Real-Time Analytics and the Emerging Data Breaches in Social Media
VerifiedAdded on 2022/11/30
|22
|4634
|243
Report
AI Summary
This report, titled "Real-Time Analytics and its Emerging Data Breaches in Social Media," delves into the critical intersection of real-time data analysis and the increasing threat of data breaches within social media platforms. The report begins with an abstract summarizing the key concepts and findings, followed by an introduction that outlines the scope, including discussions on big data privacy, the application of real-time analytics, its usage in social media, the effects of data breaches, the vulnerabilities in data privacy, and potential solutions. The report explores the importance of real-time analytics in marketing and business operations, including the ability to monitor performance, interact with customers, and gain insights into competitor activities. The report also addresses the challenges associated with real-time analytics, such as data security, privacy, and the legacy systems. The report further examines the impact of data breaches on businesses, including financial losses and erosion of trust. The report then presents a review of relevant literature, a description of the methodology used, and a discussion of the implications of the research. The report concludes with a summary of the main findings, emphasizing the importance of data security and the need for proactive measures to protect against cyber threats, including the use of strong passwords, data backup, and the implementation of robust IT security measures. The report provides examples like the Cambridge Analytica scandal, highlighting the vulnerability of data in the digital age and the need for constant vigilance.

Running head: STATISTICS 1
STATISTICS
Name
Institution
Professor
Course
Date
STATISTICS
Name
Institution
Professor
Course
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

STATISTICS 2
Real-Time Analytics and it’s Emerging Data Breaches in Social Media
1.0 Abstract
Real-time analytics is the process of data analysis done as the data is being released
therefore the user can conclude faster as soon as the data gets in their system. It is important in
marketing as it is possible to monitor how business is doing and adjust accordingly as data gets
in the system instead of waiting for aggregate data. A lot of businesses use social media sites
such as face book, twitter, Instagram among others to market their goods and services. This has
been essential as it is a quick way for customers to know whether the goods and services they
want to buy are available without waiting for a long period. Some of these business social media
sites can drive customers to your online motor stores to make purchases. Social media through
real-time analytics also allows interacting with customers making them loyal as they feel
involved in the business. Real-time analytics in social media is important in a business.
However, there are some challenges faced in real-time analytic in social media; sometimes real-
time social media analytics are ignored. Another challenge is that most businesses were
established a long time ago when data was hard to get taking a long time in gathering and
analysis. Establishing real-time analytic becomes impossible due to the existing bureaucracy.
The other challenge which is the greatest of all is cyber security. In conclusion, real-time
analytics in social media is important in business growth but dangerous if not well secured.
Table of Contents
1.0 Abstract 1
2.0 Introduction 2
2.1 Big data privacy 3
Real-Time Analytics and it’s Emerging Data Breaches in Social Media
1.0 Abstract
Real-time analytics is the process of data analysis done as the data is being released
therefore the user can conclude faster as soon as the data gets in their system. It is important in
marketing as it is possible to monitor how business is doing and adjust accordingly as data gets
in the system instead of waiting for aggregate data. A lot of businesses use social media sites
such as face book, twitter, Instagram among others to market their goods and services. This has
been essential as it is a quick way for customers to know whether the goods and services they
want to buy are available without waiting for a long period. Some of these business social media
sites can drive customers to your online motor stores to make purchases. Social media through
real-time analytics also allows interacting with customers making them loyal as they feel
involved in the business. Real-time analytics in social media is important in a business.
However, there are some challenges faced in real-time analytic in social media; sometimes real-
time social media analytics are ignored. Another challenge is that most businesses were
established a long time ago when data was hard to get taking a long time in gathering and
analysis. Establishing real-time analytic becomes impossible due to the existing bureaucracy.
The other challenge which is the greatest of all is cyber security. In conclusion, real-time
analytics in social media is important in business growth but dangerous if not well secured.
