Analysis of Security Breaches in RFID Systems: Course Report
VerifiedAdded on 2022/11/09
|32
|9176
|280
Report
AI Summary
This report provides a comprehensive analysis of security breaches in Radio Frequency Identification (RFID) systems. It begins with an introduction to RFID technology, its increasing prevalence, and the associated security concerns. The report outlines the aims and objectives of the analysis, which include determining the maximum reading distance of RFID tags and assessing their vulnerability to tracking and other threats. A literature review explores related studies on RFID security, including the protection of data stored on tags and the integrity of tags. The research methodology section details the research problem, questions, and data collection methods. Experimental approaches are discussed, including experimental design, antenna optimization, and amplifier analysis. The results of the experiments are presented and discussed, followed by conclusions and suggestions for future development. The report focuses on the physical layer security of RFID Proximity tags, examining potential vulnerabilities and experimental methods to assess these risks.

Analysis of Security Breaches in RFID 1
Analysis of Security Breaches in RFID System
Affiliate Institution
Student
Course
Date
Analysis of Security Breaches in RFID System
Affiliate Institution
Student
Course
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Analysis of Security Breaches in RFID 2
Table of Contents
1.0 Introduction...........................................................................................................................................4
1.1.0 Background.....................................................................................................................................4
1.2.0 Aims and Objective........................................................................................................................5
1.3.0 Risk analysis and uncertainties.......................................................................................................6
1.4.0 The scope of this research...............................................................................................................6
2.0 Literature review...................................................................................................................................7
2.1.0Some related studies........................................................................................................................7
Other related studies..............................................................................................................................10
3.0 Research Methodology........................................................................................................................11
3.1 Research problem and questions......................................................................................................12
Security breach and privacy...................................................................................................................12
Purpose of the research..........................................................................................................................13
Data collection and experimental setups................................................................................................13
Data analysis..........................................................................................................................................13
Business solution...................................................................................................................................15
3.2 Selection of research methodology..................................................................................................19
4.0 Experimental Approaches....................................................................................................................19
4.1 Experimental design........................................................................................................................20
4.1 Optimal Antenna.............................................................................................................................21
4.2 Amplifier.........................................................................................................................................22
4.3 Data collection.................................................................................................................................24
5.0 Results.................................................................................................................................................25
5.1 Presentation of the results................................................................................................................25
5.2 Discussion.......................................................................................................................................28
6.0 Conclusion...........................................................................................................................................29
Future development...............................................................................................................................30
References.................................................................................................................................................31
Table of Contents
1.0 Introduction...........................................................................................................................................4
1.1.0 Background.....................................................................................................................................4
1.2.0 Aims and Objective........................................................................................................................5
1.3.0 Risk analysis and uncertainties.......................................................................................................6
1.4.0 The scope of this research...............................................................................................................6
2.0 Literature review...................................................................................................................................7
2.1.0Some related studies........................................................................................................................7
Other related studies..............................................................................................................................10
3.0 Research Methodology........................................................................................................................11
3.1 Research problem and questions......................................................................................................12
Security breach and privacy...................................................................................................................12
Purpose of the research..........................................................................................................................13
Data collection and experimental setups................................................................................................13
Data analysis..........................................................................................................................................13
Business solution...................................................................................................................................15
3.2 Selection of research methodology..................................................................................................19
4.0 Experimental Approaches....................................................................................................................19
4.1 Experimental design........................................................................................................................20
4.1 Optimal Antenna.............................................................................................................................21
4.2 Amplifier.........................................................................................................................................22
4.3 Data collection.................................................................................................................................24
5.0 Results.................................................................................................................................................25
5.1 Presentation of the results................................................................................................................25
5.2 Discussion.......................................................................................................................................28
6.0 Conclusion...........................................................................................................................................29
Future development...............................................................................................................................30
References.................................................................................................................................................31

Analysis of Security Breaches in RFID 3
1.0 Introduction
This theory ponders security parts of Radio Frequency Identification, RFID. The innovation is
pervading the general public, and is quickly ending up some portion of regular day to day
existence for an ever increasing number of clients. Hence, the ramifications of shaky frameworks
are expanding. This proposal will take a gander at the security of RFID Proximity labels at the
physical layer. The proposition will endeavor to decide the most extreme reading separation of
RFID labels, and the innovation's natural weakness to following and different dangers will be
surveyed. Further, the impact of physical protecting will be explored.(Yan, 2008)
1.1.0 Background
Radio Frequency Identification (RFID) is a conventional term for frameworks transmitting the
personality of an article from a tag to peruse utilizing radio recurrence waves. Joined with
exchange of other information, and perhaps cryptographic capacities, this exchange of character
can frame expand conventions supporting propelled frameworks, for example, Access Control
Systems, Payment Systems and Article Surveillance Systems? (Xixi, 2009)
RFID is in no way, shape or form another innovation, however it has some time been very costly.
