Reviewing and Comparing Cybersecurity Documentation Frameworks
VerifiedAdded on 2021/06/14
|9
|1340
|112
Report
AI Summary
This report provides a comparative analysis of cybersecurity documentation, focusing on ISO 27001 and the NIST Cybersecurity Framework. The report begins by highlighting the differences, similarities, and intersections of the two frameworks. It then delves into the NIST Cybersecurity Framework, discussing its structure, core components, and application stages, including identification, protection, detection, response, and recovery. The ISO 27001 standard is also examined, detailing its role in designing, implementing, and managing information security systems. The report further explores the controls employed in both frameworks, including control groups, purposes, and implementation requirements. It emphasizes the importance of the NIST framework in establishing security measures and the benefits of ISO 27001 certification. The report concludes by outlining the pros and cons of each framework, providing a comprehensive overview of their strengths and weaknesses in ensuring robust cybersecurity practices and effective risk management. The report also includes references to supporting literature.

Running Head: REVIEWING THE PROCESS OF CYBER-SECURITY DOCUMENTATION 1
Reviewing the Process of Cyber-security documentation
Name of the Student
University of Affiliation
Reviewing the Process of Cyber-security documentation
Name of the Student
University of Affiliation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
REVIEWING THE PROCESS OF CYBER-SECURITY DOCUMENTATION 2
Comparison of ISO 27001 & NIST Cyber-Security Framework
Differences (Honeycutt &
Grumman, 2013)
Similarities (Honeycutt &
Grumman, 2013)
Intersections (Honeycutt & Grumman,
2013)
Cybersecurity Framework has
a better structure in regard to
the development and
execution whereas ISO 27001
has a complex setup and
clearly understood by
everybody.
Both help in selecting the
suitable approach in the
application of the cyber-
security schemes in an
organisation.
The best is often attained when the
planning and building of the entire
information system are conventional to
ISO 27001 and make use of cyber-
security structure, especially during the
process managing risk and in the
employment of the various computer-
generated security features.
Cyber-security Structure
supports the main
organisational board,
engineers and other technical
teams to readily appreciate
the implemented setups
whereas, the ISO 27001
doesn’t do something of the
sought.
Both work on any technology
thus, appropriate for most
current institutions.
Both are determined to ensure
realization of business
welfares, observing the legal
Comparison of ISO 27001 & NIST Cyber-Security Framework
Differences (Honeycutt &
Grumman, 2013)
Similarities (Honeycutt &
Grumman, 2013)
Intersections (Honeycutt & Grumman,
2013)
Cybersecurity Framework has
a better structure in regard to
the development and
execution whereas ISO 27001
has a complex setup and
clearly understood by
everybody.
Both help in selecting the
suitable approach in the
application of the cyber-
security schemes in an
organisation.
The best is often attained when the
planning and building of the entire
information system are conventional to
ISO 27001 and make use of cyber-
security structure, especially during the
process managing risk and in the
employment of the various computer-
generated security features.
Cyber-security Structure
supports the main
organisational board,
engineers and other technical
teams to readily appreciate
the implemented setups
whereas, the ISO 27001
doesn’t do something of the
sought.
Both work on any technology
thus, appropriate for most
current institutions.
Both are determined to ensure
realization of business
welfares, observing the legal
REVIEWING THE PROCESS OF CYBER-SECURITY DOCUMENTATION 3
and supervisory necessities
and also the desires of every
involved party.
With ISO 2700, companies
can get certified against it this
is not possible with the cyber-
security framework.
Both aims at exercising bet
risk management practicies.
CSF is only focused on the
planning and implementation
of systems that safeguard
information systems and its’
contents whereas ISO 27001
approaches the
implementation of the same
in a more detailed manner
since its’ procedures are
executed on the basis
Planning-Doing-Checking-
Acting sequence.
NIST Cyber-Security-Framework brief discussion
The NIST CSF was originally intended to respond to the Managerial Directive 13636
which was meant for bringing the required improvement on security systems of the National
and supervisory necessities
and also the desires of every
involved party.
With ISO 2700, companies
can get certified against it this
is not possible with the cyber-
security framework.
Both aims at exercising bet
risk management practicies.
CSF is only focused on the
planning and implementation
of systems that safeguard
information systems and its’
contents whereas ISO 27001
approaches the
implementation of the same
in a more detailed manner
since its’ procedures are
executed on the basis
Planning-Doing-Checking-
Acting sequence.
