Research Proposal: Analyzing Cyber-attacks on Microsoft Company
VerifiedAdded on 2023/01/03
|12
|2910
|86
Project
AI Summary
This research proposal investigates the impact of cyber-attacks on Microsoft, a major technology company. The proposal aims to examine the effects of cyber-attacks on organizational productivity. It outlines research objectives including understanding cyber-attacks, exploring their impact on Microsoft, and identifying effective solutions. The proposal addresses the growing issue of cyber threats like cloud vulnerabilities and social engineering, and includes a literature review discussing the impact of cyber-attacks on businesses. The methodology section details research philosophies, approaches, strategies, and ethical considerations, including data collection and analysis methods such as questionnaires and literature reviews. The proposal also includes a Gantt chart for project timeline management, and discusses the importance of protecting files, using multi-factor identification, and practicing smart cybersecurity measures. The research intends to provide insights into mitigating cyber threats and enhancing Microsoft's cybersecurity posture.

Cyber-attack on Microsoft
company-Research proposal
1
company-Research proposal
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................3
A. Task 1: Drafting a Research Proposal...........................................................................3
Research “aim”.....................................................................................................................3
Research “objective”............................................................................................................3
Research “questions”...........................................................................................................3
The issue................................................................................................................................4
Literature review based on the Cyber-attack issue on businesses...................................4
Research Methodology and ethical considerations...........................................................5
Conclusion.......................................................................................................................................9
References......................................................................................................................................11
2
INTRODUCTION...........................................................................................................................3
A. Task 1: Drafting a Research Proposal...........................................................................3
Research “aim”.....................................................................................................................3
Research “objective”............................................................................................................3
Research “questions”...........................................................................................................3
The issue................................................................................................................................4
Literature review based on the Cyber-attack issue on businesses...................................4
Research Methodology and ethical considerations...........................................................5
Conclusion.......................................................................................................................................9
References......................................................................................................................................11
2

INTRODUCTION
Cyber-attacks is an assault which have been launched by the the cybercriminals which
have been launched using one or more computers against the multiple networks or computers. A
cyber-attack can be able to disabled the computers, steal the data, or use a breached computer as
a launch point for other attacks. The Cybercriminals use variety of methods on the basis of
launching the cyber-attacks including malware, denial of services and other methods. The major
business issue which have been significantly figuring out is cyber-attacks on Microsoft
Corporation (Baezner, 2018).
It is one of the American multinational technology company that has a headquartered in
Washington. Cyber security is a top concern in today's world and even if talking about the
technological executives and work structure, a watch report revealed that 80% of the US
businesses have been majorly hacked successfully. It seems out to be the major and the impactful
business issue nowadays.
A. Task 1: Drafting a Research Proposal
Research “aim”
To functionally examine the impact of cyber-attack on productivity of an organisation. A
study on Microsoft company.
Research “objective”
To develop basic understanding the cyber-attack.
To explore the impact of cyber-attack on productivity of Microsoft.
To identify the effective ways that would be useful in resolving the issue of cyber-attack
on Microsoft.
Research “questions”
What are the Cyber-attacks and develop the effective understanding of cyber-attack on
the basis of trends?
How cyber-attacks can simply impact towards the productivity of Microsoft Company?
Describe some effective ways which are quiet useful is resolving the issues of cyber-
attack on Microsoft?
3
Cyber-attacks is an assault which have been launched by the the cybercriminals which
have been launched using one or more computers against the multiple networks or computers. A
cyber-attack can be able to disabled the computers, steal the data, or use a breached computer as
a launch point for other attacks. The Cybercriminals use variety of methods on the basis of
launching the cyber-attacks including malware, denial of services and other methods. The major
business issue which have been significantly figuring out is cyber-attacks on Microsoft
Corporation (Baezner, 2018).
It is one of the American multinational technology company that has a headquartered in
Washington. Cyber security is a top concern in today's world and even if talking about the
technological executives and work structure, a watch report revealed that 80% of the US
businesses have been majorly hacked successfully. It seems out to be the major and the impactful
business issue nowadays.
A. Task 1: Drafting a Research Proposal
Research “aim”
To functionally examine the impact of cyber-attack on productivity of an organisation. A
study on Microsoft company.
Research “objective”
To develop basic understanding the cyber-attack.
