Comprehensive Analysis of Ransomware Attacks and Prevention
VerifiedAdded on 2023/06/14
|139
|30604
|56
Report
AI Summary
This report presents an analysis of ransomware, a type of malware that encrypts files and demands a ransom for their release. It discusses the impact of ransomware attacks, particularly focusing on the WannaCry attack, which affected various sectors globally. The report explores methodologies for detecting and mitigating ransomware, including sandbox approaches, VMware, and reverse engineering using IDA Pro. It also differentiates between static and dynamic analysis in malware detection and outlines preventive measures and risk mitigation techniques to combat ransomware threats. The document concludes with suggestions and solutions to enhance cybersecurity and protect against future attacks, emphasizing the importance of proactive measures and continuous monitoring.
ANALYSIS OF RANSOMWARE
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Abstract
In our world internet is the basic need for everyone to access the mobile phones, computers,
PDA’s, etc… With the help of this internet people can easily communicated with everyone and it
is an easy way to access the information. Internet provides more flexible, availability and speed.
But with the help of this internet many viruses will be created and it is easily affect our systems.
One of the most vulnerable virus called Ransomware. It would threaten the people, international
companies and many of the internet browsers in the year 2017.But now there are many solutions
to detect this virus. Here the analysis of ransomware will be performed. Ransomware is a
malware function that will affect our documents that are stored in our system. This malware will
be created by some network browsers and spread this virus in to other systems through
communications. It will affect the entire system manually. It is also called as the cyber-attack by
using WannaCry. This ransomware WannaCry affects fields like telecommunication, gas,
government, healthcare and financial. This type malware functions first encrypt our files in the
system. And then it demand the user to release those files. Here we will use some of the
methodologies for impact rejection from the external sources. The methodologies that are used
here was Sandbox approach, VMware, Reverse Engineering. Sandbox approach will used to
reject impacts from the external sources. The main goal of this approach is to provide more
visibility and scalability. And it also used to detect this malware. The second methodology that
will be used here was VMware. It is used to work with the software without any modification. It
is a cloud computing software and it is used to provide an virtualization software. VMware
provides many features when compared to Microsoft’s virtual software. VMware is mainly used
to provide security. The third methodology that are used here was Reverse Engineering with IDA
Pro. RE is a systematic approach. It is used to analyze the design of existing devices or systems.
There are three basic steps to perform reverse engineering. That are Encryptor, Static Analysis
and Dynamic analysis. Most of the virus programmers use this methodology for software design.
This method will mainly used to identify the malware that infect our systems are not. The
analysis of this malware is used to preventing the issues. Here different types of analysis will be
used to analyze this malware. That are code analysis and behavioral analysis. This both methods
are used to confirm whether the file is malicious are not.
1
In our world internet is the basic need for everyone to access the mobile phones, computers,
PDA’s, etc… With the help of this internet people can easily communicated with everyone and it
is an easy way to access the information. Internet provides more flexible, availability and speed.
But with the help of this internet many viruses will be created and it is easily affect our systems.
One of the most vulnerable virus called Ransomware. It would threaten the people, international
companies and many of the internet browsers in the year 2017.But now there are many solutions
to detect this virus. Here the analysis of ransomware will be performed. Ransomware is a
malware function that will affect our documents that are stored in our system. This malware will
be created by some network browsers and spread this virus in to other systems through
communications. It will affect the entire system manually. It is also called as the cyber-attack by
using WannaCry. This ransomware WannaCry affects fields like telecommunication, gas,
government, healthcare and financial. This type malware functions first encrypt our files in the
system. And then it demand the user to release those files. Here we will use some of the
methodologies for impact rejection from the external sources. The methodologies that are used
here was Sandbox approach, VMware, Reverse Engineering. Sandbox approach will used to
reject impacts from the external sources. The main goal of this approach is to provide more
visibility and scalability. And it also used to detect this malware. The second methodology that
will be used here was VMware. It is used to work with the software without any modification. It
is a cloud computing software and it is used to provide an virtualization software. VMware
provides many features when compared to Microsoft’s virtual software. VMware is mainly used
to provide security. The third methodology that are used here was Reverse Engineering with IDA
Pro. RE is a systematic approach. It is used to analyze the design of existing devices or systems.
There are three basic steps to perform reverse engineering. That are Encryptor, Static Analysis
and Dynamic analysis. Most of the virus programmers use this methodology for software design.
This method will mainly used to identify the malware that infect our systems are not. The
analysis of this malware is used to preventing the issues. Here different types of analysis will be
used to analyze this malware. That are code analysis and behavioral analysis. This both methods
are used to confirm whether the file is malicious are not.
