Risk Assessment and Analysis Report: VIC Government Information System
VerifiedAdded on 2020/02/24
|13
|3696
|32
Report
AI Summary
This report presents a risk assessment and analysis for the information system of the VIC Government. It begins with an introduction to the topic and an overview of the project's objectives. The report then illustrates the security risks and threats, using a diagram created in Microsoft Visio to represent various risk factors, categorizing them as accidental, deliberate, internal, and external. The analysis includes a detailed explanation of the diagram's components and a classification of risk exposure areas, such as high, medium, and low. A comparison and ranking of accidental and deliberate threats are provided, highlighting the most critical risks. The report identifies key security and risk management challenges faced by the VIC government. It also differentiates between risk and uncertainty and explores risk mitigation and management strategies. The conclusion summarizes the findings, and references are provided to support the analysis.

Running head: RISK ASSESSMENT AND ANALYSIS
Risk Assessment and Analysis
Name of the Student:
Student ID:
Name of the University:
Author’s note:
Risk Assessment and Analysis
Name of the Student:
Student ID:
Name of the University:
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1RISK ASSESSMENT AND ANALYSIS
Table of Contents
Introduction......................................................................................................................................2
1. Illustration of Security Risks and Threats in VIC Government..................................................2
2. Explanation of the Diagram and Categorization of Risk Factors................................................3
2.1 Description of the components of diagram............................................................................3
2.2 Classification of Risk Exposure Areas..................................................................................6
3. Comparison and Ranking of Accidental and Deliberate Threats................................................6
4. Security and Risk Management Challenges for VIC government...............................................7
5. Comparing Risk and Uncertainty................................................................................................8
6. Risk Mitigation and Management...............................................................................................8
Conclusion.......................................................................................................................................9
References......................................................................................................................................11
Table of Contents
Introduction......................................................................................................................................2
1. Illustration of Security Risks and Threats in VIC Government..................................................2
2. Explanation of the Diagram and Categorization of Risk Factors................................................3
2.1 Description of the components of diagram............................................................................3
2.2 Classification of Risk Exposure Areas..................................................................................6
3. Comparison and Ranking of Accidental and Deliberate Threats................................................6
4. Security and Risk Management Challenges for VIC government...............................................7
5. Comparing Risk and Uncertainty................................................................................................8
6. Risk Mitigation and Management...............................................................................................8
Conclusion.......................................................................................................................................9
References......................................................................................................................................11

2RISK ASSESSMENT AND ANALYSIS
Introduction
The case study of VIC Government had been selected for analysing the effective
development of the risk assessment report. The inclusion of the effective and smart development
methodology would be helpful for developing the operations of VIC government. According to
Steinberg (2016), the development of the operations would be helpful for integrating the
operations of the organization and it would be helpful for forming the integration of the smart
operations in the organization. The development of the systematic flow of operations would help
the organization for forming the accurate and systematic development of the operations.
The following assignment had been developed for integrating the risk assessment in the
operations of the information system development for VIC government. The report had
considered the evaluation issues and threats by implementation of the effective analysis method.
The evaluation of the security risks and threats in the VIC government had considered the
development of a diagram using Microsoft Visio and it had pointed out the various threats and
risks of implementing information system in the organization.
1. Illustration of Security Risks and Threats in VIC Government
The risk analysis for the development of the information system in VIC government had
been employed for forming the accurate and smart tools for analyzing the development of the
information system of VIC government. The diagram had been constructed in the Microsoft
Visio and it represents the components of the risk and threats acting on the information system
that is being implemented in the VIC government. The following diagram has been constructed
for representing the various threats and risk factors,
Introduction
The case study of VIC Government had been selected for analysing the effective
development of the risk assessment report. The inclusion of the effective and smart development
methodology would be helpful for developing the operations of VIC government. According to
Steinberg (2016), the development of the operations would be helpful for integrating the
operations of the organization and it would be helpful for forming the integration of the smart
operations in the organization. The development of the systematic flow of operations would help
the organization for forming the accurate and systematic development of the operations.
The following assignment had been developed for integrating the risk assessment in the
operations of the information system development for VIC government. The report had
considered the evaluation issues and threats by implementation of the effective analysis method.
