University Report: Risk Analysis and Security for ENISA Big Data
VerifiedAdded on 2020/02/23
|17
|4120
|61
Report
AI Summary
This report analyzes the risk and security aspects of ENISA's big data strategy. It begins with an overview of ENISA's case study, including a diagram of its big data security infrastructure, highlighting layers such as data sources, integration processes, data storage, analytics and computing models, and the presentation layer. Key security functions like KNOX, Ranger, encryption, and firewall are discussed in relation to these layers. The report identifies the top threat as technology abuse, detailing various accidental and deliberate threats. It then explores key threat agents, including technology, human errors, and design flaws, and proposes impact reduction options. The report also addresses the improvement of the ETL process and justifies the importance of IT security within ENISA. The analysis underscores the importance of data privacy and the need for robust security measures to protect against data breaches and ensure effective operations. The report concludes by emphasizing the need for continuous monitoring and improvement of security measures to safeguard sensitive information and maintain the integrity of ENISA's big data operations.

Running head: RISK ANALYSIS AND SECURITY
Risk Analysis and Security: ENISA case study
Name of the Student:
Student ID:
Name of the University:
Author’s note:
Risk Analysis and Security: ENISA case study
Name of the Student:
Student ID:
Name of the University:
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1RISK ANALYSIS AND SECURITY
Table of Contents
Introduction......................................................................................................................................2
1. Overview of scenario and ENISA Big Data security infrastructure diagram..............................2
1.1 Overview of ENISA case study.............................................................................................2
1.2 ENISA Big Data Security Infrastructure Diagram................................................................3
2. Explanation of the Top Threat in the ENISA..........................................................................7
3. Key Threat Agents and their Impact Reduction Options.............................................................9
4. Improvement of ETL process....................................................................................................12
5. Justification of IT security in ENISA........................................................................................13
Conclusion.....................................................................................................................................13
References......................................................................................................................................14
Table of Contents
Introduction......................................................................................................................................2
1. Overview of scenario and ENISA Big Data security infrastructure diagram..............................2
1.1 Overview of ENISA case study.............................................................................................2
1.2 ENISA Big Data Security Infrastructure Diagram................................................................3
2. Explanation of the Top Threat in the ENISA..........................................................................7
3. Key Threat Agents and their Impact Reduction Options.............................................................9
4. Improvement of ETL process....................................................................................................12
5. Justification of IT security in ENISA........................................................................................13
Conclusion.....................................................................................................................................13
References......................................................................................................................................14

2RISK ANALYSIS AND SECURITY
Introduction
The risk analysis and security is very important for the organization to implement the
effective operations and integrating the flow of system development (Mahajan, Gaba &
Chauhan, 2016). The development of the project would help in integrating the development of
the operations and apply the effective functions within the organization. The operational
processing is implied for forming the analysis of the risk that the organization might face while
performing the required operations and functions. Accoding to Kao et al. (2014), the
development of the risk analysis is based for the development of the operations to develop the
integrated functions for the processes of the organization.
The following report would help in integrating the operations of the organization for
developing risk assessment and analysis. The report would tend to evaluate the role of
technology for implementing the effective risk assessment by evaluating the case study of
ENISA. The practice of the big data strategy had been helpful for the improvement of operations
within the organization. However, the practice of big data had formed the issues and threats of
security for the organization. The analysis of the threats of the big data strategy for ENISA
would discuss the agents of threat.
1. Overview of scenario and ENISA Big Data security infrastructure diagram
1.1 Overview of ENISA case study
The ENISA organization had deployed the big data analytics for forming the
development of the effective operations and development in the organization (Enisa.europa.eu,
2017). ENISA has implied for developing the big data strategy in their organization. The risk and
Introduction
The risk analysis and security is very important for the organization to implement the
effective operations and integrating the flow of system development (Mahajan, Gaba &
Chauhan, 2016). The development of the project would help in integrating the development of
the operations and apply the effective functions within the organization. The operational
processing is implied for forming the analysis of the risk that the organization might face while
performing the required operations and functions. Accoding to Kao et al. (2014), the
development of the risk analysis is based for the development of the operations to develop the
integrated functions for the processes of the organization.
The following report would help in integrating the operations of the organization for
developing risk assessment and analysis. The report would tend to evaluate the role of
technology for implementing the effective risk assessment by evaluating the case study of
ENISA. The practice of the big data strategy had been helpful for the improvement of operations
within the organization. However, the practice of big data had formed the issues and threats of
security for the organization. The analysis of the threats of the big data strategy for ENISA
would discuss the agents of threat.
1. Overview of scenario and ENISA Big Data security infrastructure diagram
1.1 Overview of ENISA case study
The ENISA organization had deployed the big data analytics for forming the
development of the effective operations and development in the organization (Enisa.europa.eu,
2017). ENISA has implied for developing the big data strategy in their organization. The risk and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3RISK ANALYSIS AND SECURITY
threat management should be implied for forming the effective development of improvement
operations. The big data threats would result in forming the occasional threats for the
organization in integration of the system within the organization. The ENISA is one of the most
effective operations that could monitor the flow of operations within the organization and imply
effective security system within the organization. The big data privacy is a major factor that
accords the deployment of the potential development model for the ENISA (Patil & Seshadri,
(2014). The operations of the organization would be highly improved by the use of the big data
strategy within the organization. The organization had applied ICT based solutions for
developing the security functions for their Big Data Strategy in the organization. The various
owners such as data transformers, data owners, and computation and storage providers at ENISA
would require effective data management and security for the information and data used at the
organization. The best practices of the organization for threat and data management would
involve the effective flow of operations (Vatsalan et al., (2017). The operational processing is
implied for forming the analysis of the risk that the organization might face while performing the
required operations and functions. The development of the risk analysis is based for the
development of the operations to develop the integrated functions for the processes of the
organization.