In any case, the consistent advancement underway systems and so forth has brought about a
considerable lessening in costs of RFID frameworks. The costs are presently low enough to
permit RFID frameworks to be financially possible for an expansive scope of uses. This has
brought about an exponential development of uses using RFID. This development is additionally
catalyzed by backers of RFID declaring the effectiveness and convenience of the innovation. Be
that as it may, the fast dissemination of RFID into regular day to day existence of its clients has
additionally prompted inquiries being posed about the security of such frameworks. One such
1.0 Introduction
This theory ponders security parts of Radio Frequency Identification, RFID. The innovation is
pervading the general public, and is quickly ending up some portion of regular day to day
existence for an ever increasing number of clients. Hence, the ramifications of shaky frameworks
are expanding. This proposal will take a gander at the security of RFID Proximity labels at the
physical layer. The proposition will endeavor to decide the most extreme reading separation of
RFID labels, and the innovation's natural weakness to following and different dangers will be
surveyed. Further, the impact of physical protecting will be explored.(Yan, 2008)
1.1.0 Background
Radio Frequency Identification (RFID) is a conventional term for frameworks transmitting the
personality of an article from a tag to peruse utilizing radio recurrence waves. Joined with
exchange of other information, and perhaps cryptographic capacities, this exchange of character
can frame expand conventions supporting propelled frameworks, for example, Access Control
Systems, Payment Systems and Article Surveillance Systems? (Xixi, 2009)
RFID is in no way, shape or form another innovation, however it has some time been very costly.
In any case, the consistent advancement underway systems and so forth has brought about a
considerable lessening in costs of RFID frameworks. The costs are presently low enough to
permit RFID frameworks to be financially possible for an expansive scope of uses. This has
brought about an exponential development of uses using RFID. This development is additionally
catalyzed by backers of RFID declaring the effectiveness and convenience of the innovation. Be
that as it may, the fast dissemination of RFID into regular day to day existence of its clients has
additionally prompted inquiries being posed about the security of such frameworks. One such
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Analysis of Security Breaches in RFID 4
question is the manner by which effectively people can be followed on the off chance that they
convey RFID labels. (Gaikwad et al., 2017)
All makers of RFID frameworks test the most extreme reading scope of their parsers before these
are placed into creation. Be that as it may, these parsers are commonly not advanced for most
extreme reading range. Further, they are dependent upon guidelines with respect to the
transmitting power and so on over the radio interface. Along these lines, despite the fact that the
most extreme reading scope of standard RFID parsers are confined to a couple of centimeters,
enhanced ill-conceived parsers might have the option to peruse labels at far more prominent
separations.
1.2.0 Aims and Objective
The goal of this undertaking this project is to plan an "RFID based access control framework".
The sole point of this task is to keep away from the passage of any undesirable/robber individual
to some limited region alongside the investigation of RFID and its utilization in this kind of use.
In this task, a RFID card reader will read the RFID cards of the vehicle drivers and utilizing the
idea of sequential correspondence, it will send the RFID card number to the microcontroller.
Already a portion of the card numbers (which are having the entrance to that area) will be put
away in the memory of the microcontroller. In the event that the card number sent by the RFID
reader matches with the id-number put away in microcontroller, at that point the door will open
naturally. Additionally, acquaintance this circuit would empower you see better the basic RFID
based correspondence contraption examined in this ensuing venture. It turns out to be still all the
more intriguing for our locale of gadgets aficionados as RFID source is accessible exceptionally
modest in the market and the average power level accessible for idea learning and showing
reason notwithstanding genuine field use.
question is the manner by which effectively people can be followed on the off chance that they
convey RFID labels. (Gaikwad et al., 2017)
All makers of RFID frameworks test the most extreme reading scope of their parsers before these
are placed into creation. Be that as it may, these parsers are commonly not advanced for most
extreme reading range. Further, they are dependent upon guidelines with respect to the
transmitting power and so on over the radio interface. Along these lines, despite the fact that the
most extreme reading scope of standard RFID parsers are confined to a couple of centimeters,
enhanced ill-conceived parsers might have the option to peruse labels at far more prominent
separations.
