CMP73001: Cybersecurity Risk Assessment and Management Report for AML
VerifiedAdded on 2022/09/01
|18
|3040
|16
Report
AI Summary
This report presents a cybersecurity risk management plan for Advanced Medicos Limited (AML), a healthcare product company. It begins with an introduction to the company's needs, including the necessity for rapid recovery of key services and disaster preparedness. The report covers two main tasks: identifying and managing assets, including a weighted factor analysis and the benefits of information security governance, and vulnerability and risk management, which involves describing risk management phases in ISO 31000, identifying vulnerabilities and threats, developing a risk management strategy, and performing a risk assessment. The report also includes an enterprise information policy and a detailed risk management plan for a specific threat. The conclusion summarizes the key findings and recommendations for AML to enhance its cybersecurity posture.

Running head: RISK MANAGEMENT
RISK MANAGEMENT
Name of the Student
Name of the University
Author Note:
RISK MANAGEMENT
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1RISK MANAGEMENT
Table of Contents
Introduction..........................................................................................................................2
Task 1: Identify and Manage Asset.....................................................................................3
1.1Risk Assessment.............................................................................................................3
Weighted Factor Analysis................................................................................................4
1.2 Benefits of Information Security governance for AML................................................4
1.3 Enterprise Information Policy........................................................................................5
Task 2: Vulnerability management and Risk Management.................................................7
2.1 Describe risk management phases in ISO.....................................................................7
2.2 Identifying vulnerabilities and their threats.................................................................10
2.3 developing a risk management strategy.......................................................................11
2.4 Perform risk assessment..............................................................................................13
Conclusion.........................................................................................................................14
References..........................................................................................................................15
Table of Contents
Introduction..........................................................................................................................2
Task 1: Identify and Manage Asset.....................................................................................3
1.1Risk Assessment.............................................................................................................3
Weighted Factor Analysis................................................................................................4
1.2 Benefits of Information Security governance for AML................................................4
1.3 Enterprise Information Policy........................................................................................5
Task 2: Vulnerability management and Risk Management.................................................7
2.1 Describe risk management phases in ISO.....................................................................7
2.2 Identifying vulnerabilities and their threats.................................................................10
2.3 developing a risk management strategy.......................................................................11
2.4 Perform risk assessment..............................................................................................13
Conclusion.........................................................................................................................14
References..........................................................................................................................15

2RISK MANAGEMENT
Introduction
The following report is all about Advanced Medicos Limited (AML) which is known to
be a healthcare product selling company. The organization has appointed a cyber-consultant in
order to help the security management to address the contemporary and growing risks. All these
has come into picture from cyber threats which the organization is addressing (Radanliev et al.
2019). AML has provided a platform for most of the Australian customers to sell its products on
online platform. The main focus of this organization is to among the top five organization on
global platform. After the advice from chief information officer and information security officer,
they have protect in the key services (Tam and Jones 2018). The web portal of AML needs to be
recovered from major step in less than interval of 20 minutes while the other services may
resume to work. In case of any kind of disaster, the organization should have the ability to have
both web portal and payroll system. Both the things needs to be functional in less than interval of
two days.
In the coming pages of report, two task has been covered that is identification and
managing the asset, and vulnerability and risk management plan for the organization. The report
provides a risk management strategy and along with risk assessment.
Introduction
The following report is all about Advanced Medicos Limited (AML) which is known to
be a healthcare product selling company. The organization has appointed a cyber-consultant in
order to help the security management to address the contemporary and growing risks. All these
has come into picture from cyber threats which the organization is addressing (Radanliev et al.
2019). AML has provided a platform for most of the Australian customers to sell its products on
online platform. The main focus of this organization is to among the top five organization on
global platform. After the advice from chief information officer and information security officer,
they have protect in the key services (Tam and Jones 2018). The web portal of AML needs to be
recovered from major step in less than interval of 20 minutes while the other services may
resume to work. In case of any kind of disaster, the organization should have the ability to have
both web portal and payroll system. Both the things needs to be functional in less than interval of
two days.
