SIT182 - Real-World Practices for Cyber Security: Assessment Task 2
VerifiedAdded on 2023/06/12
|14
|2344
|336
Report
AI Summary
This report details the process of identifying and exploiting vulnerabilities in a simulated cyber security environment as part of the SIT182 course. It covers a range of security flaws, including information leakage through exposed source code, directory traversal vulnerabilities allowing unauthorized file access, weak encryption methods easily bypassed using techniques like Caesar ciphers and pre-compiled hash lookups, and SQL injection vulnerabilities enabling database manipulation. Each level of the war game is analyzed, providing observations, screenshots, credential extraction, impact analysis, and recommendations for remediation. The report emphasizes the importance of secure coding practices, robust encryption, proper access controls, and SQL injection prevention to protect against real-world cyber threats. The document concludes by referencing academic sources that support the findings and recommendations.

Report Title
SIT182 – Real-World Practices for Cyber Security
Assessment Task 2 Problem Solving Task
Student Name
Student ID
SIT182 – Real-World Practices for Cyber Security
Assessment Task 2 Problem Solving Task
Student Name
Student ID
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Information Leakage Level No(s)
War Game
Level
1
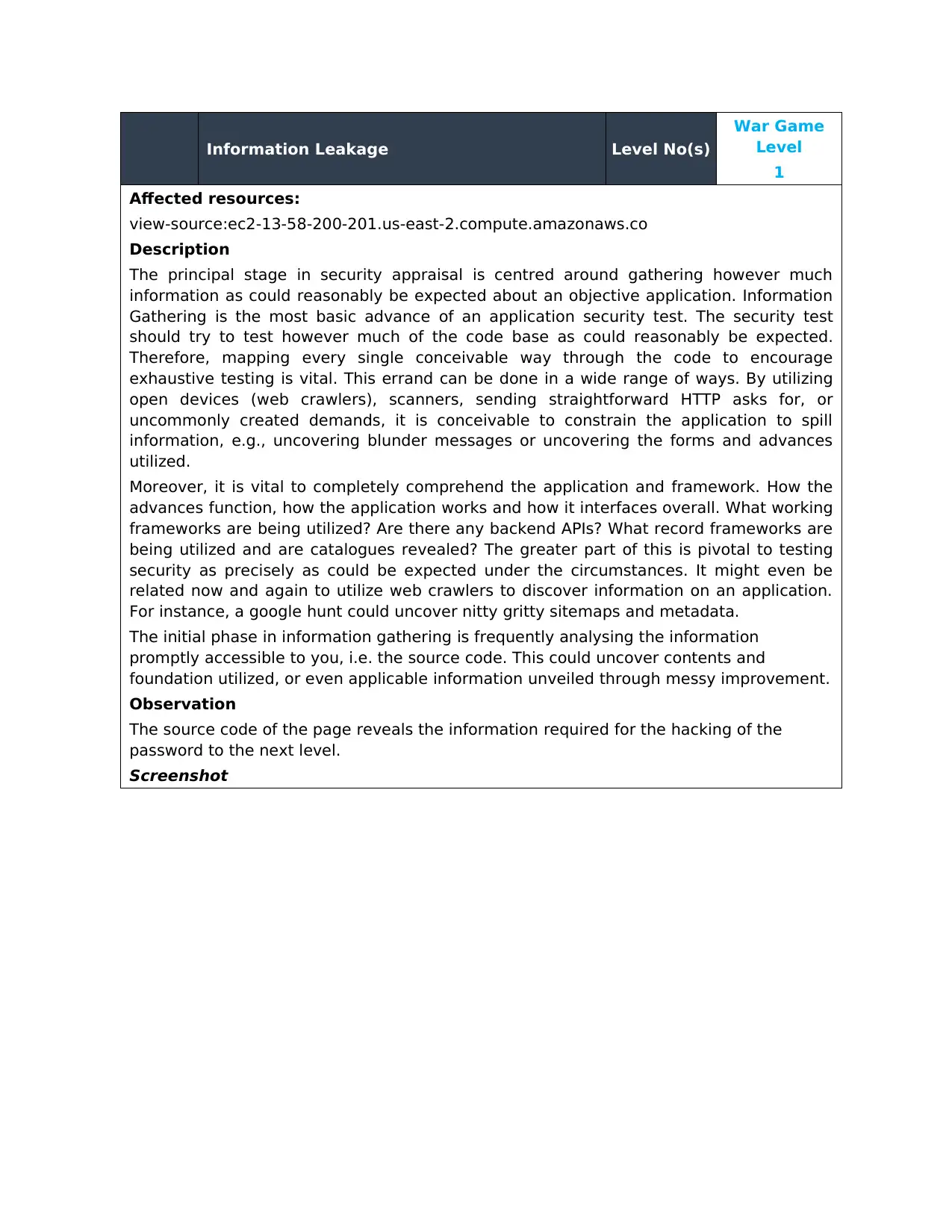
Affected resources:
view-source:ec2-13-58-200-201.us-east-2.compute.amazonaws.co
Description
The principal stage in security appraisal is centred around gathering however much
information as could reasonably be expected about an objective application. Information
Gathering is the most basic advance of an application security test. The security test
should try to test however much of the code base as could reasonably be expected.
Therefore, mapping every single conceivable way through the code to encourage
exhaustive testing is vital. This errand can be done in a wide range of ways. By utilizing
open devices (web crawlers), scanners, sending straightforward HTTP asks for, or
uncommonly created demands, it is conceivable to constrain the application to spill
information, e.g., uncovering blunder messages or uncovering the forms and advances
utilized.
Moreover, it is vital to completely comprehend the application and framework. How the
advances function, how the application works and how it interfaces overall. What working
frameworks are being utilized? Are there any backend APIs? What record frameworks are
being utilized and are catalogues revealed? The greater part of this is pivotal to testing
security as precisely as could be expected under the circumstances. It might even be
related now and again to utilize web crawlers to discover information on an application.
