Risk Assessment and Cybersecurity Management Report: AML, CMP73001
VerifiedAdded on 2022/09/18
|17
|2393
|34
Report
AI Summary
This report presents a comprehensive cybersecurity management analysis for Advanced Medicos Limited (AML), focusing on risk assessment and mitigation strategies. It begins with an overview of AML's information security challenges, including the protection of customer data and financial transactions. The report identifies and manages information assets, encompassing physical, software, service, people, information, security, network, computer, removable media, and infrastructure assets. It includes a weighted factor analysis to prioritize asset protection. Furthermore, the report addresses vulnerability and risk management, outlining enterprise risk management steps, identifying vulnerabilities and threats, and proposing a detailed risk management plan. This plan covers threat identification, risk assessment (likelihood, impact, outcome), and recommended control measures, including detective, corrective, preventive, and administrative controls. The report also provides a risk assessment table summarizing observations, existing controls, and recommended actions. Overall, the report provides a strategic framework for AML to enhance its cybersecurity posture and protect its critical assets.

Running head: CYBER SECURITY MANAGEMENT
Cyber Security Management
Name of the Student:
Name of the University:
Cyber Security Management
Name of the Student:
Name of the University:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CYBER SECURITY MANAGEMENT
Table of Contents
Background of the study on information security of Advanced Medicos Limited....................2
Task 1: Identify and manage asset.............................................................................................2
1.1 Information asset.........................................................................................................2
1.2 Role of Information security governance in asset management..................................5
1.3 Five information security policies...............................................................................6
Task 2: Vulnerability management and risk management.........................................................6
2.1 Steps of enterprise risk management................................................................................6
2.2 Vulnerabilities in company assets and threats.................................................................7
2.3 Risk management strategy.............................................................................................10
2.4 Risk assessment table.....................................................................................................13
References................................................................................................................................15