The evaluation of the security risks and threats in the VIC government had considered the
development of a diagram using Microsoft Visio and it had pointed out the various threats and
risks of implementing information system in the organization.
1. Illustration of Security Risks and Threats in VIC Government
The risk analysis for the development of the information system in VIC government had
been employed for forming the accurate and smart tools for analyzing the development of the
information system of VIC government. The diagram had been constructed in the Microsoft
Visio and it represents the components of the risk and threats acting on the information system
that is being implemented in the VIC government. The following diagram has been constructed
for representing the various threats and risk factors,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
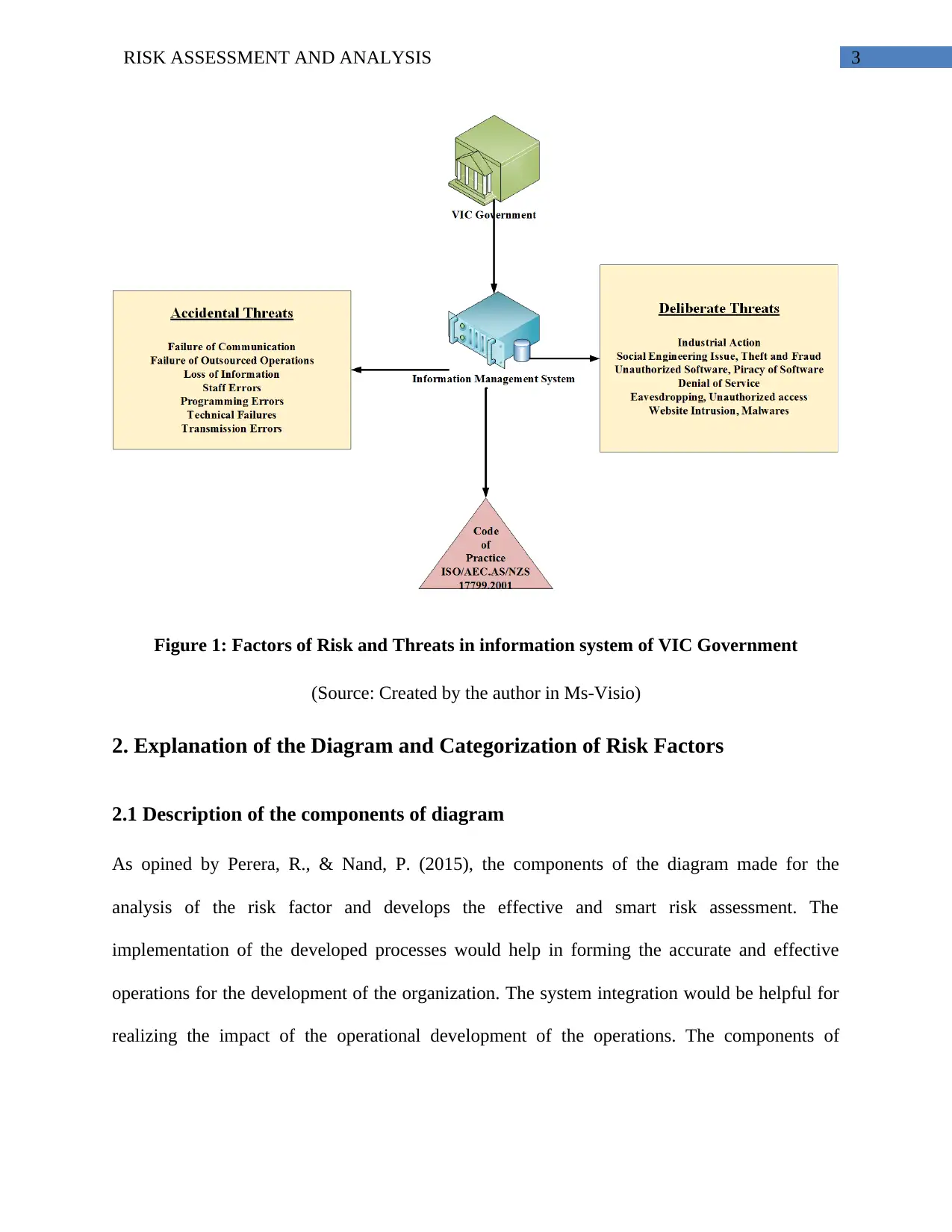
3RISK ASSESSMENT AND ANALYSIS
Figure 1: Factors of Risk and Threats in information system of VIC Government
(Source: Created by the author in Ms-Visio)
2. Explanation of the Diagram and Categorization of Risk Factors
2.1 Description of the components of diagram
As opined by Perera, R., & Nand, P. (2015), the components of the diagram made for the
analysis of the risk factor and develops the effective and smart risk assessment. The
implementation of the developed processes would help in forming the accurate and effective
operations for the development of the organization. The system integration would be helpful for
realizing the impact of the operational development of the operations. The components of
Figure 1: Factors of Risk and Threats in information system of VIC Government
(Source: Created by the author in Ms-Visio)
2. Explanation of the Diagram and Categorization of Risk Factors
2.1 Description of the components of diagram
As opined by Perera, R., & Nand, P. (2015), the components of the diagram made for the
analysis of the risk factor and develops the effective and smart risk assessment. The
implementation of the developed processes would help in forming the accurate and effective
operations for the development of the organization. The system integration would be helpful for
realizing the impact of the operational development of the operations. The components of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4RISK ASSESSMENT AND ANALYSIS
diagram are VIC Government, Information Management System, Codes of Practices, Risk and
Threats, Accidental and Deliberate Threats, and External and Internal Threats.
Component Description
VIC Government According to Von Solms and Van Niekerk (2013), the information of the
customers and the members of VIC government are the primary component
of the risk assessment for the information system implementation. The
implementation of the information system would be helpful for forming the
eventful development of the operations and carrying out the activities of the
smart system implementation. The storage of the data and information would
comprise of developing the effective and smart processing of the
information.
Information
Management
System
The information management system would be helpful for forming the
improved facilities of the operation. The implementation of the operations