For instance, a google hunt could uncover nitty gritty sitemaps and metadata.
The initial phase in information gathering is frequently analysing the information
promptly accessible to you, i.e. the source code. This could uncover contents and
foundation utilized, or even applicable information unveiled through messy improvement.
Observation
The source code of the page reveals the information required for the hacking of the
password to the next level.
Screenshot
War Game
Level
1
Affected resources:
view-source:ec2-13-58-200-201.us-east-2.compute.amazonaws.co
Description
The principal stage in security appraisal is centred around gathering however much
information as could reasonably be expected about an objective application. Information
Gathering is the most basic advance of an application security test. The security test
should try to test however much of the code base as could reasonably be expected.
Therefore, mapping every single conceivable way through the code to encourage
exhaustive testing is vital. This errand can be done in a wide range of ways. By utilizing
open devices (web crawlers), scanners, sending straightforward HTTP asks for, or
uncommonly created demands, it is conceivable to constrain the application to spill
information, e.g., uncovering blunder messages or uncovering the forms and advances
utilized.
Moreover, it is vital to completely comprehend the application and framework. How the
advances function, how the application works and how it interfaces overall. What working
frameworks are being utilized? Are there any backend APIs? What record frameworks are
being utilized and are catalogues revealed? The greater part of this is pivotal to testing
security as precisely as could be expected under the circumstances. It might even be
related now and again to utilize web crawlers to discover information on an application.
For instance, a google hunt could uncover nitty gritty sitemaps and metadata.
The initial phase in information gathering is frequently analysing the information
promptly accessible to you, i.e. the source code. This could uncover contents and
foundation utilized, or even applicable information unveiled through messy improvement.
Observation
The source code of the page reveals the information required for the hacking of the
password to the next level.
Screenshot
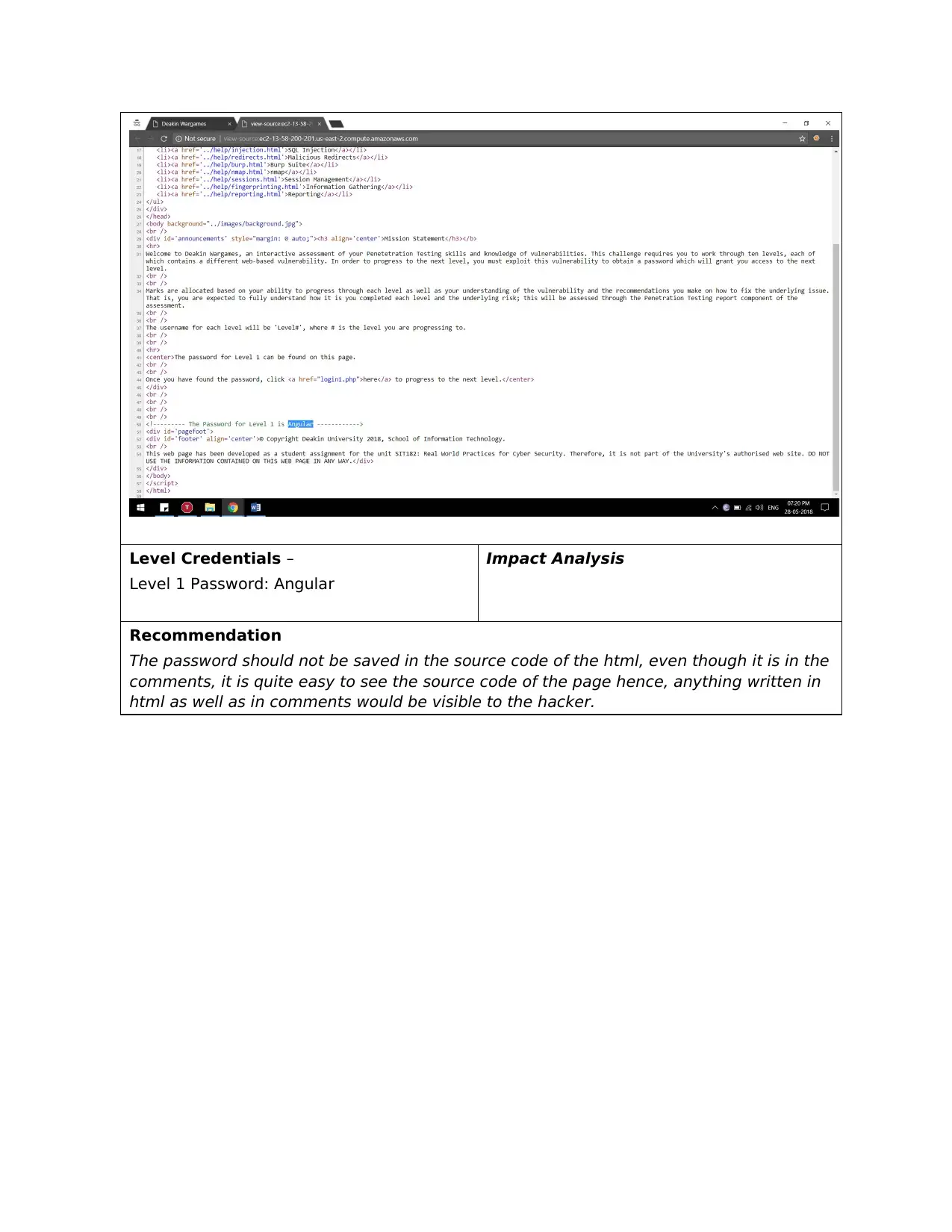
Level Credentials –
Level 1 Password: Angular
Impact Analysis
Recommendation
The password should not be saved in the source code of the html, even though it is in the
comments, it is quite easy to see the source code of the page hence, anything written in
html as well as in comments would be visible to the hacker.
