Information Security Management: Risk Assessment of CONVXYZ Network
VerifiedAdded on 2023/01/19
|27
|3351
|91
Report
AI Summary
This report presents a risk assessment of the CONVXYZ network infrastructure, adhering to ISO 27005 standards. The assessment begins with an introduction to risk management and risk assessment standards, focusing on the advantages of ISO 27001 and ISO 27005. It then details the system parameters, classifying assets as primary and secondary, and identifies vulnerabilities using the NVD database. Threat sources are identified, and their attractiveness is evaluated. The report calculates risk based on likelihood and impact, using the Boston grid. The analysis includes asset classification, threat source identification, attractiveness assessment, and vulnerability identification, culminating in risk calculation and likelihood determination. The report also presents the results of the risk assessment including an executive summary, main findings and risk treatment recommendations.

INFORMATION SECURITY MANAGEMENT
Name of the Student
Name of the University
Author Note
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION SECURITY MANAGEMENT
1. INTRODUCTION
In this report, a risk assessment will be performed on the network infrastructure of
CONVXYZ based on ISO 27005 standards. Fists of all the standards will be
reviewed in detail and according to that specific criteria’s will be mapped on the
given network infrastructure of CONVXYZ. First, the design specifies Owner
specification for the network. Now assets of the network classified according to
primary and secondary assets. The explanation for each of the assets provides a
collective explanation for a group of assets instead of explaining for each asset.
Along with that, one vulnerability for each asset defined. The vulnerabilities will
be taken from the
The report provides NVD online vulnerability database along with the official
CVE- number. Once the risks of the network are identified, Likelihood level
computation will be determined, using Boston gird, which will be followed by
Impact table specification.
- Risk management and risk assessment standards
Although there are various risk management and risk assessment standards,
when it is about managing risk in the context of IT infrastructure and network
security, three of the most widely used standards are COBIT, ITIL and ISO
27001.
1. INTRODUCTION
In this report, a risk assessment will be performed on the network infrastructure of
CONVXYZ based on ISO 27005 standards. Fists of all the standards will be
reviewed in detail and according to that specific criteria’s will be mapped on the
given network infrastructure of CONVXYZ. First, the design specifies Owner
specification for the network. Now assets of the network classified according to
primary and secondary assets. The explanation for each of the assets provides a
collective explanation for a group of assets instead of explaining for each asset.
Along with that, one vulnerability for each asset defined. The vulnerabilities will
be taken from the
The report provides NVD online vulnerability database along with the official
CVE- number. Once the risks of the network are identified, Likelihood level