To explore the impact of cyber-attack on productivity of Microsoft.
To identify the effective ways that would be useful in resolving the issue of cyber-attack
on Microsoft.
Research “questions”
What are the Cyber-attacks and develop the effective understanding of cyber-attack on
the basis of trends?
How cyber-attacks can simply impact towards the productivity of Microsoft Company?
Describe some effective ways which are quiet useful is resolving the issues of cyber-
attack on Microsoft?
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The issue
Cyber-attack is seems out to be the major issue in recent years. It is because it reflected out as a
threat of cyber bullying and struck out of all the sensitive information of the company. In relation
with the Microsoft company, has been recently facing the major threats including cloud
vulnerability, smart contract hacking, social engineering attacks, deepfake and many others.
Microsoft report shows that there is a rapid increase in certain techniques on the basis of notable
shifts and towards the credential harvesting and ransom ware, as well as increasing the focus on
the internet things. The leap sophistications in the past few years, it is very effective and
important to take some major steps of cyber space because the growing issue of hacking will
unfortunately make a growth of hackers (Trautman, 2018).
.
Literature review based on the Cyber-attack issue on businesses
The use of internet have been genuinely made the people and organisation quiet vulnerable
and effective because of the outside attacks. An author of England Mirshsa H., suggested that
cyber issues have been majorly affected the systems of information and there are different types
of malicious attacks as well including virus, spyware and the social engineering as well. The
work have been quiet effective and motivated on the basis of performing several factors which
needs to be taken into the consideration. Cyber-attacks have been majorly compared with the
critical infrastructure. The issue has been some major consequences for the country that is quiet
knowing 1/3 of the population of the world have been widely connected in various and different
platforms. It can be functionally studied that Cyberspace has a systematic power to transform the
lives of huge number of people in the world living in a country’s side.
A cyber-attack is one of the major attack which can simply assault the launched by criminals
using one or more computers against a single or the multiple computers or attacks. A cyber-
attack can simply disable the computers, steal the data, use a breached computer as a launch and
for the attacks. A Cyber-criminal uses variety of methods in launching of the malware, phishing,
denial of services, and other methods. The effective trends of the cyber-attacks includes
Software supply chain attacks on rise: The software supply chain attacks, gives a major and
typical legitimate software which helps in modifying and infecting one of the building blocks in
which the software is simply relied upon it. The software supply chain can be simply divided
4
Cyber-attack is seems out to be the major issue in recent years. It is because it reflected out as a
threat of cyber bullying and struck out of all the sensitive information of the company. In relation
with the Microsoft company, has been recently facing the major threats including cloud
vulnerability, smart contract hacking, social engineering attacks, deepfake and many others.
Microsoft report shows that there is a rapid increase in certain techniques on the basis of notable
shifts and towards the credential harvesting and ransom ware, as well as increasing the focus on
the internet things. The leap sophistications in the past few years, it is very effective and
important to take some major steps of cyber space because the growing issue of hacking will
unfortunately make a growth of hackers (Trautman, 2018).
.
Literature review based on the Cyber-attack issue on businesses
The use of internet have been genuinely made the people and organisation quiet vulnerable
and effective because of the outside attacks. An author of England Mirshsa H., suggested that
cyber issues have been majorly affected the systems of information and there are different types
of malicious attacks as well including virus, spyware and the social engineering as well. The
work have been quiet effective and motivated on the basis of performing several factors which
needs to be taken into the consideration. Cyber-attacks have been majorly compared with the
critical infrastructure. The issue has been some major consequences for the country that is quiet
knowing 1/3 of the population of the world have been widely connected in various and different
platforms. It can be functionally studied that Cyberspace has a systematic power to transform the
lives of huge number of people in the world living in a country’s side.
A cyber-attack is one of the major attack which can simply assault the launched by criminals
using one or more computers against a single or the multiple computers or attacks. A cyber-
attack can simply disable the computers, steal the data, use a breached computer as a launch and
for the attacks. A Cyber-criminal uses variety of methods in launching of the malware, phishing,
denial of services, and other methods. The effective trends of the cyber-attacks includes
Software supply chain attacks on rise: The software supply chain attacks, gives a major and
typical legitimate software which helps in modifying and infecting one of the building blocks in
which the software is simply relied upon it. The software supply chain can be simply divided
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

into two categories including a good and efficient target on suppliers because it will simply
reflected a weakest link and in the second category there must be a compromise in suppy chain
distribution radium in relation with Microsoft.