1.2 ENISA Big Data Security Infrastructure Diagram
ENISA had implied the use of the structured framework for implying the effective
operations of the big data strategy. The infrastructure of the big data analytics is developed for
implementing the effective processing of the information. The various layers of the big data
structure include data sources, integration process, data storage, analytics and computing models,
threat management should be implied for forming the effective development of improvement
operations. The big data threats would result in forming the occasional threats for the
organization in integration of the system within the organization. The ENISA is one of the most
effective operations that could monitor the flow of operations within the organization and imply
effective security system within the organization. The big data privacy is a major factor that
accords the deployment of the potential development model for the ENISA (Patil & Seshadri,
(2014). The operations of the organization would be highly improved by the use of the big data
strategy within the organization. The organization had applied ICT based solutions for
developing the security functions for their Big Data Strategy in the organization. The various
owners such as data transformers, data owners, and computation and storage providers at ENISA
would require effective data management and security for the information and data used at the
organization. The best practices of the organization for threat and data management would
involve the effective flow of operations (Vatsalan et al., (2017). The operational processing is
implied for forming the analysis of the risk that the organization might face while performing the
required operations and functions. The development of the risk analysis is based for the
development of the operations to develop the integrated functions for the processes of the
organization.
1.2 ENISA Big Data Security Infrastructure Diagram
ENISA had implied the use of the structured framework for implying the effective
operations of the big data strategy. The infrastructure of the big data analytics is developed for
