Regional Gardens: Hybrid Cloud Strategy - Architecture and Risks
VerifiedAdded on 2021/05/30
|14
|3015
|73
Report
AI Summary
This report provides a comprehensive analysis of Regional Gardens' hybrid cloud strategy. It begins with a description of cloud architecture, detailing the deployment of hybrid cloud architectures and examining both the benefits and issues associated with this model. The report then proceeds to a risk assessment, identifying potential risks and outlining corresponding control measures. Key aspects of information security are addressed, with a focus on recommended steps and controls to secure the hybrid cloud environment. Furthermore, the report offers specific recommendations for Regional Gardens' Business Continuity Plan (BCP), emphasizing the importance of incorporating both private and public cloud components. Finally, it outlines the requirements necessary for the successful implementation and management of a hybrid cloud model, ensuring that the organization can conduct remote server administration, resource management, and SLA management effectively. The report is a valuable resource for understanding and implementing a robust hybrid cloud strategy.

Running head: REGIONAL GARDENS: HYBRID CLOUD STRATEGY
Regional Gardens: Hybrid Cloud Strategy
Name of the Student
Name of the University
Author Note
Regional Gardens: Hybrid Cloud Strategy
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1REGIONAL GARDENS: HYBRID CLOUD STRATEGY
Table of Contents
1. Description of Cloud Architecture.....................................................................................2
A. Deployment of Hybrid Cloud architectures......................................................................2
B. Benefits and Issues............................................................................................................4
2. Risks Assessment...............................................................................................................5
3. Information Security steps and control..............................................................................7
4. Recommendation to Regional Garden’s BCP....................................................................8
5. Requirements......................................................................................................................9
6. Bibliography.....................................................................................................................11
Table of Contents
1. Description of Cloud Architecture.....................................................................................2
A. Deployment of Hybrid Cloud architectures......................................................................2
B. Benefits and Issues............................................................................................................4
