Risk Assessment of Public Cloud Network for Charity Organization
VerifiedAdded on 2019/10/09
|20
|6902
|292
Report
AI Summary
This report assesses the risks associated with migrating a community-based charity's data and services to a public cloud (SaaS) environment. It begins by examining the limitations and vulnerabilities of the charity's existing on-premise Windows Server 2008 R2 system, particularly concerning employee data security. The report identifies key risks such as security breaches, performance problems, lack of visibility, and limited service capabilities inherent in the private cloud setup. It then explores the specific threats that arise during the transition to a public cloud, including data transfer negligence, complexity, and manipulation, as well as data access risks, instability, and a lack of transparency. The report uses a matrix to evaluate the severity of identified threats, highlighting data access risks and poor service provider security as extreme threats. Finally, the report addresses employee privacy threats in both the current and proposed cloud environments, focusing on excessive data access privileges, data stealing, and mismanagement of employee information. The analysis underscores the importance of robust security measures and careful planning to mitigate these risks when moving to a public cloud infrastructure.

Assessment-2- Risk Assessment of Public Cloud network
About the Case
A community-based charity is providing healthcare and community services to the
disadvantaged people in the community. The community is having its own data centre (50*86
64-bit Windows server 2008 R2) for its desktop, database and file service. For public, it runs Red
Hat Enterprise Linux 5 which it is using for web service.
Since the requirements of storage and confidentiality of healthcare information is getting more,
the charitable institution is looking for a public cloud that will solve all these issues. So in this
report we are going to look at the current level risk, risk management in public cloud service
(SaaS) and the approach of security and confidentiality in public cloud network.
Employee Data Security
The first aspect of changing the data storage and services starts with identifying the risks and
threats relating to organizational data in the existing system. One of the key data for an
organization is “employee data”. So our first task is to find the sphere of employee data security
breach and vulnerability in the existing HR database management. [Chen, Y.,et.al2010]
Current threats and risks with employee data
One of the key limitation of Windows 64-bit server R2 is its maximum storage limit. As the
Microsoft Inc., it can store only up to 2TB data at its best. As the company’s information, the
organization is looking for storing around 200TB data that means at least 25% or 40TB data will
be required for employees thus current system is no way efficient or eligible to fulfil the
information requirement or data storage of the employees.
Apart from the maximum limit, there are further limitations to the server systems such as-
It works with single CPU system thus any additional CPU will get ignored.
About the Case
A community-based charity is providing healthcare and community services to the
disadvantaged people in the community. The community is having its own data centre (50*86
64-bit Windows server 2008 R2) for its desktop, database and file service. For public, it runs Red
Hat Enterprise Linux 5 which it is using for web service.
Since the requirements of storage and confidentiality of healthcare information is getting more,
the charitable institution is looking for a public cloud that will solve all these issues. So in this
report we are going to look at the current level risk, risk management in public cloud service
(SaaS) and the approach of security and confidentiality in public cloud network.
Employee Data Security
The first aspect of changing the data storage and services starts with identifying the risks and
threats relating to organizational data in the existing system. One of the key data for an
organization is “employee data”. So our first task is to find the sphere of employee data security
breach and vulnerability in the existing HR database management. [Chen, Y.,et.al2010]
Current threats and risks with employee data
One of the key limitation of Windows 64-bit server R2 is its maximum storage limit. As the
Microsoft Inc., it can store only up to 2TB data at its best. As the company’s information, the
organization is looking for storing around 200TB data that means at least 25% or 40TB data will
be required for employees thus current system is no way efficient or eligible to fulfil the
information requirement or data storage of the employees.
Apart from the maximum limit, there are further limitations to the server systems such as-
It works with single CPU system thus any additional CPU will get ignored.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

It works with 8GB Ram and additional RAM inclusion is not possible thus when the data
load increases, it will hang the system which can cause loss of employee data.
It consists of 15 User CALs thus if the number increases, the system will produce
warning message.
It allows only 50 desktop connections at a time but having an employee base of 500
people, the system is vulnerable.
The system can’t be virtualised.
It can’t be used as Hyper V spot.
It can’t be used as Domain Controller where more than 15 accounts are in the Domain
and also can’t fit to the system where trust relationship exist.[Gonzalez, N et.al2012]
Now, these are foundational limitations for which the management thought of HR database
into Public (SaaS) cloud server. But, what about the risk factors associated with existing
system.
Here we can draw 5 such risks that are present in this private cloud service-
Security Breach
Unlike public cloud which are managed by some IT experts with load of experience, private
clouds are managed by the organisational people only. Many at times, the organizations don’t
have such experts to manage private cloud network due to resources constraints. This charity
organisation is facing the same issue. Although public clouds are on target but private clouds
are easy to hack if internal people get involved. With such healthcare organisations, the
security breach risk is more in order to steal confidential health data for selling to third party.
[Krutz, R. L.,et.al2010]
Performance Problem
Because of dynamic nature of environment, it is very difficult to predict changing load at
infrastructural level that can affect application performance and user experience. In public,
clouds the user knows the cloud bandwidth, latency, jitter and resource sharing and that can’t
be altered easily (for e.g. blockchain technology) but private clouds are having flexibility in
load increases, it will hang the system which can cause loss of employee data.
It consists of 15 User CALs thus if the number increases, the system will produce
warning message.
It allows only 50 desktop connections at a time but having an employee base of 500
people, the system is vulnerable.
The system can’t be virtualised.
It can’t be used as Hyper V spot.
It can’t be used as Domain Controller where more than 15 accounts are in the Domain
and also can’t fit to the system where trust relationship exist.[Gonzalez, N et.al2012]
Now, these are foundational limitations for which the management thought of HR database
into Public (SaaS) cloud server. But, what about the risk factors associated with existing
system.