1.2.0 Aims and Objective
The goal of this undertaking this project is to plan an "RFID based access control framework".
The sole point of this task is to keep away from the passage of any undesirable/robber individual
to some limited region alongside the investigation of RFID and its utilization in this kind of use.
In this task, a RFID card reader will read the RFID cards of the vehicle drivers and utilizing the
idea of sequential correspondence, it will send the RFID card number to the microcontroller.
Already a portion of the card numbers (which are having the entrance to that area) will be put
away in the memory of the microcontroller. In the event that the card number sent by the RFID
reader matches with the id-number put away in microcontroller, at that point the door will open
naturally. Additionally, acquaintance this circuit would empower you see better the basic RFID
based correspondence contraption examined in this ensuing venture. It turns out to be still all the
more intriguing for our locale of gadgets aficionados as RFID source is accessible exceptionally
modest in the market and the average power level accessible for idea learning and showing
reason notwithstanding genuine field use.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Analysis of Security Breaches in RFID 5
1.3.0 Risk analysis and uncertainties
In embraced a test investigation of the physical properties of RFID frameworks, one of the most
noticeable dangers is the danger of absence of point by point convention data. The RFID
frameworks considered in this proposition are for the most part dependent on standard
conventions, yet even inside such measures, there is space for varieties. This implies it might
demonstrate hard to plan new hardware without any preparation that will interoperate easily with
existing gear. This is additionally upgraded by the way that not many business entertainers are
happy to give nitty-gritty data with respect to their frameworks on the off chance that they dread
that the inquirer is endeavoring to demonstrate that their frameworks are uncertain. (Voeller,
n.d.)
As this proposal is composed as a component of a specialization in Information Security,
absence of specialized ability on electronic circuits, radio strategies, proper estimation systems
and so forth may likewise turn into an issue. This may bring about a significant part of the theory
being founded on investigations performed by others, and as most dire outcome imaginable
outcome in an absolutely hypothetical writing study. Absence of aptitude may likewise back the
work off prompting challenges in keeping the due date. The time limitation is extra significant as
there might be hold ups because of conveyance times and so on if hardware or segments must be
purchased.
1.4.0 The scope of this research
This proposal targets deciding how effectively the greatest reading separation of business RFID
frameworks can be expanded, and thusly decide the labels' defenselessness to skimming and
following. T(Lee, 2017) he impact of physical protecting will likewise be tried. On the off
1.3.0 Risk analysis and uncertainties
In embraced a test investigation of the physical properties of RFID frameworks, one of the most
noticeable dangers is the danger of absence of point by point convention data. The RFID
frameworks considered in this proposition are for the most part dependent on standard
conventions, yet even inside such measures, there is space for varieties. This implies it might
demonstrate hard to plan new hardware without any preparation that will interoperate easily with
existing gear. This is additionally upgraded by the way that not many business entertainers are
happy to give nitty-gritty data with respect to their frameworks on the off chance that they dread
that the inquirer is endeavoring to demonstrate that their frameworks are uncertain. (Voeller,
n.d.)
As this proposal is composed as a component of a specialization in Information Security,
absence of specialized ability on electronic circuits, radio strategies, proper estimation systems
and so forth may likewise turn into an issue. This may bring about a significant part of the theory
being founded on investigations performed by others, and as most dire outcome imaginable
outcome in an absolutely hypothetical writing study. Absence of aptitude may likewise back the
work off prompting challenges in keeping the due date. The time limitation is extra significant as
there might be hold ups because of conveyance times and so on if hardware or segments must be
purchased.
1.4.0 The scope of this research
This proposal targets deciding how effectively the greatest reading separation of business RFID
frameworks can be expanded, and thusly decide the labels' defenselessness to skimming and
following. T(Lee, 2017) he impact of physical protecting will likewise be tried. On the off

Analysis of Security Breaches in RFID 6
chance that time licenses, further examinations concerning the danger of listening stealthily will
be made.