In the coming pages of report, two task has been covered that is identification and
managing the asset, and vulnerability and risk management plan for the organization. The report
provides a risk management strategy and along with risk assessment.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3RISK MANAGEMENT
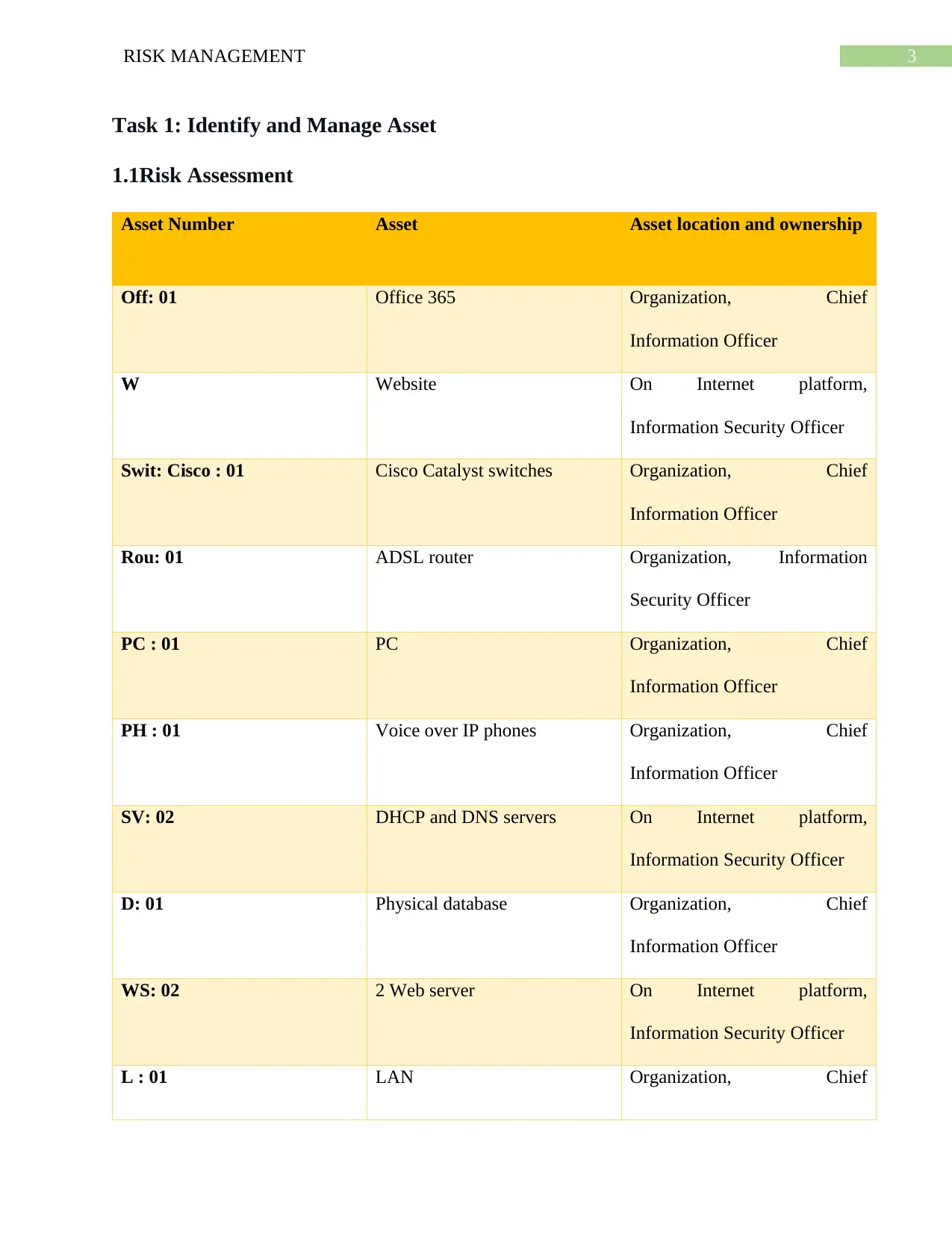
Task 1: Identify and Manage Asset
1.1Risk Assessment
Asset Number Asset Asset location and ownership
Off: 01 Office 365 Organization, Chief
Information Officer
W Website On Internet platform,
Information Security Officer
Swit: Cisco : 01 Cisco Catalyst switches Organization, Chief
Information Officer
Rou: 01 ADSL router Organization, Information
Security Officer
PC : 01 PC Organization, Chief
Information Officer
PH : 01 Voice over IP phones Organization, Chief
Information Officer
SV: 02 DHCP and DNS servers On Internet platform,
Information Security Officer
D: 01 Physical database Organization, Chief
Information Officer
WS: 02 2 Web server On Internet platform,
Information Security Officer
L : 01 LAN Organization, Chief
Task 1: Identify and Manage Asset
1.1Risk Assessment
Asset Number Asset Asset location and ownership
Off: 01 Office 365 Organization, Chief
Information Officer
W Website On Internet platform,
Information Security Officer
Swit: Cisco : 01 Cisco Catalyst switches Organization, Chief
Information Officer
Rou: 01 ADSL router Organization, Information
Security Officer
PC : 01 PC Organization, Chief
Information Officer
PH : 01 Voice over IP phones Organization, Chief
Information Officer
SV: 02 DHCP and DNS servers On Internet platform,
Information Security Officer
D: 01 Physical database Organization, Chief
Information Officer
WS: 02 2 Web server On Internet platform,
Information Security Officer