2. Risks Assessment...............................................................................................................5
3. Information Security steps and control..............................................................................7
4. Recommendation to Regional Garden’s BCP....................................................................8
5. Requirements......................................................................................................................9
6. Bibliography.....................................................................................................................11
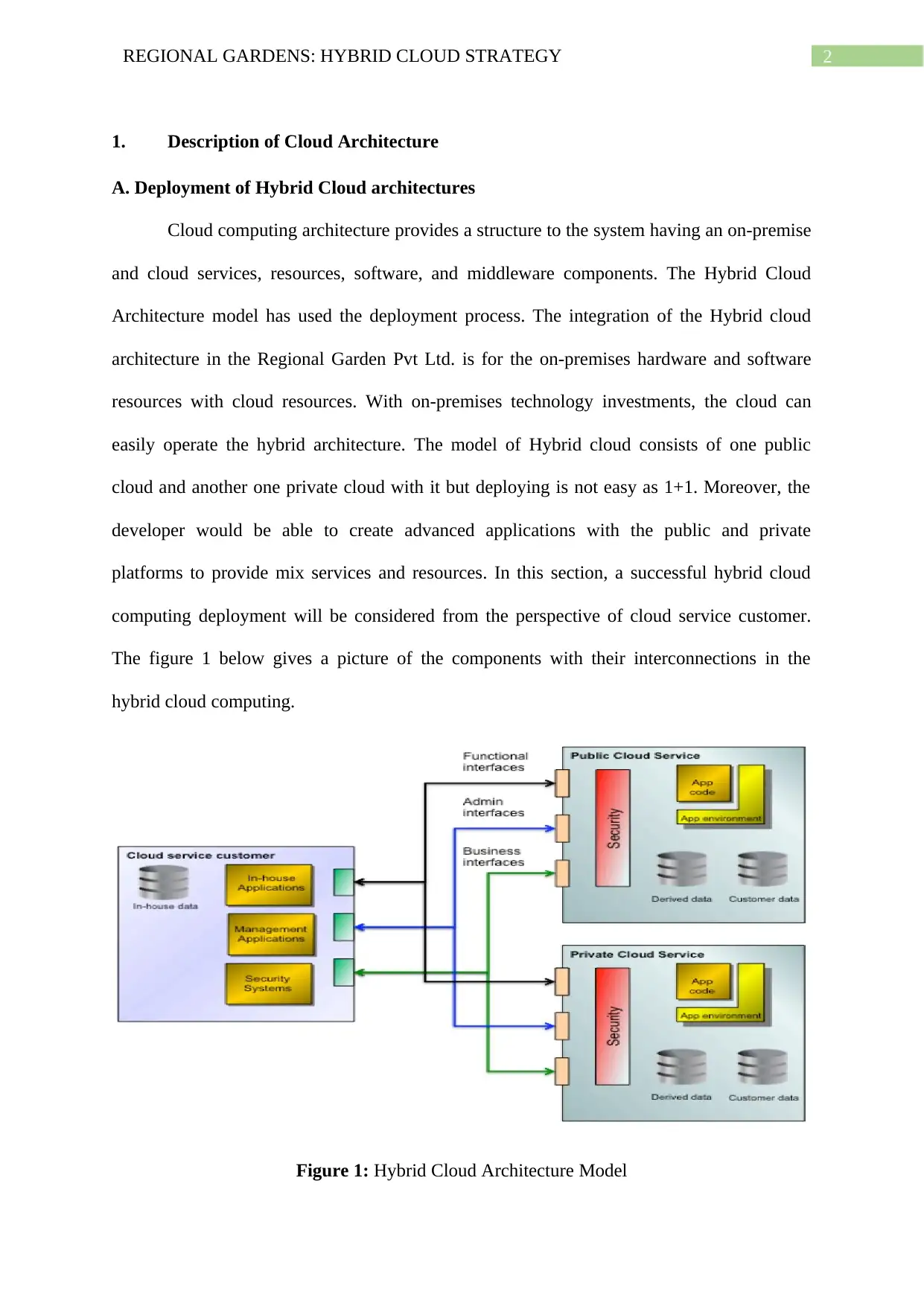
2REGIONAL GARDENS: HYBRID CLOUD STRATEGY
1. Description of Cloud Architecture
A. Deployment of Hybrid Cloud architectures
Cloud computing architecture provides a structure to the system having an on-premise
and cloud services, resources, software, and middleware components. The Hybrid Cloud
Architecture model has used the deployment process. The integration of the Hybrid cloud
architecture in the Regional Garden Pvt Ltd. is for the on-premises hardware and software
resources with cloud resources. With on-premises technology investments, the cloud can
easily operate the hybrid architecture. The model of Hybrid cloud consists of one public
cloud and another one private cloud with it but deploying is not easy as 1+1. Moreover, the
developer would be able to create advanced applications with the public and private
platforms to provide mix services and resources. In this section, a successful hybrid cloud
computing deployment will be considered from the perspective of cloud service customer.
The figure 1 below gives a picture of the components with their interconnections in the
hybrid cloud computing.
Figure 1: Hybrid Cloud Architecture Model
1. Description of Cloud Architecture
A. Deployment of Hybrid Cloud architectures
Cloud computing architecture provides a structure to the system having an on-premise
and cloud services, resources, software, and middleware components. The Hybrid Cloud
Architecture model has used the deployment process. The integration of the Hybrid cloud
architecture in the Regional Garden Pvt Ltd. is for the on-premises hardware and software
resources with cloud resources. With on-premises technology investments, the cloud can
easily operate the hybrid architecture. The model of Hybrid cloud consists of one public
cloud and another one private cloud with it but deploying is not easy as 1+1. Moreover, the
developer would be able to create advanced applications with the public and private
platforms to provide mix services and resources. In this section, a successful hybrid cloud
computing deployment will be considered from the perspective of cloud service customer.
The figure 1 below gives a picture of the components with their interconnections in the
hybrid cloud computing.