Here we can draw 5 such risks that are present in this private cloud service-
Security Breach
Unlike public cloud which are managed by some IT experts with load of experience, private
clouds are managed by the organisational people only. Many at times, the organizations don’t
have such experts to manage private cloud network due to resources constraints. This charity
organisation is facing the same issue. Although public clouds are on target but private clouds
are easy to hack if internal people get involved. With such healthcare organisations, the
security breach risk is more in order to steal confidential health data for selling to third party.
[Krutz, R. L.,et.al2010]
Performance Problem
Because of dynamic nature of environment, it is very difficult to predict changing load at
infrastructural level that can affect application performance and user experience. In public,
clouds the user knows the cloud bandwidth, latency, jitter and resource sharing and that can’t
be altered easily (for e.g. blockchain technology) but private clouds are having flexibility in

choosing the cloud infrastructure in terms of hardware and software thus it provides scope for
the IT manipulator or hackers to access systems easily to steal HR data or change performance
figures for personal benefit. [Sabahi, F. (2011)]
Open-source platform
Private clouds are majorly customised in nature as per the requirements and suitability to the
organisational environment. Many at times, when the private cloud network is set up, some
standard protocols are decided and that is followed for operating in the cloud. If the senior
management has set protocols in accordance to their personal benefit, they can manipulate HR
database in order to show better performance while reporting. [Dahbur, K., et.al2011] For ex- A
senior management may favour an employee by increasing his attendance over the network
using proxy ID. This will be possible because cloud infrastructure and operation is open to
people working inside the organisation especially the senior management.
Lack of visibility
Private cloud like Windows Server 2008 R2 may face “East-West traffic” i.e. network traffic
flowing between virtual machines. [Zissis, D et.al2012] Any issues over the cloud can’t be
monitored with traditional IT monitoring tools. Suppose the HR manager tries to enter into any
unsecured website or application, the hackers can easily hack the system HR is using (if that is
operated virtually in an open Wi-Fi service). This will make employees data vulnerable.
Limited service
Private clouds are limited due to customisation fact. It is the IT team and management who will
decide what services should be included and what shouldn’t be. Now, if the management
shows biasness while adding a specific feature or functionality for project scope, the ability to
innovate private cloud will be limited. For ex- If management allows open access to employees
for looking at payroll and performance, the employees can try to manipulate the data if that is
not in their favour.
Employee data risk and threats while shifting to SaaS
the IT manipulator or hackers to access systems easily to steal HR data or change performance
figures for personal benefit. [Sabahi, F. (2011)]
Open-source platform
Private clouds are majorly customised in nature as per the requirements and suitability to the
organisational environment. Many at times, when the private cloud network is set up, some
standard protocols are decided and that is followed for operating in the cloud. If the senior
management has set protocols in accordance to their personal benefit, they can manipulate HR
database in order to show better performance while reporting. [Dahbur, K., et.al2011] For ex- A
senior management may favour an employee by increasing his attendance over the network
using proxy ID. This will be possible because cloud infrastructure and operation is open to
people working inside the organisation especially the senior management.
Lack of visibility
Private cloud like Windows Server 2008 R2 may face “East-West traffic” i.e. network traffic
flowing between virtual machines. [Zissis, D et.al2012] Any issues over the cloud can’t be
monitored with traditional IT monitoring tools. Suppose the HR manager tries to enter into any
unsecured website or application, the hackers can easily hack the system HR is using (if that is
operated virtually in an open Wi-Fi service). This will make employees data vulnerable.
Limited service
Private clouds are limited due to customisation fact. It is the IT team and management who will
decide what services should be included and what shouldn’t be. Now, if the management
shows biasness while adding a specific feature or functionality for project scope, the ability to
innovate private cloud will be limited. For ex- If management allows open access to employees
for looking at payroll and performance, the employees can try to manipulate the data if that is
not in their favour.
Employee data risk and threats while shifting to SaaS
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

As the Charitable institution is planning to have a SaaS cloud system for management of
database, it will require to shift data from the private clouds into the public cloud. While doing
so, the following security threats may emerge- [Bamiah, M. A.,et.al 2011]
Negligence of data transfer
When the charitable institution is going to transfer the data from its private network to the
public cloud network, there is a high level chances of forgetfulness of the significant HR data
that may not be transferred by the personnel. In such case, such negligence (intentionally or by
mistake) can cause data stealing risk. As after transfer the private network data will be erased
thus recovery of such data may not be possible later.
Data transfer complexity
Many at times, when the transfer takes place, the IT manager faces difficulty to transfer all data
into new systems. When the private network data is stored for a long period of time and the
person managing the data forgot the directories where the files are stored in what form, then it
will be very difficult for the IT manager to locate the files to send into new system. If the data
are not understandable, then transfer won’t take place and that may cause loss.
Manipulated data transfer
As long as the private network, the controller has full accessibility to see and change the
information within the structure as he/she has the idea of the structure. But, while it is get
transferred into a public cloud (SaaS) which is not under the control, the concerned person may
not transfer the information that can be beneficial for him/her or will refrain his personal
intention.
Data access risk
SaaS is vendor operated could service thus the vendor may access the confidential information
in HR database that can be used for profitable purpose.
Instability
database, it will require to shift data from the private clouds into the public cloud. While doing
so, the following security threats may emerge- [Bamiah, M. A.,et.al 2011]
Negligence of data transfer
When the charitable institution is going to transfer the data from its private network to the
public cloud network, there is a high level chances of forgetfulness of the significant HR data
that may not be transferred by the personnel. In such case, such negligence (intentionally or by
mistake) can cause data stealing risk. As after transfer the private network data will be erased
thus recovery of such data may not be possible later.
Data transfer complexity
Many at times, when the transfer takes place, the IT manager faces difficulty to transfer all data
into new systems. When the private network data is stored for a long period of time and the
person managing the data forgot the directories where the files are stored in what form, then it
will be very difficult for the IT manager to locate the files to send into new system. If the data
are not understandable, then transfer won’t take place and that may cause loss.