L : 01 LAN Organization, Chief
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4RISK MANAGEMENT
Information Officer
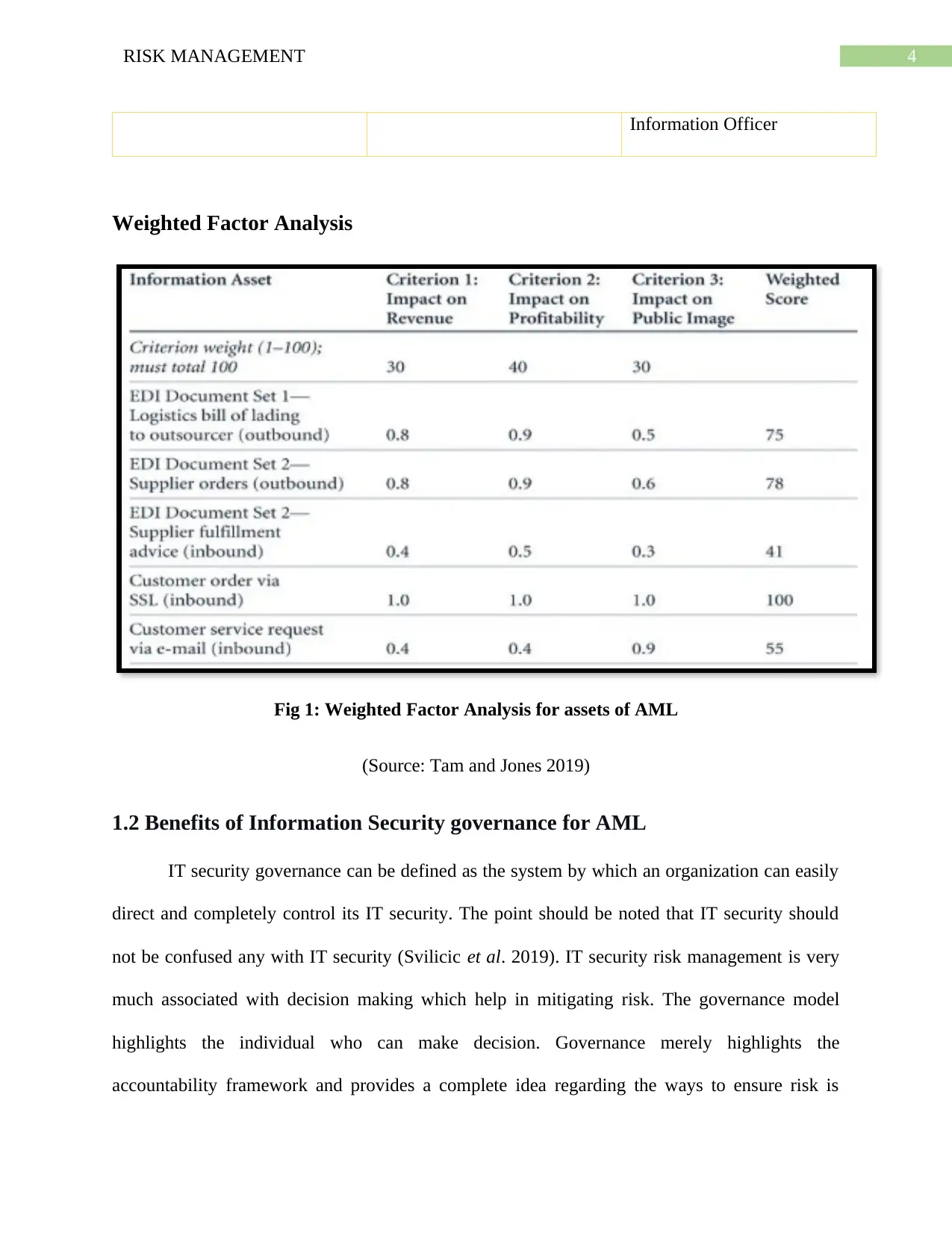
Weighted Factor Analysis
Fig 1: Weighted Factor Analysis for assets of AML
(Source: Tam and Jones 2019)
1.2 Benefits of Information Security governance for AML
IT security governance can be defined as the system by which an organization can easily
direct and completely control its IT security. The point should be noted that IT security should
not be confused any with IT security (Svilicic et al. 2019). IT security risk management is very
much associated with decision making which help in mitigating risk. The governance model
highlights the individual who can make decision. Governance merely highlights the
accountability framework and provides a complete idea regarding the ways to ensure risk is
Information Officer
Weighted Factor Analysis
Fig 1: Weighted Factor Analysis for assets of AML
(Source: Tam and Jones 2019)
1.2 Benefits of Information Security governance for AML
IT security governance can be defined as the system by which an organization can easily
direct and completely control its IT security. The point should be noted that IT security should
not be confused any with IT security (Svilicic et al. 2019). IT security risk management is very
much associated with decision making which help in mitigating risk. The governance model
highlights the individual who can make decision. Governance merely highlights the
accountability framework and provides a complete idea regarding the ways to ensure risk is

5RISK MANAGEMENT
mitigated (Nurse, Creese and De Roure 2017). On the contrary, the management of the
organization ensures that controls are implement to tackle the risks.