The focal point of this proposal will be on frameworks for Access Control and Biometric
Passports. Both these frameworks are commonly founded on the "ISO/IEC 14443: Identification
cards – Contactless coordinated circuit(s) cards and consequently this standard will fill in as a
kind of perspective point. Other significant measures, for example, the "ISO/IEC 15693:
Identification cards – contactless coordinated circuit(s) cards and "ISO/IEC 10536: Identification
cards – contactless incorporated circuit(s) cards won't be surveyed. The labels examined in this
theory will subsequently only be uninvolved labels that work in the 13.56 MHz recurrence go.
(Vacca, 2014)
Further, the trials will for the most part respect the lower layers of the RFID conventions. In this
way, security highlights executed at the application layer will be talked about, however for the
most part not be tried in the analyses as they ordinarily give little assurance against dangers, for
example, following.
2.0 Literature review
2.1.0Some related studies
The reason for this writing audit is to examine all the examination that has been finished to date.
This part will condense and after that fundamentally break down the research found. From these
discoveries, the paper will propose a hole in the examination that is obvious from the writing.
The writing will be separated into two characterized areas. The security area will talk about the
writing on training of the innovation, informing purchasers with respect to the nearness of RFID
labels, and protection reading measures. The security segment will examine the writing on
chance that time licenses, further examinations concerning the danger of listening stealthily will
be made.
The focal point of this proposal will be on frameworks for Access Control and Biometric
Passports. Both these frameworks are commonly founded on the "ISO/IEC 14443: Identification
cards – Contactless coordinated circuit(s) cards and consequently this standard will fill in as a
kind of perspective point. Other significant measures, for example, the "ISO/IEC 15693:
Identification cards – contactless coordinated circuit(s) cards and "ISO/IEC 10536: Identification
cards – contactless incorporated circuit(s) cards won't be surveyed. The labels examined in this
theory will subsequently only be uninvolved labels that work in the 13.56 MHz recurrence go.
(Vacca, 2014)
Further, the trials will for the most part respect the lower layers of the RFID conventions. In this
way, security highlights executed at the application layer will be talked about, however for the
most part not be tried in the analyses as they ordinarily give little assurance against dangers, for
example, following.
2.0 Literature review
2.1.0Some related studies
The reason for this writing audit is to examine all the examination that has been finished to date.
This part will condense and after that fundamentally break down the research found. From these
discoveries, the paper will propose a hole in the examination that is obvious from the writing.
The writing will be separated into two characterized areas. The security area will talk about the
writing on training of the innovation, informing purchasers with respect to the nearness of RFID
labels, and protection reading measures. The security segment will examine the writing on
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Analysis of Security Breaches in RFID 7
observation, robbery counteractive action, and the utilization RFID to improve the security of the
stockpile change. (Vacca, 2017)
RFID technology is still in a developing stage and more is in the pipeline as far as new
applications. Among applications previously created, RFID labels are being utilized in apparel
for charging and security purposes. RFID labels are inserted inside creatures for following
purposes. RFID labels installed in outfits can be utilized to know the quantity of hours a worker
spends to finish a standard circular task. There are a few affiliations that are master trying against
the utilization of RFID to track individuals dreading the effect on individuals' public activity and
protection. Considering tremendous scale on which RFID will work and considering the way that
it will be available wherever in our lives it is totally important for it to be a protected system.
Even however RFID is as yet not operational on enormous scale, some test shops, writing
expounded on it is generally broad. There are three essential issues encompassing RFID and the
need to ensure exclusive data: Protecting information put away on the tag; Protecting the honesty
of the tag (and in this way thee product); Securing information identified with the sequential
number on a tag, which might be put away in a system database. Industries use RFID for
different applications, for example, individual/vehicle access control, departmental store
security, gear following, things, cheap food foundations, coordination, and so forth. The upgrade
in RFID innovation has brought points of interest that are identified with asset advancement,
expanded effectiveness inside business forms, and improved client care, by and large
enhancements in business activities and human services. Different applications incorporates
programmed toll installments, departmental access control in huge structures. Individual and
vehicle control in a specific zone, security of things which shouldn't leave the zone, gear
following in building firms, clinic recording frameworks. (Anon, n.d.)
observation, robbery counteractive action, and the utilization RFID to improve the security of the
stockpile change. (Vacca, 2017)
RFID technology is still in a developing stage and more is in the pipeline as far as new
applications. Among applications previously created, RFID labels are being utilized in apparel
for charging and security purposes. RFID labels are inserted inside creatures for following
purposes. RFID labels installed in outfits can be utilized to know the quantity of hours a worker
spends to finish a standard circular task. There are a few affiliations that are master trying against
the utilization of RFID to track individuals dreading the effect on individuals' public activity and
protection. Considering tremendous scale on which RFID will work and considering the way that
it will be available wherever in our lives it is totally important for it to be a protected system.
