Risk Assessment and Mitigation for Regional Garden Ltd Data Center
VerifiedAdded on 2022/08/29
|7
|1151
|21
Report
AI Summary
This report presents a risk assessment conducted for the data center of Regional Garden Ltd, a gardening company with significant consumer and employee data. The assessment, performed by the Chief Information Officer, identifies key risks including data loss due to weak password protection, unauthorized access, network security vulnerabilities, data unavailability, and potential malware attacks. A detailed risk register outlines each risk, its description, likelihood, impact, proposed control strategies, and residual risk, alongside a risk matrix for visual representation. The report emphasizes the need for stronger security measures, including robust password policies, network segmentation, cloud storage for data backup, and updated anti-virus software. The conclusion highlights the organization's vulnerability and the importance of implementing the recommended control measures to safeguard its data and operations. The report references several sources related to risk management and information security.

Running head: RISK MANAGEMENT
Risk Management
Name of the Student:
Name of the University:
Student ID:
Subject Code:
Assessment Item Number and Name:
Lecturer Name:
Author note:
Risk Management
Name of the Student:
Name of the University:
Student ID:
Subject Code:
Assessment Item Number and Name:
Lecturer Name:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RISK ASSESSMENT
Table of Contents
Introduction:....................................................................................................................................2
Risk Assessment:.............................................................................................................................2
Risk Register:...............................................................................................................................2
Risk Matrix:.................................................................................................................................4
Explanation:.................................................................................................................................5
Conclusion:......................................................................................................................................5
References:......................................................................................................................................6
P a g e 1 | 7
Table of Contents
Introduction:....................................................................................................................................2
Risk Assessment:.............................................................................................................................2
Risk Register:...............................................................................................................................2
Risk Matrix:.................................................................................................................................4
