Real-Time Analytics: Big Data Privacy Concerns and Analysis
VerifiedAdded on 2022/09/16
|20
|3920
|24
Report
AI Summary
This report provides a comprehensive analysis of big data privacy within the context of real-time analytics. It begins by defining big data and its characteristics, highlighting its significance in modern data processing. The report then delves into the critical issue of data breaches, using Facebook as a primary example, and examines the impact of the Cambridge Analytica scandal on data privacy. It discusses the importance of data privacy, providing examples of relevant laws and regulations. Furthermore, the report explores the use of persuasive advertising on social media, including 'deepfake' videos, and details how platforms like Facebook and Google collect user data. The value of big data as a valuable asset is discussed, along with the techniques and methodologies used to ensure data privacy. The report also addresses ethical issues concerning big data privacy, including the question of how much information is too much. Finally, the report explores tracking on people's involvement in social media and the impact of data breaches on social media habits. The report is based on 15 peer reviewed journal articles.

Running head: BIG DATA AND PRIVACY
Big Data and Privacy
Name of the Student
Name of the University
Author note
Big Data and Privacy
Name of the Student
Name of the University
Author note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1BIG DATA AND PRIVACY
Table of Contents
1. Introduction....................................................................................................................2
2. Discussion......................................................................................................................2
2.1 Data Breaches.........................................................................................................2
2.2 Research on Data Breaches....................................................................................3
2.3 Trump campaign and Cambridge Analytica Scandal..............................................4
2.4 Examples of Data Privacy and Relevant Importance..............................................5
2.5 Persuasive advertising on Social Media..................................................................5
2.6 “DEEP FAKE” video advertising..............................................................................6
2.7 Misuse of Facebook Data by Cambridge Analytica.................................................6
2.8 Receiving of data by Social Media Platforms..........................................................6
2.9 Big Data as a Valuable Asset for Future..................................................................7
2.9 Techniques and methodologies engaged with big data privacy..............................8
2.10 “How much information is too much Information”..................................................9
2.11 Big Data Privacy...................................................................................................10
2.12 “Tracking on people’s involvement in social media”............................................10
2.13 Working functionality of tracking criteria..............................................................12
2.14 Impact of Data Breaches over Social Media habits.............................................13
2.15 Mass surveillance by government in USA and China..........................................13
2.16 Ethical issues concerned with big data privacy...................................................13
Table of Contents
1. Introduction....................................................................................................................2
2. Discussion......................................................................................................................2
2.1 Data Breaches.........................................................................................................2
2.2 Research on Data Breaches....................................................................................3
2.3 Trump campaign and Cambridge Analytica Scandal..............................................4
2.4 Examples of Data Privacy and Relevant Importance..............................................5
2.5 Persuasive advertising on Social Media..................................................................5
2.6 “DEEP FAKE” video advertising..............................................................................6
2.7 Misuse of Facebook Data by Cambridge Analytica.................................................6
2.8 Receiving of data by Social Media Platforms..........................................................6
2.9 Big Data as a Valuable Asset for Future..................................................................7
2.9 Techniques and methodologies engaged with big data privacy..............................8
2.10 “How much information is too much Information”..................................................9
2.11 Big Data Privacy...................................................................................................10
2.12 “Tracking on people’s involvement in social media”............................................10
2.13 Working functionality of tracking criteria..............................................................12
2.14 Impact of Data Breaches over Social Media habits.............................................13
2.15 Mass surveillance by government in USA and China..........................................13
2.16 Ethical issues concerned with big data privacy...................................................13

2BIG DATA AND PRIVACY
3. Conclusion...................................................................................................................14
References.......................................................................................................................15
3. Conclusion...................................................................................................................14
References.......................................................................................................................15
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3BIG DATA AND PRIVACY
1. Introduction
The concept of Big Data can be defined as term, which primarily refers to large
sets of data, which have a complex and varied structure. The different kind of
characteristics that are embedded in the platform of Big Data primarily correlate
themselves to the main purpose of performing analysis, storing and further application
of procedures based on extracting of generic results (Gandomi & Haider, 2015). There
have been huge contradictions in relation to the security and privacy concerns in the
field of Big Data and the different aspects of the use of this technology.