Level 1 Password: Angular
Impact Analysis
Recommendation
The password should not be saved in the source code of the html, even though it is in the
comments, it is quite easy to see the source code of the page hence, anything written in
html as well as in comments would be visible to the hacker.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Information Leakage Level No(s)
War Game
Level
2
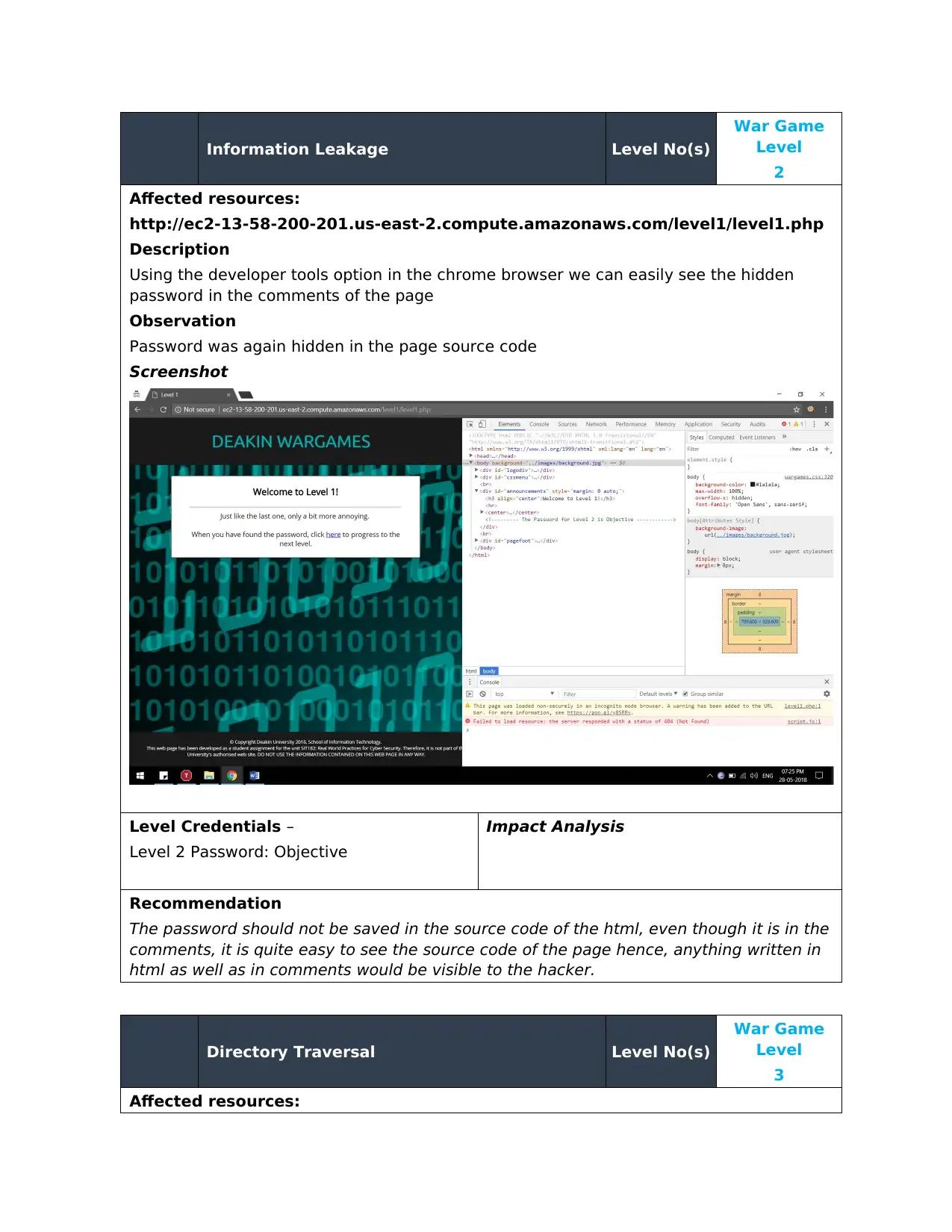
Affected resources:
http://ec2-13-58-200-201.us-east-2.compute.amazonaws.com/level1/level1.php
Description
Using the developer tools option in the chrome browser we can easily see the hidden
password in the comments of the page
Observation
Password was again hidden in the page source code
Screenshot
Level Credentials –
Level 2 Password: Objective
Impact Analysis
Recommendation
The password should not be saved in the source code of the html, even though it is in the
comments, it is quite easy to see the source code of the page hence, anything written in
html as well as in comments would be visible to the hacker.
Directory Traversal Level No(s)
War Game
Level
3
Affected resources:
War Game
Level
2
Affected resources:
http://ec2-13-58-200-201.us-east-2.compute.amazonaws.com/level1/level1.php
Description
Using the developer tools option in the chrome browser we can easily see the hidden
password in the comments of the page
Observation
Password was again hidden in the page source code
Screenshot
Level Credentials –
Level 2 Password: Objective
Impact Analysis
Recommendation
The password should not be saved in the source code of the html, even though it is in the
comments, it is quite easy to see the source code of the page hence, anything written in
html as well as in comments would be visible to the hacker.
Directory Traversal Level No(s)
War Game
Level
3
Affected resources:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

http://ec2-13-58-200-201.us-east-2.compute.amazonaws.com/level2/files/members.txt
Description
The password for this level is found using the directory traversal, we were easily able to
traverse to the different directory of the level. (Thangavel & Krishnan, 2010)
Observation
There was no security implemented so that no directory traversal should be allowed but
hacker can easily see all the files listed in the directory and traverse to find all the files
Screenshot
Level Credentials –
Level 3 Password: Misconfiguration
Impact Analysis
Recommendation
The directory traversal should not be allowed in anyone except the administrator no
other user should be allowed to have the directory traversal rights.