Table of Contents
1.0 Abstract 1
2.0 Introduction 2
2.1 Big data privacy 3

STATISTICS 3
2.3 Real-time analytics on big data 4
2.4 Real-time analytic usage in social media 5
2.5 Effect of the big data breach 6
2.6 How privacy is hampered 7
2.7 Problems 8
2.8 The possible solutions 9
3.0 Literature review 10
4.0 Methodology 11
5. 0 Discussion and implications of research 12
6.0 Conclusion 13
7.0 References 14
8.0 Appendices 15
2.0 Introduction
2.1 Big data privacy
Data privacy is an important key in big data analysts. It is the responsibility of the user to
make sure those there us transparency in data usage and collection. There the research will
discuss the huge issues related to data privacy in many of the companies. There are privacy
issues related to the risks of discrimination and bias (Akter & Wamba, 2016). Some of the fake
news interferes with the privacy of the data in big companies.
2.3 Real-time analytics on big data
2.3 Real-time analytics on big data 4
2.4 Real-time analytic usage in social media 5
2.5 Effect of the big data breach 6
2.6 How privacy is hampered 7
2.7 Problems 8
2.8 The possible solutions 9
3.0 Literature review 10
4.0 Methodology 11
5. 0 Discussion and implications of research 12
6.0 Conclusion 13
7.0 References 14
8.0 Appendices 15
2.0 Introduction
2.1 Big data privacy
Data privacy is an important key in big data analysts. It is the responsibility of the user to
make sure those there us transparency in data usage and collection. There the research will
discuss the huge issues related to data privacy in many of the companies. There are privacy
issues related to the risks of discrimination and bias (Akter & Wamba, 2016). Some of the fake
news interferes with the privacy of the data in big companies.
2.3 Real-time analytics on big data
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

STATISTICS 4
Real-time analytics is the analysis of data as soon as it enters the system. It is important
as conclusions can be drawn faster as the data gets in the system. Big data analytics examines
data in large amounts to identify hidden insights. The concept of real-time data analytics has
been around for years. Big data analytics brings about speed and efficiency (Williamson, 2016).
This ability of a business to work faster gives the organization a competitive edge that was not
there before. Big companies used big data analytics and got values in the following ways; Cost a
reduction which involves big data technologies such as Hadoop store large amounts of data
(Gandomi & Haider, 2015). Faster decision making of data is analyzed immediately; it is
possible to note where to adjust your business. New products and services as you gauge your
customers' needs you can give them what they want.
2.4 Real-time analytic usage in social media
Real-time analytics is used in social media to market goods in a business. This involves
creating social media platforms for your business (Cammack, 2015). Here, you get to keep in
touch with your customers and therefore improving the business where and when need be.
Involving the customers makes them loyal to your business as they feel like part of the business.
Customers give ideas for the growth of a business by asking for the things that they need (Perera,
Liu & Jayawardena, 2015). Real-time analytics also helps know how the competitor is doing.
This is important when running a business as you know your competitors’ prices, types of goods
and services they are offering and also the comments and responses they are getting from the
customers helping adjust accordingly.
2.5 Effect of the big data breach
Data breaches have a lot of negative effects on business. For starters, most of the
businesses that incur a data breach fail with the next three years after losing the data. Businesses
Real-time analytics is the analysis of data as soon as it enters the system. It is important
as conclusions can be drawn faster as the data gets in the system. Big data analytics examines
data in large amounts to identify hidden insights. The concept of real-time data analytics has
been around for years. Big data analytics brings about speed and efficiency (Williamson, 2016).
This ability of a business to work faster gives the organization a competitive edge that was not
there before. Big companies used big data analytics and got values in the following ways; Cost a
reduction which involves big data technologies such as Hadoop store large amounts of data
(Gandomi & Haider, 2015). Faster decision making of data is analyzed immediately; it is
possible to note where to adjust your business. New products and services as you gauge your
customers' needs you can give them what they want.