Big Data mainly deals with large and complex sets of data that are often
generated by companies in order to process them. Hence, these forms of data are
highly critical in nature as they relate to customers and their privacy. In the present time,
it has been majorly been seen that security breaches hamper the growth and reputation
of companies as people might feel that lack of security measures lead to the scenario of
breaches. This paper would thus highlight the latest security techniques that could be
applied to big data frameworks (Chen & Zhang, 2014). The primary topic of discussion
and the focus of the paper is based on the concerns in relation to security and privacy,
data breaches that have occurred in the recent years, data privacy aspects and the
various kind of ethical issues that govern the framework of the technology.
2. Discussion
2.1 Data Breaches
In the recent kind of data breaches, Facebook continues to be the leading sector
over which data breaches have occurred continuously. In a more recent news of data
1. Introduction
The concept of Big Data can be defined as term, which primarily refers to large
sets of data, which have a complex and varied structure. The different kind of
characteristics that are embedded in the platform of Big Data primarily correlate
themselves to the main purpose of performing analysis, storing and further application
of procedures based on extracting of generic results (Gandomi & Haider, 2015). There
have been huge contradictions in relation to the security and privacy concerns in the
field of Big Data and the different aspects of the use of this technology.
Big Data mainly deals with large and complex sets of data that are often
generated by companies in order to process them. Hence, these forms of data are
highly critical in nature as they relate to customers and their privacy. In the present time,
it has been majorly been seen that security breaches hamper the growth and reputation
of companies as people might feel that lack of security measures lead to the scenario of
breaches. This paper would thus highlight the latest security techniques that could be
applied to big data frameworks (Chen & Zhang, 2014). The primary topic of discussion
and the focus of the paper is based on the concerns in relation to security and privacy,
data breaches that have occurred in the recent years, data privacy aspects and the
various kind of ethical issues that govern the framework of the technology.
2. Discussion
2.1 Data Breaches
In the recent kind of data breaches, Facebook continues to be the leading sector
over which data breaches have occurred continuously. In a more recent news of data
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4BIG DATA AND PRIVACY
breach on Facebook, it was reported that nearly 540 million records in relation to
Facebook users were exposed publicly on the cloud computing service offered by
Amazon. In a published report, it was also reported that two different third-party app
developers by Facebook had posted the data records in a plain form of sight, which led
to another major kind of data breach.