Description
The password for this level is found using the directory traversal, we were easily able to
traverse to the different directory of the level. (Thangavel & Krishnan, 2010)
Observation
There was no security implemented so that no directory traversal should be allowed but
hacker can easily see all the files listed in the directory and traverse to find all the files
Screenshot
Level Credentials –
Level 3 Password: Misconfiguration
Impact Analysis
Recommendation
The directory traversal should not be allowed in anyone except the administrator no
other user should be allowed to have the directory traversal rights.
Directory Traversal Level No(s)
War Game
Level
4
Affected resources:
http://ec2-13-58-200-201.us-east-2.compute.amazonaws.com/level2/passwords/level4password.php
Description
Again the user is allowed to traverse to different levels directory, hence it was quite easy
to check with giving the path to level 1 to level 2 to check for the access permission to
the level4password.php file (Prissette, n.d.)
Observation
The level2 was able to access the file and password was made visible. There is an
interesting thing, the level4 password can be bypass using the sql injection
attack using username as Level4 and password: ' or '1'='1
Screenshot
Level Credentials –
Level 4 Password: RedTeam
Impact Analysis
Recommendation
The password stored in files is an open invitation to hackers to traverse and find such
files, the password should not be saved in plaintext files as well as should not be
accessible in directory traversal.
Weak Encryption Level No(s) War Game
War Game
Level
4
Affected resources:
http://ec2-13-58-200-201.us-east-2.compute.amazonaws.com/level2/passwords/level4password.php
Description
Again the user is allowed to traverse to different levels directory, hence it was quite easy
to check with giving the path to level 1 to level 2 to check for the access permission to
the level4password.php file (Prissette, n.d.)
Observation
The level2 was able to access the file and password was made visible. There is an
interesting thing, the level4 password can be bypass using the sql injection
attack using username as Level4 and password: ' or '1'='1
Screenshot
Level Credentials –
Level 4 Password: RedTeam
Impact Analysis
Recommendation
The password stored in files is an open invitation to hackers to traverse and find such
files, the password should not be saved in plaintext files as well as should not be
accessible in directory traversal.
Weak Encryption Level No(s) War Game
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Level
5
Affected resources:
http://ec2-13-58-200-201.us-east-2.compute.amazonaws.com/level4/level4.php
Description
Cryptography is the act of utilizing systems and calculations for securing correspondence.
There are different types of cryptography, running from the utilization of keys in
Public/Private-key Cryptography, to figures or hashing capacities. We utilize these
techniques to encode correspondence, content and documents to guarantee just the
individuals who ought to get to this substance can do as such. Besides, Cryptography
enables us to screen information uprightness. (Vlsaggio & Blasio, 2010)
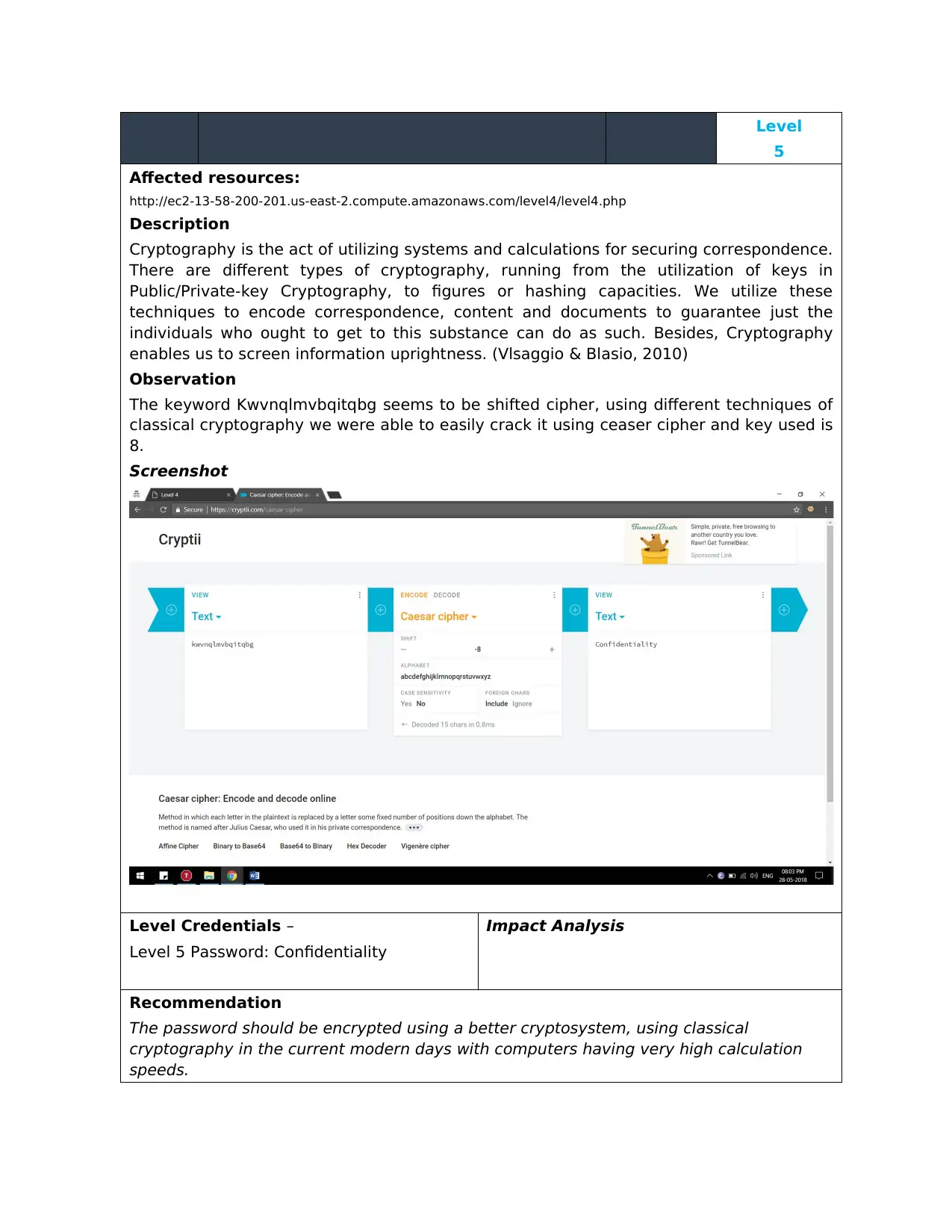
Observation
The keyword Kwvnqlmvbqitqbg seems to be shifted cipher, using different techniques of
classical cryptography we were able to easily crack it using ceaser cipher and key used is
8.