Explanation:.................................................................................................................................5
Conclusion:......................................................................................................................................5
References:......................................................................................................................................6
P a g e 1 | 7
RISK ASSESSMENT
Introduction:
The Regional Garden Ltd is a gardening company taking care of several other gardening
enterprises. It also consists of a data centers which has several important data regarding the
consumers and the employees of the organization [1]. The company has currently appointed
Chief Information Officer to conduct the risk management assessment on the company’s data
center. The following report discusses about the risks that are associated with the data center of
the organization along with the impact and the mitigation techniques.
Risk Assessment:
The risk assessment is one of the most important step for an organization. This helps it to
develop an insight regarding the prevailing issues of the organization. The following risk register
shows the risks in the organization as determined by the CIO along with all necessary
information regarding that risk.
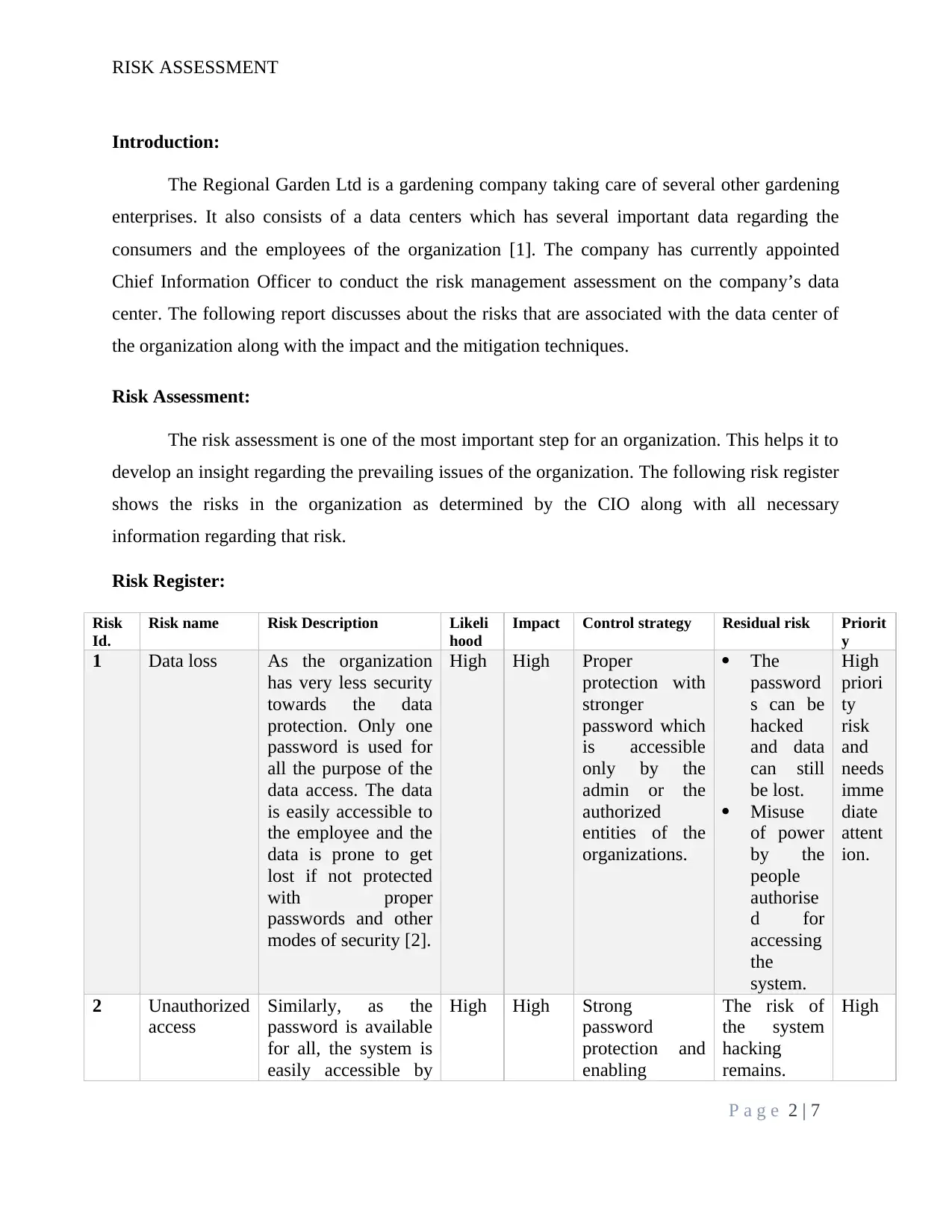
Risk Register:
Risk
Id.
Risk name Risk Description Likeli
hood
Impact Control strategy Residual risk Priorit
y
1 Data loss As the organization
has very less security
towards the data
protection. Only one
password is used for
all the purpose of the
data access. The data
is easily accessible to
the employee and the
data is prone to get
lost if not protected
with proper
passwords and other
modes of security [2].
High High Proper
protection with
stronger
password which
is accessible
only by the
admin or the
authorized
entities of the
organizations.
The
password
s can be
hacked
and data
can still
be lost.
Misuse
of power
by the
people
authorise
d for
accessing
the
system.
High
priori
ty
risk
and
needs
imme
diate
attent
ion.
2 Unauthorized
access
Similarly, as the
password is available
for all, the system is
easily accessible by
High High Strong
password
protection and
enabling
The risk of
the system
hacking
remains.
High
P a g e 2 | 7
Introduction:
The Regional Garden Ltd is a gardening company taking care of several other gardening
enterprises. It also consists of a data centers which has several important data regarding the
consumers and the employees of the organization [1]. The company has currently appointed
Chief Information Officer to conduct the risk management assessment on the company’s data
center. The following report discusses about the risks that are associated with the data center of
the organization along with the impact and the mitigation techniques.
Risk Assessment:
The risk assessment is one of the most important step for an organization. This helps it to
develop an insight regarding the prevailing issues of the organization. The following risk register
shows the risks in the organization as determined by the CIO along with all necessary
information regarding that risk.
Risk Register:
Risk
Id.