NIST Cyber-Security-Framework brief discussion
The NIST CSF was originally intended to respond to the Managerial Directive 13636
which was meant for bringing the required improvement on security systems of the National
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

REVIEWING THE PROCESS OF CYBER-SECURITY DOCUMENTATION 4
Critical Infrastructure. This CSF would form the basis on which minimum amount of cyber-
attack cases ensured. After proving that it had an incredibly positive impact on the NCI, it was
modified to suit different set-ups. This helped other administrations to adopt its' technology.
The CSF has its’ documentation divided into various fields; structural fundamentals, the
frame-shape and the execution stages. The framework fundamentals offer a detailed description
of the chief utilities that an info-security-system employs during its' daily operations. These
utilities comprise of identification, shielding, revealing, reacting and retrieval of data. For the
effective application of the individual utilities, the referencing other documents such as COBIT 5
and NIST 800-53 is inevitable. These additional references provide precise controls and
procedures needed in the actual implementation of the functions (Krutz & Vines, 2010).
Critical Infrastructure. This CSF would form the basis on which minimum amount of cyber-
attack cases ensured. After proving that it had an incredibly positive impact on the NCI, it was
modified to suit different set-ups. This helped other administrations to adopt its' technology.
The CSF has its’ documentation divided into various fields; structural fundamentals, the
frame-shape and the execution stages. The framework fundamentals offer a detailed description
of the chief utilities that an info-security-system employs during its' daily operations. These
utilities comprise of identification, shielding, revealing, reacting and retrieval of data. For the
effective application of the individual utilities, the referencing other documents such as COBIT 5
and NIST 800-53 is inevitable. These additional references provide precise controls and
procedures needed in the actual implementation of the functions (Krutz & Vines, 2010).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
REVIEWING THE PROCESS OF CYBER-SECURITY DOCUMENTATION 5
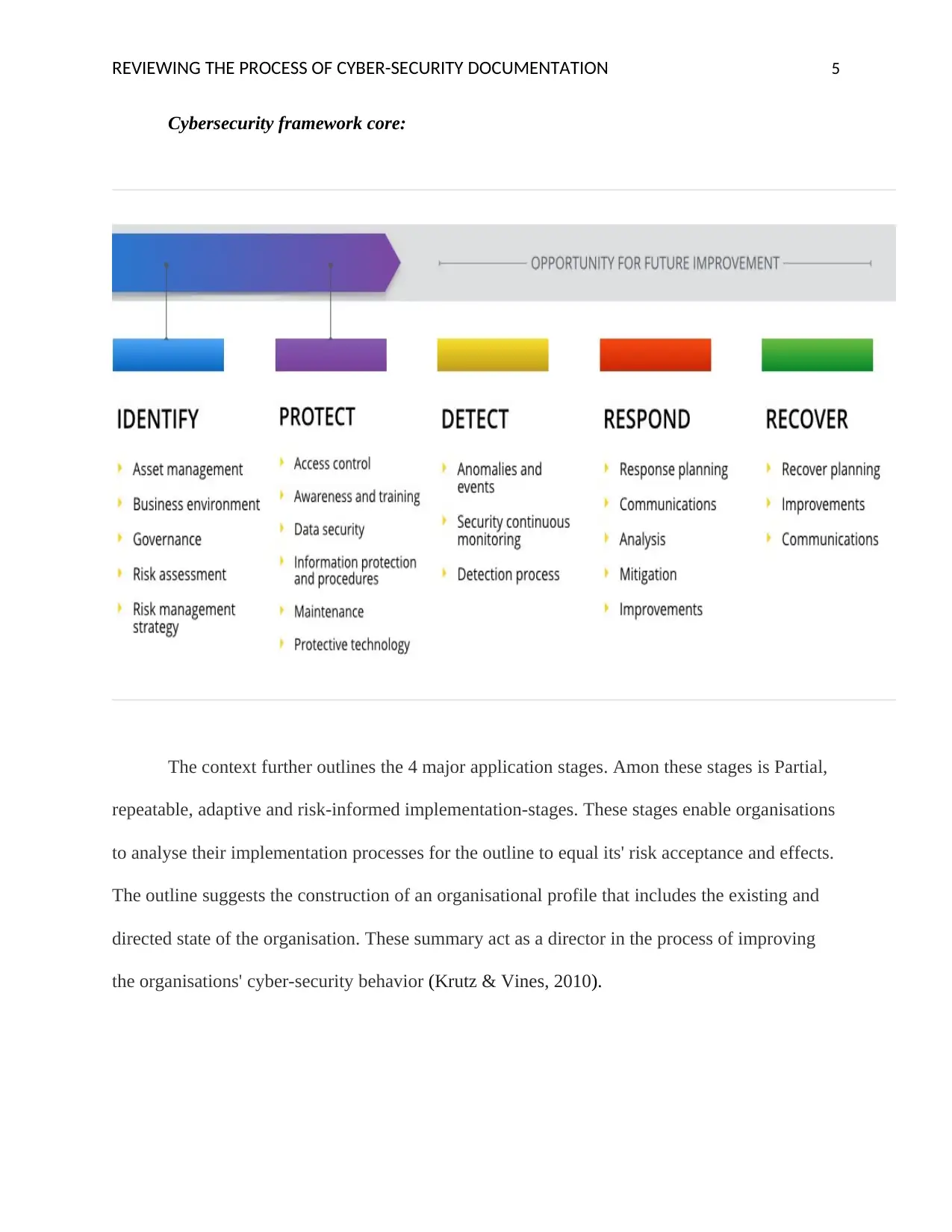
Cybersecurity framework core:
The context further outlines the 4 major application stages. Amon these stages is Partial,
repeatable, adaptive and risk-informed implementation-stages. These stages enable organisations
to analyse their implementation processes for the outline to equal its' risk acceptance and effects.