1

Table of Contents
1. Induction.............................................................................................................................................3
2. Literature Review................................................................................................................................6
3. Overview of Ransomware attack.......................................................................................................14
4. Wannacry..........................................................................................................................................16
5. Methodology.....................................................................................................................................17
6. Vmware.............................................................................................................................................27
7. Reverse Engineering..........................................................................................................................43
8. Operations of IDA Pro:.......................................................................................................................46
9. The Reverse Engineering process......................................................................................................50
10. ANALAYSIS OF MALWARE (Wannacry)..........................................................................................66
11. DIFFERENCE BETWEEN STATIC AND DYNAMIC ANALYSIS..............................................................70
12. Elements of the Malware..............................................................................................................73
13. Analysis of Wannacry.....................................................................................................................73
14. WannaCry analysis with IDA Pro....................................................................................................92
15. Ransomware Attack.....................................................................................................................109
16. Ransomware attack handling steps.............................................................................................111
17. Findings and Impact.....................................................................................................................113
18. Impacts of Ransomware attack....................................................................................................119
19. Risk Mitigation techniques..........................................................................................................120
20. Preventive measures:..................................................................................................................121
21. Forward look against Wannacry..................................................................................................122
22. Suggestion and Solutions.............................................................................................................122
23. Conclusion...................................................................................................................................125
24. References...................................................................................................................................128
2
1. Induction.............................................................................................................................................3
2. Literature Review................................................................................................................................6
3. Overview of Ransomware attack.......................................................................................................14
4. Wannacry..........................................................................................................................................16
5. Methodology.....................................................................................................................................17
6. Vmware.............................................................................................................................................27
7. Reverse Engineering..........................................................................................................................43
8. Operations of IDA Pro:.......................................................................................................................46
9. The Reverse Engineering process......................................................................................................50
10. ANALAYSIS OF MALWARE (Wannacry)..........................................................................................66
11. DIFFERENCE BETWEEN STATIC AND DYNAMIC ANALYSIS..............................................................70
12. Elements of the Malware..............................................................................................................73
13. Analysis of Wannacry.....................................................................................................................73
14. WannaCry analysis with IDA Pro....................................................................................................92
15. Ransomware Attack.....................................................................................................................109
16. Ransomware attack handling steps.............................................................................................111
17. Findings and Impact.....................................................................................................................113
18. Impacts of Ransomware attack....................................................................................................119
19. Risk Mitigation techniques..........................................................................................................120
20. Preventive measures:..................................................................................................................121
21. Forward look against Wannacry..................................................................................................122
22. Suggestion and Solutions.............................................................................................................122
23. Conclusion...................................................................................................................................125
24. References...................................................................................................................................128
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1. Induction
Now a days, many electronic devices are used in our daily life. For human, computer is the most
important electronic device. The computer is designed for work. That work is done by
information. Latin word for computer is 'computare'. The meaning of computare is performing
calculating machine. Without the help of programming, computer is nothing can do. Computer
language is full of binary numbers. It converts the decimal values into binary numbers. Central
processing Unit is a brain of the computer. The five generation of computer is briefly explained.
The first generation is vacuum tubes which is used in the time period 1940 to 1956. It may takes
to perform operations for many days. The input devices for first generation computer is punched
cards and paper tapes and output is printouts. The second generation is Transistors which is used
in time period 1956 to 1963. Transistor can make the computer cheaper, smaller, more energy
efficient and faster compared to Vacuum tubes. Punch card is used for internet and printout is
used for outputs. Integrated circuits is the third generation which is used in period of 1964 to
1971. For input keyboard is used. The output device is monitor is used. Fourth generation
computer is developed by microprocessor which is in the time period of 1971 to at present. In
this generation we are using microprocessor we can insert thousands of Integrated circuits. The
fifth generation is artificial intelligence. The time period is present and beyond. Here we can use
voice recognition.
The computer can be classified into 6 types. They are Personal computer, minicomputer,
microcomputer, mainframe, analog computer and workstation. Analog computer is represented
by only numbers. Personal computer is low cost and size is small. Minicomputer is not in small
size. Microcomputer is our personal computer (An Analysis and Averstion Of Highly Servivable
Ransomware, 2017). Mainframe is large size computer which is used to run Full Corporation.
And finally workstation is a client side computer. Computer can takes an input like numbers,
words etc. i.e. data and that data can be processing under some instruction set and produce the
output i.e. results. For future use, the output can be saved. The computer can perform both
arithmetical, numerical and logical calculations. The main usage of computer is email sending,
surfing in internet, document typing and gaming. We can create or alter the videos, spreadsheets
3
Now a days, many electronic devices are used in our daily life. For human, computer is the most
important electronic device. The computer is designed for work. That work is done by
information. Latin word for computer is 'computare'. The meaning of computare is performing
calculating machine. Without the help of programming, computer is nothing can do. Computer
language is full of binary numbers. It converts the decimal values into binary numbers. Central
processing Unit is a brain of the computer. The five generation of computer is briefly explained.
The first generation is vacuum tubes which is used in the time period 1940 to 1956. It may takes
to perform operations for many days. The input devices for first generation computer is punched
cards and paper tapes and output is printouts. The second generation is Transistors which is used
in time period 1956 to 1963. Transistor can make the computer cheaper, smaller, more energy
efficient and faster compared to Vacuum tubes. Punch card is used for internet and printout is
used for outputs. Integrated circuits is the third generation which is used in period of 1964 to
1971. For input keyboard is used. The output device is monitor is used. Fourth generation
computer is developed by microprocessor which is in the time period of 1971 to at present. In
this generation we are using microprocessor we can insert thousands of Integrated circuits. The
fifth generation is artificial intelligence. The time period is present and beyond. Here we can use
voice recognition.