Another example of data breach had occurred when Cambridge Analytica that
was working for Trump campaign had gained access to public data of over 87 million
users (Facebook says 87 million may be affected by data breach, 2019). In a news
published in September, Facebook had reported that different attack on their networks
had led to exposure of 50 million users.
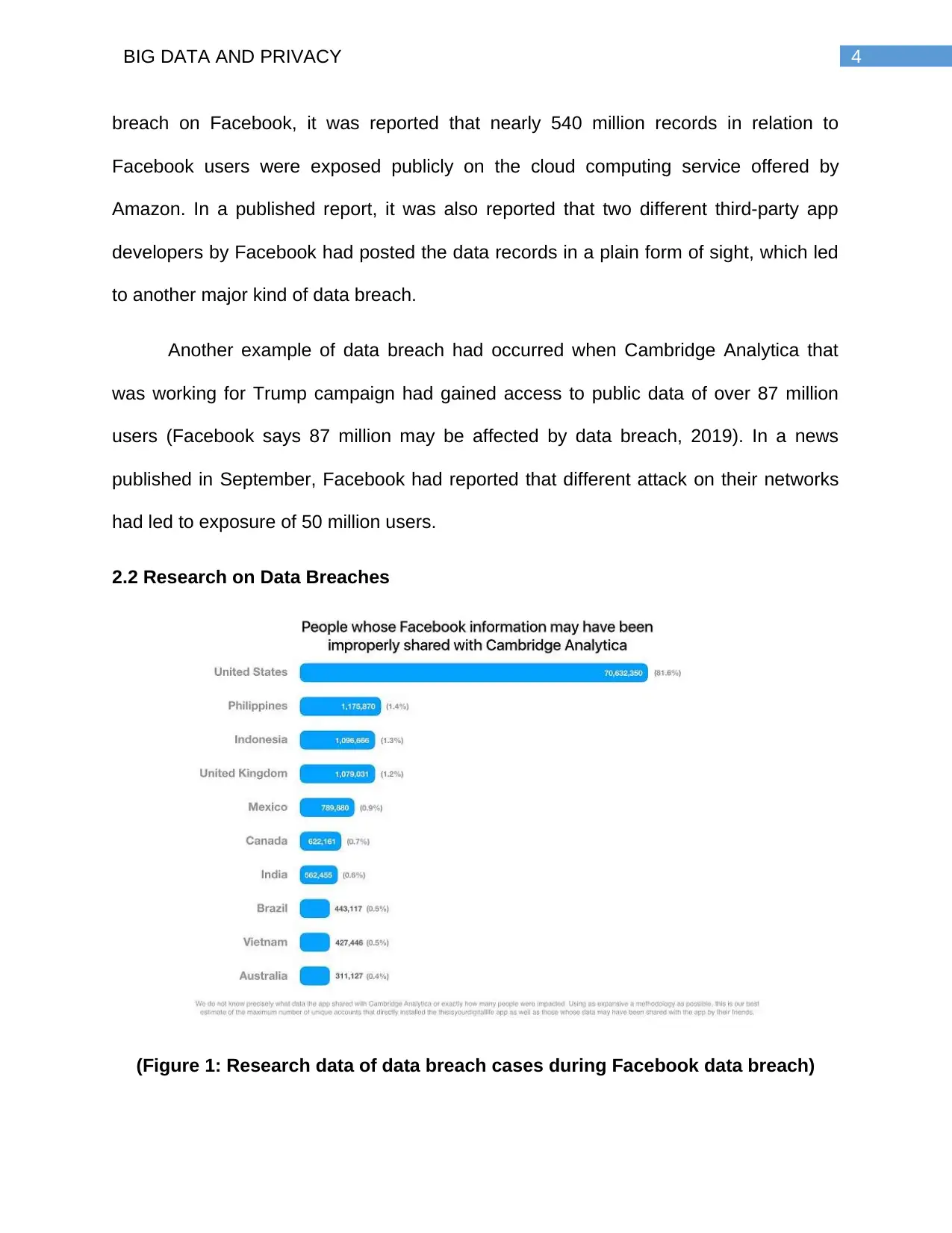
2.2 Research on Data Breaches
(Figure 1: Research data of data breach cases during Facebook data breach)
breach on Facebook, it was reported that nearly 540 million records in relation to
Facebook users were exposed publicly on the cloud computing service offered by
Amazon. In a published report, it was also reported that two different third-party app
developers by Facebook had posted the data records in a plain form of sight, which led
to another major kind of data breach.
Another example of data breach had occurred when Cambridge Analytica that
was working for Trump campaign had gained access to public data of over 87 million
users (Facebook says 87 million may be affected by data breach, 2019). In a news
published in September, Facebook had reported that different attack on their networks
had led to exposure of 50 million users.
2.2 Research on Data Breaches
(Figure 1: Research data of data breach cases during Facebook data breach)

5BIG DATA AND PRIVACY
(Source: Facebook says 87 million may be affected by data breach, 2019)
The above figure displays the list of countries and the number of people who
were largely affected during the Cambridge Analytica data breach. Nearly 87 million
users had their data breached during the failure of the data engineers to protect the
data from the social network platform. The estimate made by Facebook in respect to the
data breach had considered the fact that this number could be much higher and thus
they had been ruined (Crawford & Schultz, 2014). Different questions were also being
raised by people about their privacy concerns and the ways in which their data was
being stored that had led to such cases of breach.
However, after the incident of the data breach, the chief technology officer at
Facebook had confirmed that new kind of data privacy tools and application would be
installed within the network for protecting the network of the platform.
2.3 Trump campaign and Cambridge Analytica Scandal
Cambridge Analytica, which is one of the largest political consulting firm, had a
long term relationship with performing works during the Trump election campaign. They
further harvested data from the Facebook profiles of nearly 87 million users. They had
created a quiz based on collecting data from the people. However, during the creation
of the quiz, a certain loophole was also created within the Facebook API that further led
to negative impacts with the illegal collection of data from other Facebook friends who
had participated in the quiz (Kozlowska, 2018). In relation to this illegal process of
collecting of data, it had been reported that Facebook had majorly protested against the
selling of public data from their platform but Cambridge Analytica had gained access to
the data and sold them anyway.