2.4 Real-time analytic usage in social media
Real-time analytics is used in social media to market goods in a business. This involves
creating social media platforms for your business (Cammack, 2015). Here, you get to keep in
touch with your customers and therefore improving the business where and when need be.
Involving the customers makes them loyal to your business as they feel like part of the business.
Customers give ideas for the growth of a business by asking for the things that they need (Perera,
Liu & Jayawardena, 2015). Real-time analytics also helps know how the competitor is doing.
This is important when running a business as you know your competitors’ prices, types of goods
and services they are offering and also the comments and responses they are getting from the
customers helping adjust accordingly.
2.5 Effect of the big data breach
Data breaches have a lot of negative effects on business. For starters, most of the
businesses that incur a data breach fail with the next three years after losing the data. Businesses
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
STATISTICS 5
invest a lot of money and to ensure the smooth running of their social media and online sites but
once the breach occurs, all that time and money becomes worthless. It also takes a lot of time and
effort to rebuild trust among all stakeholders in business after a data breach (Mackey & Nayyar,
2017). Lack of trust among the employees, the employers and other stakeholders in a business
can lead to the failure of a business. These cyber thieves often use viruses such as Storm Worm
and WannaCry.
Figure 1: Data privacy
Resource:https://static.cambridge.org/binary/version/id/
urn:cambridge.org:id:binary:20180418053412948-0830:9781316838952:17963figu7_1.png?
pub-status=live
2.6 How privacy is hampered
There is several privacy hampering factors on the real-time analytics data breach. The
amount of data that is stored online is growing at an unprecedented rate exceeding even the
growth of the economy by approximately four times. He suggests that we generate about 16.3
invest a lot of money and to ensure the smooth running of their social media and online sites but
once the breach occurs, all that time and money becomes worthless. It also takes a lot of time and
effort to rebuild trust among all stakeholders in business after a data breach (Mackey & Nayyar,
2017). Lack of trust among the employees, the employers and other stakeholders in a business
can lead to the failure of a business. These cyber thieves often use viruses such as Storm Worm
and WannaCry.
Figure 1: Data privacy
Resource:https://static.cambridge.org/binary/version/id/
urn:cambridge.org:id:binary:20180418053412948-0830:9781316838952:17963figu7_1.png?
pub-status=live
2.6 How privacy is hampered
There is several privacy hampering factors on the real-time analytics data breach. The
amount of data that is stored online is growing at an unprecedented rate exceeding even the
growth of the economy by approximately four times. He suggests that we generate about 16.3

STATISTICS 6
zettabytes of data per year and by the year 2025 that will increase to 163 zettabytes (Sahay &
Ranjan, 2018). According to an article by Nick Layzel, nearly half of all the businesses in the
UK have reported at least one data breach in the last year. The risk of being targeted by
cybercriminals seems to be directly proportional to the size of the business. Large businesses are
at a higher risk of being breached with a percentage of approximately 68% (John, 2015).
2.7 Problems
Data breaches are dangerous as one can lose or compromise customers’ information. In
the infamous Equifax data breach that happened between May and July 2017, the cyber criminals
accessed personal information of around 800,000 consumers. This scares people from engaging
in businesses that involve storing large amounts of private data. Data breaches might not be
completely eradicated however; there are some ways through which the breaches could be
reduced. One of the ways is by limiting access to data. In most organizations, a lot of employees
can access the data anytime they want without necessarily having someone to monitor what they
do with the data. This makes it hard to identify the source of a data breach once it occurs since a
lot of people could have accessed it (Wedel & Kannan, 2016). The solution to this is limiting the
data accesses to a very small group with high clearance in the organization. This is good as the
CEOs or the supervisor can keep a record of the people that accessed the data and the type that
they accessed (Schwartz & Janger, 2016). The server rooms should be kept locked with a lock
that uses smart cards so that it may record the details of the person accessing the data and also
the time they accessed it. The other way of reducing data breaches is by identifying sensitive
data. This is important as the company or organization will ensure it has the right tool and
conditions to store the most important data. The sensitive data might account for less than 20%
zettabytes of data per year and by the year 2025 that will increase to 163 zettabytes (Sahay &
Ranjan, 2018). According to an article by Nick Layzel, nearly half of all the businesses in the
UK have reported at least one data breach in the last year. The risk of being targeted by
cybercriminals seems to be directly proportional to the size of the business. Large businesses are
at a higher risk of being breached with a percentage of approximately 68% (John, 2015).