implementing the effective processing of the information. The various layers of the big data
structure include data sources, integration process, data storage, analytics and computing models,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4RISK ANALYSIS AND SECURITY
and presentation layer. The big data security infrastructure had been developed using Ms-Visio
by considering the architecture of the big data strategy used in ENISA and it is shown below,
and presentation layer. The big data security infrastructure had been developed using Ms-Visio
by considering the architecture of the big data strategy used in ENISA and it is shown below,
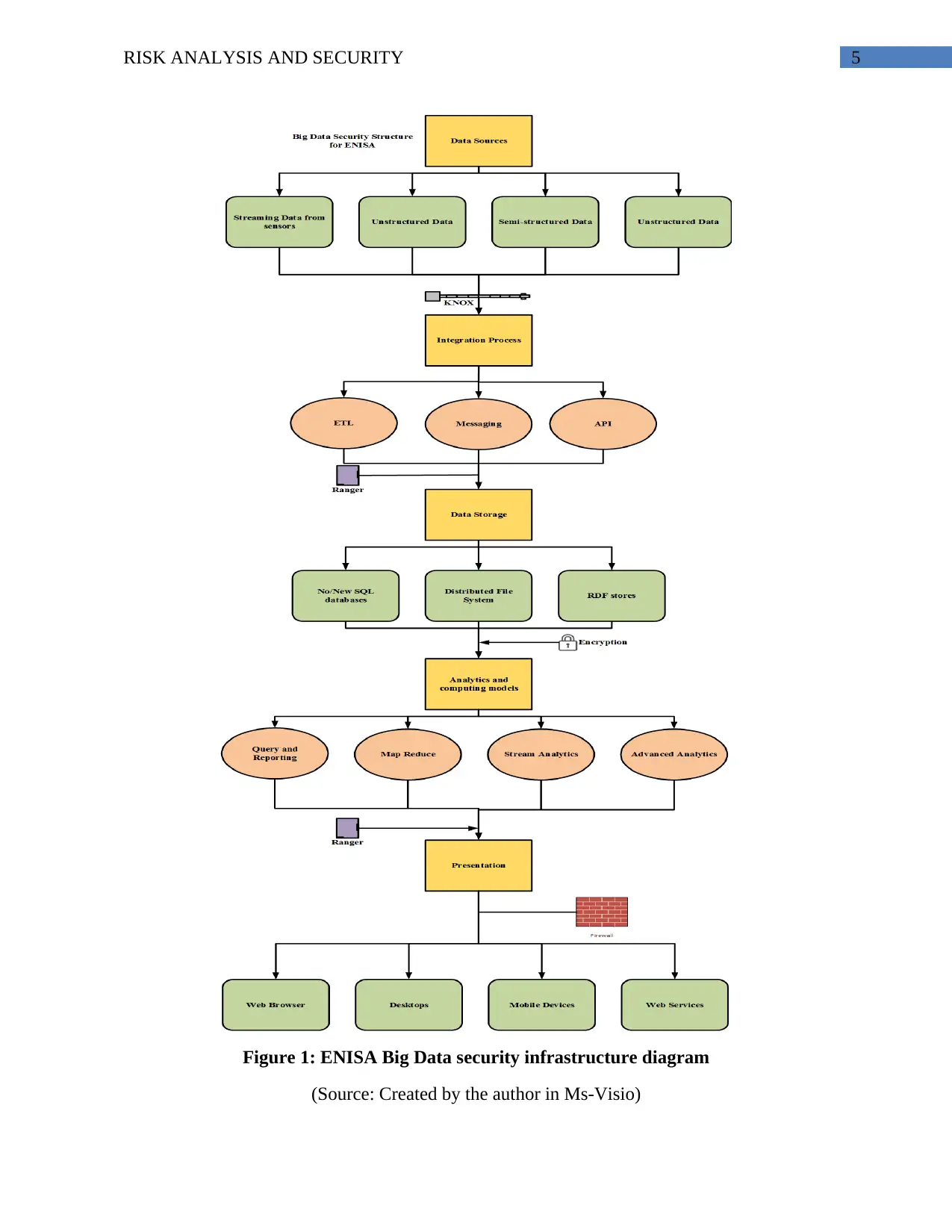
5RISK ANALYSIS AND SECURITY
Figure 1: ENISA Big Data security infrastructure diagram
(Source: Created by the author in Ms-Visio)
Figure 1: ENISA Big Data security infrastructure diagram
(Source: Created by the author in Ms-Visio)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
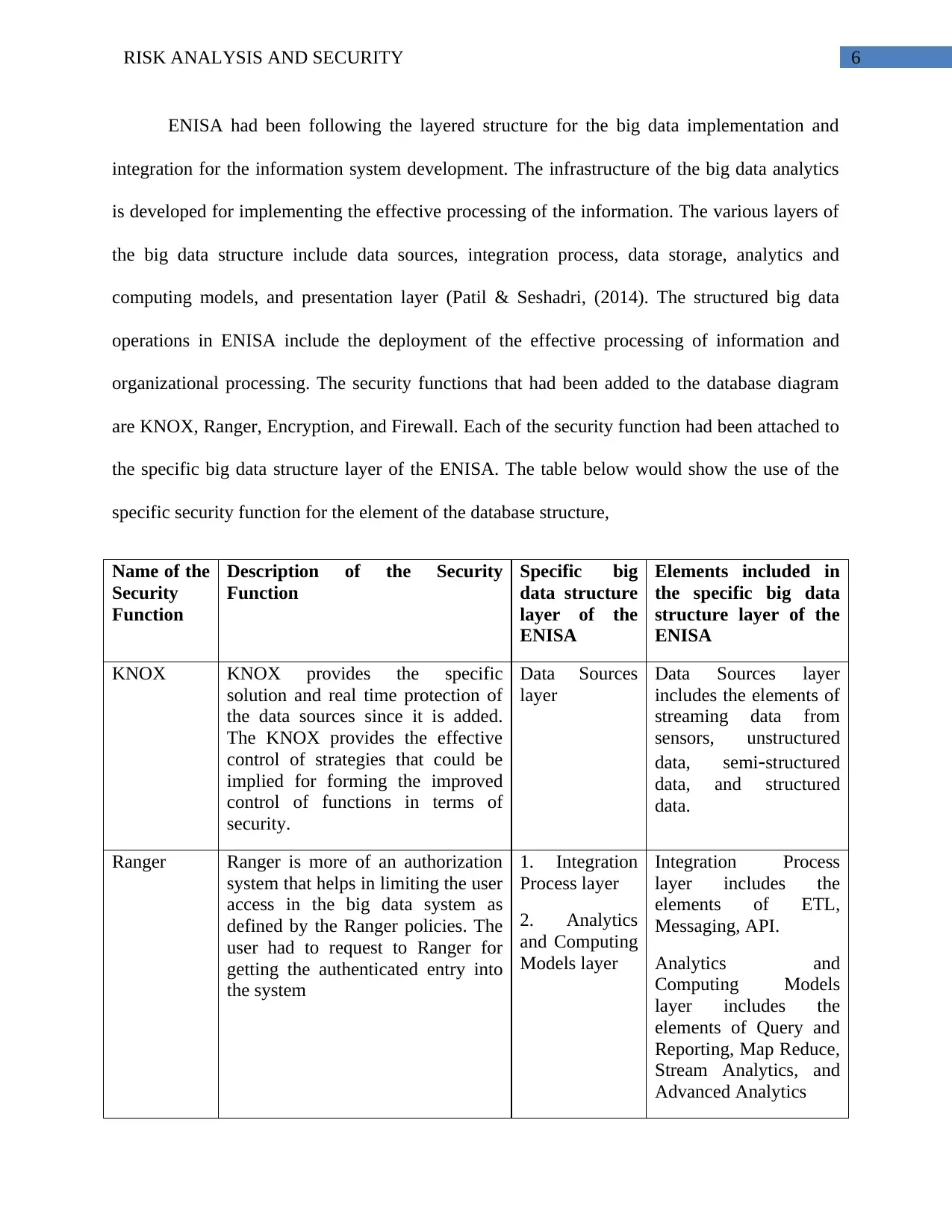
6RISK ANALYSIS AND SECURITY
ENISA had been following the layered structure for the big data implementation and
integration for the information system development. The infrastructure of the big data analytics
is developed for implementing the effective processing of the information. The various layers of
the big data structure include data sources, integration process, data storage, analytics and
computing models, and presentation layer (Patil & Seshadri, (2014). The structured big data
operations in ENISA include the deployment of the effective processing of information and
organizational processing. The security functions that had been added to the database diagram
are KNOX, Ranger, Encryption, and Firewall. Each of the security function had been attached to
the specific big data structure layer of the ENISA. The table below would show the use of the
specific security function for the element of the database structure,
Name of the
Security
Function
Description of the Security
Function
Specific big
data structure
layer of the
ENISA
Elements included in
the specific big data
structure layer of the
ENISA
KNOX KNOX provides the specific
solution and real time protection of
the data sources since it is added.