Risk name Risk Description Likeli
hood
Impact Control strategy Residual risk Priorit
y
1 Data loss As the organization
has very less security
towards the data
protection. Only one
password is used for
all the purpose of the
data access. The data
is easily accessible to
the employee and the
data is prone to get
lost if not protected
with proper
passwords and other
modes of security [2].
High High Proper
protection with
stronger
password which
is accessible
only by the
admin or the
authorized
entities of the
organizations.
The
password
s can be
hacked
and data
can still
be lost.
Misuse
of power
by the
people
authorise
d for
accessing
the
system.
High
priori
ty
risk
and
needs
imme
diate
attent
ion.
2 Unauthorized
access
Similarly, as the
password is available
for all, the system is
easily accessible by
High High Strong
password
protection and
enabling
The risk of
the system
hacking
remains.
High
P a g e 2 | 7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
RISK ASSESSMENT
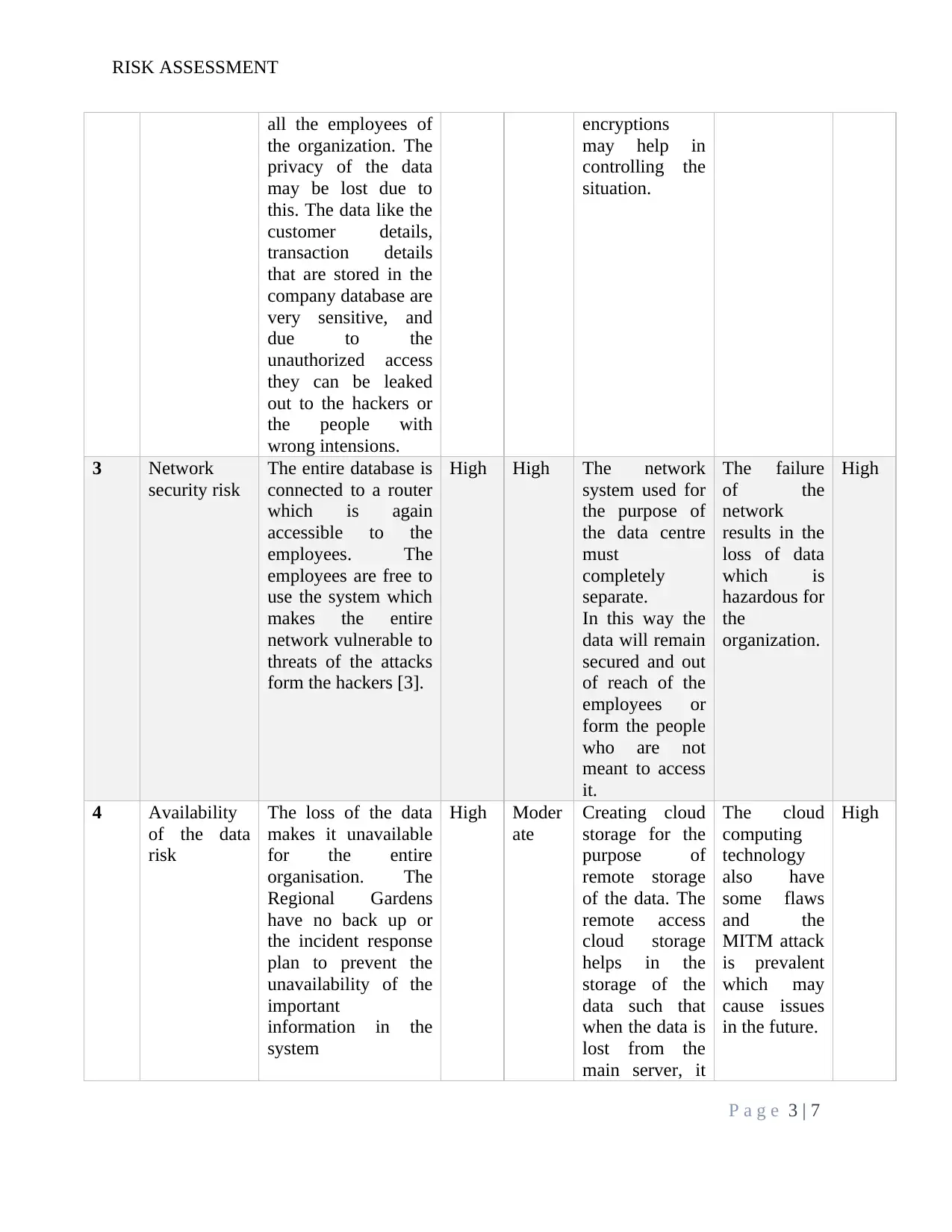
all the employees of
the organization. The
privacy of the data
may be lost due to
this. The data like the
customer details,
transaction details
that are stored in the
company database are
very sensitive, and
due to the
unauthorized access
they can be leaked
out to the hackers or
the people with
wrong intensions.