(Source: Facebook says 87 million may be affected by data breach, 2019)
The above figure displays the list of countries and the number of people who
were largely affected during the Cambridge Analytica data breach. Nearly 87 million
users had their data breached during the failure of the data engineers to protect the
data from the social network platform. The estimate made by Facebook in respect to the
data breach had considered the fact that this number could be much higher and thus
they had been ruined (Crawford & Schultz, 2014). Different questions were also being
raised by people about their privacy concerns and the ways in which their data was
being stored that had led to such cases of breach.
However, after the incident of the data breach, the chief technology officer at
Facebook had confirmed that new kind of data privacy tools and application would be
installed within the network for protecting the network of the platform.
2.3 Trump campaign and Cambridge Analytica Scandal
Cambridge Analytica, which is one of the largest political consulting firm, had a
long term relationship with performing works during the Trump election campaign. They
further harvested data from the Facebook profiles of nearly 87 million users. They had
created a quiz based on collecting data from the people. However, during the creation
of the quiz, a certain loophole was also created within the Facebook API that further led
to negative impacts with the illegal collection of data from other Facebook friends who
had participated in the quiz (Kozlowska, 2018). In relation to this illegal process of
collecting of data, it had been reported that Facebook had majorly protested against the
selling of public data from their platform but Cambridge Analytica had gained access to
the data and sold them anyway.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6BIG DATA AND PRIVACY
2.4 Examples of Data Privacy and Relevant Importance
Data privacy is an important in the recent times and hence every kind of possible
laws have been put together to create a response against any kind of illegal activity.
Some of the examples of data privacy, which have been undertaken are:
1. Children’s Online Privacy Protection Act (COPPA) – This act enabled by
the U.S government to provide parents with control over the kind of information
websites that could be visited by their children.
2. Health Insurance Portability and Accountability Act (HIPPA) – This law
ensures that the confidentiality of data in relation to patients would be maintained
across all platforms.
3. Electronic Communications Privacy Act (ECPA) – This act extends the
restrictions enabled by the government over the electronic data transmission (Fu et al.,
2015).
4. Gramm-Leach-Bliley Act – This act mandates the ways in which financial
institutions should deal with every kind of private information related to individuals.
2.5 Persuasive advertising on Social Media
The use of persuasive advertising made by Cambridge Analytica had sold the
data of customers by capturing their data from Facebook in order to aid for Trump
campaign. This advertising company had continuously made use of data for providing
data towards the campaign, thus leading to an international data scandal (Lee,
Hosanagar & Nair, 2018). This further led to an international global outage based on the
2.4 Examples of Data Privacy and Relevant Importance
Data privacy is an important in the recent times and hence every kind of possible
laws have been put together to create a response against any kind of illegal activity.
Some of the examples of data privacy, which have been undertaken are:
1. Children’s Online Privacy Protection Act (COPPA) – This act enabled by
the U.S government to provide parents with control over the kind of information
websites that could be visited by their children.
2. Health Insurance Portability and Accountability Act (HIPPA) – This law
ensures that the confidentiality of data in relation to patients would be maintained
across all platforms.
3. Electronic Communications Privacy Act (ECPA) – This act extends the
restrictions enabled by the government over the electronic data transmission (Fu et al.,
2015).
4. Gramm-Leach-Bliley Act – This act mandates the ways in which financial
institutions should deal with every kind of private information related to individuals.
2.5 Persuasive advertising on Social Media
The use of persuasive advertising made by Cambridge Analytica had sold the
data of customers by capturing their data from Facebook in order to aid for Trump
campaign. This advertising company had continuously made use of data for providing
data towards the campaign, thus leading to an international data scandal (Lee,
Hosanagar & Nair, 2018). This further led to an international global outage based on the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7BIG DATA AND PRIVACY
failure of the company top secure the privacy of data for 87 million customers. Due to
the huge data breach, $134 billion of market value of Facebook had dropped down.
