Analysis and Implementation of Rail Fence Cipher Algorithm
VerifiedAdded on 2019/09/25
|3
|454
|342
Homework Assignment
AI Summary
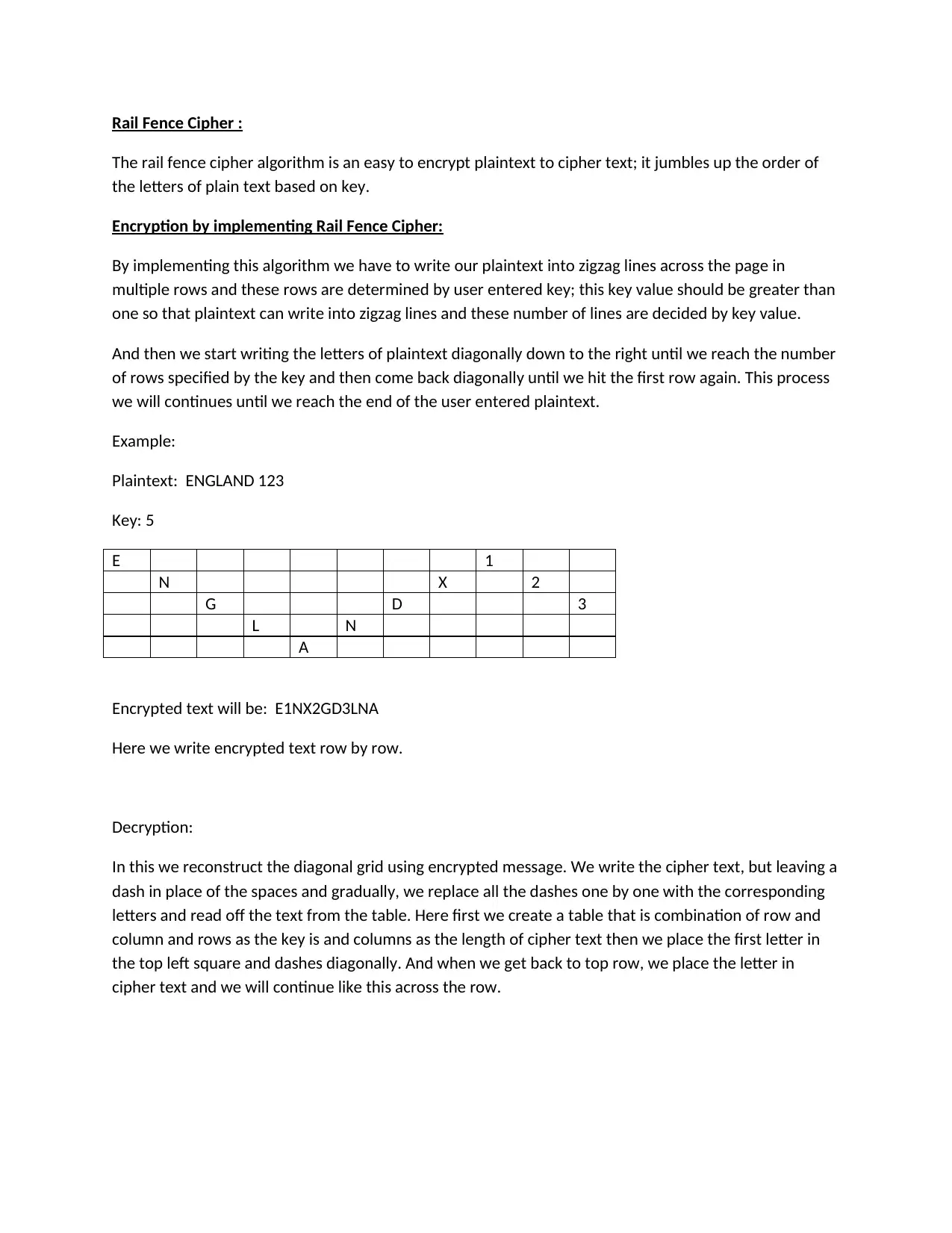
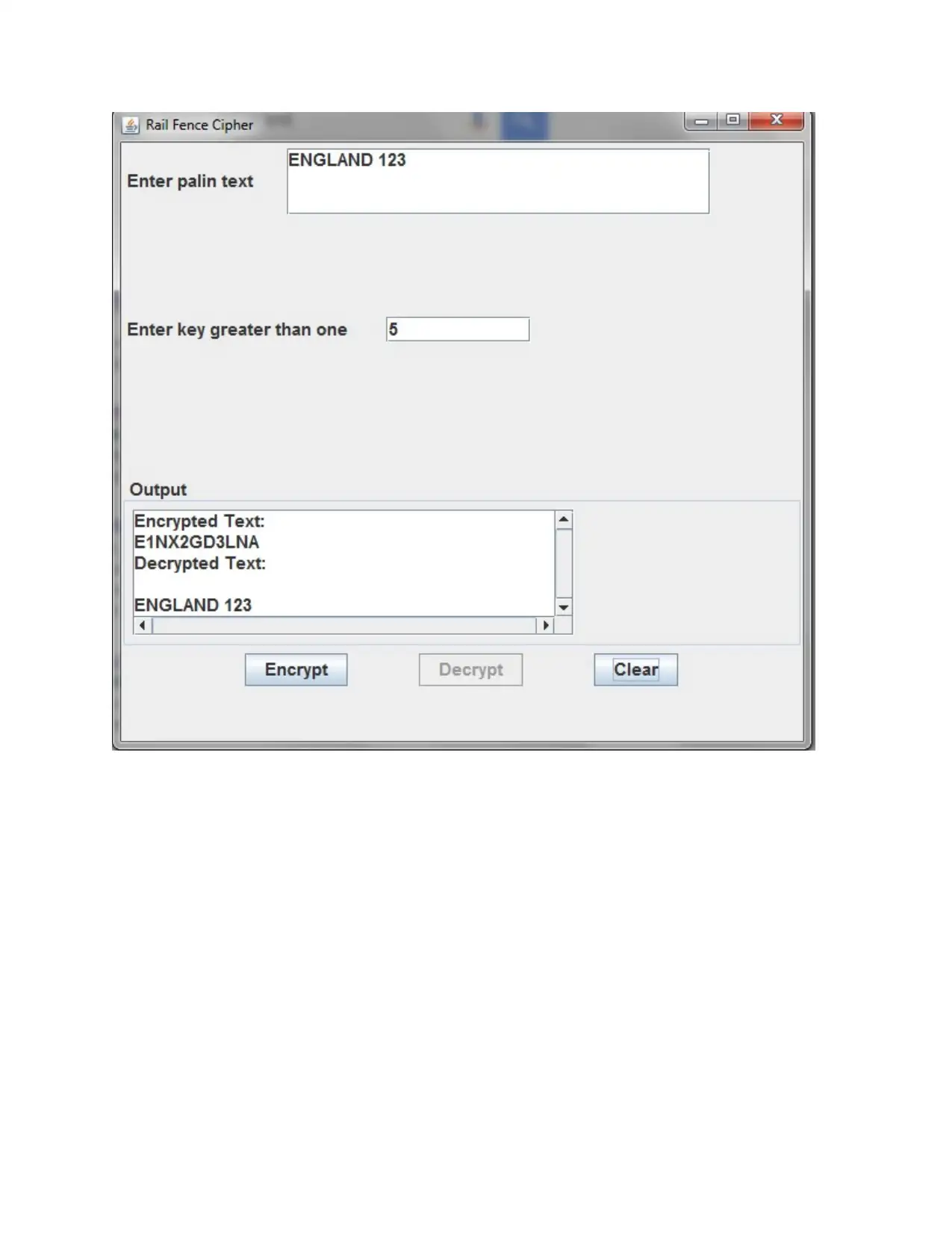
This document details the implementation of the Rail Fence Cipher algorithm. The solution explains the encryption process, which involves writing the plaintext in a zigzag pattern based on a key value, and the decryption process, which reconstructs the original text from the ciphertext. The assignment covers how to implement the algorithm, including the creation of a table to arrange the characters. The document also highlights the weaknesses of the Rail Fence Cipher, such as its limited key space and vulnerability to attacks, making it unsuitable for secure communication. The document provides the necessary details to understand the practical application of the algorithm and its limitations in cryptography.
1 out of 3








![[object Object]](/_next/static/media/star-bottom.7253800d.svg)