Manipulated data transfer
As long as the private network, the controller has full accessibility to see and change the
information within the structure as he/she has the idea of the structure. But, while it is get
transferred into a public cloud (SaaS) which is not under the control, the concerned person may
not transfer the information that can be beneficial for him/her or will refrain his personal
intention.
Data access risk
SaaS is vendor operated could service thus the vendor may access the confidential information
in HR database that can be used for profitable purpose.
Instability
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The platform is not limited to any single user thus it will increase the competition among the
users to use the service to the fullest. When the service provider is unable to provide more
space and will shut the service, it will directly affect the database of the charity.
Transparency
Although SaaS ensures high level security to the client but it doesn’t answer all the questions of
security. If the service provider is manipulating data over the cloud service, the client’s data will
be at greater risk. Until a detailed security and privacy agreement is signed, the gap of security
will be there.
Uncertainty of data location
As the information provided by the company, the database is having replica in Dublin, Ireland
alongside the main centre in California. However the processing and configuration are done in
Bangalore India. This shows that data will move more than 1 location and will be available to
multiple personnel thus at any level, data breaching or stealing can be done which the client
won’t able to find.
No direct control of own data
The whole payroll is shifting to Commercial off the Shelf (COTS0 application which is a public
cloud service. When you hand entire payroll responsibility to a third party, they get full access
to your payroll structure which they can steal and give it to competitors for a good
consideration.
Service provider poor security standards
The service provider hasn’t expressed anything regarding firewalls and standard security
protocols that they are using to keep the information security. Until they provide hard to
decode firewall and antivirus system over the network, data stealing and manipulation will be
there.
Assessment of Severity of HR database security threat
users to use the service to the fullest. When the service provider is unable to provide more
space and will shut the service, it will directly affect the database of the charity.
Transparency
Although SaaS ensures high level security to the client but it doesn’t answer all the questions of
security. If the service provider is manipulating data over the cloud service, the client’s data will
be at greater risk. Until a detailed security and privacy agreement is signed, the gap of security
will be there.
Uncertainty of data location
As the information provided by the company, the database is having replica in Dublin, Ireland
alongside the main centre in California. However the processing and configuration are done in
Bangalore India. This shows that data will move more than 1 location and will be available to
multiple personnel thus at any level, data breaching or stealing can be done which the client
won’t able to find.
No direct control of own data
The whole payroll is shifting to Commercial off the Shelf (COTS0 application which is a public
cloud service. When you hand entire payroll responsibility to a third party, they get full access
to your payroll structure which they can steal and give it to competitors for a good
consideration.
Service provider poor security standards
The service provider hasn’t expressed anything regarding firewalls and standard security
protocols that they are using to keep the information security. Until they provide hard to
decode firewall and antivirus system over the network, data stealing and manipulation will be
there.
Assessment of Severity of HR database security threat
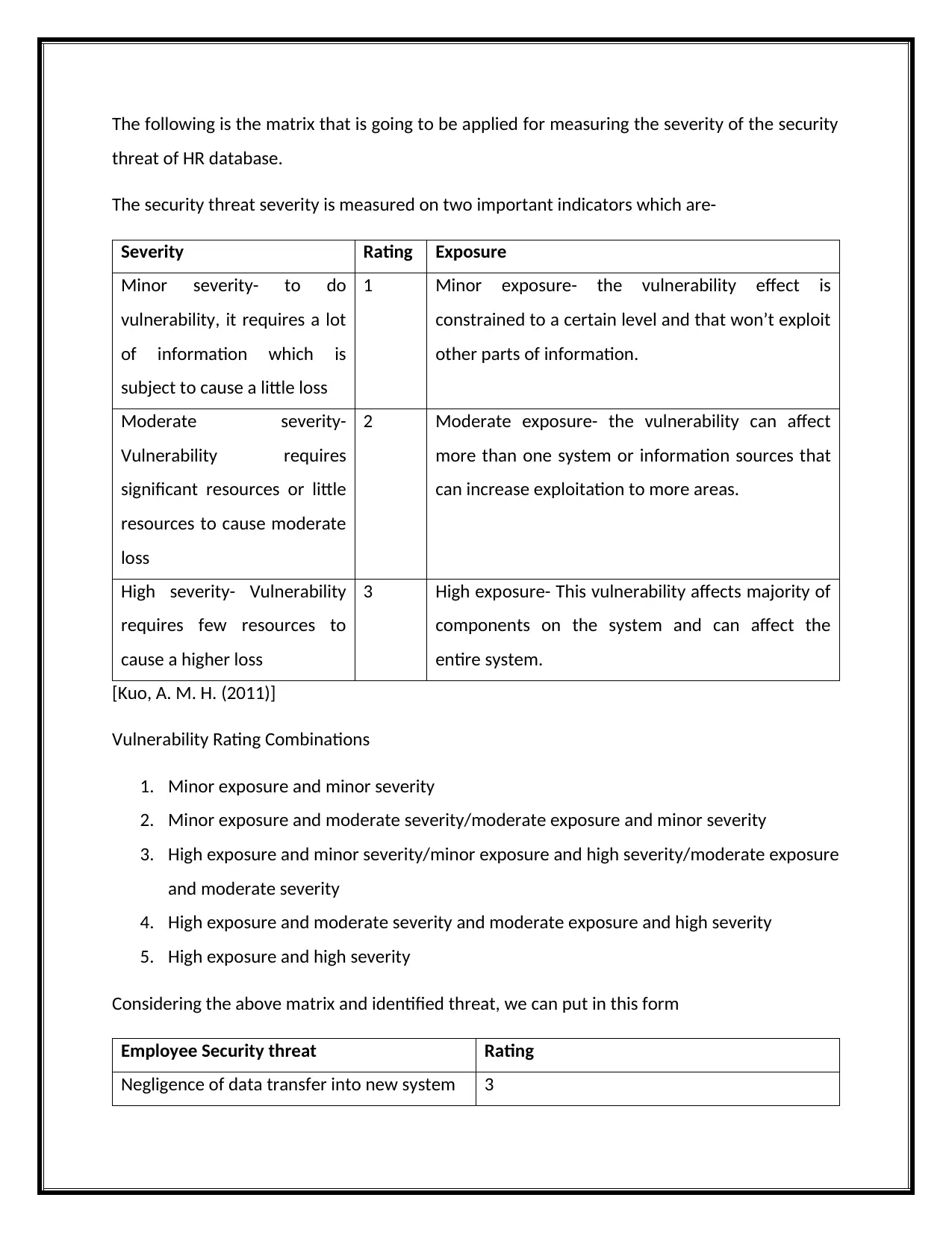
The following is the matrix that is going to be applied for measuring the severity of the security
threat of HR database.