computation will be determined, using Boston gird, which will be followed by
Impact table specification.
- Risk management and risk assessment standards
Although there are various risk management and risk assessment standards,
when it is about managing risk in the context of IT infrastructure and network
security, three of the most widely used standards are COBIT, ITIL and ISO
27001.
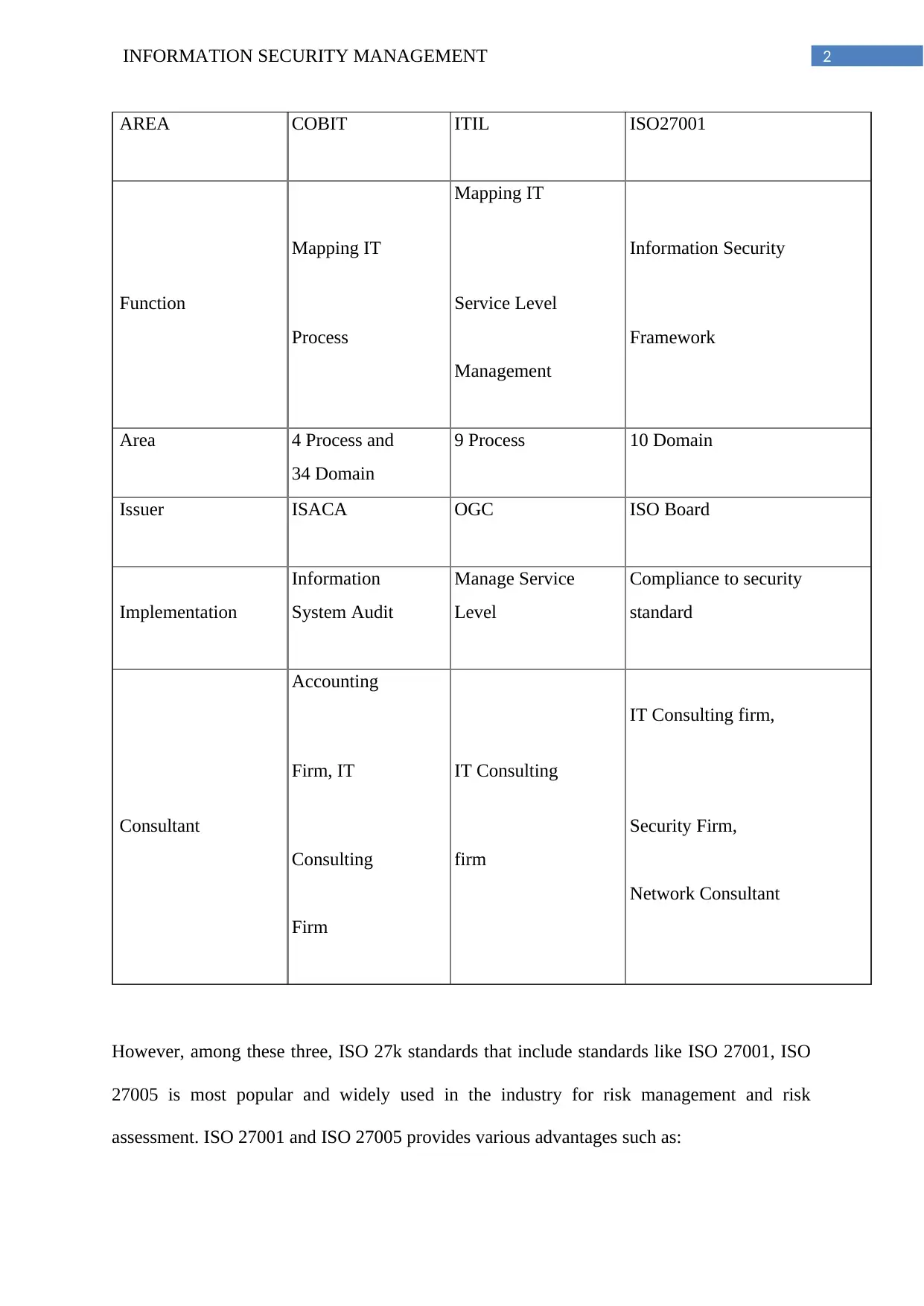
2INFORMATION SECURITY MANAGEMENT
AREA COBIT ITIL ISO27001
Mapping IT
Mapping IT
Information Security
Function Service Level
Process Framework
Management
Area 4 Process and 9 Process 10 Domain
34 Domain
Issuer ISACA OGC ISO Board
Implementation
Information Manage Service Compliance to security
System Audit Level standard
Accounting
IT Consulting firm,
Firm, IT IT Consulting
Consultant Security Firm,
Consulting firm
Network Consultant
Firm
However, among these three, ISO 27k standards that include standards like ISO 27001, ISO
27005 is most popular and widely used in the industry for risk management and risk
assessment. ISO 27001 and ISO 27005 provides various advantages such as:
AREA COBIT ITIL ISO27001
Mapping IT
Mapping IT
Information Security
Function Service Level
Process Framework
Management
Area 4 Process and 9 Process 10 Domain
34 Domain
Issuer ISACA OGC ISO Board
Implementation
Information Manage Service Compliance to security
System Audit Level standard
Accounting
IT Consulting firm,
Firm, IT IT Consulting
Consultant Security Firm,
Consulting firm
Network Consultant
Firm
However, among these three, ISO 27k standards that include standards like ISO 27001, ISO
27005 is most popular and widely used in the industry for risk management and risk
assessment. ISO 27001 and ISO 27005 provides various advantages such as:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INFORMATION SECURITY MANAGEMENT
It is only international security standards that provide an opportunity for information
auditing
It defines various requirements that are important for an information security
management system (ISMS). An ISMS consists of policies, procedures, processes,
and systems that are essential to managing information risks, such as cyber-crimes,
hacks, data hacks, and theft.
It provides assurance that if an organization has obtained ISO 27001 certifications, it
has integrated best procedures with its information security policy and strategy.
ISO standards provide assistance to organizations in avoiding penalties that are
associated with the data breach
It eliminates the need for frequent auditing
Provide compliance with business, legal, contractual and regulatory requirements
2. System parameters, table.
STAFF PC Windows 8, Intel i3, 8 GB RAM
Customer PC Windows 8, Intel i5, 8 GB RAM
Web servers CentOS 6.8 Enterprise Linux
x86 (Centos.org, 2019)
16 Core - AMD Processor
6376
16 GB RAM
RAID 1
SSD caching
It is only international security standards that provide an opportunity for information
auditing
It defines various requirements that are important for an information security
management system (ISMS). An ISMS consists of policies, procedures, processes,
and systems that are essential to managing information risks, such as cyber-crimes,
hacks, data hacks, and theft.