Table of Contents
Background of the study on information security of Advanced Medicos Limited....................2
Task 1: Identify and manage asset.............................................................................................2
1.1 Information asset.........................................................................................................2
1.2 Role of Information security governance in asset management..................................5
1.3 Five information security policies...............................................................................6
Task 2: Vulnerability management and risk management.........................................................6
2.1 Steps of enterprise risk management................................................................................6
2.2 Vulnerabilities in company assets and threats.................................................................7
2.3 Risk management strategy.............................................................................................10
2.4 Risk assessment table.....................................................................................................13
References................................................................................................................................15
2CYBER SECURITY MANAGEMENT
Background of the study on information security of Advanced Medicos
Limited
The report is reflected on the risk calculation of Advanced Medicos Limited (AML),
as the company is facing issues regarding secrecy in addition to the security of customer
private information, details of the credit card along with safekeeping of expense transactions.
In order to identify possible issues and manage the risks, a cybersecurity consultant is being
hired to help in the security management as well as report emerging project risks from the
cyberthreats.
Task 1: Identify and manage asset
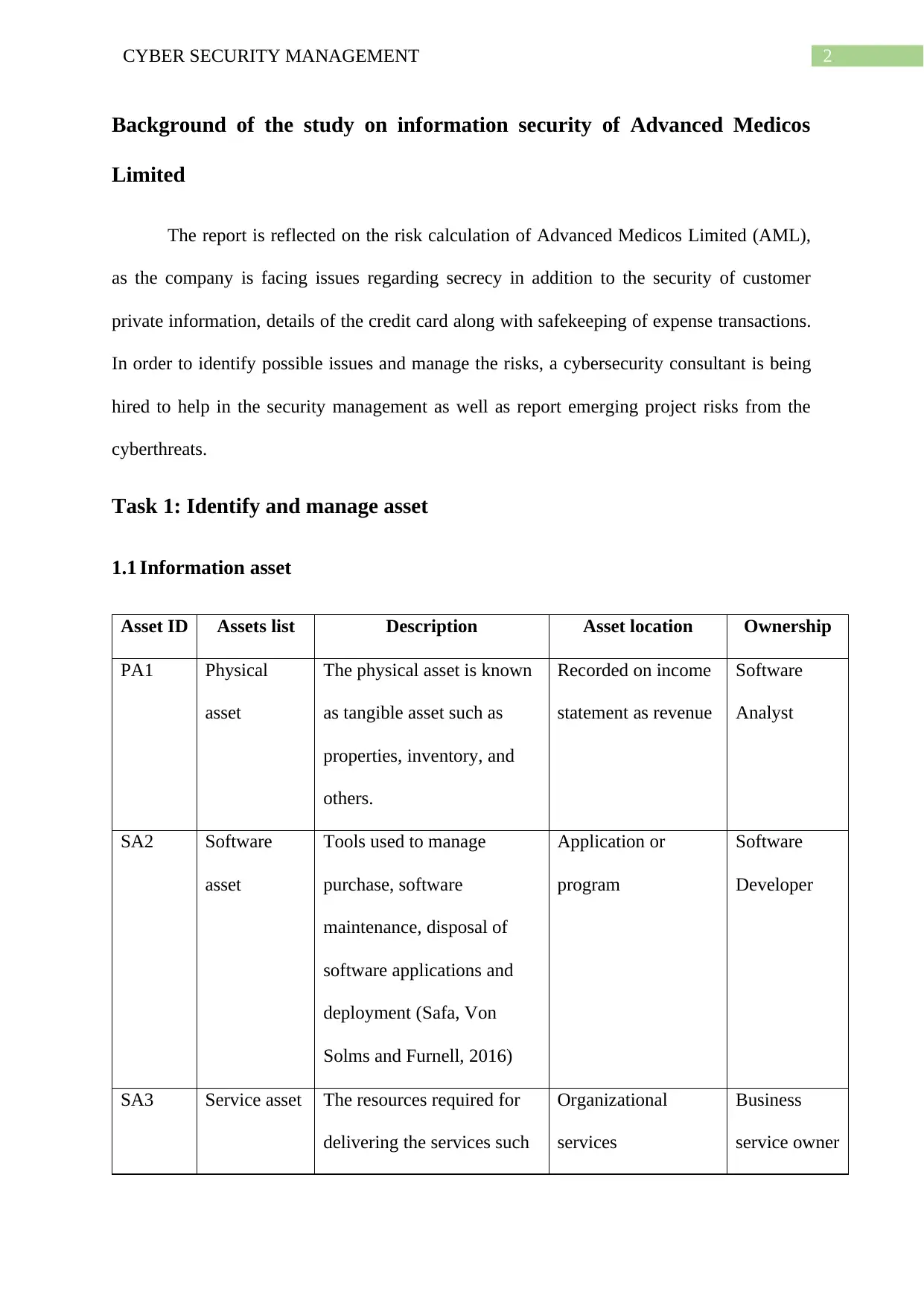
1.1 Information asset
Asset ID Assets list Description Asset location Ownership
PA1 Physical
asset
The physical asset is known
as tangible asset such as
properties, inventory, and
others.
Recorded on income
statement as revenue
Software
Analyst
SA2 Software
asset
Tools used to manage
purchase, software
maintenance, disposal of
software applications and
deployment (Safa, Von
Solms and Furnell, 2016)
Application or
program
Software
Developer
SA3 Service asset The resources required for
delivering the services such
Organizational
services
Business
service owner
Background of the study on information security of Advanced Medicos
Limited
The report is reflected on the risk calculation of Advanced Medicos Limited (AML),
as the company is facing issues regarding secrecy in addition to the security of customer