2.7 Problems
Data breaches are dangerous as one can lose or compromise customers’ information. In
the infamous Equifax data breach that happened between May and July 2017, the cyber criminals
accessed personal information of around 800,000 consumers. This scares people from engaging
in businesses that involve storing large amounts of private data. Data breaches might not be
completely eradicated however; there are some ways through which the breaches could be
reduced. One of the ways is by limiting access to data. In most organizations, a lot of employees
can access the data anytime they want without necessarily having someone to monitor what they
do with the data. This makes it hard to identify the source of a data breach once it occurs since a
lot of people could have accessed it (Wedel & Kannan, 2016). The solution to this is limiting the
data accesses to a very small group with high clearance in the organization. This is good as the
CEOs or the supervisor can keep a record of the people that accessed the data and the type that
they accessed (Schwartz & Janger, 2016). The server rooms should be kept locked with a lock
that uses smart cards so that it may record the details of the person accessing the data and also
the time they accessed it. The other way of reducing data breaches is by identifying sensitive
data. This is important as the company or organization will ensure it has the right tool and
conditions to store the most important data. The sensitive data might account for less than 20%
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

STATISTICS 7
but when lost a company can incur a lot of losses. When the sensitive data is well protected this
will give more labor force and resources to protect the other data from breaches.
2.8 The possible solutions
Citing an example from the Cambridge Analytica scandal for Trump Campaign there was
data breach resulting in his wine. Concerning the trump campaign scandal reported by
Cambridge, analytica shown in Netflix on deep fake software which was used to manipulate the
videos to grasp the people’s minds was a major breach of the data (Sundberg, 2018). The data
interfered and the polling server could have a predicted error against his opponents in the
election (Kato, 2017). Prep-planning on data security policy is also an important way towards
protecting the data from breaching. This helps in knowing the procedure to follow at a time when
under attack by cybercriminals (Seidl, 2016). It helps react to prevent extreme losses of data
during an attack. By access management, it is easier to know which user in the organization
could have been affected by the breach. The data security policies have to be updated as
technology is always changing. It would be better if people were employed to check whether
there are updates and upgrade the policies if need be to keep them relevant.
but when lost a company can incur a lot of losses. When the sensitive data is well protected this
will give more labor force and resources to protect the other data from breaches.
2.8 The possible solutions
Citing an example from the Cambridge Analytica scandal for Trump Campaign there was
data breach resulting in his wine. Concerning the trump campaign scandal reported by
Cambridge, analytica shown in Netflix on deep fake software which was used to manipulate the
videos to grasp the people’s minds was a major breach of the data (Sundberg, 2018). The data
interfered and the polling server could have a predicted error against his opponents in the
election (Kato, 2017). Prep-planning on data security policy is also an important way towards
protecting the data from breaching. This helps in knowing the procedure to follow at a time when
under attack by cybercriminals (Seidl, 2016). It helps react to prevent extreme losses of data
during an attack. By access management, it is easier to know which user in the organization
could have been affected by the breach. The data security policies have to be updated as
technology is always changing. It would be better if people were employed to check whether
there are updates and upgrade the policies if need be to keep them relevant.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

STATISTICS 8
Figure 2: Data privacy solutions
Resource: https://www.imd.org/contentassets/34690ac7e61a4bc69c3f5a7fbf4c8794/privacy-by-
design-strategies.jpg
Sensitive data should be locked away with strong passwords. Strong passwords make it
harder for hackers to access sensitive data. It is advisable to include different characters in your
passwords to make them stronger. The character should involve alphabets, numbers, symbols
and capital letters to make it a bit more complicated for hackers (Wishart, 2019). Also, it is not
advisable to use the same passwords for different departments and serves as the hackers might
try the password they cracked to access all the other servers. Some tools can be used to change
the password from time to time and also make them strong (Lupton & Williamson, 2017).