It provides assurance that if an organization has obtained ISO 27001 certifications, it
has integrated best procedures with its information security policy and strategy.
ISO standards provide assistance to organizations in avoiding penalties that are
associated with the data breach
It eliminates the need for frequent auditing
Provide compliance with business, legal, contractual and regulatory requirements
2. System parameters, table.
STAFF PC Windows 8, Intel i3, 8 GB RAM
Customer PC Windows 8, Intel i5, 8 GB RAM
Web servers CentOS 6.8 Enterprise Linux
x86 (Centos.org, 2019)
16 Core - AMD Processor
6376
16 GB RAM
RAID 1
SSD caching
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
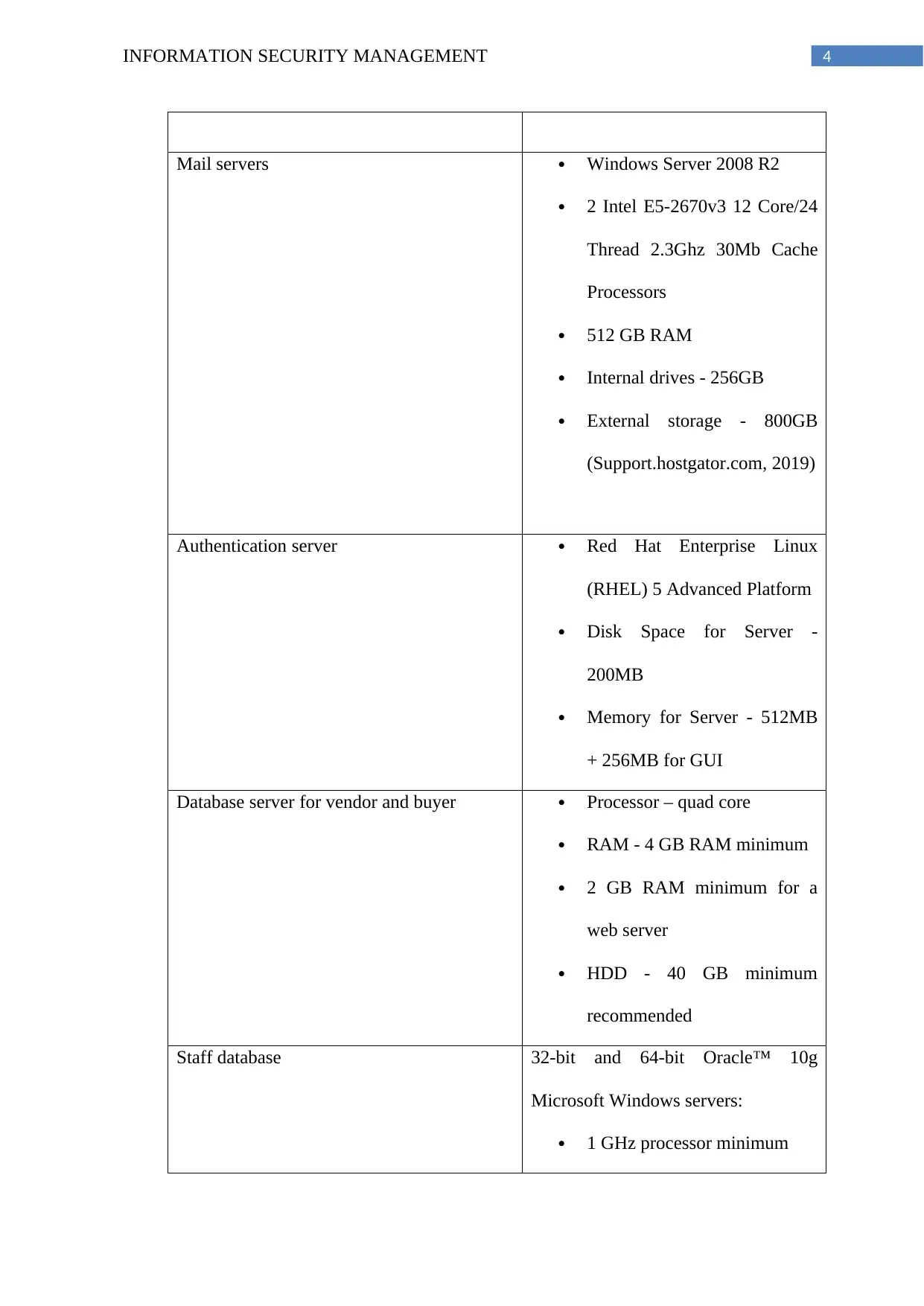
4INFORMATION SECURITY MANAGEMENT
Mail servers Windows Server 2008 R2
2 Intel E5-2670v3 12 Core/24
Thread 2.3Ghz 30Mb Cache
Processors
512 GB RAM
Internal drives - 256GB
External storage - 800GB
(Support.hostgator.com, 2019)
Authentication server Red Hat Enterprise Linux
(RHEL) 5 Advanced Platform
Disk Space for Server -
200MB
Memory for Server - 512MB
+ 256MB for GUI
Database server for vendor and buyer Processor – quad core
RAM - 4 GB RAM minimum
2 GB RAM minimum for a
web server
HDD - 40 GB minimum
recommended
Staff database 32-bit and 64-bit Oracle™ 10g
Microsoft Windows servers:
1 GHz processor minimum
Mail servers Windows Server 2008 R2
2 Intel E5-2670v3 12 Core/24
Thread 2.3Ghz 30Mb Cache
Processors
512 GB RAM
Internal drives - 256GB
External storage - 800GB
(Support.hostgator.com, 2019)
Authentication server Red Hat Enterprise Linux
(RHEL) 5 Advanced Platform
Disk Space for Server -
200MB
Memory for Server - 512MB
+ 256MB for GUI
Database server for vendor and buyer Processor – quad core
RAM - 4 GB RAM minimum
2 GB RAM minimum for a
web server
HDD - 40 GB minimum
recommended
Staff database 32-bit and 64-bit Oracle™ 10g
Microsoft Windows servers:
1 GHz processor minimum

5INFORMATION SECURITY MANAGEMENT
Minimum of 2 GB RAM (8
GB or better is recommended)
free disk space – 100 GB
minimum
Switch The Cisco SGE2000 24-Port Gigabit
Switch (Cisco.com, 2019):
Ports:
● 24 RJ-45 connectors for
10BASE-T/100BASE-TX/100
0BASE-T with 4 shared
Gigabit SFP slots
● Console port
● Auto medium dependent
interface (MDI) and MDI
crossover (MDI-X)
● Auto-negotiate/manual
setting
● RPS port for connecting to
a redundant power supply unit
VLAN:
● Port-based and 802.1Q tag-
based VLANs
● Protocol-based VLAN
● Management VLAN
Minimum of 2 GB RAM (8
GB or better is recommended)