Screenshot
Level Credentials –
Level 5 Password: Confidentiality
Impact Analysis
Recommendation
The password should be encrypted using a better cryptosystem, using classical
cryptography in the current modern days with computers having very high calculation
speeds.
5
Affected resources:
http://ec2-13-58-200-201.us-east-2.compute.amazonaws.com/level4/level4.php
Description
Cryptography is the act of utilizing systems and calculations for securing correspondence.
There are different types of cryptography, running from the utilization of keys in
Public/Private-key Cryptography, to figures or hashing capacities. We utilize these
techniques to encode correspondence, content and documents to guarantee just the
individuals who ought to get to this substance can do as such. Besides, Cryptography
enables us to screen information uprightness. (Vlsaggio & Blasio, 2010)
Observation
The keyword Kwvnqlmvbqitqbg seems to be shifted cipher, using different techniques of
classical cryptography we were able to easily crack it using ceaser cipher and key used is
8.
Screenshot
Level Credentials –
Level 5 Password: Confidentiality
Impact Analysis
Recommendation
The password should be encrypted using a better cryptosystem, using classical
cryptography in the current modern days with computers having very high calculation
speeds.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Weak Encryption Level No(s)
War Game
Level
6
Affected resources:
http://ec2-13-58-200-201.us-east-2.compute.amazonaws.com/level5/level5.php
Description
The hash is provided in place of password, the hash is quite small hence we can easily
check it using pre-compiled hash values from various sources around the world.
(Tappenden & Miller, 2008)
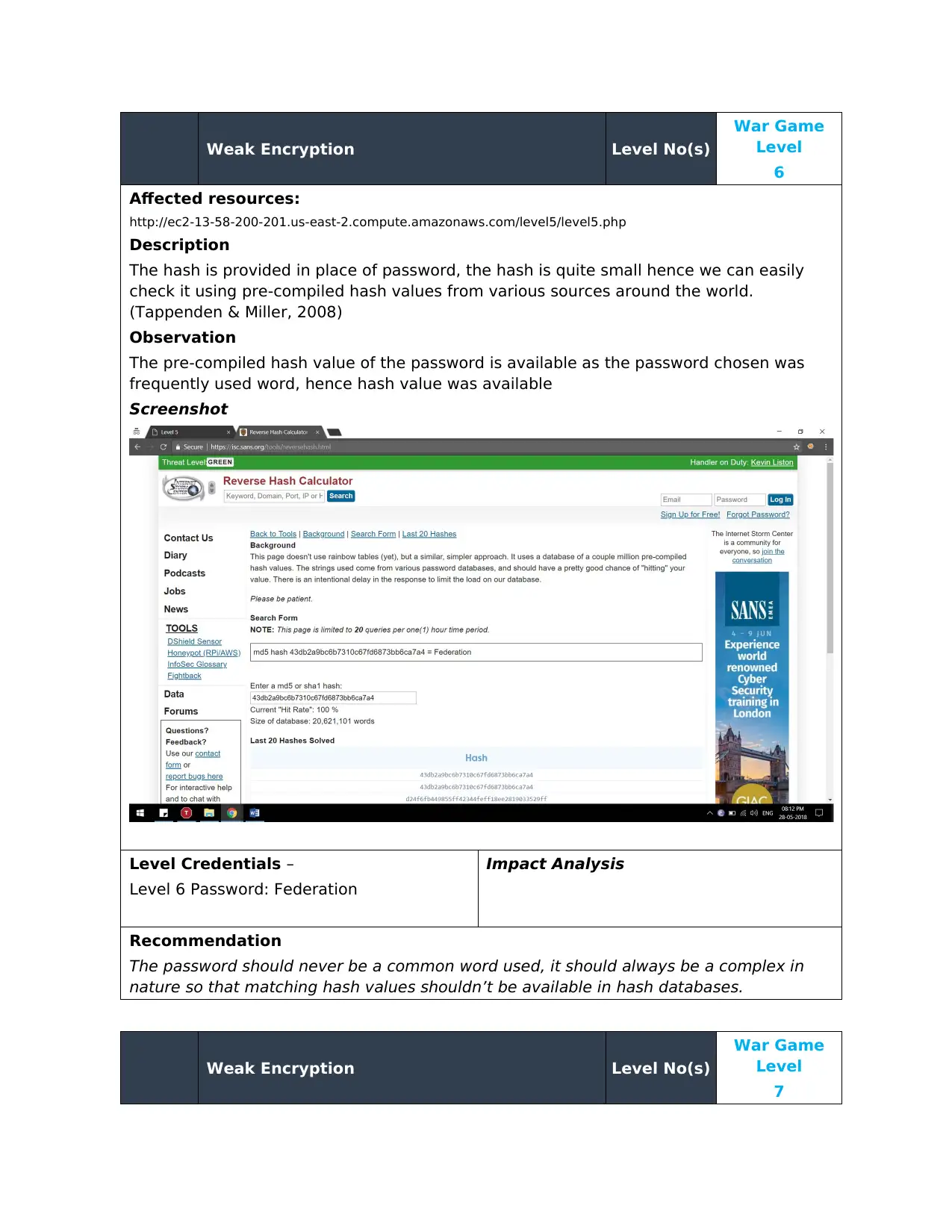
Observation
The pre-compiled hash value of the password is available as the password chosen was
frequently used word, hence hash value was available
Screenshot
Level Credentials –
Level 6 Password: Federation
Impact Analysis
Recommendation
The password should never be a common word used, it should always be a complex in
nature so that matching hash values shouldn’t be available in hash databases.
