RFID Based Security and Access Control System: Competency Report
VerifiedAdded on 2023/06/15
|9
|1608
|153
Report
AI Summary
This competency demonstration report details the development and implementation of an RFID-based security and access control system. The project involved designing a system utilizing RFID and biometrics to enhance security by reading user data upon arrival, capturing images, and granting access only upon database verification. The system incorporates a GSM modem for emergency calls and alarms. The report outlines the project's objectives, including developing an advanced security system, utilizing RFID technology, adhering to schedules, managing the team, and controlling the budget. The author's responsibilities included leading the team, establishing components, fixing RFID tags, readers, cameras, GSM modems, microcontrollers, and integrating them within the designed model. The report also discusses the engineering knowledge and skills applied, issues encountered such as database size limitations, solutions implemented, and collaborative efforts undertaken to ensure the successful delivery of the project. The author also contributed to the hardware component establishment, project development auditing, data collection, and program implementation for user access control.
COMPETENCY DEMONSTRATION REPORT
Career Episode 1
KATUDIA VEENAY KISHOR MEENA
Career Episode 1
KATUDIA VEENAY KISHOR MEENA
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CE 1.1 Project Information
Name of the project: Implementation of RFID Based Security and Access Control
System
Location of the project: [PLEASE FILL]
Project Duration: [PLEASE FILL]
Organization: [PLEASE FILL]
Role and Designation during the time: Team Leader
CE 1.2 Project Background
CE 1.2.1 Characteristics of the project
I have developed the design of the Security and access control system through utilizing
biometrics and RFID technology in a manner to enhance the security system. I had implemented
the RFID in a manner to read the user whenever he or she reaches the door, capture an image,
and will allow the individual to enter the door only if the database meets the same value. The
system will identify whether the captured image and card belongs to the same user or not and
thereafter, allows the user to enter the room. I had developed this project to be installed at the
doors. I had also installed a GSM Modem that will be applicable to the system to make an
emergency call and alarm the building to the owner of the home or office. I had developed a
project that is applicable to enhancing the security system of the building or home where the
system will be installed.
Name of the project: Implementation of RFID Based Security and Access Control
System
Location of the project: [PLEASE FILL]
Project Duration: [PLEASE FILL]
Organization: [PLEASE FILL]
Role and Designation during the time: Team Leader
CE 1.2 Project Background
CE 1.2.1 Characteristics of the project
I have developed the design of the Security and access control system through utilizing
biometrics and RFID technology in a manner to enhance the security system. I had implemented
the RFID in a manner to read the user whenever he or she reaches the door, capture an image,
and will allow the individual to enter the door only if the database meets the same value. The
system will identify whether the captured image and card belongs to the same user or not and
thereafter, allows the user to enter the room. I had developed this project to be installed at the
doors. I had also installed a GSM Modem that will be applicable to the system to make an
emergency call and alarm the building to the owner of the home or office. I had developed a
project that is applicable to enhancing the security system of the building or home where the
system will be installed.

CE 1.2.2 Objectives developed for the project
I had identified and set the following objectives for the successful delivery of the project
and introducing an option to the world with a much advanced and secured option to the world:
To develop a security system that is much advanced than earlier security systems
To utilize the RFID for presenting the advanced security system
To develop the project within the expected schedule
To manage the whole team towards single objective of project completion
To manage the budget of the project and keep it low as much possible
CE 1.2.3 My area of work
I had led the team towards the accomplishment of the objectives and activities of the
project and tried to accomplish my roles and team members’ roles with responsibility. I was
taking care of the establishment of the components within the established design and I had
connected all the components for the team within the system. I had fixed the RFID tag, and
reader, camera, GSM modem, microcontroller, non-volatile RAM, door locks, and alarm within
the designed model. I had used the “IPC80 passive RFID tag” that can be operated at 125 KHz
frequency in ASK format, and “IP 10 proximity card reader” for the signal transmission. Other
products were selected considering of high quality at lower price. We had used “FEC FC440
programmable logic controller (PLC)”, which was the most important part of the project for the
identification of the individuals and the cars through the RFID tag implemented on them.