private information, details of the credit card along with safekeeping of expense transactions.
In order to identify possible issues and manage the risks, a cybersecurity consultant is being
hired to help in the security management as well as report emerging project risks from the
cyberthreats.
Task 1: Identify and manage asset
1.1 Information asset
Asset ID Assets list Description Asset location Ownership
PA1 Physical
asset
The physical asset is known
as tangible asset such as
properties, inventory, and
others.
Recorded on income
statement as revenue
Software
Analyst
SA2 Software
asset
Tools used to manage
purchase, software
maintenance, disposal of
software applications and
deployment (Safa, Von
Solms and Furnell, 2016)
Application or
program
Software
Developer
SA3 Service asset The resources required for
delivering the services such
Organizational
services
Business
service owner
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3CYBER SECURITY MANAGEMENT
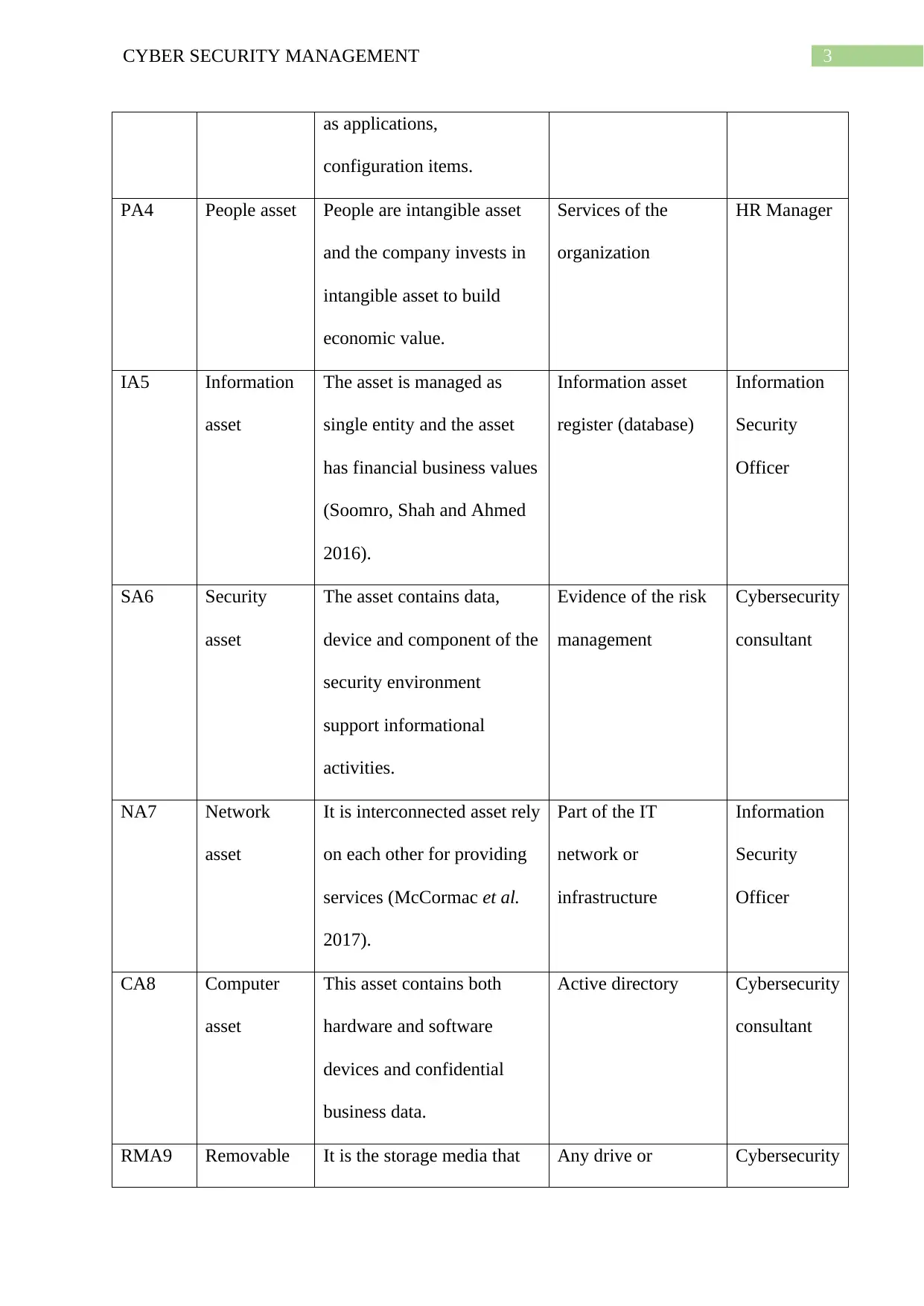
as applications,
configuration items.
PA4 People asset People are intangible asset
and the company invests in
intangible asset to build
economic value.
Services of the
organization
HR Manager
IA5 Information
asset
The asset is managed as
single entity and the asset
has financial business values
(Soomro, Shah and Ahmed
2016).
Information asset
register (database)
Information
Security
Officer
SA6 Security
asset
The asset contains data,
device and component of the
security environment
support informational
activities.
Evidence of the risk
management
Cybersecurity
consultant
NA7 Network
asset
It is interconnected asset rely
on each other for providing
services (McCormac et al.
2017).
Part of the IT
network or
infrastructure
Information
Security
Officer
CA8 Computer
asset
This asset contains both
hardware and software
devices and confidential
business data.
Active directory Cybersecurity
consultant
RMA9 Removable It is the storage media that Any drive or Cybersecurity
as applications,
configuration items.
PA4 People asset People are intangible asset
and the company invests in
intangible asset to build
economic value.
Services of the
organization
HR Manager
IA5 Information
asset
The asset is managed as
single entity and the asset
has financial business values
(Soomro, Shah and Ahmed
2016).
Information asset
register (database)
Information
Security
Officer
SA6 Security
asset
The asset contains data,
device and component of the
security environment
support informational
activities.
Evidence of the risk
management
Cybersecurity
consultant
NA7 Network
asset
It is interconnected asset rely
on each other for providing
services (McCormac et al.
2017).
Part of the IT
network or
infrastructure
Information
Security
Officer
CA8 Computer
asset
This asset contains both
hardware and software
devices and confidential
business data.