The security threat severity is measured on two important indicators which are-
Severity Rating Exposure
Minor severity- to do
vulnerability, it requires a lot
of information which is
subject to cause a little loss
1 Minor exposure- the vulnerability effect is
constrained to a certain level and that won’t exploit
other parts of information.
Moderate severity-
Vulnerability requires
significant resources or little
resources to cause moderate
loss
2 Moderate exposure- the vulnerability can affect
more than one system or information sources that
can increase exploitation to more areas.
High severity- Vulnerability
requires few resources to
cause a higher loss
3 High exposure- This vulnerability affects majority of
components on the system and can affect the
entire system.
[Kuo, A. M. H. (2011)]
Vulnerability Rating Combinations
1. Minor exposure and minor severity
2. Minor exposure and moderate severity/moderate exposure and minor severity
3. High exposure and minor severity/minor exposure and high severity/moderate exposure
and moderate severity
4. High exposure and moderate severity and moderate exposure and high severity
5. High exposure and high severity
Considering the above matrix and identified threat, we can put in this form
Employee Security threat Rating
Negligence of data transfer into new system 3
threat of HR database.
The security threat severity is measured on two important indicators which are-
Severity Rating Exposure
Minor severity- to do
vulnerability, it requires a lot
of information which is
subject to cause a little loss
1 Minor exposure- the vulnerability effect is
constrained to a certain level and that won’t exploit
other parts of information.
Moderate severity-
Vulnerability requires
significant resources or little
resources to cause moderate
loss
2 Moderate exposure- the vulnerability can affect
more than one system or information sources that
can increase exploitation to more areas.
High severity- Vulnerability
requires few resources to
cause a higher loss
3 High exposure- This vulnerability affects majority of
components on the system and can affect the
entire system.
[Kuo, A. M. H. (2011)]
Vulnerability Rating Combinations
1. Minor exposure and minor severity
2. Minor exposure and moderate severity/moderate exposure and minor severity
3. High exposure and minor severity/minor exposure and high severity/moderate exposure
and moderate severity
4. High exposure and moderate severity and moderate exposure and high severity
5. High exposure and high severity
Considering the above matrix and identified threat, we can put in this form
Employee Security threat Rating
Negligence of data transfer into new system 3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
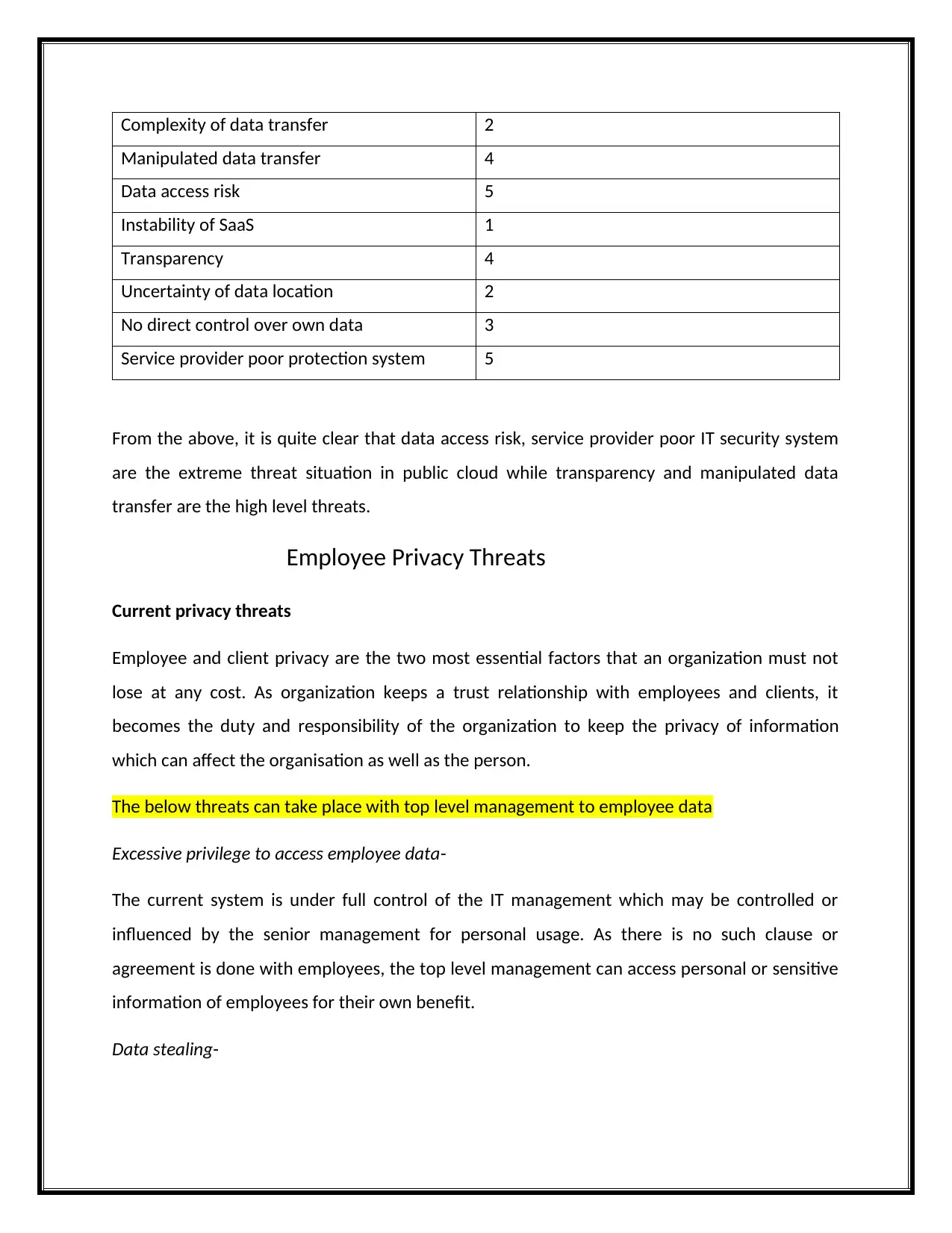
Complexity of data transfer 2
Manipulated data transfer 4
Data access risk 5
Instability of SaaS 1
Transparency 4
Uncertainty of data location 2
No direct control over own data 3
Service provider poor protection system 5
From the above, it is quite clear that data access risk, service provider poor IT security system
are the extreme threat situation in public cloud while transparency and manipulated data
transfer are the high level threats.