2.6 “DEEP FAKE” video advertising
Deep Fake videos are a kind of video advertising technique, which employs
machine learning technique for copying the exact details of any original video to
propagate the own ideas of the individual intending to create such videos and spread
negative news (Alotaibi & Mahmood, 2017). In the case of the campaign proposed by
Trump, different Deep Fake videos were uploaded on Facebook to spread wrong news
about the campaign.
2.7 Misuse of Facebook Data by Cambridge Analytica
Cambridge Analytica is a data analytics firm that was working closely with the
election team headed by Donald Trump. The company had purchased the Facebook
data for tens of millions of American people without their prior knowledge. They had
created a quiz in which they had intended to collect data from individuals in relation to
the campaign (Isaak & Hanna, 2018). However, a certain glitch within the Facebook API
had led to security breaches over the collected data.
2.8 Receiving of data by Social Media Platforms
Facebook and different other social media platforms make use of an extensive
network based on tracking technology. This technology helps the company to
understand the browsing habits of users and even during the time when they would not
be active on the social network.
failure of the company top secure the privacy of data for 87 million customers. Due to
the huge data breach, $134 billion of market value of Facebook had dropped down.
2.6 “DEEP FAKE” video advertising
Deep Fake videos are a kind of video advertising technique, which employs
machine learning technique for copying the exact details of any original video to
propagate the own ideas of the individual intending to create such videos and spread
negative news (Alotaibi & Mahmood, 2017). In the case of the campaign proposed by
Trump, different Deep Fake videos were uploaded on Facebook to spread wrong news
about the campaign.
2.7 Misuse of Facebook Data by Cambridge Analytica
Cambridge Analytica is a data analytics firm that was working closely with the
election team headed by Donald Trump. The company had purchased the Facebook
data for tens of millions of American people without their prior knowledge. They had
created a quiz in which they had intended to collect data from individuals in relation to
