Analyzing Responses to Security Breaches using AWS Zero Trust Security
VerifiedAdded on 2023/06/08
|12
|3612
|78
Report
AI Summary
This report provides a detailed analysis of responding to security and privacy breaches using the AWS Zero Trust security model. It begins by defining security breaches and then compares layered defense with zero trust models. The report highlights the benefits of AWS Zero Trust, including improved infrastructure inventory accuracy, enhanced alerting and monitoring, better user experience through single sign-on (SSO), streamlined security policy creation, and increased flexibility for data and application movement. It also addresses the risks and challenges of deploying AWS Zero Trust, such as denial-of-service attacks, stolen credentials, and the need for ongoing supervision. The downsides of using AWS Zero Trust compared to alternative solutions like defense in depth are discussed, focusing on cost and potential impact on user productivity. Finally, the report touches on the implementation of zero trust for Dr. Alarms, emphasizing the importance of continuous verification and network segmentation.

RESPONDING TO
SECURITY AND PRIVACY
BREACHES
SECURITY AND PRIVACY
BREACHES
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................3
MAIN BODY..................................................................................................................................3
Benefits of AWS Zero Trust Models-.........................................................................................3
Risks and Challenges of Deploying AWS Zero Trust Models....................................................5
Risks............................................................................................................................................5
Challenges....................................................................................................................................6
Downsides of using AWS Zero Trust as opposed to alternative solutions..................................7
Zero Trust implementation for Dr Alarms...................................................................................7
CONCLUSION................................................................................................................................9
REFERENCES................................................................................................................................1
INTRODUCTION...........................................................................................................................3
MAIN BODY..................................................................................................................................3
Benefits of AWS Zero Trust Models-.........................................................................................3
Risks and Challenges of Deploying AWS Zero Trust Models....................................................5
Risks............................................................................................................................................5
Challenges....................................................................................................................................6
Downsides of using AWS Zero Trust as opposed to alternative solutions..................................7
Zero Trust implementation for Dr Alarms...................................................................................7
CONCLUSION................................................................................................................................9
REFERENCES................................................................................................................................1

INTRODUCTION
Security beaches referred to as any of the incident which has the outcomes in the
unauthorised access to the data of computer, applications as well as the devices and the network.
This leads to the information is being accessed without any authorisation. When there is weak
and the stolen credentials of securing the data then the security breaches happens. The stolen
password is one of the most common cause of the data breaches (Ghafir & et.al., (2018). This
report will discuss the comparison between the layered defence and the zero trust security
models. Along with this, the main benefits of using the zero trust security models will be
illustrated as well as the main risks and the challenges of using the AWS zero trust security
models will be discussed. Further, the zero trust implementation strategies will be covered within
this report.
MAIN BODY
Benefits of AWS Zero Trust Models-
The zero trust model is basically the security framework which requires all the users
which involves inside and the outside network of the organisation. These has to be authenticated,
authorised as well as it is continuously validated for the configuration of the security as well as
the posture before it is been granted to keep the applications and the data. This model assumes
that there is none of the traditional network edge as networks can be local, or in the cloud, or
may be in the combination or the hybrid within the resources as well as the workers at the any of
the location (Wylde, (2021).
The zero trust framework is used for the security of the infrastructure as well as the data
for the present digital transformation. It helps the companies to solve and address the modern
challenges which are faced within their businesses which involves securing the remote workers,
hybrid cloud environments as well as the ransomware threats. There are number of the benefits
for the companies using this security models within the AWS as this framework is very holistic
for the organisations. These benefits are such as-
Accuracy within infrastructure inventory: The zero trust model requires the administration
which handles exactly the same thing which the users devices, services as well as the
applications are involves in the corporate infrastructure as well as where all the resources are
residing. This means there is accurate infrastructure inventory which is very helpful as regarding
Security beaches referred to as any of the incident which has the outcomes in the
unauthorised access to the data of computer, applications as well as the devices and the network.
This leads to the information is being accessed without any authorisation. When there is weak
and the stolen credentials of securing the data then the security breaches happens. The stolen
password is one of the most common cause of the data breaches (Ghafir & et.al., (2018). This
report will discuss the comparison between the layered defence and the zero trust security
models. Along with this, the main benefits of using the zero trust security models will be
illustrated as well as the main risks and the challenges of using the AWS zero trust security
models will be discussed. Further, the zero trust implementation strategies will be covered within
this report.