Second trend simply reflects the evasive phishing cyber-attacks in which phishing is one of
the popular technique and it remains as one of the part of cyber security. The social engineered
techniques include solution securities and frequency level. The scams include malicious
attachments links and harder to detect.
The productivity of the Microsoft company have been badly impacted because Microsoft is
one of the computer platform and millions of users have their person as well as reflective data, in
a lot of ways. There is a need to have proper functionality but because of cyber-attacks,
Microsoft have been faced a serious deprive issue. Today everyone is using mobile and search
will be from the software. If Microsoft has a cyber-attack then it will automatically reduce the
users.
The resolving of the Cyber-attacks issues that can simply arises in the Microsoft can be done
on the basis of essential factors which have been mentioned below
Protecting the files and the devices: there is a need to keep software up to date. The files
must be secure enough so that no cyber-attacks cannot be done easily. Multifactor identification
helps in prevent from all the cybercriminals which can simply accessing from all the accounts.
Practicing the smart cyber security: It refers to the usage of strong passwords that contain
at-least 12 letters on the basis of numbers, letters and symbols. Use a VPN which helps in
protecting from all the danger and the online threats. The current news and development also
helps in protecting the smart cyber security.
Research Methodology and ethical considerations
The research methodology is one of the efficient and significant part of the research project
because it can functionally refers to the process of gathering and analysing the data figures so
that there must be an effective essential process regarding the field of study. The research
methodology is seems out to be the essential data analysation and data collection process in
which there must be a huge importance of the corporate social responsibility for an effective
organisation in which there is an effective business functions at the international marketplace.
There are several types of research methodologies that will be essential in data collection and
data analysis of the importance of corporate social responsibility for an organisation in operating
5
reflected a weakest link and in the second category there must be a compromise in suppy chain
distribution radium in relation with Microsoft.
Second trend simply reflects the evasive phishing cyber-attacks in which phishing is one of
the popular technique and it remains as one of the part of cyber security. The social engineered
techniques include solution securities and frequency level. The scams include malicious
attachments links and harder to detect.
The productivity of the Microsoft company have been badly impacted because Microsoft is
one of the computer platform and millions of users have their person as well as reflective data, in
a lot of ways. There is a need to have proper functionality but because of cyber-attacks,
Microsoft have been faced a serious deprive issue. Today everyone is using mobile and search
will be from the software. If Microsoft has a cyber-attack then it will automatically reduce the
users.
The resolving of the Cyber-attacks issues that can simply arises in the Microsoft can be done
on the basis of essential factors which have been mentioned below
Protecting the files and the devices: there is a need to keep software up to date. The files
must be secure enough so that no cyber-attacks cannot be done easily. Multifactor identification
helps in prevent from all the cybercriminals which can simply accessing from all the accounts.
Practicing the smart cyber security: It refers to the usage of strong passwords that contain
at-least 12 letters on the basis of numbers, letters and symbols. Use a VPN which helps in
protecting from all the danger and the online threats. The current news and development also
helps in protecting the smart cyber security.
Research Methodology and ethical considerations
The research methodology is one of the efficient and significant part of the research project
because it can functionally refers to the process of gathering and analysing the data figures so
that there must be an effective essential process regarding the field of study. The research
methodology is seems out to be the essential data analysation and data collection process in
which there must be a huge importance of the corporate social responsibility for an effective
organisation in which there is an effective business functions at the international marketplace.
There are several types of research methodologies that will be essential in data collection and
data analysis of the importance of corporate social responsibility for an organisation in operating
5

their business functions at international marketplace. There are some fundamental and useful
methodologies of the above mentioned topic that even helps in defining the below detail.
Research philosophies: It refers to the processes which have been significantly used by the
researcher in analysing, collecting and usage of several information about the studies topic. The
research methodology based on this section can be simply divided into two types including
interpretivism and positivism philosophy. For carrying the investigation further, there is a need
to have proper role of corporate governance for an organisation. To carry forward with the
current investigation, there is a need to have proper role of the corporate governance for the
organisation. The positivism philosophy is quiet useful and valuable for all the researcher
because it simply helps them in analysing and gathering several information, in a representative
and quantitative form and also assist on the basis of saving the cost and time. The interpretivism
philosophy is quiet useful and valuable for all the researcher because it helps in investigating and
useful information based on qualitative data. It gives maximum sources and time.