Managing AML from the view point of security professional require some classification
of asset along with its operational structure (Santini et al. 2019). The whole method of
identification is all about identification of that require system in order to assign different kind of
asset into group. All the group are completely devised considered the asset along with finding
the attributes. All the required rules are being applied for each kind of asset in order to keep a
track of each item (McNeil, Llansó and Pearson 2018). This merely being accountability of
structure so that management becomes very much visible for each item. It merely helps in easy
tracking of asset.
AML is able to apply this for complete classification of asset system for the provided
information. It mere allow different department in the organization to take into account all
valuable asset within these items (Jabbour and Poisson 2016). There are various kind of asset
which are completely related both to information security and information technology. The main
goal of information security professional is all about mitigating all the possible risk and possible
threats. AML needs to have seamless business operation along with safeguarding the valuable
asset of the organization (Kaffenberger and Kop 2019). There is a list of system which can help
the organization to easily monitor and manage various assets with AML.
1.3 Enterprise Information Policy
Security threats are changing at a rapid rate and compliance requirements for legal and
government bodies are becoming much more complex (Janiszewski, Felkner and Lewandowski
2019). Some of the essential characteristics of information security policy are
mitigated (Nurse, Creese and De Roure 2017). On the contrary, the management of the
organization ensures that controls are implement to tackle the risks.
Managing AML from the view point of security professional require some classification
of asset along with its operational structure (Santini et al. 2019). The whole method of
identification is all about identification of that require system in order to assign different kind of
asset into group. All the group are completely devised considered the asset along with finding
the attributes. All the required rules are being applied for each kind of asset in order to keep a
track of each item (McNeil, Llansó and Pearson 2018). This merely being accountability of
structure so that management becomes very much visible for each item. It merely helps in easy
tracking of asset.
AML is able to apply this for complete classification of asset system for the provided
information. It mere allow different department in the organization to take into account all
valuable asset within these items (Jabbour and Poisson 2016). There are various kind of asset
which are completely related both to information security and information technology. The main
goal of information security professional is all about mitigating all the possible risk and possible
threats. AML needs to have seamless business operation along with safeguarding the valuable
asset of the organization (Kaffenberger and Kop 2019). There is a list of system which can help
the organization to easily monitor and manage various assets with AML.
1.3 Enterprise Information Policy
Security threats are changing at a rapid rate and compliance requirements for legal and
government bodies are becoming much more complex (Janiszewski, Felkner and Lewandowski
2019). Some of the essential characteristics of information security policy are
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6RISK MANAGEMENT
Information security policy should be prepared from end to end.
The policy should come up with space for revision and any kind of update
This needs to have risk assement for the organization.
It should be completely practical and enforceable in nature.
The policy needs secure AML from all the possible sides that is it should cover software,
hardware, physical aspects, human resources and access control. AML will change over the
period of time and grow so it should have possible space for any kind of updates (Schear et al.
2016). Organization merely go for complete risk assessment in order to identify all the potential
hazards and risk. The point should be noted that it is very much easy to pick up information
security policy. AML needs to have these policies in order to enhance its overall security like
Human Resource Policy: The main notion of this policy is all about addressing all the
possible risk, fraud, theft and even misuse of facilities. The policy aims in creating a secure
environment (Tonn et al. 2019). Security responsibilities needs to be addressed at the very
recruitment stage which includes both job description and contract.
Access Control Policy: Complete access to information assets stand out to be privilege
for all the smart working employees and stakeholders (Hartmann and Driessen 2017). This stand
out to be important for carrying out all the day to day task. Proper access and authorization to
smart work information assets. The main target of this policy is all about defining complete
access control to information system and all the required the computer resources.
Physical Security Policy: The policy document focus on the point that all the information
processing facilities needs to be completely protected from any kind of modification of theft by
unauthorized user (Dippenaar. and Bezuidenhout 2019). All the control needs to be placed in
Information security policy should be prepared from end to end.
The policy should come up with space for revision and any kind of update
This needs to have risk assement for the organization.
It should be completely practical and enforceable in nature.
The policy needs secure AML from all the possible sides that is it should cover software,
hardware, physical aspects, human resources and access control. AML will change over the
period of time and grow so it should have possible space for any kind of updates (Schear et al.
2016). Organization merely go for complete risk assessment in order to identify all the potential
hazards and risk. The point should be noted that it is very much easy to pick up information
security policy. AML needs to have these policies in order to enhance its overall security like
Human Resource Policy: The main notion of this policy is all about addressing all the
possible risk, fraud, theft and even misuse of facilities. The policy aims in creating a secure
environment (Tonn et al. 2019). Security responsibilities needs to be addressed at the very
recruitment stage which includes both job description and contract.