MAIN BODY
Benefits of AWS Zero Trust Models-
The zero trust model is basically the security framework which requires all the users
which involves inside and the outside network of the organisation. These has to be authenticated,
authorised as well as it is continuously validated for the configuration of the security as well as
the posture before it is been granted to keep the applications and the data. This model assumes
that there is none of the traditional network edge as networks can be local, or in the cloud, or
may be in the combination or the hybrid within the resources as well as the workers at the any of
the location (Wylde, (2021).
The zero trust framework is used for the security of the infrastructure as well as the data
for the present digital transformation. It helps the companies to solve and address the modern
challenges which are faced within their businesses which involves securing the remote workers,
hybrid cloud environments as well as the ransomware threats. There are number of the benefits
for the companies using this security models within the AWS as this framework is very holistic
for the organisations. These benefits are such as-
Accuracy within infrastructure inventory: The zero trust model requires the administration
which handles exactly the same thing which the users devices, services as well as the
applications are involves in the corporate infrastructure as well as where all the resources are
residing. This means there is accurate infrastructure inventory which is very helpful as regarding
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

the security matters and this also highly beneficial for the long term performance for the overall
purpose of the planning.
Improving the alerting and monitoringto implement : Monitoring the zero trust model is very
complex till the right resources are not used by the companies such as the security orchestration,
automation as well as the response and the network detection response (Samaniego & Deters,
(2018). Using the combination of the log as well as the event analysis helps in identifying the
security issuers and then this allows to provide the strategies or the ways for remediate these
issue and the problems. This enables the security operations centre administrating the ability for
quickly detecting and then responding to the cybersecurity threats if happens. AWS is the
platform where the companies stores there data using this model will allow them to effectively
detect the issues and the problems and taking the immediate actions for solving them so that the
cybersecurity threats can be eliminated.
Improves the experience of the user: When any of the organisation think of using the IT
security, the first and the foremost thing which comes in there mind is how to effectively keep
the track over the various passwords which they requires for accessing the number of the
applications and the data. One of the key aspect of the zero trust model is the ability of deploying
of single sign-on (SSO) tools as this helps them in simplifying the problem of managing the
various passwords for keeping the track over them (Egerton & et.al., (2021).
The SSO is the authentication framework which helps in organising the resources of the
infrastructure or the devices of the users which they have to access. This helps them in reducing
the problem of the password mismanagement as well as allows the users for easily getting the
resources they requires and on the other hand, the single authentication as well as controls the
operations transparently in the background. Using SSO within the AWS will help them in
managing the passwords of the applications effectively.
Creates the security policy: The companies which are using the transitional models has the
higher level of the risks for privacy and the security breaches. In this, each of the security tool is
separately configured as well as operated independently among all of the security tools. The zero
trust regarding this helps much to the companies as in this model, the universal policy can be
made and created once and this is then implemented throughout the organisation. In this, the
deployment and the management of the security policy becomes more streamlined from the
purpose of the planning.
Improving the alerting and monitoringto implement : Monitoring the zero trust model is very
complex till the right resources are not used by the companies such as the security orchestration,
automation as well as the response and the network detection response (Samaniego & Deters,
(2018). Using the combination of the log as well as the event analysis helps in identifying the
security issuers and then this allows to provide the strategies or the ways for remediate these
issue and the problems. This enables the security operations centre administrating the ability for
quickly detecting and then responding to the cybersecurity threats if happens. AWS is the
platform where the companies stores there data using this model will allow them to effectively
detect the issues and the problems and taking the immediate actions for solving them so that the
cybersecurity threats can be eliminated.
Improves the experience of the user: When any of the organisation think of using the IT
security, the first and the foremost thing which comes in there mind is how to effectively keep
the track over the various passwords which they requires for accessing the number of the
applications and the data. One of the key aspect of the zero trust model is the ability of deploying
of single sign-on (SSO) tools as this helps them in simplifying the problem of managing the
various passwords for keeping the track over them (Egerton & et.al., (2021).
The SSO is the authentication framework which helps in organising the resources of the
infrastructure or the devices of the users which they have to access. This helps them in reducing
the problem of the password mismanagement as well as allows the users for easily getting the
resources they requires and on the other hand, the single authentication as well as controls the
operations transparently in the background. Using SSO within the AWS will help them in
managing the passwords of the applications effectively.