Weak Encryption Level No(s)
War Game
Level
7
War Game
Level
6
Affected resources:
http://ec2-13-58-200-201.us-east-2.compute.amazonaws.com/level5/level5.php
Description
The hash is provided in place of password, the hash is quite small hence we can easily
check it using pre-compiled hash values from various sources around the world.
(Tappenden & Miller, 2008)
Observation
The pre-compiled hash value of the password is available as the password chosen was
frequently used word, hence hash value was available
Screenshot
Level Credentials –
Level 6 Password: Federation
Impact Analysis
Recommendation
The password should never be a common word used, it should always be a complex in
nature so that matching hash values shouldn’t be available in hash databases.
Weak Encryption Level No(s)
War Game
Level
7

Affected resources:
http://ec2-13-58-200-201.us-east-2.compute.amazonaws.com/level6/level6.php
Description
The encryption used seems to be AES or 3DES as the key size is bigger than 32bytes
which is the limit for the DES algorithm.
Observation
The keys were encrypted using md5 and were encoded using base64, the “=” sign
represents the 256 bit string size.
Screenshot
Level Credentials –
Level 7 Password: used SQL injection
attack to bypass it ' or '1'='1
Impact Analysis
Recommendation
Sql injection attack mitigation methods should be used to secure the website
Session Management
TCP sessions are normally executed in programming utilizing youngster forms and additionally multithreading,
where another procedure or string is made when the PC sets up or joins a session. HTTP sessions are commonly not
executed utilizing one string for every session, but rather by methods for a database with information about the
condition of every session. The preferred standpoint with numerous procedures or strings is casual intricacy of the
product, since each string is an occurrence with its own particular history and typified factors. The detriment is
extensive overhead as far as framework assets, and that the session might be hindered if the framework is restarted.
At the point when a customer may interface with any server in a group of servers, an exceptional issue is
experienced in keeping up consistency when the servers must keep up session state. The customer should either be
coordinated to a similar server for the length of the session, or the servers must transmit server-side session
information by means of a mutual record framework or database. Something else, the customer may reconnect to an
unexpected server in comparison to the one it began the session with, which will cause issues when the new server
does not approach the put away condition of the old one. (Ayadi, Serhrouchni, Pujolle & Simoni, 2011)
The session ID or token ties the client confirmation qualifications (as a client session) to the client HTTP activity
and the suitable access controls implemented by the web application. (Ayadi, Serhrouchni, Pujolle & Simoni, 2011)
Besides, Cookies frequently assume a major part in session factors. The session ID trade component in view of
treats gives different security includes as treat properties that can be utilized to ensure the trading of the session ID.
Cookie Manipulation Level No(s) War Game
Level
http://ec2-13-58-200-201.us-east-2.compute.amazonaws.com/level6/level6.php
Description
The encryption used seems to be AES or 3DES as the key size is bigger than 32bytes
which is the limit for the DES algorithm.
Observation
The keys were encrypted using md5 and were encoded using base64, the “=” sign
represents the 256 bit string size.
Screenshot
Level Credentials –
Level 7 Password: used SQL injection
attack to bypass it ' or '1'='1
Impact Analysis
Recommendation
Sql injection attack mitigation methods should be used to secure the website
Session Management
TCP sessions are normally executed in programming utilizing youngster forms and additionally multithreading,
where another procedure or string is made when the PC sets up or joins a session. HTTP sessions are commonly not
executed utilizing one string for every session, but rather by methods for a database with information about the
condition of every session. The preferred standpoint with numerous procedures or strings is casual intricacy of the
product, since each string is an occurrence with its own particular history and typified factors. The detriment is
extensive overhead as far as framework assets, and that the session might be hindered if the framework is restarted.
At the point when a customer may interface with any server in a group of servers, an exceptional issue is
experienced in keeping up consistency when the servers must keep up session state. The customer should either be
coordinated to a similar server for the length of the session, or the servers must transmit server-side session
information by means of a mutual record framework or database. Something else, the customer may reconnect to an
unexpected server in comparison to the one it began the session with, which will cause issues when the new server
does not approach the put away condition of the old one. (Ayadi, Serhrouchni, Pujolle & Simoni, 2011)
The session ID or token ties the client confirmation qualifications (as a client session) to the client HTTP activity
and the suitable access controls implemented by the web application. (Ayadi, Serhrouchni, Pujolle & Simoni, 2011)
Besides, Cookies frequently assume a major part in session factors. The session ID trade component in view of
treats gives different security includes as treat properties that can be utilized to ensure the trading of the session ID.