Access Control Policy: Complete access to information assets stand out to be privilege
for all the smart working employees and stakeholders (Hartmann and Driessen 2017). This stand
out to be important for carrying out all the day to day task. Proper access and authorization to
smart work information assets. The main target of this policy is all about defining complete
access control to information system and all the required the computer resources.
Physical Security Policy: The policy document focus on the point that all the information
processing facilities needs to be completely protected from any kind of modification of theft by
unauthorized user (Dippenaar. and Bezuidenhout 2019). All the control needs to be placed in
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7RISK MANAGEMENT
order to reduce loss or any kind of damage. All the equipment’s need to be protected from any
kind of security threats and hazard on environment.
Acceptable Usage Policy: Access to all the information assets is completely grant by
employees and stakeholders (Green 2017). This stand out to be very much vital in managing
daily tasks. Complete use and protection of AML information assets stand out to be very much
important.
BYOD policy: The policy aims establish come rules and regulation for complete usage of
hand held devices and application in the domain of corporate environment (Susanto et al. 2019).
The mere focus of this policy is all about protection of corporate and integrity of information and
data.
Task 2: Vulnerability management and Risk Management
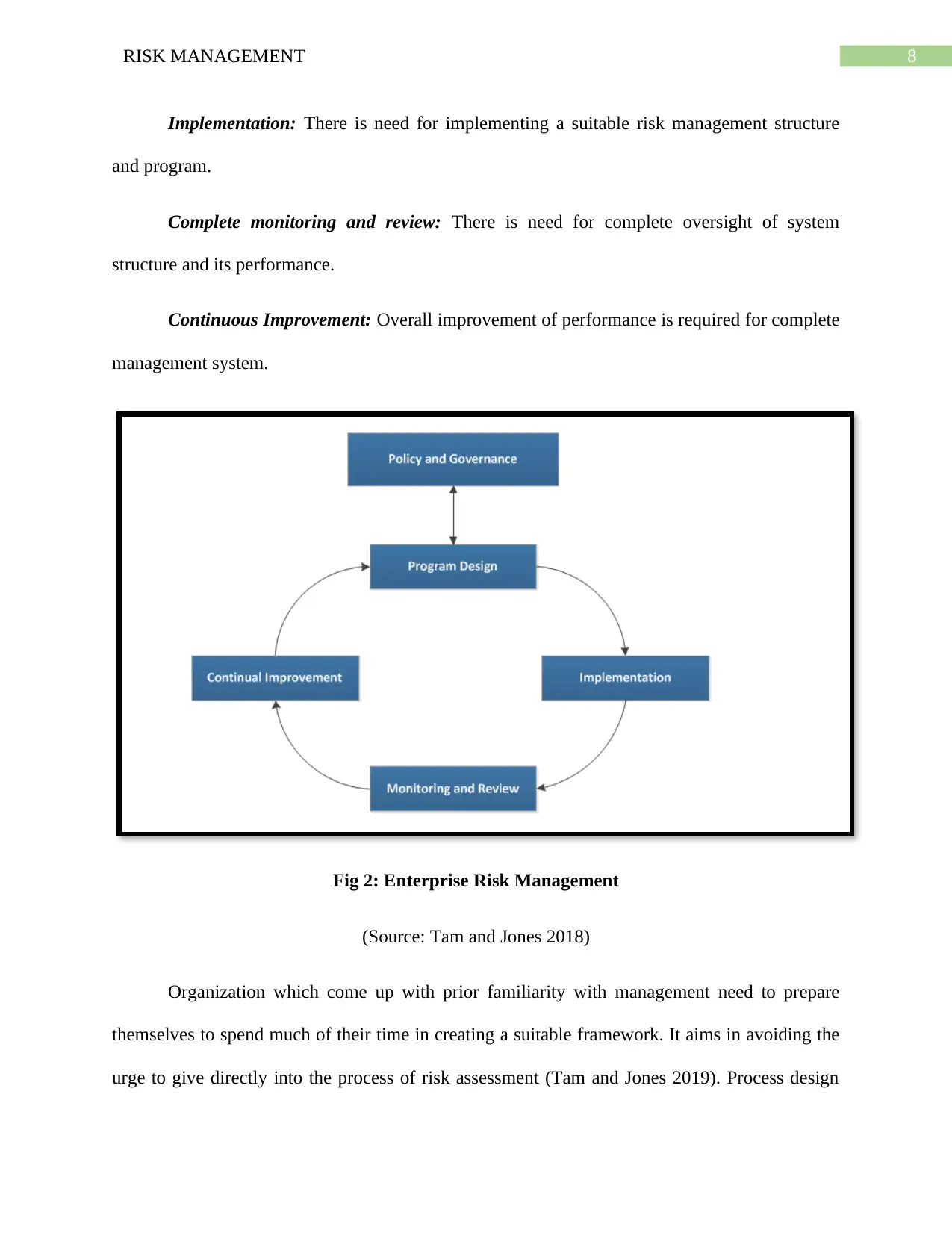
2.1 Describe risk management phases in ISO
ISO 31000 framework focus on series of steps, do, check, act and cycle that stand out to
be framework for different kind of design system. The given standard highlights to provide a
management system instead it assist the organization for complete risk management (Radanliev
et al. 2019). The statement encourages the organization to be completely flexible for
incorporation of some framework as per requirement. Some of the important elements of this
framework has been described below like
Policy and Governance: It provides the demonstration and mandates the overall
commitment of the organization.