I had identified and set the following objectives for the successful delivery of the project
and introducing an option to the world with a much advanced and secured option to the world:
To develop a security system that is much advanced than earlier security systems
To utilize the RFID for presenting the advanced security system
To develop the project within the expected schedule
To manage the whole team towards single objective of project completion
To manage the budget of the project and keep it low as much possible
CE 1.2.3 My area of work
I had led the team towards the accomplishment of the objectives and activities of the
project and tried to accomplish my roles and team members’ roles with responsibility. I was
taking care of the establishment of the components within the established design and I had
connected all the components for the team within the system. I had fixed the RFID tag, and
reader, camera, GSM modem, microcontroller, non-volatile RAM, door locks, and alarm within
the designed model. I had used the “IPC80 passive RFID tag” that can be operated at 125 KHz
frequency in ASK format, and “IP 10 proximity card reader” for the signal transmission. Other
products were selected considering of high quality at lower price. We had used “FEC FC440
programmable logic controller (PLC)”, which was the most important part of the project for the
identification of the individuals and the cars through the RFID tag implemented on them.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CE 1.2.4 Project Group
CE 1.2.5 My responsibilities throughout the project
Throughout the whole project, I was responsible for the component purchasing and
system configuration for this project. I assigned the team members with the role that is easy to be
accomplished by them. It was my responsibility to audit that the components are established in
an effective manner for the identification of the tags and matching the data already present in the
database. I had setup two monitoring system established within the building that includes the
entrance and the exit monitoring system and the users will have to move through the evaluation
process at these entry and exit points. I had to make sure that only after the evaluation, the user
will be allowed to enter the premises or leave the premise in manner to make the project much
feasible.
CE 1.2.5 My responsibilities throughout the project
Throughout the whole project, I was responsible for the component purchasing and
system configuration for this project. I assigned the team members with the role that is easy to be
accomplished by them. It was my responsibility to audit that the components are established in
an effective manner for the identification of the tags and matching the data already present in the
database. I had setup two monitoring system established within the building that includes the
entrance and the exit monitoring system and the users will have to move through the evaluation
process at these entry and exit points. I had to make sure that only after the evaluation, the user
will be allowed to enter the premises or leave the premise in manner to make the project much
feasible.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CE 1.3 Distinctive Activity
CE 1.3.1 Comprehending the theory of the project
RFID is a wireless technology that has many applications in the real world for the
automation of various systems. I had used it in my current project for developing a system that
can detect the identity of the individuals entering and leaving a building through utilizing the
PLC. Whenever an individual or car reaches the entry or exit gate, the system will detect the
identity through the RFID tagged in the identity card of the individual or the car or any other
medium. Every RFID tag has been implemented with an UID and the data saved in this tag will
be evaluated using the PLC and the allowance will only be provided if the data collected by
receiver matches with the database. Thereafter, the system will block another user to enter the
premise with same UID.
CE 1.3.2 Engineering knowledge and skills applied in the project
I had implemented Electronics and Telecommunication Engineering skills and
knowledge for the successful establishment of these electronic components and PLC
programming. I had established the components and programming as expressed in the following
flow chart and the project execution was carried out on the same flow chart:
CE 1.3.1 Comprehending the theory of the project
RFID is a wireless technology that has many applications in the real world for the
automation of various systems. I had used it in my current project for developing a system that
can detect the identity of the individuals entering and leaving a building through utilizing the
PLC. Whenever an individual or car reaches the entry or exit gate, the system will detect the
identity through the RFID tagged in the identity card of the individual or the car or any other
medium. Every RFID tag has been implemented with an UID and the data saved in this tag will
be evaluated using the PLC and the allowance will only be provided if the data collected by
receiver matches with the database. Thereafter, the system will block another user to enter the
premise with same UID.