free disk space – 100 GB
minimum
Switch The Cisco SGE2000 24-Port Gigabit
Switch (Cisco.com, 2019):
Ports:
● 24 RJ-45 connectors for
10BASE-T/100BASE-TX/100
0BASE-T with 4 shared
Gigabit SFP slots
● Console port
● Auto medium dependent
interface (MDI) and MDI
crossover (MDI-X)
● Auto-negotiate/manual
setting
● RPS port for connecting to
a redundant power supply unit
VLAN:
● Port-based and 802.1Q tag-
based VLANs
● Protocol-based VLAN
● Management VLAN
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6INFORMATION SECURITY MANAGEMENT
● Private VLAN Edge (PVE)
● GVRP
Web user interface:
HTTP/HTTPS
SNMP:
SNMP versions 1, 2c, and
3 with support for traps
RMON:
Embedded RMON
software agent
Firmware upgrade
Web browser upgrade
(HTTP) and Trivial File
Transfer Protocol (TFTP)
Dual images for resilient
firmware upgrades
Firewall Hardware Specifications PA-3260
Interfaces supported
4 (12) 10/100/1000, (8) 1G/10G
● Private VLAN Edge (PVE)
● GVRP
Web user interface:
HTTP/HTTPS
SNMP:
SNMP versions 1, 2c, and
3 with support for traps
RMON:
Embedded RMON
software agent
Firmware upgrade
Web browser upgrade
(HTTP) and Trivial File
Transfer Protocol (TFTP)
Dual images for resilient
firmware upgrades
Firewall Hardware Specifications PA-3260
Interfaces supported
4 (12) 10/100/1000, (8) 1G/10G
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INFORMATION SECURITY MANAGEMENT
SFP/SFP+, (4) 40G QSFP+
Management I/O
(1) 10/100/1000 out-of-band
management port, (2)
10/100/1000 high
availability, (1) 10G SFP+
high availability, (1) RJ-45
console port, (1) Micro
USB
Size:
2U, 19” standard rack
(3.5” H x 20.53” D x
17.34” W)
Power supply
650 W AC or DC
(180/240) Redundant
power supply Yes Disk
drives 240 GB SSD
Hot-swappable fans
SFP/SFP+, (4) 40G QSFP+
Management I/O
(1) 10/100/1000 out-of-band
management port, (2)
10/100/1000 high
availability, (1) 10G SFP+
high availability, (1) RJ-45
console port, (1) Micro
USB
Size:
2U, 19” standard rack
(3.5” H x 20.53” D x
17.34” W)
Power supply
650 W AC or DC
(180/240) Redundant
power supply Yes Disk
drives 240 GB SSD
Hot-swappable fans
8INFORMATION SECURITY MANAGEMENT
Yes
3. Risk assessment process
a. Asset classification (primary and supporting) + Asset ID
Primary assets are those that should be incorporate first and once these assets are
incorporated into the system, then only other assets are possible to be
implemented in the system. Such assets are known as secondary assets. Based on
this description, the assets have been classified into primary and secondary assets.