would comprise of forming the VIC system implementation. According to
Bommer, Crowley and Pinho (2015), the development of the storage and
system database would be possible due to the implementation of the effective
and smart processing of the information system. The implementation had
been largely implied for developing the effective processing of the
information at VIC government. The management of the information would
form the effective deployment of the faster and improved services in the
operations.
Codes of
Practices
ISO/IEC.AC/AZS 17799:2001 is the ACS code of ethic developed for
implementing the effective and smart processing of the operations in the VIC
government organization. The codes of practices would be implied for
forming the effective and improved processes of the organization. The
development of the code of practices would be implied for keeping the
concerns of the operations intact for the implementation of the operations.
The code of practices would be implied by Australian Computer Society.
Risk and Threats Alcorn, Good and Pain (2013) have defined risk as the primary factor that
can cause the development of the effective and implied operations
unsuccessful. The risk consists of some hindrances that would form the
impact on the operations and it would result in forming the issues of the
operation. The risks of VIC information system implementation are staff
errors, denial of service, industrial action, transmission errors, programming
errors, theft and fraud, technical failures, eavesdropping, social engineering
issue, and malwares.
Bommer, Crowley and Pinho (2015) have defined threat as the factors of
unsure that can affect the development of the information system
development. The implication of the effective and employed development of
the operations would form the integration of the functions. The development
diagram are VIC Government, Information Management System, Codes of Practices, Risk and
Threats, Accidental and Deliberate Threats, and External and Internal Threats.
Component Description
VIC Government According to Von Solms and Van Niekerk (2013), the information of the
customers and the members of VIC government are the primary component
of the risk assessment for the information system implementation. The
implementation of the information system would be helpful for forming the
eventful development of the operations and carrying out the activities of the
smart system implementation. The storage of the data and information would
comprise of developing the effective and smart processing of the
information.
Information
Management
System
The information management system would be helpful for forming the
improved facilities of the operation. The implementation of the operations
would comprise of forming the VIC system implementation. According to
Bommer, Crowley and Pinho (2015), the development of the storage and
system database would be possible due to the implementation of the effective
and smart processing of the information system. The implementation had
been largely implied for developing the effective processing of the
information at VIC government. The management of the information would
form the effective deployment of the faster and improved services in the
operations.