CE 1.3.2 Engineering knowledge and skills applied in the project
I had implemented Electronics and Telecommunication Engineering skills and
knowledge for the successful establishment of these electronic components and PLC
programming. I had established the components and programming as expressed in the following
flow chart and the project execution was carried out on the same flow chart:
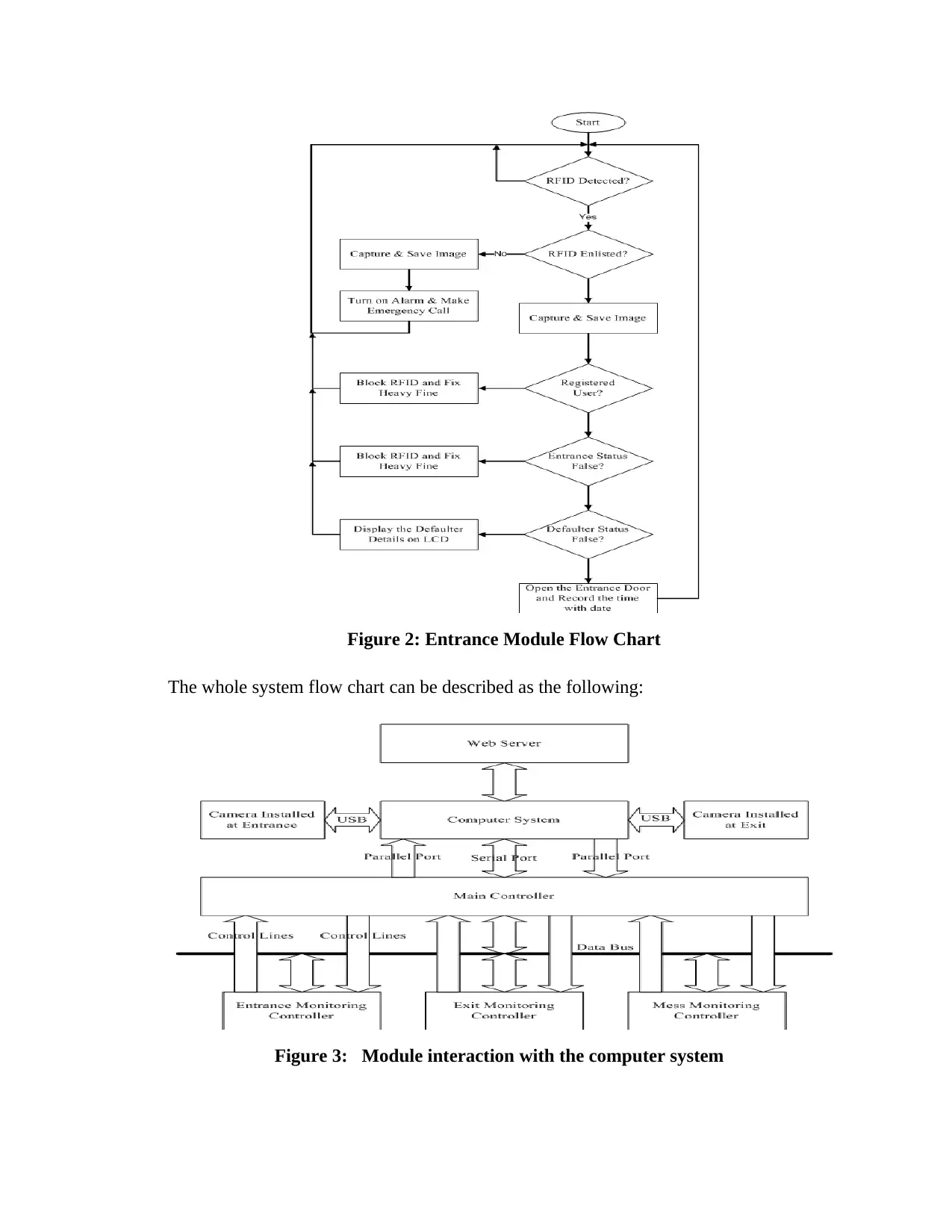
Figure 2: Entrance Module Flow Chart
The whole system flow chart can be described as the following:
Figure 3: “Module interaction with the computer system”
The whole system flow chart can be described as the following:
Figure 3: “Module interaction with the computer system”
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CE 1.3.3 Accomplishment and task performed
The project was divided in two sections with two phases of the evaluation including the
hardware and software, and entrance and exit monitoring system. I had to establish Entrance
Monitoring Controller that was comprised of GSM Modem, RFID, alarm, NV RAM, 16x4 LCD,
scroll keys, and door lock through interfacing AT89C52 microcontroller. Thereafter same
electronic components were installed on the Exit Monitoring Controller. The final phase includes
the web server and computer system where all the information and details related to the
individuals and it will record the details of the check-in and checkout of the individuals
interacting with the system.
CE 1.3.4 Identified issues and their solutions
1.3.4.1 Issues
The biggest problem in the execution of this project was to build a database that will be
comprised of enough data, which can be utilized for the identification and evaluation processes.
A database with large storage of information was needed for the feasibility of the project.
1.3.4.2 Solutions
I had divided the access and security control of the project in two parts that will include
the registration or data feeding into the system and recognition of the data or information
gathered. In manner to enhance the efficiency of the project, I had collected ten images of the
individuals with the access to enter the premise during the moment of issuing the RFID tags for
the individuals.