The computer can be classified into 6 types. They are Personal computer, minicomputer,
microcomputer, mainframe, analog computer and workstation. Analog computer is represented
by only numbers. Personal computer is low cost and size is small. Minicomputer is not in small
size. Microcomputer is our personal computer (An Analysis and Averstion Of Highly Servivable
Ransomware, 2017). Mainframe is large size computer which is used to run Full Corporation.
And finally workstation is a client side computer. Computer can takes an input like numbers,
words etc. i.e. data and that data can be processing under some instruction set and produce the
output i.e. results. For future use, the output can be saved. The computer can perform both
arithmetical, numerical and logical calculations. The main usage of computer is email sending,
surfing in internet, document typing and gaming. We can create or alter the videos, spreadsheets
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

and presentations. Now a days, human are using internet with the help of computer and mobile
phones. Internet is the largest computer network that uses Internet protocol (IP/TCP) to link
various devices and it is the system of computer networks that connected each other. It is
considered as an inexpensive and effective communication way. It has various networks that
includes public, private, business and academic that are linked with the help of wireless, optical
networking and electronic technologies. In general internet provides various services such as
telephony, file sharing and electronic mail and it is also used to carry lot of information services
and resources. ARPANET, the primary network which connects military and academic networks.
The main usage of internet is it is widely used for academic and commercial purpose.
The service such as internet telephony, digital newspaper, online music, video streaming can be
achieved by redefining, reshaping process of information gathered from paper mail, radio,
newspapers and telephony. Internet forums, social messaging and instant messaging are the new
services which is used to improve interactions between peoples. The service provided by the
internet in the business sector is online shopping, financial services and business to business
service. It is defined by connecting millions of computers with various networks. It is easily
possible to create an account in ISP. Then the user can have the service such as chatting,
searching and e-mail services. The key advantages of internet is easy access of information. It is
possible for the client to get information easily by searching the internet, regarding the product
and they can check at any part of the day. The main features of internet are simple to use,
secured one, resource can be shared easily, flexible for communication, speed and availability,
economic simplicity and secured one. The various services provided by the internet is social
networking media, electronic mail, file transfer protocol, searching, net news, telnet, use net and
online chat.
Ransomware is one of the malware used to intimidate the data and the system is to be block by a
humble ransomware it not challenging for to recover the file, but progressive malware technique
is scramble all the file and is not be accessible. It occurrence with help of Trojan file which mean
spiteful processer program. When operator sweeping or moving that file it will robotically come
to email and it will access the computer to encrypt the file without any contact with operator. At
4
phones. Internet is the largest computer network that uses Internet protocol (IP/TCP) to link
various devices and it is the system of computer networks that connected each other. It is
considered as an inexpensive and effective communication way. It has various networks that
includes public, private, business and academic that are linked with the help of wireless, optical
networking and electronic technologies. In general internet provides various services such as
telephony, file sharing and electronic mail and it is also used to carry lot of information services
and resources. ARPANET, the primary network which connects military and academic networks.
The main usage of internet is it is widely used for academic and commercial purpose.
The service such as internet telephony, digital newspaper, online music, video streaming can be
achieved by redefining, reshaping process of information gathered from paper mail, radio,
newspapers and telephony. Internet forums, social messaging and instant messaging are the new
services which is used to improve interactions between peoples. The service provided by the
internet in the business sector is online shopping, financial services and business to business
service. It is defined by connecting millions of computers with various networks. It is easily
possible to create an account in ISP. Then the user can have the service such as chatting,
searching and e-mail services. The key advantages of internet is easy access of information. It is
possible for the client to get information easily by searching the internet, regarding the product
and they can check at any part of the day. The main features of internet are simple to use,
secured one, resource can be shared easily, flexible for communication, speed and availability,
economic simplicity and secured one. The various services provided by the internet is social
networking media, electronic mail, file transfer protocol, searching, net news, telnet, use net and
online chat.
Ransomware is one of the malware used to intimidate the data and the system is to be block by a
humble ransomware it not challenging for to recover the file, but progressive malware technique
is scramble all the file and is not be accessible. It occurrence with help of Trojan file which mean
spiteful processer program. When operator sweeping or moving that file it will robotically come
to email and it will access the computer to encrypt the file without any contact with operator. At
4

the year of two thousand twelve this malware cheats can be developed internationally. The
advanced malware of extortion is having three procedure between enemies and target that is,
To release the malware vital is to be placed for necessary target and that vital is generated only
by the attacker. To encrypt the data with help of symmetric vital that is called mixture encryption
and it tips to minor occurrence. In this we recover the records with augmented persons.
The compensation conventional from the invader to activate the symmetric code to encrypt the
file and their by completion of occurrence. Without symmetric vital it not possible to access the
target details. The vital exposed only the target should generate that until it will not access. If
generate a small empty message will send to invader and then encrypted starts. It possible to
encrypted personal data and also details. First it distress the main server and then it take control.