Figure 1: Hybrid Cloud Architecture Model
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3REGIONAL GARDENS: HYBRID CLOUD STRATEGY
Source: (Borrett, 2016)
The components that are a concern to the cloud service customer have been divided
into three groups. The first component is the customer’s in-house systems; the second
component is running in the private cloud services which can be either on-premises or off-
premises, and the third component is running in the public cloud services. Its architecture also
has three types of interfaces existing between the groups. One is the functional interfaces
used for the applications and services, and another one is the administration interfaces that
manage and control the application and services. The administration interfaces include
security administration, and the final one is the business interfaces that is used in managing
the billing, subscriptions and payments. When looked into the customer’s in-house systems, it
consists of the management application, in-house applications, in-house datasets and
databases and not last but the least is the security system. The app code is running the
applications within the cloud services in both the public and private cloud services including
its application environment, the logs having the customer data and derived data for both the
public and private cloud services and various components of security. The main concern
while deploying hybrid cloud is that it ensures the efficient and effective integration of the
components in all the three groups including the interfaces between them. Figure 2 below
gives a view of Hybrid cloud development model,
Figure 2: Hybrid Cloud Deployment Models
Source: (Borrett, 2016)
The components that are a concern to the cloud service customer have been divided
into three groups. The first component is the customer’s in-house systems; the second
component is running in the private cloud services which can be either on-premises or off-
premises, and the third component is running in the public cloud services. Its architecture also
has three types of interfaces existing between the groups. One is the functional interfaces
used for the applications and services, and another one is the administration interfaces that
manage and control the application and services. The administration interfaces include
security administration, and the final one is the business interfaces that is used in managing
the billing, subscriptions and payments. When looked into the customer’s in-house systems, it
consists of the management application, in-house applications, in-house datasets and
databases and not last but the least is the security system. The app code is running the
applications within the cloud services in both the public and private cloud services including
its application environment, the logs having the customer data and derived data for both the
public and private cloud services and various components of security. The main concern
while deploying hybrid cloud is that it ensures the efficient and effective integration of the
components in all the three groups including the interfaces between them. Figure 2 below
gives a view of Hybrid cloud development model,
Figure 2: Hybrid Cloud Deployment Models
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4REGIONAL GARDENS: HYBRID CLOUD STRATEGY
Source: (Rouse, 2018)
B. Benefits and Issues
Benefits to adopt Hybrid Cloud Model:
Cost Saving: The implementation of hybrid cloud is because of the cost savings. The
Regional Garden can leverage the public cloud services to offload the heavy usage and pay
only when required. Instead of spending money on building the infrastructure that bears the
occasional bursts in the usage of the system which happen only for a small fraction of the
time. When the cost is saved on building the infrastructure, then the organisation could
devote more of their funds to another critical project which will be helpful in moving the
business ahead.
Improve Security: Hybrid Cloud Computing model can offer better security for the
organisation than the traditional model in utilising it. The environment of the hybrid cloud
has deployed 45% of the application in cloud computing. With the use of hybrid cloud, the
number of application that has deployed into the cloud has expanded.
Enhanced agility: The Hybrid Cloud could leverage the public cloud that enhances the agility
at the time when the users are heavy when the user with less downtime experiences few
outages.
Greater accessibility: The employees of the Regional Garden organisation become mobile
with greater accessibility into their critical business application. Today the organisation can
make the work happen 24/7 days to have effective competition. With the cloud, employees
can easily access the data from anywhere and anytime.
Issues with the Model:
Source: (Rouse, 2018)
B. Benefits and Issues
Benefits to adopt Hybrid Cloud Model:
Cost Saving: The implementation of hybrid cloud is because of the cost savings. The
Regional Garden can leverage the public cloud services to offload the heavy usage and pay
only when required. Instead of spending money on building the infrastructure that bears the
occasional bursts in the usage of the system which happen only for a small fraction of the
time. When the cost is saved on building the infrastructure, then the organisation could
devote more of their funds to another critical project which will be helpful in moving the
business ahead.
Improve Security: Hybrid Cloud Computing model can offer better security for the
organisation than the traditional model in utilising it. The environment of the hybrid cloud
has deployed 45% of the application in cloud computing. With the use of hybrid cloud, the
number of application that has deployed into the cloud has expanded.
Enhanced agility: The Hybrid Cloud could leverage the public cloud that enhances the agility
at the time when the users are heavy when the user with less downtime experiences few
outages.
Greater accessibility: The employees of the Regional Garden organisation become mobile
with greater accessibility into their critical business application. Today the organisation can
make the work happen 24/7 days to have effective competition. With the cloud, employees
can easily access the data from anywhere and anytime.
Issues with the Model:
5REGIONAL GARDENS: HYBRID CLOUD STRATEGY
Data redundancy: Due to the complexity of the hybrid Cloud System, redundancy is needed
across the data centres to moderate the impact of an outage of single data centre otherwise the
risk of security can be serious when the copies of redundant data are distributed over the data
centre.
Compliance: It becomes difficult to maintain and demonstrate the compliance in the hybrid
cloud.
SLA poor construction: Both public and private cloud provider should meet the expectation
that is detailed in SLA and look into some potential problems of the public and private cloud
integration that has disrupted the services.