The outline suggests the construction of an organisational profile that includes the existing and
directed state of the organisation. These summary act as a director in the process of improving
the organisations' cyber-security behavior (Krutz & Vines, 2010).
Cybersecurity framework core:
The context further outlines the 4 major application stages. Amon these stages is Partial,
repeatable, adaptive and risk-informed implementation-stages. These stages enable organisations
to analyse their implementation processes for the outline to equal its' risk acceptance and effects.
The outline suggests the construction of an organisational profile that includes the existing and
directed state of the organisation. These summary act as a director in the process of improving
the organisations' cyber-security behavior (Krutz & Vines, 2010).
REVIEWING THE PROCESS OF CYBER-SECURITY DOCUMENTATION 6
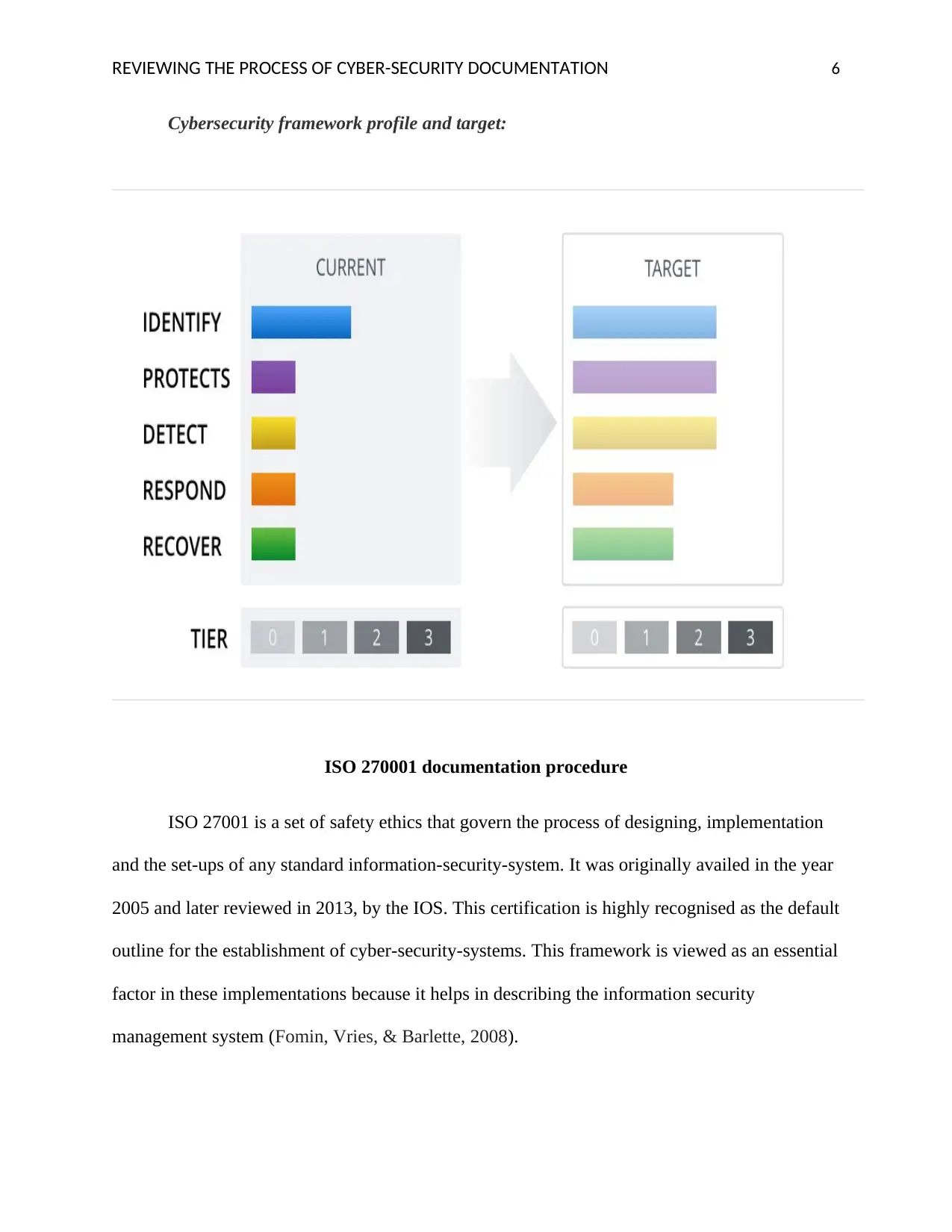
Cybersecurity framework profile and target:
ISO 270001 documentation procedure
ISO 27001 is a set of safety ethics that govern the process of designing, implementation
and the set-ups of any standard information-security-system. It was originally availed in the year
2005 and later reviewed in 2013, by the IOS. This certification is highly recognised as the default
outline for the establishment of cyber-security-systems. This framework is viewed as an essential
factor in these implementations because it helps in describing the information security
management system (Fomin, Vries, & Barlette, 2008).
Cybersecurity framework profile and target:
ISO 270001 documentation procedure
ISO 27001 is a set of safety ethics that govern the process of designing, implementation
and the set-ups of any standard information-security-system. It was originally availed in the year
2005 and later reviewed in 2013, by the IOS. This certification is highly recognised as the default
outline for the establishment of cyber-security-systems. This framework is viewed as an essential
factor in these implementations because it helps in describing the information security
management system (Fomin, Vries, & Barlette, 2008).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

REVIEWING THE PROCESS OF CYBER-SECURITY DOCUMENTATION 7
What are some of the controls employed in the documentation CSF and ISO 270001?
(Knowles, Prince, Hutchison, Disso, & Jones, 2015.)
1. Control groups including tropical information protection.
2. Control purposes including various sub-topical safety zones within the control
classifications.
3. Controls which provides the specific information protection requirements based on ISO