If all data will encrypt it request the compensation to decrypt the data. The invader not get any
expense the intimidate data will be demolished. These malware are extent with help of email
messages or any file or buried in any word file. And also through way of inferior infection or if
computer previously attacked by any worm then it leads to further attacks. In this malware
occurrence also mobile, for her it will first to encrypt the android boards. But it can be simply
returned data by method of online harmonization. Here it will be in form of apk file. The law
administration assistance requested that what reason for attacking of ransomware is that using
the processer in unlawful actions and downloading the abandoned software. For this action law
enforcement introduced a new system to tracking the all computer and all activity should be
recorded. If this malware attack your system, first you have to backup the all file and folder and
then clean the computer, if advanced malware means the recovery is not possible. After the
payment file there is ten percent to recover the file, that regarding to invader action. The main
thing of this malware is to make a deal of payment.
5
advanced malware of extortion is having three procedure between enemies and target that is,
To release the malware vital is to be placed for necessary target and that vital is generated only
by the attacker. To encrypt the data with help of symmetric vital that is called mixture encryption
and it tips to minor occurrence. In this we recover the records with augmented persons.
The compensation conventional from the invader to activate the symmetric code to encrypt the
file and their by completion of occurrence. Without symmetric vital it not possible to access the
target details. The vital exposed only the target should generate that until it will not access. If
generate a small empty message will send to invader and then encrypted starts. It possible to
encrypted personal data and also details. First it distress the main server and then it take control.
If all data will encrypt it request the compensation to decrypt the data. The invader not get any
expense the intimidate data will be demolished. These malware are extent with help of email
messages or any file or buried in any word file. And also through way of inferior infection or if
computer previously attacked by any worm then it leads to further attacks. In this malware
occurrence also mobile, for her it will first to encrypt the android boards. But it can be simply
returned data by method of online harmonization. Here it will be in form of apk file. The law
administration assistance requested that what reason for attacking of ransomware is that using
the processer in unlawful actions and downloading the abandoned software. For this action law
enforcement introduced a new system to tracking the all computer and all activity should be
recorded. If this malware attack your system, first you have to backup the all file and folder and
then clean the computer, if advanced malware means the recovery is not possible. After the
payment file there is ten percent to recover the file, that regarding to invader action. The main
thing of this malware is to make a deal of payment.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
2. Literature Review
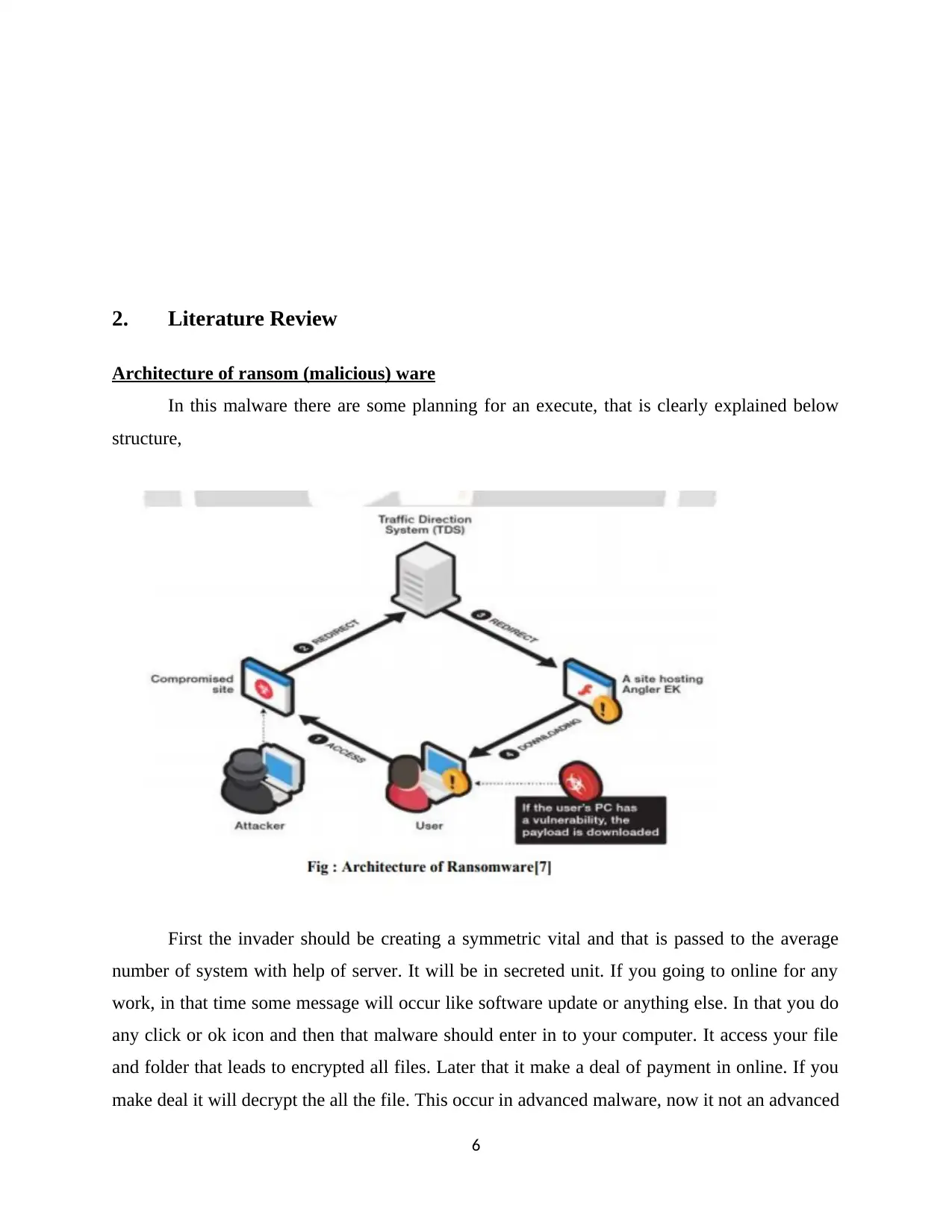
Architecture of ransom (malicious) ware
In this malware there are some planning for an execute, that is clearly explained below
structure,
First the invader should be creating a symmetric vital and that is passed to the average
number of system with help of server. It will be in secreted unit. If you going to online for any
work, in that time some message will occur like software update or anything else. In that you do
any click or ok icon and then that malware should enter in to your computer. It access your file
and folder that leads to encrypted all files. Later that it make a deal of payment in online. If you
make deal it will decrypt the all the file. This occur in advanced malware, now it not an advanced
6
Architecture of ransom (malicious) ware
In this malware there are some planning for an execute, that is clearly explained below
structure,
First the invader should be creating a symmetric vital and that is passed to the average
number of system with help of server. It will be in secreted unit. If you going to online for any
work, in that time some message will occur like software update or anything else. In that you do
any click or ok icon and then that malware should enter in to your computer. It access your file
and folder that leads to encrypted all files. Later that it make a deal of payment in online. If you
make deal it will decrypt the all the file. This occur in advanced malware, now it not an advanced
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