Research approach: It is one of the process of researchers for various researches and the
main purpose of the research approach is to have an effective and collective information. The
research approaches are of two types including deductive and inductive. The inductive approach
suggest that there is a need to have qualitative information analysation and in other form, there is
a need to have quantitative information as well. The accordance suggest that more valuability
and suitability can be simply reflected in the deductive type of research approach on the basis of
facilitates that quantitative information evaluation and there is a need to have a maximum time
period which gives a suitable and effective result in accomplishing the purpose-able project. The
inductive approach is quiet useful for the investigation and on the basis of quantitative collection
of data as well maximum time.
Methodological research choice: the research choices in terms of methodology are quantitative
and qualitative research choices. The two significant choices are useful and quiet essential for the
current project presentation and in terms of possible and effective manner. In this research based
project, quantitative method will be followed because it simply facilitates in gathering the
numerical information and do not support in the selection of large sample sizes.
Research strategies: It refers to the proper and the most effective, significant procedure
which suggest that there is a need to have information and data collection on the basis of several
research strategies. The introduction should have proper and significant procedure which can
6
methodologies of the above mentioned topic that even helps in defining the below detail.
Research philosophies: It refers to the processes which have been significantly used by the
researcher in analysing, collecting and usage of several information about the studies topic. The
research methodology based on this section can be simply divided into two types including
interpretivism and positivism philosophy. For carrying the investigation further, there is a need
to have proper role of corporate governance for an organisation. To carry forward with the
current investigation, there is a need to have proper role of the corporate governance for the
organisation. The positivism philosophy is quiet useful and valuable for all the researcher
because it simply helps them in analysing and gathering several information, in a representative
and quantitative form and also assist on the basis of saving the cost and time. The interpretivism
philosophy is quiet useful and valuable for all the researcher because it helps in investigating and
useful information based on qualitative data. It gives maximum sources and time.
Research approach: It is one of the process of researchers for various researches and the
main purpose of the research approach is to have an effective and collective information. The
research approaches are of two types including deductive and inductive. The inductive approach
suggest that there is a need to have qualitative information analysation and in other form, there is
a need to have quantitative information as well. The accordance suggest that more valuability
and suitability can be simply reflected in the deductive type of research approach on the basis of
facilitates that quantitative information evaluation and there is a need to have a maximum time
period which gives a suitable and effective result in accomplishing the purpose-able project. The
inductive approach is quiet useful for the investigation and on the basis of quantitative collection
of data as well maximum time.
Methodological research choice: the research choices in terms of methodology are quantitative
and qualitative research choices. The two significant choices are useful and quiet essential for the
current project presentation and in terms of possible and effective manner. In this research based
project, quantitative method will be followed because it simply facilitates in gathering the
numerical information and do not support in the selection of large sample sizes.
Research strategies: It refers to the proper and the most effective, significant procedure
which suggest that there is a need to have information and data collection on the basis of several
research strategies. The introduction should have proper and significant procedure which can
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
simply include several types of actions and the effective strategies, the research of experiment
and the survey. There is several important research which suggest that in accordance with the
existing topic, survey should followed researcher on the basis of collection and analysation of the
output in the fulfilment of the research objectives in an efficient and successful manner.