Design of Program: It is all about design of framework in order to manage the risk on
daily basis.
order to reduce loss or any kind of damage. All the equipment’s need to be protected from any
kind of security threats and hazard on environment.
Acceptable Usage Policy: Access to all the information assets is completely grant by
employees and stakeholders (Green 2017). This stand out to be very much vital in managing
daily tasks. Complete use and protection of AML information assets stand out to be very much
important.
BYOD policy: The policy aims establish come rules and regulation for complete usage of
hand held devices and application in the domain of corporate environment (Susanto et al. 2019).
The mere focus of this policy is all about protection of corporate and integrity of information and
data.
Task 2: Vulnerability management and Risk Management
2.1 Describe risk management phases in ISO
ISO 31000 framework focus on series of steps, do, check, act and cycle that stand out to
be framework for different kind of design system. The given standard highlights to provide a
management system instead it assist the organization for complete risk management (Radanliev
et al. 2019). The statement encourages the organization to be completely flexible for
incorporation of some framework as per requirement. Some of the important elements of this
framework has been described below like
Policy and Governance: It provides the demonstration and mandates the overall
commitment of the organization.
Design of Program: It is all about design of framework in order to manage the risk on
daily basis.
8RISK MANAGEMENT
Implementation: There is need for implementing a suitable risk management structure
and program.
Complete monitoring and review: There is need for complete oversight of system
structure and its performance.
Continuous Improvement: Overall improvement of performance is required for complete
management system.
Fig 2: Enterprise Risk Management
(Source: Tam and Jones 2018)
Organization which come up with prior familiarity with management need to prepare
themselves to spend much of their time in creating a suitable framework. It aims in avoiding the
urge to give directly into the process of risk assessment (Tam and Jones 2019). Process design
Implementation: There is need for implementing a suitable risk management structure
and program.
Complete monitoring and review: There is need for complete oversight of system