Besides, the Security use of smartcards and biometrics is very helpful when it comes to the
protection of data, especially important and sensitive ones.
Data should be backed up regularly to avoid losses. This can be done daily or weekly
depending on the resources of the organization. The data should also be protected using antivirus
Figure 2: Data privacy solutions
Resource: https://www.imd.org/contentassets/34690ac7e61a4bc69c3f5a7fbf4c8794/privacy-by-
design-strategies.jpg
Sensitive data should be locked away with strong passwords. Strong passwords make it
harder for hackers to access sensitive data. It is advisable to include different characters in your
passwords to make them stronger. The character should involve alphabets, numbers, symbols
and capital letters to make it a bit more complicated for hackers (Wishart, 2019). Also, it is not
advisable to use the same passwords for different departments and serves as the hackers might
try the password they cracked to access all the other servers. Some tools can be used to change
the password from time to time and also make them strong (Lupton & Williamson, 2017).
Besides, the Security use of smartcards and biometrics is very helpful when it comes to the
protection of data, especially important and sensitive ones.
Data should be backed up regularly to avoid losses. This can be done daily or weekly
depending on the resources of the organization. The data should also be protected using antivirus
STATISTICS 9
software that should be updated regularly. This can be attained by having an IT department that
is functioning in the organization. The IT department employees should be professionals. Data
breaches have caused the change in some good businesses to bad.
3.0 Literature review
Some of the affected organizations in the world as shown in include Target Stores in
December 2013. The breach was not noticed until several weeks later. The credit and debit card
information of 110 million people information was illegally accessed. The store announced that
it was hacked through a third-party HVAC vender to and the hackers had collected over 40
million numbers of credit and debit card numbers (Winn & Wrathall, 2017). By January 2014
personal identifiable information of over 70 million people had been compromised. Both the CIO
and the CEO of the company had to resign. The company had to agree to a settlement with its