27001.
4. Implementation requirement level controls which prescriptive requirement provided
along with the associated risk factors.
5. Requirements control which provide detailed prescriptive requirements contained in an
information requirement level that support the control specification.
6. Standard mappings controls which specify an authoritative source that is directly or
indirectly supported by the control requirements.
NIST Cyber-Security-Framework is essential in founding safety measures for any
organisation.
The creation of Framework-Profiles helps the organisations involved in finding sectors
that critically require strengthening and areas requiring implementation of new processes.
Besides, this framework, ensure efficiency in cost and communicating development activities
among the parties involved. Finally, the sketches and related execution strategies can be
leveraged as durable quantities in a demonstration of the outstanding repair. (Marston, Li,
Bandyopadhyay, Zhang, & Ghalsasi, 2011).
What are some of the controls employed in the documentation CSF and ISO 270001?
(Knowles, Prince, Hutchison, Disso, & Jones, 2015.)
1. Control groups including tropical information protection.
2. Control purposes including various sub-topical safety zones within the control
classifications.
3. Controls which provides the specific information protection requirements based on ISO
27001.
4. Implementation requirement level controls which prescriptive requirement provided
along with the associated risk factors.
5. Requirements control which provide detailed prescriptive requirements contained in an
information requirement level that support the control specification.
6. Standard mappings controls which specify an authoritative source that is directly or
indirectly supported by the control requirements.
NIST Cyber-Security-Framework is essential in founding safety measures for any
organisation.
The creation of Framework-Profiles helps the organisations involved in finding sectors
that critically require strengthening and areas requiring implementation of new processes.
Besides, this framework, ensure efficiency in cost and communicating development activities
among the parties involved. Finally, the sketches and related execution strategies can be
leveraged as durable quantities in a demonstration of the outstanding repair. (Marston, Li,
Bandyopadhyay, Zhang, & Ghalsasi, 2011).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

REVIEWING THE PROCESS OF CYBER-SECURITY DOCUMENTATION 8
Among the current industry-related standards, ISO 270001 is the most recommended.