the campaign (Isaak & Hanna, 2018). However, a certain glitch within the Facebook API
had led to security breaches over the collected data.
2.8 Receiving of data by Social Media Platforms
Facebook and different other social media platforms make use of an extensive
network based on tracking technology. This technology helps the company to
understand the browsing habits of users and even during the time when they would not
be active on the social network.
8BIG DATA AND PRIVACY
Whenever a user visits a particular website, the browser sends a certain request
to the server of the site. The browser would then pass on the IP address in order to let
the website know about the path to which the content of the site would be sent. It also
receives cookies, which are defined as identifiers that are used by websites for knowing
the previous used website by the user (DeNardis & Hackl, 2015). Facebook also offer
their own developed tracking cookies that are installed within most webpages. They
thus track the information of users and thus provide content based on the preferences
of users.
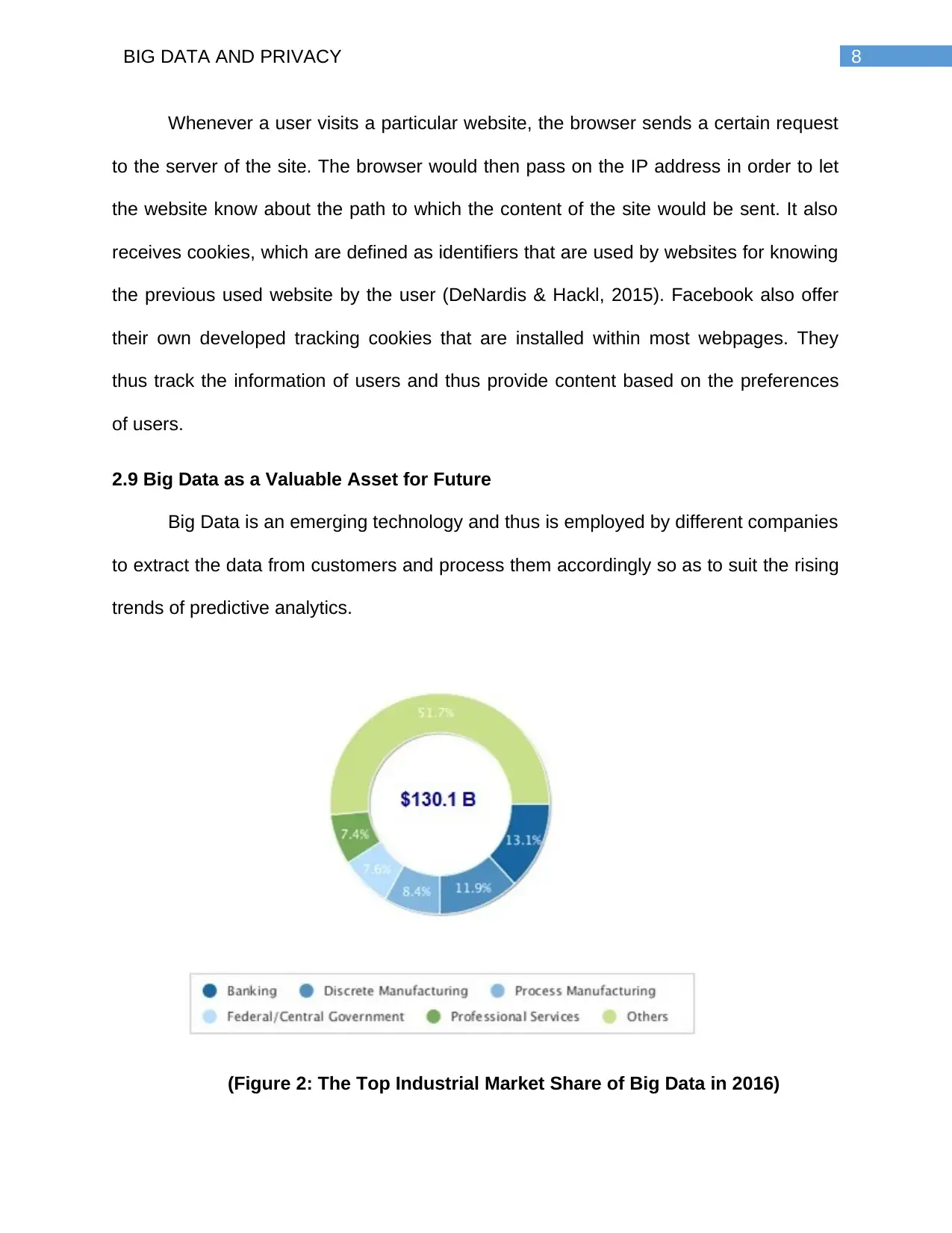
2.9 Big Data as a Valuable Asset for Future
Big Data is an emerging technology and thus is employed by different companies
to extract the data from customers and process them accordingly so as to suit the rising
trends of predictive analytics.
(Figure 2: The Top Industrial Market Share of Big Data in 2016)
Whenever a user visits a particular website, the browser sends a certain request
to the server of the site. The browser would then pass on the IP address in order to let
the website know about the path to which the content of the site would be sent. It also
receives cookies, which are defined as identifiers that are used by websites for knowing
the previous used website by the user (DeNardis & Hackl, 2015). Facebook also offer
their own developed tracking cookies that are installed within most webpages. They
thus track the information of users and thus provide content based on the preferences
of users.
2.9 Big Data as a Valuable Asset for Future
Big Data is an emerging technology and thus is employed by different companies
to extract the data from customers and process them accordingly so as to suit the rising
trends of predictive analytics.