The KNOX provides the effective
control of strategies that could be
implied for forming the improved
control of functions in terms of
security.
Data Sources
layer
Data Sources layer
includes the elements of
streaming data from
sensors, unstructured
data, semi-structured
data, and structured
data.
Ranger Ranger is more of an authorization
system that helps in limiting the user
access in the big data system as
defined by the Ranger policies. The
user had to request to Ranger for
getting the authenticated entry into
the system
1. Integration
Process layer
2. Analytics
and Computing
Models layer
Integration Process
layer includes the
elements of ETL,
Messaging, API.
Analytics and
Computing Models
layer includes the
elements of Query and
Reporting, Map Reduce,
Stream Analytics, and
Advanced Analytics
ENISA had been following the layered structure for the big data implementation and
integration for the information system development. The infrastructure of the big data analytics
is developed for implementing the effective processing of the information. The various layers of
the big data structure include data sources, integration process, data storage, analytics and
computing models, and presentation layer (Patil & Seshadri, (2014). The structured big data
operations in ENISA include the deployment of the effective processing of information and
organizational processing. The security functions that had been added to the database diagram
are KNOX, Ranger, Encryption, and Firewall. Each of the security function had been attached to
the specific big data structure layer of the ENISA. The table below would show the use of the
specific security function for the element of the database structure,
Name of the
Security
Function
Description of the Security
Function
Specific big
data structure
layer of the
ENISA
Elements included in
the specific big data
structure layer of the
ENISA
KNOX KNOX provides the specific
solution and real time protection of
the data sources since it is added.
The KNOX provides the effective
control of strategies that could be
implied for forming the improved
control of functions in terms of
security.
Data Sources
layer
Data Sources layer
includes the elements of
streaming data from
sensors, unstructured
data, semi-structured
data, and structured
data.
Ranger Ranger is more of an authorization
system that helps in limiting the user
access in the big data system as
defined by the Ranger policies. The
user had to request to Ranger for
getting the authenticated entry into
the system
1. Integration
Process layer
2. Analytics
and Computing
Models layer
Integration Process
layer includes the
elements of ETL,
Messaging, API.
Analytics and
Computing Models
layer includes the
elements of Query and
Reporting, Map Reduce,
Stream Analytics, and
Advanced Analytics
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
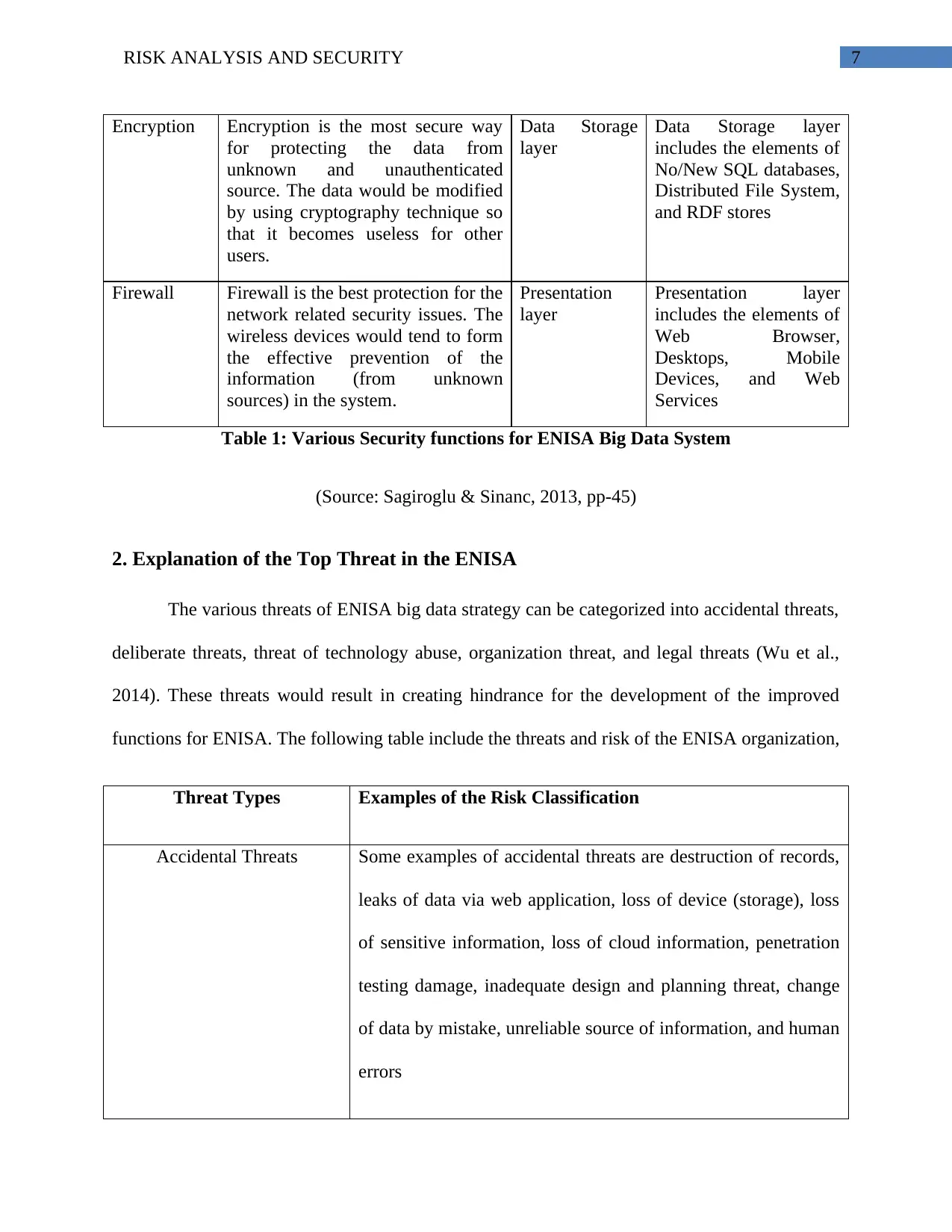
7RISK ANALYSIS AND SECURITY
Encryption Encryption is the most secure way
for protecting the data from
unknown and unauthenticated
source. The data would be modified
by using cryptography technique so
that it becomes useless for other
users.