encryptions
may help in
controlling the
situation.
3 Network
security risk
The entire database is
connected to a router
which is again
accessible to the
employees. The
employees are free to
use the system which
makes the entire
network vulnerable to
threats of the attacks
form the hackers [3].
High High The network
system used for
the purpose of
the data centre
must
completely
separate.
In this way the
data will remain
secured and out
of reach of the
employees or
form the people
who are not
meant to access
it.
The failure
of the
network
results in the
loss of data
which is
hazardous for
the
organization.
High
4 Availability
of the data
risk
The loss of the data
makes it unavailable
for the entire
organisation. The
Regional Gardens
have no back up or
the incident response
plan to prevent the
unavailability of the
important
information in the
system
High Moder
ate
Creating cloud
storage for the
purpose of
remote storage
of the data. The
remote access
cloud storage
helps in the
storage of the
data such that
when the data is
lost from the
main server, it
The cloud
computing
technology
also have
some flaws
and the
MITM attack
is prevalent
which may
cause issues
in the future.
High
P a g e 3 | 7
all the employees of
the organization. The
privacy of the data
may be lost due to
this. The data like the
customer details,
transaction details
that are stored in the
company database are
very sensitive, and
due to the
unauthorized access
they can be leaked
out to the hackers or
the people with
wrong intensions.
encryptions
may help in
controlling the
situation.
3 Network
security risk
The entire database is
connected to a router
which is again
accessible to the
employees. The
employees are free to
use the system which
makes the entire
network vulnerable to
threats of the attacks
form the hackers [3].
High High The network
system used for
the purpose of
the data centre
must
completely
separate.
In this way the
data will remain
secured and out
of reach of the
employees or
form the people
who are not
meant to access
it.
The failure
of the
network
results in the
loss of data
which is
hazardous for
the
organization.
High
4 Availability
of the data
risk
The loss of the data
makes it unavailable
for the entire
organisation. The
Regional Gardens
have no back up or
the incident response
plan to prevent the
unavailability of the
important
information in the
system
High Moder
ate
Creating cloud
storage for the
purpose of
remote storage
of the data. The
remote access
cloud storage
helps in the
storage of the
data such that
when the data is
lost from the
main server, it
The cloud
computing
technology
also have
some flaws
and the
MITM attack
is prevalent
which may
cause issues
in the future.