Codes of
Practices
ISO/IEC.AC/AZS 17799:2001 is the ACS code of ethic developed for
implementing the effective and smart processing of the operations in the VIC
government organization. The codes of practices would be implied for
forming the effective and improved processes of the organization. The
development of the code of practices would be implied for keeping the
concerns of the operations intact for the implementation of the operations.
The code of practices would be implied by Australian Computer Society.
Risk and Threats Alcorn, Good and Pain (2013) have defined risk as the primary factor that
can cause the development of the effective and implied operations
unsuccessful. The risk consists of some hindrances that would form the
impact on the operations and it would result in forming the issues of the
operation. The risks of VIC information system implementation are staff
errors, denial of service, industrial action, transmission errors, programming
errors, theft and fraud, technical failures, eavesdropping, social engineering
issue, and malwares.
Bommer, Crowley and Pinho (2015) have defined threat as the factors of
unsure that can affect the development of the information system
development. The implication of the effective and employed development of
the operations would form the integration of the functions. The development
5RISK ASSESSMENT AND ANALYSIS
of the operations would not be ensured for forming the estimated outcome
from the operations due to threats. The factors of threats in the information
system implementation are unauthorized software, website intrusion,
unauthorized access, piracy of software, loss of information, and failure of
communication.
Accidental and
Deliberate
Threats
Von Solms and Van Niekerk (2013) have defined the accidental threats as
the sudden issues of the operations of the organization. The accidental threat
would not be intended for occurrence and hence it would not be of much
critical impact on the operations of the system. Proper planning would be
implied for forming the safety of operations with the organization for
implementing the information system. The accidental threats are technical
failures, transmission errors, programming errors, loss of information, failure
of outsourced operations, failure of communication, and staff errors.
On the contrary, Perera and Nand (2015) have developed the analysis of the
deliberate threat to be the most crucial in impacting the operations of the
organization. The deliberate threats are implied for harming the operations of
the organization purposely. It is the most critical hindrance and have highest
priority of harming the operations of the organization. The deliberate threats
are eavesdropping, industrial action, denial of service, website intrusion,
piracy of software, theft and fraud, unauthorized access, malwares,
unauthorized software, and social engineering issue.
External and
Internal Threats
Man et al. (2014) have stated that the external threats are a result of outside
interference on the information system and its operations. The external
threats are classified for forming the major issues in the development of the
operations as they cause critical hindrance and have highest priority of
harming the operations of the organization. The external threats for VIC
information system implementation are technical failures, eavesdropping,
programming errors, unauthorized access, denial of service, transmission
errors, malwares, and website intrusion.
As opined by Lam (2014), the internal threats are some inbuilt issues and
problems that the development of the information system faces due to the
interior faults and errors. The internal errors consist of some sudden issues of
the operations of the organization. The internal threats for VIC information
system implementation are unauthorized software, piracy of software,
industrial action, failure of communication, loss of information, failure of
outsourced operations, social engineering issue, and staff errors.
Table 1: Explanation of the Diagram developed for Risk Analysis
of the operations would not be ensured for forming the estimated outcome
from the operations due to threats. The factors of threats in the information
system implementation are unauthorized software, website intrusion,
unauthorized access, piracy of software, loss of information, and failure of
communication.
Accidental and
Deliberate
Threats
Von Solms and Van Niekerk (2013) have defined the accidental threats as
the sudden issues of the operations of the organization. The accidental threat
would not be intended for occurrence and hence it would not be of much
critical impact on the operations of the system. Proper planning would be
implied for forming the safety of operations with the organization for
implementing the information system. The accidental threats are technical
failures, transmission errors, programming errors, loss of information, failure
of outsourced operations, failure of communication, and staff errors.
On the contrary, Perera and Nand (2015) have developed the analysis of the
deliberate threat to be the most crucial in impacting the operations of the
organization. The deliberate threats are implied for harming the operations of
the organization purposely. It is the most critical hindrance and have highest
priority of harming the operations of the organization. The deliberate threats
are eavesdropping, industrial action, denial of service, website intrusion,
piracy of software, theft and fraud, unauthorized access, malwares,
unauthorized software, and social engineering issue.