mean simply recover the file will help of professional people. This all the things are happen by
your action only and another way to enter your processor is that downloading the unnecessary
file and folder or any abandoned software or any update in unwanted links. Another way hacking
is that message to your email that is an unwanted posts occur your mail if you respond that, it
automatically affect your computer. And directly attack the processor then it will be
uncontrollable for user. The recovering of files and folder is impossible in this malware. So you
should be very careful in your action or activities. The virtual attackers are hacked any company
details with help of this malware. The easy way is email message and internet perusing. Cyber
give various approaches for activate in that simple way is email supplement. Once your
computer attack with any virus that lead to be secondary management. There are various way of
attacking happen but without our action hacking is not possible, so our action should be legal
activates and lawful. So all action are done with help of us. Now a days this malware occurrence
the mobile also and it will the pin number of your phone for make a demand in advanced
version. But in normal malware easy to recover it by online synchronization. Using this invader
have hack all database of any company, industry, government agencies, academics, institution
through an individual person. For an efficacious malware the top encryption is required. Now a
day the technology should be protected with help of an encryption. The upsetting ransomware
attack is activate with help of WannaCry plagued one hundred fifty counties and all around the
continents. The main objective of this malware is online transaction illegally and it is encrypted
file is known as hacking. The first version of the malware is that identified in Russia ornographic
image in target apparatus. And request an expense to eradicate it. The result is that after analysis
maggot, try to notice and closed the announcement using analysis result. And enquiry sample are
given below,
This malware is only targeted the higher back ground people for a higher dealing not an
ordinary people. The file should be encrypt in one hundred twenty eight bits in cipher block
7
your action only and another way to enter your processor is that downloading the unnecessary
file and folder or any abandoned software or any update in unwanted links. Another way hacking
is that message to your email that is an unwanted posts occur your mail if you respond that, it
automatically affect your computer. And directly attack the processor then it will be
uncontrollable for user. The recovering of files and folder is impossible in this malware. So you
should be very careful in your action or activities. The virtual attackers are hacked any company
details with help of this malware. The easy way is email message and internet perusing. Cyber
give various approaches for activate in that simple way is email supplement. Once your
computer attack with any virus that lead to be secondary management. There are various way of
attacking happen but without our action hacking is not possible, so our action should be legal
activates and lawful. So all action are done with help of us. Now a days this malware occurrence
the mobile also and it will the pin number of your phone for make a demand in advanced
version. But in normal malware easy to recover it by online synchronization. Using this invader
have hack all database of any company, industry, government agencies, academics, institution
through an individual person. For an efficacious malware the top encryption is required. Now a
day the technology should be protected with help of an encryption. The upsetting ransomware
attack is activate with help of WannaCry plagued one hundred fifty counties and all around the
continents. The main objective of this malware is online transaction illegally and it is encrypted
file is known as hacking. The first version of the malware is that identified in Russia ornographic
image in target apparatus. And request an expense to eradicate it. The result is that after analysis
maggot, try to notice and closed the announcement using analysis result. And enquiry sample are
given below,
This malware is only targeted the higher back ground people for a higher dealing not an
ordinary people. The file should be encrypt in one hundred twenty eight bits in cipher block
7

chaining mode. The cipher block chaining method is mean encrypted the number of file into
simple part. The single bit error that affect all sequences of file and then demand of arrangement
should change leads to corrupted. (Zheng, 2017). The United States of America has to select the
(AES) advanced encryption standards to safe the important files and folder (Guo et al., 2015).