The reason for the same has been defined as well along with the classification.
Assets Assets type Description
STAFF PC Primary It does not require
support for another
resource incorporated
into the system. Rather
Individual
visitors/customers can
browse the website of
CONVXYZ and
register/login with their
PCs via the Internet.
Web servers Secondary Web servers provide
webs pages through
HTTP to the clients of
Yes
3. Risk assessment process
a. Asset classification (primary and supporting) + Asset ID
Primary assets are those that should be incorporate first and once these assets are
incorporated into the system, then only other assets are possible to be
implemented in the system. Such assets are known as secondary assets. Based on
this description, the assets have been classified into primary and secondary assets.
The reason for the same has been defined as well along with the classification.
Assets Assets type Description
STAFF PC Primary It does not require
support for another
resource incorporated
into the system. Rather
Individual
visitors/customers can
browse the website of
CONVXYZ and
register/login with their
PCs via the Internet.
Web servers Secondary Web servers provide
webs pages through
HTTP to the clients of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9INFORMATION SECURITY MANAGEMENT
CONVXYZ once
request for the same is
made. Now it is not
possible to set up a
webs server if necessary
hardware support as
specified in the system
specifications not
incorporated into the
system. Along with that
necessary network,
support is also
necessary to complete
the setup. Hence, it is
classified as a
secondary asset in this
context.
Mail servers Secondary The mail server enables
staff to send and receive
emails from the
customers and other
members of staff. Still,
it is not possible to
execute this
functionality without
CONVXYZ once
request for the same is
made. Now it is not
possible to set up a
webs server if necessary
hardware support as
specified in the system
specifications not
incorporated into the
system. Along with that
necessary network,
support is also
necessary to complete
the setup. Hence, it is
classified as a
secondary asset in this
context.
Mail servers Secondary The mail server enables
staff to send and receive
emails from the
customers and other
members of staff. Still,
it is not possible to
execute this
functionality without
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