Creates the security policy: The companies which are using the transitional models has the
higher level of the risks for privacy and the security breaches. In this, each of the security tool is
separately configured as well as operated independently among all of the security tools. The zero
trust regarding this helps much to the companies as in this model, the universal policy can be
made and created once and this is then implemented throughout the organisation. In this, the
deployment and the management of the security policy becomes more streamlined from the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

administrators point of view and the security gaps in some of the parts of infrastructure becomes
less likely (Chuan & et.al., (2020).
Higher flexibility for movement of data, apps and services: The business goals changes
continuously and according to this, the technology requirements has to support them like
applications, data as well as the IT services are frequently moving across the infrastructure of the
corporate. Before the zero trust model, the movements of the applications and the data from the
private data centres to the cloud environment. They have forced the security administrators for
the manually recreation of the security policy at the new location or the area. So this was very
time consuming process and there are higher chances of the security vulnerabilities (Mandal,
Khan & Jain, (2021). Zero trust helps them in managing the applications and the data centrally in
which the automation tools can be utilised for migrating the policies whenever they are required.
Huge amount of the investment against stolen data: The zero trust model mist be considered as
the insurance policy against the stolen data and the lost data. The zero trust model when
implemented and the management helps in preventing such losses so huge amount of the
investment must be viewed as the money well spent or it is worth it.
Risks and Challenges of Deploying AWS Zero Trust Models
Zero Trust can be defined as a framework entails its employers to ensure if their data is
genuine, official and legalised continuously for the purpose of safety configurations or not. This
model presumes that there is no out-dated network edge (Masinde, & Graffi, 2020). This model
believes that the network can either be local, saved in the cloud, or a mixture or a fusion with
resources as well as workers in any location. However, there are certain risk and challenges
associated with the use of AWS Zero Trust Models, that have been explained below:
Risks
The risks in relation to the AWS Zero Trust Security Model are as follows:
Denial of service or network disruption: A DOS is a kind of attack that aims to shut down a
machine or a network forcefully with an objective to make it distant to its intended users. It has
been identified that the individuals who make use of the Zero Trust Security Model are prone to
the Denial of service attacks while carrying out their routine operations. The DOS restricts the
users in accessing the information by flooding the target with traffic and sending the information
that leads to a crash.
less likely (Chuan & et.al., (2020).
Higher flexibility for movement of data, apps and services: The business goals changes
continuously and according to this, the technology requirements has to support them like
applications, data as well as the IT services are frequently moving across the infrastructure of the
corporate. Before the zero trust model, the movements of the applications and the data from the
private data centres to the cloud environment. They have forced the security administrators for
the manually recreation of the security policy at the new location or the area. So this was very
time consuming process and there are higher chances of the security vulnerabilities (Mandal,
Khan & Jain, (2021). Zero trust helps them in managing the applications and the data centrally in
which the automation tools can be utilised for migrating the policies whenever they are required.
Huge amount of the investment against stolen data: The zero trust model mist be considered as
the insurance policy against the stolen data and the lost data. The zero trust model when
implemented and the management helps in preventing such losses so huge amount of the
investment must be viewed as the money well spent or it is worth it.
Risks and Challenges of Deploying AWS Zero Trust Models
Zero Trust can be defined as a framework entails its employers to ensure if their data is
genuine, official and legalised continuously for the purpose of safety configurations or not. This
model presumes that there is no out-dated network edge (Masinde, & Graffi, 2020). This model
believes that the network can either be local, saved in the cloud, or a mixture or a fusion with
resources as well as workers in any location. However, there are certain risk and challenges
associated with the use of AWS Zero Trust Models, that have been explained below:
Risks
The risks in relation to the AWS Zero Trust Security Model are as follows:
Denial of service or network disruption: A DOS is a kind of attack that aims to shut down a
machine or a network forcefully with an objective to make it distant to its intended users. It has
been identified that the individuals who make use of the Zero Trust Security Model are prone to
the Denial of service attacks while carrying out their routine operations. The DOS restricts the
users in accessing the information by flooding the target with traffic and sending the information
that leads to a crash.