Cookie Manipulation Level No(s) War Game
Level
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
8
Affected resources:
http://ec2-13-58-200-201.us-east-2.compute.amazonaws.com/level7/level7.php
Description
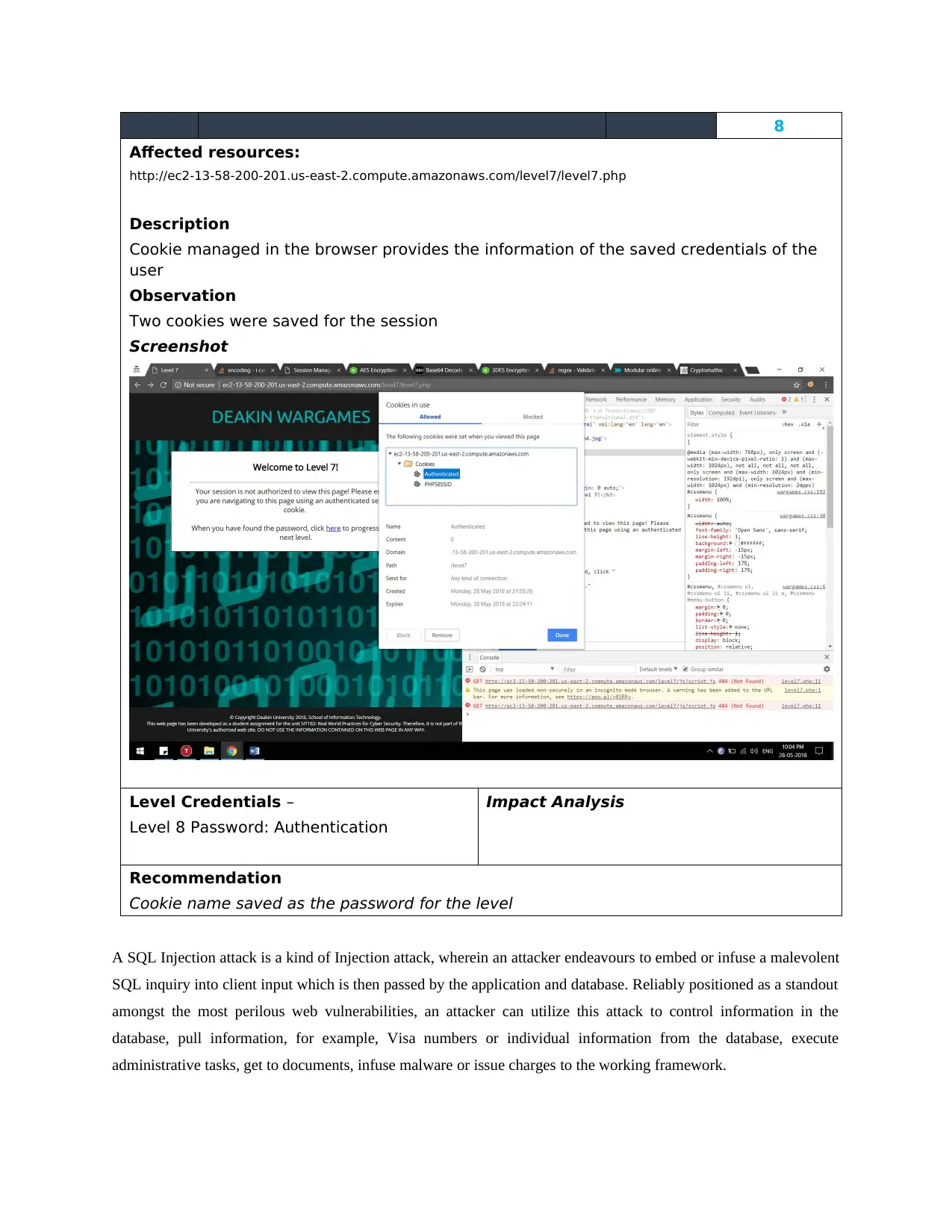
Cookie managed in the browser provides the information of the saved credentials of the
user
Observation
Two cookies were saved for the session
Screenshot
Level Credentials –
Level 8 Password: Authentication
Impact Analysis
Recommendation
Cookie name saved as the password for the level
A SQL Injection attack is a kind of Injection attack, wherein an attacker endeavours to embed or infuse a malevolent
SQL inquiry into client input which is then passed by the application and database. Reliably positioned as a standout
amongst the most perilous web vulnerabilities, an attacker can utilize this attack to control information in the
database, pull information, for example, Visa numbers or individual information from the database, execute
administrative tasks, get to documents, infuse malware or issue charges to the working framework.
Affected resources:
http://ec2-13-58-200-201.us-east-2.compute.amazonaws.com/level7/level7.php
Description
Cookie managed in the browser provides the information of the saved credentials of the
user
Observation
Two cookies were saved for the session
Screenshot
Level Credentials –
Level 8 Password: Authentication
Impact Analysis
Recommendation
Cookie name saved as the password for the level
A SQL Injection attack is a kind of Injection attack, wherein an attacker endeavours to embed or infuse a malevolent
SQL inquiry into client input which is then passed by the application and database. Reliably positioned as a standout
amongst the most perilous web vulnerabilities, an attacker can utilize this attack to control information in the
database, pull information, for example, Visa numbers or individual information from the database, execute
administrative tasks, get to documents, infuse malware or issue charges to the working framework.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The initial phase in this attack is recognizing where an application collaborates with a database; a few cases of this
would be a login page, enrolment page or when the URL gets to a specific document. The attack depends on the
application neglecting to accurately sterilize client input. For instance, there ought to be no motivation behind why a
solitary statement (') ought to be acknowledged as info. Most applications keep this through character encoding,
dark/white-posting or parametrised questions (pre-arranged articulations). Nonetheless, if an application does not
effectively disinfect client input, the addition of a solitary statement can disturb the SQL question running out of
sight; this is the initial phase in distinguishing this defencelessness.
A case of this could be in a sites look bar which will scan the site for a specific item. At the point when a client
composes something that will be looked on the site, regularly a SQL question will keep running out of sight along
the lines of SELECT name, value, portrayal FROM things WHERE name = 'Client INPUT HERE';. In the event that
we put a solitary statement in the inquiry bar, the question will execute as SELECT name, value, portrayal FROM
things WHERE name = ' ';. If not disinfected accurately this will create a SQL blunder, affirming the presence of the
defencelessness. Likewise, contingent upon the level of security set up, the SQL blunder could likewise uncover the
SQL inquiry being utilized; this makes it fundamentally less demanding to infuse a malignant SQL articulation.
Something else, experimentation is frequently utilized.