structure and its performance.
Continuous Improvement: Overall improvement of performance is required for complete
management system.
Fig 2: Enterprise Risk Management
(Source: Tam and Jones 2018)
Organization which come up with prior familiarity with management need to prepare
themselves to spend much of their time in creating a suitable framework. It aims in avoiding the
urge to give directly into the process of risk assessment (Tam and Jones 2019). Process design
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9RISK MANAGEMENT
stand out to be important step as this the framework which provides complete stability and
continuity in order to assist the framework.
stand out to be important step as this the framework which provides complete stability and
continuity in order to assist the framework.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10RISK MANAGEMENT
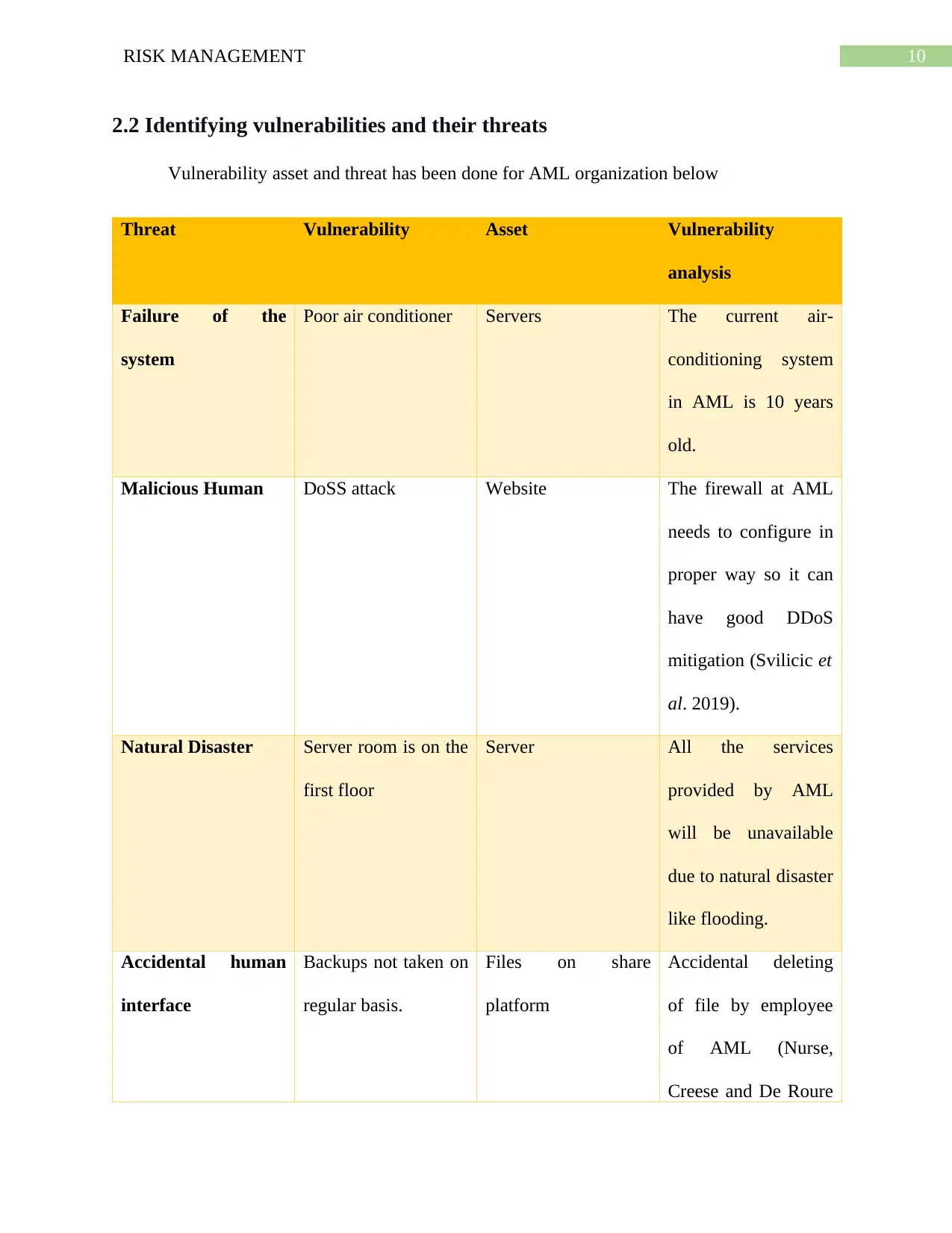
2.2 Identifying vulnerabilities and their threats
Vulnerability asset and threat has been done for AML organization below
Threat Vulnerability Asset Vulnerability
analysis
Failure of the
system
Poor air conditioner Servers The current air-
conditioning system
in AML is 10 years
old.
Malicious Human DoSS attack Website The firewall at AML
needs to configure in
proper way so it can
have good DDoS
mitigation (Svilicic et
al. 2019).
Natural Disaster Server room is on the
first floor
Server All the services
provided by AML
will be unavailable
due to natural disaster
like flooding.
Accidental human
interface
Backups not taken on
regular basis.
Files on share
platform
Accidental deleting
of file by employee
of AML (Nurse,
Creese and De Roure
2.2 Identifying vulnerabilities and their threats
Vulnerability asset and threat has been done for AML organization below
Threat Vulnerability Asset Vulnerability
analysis
Failure of the
system
Poor air conditioner Servers The current air-
conditioning system
in AML is 10 years
old.
Malicious Human DoSS attack Website The firewall at AML
needs to configure in
proper way so it can
have good DDoS
mitigation (Svilicic et
al. 2019).
Natural Disaster Server room is on the
first floor
Server All the services
provided by AML
will be unavailable
due to natural disaster
like flooding.
Accidental human
interface
Backups not taken on
regular basis.
Files on share
platform
Accidental deleting
of file by employee
of AML (Nurse,
Creese and De Roure
11RISK MANAGEMENT
2017).