Employee Privacy Threats
Current privacy threats
Employee and client privacy are the two most essential factors that an organization must not
lose at any cost. As organization keeps a trust relationship with employees and clients, it
becomes the duty and responsibility of the organization to keep the privacy of information
which can affect the organisation as well as the person.
The below threats can take place with top level management to employee data
Excessive privilege to access employee data-
The current system is under full control of the IT management which may be controlled or
influenced by the senior management for personal usage. As there is no such clause or
agreement is done with employees, the top level management can access personal or sensitive
information of employees for their own benefit.
Data stealing-
Manipulated data transfer 4
Data access risk 5
Instability of SaaS 1
Transparency 4
Uncertainty of data location 2
No direct control over own data 3
Service provider poor protection system 5
From the above, it is quite clear that data access risk, service provider poor IT security system
are the extreme threat situation in public cloud while transparency and manipulated data
transfer are the high level threats.
Employee Privacy Threats
Current privacy threats
Employee and client privacy are the two most essential factors that an organization must not
lose at any cost. As organization keeps a trust relationship with employees and clients, it
becomes the duty and responsibility of the organization to keep the privacy of information
which can affect the organisation as well as the person.
The below threats can take place with top level management to employee data
Excessive privilege to access employee data-
The current system is under full control of the IT management which may be controlled or
influenced by the senior management for personal usage. As there is no such clause or
agreement is done with employees, the top level management can access personal or sensitive
information of employees for their own benefit.
Data stealing-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The top level management can steal the confidential data about employees to use it illegally or
unethically in outside profitable purpose. As the charitable organisation is related to healthcare
service, thus stealing employees’ performance data can open the gateway to steal client’s
confidential information.
Mismanagement of employee data
It can be the most probable threat that is possible with the existing private server system. As
the data entry, processing, configuration and protection is done by the people inside the
organisation who can be forced by the top management to misplace data to get their personal
interest. Such mismanagement can cause financial, psychological and emotional damage to the
employees.
Employee’s action threat to privacy of other employees
It is not only the top level or IT manager or HR head who can do manipulation in the existing
database system but also an employee can use the system for taking personal advantage by
putting others in trouble.
Access of other’s data- The current system includes authentication and accessibility of
employees using unique ID given by the Charity. Suppose an employee gets other’s ID and code,
he/she can manipulate the database using proxy server. As it is a private or loop system, the
employees may find space to decode the structural security using virus or malware. [Chen,
D.,et.al2012]
Use of infected system- Employee intentionally or unintentionally may use his portal through an
infected (virus or malware infected) system to access HR data. By doing such, the cyber threats
will enter into the central database and will make the system corrupt.
Leak of confidential information about the organisation- As employees have accessibility to
internal records of the organisation, they can use it for personal advantages. They may leak HR
database information to rivalry organisations for monetary consideration.
Additional risks and threats with SaaS
unethically in outside profitable purpose. As the charitable organisation is related to healthcare
service, thus stealing employees’ performance data can open the gateway to steal client’s
confidential information.
Mismanagement of employee data
It can be the most probable threat that is possible with the existing private server system. As
the data entry, processing, configuration and protection is done by the people inside the
organisation who can be forced by the top management to misplace data to get their personal
interest. Such mismanagement can cause financial, psychological and emotional damage to the
employees.
Employee’s action threat to privacy of other employees
It is not only the top level or IT manager or HR head who can do manipulation in the existing
database system but also an employee can use the system for taking personal advantage by
putting others in trouble.
Access of other’s data- The current system includes authentication and accessibility of
employees using unique ID given by the Charity. Suppose an employee gets other’s ID and code,
he/she can manipulate the database using proxy server. As it is a private or loop system, the
employees may find space to decode the structural security using virus or malware. [Chen,
D.,et.al2012]
Use of infected system- Employee intentionally or unintentionally may use his portal through an
infected (virus or malware infected) system to access HR data. By doing such, the cyber threats
will enter into the central database and will make the system corrupt.
Leak of confidential information about the organisation- As employees have accessibility to
internal records of the organisation, they can use it for personal advantages. They may leak HR
database information to rivalry organisations for monetary consideration.
Additional risks and threats with SaaS

Like security threat, privacy is also under question mark in SaaS. Although the level of privacy
risk and threats are not that much like in earlier case, still some privacy concerns do exist.