External and
Internal Threats
Man et al. (2014) have stated that the external threats are a result of outside
interference on the information system and its operations. The external
threats are classified for forming the major issues in the development of the
operations as they cause critical hindrance and have highest priority of
harming the operations of the organization. The external threats for VIC
information system implementation are technical failures, eavesdropping,
programming errors, unauthorized access, denial of service, transmission
errors, malwares, and website intrusion.
As opined by Lam (2014), the internal threats are some inbuilt issues and
problems that the development of the information system faces due to the
interior faults and errors. The internal errors consist of some sudden issues of
the operations of the organization. The internal threats for VIC information
system implementation are unauthorized software, piracy of software,
industrial action, failure of communication, loss of information, failure of
outsourced operations, social engineering issue, and staff errors.
Table 1: Explanation of the Diagram developed for Risk Analysis
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6RISK ASSESSMENT AND ANALYSIS
2.2 Classification of Risk Exposure Areas
Man et al. (2014) has classified risk in terms of the risk exposure areas and they are
namely high, medium, medium-low, and low risk exposure areas. The explanation and example
of the risk exposure areas are given in the table below,
Risk Exposure Areas Description Examples
High Risk Exposure Areas Have high capacity of impact
on the operations of the
project and it would form the
major and critical impact on
the information system of VIC
government
a) Intrusion
b) Phishing
c) Malware
d) Data theft
Medium Risk Exposure Areas Have medium capacity of
impact on the operations of
the project and it would form
the moderate impact on the
information system of VIC
government
a) Issues of design
b) Data misinterpretation
c) Software issues
Medium Low Risk Exposure
Areas
Have Low capacity of impact
on the operations of the
project and it would form the
minor impact on the
information system of VIC
government
a) Wrong data entry
b) Data incompatibility
c) Integration issue
Low Risk Exposure Areas Have least capacity of impact
on the operations of the
project and it would form no
impact on the information
system of VIC government
a) Social engineering
issues
b) Errors generated by the
users
Table 2: Explanation of the Risk Exposure Areas
3. Comparison and Ranking of Accidental and Deliberate Threats
Rank Description Examples Justification of
ranking
1st Perera and Nand (2015) have Eavesdropping, industrial It is the most critical
2.2 Classification of Risk Exposure Areas
Man et al. (2014) has classified risk in terms of the risk exposure areas and they are
namely high, medium, medium-low, and low risk exposure areas. The explanation and example
of the risk exposure areas are given in the table below,
Risk Exposure Areas Description Examples
High Risk Exposure Areas Have high capacity of impact
on the operations of the
project and it would form the
major and critical impact on
the information system of VIC
government
a) Intrusion
b) Phishing
c) Malware
d) Data theft
Medium Risk Exposure Areas Have medium capacity of
impact on the operations of
the project and it would form
the moderate impact on the
information system of VIC
government
a) Issues of design
b) Data misinterpretation
c) Software issues
Medium Low Risk Exposure
Areas
Have Low capacity of impact
on the operations of the
project and it would form the
minor impact on the
information system of VIC
government
a) Wrong data entry
b) Data incompatibility
c) Integration issue
Low Risk Exposure Areas Have least capacity of impact
on the operations of the
project and it would form no
impact on the information
system of VIC government
a) Social engineering
issues
b) Errors generated by the
users
Table 2: Explanation of the Risk Exposure Areas
3. Comparison and Ranking of Accidental and Deliberate Threats
Rank Description Examples Justification of
ranking
1st Perera and Nand (2015) have Eavesdropping, industrial It is the most critical
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7RISK ASSESSMENT AND ANALYSIS
developed the analysis of the
deliberate threat to be the most
crucial in impacting the
operations of the organization.
The deliberate threats are
implied for harming the
operations of the organization
purposely.
action, denial of service,
website intrusion, piracy of
software, theft and fraud,
unauthorized access,
malwares, unauthorized
software, and social
engineering issue
hindrance and has
highest priority of
harming the operations
of the organization.
Hence it has been
ranked first.
2nd Von Solms and Van Niekerk
(2013) have defined the
accidental threats as the sudden
issues of the operations of the
organization. The accidental
threat would not be intended
for occurrence and hence it
would not be of much critical
impact on the operations of the
system.