Risk Management: From the perspective of the business it is difficult to manage the risk.
Hybrid cloud has begun to use new Application Programming Interface (APIs) for complex
network configuration which introduces some new threats.
2. Risks Assessment
Risk Impact Control Measure
1 Compliance is Poor data moves back
and forth which
make difficult to
maintain and
demonstrate the
compliance
demonstrate that the
public and private cloud
provider comply to
Coordinate together
2 APIs are Unprotected sensitive data
are exposed to
malicious
attacks and
exploit
authentication
Handling the API keys
by third-party
developers and verify
the third-party before
the API keys are release
so that security breach
can be avoided
3 IP Protection is Poor security risk has
been identified
in the IP
identify the risk
associated with IP that
classifies the data, know
the source threats,
follow and develop a
detail threat model
Data redundancy: Due to the complexity of the hybrid Cloud System, redundancy is needed
across the data centres to moderate the impact of an outage of single data centre otherwise the
risk of security can be serious when the copies of redundant data are distributed over the data
centre.
Compliance: It becomes difficult to maintain and demonstrate the compliance in the hybrid
cloud.
SLA poor construction: Both public and private cloud provider should meet the expectation
that is detailed in SLA and look into some potential problems of the public and private cloud
integration that has disrupted the services.
Risk Management: From the perspective of the business it is difficult to manage the risk.
Hybrid cloud has begun to use new Application Programming Interface (APIs) for complex
network configuration which introduces some new threats.
2. Risks Assessment
Risk Impact Control Measure
1 Compliance is Poor data moves back
and forth which
make difficult to
maintain and
demonstrate the
compliance
demonstrate that the
public and private cloud
provider comply to
Coordinate together
2 APIs are Unprotected sensitive data
are exposed to
malicious
attacks and
exploit
authentication
Handling the API keys
by third-party
developers and verify
the third-party before
the API keys are release
so that security breach
can be avoided
3 IP Protection is Poor security risk has
been identified
in the IP
identify the risk
associated with IP that
classifies the data, know
the source threats,
follow and develop a
detail threat model
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6REGIONAL GARDENS: HYBRID CLOUD STRATEGY
4 Encryption Lack data security
incursions
Use of proxy server,
Employ VPN, through
cryptographic protocols
shield the transmissions
from random attacks,
manage server
authentication and
prevention of data
interception by
encrypting all the
transmissions with the
use of SSL or TLS,
send unencrypted
network traffic using
Secure Shell (SSH)
network tunnel protocol
5 Data Redundancy is poor the hybrid IT
cloud, and the
organisation are
at risk
Implement redundancy
from the hybrid cloud,
public cloud provider,
and utilising multiple
data centres
6 Data Ownership Lack loss of ability to
govern the
organisation
data set
Verify the data security
and ownership, know
about the data access
and what provider does
with access logs,
statistics, geographic or
jurisdiction location of
stored data
7 Bad Construction of cross-platform tools In a hybrid
environment,
the cross-
platform
management is
defined or
executed poorly
determine the migration
tools of cloud
application between
public and private
clouds for
interoperability and
moving apps, getting a
cloud monitoring tool
for virtualised
environment
accommodation,
maintaining access and
security for dynamic
cloud and movement of
VM through Cloud
automation tools
8 Security Risk Assessment Inadequate data breaches
occur, failed to
perform detailed
risk profiles
Scan of IDS or IPS
system for malicious
traffic, activate log
monitoring and current
updates of software, and
4 Encryption Lack data security
incursions
Use of proxy server,
Employ VPN, through
cryptographic protocols
shield the transmissions
from random attacks,
manage server
authentication and
prevention of data
interception by
encrypting all the
transmissions with the
use of SSL or TLS,
send unencrypted
network traffic using
Secure Shell (SSH)
network tunnel protocol
5 Data Redundancy is poor the hybrid IT
cloud, and the
organisation are
at risk
Implement redundancy
from the hybrid cloud,
public cloud provider,
and utilising multiple
data centres
6 Data Ownership Lack loss of ability to
govern the
organisation
data set
Verify the data security
and ownership, know
about the data access
and what provider does
with access logs,
statistics, geographic or
jurisdiction location of
stored data
7 Bad Construction of cross-platform tools In a hybrid
environment,
the cross-
platform
management is
defined or
executed poorly
determine the migration
tools of cloud
application between
public and private
clouds for
interoperability and
moving apps, getting a
cloud monitoring tool
for virtualised
environment
accommodation,
maintaining access and
security for dynamic
cloud and movement of
VM through Cloud
automation tools
8 Security Risk Assessment Inadequate data breaches
occur, failed to
perform detailed
risk profiles
Scan of IDS or IPS
system for malicious
traffic, activate log
monitoring and current
updates of software, and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7REGIONAL GARDENS: HYBRID CLOUD STRATEGY
handle network
organisation security
with the use of SIEM
system.