customers and was given 180 days to improve its security. Strong passwords have been put into
place in the target stores to prevent another hacking in the future. The company has ensured
limited access to crucial data. They have continued assuring their customers that their data is
safely stored.
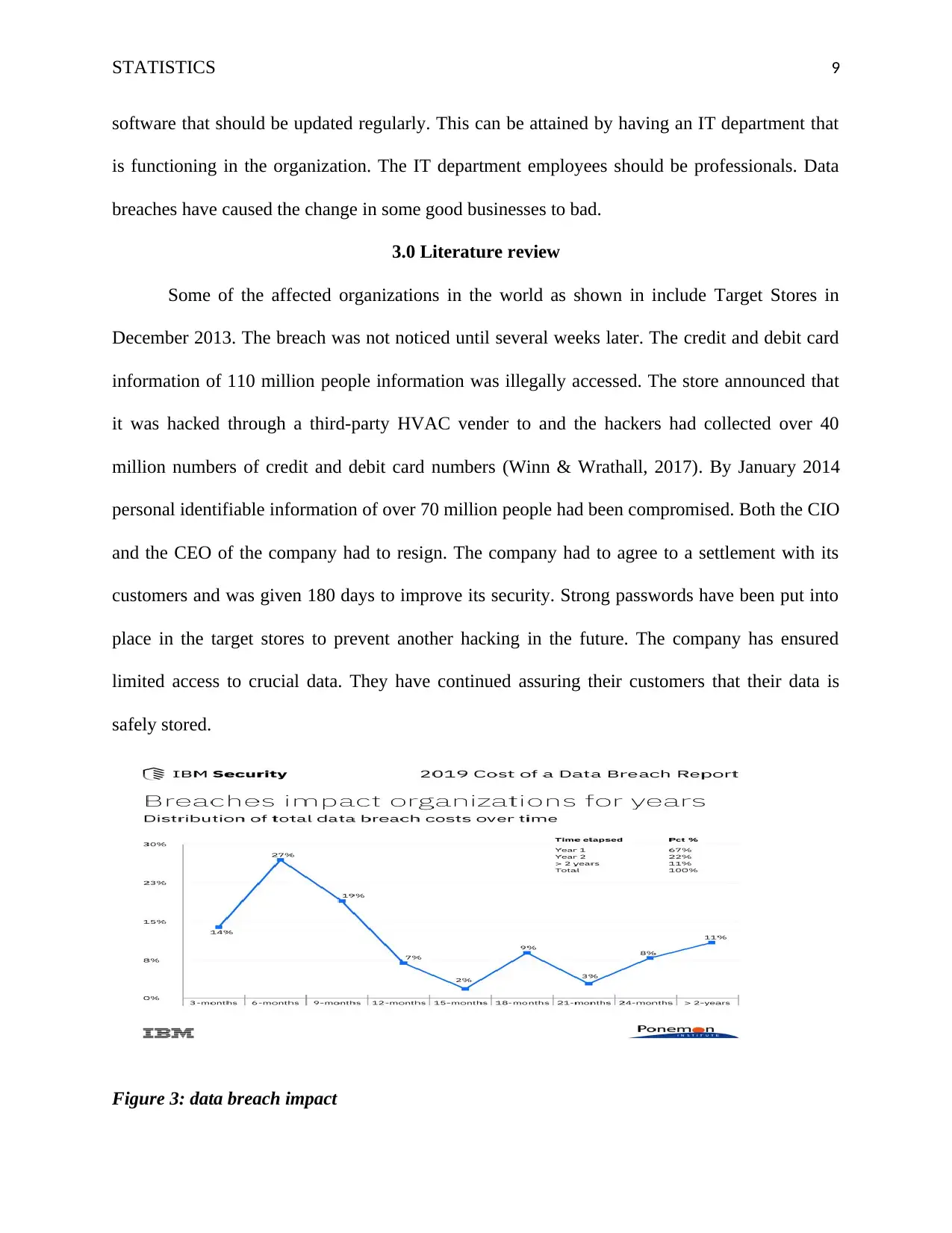
Figure 3: data breach impact
software that should be updated regularly. This can be attained by having an IT department that
is functioning in the organization. The IT department employees should be professionals. Data
breaches have caused the change in some good businesses to bad.
3.0 Literature review
Some of the affected organizations in the world as shown in include Target Stores in
December 2013. The breach was not noticed until several weeks later. The credit and debit card
information of 110 million people information was illegally accessed. The store announced that
it was hacked through a third-party HVAC vender to and the hackers had collected over 40
million numbers of credit and debit card numbers (Winn & Wrathall, 2017). By January 2014
personal identifiable information of over 70 million people had been compromised. Both the CIO
and the CEO of the company had to resign. The company had to agree to a settlement with its
customers and was given 180 days to improve its security. Strong passwords have been put into
place in the target stores to prevent another hacking in the future. The company has ensured
limited access to crucial data. They have continued assuring their customers that their data is
safely stored.
Figure 3: data breach impact
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

STATISTICS 10
Source: https://newsroom.ibm.com/download/Impact+of+Data+Breaches+Felt+for+Years.jpg
Another big data breach was uber in late 2016. This impacted to the exposing of personal
information of 57 million uber users and 600,000 drivers. The uber company did not make the
breach public until a year later. The company did not handle the situation as good as their
customers expected them to as they paid the hackers a hundred thousand dollars to destroy the
data without being sure whether the hackers destroyed the data. Some of the data compromised
were the customer’s addresses and their email addresses which are very sensitive data. This
resulted in the firing of the CSO Mr (Polonkey, 2016). Sullivan as he was blamed for the breach.