Even however RFID is as yet not operational on enormous scale, some test shops, writing
expounded on it is generally broad. There are three essential issues encompassing RFID and the
need to ensure exclusive data: Protecting information put away on the tag; Protecting the honesty
of the tag (and in this way thee product); Securing information identified with the sequential
number on a tag, which might be put away in a system database. Industries use RFID for
different applications, for example, individual/vehicle access control, departmental store
security, gear following, things, cheap food foundations, coordination, and so forth. The upgrade
in RFID innovation has brought points of interest that are identified with asset advancement,
expanded effectiveness inside business forms, and improved client care, by and large
enhancements in business activities and human services. Different applications incorporates
programmed toll installments, departmental access control in huge structures. Individual and
vehicle control in a specific zone, security of things which shouldn't leave the zone, gear
following in building firms, clinic recording frameworks. (Anon, n.d.)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Analysis of Security Breaches in RFID 8
The Radio Frequency Identification (RFID) is a programmed distinguishing proof framework.
RFID utilizes RF to recognize-tagged things .This information is then gathered and transmitted
to a host framework utilizing a RF Reader. The information transmitted by the tag may give
distinguishing proof or area data, or points of interest about the item labeled, for example, value,
shading, date of procurement; etc. In Bar code the scanner gadget coordinates a light shaft at the
standardized tag. The gadget contains a little tactile reading component. This sensor identifies
the light being reflected again from the standardized identification, and changes over light
vitality into electrical vitality. The outcome is an electrical sign that can be changed over into
information. Every type of correspondence must pursue a lot of conventions, managing such
issues as giving access to the interchanges medium, structure and importance of the information
to be transmitted, and coding and regulation of the information into the transmitted sign. The
conventions have been grown to some degree freely and notwithstanding when institutionalized
are commonly inoperable. Every RFID framework comprises of at any rate one examiner, all the
more normally known as a reader, which uses a radio connect to speak with at any rate one
transponder. The tag by and large contains at least one coordinated circuits, and an exceptional
distinguishing number put away in non-unpredictable memory. The reader is regularly (however
not constantly) incorporated into a system so as to utilize the distinguishing proof information it
gathers. There are three key design parameters that decide the kind of RFID framework being
used: the recurrence (for all intents and purposes proportional to the method of coupling), the
methods for driving the tag, and the correspondences convention utilized. RFID labels react to
reader cross examination without alarming their proprietors or bearers. In this manner, where
perused range grants, furtive checking of labels is a conceivable risk. Most RFID labels radiate
special identifiers, even labels that ensure information with cryptographic calculations in result,
The Radio Frequency Identification (RFID) is a programmed distinguishing proof framework.
RFID utilizes RF to recognize-tagged things .This information is then gathered and transmitted
to a host framework utilizing a RF Reader. The information transmitted by the tag may give
distinguishing proof or area data, or points of interest about the item labeled, for example, value,
shading, date of procurement; etc. In Bar code the scanner gadget coordinates a light shaft at the
standardized tag. The gadget contains a little tactile reading component. This sensor identifies
the light being reflected again from the standardized identification, and changes over light
vitality into electrical vitality. The outcome is an electrical sign that can be changed over into
information. Every type of correspondence must pursue a lot of conventions, managing such
issues as giving access to the interchanges medium, structure and importance of the information
to be transmitted, and coding and regulation of the information into the transmitted sign. The
conventions have been grown to some degree freely and notwithstanding when institutionalized
are commonly inoperable. Every RFID framework comprises of at any rate one examiner, all the
more normally known as a reader, which uses a radio connect to speak with at any rate one
transponder. The tag by and large contains at least one coordinated circuits, and an exceptional
distinguishing number put away in non-unpredictable memory. The reader is regularly (however
not constantly) incorporated into a system so as to utilize the distinguishing proof information it
gathers. There are three key design parameters that decide the kind of RFID framework being
used: the recurrence (for all intents and purposes proportional to the method of coupling), the
methods for driving the tag, and the correspondences convention utilized. RFID labels react to
reader cross examination without alarming their proprietors or bearers. In this manner, where
perused range grants, furtive checking of labels is a conceivable risk. Most RFID labels radiate
special identifiers, even labels that ensure information with cryptographic calculations in result,

Analysis of Security Breaches in RFID 9
an individual conveying a RFID tag successfully communicates a fixed sequential number to
close by readers, giving a prepared vehicle to furtive physical following. Such following is
conceivable regardless of whether a fixed label sequential number is irregular and conveys no
inborn information. The risk to protection develops when a label sequential number is joined
with individual data. (Anon, n.d.)