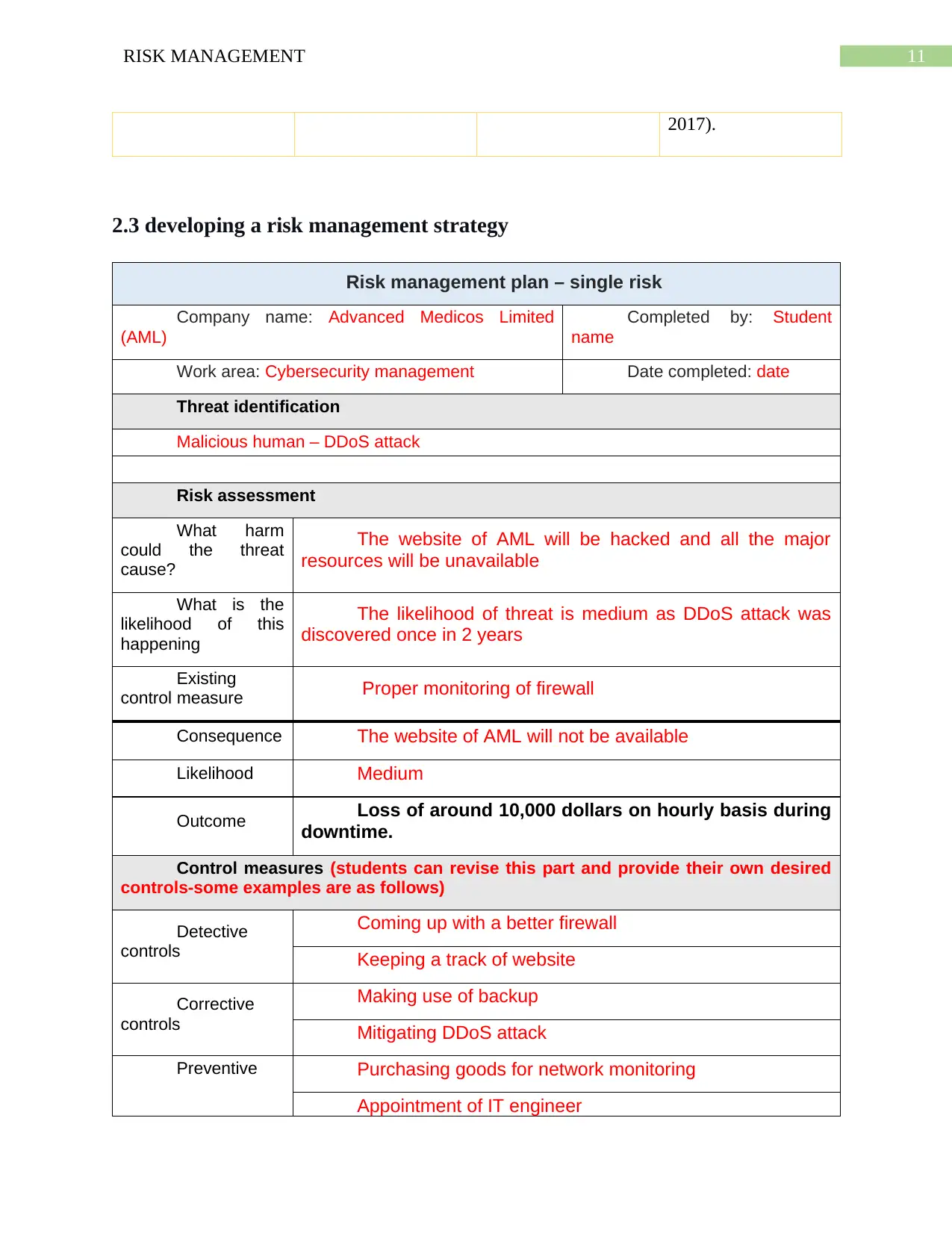
2.3 developing a risk management strategy
Risk management plan – single risk
Company name: Advanced Medicos Limited
(AML)
Completed by: Student
name
Work area: Cybersecurity management Date completed: date
Threat identification
Malicious human – DDoS attack
Risk assessment
What harm
could the threat
cause?
The website of AML will be hacked and all the major
resources will be unavailable
What is the
likelihood of this
happening
The likelihood of threat is medium as DDoS attack was
discovered once in 2 years
Existing
control measure Proper monitoring of firewall
Consequence The website of AML will not be available
Likelihood Medium
Outcome Loss of around 10,000 dollars on hourly basis during
downtime.
Control measures (students can revise this part and provide their own desired
controls-some examples are as follows)
Detective
controls
Coming up with a better firewall
Keeping a track of website
Corrective
controls
Making use of backup
Mitigating DDoS attack
Preventive Purchasing goods for network monitoring
Appointment of IT engineer
2017).
2.3 developing a risk management strategy
Risk management plan – single risk
Company name: Advanced Medicos Limited
(AML)
Completed by: Student
name
Work area: Cybersecurity management Date completed: date
Threat identification
Malicious human – DDoS attack
Risk assessment
What harm
could the threat
cause?
The website of AML will be hacked and all the major
resources will be unavailable
What is the
likelihood of this
happening
The likelihood of threat is medium as DDoS attack was
discovered once in 2 years
Existing
control measure Proper monitoring of firewall
Consequence The website of AML will not be available
Likelihood Medium
Outcome Loss of around 10,000 dollars on hourly basis during
downtime.
Control measures (students can revise this part and provide their own desired
controls-some examples are as follows)
Detective
controls
Coming up with a better firewall
Keeping a track of website
Corrective
controls
Making use of backup
Mitigating DDoS attack
Preventive Purchasing goods for network monitoring
Appointment of IT engineer
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