Data Storage
layer
Data Storage layer
includes the elements of
No/New SQL databases,
Distributed File System,
and RDF stores
Firewall Firewall is the best protection for the
network related security issues. The
wireless devices would tend to form
the effective prevention of the
information (from unknown
sources) in the system.
Presentation
layer
Presentation layer
includes the elements of
Web Browser,
Desktops, Mobile
Devices, and Web
Services
Table 1: Various Security functions for ENISA Big Data System
(Source: Sagiroglu & Sinanc, 2013, pp-45)
2. Explanation of the Top Threat in the ENISA
The various threats of ENISA big data strategy can be categorized into accidental threats,
deliberate threats, threat of technology abuse, organization threat, and legal threats (Wu et al.,
2014). These threats would result in creating hindrance for the development of the improved
functions for ENISA. The following table include the threats and risk of the ENISA organization,
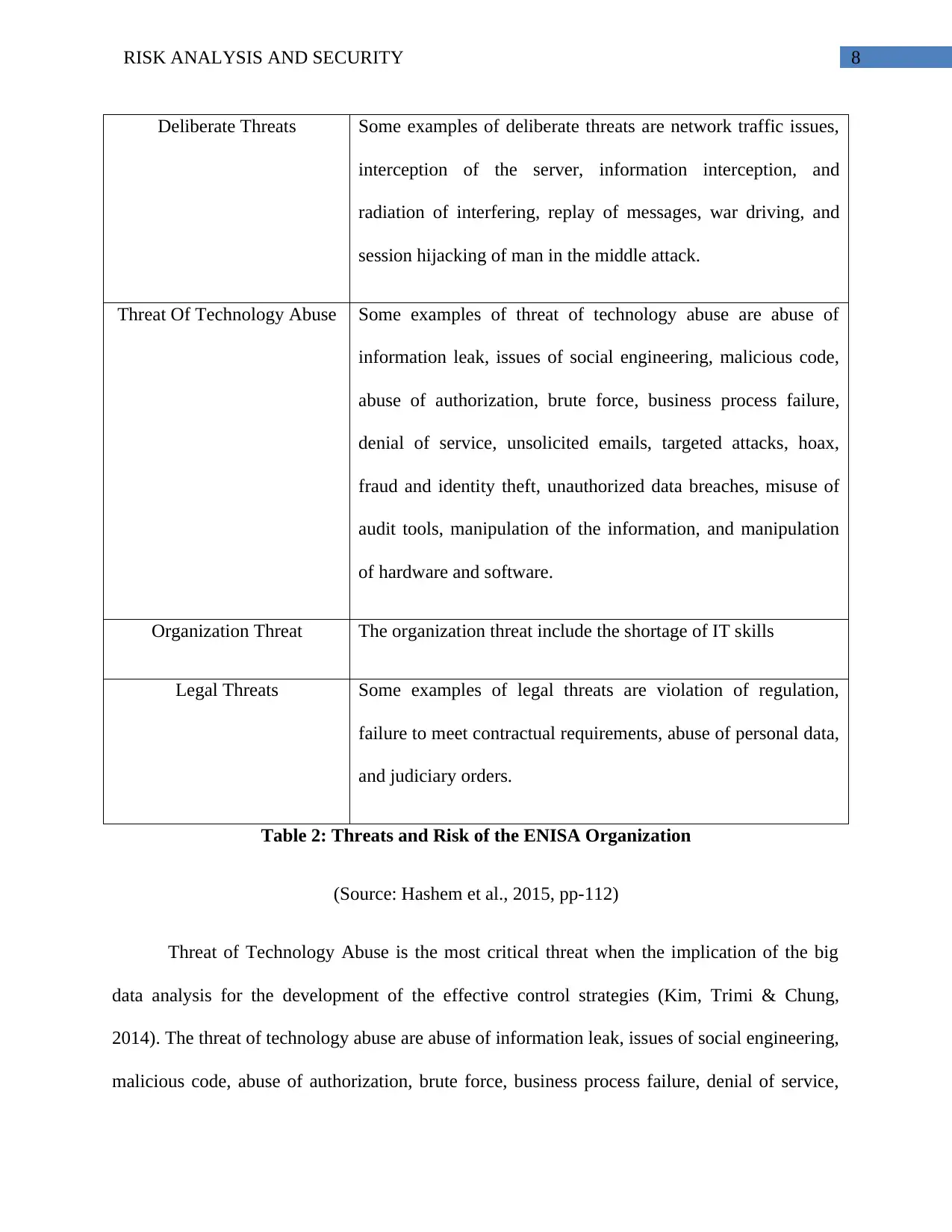
Threat Types Examples of the Risk Classification
Accidental Threats Some examples of accidental threats are destruction of records,
leaks of data via web application, loss of device (storage), loss
of sensitive information, loss of cloud information, penetration
testing damage, inadequate design and planning threat, change
of data by mistake, unreliable source of information, and human
errors
Encryption Encryption is the most secure way
for protecting the data from
unknown and unauthenticated
source. The data would be modified
by using cryptography technique so
that it becomes useless for other
users.