Active directory Cybersecurity
consultant
RMA9 Removable It is the storage media that Any drive or Cybersecurity
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4CYBER SECURITY MANAGEMENT
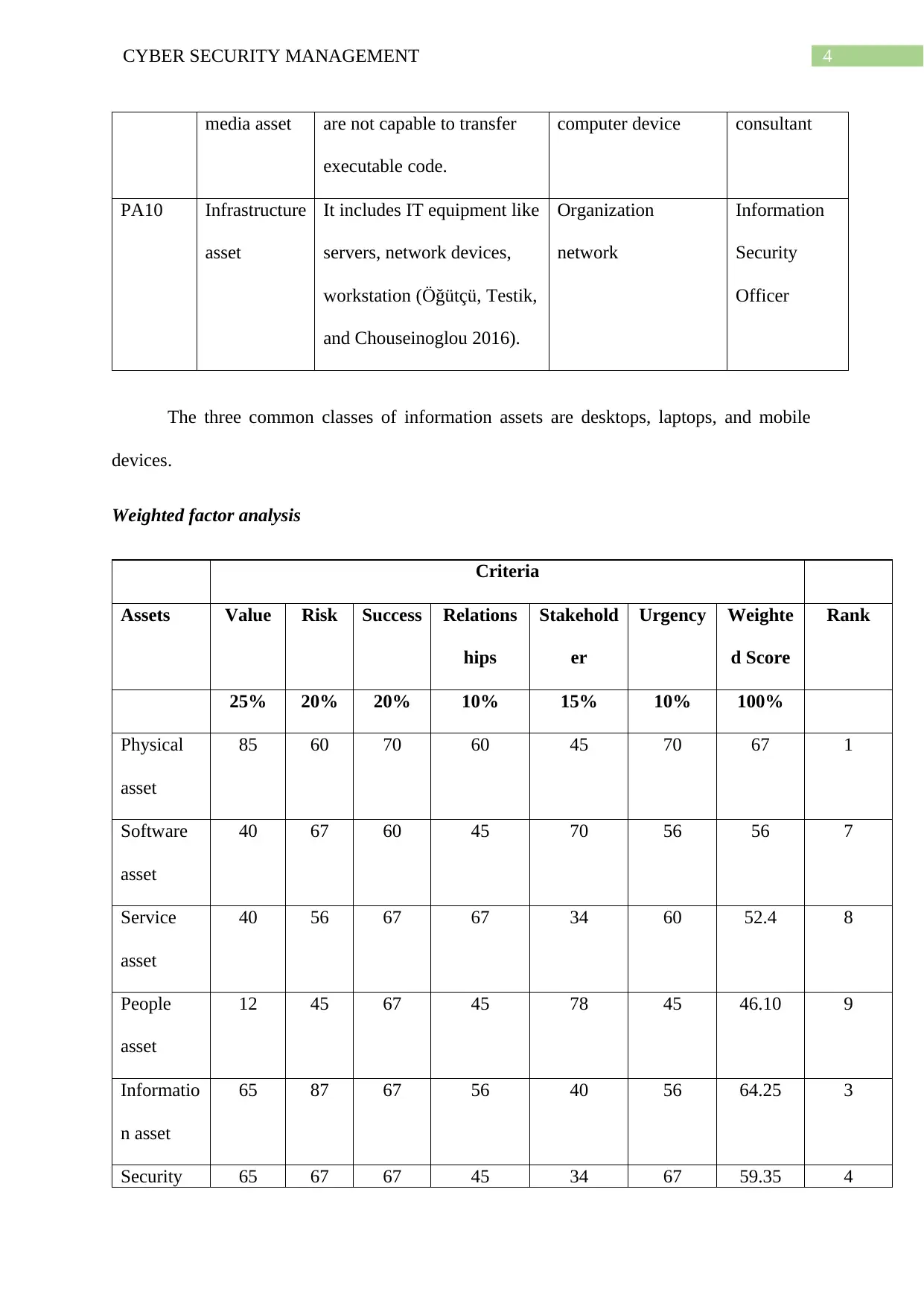
media asset are not capable to transfer
executable code.
computer device consultant
PA10 Infrastructure
asset
It includes IT equipment like
servers, network devices,
workstation (Öğütçü, Testik,
and Chouseinoglou 2016).
Organization
network
Information
Security
Officer
The three common classes of information assets are desktops, laptops, and mobile
devices.
Weighted factor analysis
Criteria
Assets Value Risk Success Relations
hips
Stakehold
er
Urgency Weighte
d Score
Rank
25% 20% 20% 10% 15% 10% 100%
Physical
asset
85 60 70 60 45 70 67 1
Software
asset
40 67 60 45 70 56 56 7
Service
asset
40 56 67 67 34 60 52.4 8
People
asset
12 45 67 45 78 45 46.10 9
Informatio
n asset
65 87 67 56 40 56 64.25 3
Security 65 67 67 45 34 67 59.35 4
media asset are not capable to transfer
executable code.
computer device consultant
PA10 Infrastructure
asset
It includes IT equipment like
servers, network devices,
workstation (Öğütçü, Testik,
and Chouseinoglou 2016).
