Analysis of IT System Issues at Red Star College: Solutions
VerifiedAdded on 2022/08/25
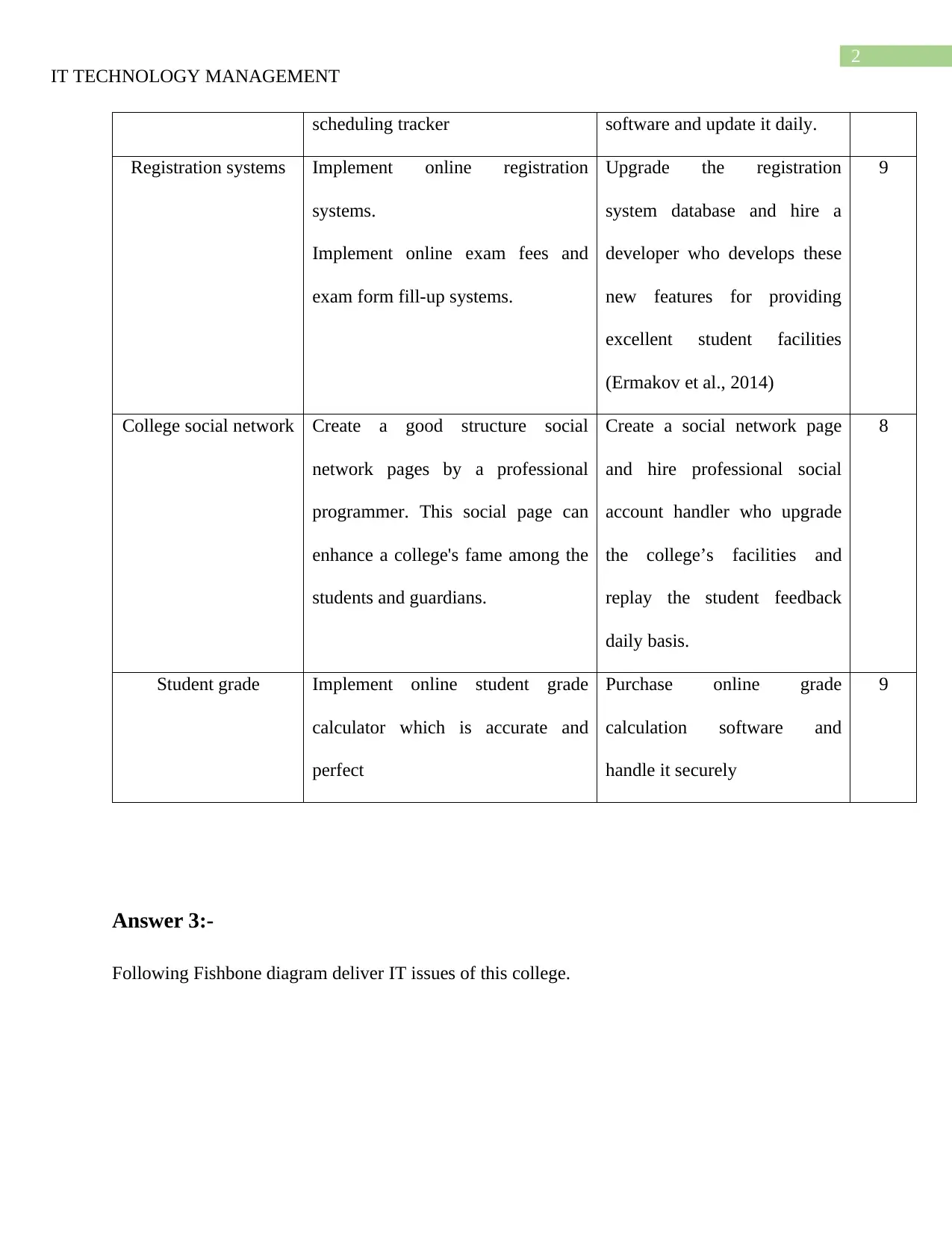
|5
|555
|28
Homework Assignment
AI Summary
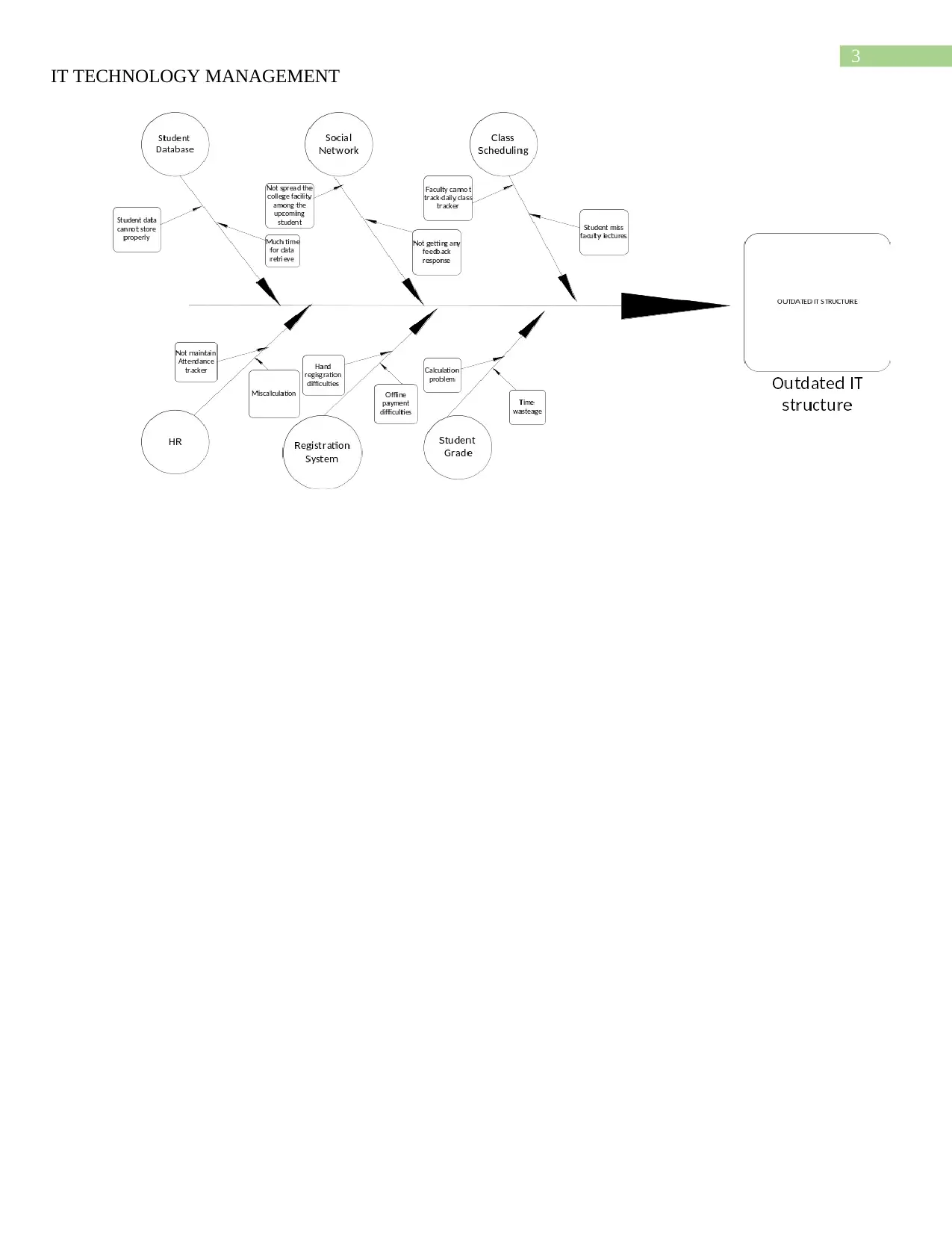
This assignment analyzes the outdated IT system of Red Star College, a private school facing significant challenges due to its 1995 IT infrastructure. The student addresses the college president's request by listing the crucial reasons for implementing a new IT system, emphasizing issues like an old database, security vulnerabilities, and the inability to meet student and faculty technical requirements. The solution then proposes a series of IT-related changes, including database upgrades, online class scheduling, registration systems, and social network enhancements, assigning a relative importance weight to each. The assignment highlights the need for a modern IT structure to improve database management, security, and overall operational efficiency. A Fishbone diagram is also included to illustrate the IT issues. The solution uses references to support the arguments and recommendations for the college.
1 out of 5






![[object Object]](/_next/static/media/star-bottom.7253800d.svg)