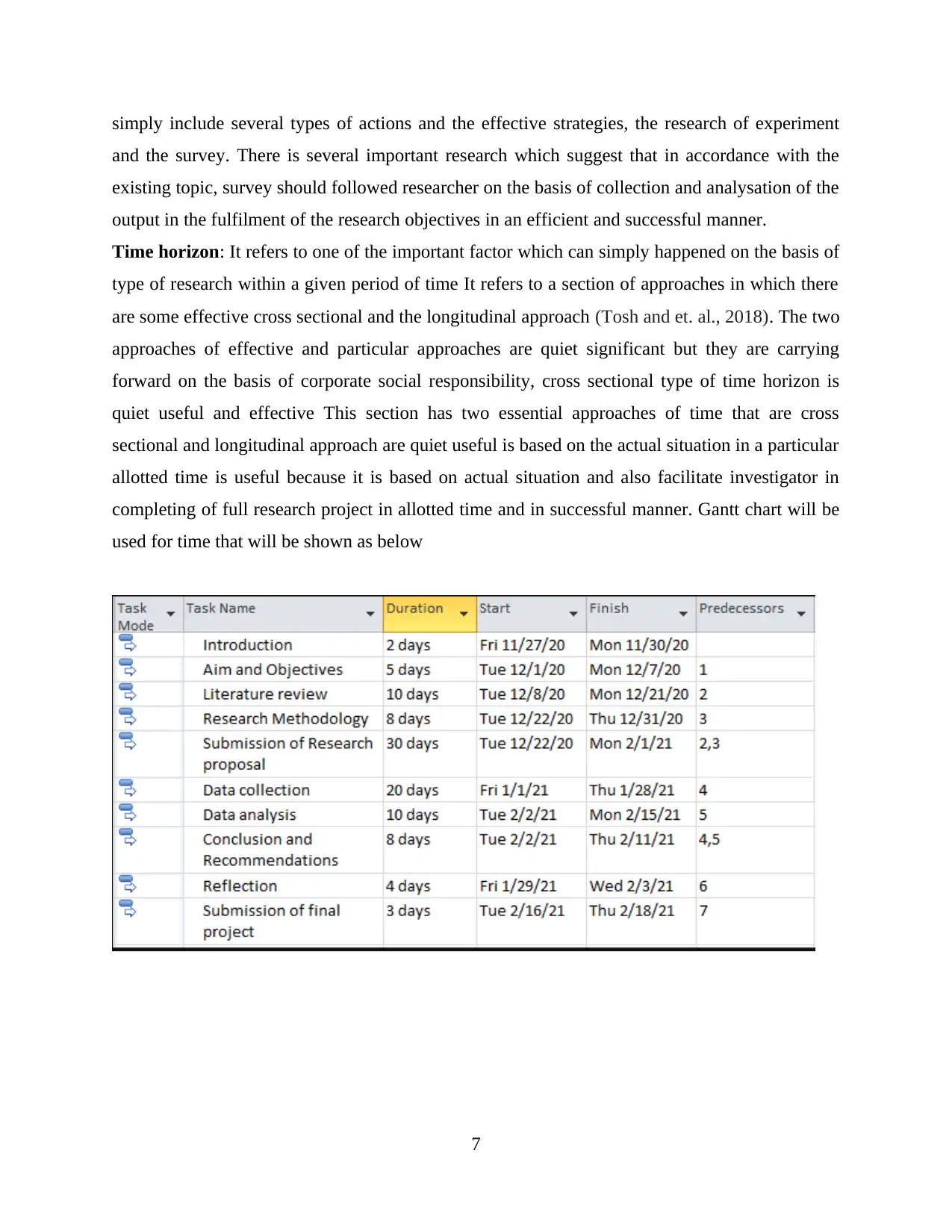
Time horizon: It refers to one of the important factor which can simply happened on the basis of
type of research within a given period of time It refers to a section of approaches in which there
are some effective cross sectional and the longitudinal approach (Tosh and et. al., 2018). The two
approaches of effective and particular approaches are quiet significant but they are carrying
forward on the basis of corporate social responsibility, cross sectional type of time horizon is
quiet useful and effective This section has two essential approaches of time that are cross
sectional and longitudinal approach are quiet useful is based on the actual situation in a particular
allotted time is useful because it is based on actual situation and also facilitate investigator in
completing of full research project in allotted time and in successful manner. Gantt chart will be
used for time that will be shown as below
7
and the survey. There is several important research which suggest that in accordance with the
existing topic, survey should followed researcher on the basis of collection and analysation of the
output in the fulfilment of the research objectives in an efficient and successful manner.