Organization
network
Information
Security
Officer
The three common classes of information assets are desktops, laptops, and mobile
devices.
Weighted factor analysis
Criteria
Assets Value Risk Success Relations
hips
Stakehold
er
Urgency Weighte
d Score
Rank
25% 20% 20% 10% 15% 10% 100%
Physical
asset
85 60 70 60 45 70 67 1
Software
asset
40 67 60 45 70 56 56 7
Service
asset
40 56 67 67 34 60 52.4 8
People
asset
12 45 67 45 78 45 46.10 9
Informatio
n asset
65 87 67 56 40 56 64.25 3
Security 65 67 67 45 34 67 59.35 4
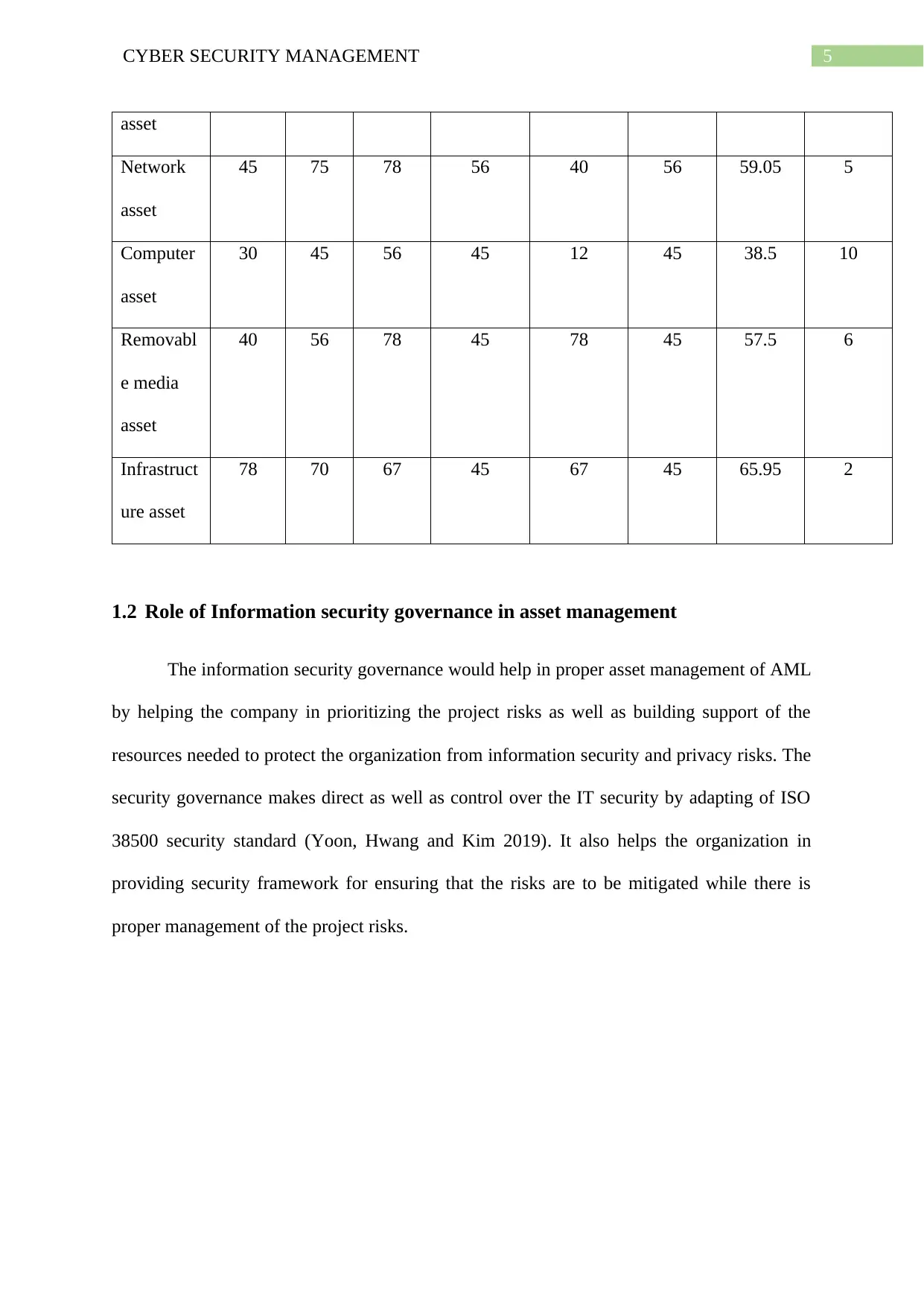
5CYBER SECURITY MANAGEMENT
asset
Network
asset
45 75 78 56 40 56 59.05 5
Computer
asset
30 45 56 45 12 45 38.5 10
Removabl
e media
asset
40 56 78 45 78 45 57.5 6
Infrastruct
ure asset
78 70 67 45 67 45 65.95 2
1.2 Role of Information security governance in asset management
The information security governance would help in proper asset management of AML
by helping the company in prioritizing the project risks as well as building support of the
resources needed to protect the organization from information security and privacy risks. The
security governance makes direct as well as control over the IT security by adapting of ISO
38500 security standard (Yoon, Hwang and Kim 2019). It also helps the organization in
providing security framework for ensuring that the risks are to be mitigated while there is
proper management of the project risks.