9 Weak Security Management fail to provide
authentication,
identity
management,
and procedure
of authorisation
by both private
and public cloud
use an identity
management service,
synchronising data
security, replicating
controls for the clouds,
maintaining of in-house
storage of data for
sensitive data
10 SLAs defined poorly loss to govern
the own set of
data
in the SLA security
measures are well
defined and clarify the
access protections and
permissions, services
reasonable expectations
must be detailed clearly
in SLA, review the
agreement by the
attorney before signing
it
11 Leakage of Data data is corrupted
or destroyed
Data loss prevention,
the fine print is read,
take security measures
for countering security
breaches, software
errors and infrastructure
malfunctioning
3. Information Security steps and control
The general Information Security steps and controls recommended to secure the
Hybrid Cloud are as follow:
Step 1: Identify and prioritise information that is confidential: The organisation has to
categorise the type of information, it can be by value, and another one by confidentiality and
then can prioritise the data that has to secure first. There are some the specific systems that
can update the information.
handle network
organisation security
with the use of SIEM
system.
9 Weak Security Management fail to provide
authentication,
identity
management,
and procedure
of authorisation
by both private
and public cloud
use an identity
management service,
synchronising data
security, replicating
controls for the clouds,
maintaining of in-house
storage of data for
sensitive data
10 SLAs defined poorly loss to govern
the own set of
data
in the SLA security
measures are well
defined and clarify the
access protections and
permissions, services
reasonable expectations
must be detailed clearly
in SLA, review the
agreement by the
attorney before signing
it
11 Leakage of Data data is corrupted
or destroyed
Data loss prevention,
the fine print is read,
take security measures
for countering security
breaches, software
errors and infrastructure
malfunctioning
3. Information Security steps and control
The general Information Security steps and controls recommended to secure the
Hybrid Cloud are as follow:
Step 1: Identify and prioritise information that is confidential: The organisation has to
categorise the type of information, it can be by value, and another one by confidentiality and
then can prioritise the data that has to secure first. There are some the specific systems that
can update the information.

8REGIONAL GARDENS: HYBRID CLOUD STRATEGY
Step 2: Perform a risk assessment with the flows of current information: The confidential
information flow in the organisation and understanding the current workflow is essential to
identify the business process. However, to determine the risk of leakage requires an in-depth
examination which will help the company to identify the vulnerabilities quickly.
Step 3: Determine the policies of usage, access and information-distribution: Distribution
policies have to be defined regarding Customer information, Intellectual property, Executive
communications and Employee records to enforce and implement monitoring along the
communication paths and this can quickly craft the types of confidential information.
Step 4: System monitoring and enforcement implementation: To monitor the usage of
information and traffic it is crucial to protect the assets of confidential information. It helps in
establishing the control points to verify the compliance with performance enforcement and
distribution policies. The monitoring system can identify false alarms and stop unauthorised
traffic.
Step 5: Periodically reviewing the progress: The organisation need to review the policies,
training and system to achieve maximum effectiveness. Through monitoring systems, the
training of the employee can be improved and expand the deployment to eliminate the
vulnerabilities systematically.
4. Recommendation to Regional Garden’s BCP
A business continuity plan is a step by step procedure that consists of various
functions and plan that are mainly formed up to keep running those procedures and
information which is developed, compiled and maintained in readiness of an emergency or
disaster. It depicts how to resume business after a disruption into its normal form or to keep
running with the present status. The Regional Garden’s BCP should be including the private
portion of the cloud for the critical application used by the organisations and less to some
Step 2: Perform a risk assessment with the flows of current information: The confidential
information flow in the organisation and understanding the current workflow is essential to
identify the business process. However, to determine the risk of leakage requires an in-depth
examination which will help the company to identify the vulnerabilities quickly.