Stolen credential and insider threats: It has been observed that the usage of this security model
also makes its users vulnerable to the threat of insiders and stolen credentials of its users. When
the usernames and the passwords of an individual that needs to secured at any cost are known to
the hackers, there is a high risk that the user will have face data security and privacy issues as
their data and important information is at risk of being stolen (Souppaya, Scarfone, & Dodson,
2022). Therefore, the users of the Zero Trust Model need to take care and plan certain strategies
that could help them in enhancing the security of their data.
Challenges
It has been noted that the use of this model is highly beneficial for its users but there are
still certain challenges that the users of this model have to face are as follows:
Piecemeal approach leads to the development of gaps
The use of the Zero Trust model is quiet advantageous for its users as it provides them
with high and security feature and allows them to feel safe while their data and information is
being protected by the model. However, it has been noted that even though this model provides
security to the users to a great extent but in the process it can create major difficulties for the
company and put the same into a big risk. There are a wide range of companies that makes their
own strategies using a piecemeal approach in order to secure their data, but it is not as safe as it
is being advertised.
Obligation to ongoing supervision
Using this model for the purpose of data security is a hectic process. This software or
system requires continuous input from the side of its users in order to protect the information
they have stored that needs to be protected. In today’s world, the organizations keep on evolving
and for the same, they regularly change and updates their locations and policies. Then the
company again needs to monitor the process. Therefore, it can be stated that one of the leading
obstacle or challenge linked with the concept of the Zero Trust model is that it requires constant
supervision.
Zero trust Vs. Efficiency
The Zero trust cybersecurity approach also affects the efficiency and the productivity of
their employees working within an enterprise. The major challenge of this model is that restricts
the users from accessing the data without bringing the work to the halt (Chadwick, and et.al,
2020). In order to work within an organization, there is a need for them to have access to the data
also makes its users vulnerable to the threat of insiders and stolen credentials of its users. When
the usernames and the passwords of an individual that needs to secured at any cost are known to
the hackers, there is a high risk that the user will have face data security and privacy issues as
their data and important information is at risk of being stolen (Souppaya, Scarfone, & Dodson,
2022). Therefore, the users of the Zero Trust Model need to take care and plan certain strategies
that could help them in enhancing the security of their data.
Challenges
It has been noted that the use of this model is highly beneficial for its users but there are
still certain challenges that the users of this model have to face are as follows:
Piecemeal approach leads to the development of gaps
The use of the Zero Trust model is quiet advantageous for its users as it provides them
with high and security feature and allows them to feel safe while their data and information is
being protected by the model. However, it has been noted that even though this model provides
security to the users to a great extent but in the process it can create major difficulties for the
company and put the same into a big risk. There are a wide range of companies that makes their
own strategies using a piecemeal approach in order to secure their data, but it is not as safe as it
is being advertised.
Obligation to ongoing supervision
Using this model for the purpose of data security is a hectic process. This software or
system requires continuous input from the side of its users in order to protect the information
they have stored that needs to be protected. In today’s world, the organizations keep on evolving
and for the same, they regularly change and updates their locations and policies. Then the
company again needs to monitor the process. Therefore, it can be stated that one of the leading
obstacle or challenge linked with the concept of the Zero Trust model is that it requires constant
supervision.
Zero trust Vs. Efficiency
The Zero trust cybersecurity approach also affects the efficiency and the productivity of
their employees working within an enterprise. The major challenge of this model is that restricts
the users from accessing the data without bringing the work to the halt (Chadwick, and et.al,
2020). In order to work within an organization, there is a need for them to have access to the data
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

on a regular basis. There are times when the employees have to change their roles and
responsibilities. But if the system will restrict them in accessing the data it will surely affect the
productivity of that company.
Downsides of using AWS Zero Trust as opposed to alternative solutions
The disadvantages or downsides of using AWS Zero Trust as compared to other solutions
are explained below:
Similar to the Zero Trust, the defence in depth is also a type of security tactic that makes use of
multiple layers of security defence in order to protect the data and other systems from being
attacked. However, it has been identified that there are certain downsides of using Zero trust as
compared to the Defence in Depth. One of the leading disadvantage is that it is costlier to
implement within the company as compared to the defence on depth. Most of the times, the
reason behind the expensive system is that they internally try to implement the software on their
own. Another downside is that it can slow down the experience of the user and lead to the in
productivity within the company.