The public doesn’t know for sure whether Mr. Sullivan was responsible for the breach or not.
The breach cost the company a great deal in terms of reputation and money. At the time of the
incident, the company was in talks with Softbank. Its valuation dropped from $68 billion to $48
billion but not all the drop was as a result of the breach (Ritter, Wright, Casey & Mitchell, 2015).
Since the time of the incident, Uber Company has upgraded its cyber security to ensure no
unauthorized person can access the personal information of the customers, the drivers or the
company. Uber Company has frequently assured their service users that their information is safe
(Kitchin, 2017).
Another one of the victims of this problem is Marriott International. The hack took a
period of almost for years from 2014 to 2018. Data of about 500 million people were stolen. The
breach occurred on systems that supported Starwood hotel brands. Among the information that
was stolen were guest numbers, passport numbers, travel information, credit card numbers, and
other personal information (Mergel, Rethemeyer & Isett, 2016). The company is not certain
whether the credit cards were decrypted or not. The breach was later said to have been done by
Chinese intelligence to gather information about American citizens. If this is true, then this will
Source: https://newsroom.ibm.com/download/Impact+of+Data+Breaches+Felt+for+Years.jpg
Another big data breach was uber in late 2016. This impacted to the exposing of personal
information of 57 million uber users and 600,000 drivers. The uber company did not make the
breach public until a year later. The company did not handle the situation as good as their
customers expected them to as they paid the hackers a hundred thousand dollars to destroy the
data without being sure whether the hackers destroyed the data. Some of the data compromised
were the customer’s addresses and their email addresses which are very sensitive data. This
resulted in the firing of the CSO Mr (Polonkey, 2016). Sullivan as he was blamed for the breach.
The public doesn’t know for sure whether Mr. Sullivan was responsible for the breach or not.
The breach cost the company a great deal in terms of reputation and money. At the time of the
incident, the company was in talks with Softbank. Its valuation dropped from $68 billion to $48
billion but not all the drop was as a result of the breach (Ritter, Wright, Casey & Mitchell, 2015).
Since the time of the incident, Uber Company has upgraded its cyber security to ensure no
unauthorized person can access the personal information of the customers, the drivers or the
company. Uber Company has frequently assured their service users that their information is safe
(Kitchin, 2017).
Another one of the victims of this problem is Marriott International. The hack took a
period of almost for years from 2014 to 2018. Data of about 500 million people were stolen. The
breach occurred on systems that supported Starwood hotel brands. Among the information that
was stolen were guest numbers, passport numbers, travel information, credit card numbers, and
other personal information (Mergel, Rethemeyer & Isett, 2016). The company is not certain
whether the credit cards were decrypted or not. The breach was later said to have been done by
Chinese intelligence to gather information about American citizens. If this is true, then this will
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

STATISTICS 11
be the biggest data breach done by a nation. Adult Friend Finder also suffered a data breach in
October 2016. The breach affected more than 412.2 million accounts. Adult Friend Finder is an
online adult site where adults meet and hookup. Data collected for 20 years was breached. The
information included names, email addresses, and passwords. The passwords used to protect the
data were weak and easy to hack.
Figure 4: data breach factors
https://encrypted-tbn0.gstatic.com/images?q=tbn:ANd9GcTyxArbxk8eFnixpv5zAFcYA1jC-
2btGuhEhu9a8i8-OI5fik9W
The bank of Bangladesh was another organization affected by the big data breach which
led to a loss of $81 million in the year 2016. The hackers were suspected to be from South
Korea. The hackers breached the bank system by the use of the SWIFT network. They breached
the system in such a way that they sent the fraudulent money order transfer to the New York
branch in the United States of America central bank. Some of the money was connected to the
Casino system. This was one of the largest World Bank heist. This was a result of the data breach
be the biggest data breach done by a nation. Adult Friend Finder also suffered a data breach in
October 2016. The breach affected more than 412.2 million accounts. Adult Friend Finder is an
online adult site where adults meet and hookup. Data collected for 20 years was breached. The
information included names, email addresses, and passwords. The passwords used to protect the
data were weak and easy to hack.