Step 3: Determine the policies of usage, access and information-distribution: Distribution
policies have to be defined regarding Customer information, Intellectual property, Executive
communications and Employee records to enforce and implement monitoring along the
communication paths and this can quickly craft the types of confidential information.
Step 4: System monitoring and enforcement implementation: To monitor the usage of
information and traffic it is crucial to protect the assets of confidential information. It helps in
establishing the control points to verify the compliance with performance enforcement and
distribution policies. The monitoring system can identify false alarms and stop unauthorised
traffic.
Step 5: Periodically reviewing the progress: The organisation need to review the policies,
training and system to achieve maximum effectiveness. Through monitoring systems, the
training of the employee can be improved and expand the deployment to eliminate the
vulnerabilities systematically.
4. Recommendation to Regional Garden’s BCP
A business continuity plan is a step by step procedure that consists of various
functions and plan that are mainly formed up to keep running those procedures and
information which is developed, compiled and maintained in readiness of an emergency or
disaster. It depicts how to resume business after a disruption into its normal form or to keep
running with the present status. The Regional Garden’s BCP should be including the private
portion of the cloud for the critical application used by the organisations and less to some
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9REGIONAL GARDENS: HYBRID CLOUD STRATEGY
extent for the public part of the cloud that is being used by them. The Regional Gardens' BCP
should also include policies such as transferring data only from behind the firewall and not
exposing the data to the public clouds so that the data is subjected to any external agents so
that the data of the organisation is not hampered. The organisation can also involve additional
policies such as assigning business continuity and recovery professionals to develop plans
and coordination between business and IT. Secondly, running periodic testing of plans,
ideally quarterly, with published results and analysis. And optionally they might also include
evaluating and deploying optimisation technologies to address data growth, network latency,
and congestion. As the data centres continue to consolidate, the number of remote and brand
locations continue to expand. In such cases centralising backup and replication processes in a
core data centre is the only way to go with business continuity. With centralised cloud data
depository, more data can be protected, more often and with faster data recovery rate. The
hybrid cloud solutions can be used to send backup and archive data to the third-party cloud
inefficient and cost-effective manner. Plus, businesses can send data offsite to the secure
cloud without any changes to their current processes.
5. Requirements
To conduct remote server administration, resource and SLA management for the
hybrid cloud model the Regional Gardens need to set principles and requirement for the
success of the organisation.
As the Regional Garden migrate their workload to hybrid cloud, the first shift will be
done with the operation of IaaS. The management capacity and skills of monitoring will be
used to control the shift that virtualised the environments. The second shift will be to refactor
in the new hybrid cloud application that will be developed basically for the cloud. All the
operations manager will have to focus on monitoring and managing the platform. As here
extent for the public part of the cloud that is being used by them. The Regional Gardens' BCP
should also include policies such as transferring data only from behind the firewall and not
exposing the data to the public clouds so that the data is subjected to any external agents so
that the data of the organisation is not hampered. The organisation can also involve additional
policies such as assigning business continuity and recovery professionals to develop plans
and coordination between business and IT. Secondly, running periodic testing of plans,
ideally quarterly, with published results and analysis. And optionally they might also include
evaluating and deploying optimisation technologies to address data growth, network latency,
and congestion. As the data centres continue to consolidate, the number of remote and brand
locations continue to expand. In such cases centralising backup and replication processes in a
core data centre is the only way to go with business continuity. With centralised cloud data
depository, more data can be protected, more often and with faster data recovery rate. The
hybrid cloud solutions can be used to send backup and archive data to the third-party cloud
inefficient and cost-effective manner. Plus, businesses can send data offsite to the secure
cloud without any changes to their current processes.
5. Requirements
To conduct remote server administration, resource and SLA management for the
hybrid cloud model the Regional Gardens need to set principles and requirement for the
success of the organisation.
As the Regional Garden migrate their workload to hybrid cloud, the first shift will be
done with the operation of IaaS. The management capacity and skills of monitoring will be
used to control the shift that virtualised the environments. The second shift will be to refactor
in the new hybrid cloud application that will be developed basically for the cloud. All the
operations manager will have to focus on monitoring and managing the platform. As here
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10REGIONAL GARDENS: HYBRID CLOUD STRATEGY
AWS is used as a platform that is based on the modern application server with a combination
of both public and private service provider to form a hybrid cloud model.