Time horizon: It refers to one of the important factor which can simply happened on the basis of
type of research within a given period of time It refers to a section of approaches in which there
are some effective cross sectional and the longitudinal approach (Tosh and et. al., 2018). The two
approaches of effective and particular approaches are quiet significant but they are carrying
forward on the basis of corporate social responsibility, cross sectional type of time horizon is
quiet useful and effective This section has two essential approaches of time that are cross
sectional and longitudinal approach are quiet useful is based on the actual situation in a particular
allotted time is useful because it is based on actual situation and also facilitate investigator in
completing of full research project in allotted time and in successful manner. Gantt chart will be
used for time that will be shown as below
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Data collection and data analysis: It is one of the most essential and an effective part of
the research methodology. The essential part should not be able to conduct the investigation
process on the basis of full investigation and a specific growth. The data analysis and the data
collection effectively are listed below:
Data collection: It refers to the process of primary and secondary information gathering
(Herrmann, 2019). For the collection of all the information which are quiet related with
the primary factor, the questionnaire must have a proper and an effective application of
this project. In comparison to that, the secondary type of data includes articles,
publications, project and many other things which seem to be an effective source for the
literature review and it effectively applied in the project. The literature review helps in
fulfilling the research gap and achieving the aims and objectives.
Data analysis: It refers to one of the procedure of analysing several information and
collection of data from the instrumental research. The information related to the
quantitative sources must have questionnaire and frequency distribution analysis which
will systematically help in the techniques related to analytical ability. The facilitate
8
the research methodology. The essential part should not be able to conduct the investigation
process on the basis of full investigation and a specific growth. The data analysis and the data
collection effectively are listed below:
Data collection: It refers to the process of primary and secondary information gathering
(Herrmann, 2019). For the collection of all the information which are quiet related with
the primary factor, the questionnaire must have a proper and an effective application of
this project. In comparison to that, the secondary type of data includes articles,
publications, project and many other things which seem to be an effective source for the
literature review and it effectively applied in the project. The literature review helps in
fulfilling the research gap and achieving the aims and objectives.
Data analysis: It refers to one of the procedure of analysing several information and
collection of data from the instrumental research. The information related to the
quantitative sources must have questionnaire and frequency distribution analysis which
will systematically help in the techniques related to analytical ability. The facilitate
8

investigator should have quantitative information and systematic output which includes
aims and the objectives.
Sampling techniques: It can be said that there are simply two types of the sampling techniques
including probability and the non-probability. The study suggests that probability sampling is
quiet efficient and valuable because the researchers need to select and choose a great number of
sample. The use of probability sampling includes almost 30 employees on the basis of random
sampling. One of the main reasons of selecting the probability sampling is to stop consuming the
time period and helps in proving the significant outputs which are quiet related with the efficient
time. One of the effective and the main reason is to helps in providing some outputs which are
quantitative. In comparison to that, the non-probability sampling not effectively valuable on the
basis of existing topic because there are some small number of samples which provide maximum
time (Wu and et. al., 2018).
Research instruments: The effective collections of the information regarding a specific area are
all included in the research instrument. The different instruments including information
gathering, questionnaire, modelling and interviewing helps in information gathering. . The
essential factor on the basis of effectiveness of corporate social responsibility and operating the
businesses at the global level, the questionnaire is very important and valuable for the entire
investigator because it systematically helps in the important time consuming. It will help in
assisting the project aim and objectives successfully Banner(M., 2018).
Ethical considerations: the significant and important research which follow the ethical
principles before investigation. The effective principles, values, ethics, integrity, truthfulness,
confidentiality and effective principles must be followed within an investigation. It is because the
completing of each and every task must have ethical output and aims can be effectively
measured. s
Therefore, above mentioned all these type of research methodologies is important for
researcher in accomplishment of project and and objectives in positive and effective manner that
result in completion of full project successfully.
Conclusion
The above discussion is based on research proposal on cyber-attacks which impact towards
the organisation. The discussion includes aims and objectives of Cyber-attacks. A literature
review based on the cyber-security. A research methodology is also presented above. There is a
9
aims and the objectives.
Sampling techniques: It can be said that there are simply two types of the sampling techniques
including probability and the non-probability. The study suggests that probability sampling is
quiet efficient and valuable because the researchers need to select and choose a great number of
sample. The use of probability sampling includes almost 30 employees on the basis of random
sampling. One of the main reasons of selecting the probability sampling is to stop consuming the
time period and helps in proving the significant outputs which are quiet related with the efficient
time. One of the effective and the main reason is to helps in providing some outputs which are
quantitative. In comparison to that, the non-probability sampling not effectively valuable on the
basis of existing topic because there are some small number of samples which provide maximum
time (Wu and et. al., 2018).