High
P a g e 3 | 7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
RISK ASSESSMENT
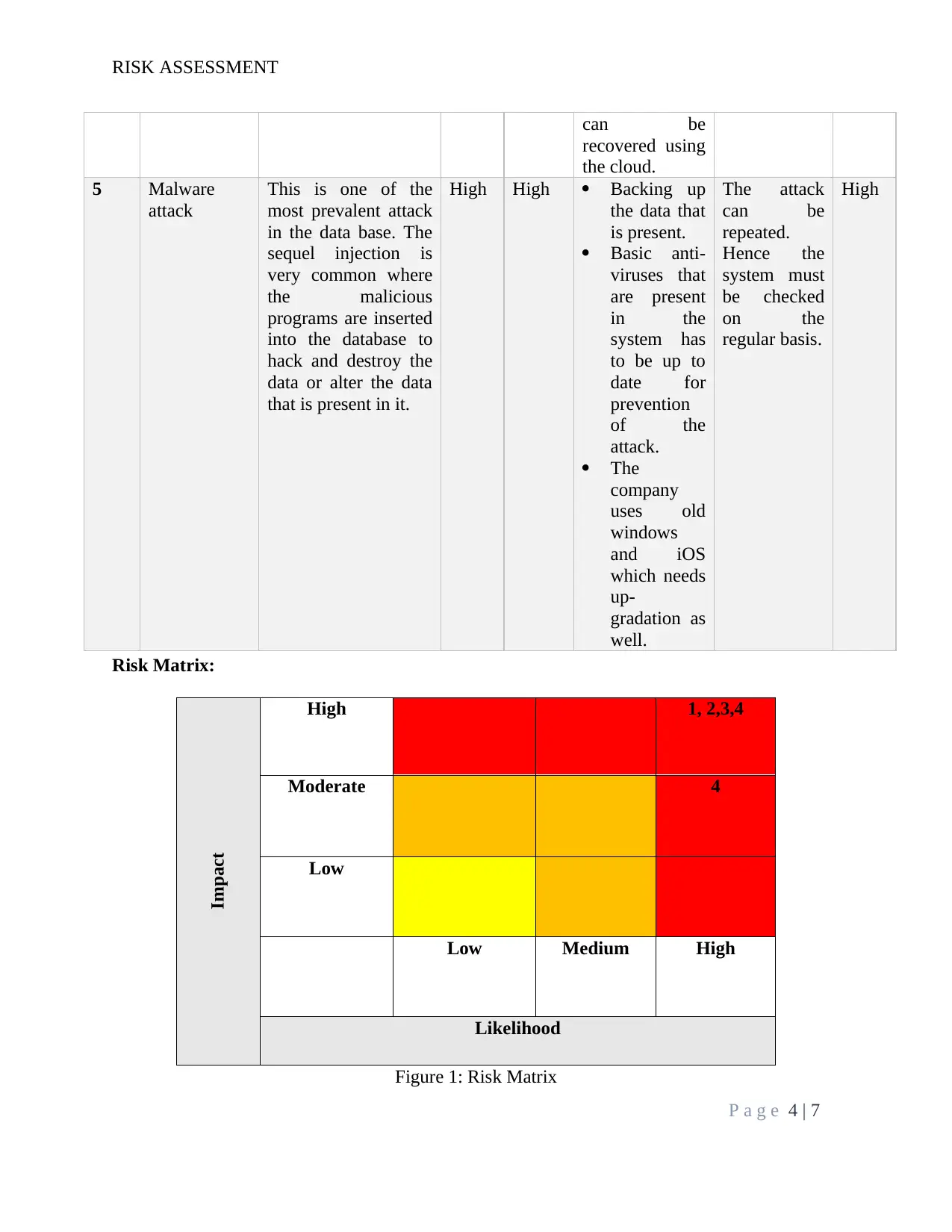
can be
recovered using
the cloud.
5 Malware
attack
This is one of the
most prevalent attack
in the data base. The
sequel injection is
very common where
the malicious
programs are inserted
into the database to
hack and destroy the
data or alter the data
that is present in it.
High High Backing up
the data that
is present.
Basic anti-
viruses that
are present
in the
system has
to be up to
date for
prevention
of the
attack.
The
company
uses old
windows
and iOS
which needs
up-
gradation as
well.
The attack
can be
repeated.
Hence the
system must
be checked
on the
regular basis.
High
Risk Matrix:Impact
High 1, 2,3,4
Moderate 4
Low
Low Medium High
Likelihood
Figure 1: Risk Matrix
P a g e 4 | 7
can be
recovered using
the cloud.