Data Storage
layer
Data Storage layer
includes the elements of
No/New SQL databases,
Distributed File System,
and RDF stores
Firewall Firewall is the best protection for the
network related security issues. The
wireless devices would tend to form
the effective prevention of the
information (from unknown
sources) in the system.
Presentation
layer
Presentation layer
includes the elements of
Web Browser,
Desktops, Mobile
Devices, and Web
Services
Table 1: Various Security functions for ENISA Big Data System
(Source: Sagiroglu & Sinanc, 2013, pp-45)
2. Explanation of the Top Threat in the ENISA
The various threats of ENISA big data strategy can be categorized into accidental threats,
deliberate threats, threat of technology abuse, organization threat, and legal threats (Wu et al.,
2014). These threats would result in creating hindrance for the development of the improved
functions for ENISA. The following table include the threats and risk of the ENISA organization,
Threat Types Examples of the Risk Classification
Accidental Threats Some examples of accidental threats are destruction of records,
leaks of data via web application, loss of device (storage), loss
of sensitive information, loss of cloud information, penetration
testing damage, inadequate design and planning threat, change
of data by mistake, unreliable source of information, and human
errors
8RISK ANALYSIS AND SECURITY
Deliberate Threats Some examples of deliberate threats are network traffic issues,
interception of the server, information interception, and
radiation of interfering, replay of messages, war driving, and
session hijacking of man in the middle attack.
Threat Of Technology Abuse Some examples of threat of technology abuse are abuse of
information leak, issues of social engineering, malicious code,
abuse of authorization, brute force, business process failure,
denial of service, unsolicited emails, targeted attacks, hoax,
fraud and identity theft, unauthorized data breaches, misuse of
audit tools, manipulation of the information, and manipulation
of hardware and software.
Organization Threat The organization threat include the shortage of IT skills
Legal Threats Some examples of legal threats are violation of regulation,
failure to meet contractual requirements, abuse of personal data,
and judiciary orders.
Table 2: Threats and Risk of the ENISA Organization
(Source: Hashem et al., 2015, pp-112)
Threat of Technology Abuse is the most critical threat when the implication of the big
data analysis for the development of the effective control strategies (Kim, Trimi & Chung,
2014). The threat of technology abuse are abuse of information leak, issues of social engineering,
malicious code, abuse of authorization, brute force, business process failure, denial of service,
Deliberate Threats Some examples of deliberate threats are network traffic issues,
interception of the server, information interception, and
radiation of interfering, replay of messages, war driving, and
session hijacking of man in the middle attack.
Threat Of Technology Abuse Some examples of threat of technology abuse are abuse of
information leak, issues of social engineering, malicious code,
abuse of authorization, brute force, business process failure,
denial of service, unsolicited emails, targeted attacks, hoax,
fraud and identity theft, unauthorized data breaches, misuse of
audit tools, manipulation of the information, and manipulation
of hardware and software.
Organization Threat The organization threat include the shortage of IT skills
Legal Threats Some examples of legal threats are violation of regulation,
failure to meet contractual requirements, abuse of personal data,
and judiciary orders.
Table 2: Threats and Risk of the ENISA Organization
(Source: Hashem et al., 2015, pp-112)
Threat of Technology Abuse is the most critical threat when the implication of the big
data analysis for the development of the effective control strategies (Kim, Trimi & Chung,
2014). The threat of technology abuse are abuse of information leak, issues of social engineering,
malicious code, abuse of authorization, brute force, business process failure, denial of service,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9RISK ANALYSIS AND SECURITY
unsolicited emails, targeted attacks, hoax, fraud and identity theft, unauthorized data breaches,
misuse of audit tools, manipulation of the information, and manipulation of hardware and
software. The Threat of Technology Abuse is considered as the most critical threat because the
development of the operations had caused the major issue in integration of the operations. The
technology abuse is done for intentionally harming the organization and causing the issues in
integration of the operations (Chen & Zhang, 2014). The information leak would form the major
issue as the sensitive and confidential information stored in the database would be misused for
personal use.
3. Key Threat Agents and their Impact Reduction Options
The threat of technology abuse are abuse of information leak, issues of social
engineering, malicious code, abuse of authorization, brute force, business process failure, denial
of service, unsolicited emails, targeted attacks, hoax, fraud and identity theft, unauthorized data
breaches, misuse of audit tools, manipulation of the information, and manipulation of hardware
and software. The key threat agents for the ENISA are Technology, Human Errors, Designing
Errors, and Personal gain (Lu et al., 2014). These agents would involve the deployment of the
issues and hindrances in the development of the operations. The involvement of the effective
methods of threat detection and analysis would tend to form the extortion of the processes and
development of hindrances in the organization.