Zero Trust implementation for Dr Alarms
The zero trust implementation includes the policy for never trusting as well as the always
performing the verification for the authenticity as well as the privileges. Implementation of the
zero trust focused on the network access control systems as well as the segmentation of the
network regarding the areas which is required for the protection (DUMITRU, (2022). The
implementation of the Zero trust model can only be implemented when the individual has the
thorough understanding of the most of the common challenges which the company may face
such as the complex infrastructure, cost efforts as well as the need for flexible software.
The step by step implementation of the Zero Trust security model for Dr Alarms is as follows:
Determine the attack surface
In today’s world, it is useless to tirelessly work in order to identify the attack surface
associated with the operations of the company. It has been observed that the attack surface is
always expanding and therefore, it gets impossible for the company to determine the areas which
are prone to being attacked and are at risk of the cyberattacks (Zalivaka, Ivaniuk, & Chang,
2018). Therefore, the Zero Trust Security Model tries to the sources of the company that needs to
be protected at any cost and takes initiatives in order secure the same. The data and the sources
that are most essential for the company includes data such as credit card information, protected
responsibilities. But if the system will restrict them in accessing the data it will surely affect the
productivity of that company.
Downsides of using AWS Zero Trust as opposed to alternative solutions
The disadvantages or downsides of using AWS Zero Trust as compared to other solutions
are explained below:
Similar to the Zero Trust, the defence in depth is also a type of security tactic that makes use of
multiple layers of security defence in order to protect the data and other systems from being
attacked. However, it has been identified that there are certain downsides of using Zero trust as
compared to the Defence in Depth. One of the leading disadvantage is that it is costlier to
implement within the company as compared to the defence on depth. Most of the times, the
reason behind the expensive system is that they internally try to implement the software on their
own. Another downside is that it can slow down the experience of the user and lead to the in
productivity within the company.
Zero Trust implementation for Dr Alarms
The zero trust implementation includes the policy for never trusting as well as the always
performing the verification for the authenticity as well as the privileges. Implementation of the
zero trust focused on the network access control systems as well as the segmentation of the
network regarding the areas which is required for the protection (DUMITRU, (2022). The
implementation of the Zero trust model can only be implemented when the individual has the
thorough understanding of the most of the common challenges which the company may face
such as the complex infrastructure, cost efforts as well as the need for flexible software.
The step by step implementation of the Zero Trust security model for Dr Alarms is as follows:
Determine the attack surface
In today’s world, it is useless to tirelessly work in order to identify the attack surface
associated with the operations of the company. It has been observed that the attack surface is
always expanding and therefore, it gets impossible for the company to determine the areas which
are prone to being attacked and are at risk of the cyberattacks (Zalivaka, Ivaniuk, & Chang,
2018). Therefore, the Zero Trust Security Model tries to the sources of the company that needs to
be protected at any cost and takes initiatives in order secure the same. The data and the sources
that are most essential for the company includes data such as credit card information, protected
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

health information and intellectual property. It also intends to safeguard applications, assets and
other services that are important for the company.
Map transaction flows
In order to determine the data that needs to protected, the Zero trust model tracks the flow
of traffic on a network. This helps them in determining the process of protecting the data. Thus,
it is domineering to extract insights that are in relation with the interdependencies of the DAAS.
When an organization knows how to implement the use of certain resources, it gets easy for them
to enforce controls and make sure the controls are helping the company in securing the useful
information.
Zero trust architecture
It has been determined that the Zero Trust networks are completely personalized. They
are not extracted from any single or universal design. Once, the individual has formulated a
protect surface and developed flows in relation to the needs of an organization, one can develop
a Zero Trust Architecture (Awan, and et.al 2019). The process makes use of the next generation
firewall for the purpose of segmenting a gateway developing a micro perimeter in order to
protect the surface. The segmentation gateway can use additional layers of inspection in order
make the resources accessible within the protect surface.
Development of Zero trust policy
Once the network is developed, an individual or the company is required to formulate the
Zero trust policies using certain types of methodologies. There is a method called Kipling
method that helps the users in determining which resources are to be provided with the required
access to others (De Giovanni, 2020). This stage of the entire implementation process includes
identification of a number of factors such as names of the individuals or the designation that will
be using and accessing the information, application name that will be used by the company in
order to access a resource within the protect surface, defining where is the packet destination, the
time at which the individuals will be able to extract the information, and lastly, it will present the
ways in which the packet extraction protect the surface by using a particular application.