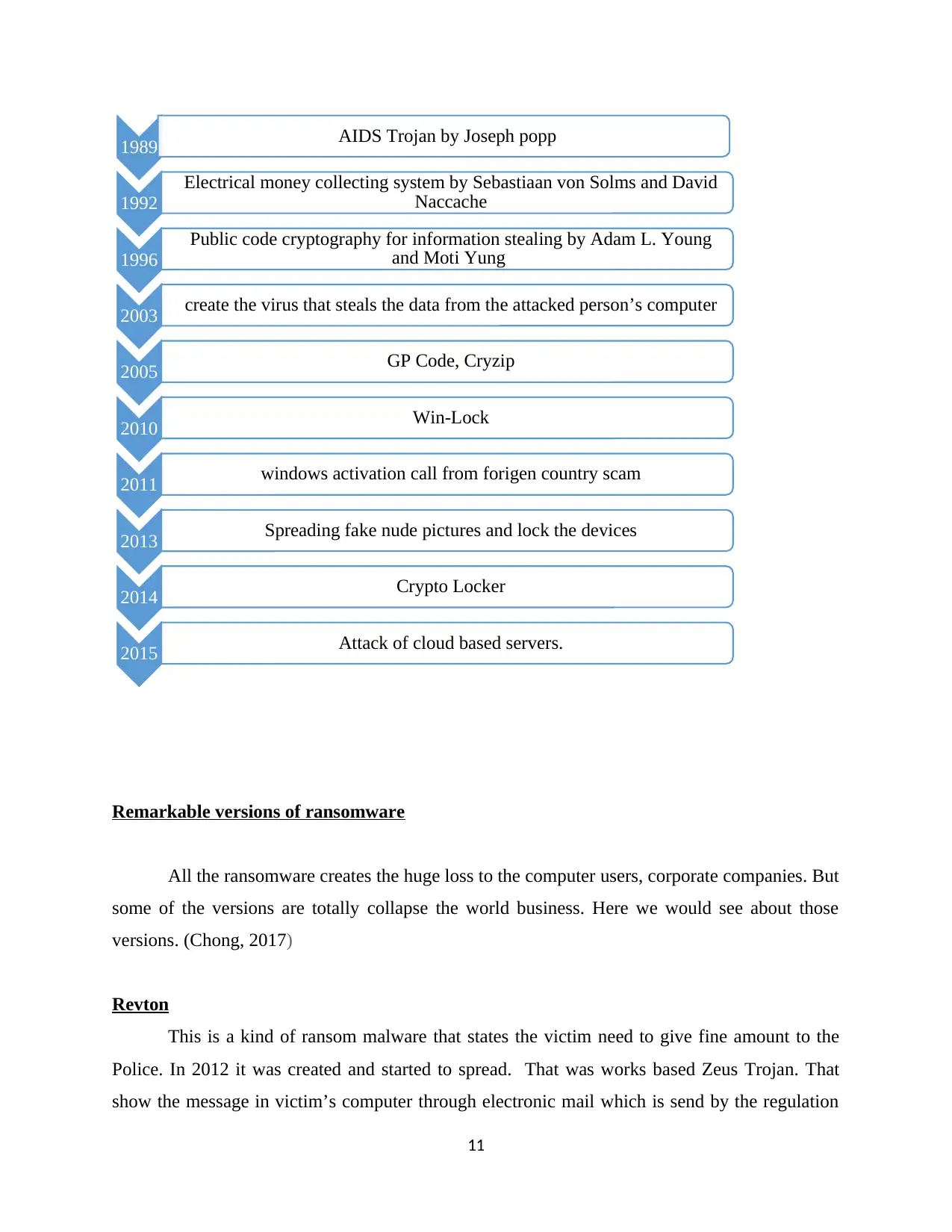
The evaluation of the ransomware was stared on the year of Nineteen eight nine. It was carried
out Joseph popp. It was named as AIDS Trojan. But it was not too effective, it simply hide the
data on the computer hard disk. And encrypt the file names alone. Then it shows the message to
the user license has finished for the usage access of the data on the computer. Then it asks some
money to repair the tool. Probably the money asked by the joseph was hundred and eighty nine
US dollars. After the completion of the payment the decryption code was created from the
Trojan. It is a “PC Cyborg”. He was announced as a mentally up normal person due to the
activities done by himself. On the other hand joseph assured that he want to donate part of his
earnings by the malware for the use of HIV research. (RANSOMWARE AND ITS IMPACT IN
INDIA – A LITERATUER STUDY, 2018). After three years latter (in Nineteen Ninety Two)
Sebastiaan von Solms and David Naccache they were developed the system to collect the money
electronically. The system was used to collects the currency securely for the human abduction.