Here are the some of the key privacy risk or threats factors that the charitable organisation HR
department-
Client’s data leak- Since it is a community cum healthcare organisation, majority of the
employees are expected to have information regarding the clients to give varieties of service in
accordance to their need. In SaaS system, the employees are going to put data into the vendor
service system where if the vendor does any negligence on data storing or processing, the client
data will be vulnerable. Healthcare and community services information come under highly
confidential information, if it leaks through employee portal, it will put the client service under
scanner.
Lack of internal control- SaaS is a publically managed software service provision. The control
over its management and usage lie with the vendor only. Thus, the organisation doesn’t have
control over its storage and supply of information. If the vendor doesn’t provide adequate
firewall security, it will expose confidential data of employees and clients in a public network.
Lack of transparency- Privacy has lot to do with transparency. The vendor may not provide
adequate assistance to upload the data into the system or may not agree to take any risk of
data uploading. As in such case, any mistake done by the HR department or employees
regarding their performance or payroll will make vulnerability of data. Even data loss can take
place with loads of data entry into the same system used by any other client.
Limited service- SaaS vendor is providing restricted software application services to the client
thus they are limiting the uploading of the data. There can be some confidential information of
employees and clients that vendor may not provide under agreement which then have to store
in local network. This will be subject to privacy breach as local network (intranet) may not be
secured adequately.
Virtual support- This is another important concern for privacy of employee data. As per the
organisation request, the data will be uploaded by the employees only which will be processed,
risk and threats are not that much like in earlier case, still some privacy concerns do exist.
Here are the some of the key privacy risk or threats factors that the charitable organisation HR
department-
Client’s data leak- Since it is a community cum healthcare organisation, majority of the
employees are expected to have information regarding the clients to give varieties of service in
accordance to their need. In SaaS system, the employees are going to put data into the vendor
service system where if the vendor does any negligence on data storing or processing, the client
data will be vulnerable. Healthcare and community services information come under highly
confidential information, if it leaks through employee portal, it will put the client service under
scanner.
Lack of internal control- SaaS is a publically managed software service provision. The control
over its management and usage lie with the vendor only. Thus, the organisation doesn’t have
control over its storage and supply of information. If the vendor doesn’t provide adequate
firewall security, it will expose confidential data of employees and clients in a public network.
Lack of transparency- Privacy has lot to do with transparency. The vendor may not provide
adequate assistance to upload the data into the system or may not agree to take any risk of
data uploading. As in such case, any mistake done by the HR department or employees
regarding their performance or payroll will make vulnerability of data. Even data loss can take
place with loads of data entry into the same system used by any other client.
