiency.
As stated by (Al-Zahrani, 2020), the reason for the continuously growing data thefts is a lack
of available security forces in software nowadays. Regrettably, more significant ICT usage
has resulted in an unprecedented surge in security breaches and information pilferage.
People's and organisations' digital (data) resources are incredibly vulnerable. The rising use
of switches as well as other electronic objects, as well as the abundance of digital information
flow, has dramatically enhanced usable-security requirements. In real-world problems, fuzzy
logic is instrumental, especially when we cannot determine whether a given approach is
absolutely legitimate or completely untrue. Fuzzy logic is similar to human thinking and
effectively overcomes inaccuracies and uncertainty in decision-making. An analysis of
previous high-quality research articles and other trustworthy reliable sources can be used for
attribute identification and choosing for usable-security evaluations for healthcare
management system apps.
the tracking of the software's security state mostly during the development phase. The
Viewnext-UEx model has been validated using real-world data. According to the research
study, the amount of identified weaknesses has decreased by 66percent. Vulnerabilities' risk
level is also significantly reduced. This results in noticeable cost savings and delays, which
are especially apparent in the later development stages. The security and reliability of
programming are improved, as is development efficiency.
As stated by (Al-Zahrani, 2020), the reason for the continuously growing data thefts is a lack
of available security forces in software nowadays. Regrettably, more significant ICT usage
has resulted in an unprecedented surge in security breaches and information pilferage.
People's and organisations' digital (data) resources are incredibly vulnerable. The rising use
of switches as well as other electronic objects, as well as the abundance of digital information
flow, has dramatically enhanced usable-security requirements. In real-world problems, fuzzy
logic is instrumental, especially when we cannot determine whether a given approach is
absolutely legitimate or completely untrue. Fuzzy logic is similar to human thinking and
effectively overcomes inaccuracies and uncertainty in decision-making. An analysis of
previous high-quality research articles and other trustworthy reliable sources can be used for
attribute identification and choosing for usable-security evaluations for healthcare
management system apps.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 31
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