ISO 27001 is an international based industrial best practice because it best describes the
information in security management. It demonstrates how a firm follows the best
independent data safety run-through. This standard is reinforced by its program of exercise
for the data safety organisation. It also essential in safeguarding organisations' delicate data,
escaping business drawbacks that are associated with the information breaks and sanctions
organisation in tendering contracts based on ISO condition (Tarantino, 2008).
Pros: Submission to ISO 27001 proves to clients that the organisation have employed
best practices in securing their information.
Any organization that comply with ISO 27001 finds it easy to avoide finance-related
punishments and other damages related to illegal activities are avoided (Fenz, Goluch,
Ekelhart, Riedl, & Weippl, 2007).
Cons: ISO/IEC 27001 is industry-agnostic and doesn’t fully address some of the
concerns. The requirements provided by ISO are also more generic and less prescriptive
(Fenz, Goluch, Ekelhart, Riedl, & Weippl, 2007).
Among the current industry-related standards, ISO 270001 is the most recommended.
ISO 27001 is an international based industrial best practice because it best describes the
information in security management. It demonstrates how a firm follows the best
independent data safety run-through. This standard is reinforced by its program of exercise
for the data safety organisation. It also essential in safeguarding organisations' delicate data,
escaping business drawbacks that are associated with the information breaks and sanctions
organisation in tendering contracts based on ISO condition (Tarantino, 2008).
Pros: Submission to ISO 27001 proves to clients that the organisation have employed
best practices in securing their information.
Any organization that comply with ISO 27001 finds it easy to avoide finance-related
punishments and other damages related to illegal activities are avoided (Fenz, Goluch,
Ekelhart, Riedl, & Weippl, 2007).
Cons: ISO/IEC 27001 is industry-agnostic and doesn’t fully address some of the
concerns. The requirements provided by ISO are also more generic and less prescriptive
(Fenz, Goluch, Ekelhart, Riedl, & Weippl, 2007).

REVIEWING THE PROCESS OF CYBER-SECURITY DOCUMENTATION 9
References
Fenz, S., Goluch, G., Ekelhart, A., Riedl, B., & Weippl, E. (2007, December). Information
security fortification by ontological mapping of the ISO/IEC 27001 standard. In prdc(pp. 381-
388). IEEE.
Fomin, V. V., Vries, H., & Barlette, Y. (2008, September). ISO/IEC 27001 information systems
management standard: exploring the reasons for low adoption. In Proceedings of the third
European conference on Management of Technology (EuroMOT).
Honeycutt, D., & Grumman, N. (2013). Developing a Framework to Improve Critical
Infrastructure Cybersecurity.
Knowles, W., Prince, D., Hutchison, D., Disso, J. F. P., & Jones, K. (2015). A survey of cyber
security management in industrial control systems. International journal of critical
infrastructure protection.
Krutz, R. L., & Vines, R. D. (2010). Cloud security: A comprehensive guide to secure cloud
computing. Wiley Publishing.
Marston, S., Li, Z., Bandyopadhyay, S., Zhang, J., & Ghalsasi, A. (2011). Cloud computing—
The business perspective. Decision support systems, 51(1), 176-189.
Tarantino, A. (2008). Governance, risk, and compliance handbook: technology, finance,
environmental, and international guidance and best practices. John Wiley & Sons.
References
Fenz, S., Goluch, G., Ekelhart, A., Riedl, B., & Weippl, E. (2007, December). Information
security fortification by ontological mapping of the ISO/IEC 27001 standard. In prdc(pp. 381-
388). IEEE.
Fomin, V. V., Vries, H., & Barlette, Y. (2008, September). ISO/IEC 27001 information systems
management standard: exploring the reasons for low adoption. In Proceedings of the third
European conference on Management of Technology (EuroMOT).
Honeycutt, D., & Grumman, N. (2013). Developing a Framework to Improve Critical
Infrastructure Cybersecurity.
Knowles, W., Prince, D., Hutchison, D., Disso, J. F. P., & Jones, K. (2015). A survey of cyber
security management in industrial control systems. International journal of critical
infrastructure protection.
Krutz, R. L., & Vines, R. D. (2010). Cloud security: A comprehensive guide to secure cloud
computing. Wiley Publishing.
Marston, S., Li, Z., Bandyopadhyay, S., Zhang, J., & Ghalsasi, A. (2011). Cloud computing—
The business perspective. Decision support systems, 51(1), 176-189.
Tarantino, A. (2008). Governance, risk, and compliance handbook: technology, finance,
environmental, and international guidance and best practices. John Wiley & Sons.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