Monitor and Maintain the network
Last but not the least, the final step of implementing the Zero Trust Model involves
reviewing each and every log, the internal and external processes, all the ways and procedures
though layer 7, emphasizing on the operational aspects associated with the Zero Trust (Pan, &
other services that are important for the company.
Map transaction flows
In order to determine the data that needs to protected, the Zero trust model tracks the flow
of traffic on a network. This helps them in determining the process of protecting the data. Thus,
it is domineering to extract insights that are in relation with the interdependencies of the DAAS.
When an organization knows how to implement the use of certain resources, it gets easy for them
to enforce controls and make sure the controls are helping the company in securing the useful
information.
Zero trust architecture
It has been determined that the Zero Trust networks are completely personalized. They
are not extracted from any single or universal design. Once, the individual has formulated a
protect surface and developed flows in relation to the needs of an organization, one can develop
a Zero Trust Architecture (Awan, and et.al 2019). The process makes use of the next generation
firewall for the purpose of segmenting a gateway developing a micro perimeter in order to
protect the surface. The segmentation gateway can use additional layers of inspection in order
make the resources accessible within the protect surface.
Development of Zero trust policy
Once the network is developed, an individual or the company is required to formulate the
Zero trust policies using certain types of methodologies. There is a method called Kipling
method that helps the users in determining which resources are to be provided with the required
access to others (De Giovanni, 2020). This stage of the entire implementation process includes
identification of a number of factors such as names of the individuals or the designation that will
be using and accessing the information, application name that will be used by the company in
order to access a resource within the protect surface, defining where is the packet destination, the
time at which the individuals will be able to extract the information, and lastly, it will present the
ways in which the packet extraction protect the surface by using a particular application.
Monitor and Maintain the network
Last but not the least, the final step of implementing the Zero Trust Model involves
reviewing each and every log, the internal and external processes, all the ways and procedures
though layer 7, emphasizing on the operational aspects associated with the Zero Trust (Pan, &
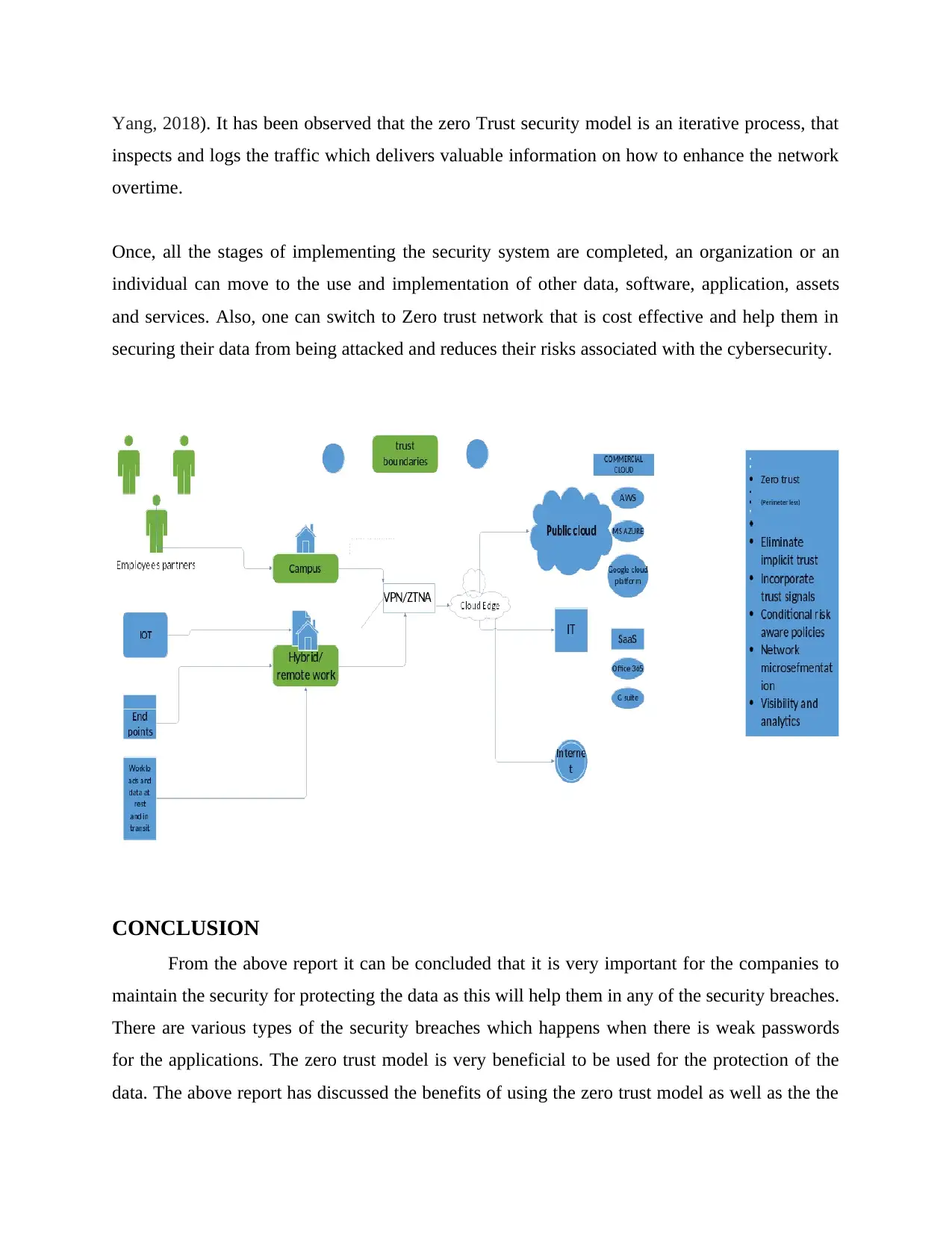
Yang, 2018). It has been observed that the zero Trust security model is an iterative process, that
inspects and logs the traffic which delivers valuable information on how to enhance the network
overtime.
Once, all the stages of implementing the security system are completed, an organization or an
individual can move to the use and implementation of other data, software, application, assets