5 Malware
attack
This is one of the
most prevalent attack
in the data base. The
sequel injection is
very common where
the malicious
programs are inserted
into the database to
hack and destroy the
data or alter the data
that is present in it.
High High Backing up
the data that
is present.
Basic anti-
viruses that
are present
in the
system has
to be up to
date for
prevention
of the
attack.
The
company
uses old
windows
and iOS
which needs
up-
gradation as
well.
The attack
can be
repeated.
Hence the
system must
be checked
on the
regular basis.
High
Risk Matrix:Impact
High 1, 2,3,4
Moderate 4
Low
Low Medium High
Likelihood
Figure 1: Risk Matrix
P a g e 4 | 7

RISK ASSESSMENT
Explanation:
The Risk Id present in the risk register defines the serial number of the risk that
determined.
The Risk is the risk that is identified in the system.
The next column describes the risks that has been identified.
Likelihood is the frequency of the risk occurrence in the organization.
Impact is the intensity of the effect of risk on the organization.
The residual risk is the risk that remains even after the control techniques are defined in
the system [4].
The Priority of the risk states which risks have to be mitigated at the shortest notice else
can result to be hazardous for the organization.
Conclusion:
From the above report it can be said that the Regional Garden Ltd which have a data
center of its own, is vulnerable to various attacks due to its lack of up-dates and security. Thus
the risk assessment is performed on the system which has led the identification of the factors that
can cause the loss of data or many other problems to the organization. The control measures are
stated as well for mitigation of the risks that has been identified.
P a g e 5 | 7
Explanation:
The Risk Id present in the risk register defines the serial number of the risk that
determined.
The Risk is the risk that is identified in the system.
The next column describes the risks that has been identified.
Likelihood is the frequency of the risk occurrence in the organization.
Impact is the intensity of the effect of risk on the organization.
The residual risk is the risk that remains even after the control techniques are defined in
the system [4].
The Priority of the risk states which risks have to be mitigated at the shortest notice else
can result to be hazardous for the organization.
Conclusion:
From the above report it can be said that the Regional Garden Ltd which have a data
center of its own, is vulnerable to various attacks due to its lack of up-dates and security. Thus
the risk assessment is performed on the system which has led the identification of the factors that
can cause the loss of data or many other problems to the organization. The control measures are
stated as well for mitigation of the risks that has been identified.
P a g e 5 | 7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

RISK ASSESSMENT
References:
[1] R., Hoffmann, M., Kiedrowicz, & J., Stanik, Risk management system as the basic
paradigm of the information security management system in an organization, In MATEC
Web of Conferences (Vol. 76, p. 04010), EDP Sciences, (2016).
[2] R. L., Kliem, & I. S. Ludin, Reducing project risk, Routledge, (2019).
[3] K. A., Lewis, J., Tzilivakis, D. J., Warner, & A. Green, An international database for
pesticide risk assessments and management, Human and Ecological Risk Assessment: An
International Journal, 22(4), 1050-1064, (2016).
[4] T. R. Peltier, Information Security Policies, Procedures, and Standards: guidelines for
effective information security management, Auerbach Publications, (2016).
P a g e 6 | 7
References:
[1] R., Hoffmann, M., Kiedrowicz, & J., Stanik, Risk management system as the basic
paradigm of the information security management system in an organization, In MATEC
Web of Conferences (Vol. 76, p. 04010), EDP Sciences, (2016).
[2] R. L., Kliem, & I. S. Ludin, Reducing project risk, Routledge, (2019).
[3] K. A., Lewis, J., Tzilivakis, D. J., Warner, & A. Green, An international database for
pesticide risk assessments and management, Human and Ecological Risk Assessment: An
International Journal, 22(4), 1050-1064, (2016).
[4] T. R. Peltier, Information Security Policies, Procedures, and Standards: guidelines for
effective information security management, Auerbach Publications, (2016).
P a g e 6 | 7
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