This process was likewise planned for crypto viral coercion assaults. Here the NEWS paper was
used as the currency exchanging. After four years later (in Nineteen Ninety Six) another idea was
proposed by Adam L. Young and Moti Yung, which was use the public code cryptography for
information stealing assaults. He reviewed the first ransomware created by joseph as it only do
the symmetric cryptography, the decryption code was retrieved from Trojan. Crypto virus
contains opening code only, so the attacker must keep those files securely. But in his practice the
affected person need to send the unequal cipher text for the attacker, then attacker send the
refurbishing code for the exchange of money. Here the attacker can able to hold the process until
the partial payment completion.(Digital Extortion: An Empirical Investigation on Ransomware
Infection and Countermeasures, 2018)
In 2003 the attack conducted by Adam.L. Who create the virus that steals the data from the
attacked person’s computer, and send it to the attacker. Then the attacker threatens the victim to
give a money unless he leaks the data retrieved from the victim’s computer. This non encrypted
8
simple part. The single bit error that affect all sequences of file and then demand of arrangement
should change leads to corrupted. (Zheng, 2017). The United States of America has to select the
(AES) advanced encryption standards to safe the important files and folder (Guo et al., 2015).
The evaluation of the ransomware was stared on the year of Nineteen eight nine. It was carried
out Joseph popp. It was named as AIDS Trojan. But it was not too effective, it simply hide the
data on the computer hard disk. And encrypt the file names alone. Then it shows the message to
the user license has finished for the usage access of the data on the computer. Then it asks some
money to repair the tool. Probably the money asked by the joseph was hundred and eighty nine
US dollars. After the completion of the payment the decryption code was created from the
Trojan. It is a “PC Cyborg”. He was announced as a mentally up normal person due to the
activities done by himself. On the other hand joseph assured that he want to donate part of his
earnings by the malware for the use of HIV research. (RANSOMWARE AND ITS IMPACT IN
INDIA – A LITERATUER STUDY, 2018). After three years latter (in Nineteen Ninety Two)
Sebastiaan von Solms and David Naccache they were developed the system to collect the money
electronically. The system was used to collects the currency securely for the human abduction.
This process was likewise planned for crypto viral coercion assaults. Here the NEWS paper was
used as the currency exchanging. After four years later (in Nineteen Ninety Six) another idea was
proposed by Adam L. Young and Moti Yung, which was use the public code cryptography for
information stealing assaults. He reviewed the first ransomware created by joseph as it only do
the symmetric cryptography, the decryption code was retrieved from Trojan. Crypto virus
contains opening code only, so the attacker must keep those files securely. But in his practice the
affected person need to send the unequal cipher text for the attacker, then attacker send the
refurbishing code for the exchange of money. Here the attacker can able to hold the process until
the partial payment completion.(Digital Extortion: An Empirical Investigation on Ransomware
Infection and Countermeasures, 2018)
In 2003 the attack conducted by Adam.L. Who create the virus that steals the data from the
attacked person’s computer, and send it to the attacker. Then the attacker threatens the victim to
give a money unless he leaks the data retrieved from the victim’s computer. This non encrypted
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

type attack. During the attack if someone won’t pay the money he asked they lost their data and
reputations, ect. After the long time May-2005 the expensive ransomwares like GP Code,
Cryzip, TROJ RANSO. A, MayArchive, Krotten, and Archiveus uses the advanced RSA
techniques. The key code size were continuously increased. In Jun-2006 the repairing code was
encrypted by the 660 bit RSA technology. After the two years later next variant of the Gp-code
was released, that uses the 1024 bit RSA encryption technology. To repair the computer we need
the help from the attacker, it is impossible to break the malware (Ali, 2017). During the AUG-
2010, there are 9 persons are arrested by the Russian officers for the malware creation and
spreading. This not similar as the existing viruses they are called as Win-Lock. Here that restricts
the system and shows the porn images, then asks money to the users, probably the money asked
by the attackers was around ten US dollar. From this operation the attackers earned nearly
16000000 US dollars from the victims of Russia and its nearby countries. After one year JAN-
2011 another type of the method was carried out by the attackers. Here also there is no
encryption methods used. In this type the attacker shows the message regards to windows
activation. Here the internet based activation option was given to the victim. That makes the user
to call for an international no to input a 6 digit password. That leads to user lost huge amount for
the foreign calls. After two years later FEB-2013 the another version of the virus was created and
start to spread that shows the undressed picture of the famous heroines, pop singers, etc.… this
also don’t use encryption techniques, it simply feats the performance of browser. During the
JUL-2013 Virginia man can be arrested for his action related to child abuse. (Acharya, 2017)
Those kind of procedures are abandoned in yearly 2014, by the use of Crypto Locker. They use
the digital currency, bitcoins for the collection of the ransom currency. Based on the study
conducted by the ZDNet in DEC-2013 the fund transferred by the crypto lockers was nearly
2700000 US dollars. They are collected for the repairing code for the malware. That was used by
the large amount of virus writers. But it has one major fault, which is the decryption key was
stored in the affected computer. So the victim can able to retrieve the code. Then the malwares
are produced purposively for attack cloud based systems. On JAN-2015 that attacks the Linux
operated online-servers, and individual online sites by hacking it. Then the Microsoft
Corporation analyze the problem by it sub body named as Antimalware & cyber security. And
they found the .LNK files install the malware by autonomously infects the system, in earlier
9
reputations, ect. After the long time May-2005 the expensive ransomwares like GP Code,
Cryzip, TROJ RANSO. A, MayArchive, Krotten, and Archiveus uses the advanced RSA