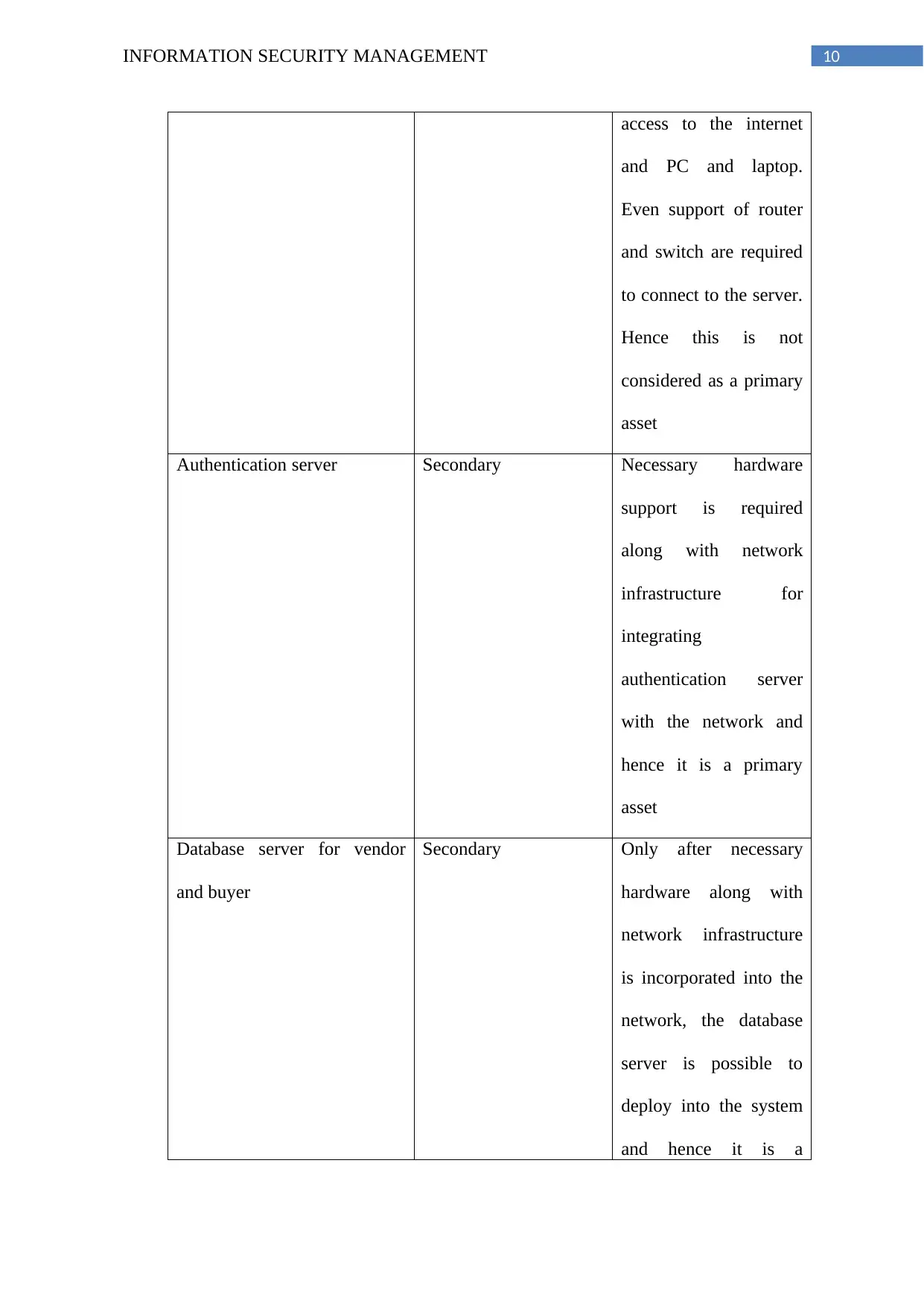
10INFORMATION SECURITY MANAGEMENT
access to the internet
and PC and laptop.
Even support of router
and switch are required
to connect to the server.
Hence this is not
considered as a primary
asset
Authentication server Secondary Necessary hardware
support is required
along with network
infrastructure for
integrating
authentication server
with the network and
hence it is a primary
asset
Database server for vendor
and buyer
Secondary Only after necessary
hardware along with
network infrastructure
is incorporated into the
network, the database
server is possible to
deploy into the system
and hence it is a
access to the internet
and PC and laptop.
Even support of router
and switch are required
to connect to the server.
Hence this is not
considered as a primary
asset
Authentication server Secondary Necessary hardware
support is required
along with network
infrastructure for
integrating
authentication server
with the network and
hence it is a primary
asset
Database server for vendor
and buyer
Secondary Only after necessary
hardware along with
network infrastructure
is incorporated into the
network, the database
server is possible to
deploy into the system
and hence it is a
11INFORMATION SECURITY MANAGEMENT
secondary asset
Switch Primary It is necessary to
incorporate network
switches so that it is
possible to connect
computers and other
devices with the local
wired network. Hence it
is a primary resource
Firewall Primary It provides a secure
connection to the
internet and hence it is
required first before a
secure and reliable
internet connection
ensured. Hence it is a
primary asset in this
network
Router Primary It is required to
incorporate into the
network for connecting
all of the devices
including pc and laptop
to the network of
CONVXYZ or
secondary asset
Switch Primary It is necessary to
incorporate network
switches so that it is
possible to connect
computers and other
devices with the local
wired network. Hence it
is a primary resource
Firewall Primary It provides a secure
connection to the
internet and hence it is
required first before a
secure and reliable
internet connection
ensured. Hence it is a
primary asset in this
network
Router Primary It is required to
incorporate into the
network for connecting
all of the devices
including pc and laptop
to the network of
CONVXYZ or
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 27
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