During the second shift, the SLA management has to focus less on the availability and
more on the consumption patterns in the hybrid cloud model. The model has been given to
support the availability and resilience of the design, and the important thing over here is to
shift towards understanding the services that have to consumed. It will help the company to
determine the cost management and efficiency. The critical requirement for the Regional
Garden particularly is the integration between the cloud services and the SLA management.
The organisation need to understand the level of services required the processes. The
organisation potentially negotiate contract terms through SLA to meet the requirement.
Priority has been given to data integrity and security. Thus, this model will be made available
for the new techniques that are mainly in support of the hybrid cloud model.
AWS is used as a platform that is based on the modern application server with a combination
of both public and private service provider to form a hybrid cloud model.
During the second shift, the SLA management has to focus less on the availability and
more on the consumption patterns in the hybrid cloud model. The model has been given to
support the availability and resilience of the design, and the important thing over here is to
shift towards understanding the services that have to consumed. It will help the company to
determine the cost management and efficiency. The critical requirement for the Regional
Garden particularly is the integration between the cloud services and the SLA management.
The organisation need to understand the level of services required the processes. The
organisation potentially negotiate contract terms through SLA to meet the requirement.
Priority has been given to data integrity and security. Thus, this model will be made available
for the new techniques that are mainly in support of the hybrid cloud model.

11REGIONAL GARDENS: HYBRID CLOUD STRATEGY
6. Bibliography
Borrett, M. (2016). Practical Guide to Hybrid Cloud Computing [Ebook]. Retrieved from
http://www.cloud-council.org/deliverables/CSCC-Practical-Guide-to-Hybrid-Cloud-
Computing.pdf
Chang, V., Kuo, Y. H., & Ramachandran, M. (2016). Cloud computing adoption framework:
A security framework for business clouds. Future Generation Computer Systems, 57,
24-41.
Goyal, S. (2014). Public vs private vs hybrid vs community-cloud computing: A critical
review. International Journal of Computer Network and Information Security, 6(3),
20.
He, W., & Wang, F. K. (2015). A hybrid cloud model for cloud adoption by multinational
enterprises. Journal of Global Information Management (JGIM), 23(1), 1-23.
Katyal, M., & Mishra, A. (2014). A comparative study of load balancing algorithms in cloud
computing environment. arXiv preprint arXiv:1403.6918.
Li, J., Li, Y. K., Chen, X., Lee, P. P., & Lou, W. (2015). A hybrid cloud approach for
securely authorised deduplication. IEEE Transactions on Parallel and Distributed
Systems, 26(5), 1206-1216.
Linthicum, D. S. (2016). Practical use of microservices in moving workloads to the
cloud. IEEE Cloud Computing, 3(5), 6-9.
Nikulchev, E., Lukyanchikov, O., Pluzhnik, E., & Biryukov, D. (2016). Features
management and middleware of hybrid cloud infrastructures. International Journal of
Advanced Computer Science and Applications, 7(1), 30-36.
6. Bibliography
Borrett, M. (2016). Practical Guide to Hybrid Cloud Computing [Ebook]. Retrieved from
http://www.cloud-council.org/deliverables/CSCC-Practical-Guide-to-Hybrid-Cloud-
Computing.pdf
Chang, V., Kuo, Y. H., & Ramachandran, M. (2016). Cloud computing adoption framework:
A security framework for business clouds. Future Generation Computer Systems, 57,
24-41.
Goyal, S. (2014). Public vs private vs hybrid vs community-cloud computing: A critical
review. International Journal of Computer Network and Information Security, 6(3),
20.
He, W., & Wang, F. K. (2015). A hybrid cloud model for cloud adoption by multinational
enterprises. Journal of Global Information Management (JGIM), 23(1), 1-23.
Katyal, M., & Mishra, A. (2014). A comparative study of load balancing algorithms in cloud
computing environment. arXiv preprint arXiv:1403.6918.
Li, J., Li, Y. K., Chen, X., Lee, P. P., & Lou, W. (2015). A hybrid cloud approach for
securely authorised deduplication. IEEE Transactions on Parallel and Distributed
Systems, 26(5), 1206-1216.
Linthicum, D. S. (2016). Practical use of microservices in moving workloads to the
cloud. IEEE Cloud Computing, 3(5), 6-9.
Nikulchev, E., Lukyanchikov, O., Pluzhnik, E., & Biryukov, D. (2016). Features
management and middleware of hybrid cloud infrastructures. International Journal of
Advanced Computer Science and Applications, 7(1), 30-36.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