asset
Network
asset
45 75 78 56 40 56 59.05 5
Computer
asset
30 45 56 45 12 45 38.5 10
Removabl
e media
asset
40 56 78 45 78 45 57.5 6
Infrastruct
ure asset
78 70 67 45 67 45 65.95 2
1.2 Role of Information security governance in asset management
The information security governance would help in proper asset management of AML
by helping the company in prioritizing the project risks as well as building support of the
resources needed to protect the organization from information security and privacy risks. The
security governance makes direct as well as control over the IT security by adapting of ISO
38500 security standard (Yoon, Hwang and Kim 2019). It also helps the organization in
providing security framework for ensuring that the risks are to be mitigated while there is
proper management of the project risks.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CYBER SECURITY MANAGEMENT
1.3 Five information security policies
Following are list of the information security policies created for maintaining the
cybersecurity threats of AML as:
i. Enterprise information security policy: It provides details on security of the
organization. It helps to guide people and users to set direction as well as
scope of security efforts of the organization.
ii. Human resource information policy: The determination of this policy is to
give guidance to grow as well as implement the human resources system such
that the system is efficient and comply with the proper legislations (Cram,
Proudfoot and D’Arcy 2017).
iii. Information security policy: The resolution of this policy is to make sure that
the users as well as networks of IT structure in the organization should
maintain security of data stored in the digital form. Only authorized person
should able to access to data.
iv. Records and information management policy: It provides guidance regarding
preservation along with security of the records that should legal and
operational (Safa, Von Solms and Furnell 2016).
v. Information security incident management policy: It should ensure that the
incidents affect regular operations of business should be managed.
Task 2: Vulnerability management and risk management
2.1 Steps of enterprise risk management
Step 1- Establishing the enterprise risk structure: The organization is required to
communicate as well as manage the project risks regards to its position. Each one in the
1.3 Five information security policies
Following are list of the information security policies created for maintaining the
cybersecurity threats of AML as:
i. Enterprise information security policy: It provides details on security of the
organization. It helps to guide people and users to set direction as well as
scope of security efforts of the organization.
ii. Human resource information policy: The determination of this policy is to
give guidance to grow as well as implement the human resources system such
that the system is efficient and comply with the proper legislations (Cram,
Proudfoot and D’Arcy 2017).
iii. Information security policy: The resolution of this policy is to make sure that
the users as well as networks of IT structure in the organization should
maintain security of data stored in the digital form. Only authorized person
should able to access to data.
iv. Records and information management policy: It provides guidance regarding
preservation along with security of the records that should legal and
operational (Safa, Von Solms and Furnell 2016).
v. Information security incident management policy: It should ensure that the
incidents affect regular operations of business should be managed.
Task 2: Vulnerability management and risk management
2.1 Steps of enterprise risk management
Step 1- Establishing the enterprise risk structure: The organization is required to
communicate as well as manage the project risks regards to its position. Each one in the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7CYBER SECURITY MANAGEMENT
organization should follow policies to manage possible organizational risks (Hubbard
2020).
Step 2: Assign responsibility: After establishment of enterprise risk structure, it is
required to assign and take ownership of the risks to mitigate and manage it.
Step 3: Producing enterprise risk map: The causes of organizational risks, mitigation
strategies are come in the organization and possible actions are to be identified to manage
it (Aven 2016). The risks are managed efficiently, then it is required to map risks to
various parts of the risk management structure.
Step 4: Decision making: The main aspect of managing the enterprise risk
management is performing actions for managing risks. Decision making process is used
to establish risks against business objectives and set of baseline (Almeida, Hankins and
Williams 2017).
2.2 Vulnerabilities in company assets and threats
Risk
ID
Threat
source
Vulnerability Vulnerability
description
Affected
assets
Existing
controls
Risk
ranking
1 Hacker Password
strength
There is
unclear
allocation of
the information
security
responsibilities
(Giannakis and
Papadopoulos
Information,
infrastructure,
network,
people
The network
password
should be
unique so that
no one can
guess.