(Figure 2: The Top Industrial Market Share of Big Data in 2016)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9BIG DATA AND PRIVACY
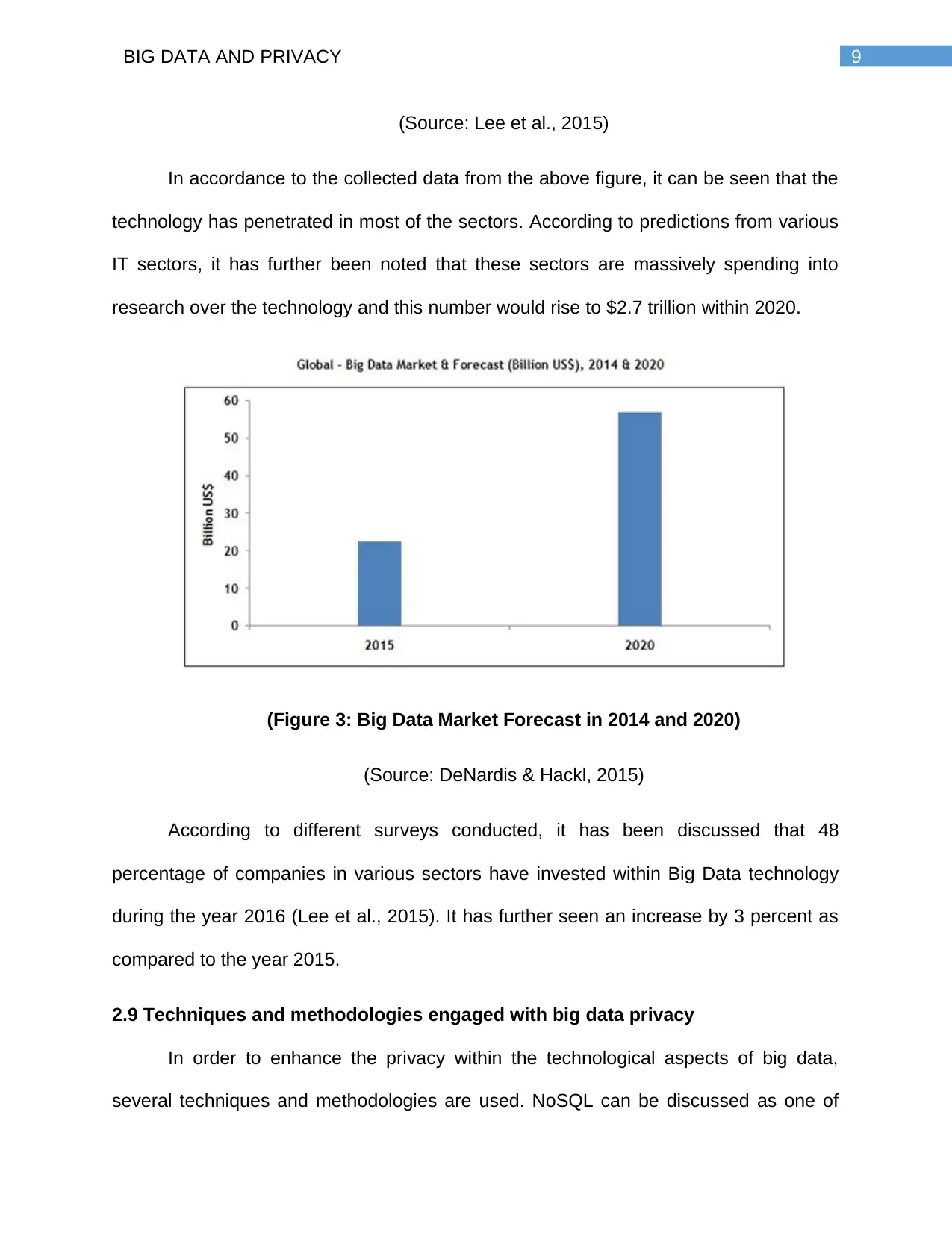
(Source: Lee et al., 2015)
In accordance to the collected data from the above figure, it can be seen that the
technology has penetrated in most of the sectors. According to predictions from various
IT sectors, it has further been noted that these sectors are massively spending into
research over the technology and this number would rise to $2.7 trillion within 2020.
(Figure 3: Big Data Market Forecast in 2014 and 2020)
(Source: DeNardis & Hackl, 2015)
According to different surveys conducted, it has been discussed that 48
percentage of companies in various sectors have invested within Big Data technology
during the year 2016 (Lee et al., 2015). It has further seen an increase by 3 percent as
compared to the year 2015.
2.9 Techniques and methodologies engaged with big data privacy
In order to enhance the privacy within the technological aspects of big data,
several techniques and methodologies are used. NoSQL can be discussed as one of
(Source: Lee et al., 2015)
In accordance to the collected data from the above figure, it can be seen that the
technology has penetrated in most of the sectors. According to predictions from various
IT sectors, it has further been noted that these sectors are massively spending into
research over the technology and this number would rise to $2.7 trillion within 2020.
(Figure 3: Big Data Market Forecast in 2014 and 2020)
(Source: DeNardis & Hackl, 2015)
According to different surveys conducted, it has been discussed that 48
percentage of companies in various sectors have invested within Big Data technology
during the year 2016 (Lee et al., 2015). It has further seen an increase by 3 percent as
compared to the year 2015.