Technology: The technology is the most primary factor that had formed the issues in
development of the effective operations and it would form the improvement issues for the
development of the systematic operational development (Thuraisingham, 2015). The
technological deployment would serve the automatic processing of issues regarding the
unsolicited emails, targeted attacks, hoax, fraud and identity theft, unauthorized data breaches,
misuse of audit tools, manipulation of the information, and manipulation of hardware and
software. The Threat of Technology Abuse is considered as the most critical threat because the
development of the operations had caused the major issue in integration of the operations. The
technology abuse is done for intentionally harming the organization and causing the issues in
integration of the operations (Chen & Zhang, 2014). The information leak would form the major
issue as the sensitive and confidential information stored in the database would be misused for
personal use.
3. Key Threat Agents and their Impact Reduction Options
The threat of technology abuse are abuse of information leak, issues of social
engineering, malicious code, abuse of authorization, brute force, business process failure, denial
of service, unsolicited emails, targeted attacks, hoax, fraud and identity theft, unauthorized data
breaches, misuse of audit tools, manipulation of the information, and manipulation of hardware
and software. The key threat agents for the ENISA are Technology, Human Errors, Designing
Errors, and Personal gain (Lu et al., 2014). These agents would involve the deployment of the
issues and hindrances in the development of the operations. The involvement of the effective
methods of threat detection and analysis would tend to form the extortion of the processes and
development of hindrances in the organization.
Technology: The technology is the most primary factor that had formed the issues in
development of the effective operations and it would form the improvement issues for the
development of the systematic operational development (Thuraisingham, 2015). The
technological deployment would serve the automatic processing of issues regarding the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10RISK ANALYSIS AND SECURITY
operations. The implication of the technological issues would comprise of forming the influential
development of the affective flow of operations. The technological hindrances are the major
factor for deployment of the simple and achievable operation development. Examples- leaks of
data via web application, loss of device (storage), loss of sensitive information, loss of cloud
information, penetration testing damage, and inadequate design and planning threat.
Human Errors: The human design errors are a major factor that forms the hindrances in
the development of the big data analytics for organizational development. The influence of the
system integrated operations would tend to implement the evaluation of the human actions and
functions (Erl, Khattak & Buhler, 2016). However, the errors made by the human are cohesive
for forming the issues in the development of the functions. The human made errors are
responsible for the deployment of the improved functions. Examples- change of data by mistake,
information interception, replay of messages, session hijacking or man in the middle attack,
unauthorized data breaches, manipulation of the information, and manipulation of hardware and
software.
Designing Errors: The designing errors are implied due to lack of the systematic and
influential operation in the organization. The designing errors would form the implication of the
operational processing (Kshetri, 2014). The designing errors are result of the implication of
incorrect development model. The designing errors are developed for critically evaluating the
effective and prone development of the operations. Example- business process failure,
inadequate design and planning threat, change of data by mistake, and unreliable source of
information
operations. The implication of the technological issues would comprise of forming the influential
development of the affective flow of operations. The technological hindrances are the major
factor for deployment of the simple and achievable operation development. Examples- leaks of
data via web application, loss of device (storage), loss of sensitive information, loss of cloud
information, penetration testing damage, and inadequate design and planning threat.
Human Errors: The human design errors are a major factor that forms the hindrances in
the development of the big data analytics for organizational development. The influence of the
system integrated operations would tend to implement the evaluation of the human actions and
functions (Erl, Khattak & Buhler, 2016). However, the errors made by the human are cohesive
for forming the issues in the development of the functions. The human made errors are