Critical
organization should follow policies to manage possible organizational risks (Hubbard
2020).
Step 2: Assign responsibility: After establishment of enterprise risk structure, it is
required to assign and take ownership of the risks to mitigate and manage it.
Step 3: Producing enterprise risk map: The causes of organizational risks, mitigation
strategies are come in the organization and possible actions are to be identified to manage
it (Aven 2016). The risks are managed efficiently, then it is required to map risks to
various parts of the risk management structure.
Step 4: Decision making: The main aspect of managing the enterprise risk
management is performing actions for managing risks. Decision making process is used
to establish risks against business objectives and set of baseline (Almeida, Hankins and
Williams 2017).
2.2 Vulnerabilities in company assets and threats
Risk
ID
Threat
source
Vulnerability Vulnerability
description
Affected
assets
Existing
controls
Risk
ranking
1 Hacker Password
strength
There is
unclear
allocation of
the information
security
responsibilities
(Giannakis and
Papadopoulos
Information,
infrastructure,
network,
people
The network
password
should be
unique so that
no one can
guess.
Critical
8CYBER SECURITY MANAGEMENT
2016).
2 Physical
database
usage
Unnecessary
services
The
organization is
designed with
low level of
security as
physical
database is
used for storing
data (Sweeting
2017).
Information,
hardware,
physical
Strict
guidelines to
restrict the
unauthorized
access to
customer’s
data.
Medium
3 Security
configuration
issues
Disaster
recovery
There is no
such security
configuration
to routers in
addition
switches.
Infrastructure
, information,
physical,
people
None Medium
4 Lack of
security
measures in
server room
Accessible by
all staffs
The servers
located in the
server room is
accessible by
the staffs
(Wiengarten et
al. 2017).
Software,
service and
information
Training to
the unskilled
employees
High
5 Computer Integrity The backup’s Infrastructure None Medium
2016).
2 Physical
database
usage
Unnecessary
services
The
organization is
designed with
low level of
security as
physical
database is
used for storing
data (Sweeting
2017).
Information,
hardware,
physical
Strict
guidelines to
restrict the
unauthorized
access to
customer’s
data.
Medium
3 Security
configuration
issues
Disaster
recovery
There is no
such security
configuration
to routers in
addition
switches.
Infrastructure
, information,
physical,
people
None Medium
4 Lack of
security
measures in
server room
Accessible by
all staffs
The servers
located in the
server room is
accessible by
the staffs
(Wiengarten et
al. 2017).
Software,
service and
information
Training to
the unskilled
employees
High
5 Computer Integrity The backup’s Infrastructure None Medium
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9CYBER SECURITY MANAGEMENT
criminal checks files are stored
in single
computer lead
to cause stolen
of the data.
, information,
physical,
people
6 Poorly
trained staffs
Lack of
documentation
Lack of
technical skills
on managing
information
security
breaches (Cole,
Giné and
Vickery 2017)
Information,
infrastructure,
network,
people
Training to
the unskilled
employees
Low
criminal checks files are stored
in single
computer lead
to cause stolen
of the data.
, information,
physical,
people
6 Poorly
trained staffs
Lack of
documentation
Lack of
technical skills
on managing
information
security
breaches (Cole,
Giné and
Vickery 2017)
Information,
infrastructure,
network,
people
Training to
the unskilled
employees
Low
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10CYBER SECURITY MANAGEMENT
2.3 Risk management strategy
Risk management plan – Information Security Risk
Company name: Advanced Medicos Limited (AML) Completed by: Student name
Work area: Cybersecurity management Date completed: Date
Threat identification
Unauthorized access to the network
Risk assessment
What harm could the
threat cause? The threat provides impact on the customer satisfaction as customer’s data are being stolen.
What is the likelihood
of this happening There are high chances of the information security risks.
Existing control
measure The network password should be unique so that no one can guess.
Consequence High
Likelihood High
Outcome Critical
2.3 Risk management strategy
Risk management plan – Information Security Risk
Company name: Advanced Medicos Limited (AML) Completed by: Student name
Work area: Cybersecurity management Date completed: Date
Threat identification
Unauthorized access to the network
Risk assessment
What harm could the
threat cause? The threat provides impact on the customer satisfaction as customer’s data are being stolen.
What is the likelihood
of this happening There are high chances of the information security risks.
Existing control
measure The network password should be unique so that no one can guess.