Limited service- SaaS vendor is providing restricted software application services to the client
thus they are limiting the uploading of the data. There can be some confidential information of
employees and clients that vendor may not provide under agreement which then have to store
in local network. This will be subject to privacy breach as local network (intranet) may not be
secured adequately.
Virtual support- This is another important concern for privacy of employee data. As per the
organisation request, the data will be uploaded by the employees only which will be processed,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
configured and stored over the cloud at different places. After uploading, at no stage physical
support is given to the employee’s data, whole responsibility is on the people sitting in
California, Doblin and Bangalore to keep the privacy. If at any place, they open up the
information without knowledge of the charitable institution, it will put the client service in deep
trouble.
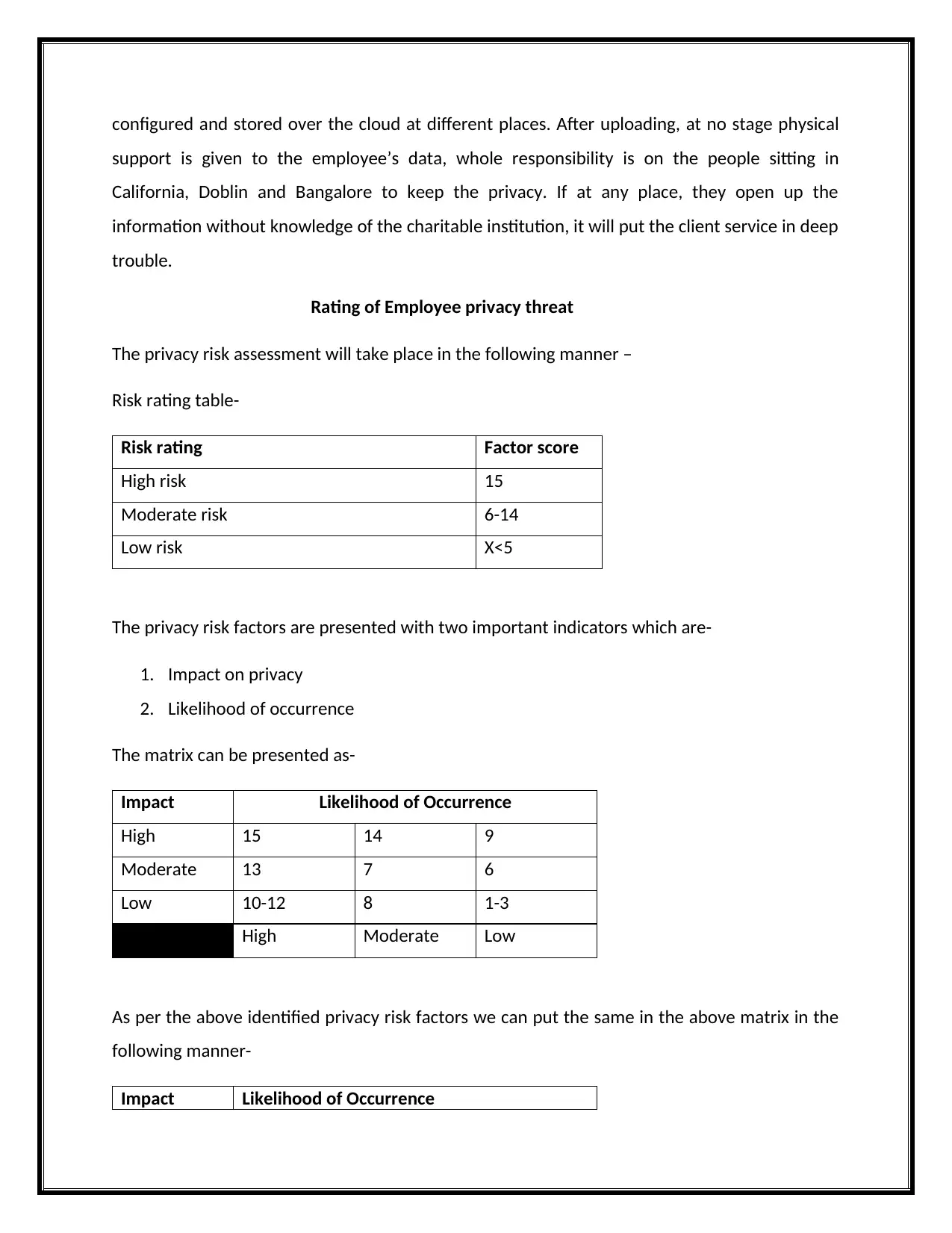
Rating of Employee privacy threat
The privacy risk assessment will take place in the following manner –
Risk rating table-
Risk rating Factor score
High risk 15
Moderate risk 6-14
Low risk X<5
The privacy risk factors are presented with two important indicators which are-
1. Impact on privacy
2. Likelihood of occurrence
The matrix can be presented as-
Impact Likelihood of Occurrence
High 15 14 9
Moderate 13 7 6
Low 10-12 8 1-3
High Moderate Low
As per the above identified privacy risk factors we can put the same in the above matrix in the
following manner-
Impact Likelihood of Occurrence
support is given to the employee’s data, whole responsibility is on the people sitting in
California, Doblin and Bangalore to keep the privacy. If at any place, they open up the
information without knowledge of the charitable institution, it will put the client service in deep
trouble.
Rating of Employee privacy threat
The privacy risk assessment will take place in the following manner –
Risk rating table-
Risk rating Factor score
High risk 15
Moderate risk 6-14
Low risk X<5
The privacy risk factors are presented with two important indicators which are-
1. Impact on privacy
2. Likelihood of occurrence
The matrix can be presented as-
Impact Likelihood of Occurrence
High 15 14 9
Moderate 13 7 6
Low 10-12 8 1-3
High Moderate Low
As per the above identified privacy risk factors we can put the same in the above matrix in the
following manner-
Impact Likelihood of Occurrence
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
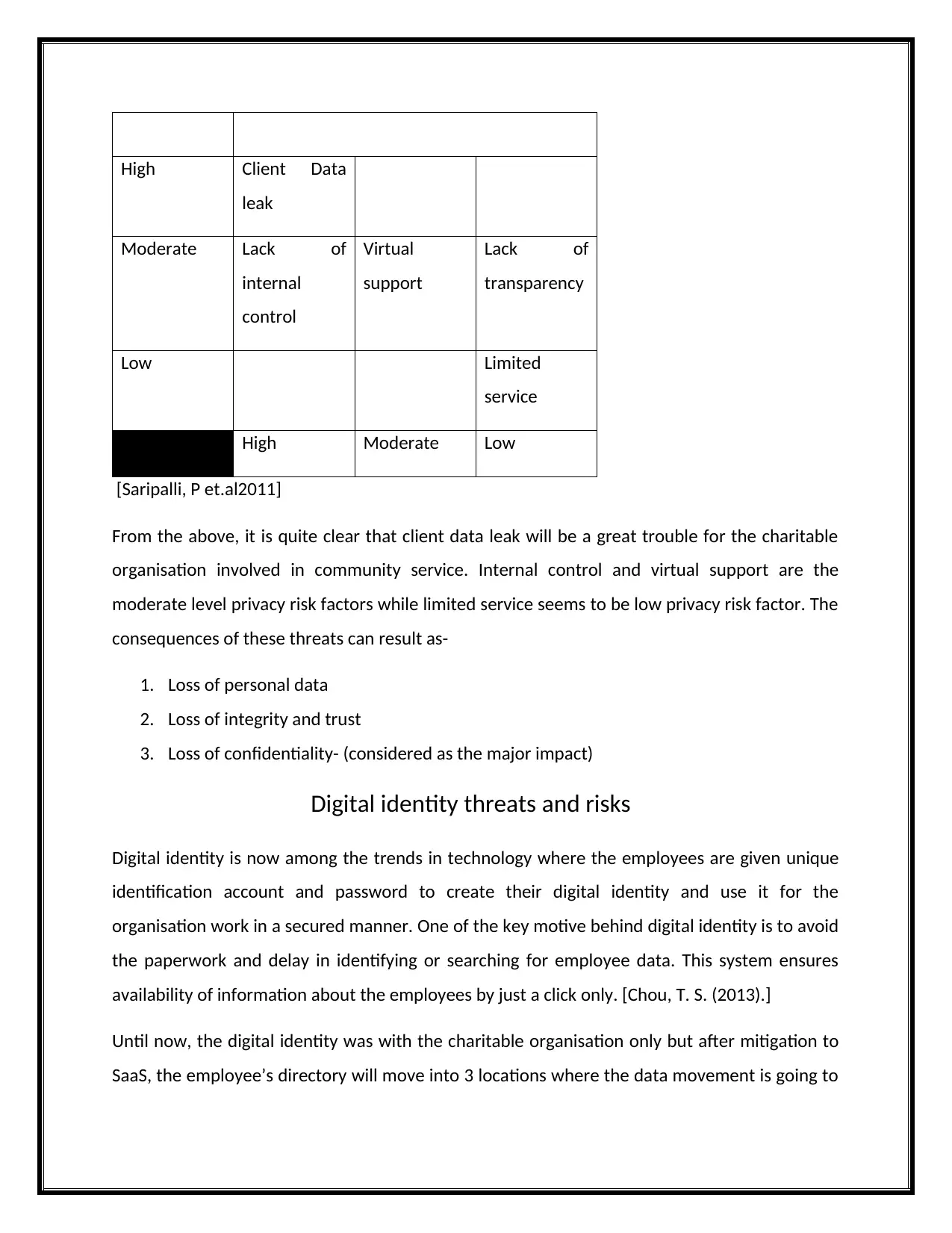
High Client Data
leak
Moderate Lack of
internal
control
Virtual
support
Lack of
transparency
Low Limited
service
High Moderate Low
[Saripalli, P et.al2011]
From the above, it is quite clear that client data leak will be a great trouble for the charitable
organisation involved in community service. Internal control and virtual support are the
moderate level privacy risk factors while limited service seems to be low privacy risk factor. The
consequences of these threats can result as-
1. Loss of personal data
2. Loss of integrity and trust
3. Loss of confidentiality- (considered as the major impact)
Digital identity threats and risks
Digital identity is now among the trends in technology where the employees are given unique
identification account and password to create their digital identity and use it for the
organisation work in a secured manner. One of the key motive behind digital identity is to avoid
the paperwork and delay in identifying or searching for employee data. This system ensures
availability of information about the employees by just a click only. [Chou, T. S. (2013).]