and services. Also, one can switch to Zero trust network that is cost effective and help them in
securing their data from being attacked and reduces their risks associated with the cybersecurity.
CONCLUSION
From the above report it can be concluded that it is very important for the companies to
maintain the security for protecting the data as this will help them in any of the security breaches.
There are various types of the security breaches which happens when there is weak passwords
for the applications. The zero trust model is very beneficial to be used for the protection of the
data. The above report has discussed the benefits of using the zero trust model as well as the the
inspects and logs the traffic which delivers valuable information on how to enhance the network
overtime.
Once, all the stages of implementing the security system are completed, an organization or an
individual can move to the use and implementation of other data, software, application, assets
and services. Also, one can switch to Zero trust network that is cost effective and help them in
securing their data from being attacked and reduces their risks associated with the cybersecurity.
CONCLUSION
From the above report it can be concluded that it is very important for the companies to
maintain the security for protecting the data as this will help them in any of the security breaches.
There are various types of the security breaches which happens when there is weak passwords
for the applications. The zero trust model is very beneficial to be used for the protection of the
data. The above report has discussed the benefits of using the zero trust model as well as the the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
challenges which is faced by using this model. Along with this, the overall implementation
strategy for the zero trust model has been discussed for the AWS.
strategy for the zero trust model has been discussed for the AWS.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

REFERENCES
Books and journals
Awan, K. A., and et.al (2019). Holitrust-a holistic cross-domain trust management mechanism
for service-centric Internet of Things. Ieee Access. 7. 52191-52201.
Chadwick, D. W., and et.al (2020). A cloud-edge based data security architecture for sharing and
analysing cyber threat information. Future Generation Computer Systems. 102. 710-
722.
Chuan, T., & et.al., (2020, November). An implementation method of zero-trust architecture.
In Journal of Physics: Conference Series (Vol. 1651, No. 1, p. 012010). IOP Publishing.
De Giovanni, P. (2020). Blockchain and smart contracts in supply chain management: A game
theoretic model. International Journal of Production Economics. 228. 107855.
DelBene, K., Medin, M., & Murray, R. (2019). The Road to Zero Trust (Security). DIB Zero
Trust White Paper, 9.
DUMITRU, I. A. (2022, April). Zero Trust Security. In International Conference on
Cybersecurity and Cybercrime(Vol. 9, pp. 99-104).
Egerton, H., & et.al., (2021). Applying Zero Trust Security Principles to Defence Mechanisms
Against Data Exfiltration Attacks. Security and Privacy in the Internet of Things:
Architectures, Techniques, and Applications, 57-89.