Consequence High
Likelihood High
Outcome Critical
11CYBER SECURITY MANAGEMENT
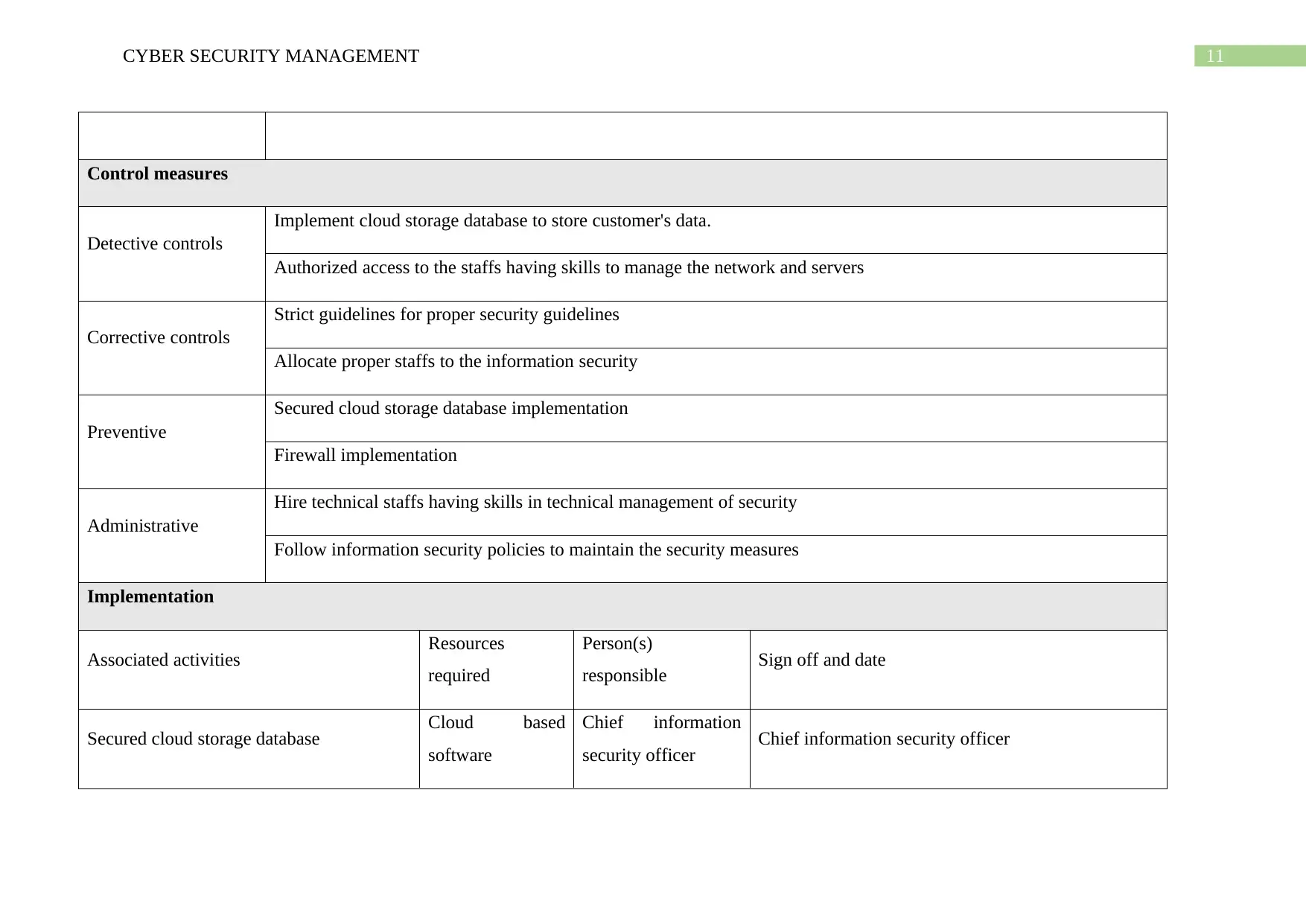
Control measures
Detective controls
Implement cloud storage database to store customer's data.
Authorized access to the staffs having skills to manage the network and servers
Corrective controls
Strict guidelines for proper security guidelines
Allocate proper staffs to the information security
Preventive
Secured cloud storage database implementation
Firewall implementation
Administrative
Hire technical staffs having skills in technical management of security
Follow information security policies to maintain the security measures
Implementation
Associated activities Resources
required
Person(s)
responsible Sign off and date
Secured cloud storage database Cloud based
software
Chief information
security officer Chief information security officer
Control measures
Detective controls
Implement cloud storage database to store customer's data.
Authorized access to the staffs having skills to manage the network and servers
Corrective controls
Strict guidelines for proper security guidelines
Allocate proper staffs to the information security
Preventive
Secured cloud storage database implementation
Firewall implementation
Administrative
Hire technical staffs having skills in technical management of security
Follow information security policies to maintain the security measures
Implementation
Associated activities Resources
required
Person(s)
responsible Sign off and date
Secured cloud storage database Cloud based
software
Chief information
security officer Chief information security officer
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