RFID (Radio Frequency Identification) is as of late getting to be mainstream because of its
comfort and prudent proficiency. Moreover, RFID these days comes into the spotlight as an
innovation to substitute the scanner tag. Then again, RFID is risked from different tackles and
issues as an impediment of boundless RFID arrangement: replay, ridiculing, de-synchronization,
un-versatility, and label cloning. Two validation conventions are proposed for RFID frameworks.
. Another confirmation convention with intermediary, including the properties of the
intermediary, and how it helps in validation is proposed. Comparing with the old style
standardized identification framework, RFID expands the operational good ways from crawls to
various feet (uninvolved RFID labels) or even several feet. Their remote transmission, preparing
and capacity abilities empower them to help the full mechanization of many stock administration
works in the business. Checking an enormous arrangement of RFID labels and recognizing the
missing ones the items that the missing labels are related is troublesome. In view of probabilistic
strategies, plan of a progression of missing-label recognizable proof conventions that utilize
novel systems to decrease the execution time is made.
Other related studies
All through the writing on the instruction of general society of RFID labels, it is reliable that
every one of the creators concur on this theme. VeriChip is an association that inserts people
with RFID labels all together for specific capacities, predominantly restorative records, to be
an individual conveying a RFID tag successfully communicates a fixed sequential number to
close by readers, giving a prepared vehicle to furtive physical following. Such following is
conceivable regardless of whether a fixed label sequential number is irregular and conveys no
inborn information. The risk to protection develops when a label sequential number is joined
with individual data. (Anon, n.d.)
RFID (Radio Frequency Identification) is as of late getting to be mainstream because of its
comfort and prudent proficiency. Moreover, RFID these days comes into the spotlight as an
innovation to substitute the scanner tag. Then again, RFID is risked from different tackles and
issues as an impediment of boundless RFID arrangement: replay, ridiculing, de-synchronization,
un-versatility, and label cloning. Two validation conventions are proposed for RFID frameworks.
. Another confirmation convention with intermediary, including the properties of the
intermediary, and how it helps in validation is proposed. Comparing with the old style
standardized identification framework, RFID expands the operational good ways from crawls to
various feet (uninvolved RFID labels) or even several feet. Their remote transmission, preparing
and capacity abilities empower them to help the full mechanization of many stock administration
works in the business. Checking an enormous arrangement of RFID labels and recognizing the
missing ones the items that the missing labels are related is troublesome. In view of probabilistic
strategies, plan of a progression of missing-label recognizable proof conventions that utilize
novel systems to decrease the execution time is made.