The project was divided in two sections with two phases of the evaluation including the
hardware and software, and entrance and exit monitoring system. I had to establish Entrance
Monitoring Controller that was comprised of GSM Modem, RFID, alarm, NV RAM, 16x4 LCD,
scroll keys, and door lock through interfacing AT89C52 microcontroller. Thereafter same
electronic components were installed on the Exit Monitoring Controller. The final phase includes
the web server and computer system where all the information and details related to the
individuals and it will record the details of the check-in and checkout of the individuals
interacting with the system.
CE 1.3.4 Identified issues and their solutions
1.3.4.1 Issues
The biggest problem in the execution of this project was to build a database that will be
comprised of enough data, which can be utilized for the identification and evaluation processes.
A database with large storage of information was needed for the feasibility of the project.
1.3.4.2 Solutions
I had divided the access and security control of the project in two parts that will include
the registration or data feeding into the system and recognition of the data or information
gathered. In manner to enhance the efficiency of the project, I had collected ten images of the
individuals with the access to enter the premise during the moment of issuing the RFID tags for
the individuals.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CE 1.3.5 Plan to produce creative and innovative work
Automated recognition system can always be a favourable approach for the enhancement
in the livelihood of the human kind and this system is an approach towards enhancing the
security through restricting the number of authorized users only within a premise. I had used
RFID in manner to provide a remote and automated control over the gates through the
implementation of PLC for the registration and recognition of the data related to the identity of
the individuals. This system will allow the users to enter the premise only if they have an
authorized access (data is already present in the database related to their identity).
CE 1.3.6 Collaborative work
The project was completed under the proper guidance of the assistance professor who
was responsible for our positive motivation towards the accomplishment of the milestones of the
project. I led the team in right path that was consist of four members including me as a leader
and every individual had contributed in an effective and efficient manner for the successful
execution of the project. Every individual involved in this project were responsible for the
feasible delivery of the project and thus, it resulted in the presentation of a successful automated
identification system.
CE 1.4 Project Review
CE .4.1 Project Overview
We had successfully delivered an effective and efficient access and security control
system through the implementation of RFID wireless technology. I had developed a system that
can positively differentiate between an authorized and unauthorized user and stop them from
entering the premise of the building. Even if any individual entered the premise through any
Automated recognition system can always be a favourable approach for the enhancement
in the livelihood of the human kind and this system is an approach towards enhancing the
security through restricting the number of authorized users only within a premise. I had used
RFID in manner to provide a remote and automated control over the gates through the
implementation of PLC for the registration and recognition of the data related to the identity of
the individuals. This system will allow the users to enter the premise only if they have an
authorized access (data is already present in the database related to their identity).
CE 1.3.6 Collaborative work
The project was completed under the proper guidance of the assistance professor who
was responsible for our positive motivation towards the accomplishment of the milestones of the
project. I led the team in right path that was consist of four members including me as a leader
and every individual had contributed in an effective and efficient manner for the successful
execution of the project. Every individual involved in this project were responsible for the
feasible delivery of the project and thus, it resulted in the presentation of a successful automated
identification system.
CE 1.4 Project Review
CE .4.1 Project Overview
We had successfully delivered an effective and efficient access and security control
system through the implementation of RFID wireless technology. I had developed a system that
can positively differentiate between an authorized and unauthorized user and stop them from
entering the premise of the building. Even if any individual entered the premise through any

way, he or she would not be able to get out from there, if proper identification does not matches
the data stored in the database. Entry and exit points were safely guarded by this developed
project and authorized users were issued with a RFID tag that comprised of the key to open the
gates.
CE 1.4.2 My contribution to work
I had contributed in the establishment of the hardware component for the whole project. I
led the team thus, it was my duty to regularly audit the development of the project and manage
the activities those might affect the efficiency and effectiveness of the project. I had contributed
in developing the layout of the whole design and collect data of the authorized users and feed
into the database for the evaluation of the individual’s identity through cross checking the
gathered data and recognized value. I had implemented the program for blocking the user with
the same UID to enter twice the premise.
the data stored in the database. Entry and exit points were safely guarded by this developed
project and authorized users were issued with a RFID tag that comprised of the key to open the
gates.
CE 1.4.2 My contribution to work
I had contributed in the establishment of the hardware component for the whole project. I
led the team thus, it was my duty to regularly audit the development of the project and manage
the activities those might affect the efficiency and effectiveness of the project. I had contributed
in developing the layout of the whole design and collect data of the authorized users and feed
into the database for the evaluation of the individual’s identity through cross checking the
gathered data and recognized value. I had implemented the program for blocking the user with
the same UID to enter twice the premise.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