2.9 Techniques and methodologies engaged with big data privacy
In order to enhance the privacy within the technological aspects of big data,
several techniques and methodologies are used. NoSQL can be discussed as one of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10BIG DATA AND PRIVACY
the widely distributed database system, which has gained tremendous prominence in
the systems of big data. On the other hand, Apache Hadoop is another form of tool,
which is majorly used by companies during the processing of raw extracted data (Zhang
et al., 2016). Other tools such as R, SQL and Python could be used for performing data
analysis.
(Figure 4: Three-Step Framework for implementing Big Data Security)
(Source: Zhang et al., 2016)
Data visualisation technique is also used for understanding the changes and
trends within the data sets over a specified time period. Hence, to achieve data
visualisation, tools such as Kibana and Elastic Stack are used.
2.10 “How much information is too much Information”
The violation of data privacy is considered as the widely discussed topic in the
present times. Use of accounts that are permanently logged in and making use of
websites for the purpose of running click analytics for the purpose of recording
the widely distributed database system, which has gained tremendous prominence in
the systems of big data. On the other hand, Apache Hadoop is another form of tool,
which is majorly used by companies during the processing of raw extracted data (Zhang
et al., 2016). Other tools such as R, SQL and Python could be used for performing data
analysis.
(Figure 4: Three-Step Framework for implementing Big Data Security)
(Source: Zhang et al., 2016)
Data visualisation technique is also used for understanding the changes and
trends within the data sets over a specified time period. Hence, to achieve data
visualisation, tools such as Kibana and Elastic Stack are used.
2.10 “How much information is too much Information”
The violation of data privacy is considered as the widely discussed topic in the
present times. Use of accounts that are permanently logged in and making use of
websites for the purpose of running click analytics for the purpose of recording

11BIG DATA AND PRIVACY
preferences of users could be considered as some ways in which information is
extracted.
Large tech giants such as Amazon, Facebook and Google use predictive
analytics technology for understanding the choices and interests of users. They
understand the type of product that are searched by users and thus provide this
information to other serving companies such as Google AdSense for the purpose of
tracking the behavioural patterns of users to purchase items (Branco, Sun & Villas-
Boas, 2015). During this process, people should be highly be aware that their data is
being sold to different third party applications for fulfilling the benefit of one company.
2.11 Big Data Privacy
There are different cases of breach in the data of users that are preserved by
companies. However, some of the reasons for which people should be aware of big
data privacy are:
1. According to different studies, it has been seen that nearly 50-60% of projects
based on Big Data have failed. They have thus created zero business value. This has
mainly been due to the reason that they had missed the planned scheduling of jobs and
bursting budget (Lu et al., 2014). A right skilled team should also be taken into
consideration during proceeding over Big Data projects.
2. Millions of dollars are spent over purchasing software licenses, large hardware
clusters and other human resources but the end result leads to failure in launching
such projects. These technologies needs to be embedded into the core functionality of
preferences of users could be considered as some ways in which information is
extracted.
Large tech giants such as Amazon, Facebook and Google use predictive
analytics technology for understanding the choices and interests of users. They
understand the type of product that are searched by users and thus provide this
information to other serving companies such as Google AdSense for the purpose of
tracking the behavioural patterns of users to purchase items (Branco, Sun & Villas-
Boas, 2015). During this process, people should be highly be aware that their data is
being sold to different third party applications for fulfilling the benefit of one company.
2.11 Big Data Privacy
There are different cases of breach in the data of users that are preserved by
companies. However, some of the reasons for which people should be aware of big
data privacy are:
1. According to different studies, it has been seen that nearly 50-60% of projects
based on Big Data have failed. They have thus created zero business value. This has
mainly been due to the reason that they had missed the planned scheduling of jobs and
bursting budget (Lu et al., 2014). A right skilled team should also be taken into
consideration during proceeding over Big Data projects.
2. Millions of dollars are spent over purchasing software licenses, large hardware
clusters and other human resources but the end result leads to failure in launching
such projects. These technologies needs to be embedded into the core functionality of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