Technical failures,
transmission errors,
programming errors, loss of
information, failure of
outsourced operations,
failure of communication,
and staff errors.
Proper planning would
be implied for forming
the safety of operations
with the organization for
implementing the
information system.
Hence it has been
ranked second.
Table 3: Comparison of Accidental and Deliberate Threats for VIC government
4. Security and Risk Management Challenges for VIC government
The VIC information system implementation had been implied for forming the effective
development of the operations of the organization. However the organization had to face some
issues of security challenges and operational challenges that has been explained below,
Security Challenges: The security challenges are implied for harming the operations of
the organization purposely (Rasmussen, 2013). The security challenges are the most crucial in
impacting the operations of the organization and it results in forming major hindrance in the
operations of the organization. The security challenges include eavesdropping, industrial action,
denial of service, website intrusion, piracy of software, theft and fraud, unauthorized access,
malwares, unauthorized software, and social engineering issue.
developed the analysis of the
deliberate threat to be the most
crucial in impacting the
operations of the organization.
The deliberate threats are
implied for harming the
operations of the organization
purposely.
action, denial of service,
website intrusion, piracy of
software, theft and fraud,
unauthorized access,
malwares, unauthorized
software, and social
engineering issue
hindrance and has
highest priority of
harming the operations
of the organization.
Hence it has been
ranked first.
2nd Von Solms and Van Niekerk
(2013) have defined the
accidental threats as the sudden
issues of the operations of the
organization. The accidental
threat would not be intended
for occurrence and hence it
would not be of much critical
impact on the operations of the
system.
Technical failures,
transmission errors,
programming errors, loss of
information, failure of
outsourced operations,
failure of communication,
and staff errors.
Proper planning would
be implied for forming
the safety of operations
with the organization for
implementing the
information system.
Hence it has been
ranked second.
Table 3: Comparison of Accidental and Deliberate Threats for VIC government
4. Security and Risk Management Challenges for VIC government
The VIC information system implementation had been implied for forming the effective
development of the operations of the organization. However the organization had to face some
issues of security challenges and operational challenges that has been explained below,
Security Challenges: The security challenges are implied for harming the operations of
the organization purposely (Rasmussen, 2013). The security challenges are the most crucial in
impacting the operations of the organization and it results in forming major hindrance in the
operations of the organization. The security challenges include eavesdropping, industrial action,
denial of service, website intrusion, piracy of software, theft and fraud, unauthorized access,
malwares, unauthorized software, and social engineering issue.

8RISK ASSESSMENT AND ANALYSIS
Operational Challenges: The operational challenges are the sudden issues of the
operations of the organization (Healey, 2016). The operational challenges would not be intended
for occurrence and hence it would not be of much critical impact on the operations of the system.
The operational challenges include technical failures, transmission errors, programming errors,
loss of information, failure of outsourced operations, failure of communication, and staff errors.
5. Comparing Risk and Uncertainty
Silbey (2013) considers risk as the primary factor that can cause the development of the
effective and implied operations unsuccessful. The risk consists of some hindrances that would
form the impact on the operations and it would result in forming the issues of the operation. The
risks of VIC information system implementation are staff errors, denial of service, industrial
action, transmission errors, programming errors, theft and fraud, technical failures,
eavesdropping, social engineering issue, and malwares.
Covello et al. (2013) considers uncertainty as the factors of doubt that can affect the
development of the information system development. The implication of the effective and
employed development of the operations would form the integration of the functions. The
development of the operations would not be ensured for forming the estimated outcome from the
operations due to uncertainties. The factors of uncertainties in the information system
implementation are unauthorized software, website intrusion, unauthorized access, piracy of
software, loss of information, and failure of communication.
6. Risk Mitigation and Management
The risk consists of some hindrances that would form the impact on the operations and it would
result in forming the issues of the operation of VIC information system implementation. Hence it
Operational Challenges: The operational challenges are the sudden issues of the
operations of the organization (Healey, 2016). The operational challenges would not be intended
for occurrence and hence it would not be of much critical impact on the operations of the system.