Ghafir, I., & et.al., (2018). Security threats to critical infrastructure: the human factor. The
Journal of Supercomputing, 74(10), 4986-5002.
Mandal, S., Khan, D. A., & Jain, S. (2021). Cloud-based zero trust access control policy: an
approach to support work-from-home driven by COVID-19 pandemic. New Generation
Computing, 39(3), 599-622.
Masinde, N., & Graffi, K. (2020). Peer-to-peer-based social networks: A comprehensive
survey. SN Computer Science. 1(5). 1-51.
Pan, J., & Yang, Z. (2018, March). Cybersecurity challenges and opportunities in the new" edge
computing+ IoT" world. In Proceedings of the 2018 ACM International Workshop on
Security in Software Defined Networks & Network Function Virtualization (pp. 29-32).
Samaniego, M., & Deters, R. (2018, July). Zero-trust hierarchical management in IoT. In 2018
IEEE international congress on Internet of Things (ICIOT) (pp. 88-95). IEEE.
Souppaya, M., Scarfone, K., & Dodson, D. (2022). Secure Software Development Framework
(SSDF) Version 1.1. NIST Special Publication. 800. 218.
Wylde, A. (2021, June). Zero trust: Never trust, always verify. In 2021 international conference
on cyber situational awareness, data analytics and assessment (cybersa) (pp. 1-4). IEEE.
1
Books and journals
Awan, K. A., and et.al (2019). Holitrust-a holistic cross-domain trust management mechanism
for service-centric Internet of Things. Ieee Access. 7. 52191-52201.
Chadwick, D. W., and et.al (2020). A cloud-edge based data security architecture for sharing and
analysing cyber threat information. Future Generation Computer Systems. 102. 710-
722.
Chuan, T., & et.al., (2020, November). An implementation method of zero-trust architecture.
In Journal of Physics: Conference Series (Vol. 1651, No. 1, p. 012010). IOP Publishing.
De Giovanni, P. (2020). Blockchain and smart contracts in supply chain management: A game
theoretic model. International Journal of Production Economics. 228. 107855.
DelBene, K., Medin, M., & Murray, R. (2019). The Road to Zero Trust (Security). DIB Zero
Trust White Paper, 9.
DUMITRU, I. A. (2022, April). Zero Trust Security. In International Conference on
Cybersecurity and Cybercrime(Vol. 9, pp. 99-104).
Egerton, H., & et.al., (2021). Applying Zero Trust Security Principles to Defence Mechanisms
Against Data Exfiltration Attacks. Security and Privacy in the Internet of Things:
Architectures, Techniques, and Applications, 57-89.
Ghafir, I., & et.al., (2018). Security threats to critical infrastructure: the human factor. The
Journal of Supercomputing, 74(10), 4986-5002.
Mandal, S., Khan, D. A., & Jain, S. (2021). Cloud-based zero trust access control policy: an
approach to support work-from-home driven by COVID-19 pandemic. New Generation
Computing, 39(3), 599-622.
Masinde, N., & Graffi, K. (2020). Peer-to-peer-based social networks: A comprehensive
survey. SN Computer Science. 1(5). 1-51.
Pan, J., & Yang, Z. (2018, March). Cybersecurity challenges and opportunities in the new" edge
computing+ IoT" world. In Proceedings of the 2018 ACM International Workshop on
Security in Software Defined Networks & Network Function Virtualization (pp. 29-32).
Samaniego, M., & Deters, R. (2018, July). Zero-trust hierarchical management in IoT. In 2018
IEEE international congress on Internet of Things (ICIOT) (pp. 88-95). IEEE.
Souppaya, M., Scarfone, K., & Dodson, D. (2022). Secure Software Development Framework
(SSDF) Version 1.1. NIST Special Publication. 800. 218.
Wylde, A. (2021, June). Zero trust: Never trust, always verify. In 2021 international conference
on cyber situational awareness, data analytics and assessment (cybersa) (pp. 1-4). IEEE.
1

Zalivaka, S. S., Ivaniuk, A. A., & Chang, C. H. (2018). Reliable and modeling attack resistant
authentication of arbiter PUF in FPGA implementation with trinary quadruple
response. IEEE Transactions on Information Forensics and Security. 14(4). 1109-1123.
2
authentication of arbiter PUF in FPGA implementation with trinary quadruple
response. IEEE Transactions on Information Forensics and Security. 14(4). 1109-1123.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