Other related studies
All through the writing on the instruction of general society of RFID labels, it is reliable that
every one of the creators concur on this theme. VeriChip is an association that inserts people
with RFID labels all together for specific capacities, predominantly restorative records, to be
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Analysis of Security Breaches in RFID 10
recorded on the tag. VeriChip states on their website page that training about the innovation is
given to each customer before implantation. Each article features the way that before this
innovation is executed, there should be training about the innovation to the overall population,
paying little mind to whom the duty falls on.(Maruthaveni, 2017)
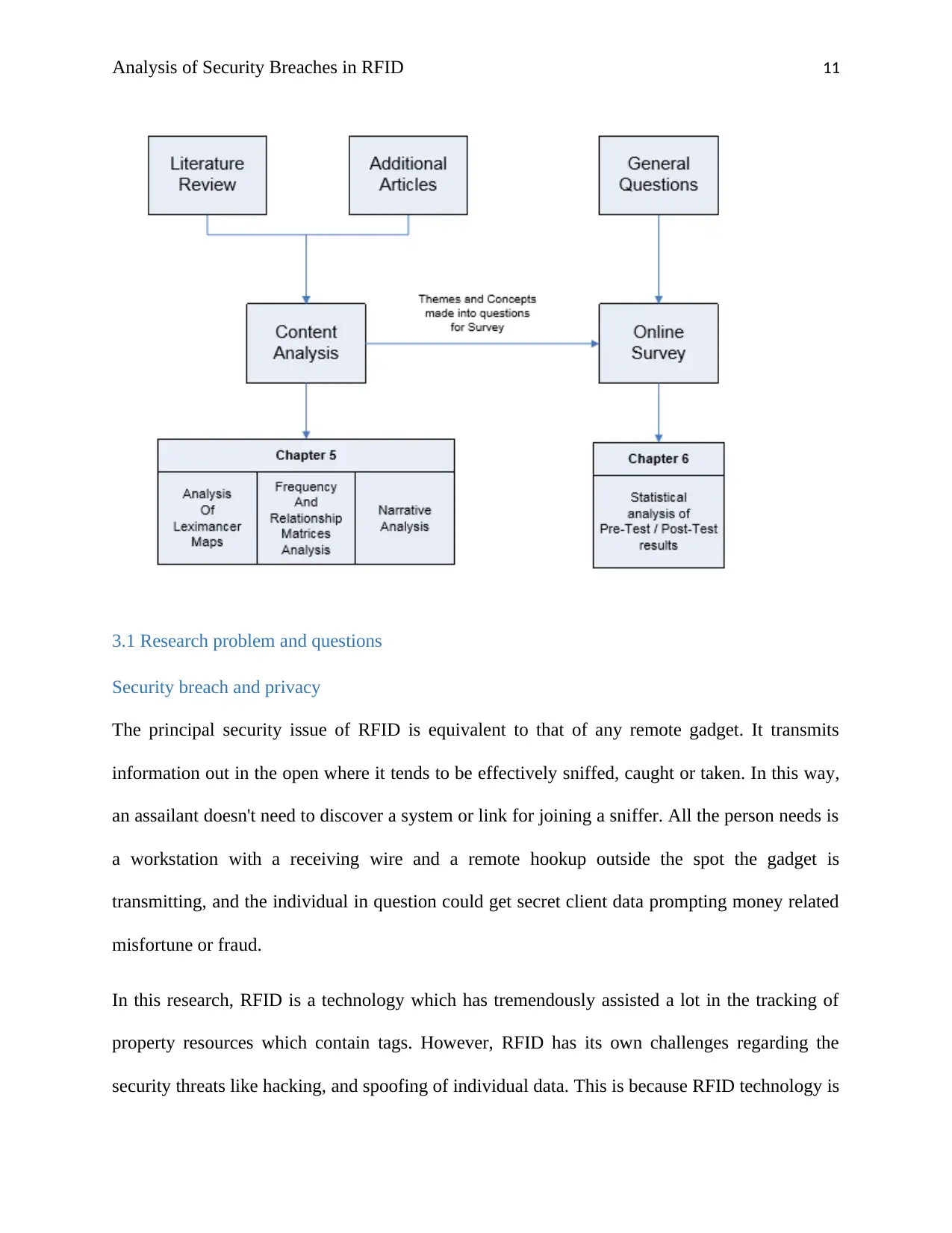
3.0 Research Methodology
The strategy in this paper will be twofold. Right off the bat, subsequent to checking on the
writing, it has turned out to be evident that the bit of missing exploration is that there are no
papers that completely list and examine every one of the issues raised by RFID. This can be
acquired by playing out a substance examination of this subject. The substance investigation will
be PC supported and performed with the assistance of an apparatus named "Leximancer".
It will pursue a great pre-test/post-test plan, which inquires questions, presents data, and after
that poses similar inquiries once more, to check whether giving the respondent accurate data
about the point changes their conclusion. Content Analysis is both subjective and quantitative.
The explanation behind this is content investigation will tally each opportunity specific words
come up and give some measurably investigation, subsequently making it quantitative. It
moreover demonstrates the connections between the topics, and along these lines making it
subjective as well. The online review will be quantitative. Figure 1 is an outline of how the two
inquire about strategies will be utilized so as to finish this exploration.
recorded on the tag. VeriChip states on their website page that training about the innovation is
given to each customer before implantation. Each article features the way that before this
innovation is executed, there should be training about the innovation to the overall population,
paying little mind to whom the duty falls on.(Maruthaveni, 2017)
3.0 Research Methodology
The strategy in this paper will be twofold. Right off the bat, subsequent to checking on the
writing, it has turned out to be evident that the bit of missing exploration is that there are no
papers that completely list and examine every one of the issues raised by RFID. This can be
acquired by playing out a substance examination of this subject. The substance investigation will
be PC supported and performed with the assistance of an apparatus named "Leximancer".