SQL Injection Level No(s)
War Game
Level
9
Affected resources:
http://ec2-13-58-200-201.us-east-2.compute.amazonaws.com/level9/level9.php
Description
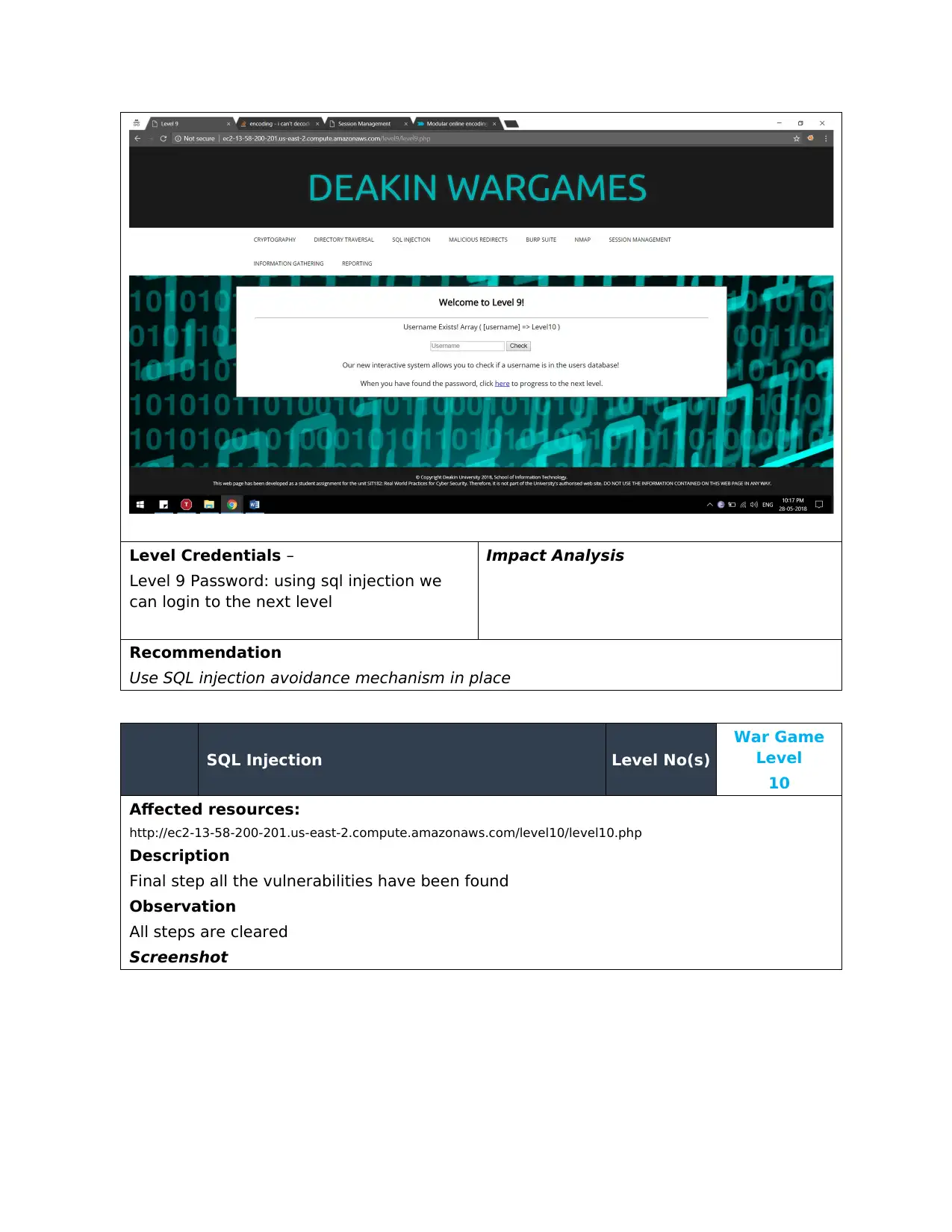
Using the ‘ or ‘1’ = ‘1 we get the Username Exists! Array as Level10.
Observation
Gave out the matching username on sql injection attack
Screenshot
would be a login page, enrolment page or when the URL gets to a specific document. The attack depends on the
application neglecting to accurately sterilize client input. For instance, there ought to be no motivation behind why a
solitary statement (') ought to be acknowledged as info. Most applications keep this through character encoding,
dark/white-posting or parametrised questions (pre-arranged articulations). Nonetheless, if an application does not
effectively disinfect client input, the addition of a solitary statement can disturb the SQL question running out of
sight; this is the initial phase in distinguishing this defencelessness.
A case of this could be in a sites look bar which will scan the site for a specific item. At the point when a client
composes something that will be looked on the site, regularly a SQL question will keep running out of sight along
the lines of SELECT name, value, portrayal FROM things WHERE name = 'Client INPUT HERE';. In the event that
we put a solitary statement in the inquiry bar, the question will execute as SELECT name, value, portrayal FROM
things WHERE name = ' ';. If not disinfected accurately this will create a SQL blunder, affirming the presence of the
defencelessness. Likewise, contingent upon the level of security set up, the SQL blunder could likewise uncover the
SQL inquiry being utilized; this makes it fundamentally less demanding to infuse a malignant SQL articulation.
Something else, experimentation is frequently utilized.
SQL Injection Level No(s)
War Game
Level
9
Affected resources:
http://ec2-13-58-200-201.us-east-2.compute.amazonaws.com/level9/level9.php
Description
Using the ‘ or ‘1’ = ‘1 we get the Username Exists! Array as Level10.
Observation
Gave out the matching username on sql injection attack
Screenshot
Level Credentials –
Level 9 Password: using sql injection we
can login to the next level
Impact Analysis
Recommendation
Use SQL injection avoidance mechanism in place
SQL Injection Level No(s)
War Game
Level
10
Affected resources:
http://ec2-13-58-200-201.us-east-2.compute.amazonaws.com/level10/level10.php
Description
Final step all the vulnerabilities have been found
Observation
All steps are cleared
Screenshot
Level 9 Password: using sql injection we
can login to the next level
Impact Analysis
Recommendation
Use SQL injection avoidance mechanism in place
SQL Injection Level No(s)
War Game
Level
10
Affected resources:
http://ec2-13-58-200-201.us-east-2.compute.amazonaws.com/level10/level10.php
Description
Final step all the vulnerabilities have been found
Observation
All steps are cleared
Screenshot
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