Until now, the digital identity was with the charitable organisation only but after mitigation to
SaaS, the employee’s directory will move into 3 locations where the data movement is going to
leak
Moderate Lack of
internal
control
Virtual
support
Lack of
transparency
Low Limited
service
High Moderate Low
[Saripalli, P et.al2011]
From the above, it is quite clear that client data leak will be a great trouble for the charitable
organisation involved in community service. Internal control and virtual support are the
moderate level privacy risk factors while limited service seems to be low privacy risk factor. The
consequences of these threats can result as-
1. Loss of personal data
2. Loss of integrity and trust
3. Loss of confidentiality- (considered as the major impact)
Digital identity threats and risks
Digital identity is now among the trends in technology where the employees are given unique
identification account and password to create their digital identity and use it for the
organisation work in a secured manner. One of the key motive behind digital identity is to avoid
the paperwork and delay in identifying or searching for employee data. This system ensures
availability of information about the employees by just a click only. [Chou, T. S. (2013).]
Until now, the digital identity was with the charitable organisation only but after mitigation to
SaaS, the employee’s directory will move into 3 locations where the data movement is going to

take place. In earlier case, if vulnerability takes place, it can easily be detected as people within
the organisation can do so but when it is in public platform, the risk proportion increases.
Here are the potential risk and threats that employees of this charitable institution can face-
Privacy under check- In SaaS arrangement, the employees are required to upload their personal
and professional information (required under employment agreement) to the third party. Even
if the organisation does a privacy agreement with the vendor but the organisation has hardly
any accessibility to cross check the data trespassing over their software application. The vendor
may secretly leak all private information about employees or information about client using
proxy code or identity for own benefit. In that case, the employee’s privacy will be at greater
risk.
At hacker’s target- Public cloud network is always under the target of hackers and when it
comes to healthcare information which is considered to be the most sensitive information
about an individual, any sort of leak or destruction of information will lead to severe loss of the
organisation and the personal as well. The charitable institution’s employees may have client
details associated with their performance thus if hackers succeed to crack the application, it will
not only take the employee’s personal data but also will steal the client’s data for monetary
consideration. [Saripalli, P.,et.al2012]
Dummy ID- [Ko, R. K.,et.al2012]Virtual ID allows to make fake or dummy accounts to steal
confidential information about the organisation and client. In public cloud network, opening
such ID is easier than in private network. If anyone opens a dummy id that resembles with the
charitable employees Id, it will allow a direct accessibility to the detail records of clients and
employees. Information like their bank details, health information etc. can be used for unethical
or illegal purpose. Although such opening is not possible without involvement of internal
persons, but risk is always there.
Control of information- When employee data goes into SaaS, there the control over information
security and privacy stays with the vendor only. Now onwards, it all depends on the vendor
regarding how they will provide protection to the employee data. Suppose they don’t provide
the organisation can do so but when it is in public platform, the risk proportion increases.
Here are the potential risk and threats that employees of this charitable institution can face-
Privacy under check- In SaaS arrangement, the employees are required to upload their personal
and professional information (required under employment agreement) to the third party. Even
if the organisation does a privacy agreement with the vendor but the organisation has hardly
any accessibility to cross check the data trespassing over their software application. The vendor
may secretly leak all private information about employees or information about client using
proxy code or identity for own benefit. In that case, the employee’s privacy will be at greater
risk.
At hacker’s target- Public cloud network is always under the target of hackers and when it
comes to healthcare information which is considered to be the most sensitive information
about an individual, any sort of leak or destruction of information will lead to severe loss of the
organisation and the personal as well. The charitable institution’s employees may have client
details associated with their performance thus if hackers succeed to crack the application, it will
not only take the employee’s personal data but also will steal the client’s data for monetary
consideration. [Saripalli, P.,et.al2012]
Dummy ID- [Ko, R. K.,et.al2012]Virtual ID allows to make fake or dummy accounts to steal
confidential information about the organisation and client. In public cloud network, opening
such ID is easier than in private network. If anyone opens a dummy id that resembles with the
charitable employees Id, it will allow a direct accessibility to the detail records of clients and
employees. Information like their bank details, health information etc. can be used for unethical
or illegal purpose. Although such opening is not possible without involvement of internal
persons, but risk is always there.
Control of information- When employee data goes into SaaS, there the control over information
security and privacy stays with the vendor only. Now onwards, it all depends on the vendor
regarding how they will provide protection to the employee data. Suppose they don’t provide
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