It will pursue a great pre-test/post-test plan, which inquires questions, presents data, and after
that poses similar inquiries once more, to check whether giving the respondent accurate data
about the point changes their conclusion. Content Analysis is both subjective and quantitative.
The explanation behind this is content investigation will tally each opportunity specific words
come up and give some measurably investigation, subsequently making it quantitative. It
moreover demonstrates the connections between the topics, and along these lines making it
subjective as well. The online review will be quantitative. Figure 1 is an outline of how the two
inquire about strategies will be utilized so as to finish this exploration.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Analysis of Security Breaches in RFID 11
3.1 Research problem and questions
Security breach and privacy
The principal security issue of RFID is equivalent to that of any remote gadget. It transmits
information out in the open where it tends to be effectively sniffed, caught or taken. In this way,
an assailant doesn't need to discover a system or link for joining a sniffer. All the person needs is
a workstation with a receiving wire and a remote hookup outside the spot the gadget is
transmitting, and the individual in question could get secret client data prompting money related
misfortune or fraud.
In this research, RFID is a technology which has tremendously assisted a lot in the tracking of
property resources which contain tags. However, RFID has its own challenges regarding the
security threats like hacking, and spoofing of individual data. This is because RFID technology is
3.1 Research problem and questions
Security breach and privacy
The principal security issue of RFID is equivalent to that of any remote gadget. It transmits
information out in the open where it tends to be effectively sniffed, caught or taken. In this way,
an assailant doesn't need to discover a system or link for joining a sniffer. All the person needs is
a workstation with a receiving wire and a remote hookup outside the spot the gadget is
transmitting, and the individual in question could get secret client data prompting money related
misfortune or fraud.
In this research, RFID is a technology which has tremendously assisted a lot in the tracking of
property resources which contain tags. However, RFID has its own challenges regarding the
security threats like hacking, and spoofing of individual data. This is because RFID technology is

Analysis of Security Breaches in RFID 12
consisted of readers which may disclose personal data and hence may lead to an attack or cause a
(DoS) denial of service attack.
The main idea for this report is to work on some specific elements of RFID which will help to
gap the security as a threat to the RFID users. By learning how RFID works, its defects and
security breaches will be clearly outline and the solutions to be put in place are outlined so that
an improvement can be made.
Purpose of the research
The purpose of this research was to carry out a case study analysis report on the security
breaches and the threats which may be initiated by the use of RFID tags. From the research the
report shows that the RFID may expose us to security threats such as hacking, or get hacked by
intruders. The case study shows that the RFID tags comprise of the personal entry data getting
expose over the space through which a hacker may spoofed and modified our data. This is too
dangerous indeed.
Data collection and experimental setups
The research was carried out following the experimental setups. This means that the research
was done on a real-time basis methodology. Experiments were setup and the data collected and
analyzed to produce the best results which will enable the researcher to come up with a solution
which will help to solve the problem.
Data analysis
During the research process, a case study was carried out and the data were collected from
various sources such as internet research, documentaries, direct observations and interviews form
consisted of readers which may disclose personal data and hence may lead to an attack or cause a
(DoS) denial of service attack.
The main idea for this report is to work on some specific elements of RFID which will help to
gap the security as a threat to the RFID users. By learning how RFID works, its defects and
security breaches will be clearly outline and the solutions to be put in place are outlined so that
an improvement can be made.
Purpose of the research
The purpose of this research was to carry out a case study analysis report on the security
breaches and the threats which may be initiated by the use of RFID tags. From the research the
report shows that the RFID may expose us to security threats such as hacking, or get hacked by
intruders. The case study shows that the RFID tags comprise of the personal entry data getting
expose over the space through which a hacker may spoofed and modified our data. This is too
dangerous indeed.
Data collection and experimental setups
The research was carried out following the experimental setups. This means that the research
was done on a real-time basis methodology. Experiments were setup and the data collected and
analyzed to produce the best results which will enable the researcher to come up with a solution
which will help to solve the problem.
Data analysis
During the research process, a case study was carried out and the data were collected from
various sources such as internet research, documentaries, direct observations and interviews form
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 32
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.