responsible for the deployment of the improved functions. Examples- change of data by mistake,
information interception, replay of messages, session hijacking or man in the middle attack,
unauthorized data breaches, manipulation of the information, and manipulation of hardware and
software.
Designing Errors: The designing errors are implied due to lack of the systematic and
influential operation in the organization. The designing errors would form the implication of the
operational processing (Kshetri, 2014). The designing errors are result of the implication of
incorrect development model. The designing errors are developed for critically evaluating the
effective and prone development of the operations. Example- business process failure,
inadequate design and planning threat, change of data by mistake, and unreliable source of
information
11RISK ANALYSIS AND SECURITY
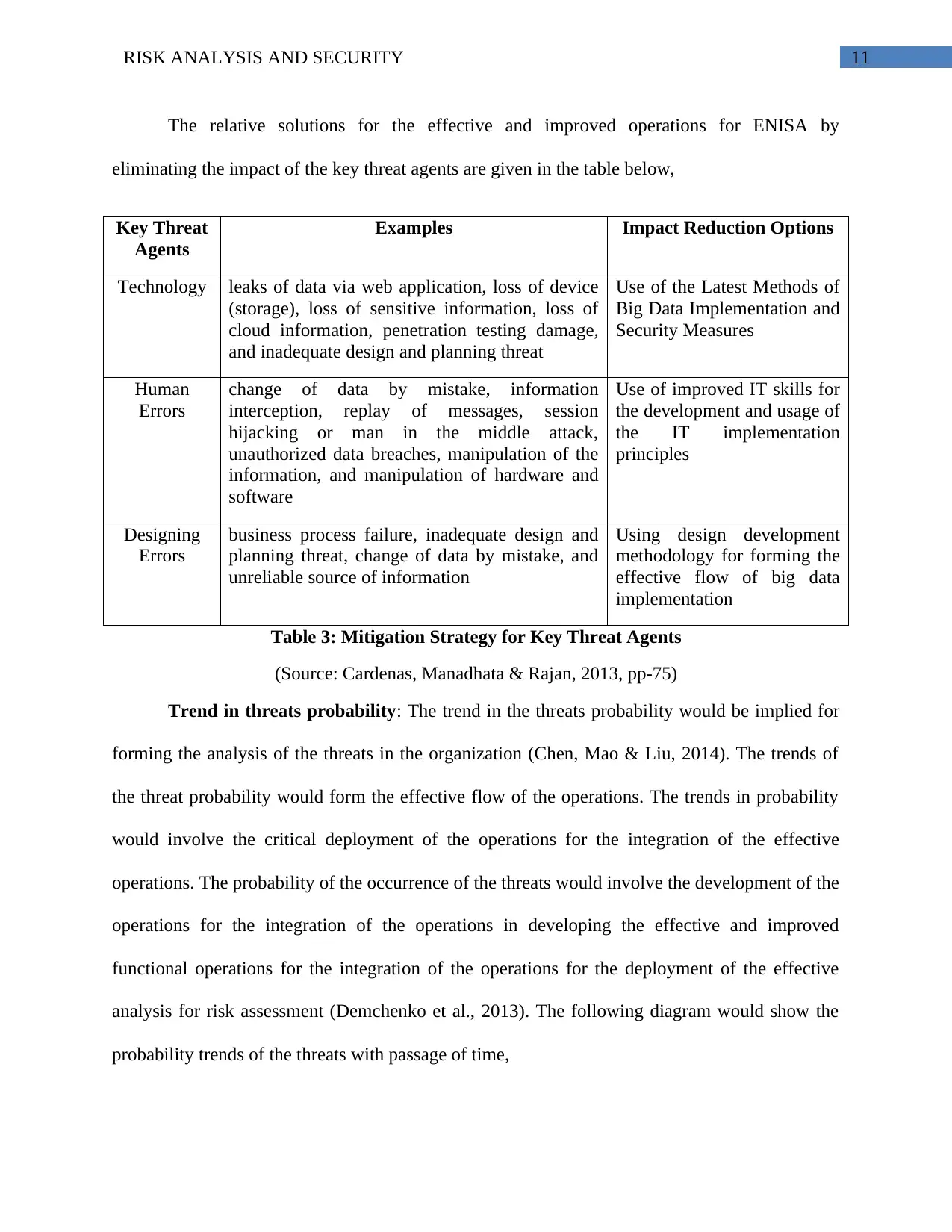
The relative solutions for the effective and improved operations for ENISA by
eliminating the impact of the key threat agents are given in the table below,
Key Threat
Agents
Examples Impact Reduction Options
Technology leaks of data via web application, loss of device
(storage), loss of sensitive information, loss of
cloud information, penetration testing damage,
and inadequate design and planning threat
Use of the Latest Methods of
Big Data Implementation and
Security Measures
Human
Errors
change of data by mistake, information
interception, replay of messages, session
hijacking or man in the middle attack,
unauthorized data breaches, manipulation of the
information, and manipulation of hardware and
software
Use of improved IT skills for
the development and usage of
the IT implementation
principles
Designing
Errors
business process failure, inadequate design and
planning threat, change of data by mistake, and
unreliable source of information
Using design development
methodology for forming the
effective flow of big data
implementation
Table 3: Mitigation Strategy for Key Threat Agents
(Source: Cardenas, Manadhata & Rajan, 2013, pp-75)
Trend in threats probability: The trend in the threats probability would be implied for
forming the analysis of the threats in the organization (Chen, Mao & Liu, 2014). The trends of
the threat probability would form the effective flow of the operations. The trends in probability
would involve the critical deployment of the operations for the integration of the effective
operations. The probability of the occurrence of the threats would involve the development of the
operations for the integration of the operations in developing the effective and improved
functional operations for the integration of the operations for the deployment of the effective
analysis for risk assessment (Demchenko et al., 2013). The following diagram would show the
probability trends of the threats with passage of time,
The relative solutions for the effective and improved operations for ENISA by
eliminating the impact of the key threat agents are given in the table below,
Key Threat
Agents
Examples Impact Reduction Options
Technology leaks of data via web application, loss of device
(storage), loss of sensitive information, loss of
cloud information, penetration testing damage,
and inadequate design and planning threat
Use of the Latest Methods of
Big Data Implementation and
Security Measures
Human
Errors
change of data by mistake, information
interception, replay of messages, session
hijacking or man in the middle attack,
unauthorized data breaches, manipulation of the
information, and manipulation of hardware and
software
Use of improved IT skills for
the development and usage of
the IT implementation
principles
Designing
Errors
business process failure, inadequate design and
planning threat, change of data by mistake, and
unreliable source of information
Using design development
methodology for forming the
effective flow of big data
implementation
Table 3: Mitigation Strategy for Key Threat Agents
(Source: Cardenas, Manadhata & Rajan, 2013, pp-75)
Trend in threats probability: The trend in the threats probability would be implied for
forming the analysis of the threats in the organization (Chen, Mao & Liu, 2014). The trends of
the threat probability would form the effective flow of the operations. The trends in probability
would involve the critical deployment of the operations for the integration of the effective
operations. The probability of the occurrence of the threats would involve the development of the
operations for the integration of the operations in developing the effective and improved
functional operations for the integration of the operations for the deployment of the effective
analysis for risk assessment (Demchenko et al., 2013). The following diagram would show the
probability trends of the threats with passage of time,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