The operational challenges include technical failures, transmission errors, programming errors,
loss of information, failure of outsourced operations, failure of communication, and staff errors.
5. Comparing Risk and Uncertainty
Silbey (2013) considers risk as the primary factor that can cause the development of the
effective and implied operations unsuccessful. The risk consists of some hindrances that would
form the impact on the operations and it would result in forming the issues of the operation. The
risks of VIC information system implementation are staff errors, denial of service, industrial
action, transmission errors, programming errors, theft and fraud, technical failures,
eavesdropping, social engineering issue, and malwares.
Covello et al. (2013) considers uncertainty as the factors of doubt that can affect the
development of the information system development. The implication of the effective and
employed development of the operations would form the integration of the functions. The
development of the operations would not be ensured for forming the estimated outcome from the
operations due to uncertainties. The factors of uncertainties in the information system
implementation are unauthorized software, website intrusion, unauthorized access, piracy of
software, loss of information, and failure of communication.
6. Risk Mitigation and Management
The risk consists of some hindrances that would form the impact on the operations and it would
result in forming the issues of the operation of VIC information system implementation. Hence it
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9RISK ASSESSMENT AND ANALYSIS
is crucial for developing a risk mitigation and management plan for forming the effective
solution to the development of the operations in the organization. The risk mitigation and
management consists of four steps namely identification of the risk, analysis of the risk,
mitigation of the risk, and evaluation of the risk.
Step Description
Identification of the risk The identification of the risk factor is helpful
for identifying the factors of risk in the
operations. It is the first step in the
development of risk assessment and
management.
Analysis of the risk The analysis of the risk is formed for the
development of the risk mitigation and
management plan and it would prioritize them.
It is the second step in the development of risk
assessment and management.
Mitigation of the risk The mitigation of the risk forms an effective
risk mitigation strategy to be implemented for
the effective deployment of the risk mitigation
and management plan operations. It is the third
step in the development of risk assessment and
management.
Evaluation of the risk The evaluation of the risk forms the accurate
and improved processes for the operations of
risk mitigation and management plan. It is the
last step in the development of risk assessment
and management.
Table 4: Steps of Risk Mitigation and Management Plan
Conclusion
The report had been developed on two factors and they are risk assessment and case
study of implementing information system in VIC government. The case study of VIC
Government had been analysed for integrating the risk assessment in the operations of the
is crucial for developing a risk mitigation and management plan for forming the effective
solution to the development of the operations in the organization. The risk mitigation and
management consists of four steps namely identification of the risk, analysis of the risk,
mitigation of the risk, and evaluation of the risk.
Step Description
Identification of the risk The identification of the risk factor is helpful
for identifying the factors of risk in the
operations. It is the first step in the
development of risk assessment and
management.
Analysis of the risk The analysis of the risk is formed for the
development of the risk mitigation and
management plan and it would prioritize them.
It is the second step in the development of risk
assessment and management.
Mitigation of the risk The mitigation of the risk forms an effective
risk mitigation strategy to be implemented for
the effective deployment of the risk mitigation
and management plan operations. It is the third
step in the development of risk assessment and
management.
Evaluation of the risk The evaluation of the risk forms the accurate
and improved processes for the operations of
risk mitigation and management plan. It is the
last step in the development of risk assessment
and management.
Table 4: Steps of Risk Mitigation and Management Plan
Conclusion
The report had been developed on two factors and they are risk assessment and case
study of implementing information system in VIC government. The case study of VIC
Government had been analysed for integrating the risk assessment in the operations of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10RISK ASSESSMENT AND ANALYSIS
information system development. The evaluation of the security risks and threats in the VIC
government had pointed out the various threats and risks of implementing information system in
the organization. The components of diagram VIC Government, information management
system, codes of practices, risk and threats, accidental and deliberate threats, and external and
internal threats were evaluated for forming the analysis of the risk analysis process. The
classification of the risk in terms of the risk exposure areas and they are namely high, medium,
medium-low, and low risk exposure areas had helped in forming a deep analysis of the
comparison and ranking of accidental and deliberate threats. The VIC information system
implementation had to face some issues of security challenges and operational challenges that
had been explained in the report. The completion of the report had helped in forming the
inference that risk is the primary factor that can cause the development of the effective and
implied operations unsuccessful and uncertainty is the factors of doubt that can affect the
development of the information system development. The risk mitigation and management
consisted of four steps namely identification of the risk, analysis of the risk, mitigation of the
risk, and evaluation of the risk.