Research instruments: The effective collections of the information regarding a specific area are
all included in the research instrument. The different instruments including information
gathering, questionnaire, modelling and interviewing helps in information gathering. . The
essential factor on the basis of effectiveness of corporate social responsibility and operating the
businesses at the global level, the questionnaire is very important and valuable for the entire
investigator because it systematically helps in the important time consuming. It will help in
assisting the project aim and objectives successfully Banner(M., 2018).
Ethical considerations: the significant and important research which follow the ethical
principles before investigation. The effective principles, values, ethics, integrity, truthfulness,
confidentiality and effective principles must be followed within an investigation. It is because the
completing of each and every task must have ethical output and aims can be effectively
measured. s
Therefore, above mentioned all these type of research methodologies is important for
researcher in accomplishment of project and and objectives in positive and effective manner that
result in completion of full project successfully.
Conclusion
The above discussion is based on research proposal on cyber-attacks which impact towards
the organisation. The discussion includes aims and objectives of Cyber-attacks. A literature
review based on the cyber-security. A research methodology is also presented above. There is a
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
need to have quantitative sets of data to be use so that there must be a significant and reliable
source and it must be primary source of data from all the employees who are working in
Microsoft so that a proper structure and effective way to tackle and resolve the issue of Cyber-
attacks.
10
source and it must be primary source of data from all the employees who are working in
Microsoft so that a proper structure and effective way to tackle and resolve the issue of Cyber-
attacks.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Malik, M.S. and Islam, U., 2019. Cybercrime: an emerging threat to the banking sector of
Pakistan. Journal of Financial Crime.
Akram, J. and Ping, L., 2019. How to build a vulnerability benchmark to overcome cyber
security attacks. IET Information Security, 14(1), pp.60-71.
Baezner, M., 2018. Cyber and Information warfare in the Ukrainian conflict (No. 1, pp. 1-56).
ETH Zurich.
Kang, S. and Na, Y.K., 2018. The effect of the relationship characteristics and social capital of
the sharing economy business on the social network, relationship competitive
advantage, and continuance commitment. Sustainability, 10(7), p.2203.
Tosh and et. al., 2018. Establishing evolutionary game models for cyber security information
exchange (cybex). Journal of Computer and System Sciences, 98, pp.27-52.
Herrmann, D., 2019. Cyber Espionage and Cyber Defence. In Information Technology for Peace
and Security (pp. 83-106). Springer Vieweg, Wiesbaden.
Banner, M., 2018. Digital Presence and Transformation: The growing importance of digital
presence in today's business marketplace.
Trautman, L.J., 2018. How Google Perceives Customer Privacy, Cyber, E-commerce, Political
and Regulatory Compliance Risks. Wm. & Mary Bus. L. Rev., 10, p.1.
Wu and et. al., 2018. Cybersecurity for digital manufacturing. Journal of manufacturing
systems, 48, pp.3-12.
11
Malik, M.S. and Islam, U., 2019. Cybercrime: an emerging threat to the banking sector of
Pakistan. Journal of Financial Crime.
Akram, J. and Ping, L., 2019. How to build a vulnerability benchmark to overcome cyber
security attacks. IET Information Security, 14(1), pp.60-71.
Baezner, M., 2018. Cyber and Information warfare in the Ukrainian conflict (No. 1, pp. 1-56).
ETH Zurich.
Kang, S. and Na, Y.K., 2018. The effect of the relationship characteristics and social capital of
the sharing economy business on the social network, relationship competitive
advantage, and continuance commitment. Sustainability, 10(7), p.2203.
Tosh and et. al., 2018. Establishing evolutionary game models for cyber security information
exchange (cybex). Journal of Computer and System Sciences, 98, pp.27-52.
Herrmann, D., 2019. Cyber Espionage and Cyber Defence. In Information Technology for Peace
and Security (pp. 83-106). Springer Vieweg, Wiesbaden.
Banner, M., 2018. Digital Presence and Transformation: The growing importance of digital
presence in today's business marketplace.
Trautman, L.J., 2018. How Google Perceives Customer Privacy, Cyber, E-commerce, Political
and Regulatory Compliance Risks. Wm. & Mary Bus. L. Rev., 10, p.1.
Wu and et. al., 2018. Cybersecurity for digital manufacturing. Journal of manufacturing
systems, 48, pp.3-12.
11

12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