Figure 4: data breach factors
https://encrypted-tbn0.gstatic.com/images?q=tbn:ANd9GcTyxArbxk8eFnixpv5zAFcYA1jC-
2btGuhEhu9a8i8-OI5fik9W
The bank of Bangladesh was another organization affected by the big data breach which
led to a loss of $81 million in the year 2016. The hackers were suspected to be from South
Korea. The hackers breached the bank system by the use of the SWIFT network. They breached
the system in such a way that they sent the fraudulent money order transfer to the New York
branch in the United States of America central bank. Some of the money was connected to the
Casino system. This was one of the largest World Bank heist. This was a result of the data breach

STATISTICS 12
which led to a loss of large amounts of money in the bank of Bangladesh (Rao Suma & Sunitha,
2015). Some of the cash was able to be recovered but unfortunately, the amount stolen through
the casino play was unable to be recovered. There are so many incidents in the world where
many companies and organizations daily. Besides, there are incidents daily where people lose a
lot of money through hacking and breaching of data. Online banking has been a major threat to
data breaches leading to a lot of challenges. It was reported that 30% of online transactions are
affected by fraud activities (Kusumoto, 2016). Some hackers develop hacking virus which
attacks the money transacting systems leading to the redirection of the money to other accounts.
What I'm proposing on emerging data breach
I am proposing that the organization dealing with vital and sensitive data should have
data protection mechanisms. Taking an example of the banks and other organizations handling
the public information I propose the use of the anti-hackers software. The software will add some
advantages to the organization as it will protect the information from reaching the wrong
individuals. This can be done through customization and installing of the powering security
software such as Absas.net. The implementation of the security software will enhance
protection of the individual data and organizational from being breached.
4.0 Methodology
In the study of the topic under discussion, there are different methods to be used. The
methods are based on the qualitative and quantitative aspects of research. The research on other
review articles will be the most appropriate procedure for research. The reports regarding the
required information based on the requirements of the research will be well analyzed. The
researchers will follow the already analyzed reports discussing the breach of big data. The
which led to a loss of large amounts of money in the bank of Bangladesh (Rao Suma & Sunitha,
2015). Some of the cash was able to be recovered but unfortunately, the amount stolen through
the casino play was unable to be recovered. There are so many incidents in the world where
many companies and organizations daily. Besides, there are incidents daily where people lose a
lot of money through hacking and breaching of data. Online banking has been a major threat to
data breaches leading to a lot of challenges. It was reported that 30% of online transactions are
affected by fraud activities (Kusumoto, 2016). Some hackers develop hacking virus which
attacks the money transacting systems leading to the redirection of the money to other accounts.
What I'm proposing on emerging data breach
I am proposing that the organization dealing with vital and sensitive data should have
data protection mechanisms. Taking an example of the banks and other organizations handling
the public information I propose the use of the anti-hackers software. The software will add some
advantages to the organization as it will protect the information from reaching the wrong
individuals. This can be done through customization and installing of the powering security
software such as Absas.net. The implementation of the security software will enhance
protection of the individual data and organizational from being breached.
4.0 Methodology
In the study of the topic under discussion, there are different methods to be used. The
methods are based on the qualitative and quantitative aspects of research. The research on other
review articles will be the most appropriate procedure for research. The reports regarding the
required information based on the requirements of the research will be well analyzed. The
researchers will follow the already analyzed reports discussing the breach of big data. The
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 22
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