information system development. The evaluation of the security risks and threats in the VIC
government had pointed out the various threats and risks of implementing information system in
the organization. The components of diagram VIC Government, information management
system, codes of practices, risk and threats, accidental and deliberate threats, and external and
internal threats were evaluated for forming the analysis of the risk analysis process. The
classification of the risk in terms of the risk exposure areas and they are namely high, medium,
medium-low, and low risk exposure areas had helped in forming a deep analysis of the
comparison and ranking of accidental and deliberate threats. The VIC information system
implementation had to face some issues of security challenges and operational challenges that
had been explained in the report. The completion of the report had helped in forming the
inference that risk is the primary factor that can cause the development of the effective and
implied operations unsuccessful and uncertainty is the factors of doubt that can affect the
development of the information system development. The risk mitigation and management
consisted of four steps namely identification of the risk, analysis of the risk, mitigation of the
risk, and evaluation of the risk.

11RISK ASSESSMENT AND ANALYSIS
References
Alcorn, A.M., Good, J. and Pain, H., (2013, July). Deliberate system-side errors as a potential
pedagogic strategy for exploratory virtual learning environments. In International
Conference on Artificial Intelligence in Education (pp. 483-492). Springer Berlin
Heidelberg
Ali, E., Denis, A. F., Kujur, F. E., & Chaudhary, M. (2014). Risk Management Strategies for
Accidental Risk Occurrence on Construction Sites–A Case Study of Allahabad. Journal
of Academia and Industrial Research (JAIR),3(2), 89.
Bommer, J. J., Crowley, H., & Pinho, R. (2015). A risk-mitigation approach to the management
of induced seismicity. Journal of Seismology, 19(2), 623-646.
Covello, V. T., Lave, L. B., Moghissi, A. A., & Uppuluri, V. R. R. (Eds.). (2013). Uncertainty in
risk assessment, risk management, and decision making (Vol. 4). Springer Science &
Business Media.
Healey, A. N. (2016). The insider threat to nuclear safety and security. Security Journal, 29(1),
23-38.
Lam, J. (2014). Enterprise risk management: from incentives to controls. John Wiley & Sons.
Mans, R. S., van der Aalst, W. M., Vanwersch, R. J., & Moleman, A. J. (2013). Process mining
in healthcare: Data challenges when answering frequently posed questions. In Process
Support and Knowledge Representation in Health Care (pp. 140-153). Springer Berlin
Heidelberg.
References
Alcorn, A.M., Good, J. and Pain, H., (2013, July). Deliberate system-side errors as a potential
pedagogic strategy for exploratory virtual learning environments. In International
Conference on Artificial Intelligence in Education (pp. 483-492). Springer Berlin
Heidelberg
Ali, E., Denis, A. F., Kujur, F. E., & Chaudhary, M. (2014). Risk Management Strategies for
Accidental Risk Occurrence on Construction Sites–A Case Study of Allahabad. Journal
of Academia and Industrial Research (JAIR),3(2), 89.
Bommer, J. J., Crowley, H., & Pinho, R. (2015). A risk-mitigation approach to the management
of induced seismicity. Journal of Seismology, 19(2), 623-646.
Covello, V. T., Lave, L. B., Moghissi, A. A., & Uppuluri, V. R. R. (Eds.). (2013). Uncertainty in
risk assessment, risk management, and decision making (Vol. 4). Springer Science &
Business Media.
Healey, A. N. (2016). The insider threat to nuclear safety and security. Security Journal, 29(1),
23-38.
Lam, J. (2014). Enterprise risk management: from incentives to controls. John Wiley & Sons.
Mans, R. S., van der Aalst, W. M., Vanwersch, R. J., & Moleman, A. J. (2013). Process mining
in healthcare: Data challenges when answering frequently posed questions. In Process
Support and Knowledge Representation in Health Care (pp. 140-153). Springer Berlin
Heidelberg.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