techniques. The key code size were continuously increased. In Jun-2006 the repairing code was
encrypted by the 660 bit RSA technology. After the two years later next variant of the Gp-code
was released, that uses the 1024 bit RSA encryption technology. To repair the computer we need
the help from the attacker, it is impossible to break the malware (Ali, 2017). During the AUG-
2010, there are 9 persons are arrested by the Russian officers for the malware creation and
spreading. This not similar as the existing viruses they are called as Win-Lock. Here that restricts
the system and shows the porn images, then asks money to the users, probably the money asked
by the attackers was around ten US dollar. From this operation the attackers earned nearly
16000000 US dollars from the victims of Russia and its nearby countries. After one year JAN-
2011 another type of the method was carried out by the attackers. Here also there is no
encryption methods used. In this type the attacker shows the message regards to windows
activation. Here the internet based activation option was given to the victim. That makes the user
to call for an international no to input a 6 digit password. That leads to user lost huge amount for
the foreign calls. After two years later FEB-2013 the another version of the virus was created and
start to spread that shows the undressed picture of the famous heroines, pop singers, etc.… this
also don’t use encryption techniques, it simply feats the performance of browser. During the
JUL-2013 Virginia man can be arrested for his action related to child abuse. (Acharya, 2017)
Those kind of procedures are abandoned in yearly 2014, by the use of Crypto Locker. They use
the digital currency, bitcoins for the collection of the ransom currency. Based on the study
conducted by the ZDNet in DEC-2013 the fund transferred by the crypto lockers was nearly
2700000 US dollars. They are collected for the repairing code for the malware. That was used by
the large amount of virus writers. But it has one major fault, which is the decryption key was
stored in the affected computer. So the victim can able to retrieve the code. Then the malwares
are produced purposively for attack cloud based systems. On JAN-2015 that attacks the Linux
operated online-servers, and individual online sites by hacking it. Then the Microsoft
Corporation analyze the problem by it sub body named as Antimalware & cyber security. And
they found the .LNK files install the malware by autonomously infects the system, in earlier
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

method the victim download the .WSF files. So the attacks in the power shell windows
applications. That states that the windows based systems has a weakness that are used by the
criminals.Then criminals follow the advanced technology supplied by the darkweb dealers. That
gives more security for the criminals. If the criminal use those technology that is not possible to
locate the attackers locations easily. The famous cyber security company states the ransomware
was too dangerous threat for the modern computers. (“Ransomware becomes the most prevalent
form of malware and hits an ever-wider range of victims, 2017”)
The increasing no of mobiles and its features leads to cyber-attack on the mobile. It is
higher in android platforms because it was an open source software, which allow the third party
application (Android Malware Detection And Prevention, 2017). In apple phones it just luck the
phone, if we want to use the phone we need to pay the money for the attackers.
In the above time line shows the details about various ransomwares.
10
applications. That states that the windows based systems has a weakness that are used by the
criminals.Then criminals follow the advanced technology supplied by the darkweb dealers. That
gives more security for the criminals. If the criminal use those technology that is not possible to
locate the attackers locations easily. The famous cyber security company states the ransomware
was too dangerous threat for the modern computers. (“Ransomware becomes the most prevalent
form of malware and hits an ever-wider range of victims, 2017”)
The increasing no of mobiles and its features leads to cyber-attack on the mobile. It is
higher in android platforms because it was an open source software, which allow the third party
application (Android Malware Detection And Prevention, 2017). In apple phones it just luck the
phone, if we want to use the phone we need to pay the money for the attackers.
In the above time line shows the details about various ransomwares.
10
Remarkable versions of ransomware
All the ransomware creates the huge loss to the computer users, corporate companies. But
some of the versions are totally collapse the world business. Here we would see about those
versions. (Chong, 2017)
Revton
This is a kind of ransom malware that states the victim need to give fine amount to the
Police. In 2012 it was created and started to spread. That was works based Zeus Trojan. That
show the message in victim’s computer through electronic mail which is send by the regulation
11
1989 AIDS Trojan by Joseph popp
1992
Electrical money collecting system by Sebastiaan von Solms and David
Naccache
1996
Public code cryptography for information stealing by Adam L. Young
and Moti Yung
2003 create the virus that steals the data from the attacked person’s computer
2005 GP Code, Cryzip
2010 Win-Lock
2011 windows activation call from forigen country scam
2013 Spreading fake nude pictures and lock the devices
2014 Crypto Locker
2015 Attack of cloud based servers.
All the ransomware creates the huge loss to the computer users, corporate companies. But
some of the versions are totally collapse the world business. Here we would see about those
versions. (Chong, 2017)
Revton
This is a kind of ransom malware that states the victim need to give fine amount to the
Police. In 2012 it was created and started to spread. That was works based Zeus Trojan. That
show the message in victim’s computer through electronic mail which is send by the regulation
11
1989 AIDS Trojan by Joseph popp
1992
Electrical money collecting system by Sebastiaan von Solms and David
Naccache
1996
Public code cryptography for information stealing by Adam L. Young
and Moti Yung
2003 create the virus that steals the data from the attacked person’s computer
2005 GP Code, Cryzip
2010 Win-Lock
2011 windows activation call from forigen country scam
2013 Spreading fake nude pictures and lock the devices
2014 Crypto Locker
2015 Attack of cloud based servers.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 139
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
