Data Integrity Policy: Risk Assessment for Regional Gardens Ltd
VerifiedAdded on 2022/08/24
|10
|1675
|9
Report
AI Summary
This report presents a comprehensive risk assessment for Regional Gardens Ltd., examining various internal and external threats. The student, acting as a Chief Information Officer, identifies vulnerabilities in the company's IT infrastructure, including outdated systems, unsecured networks, and lack of data backup. The report outlines the need for a data integrity policy and provides detailed recommendations, including updating IT assets, implementing access control policies, improving network security with IDS and IPS systems, establishing data backup and recovery systems, and enforcing strong password policies. The report also references relevant government regulations for data privacy and emphasizes the importance of a risk register for managing and mitigating identified risks. The conclusion highlights the necessity of a robust risk framework, such as ISO 31000, to ensure a high level of security and data integrity for the company. The report includes a risk register that assesses risk types, reasons, impacts, controls, residual risks, and priorities. It provides references to various sources on risk management, IT security, and data protection.

1/18/2020
RISK ASSESSMENT 0
Risk Assessment
Report
Student name
RISK ASSESSMENT 0
Risk Assessment
Report
Student name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RISK ASSESSMENT
Brief Overview
Many companies have used risk assessment for analysing their threats and risks from various
internal and external issues. In addition, Risk Register (RR) has used for managing all the risks of
various processes using proper controls and mitigation strategies. This report will identify all the
risks of Regional Gardens Ltd. It will analyse different risks in their functions based on the case
study. Thus, risk analysis is necessary for managing various issues in a firm. This report will
provide risk factors of the company and its impact on the various things. It is necessary to
improve the outcomes of a firm. This report will analyse the case study to find risks for the
company.
Policy Purpose and Rationale
There is various internal and external risk in a company, which can be managed using avoidance
and preventions of risks and threats. Thus, a company can avoid various issues and challenges,
which has raised because of technical issues. Thus, basic functions can reduce the risks of a
company as well. Thus, there are many things to reduce from a firm, which can damage a firm
financially and reputationally (Sotnikov, 2018).
A Chief Information Officer (CIO) can provide suggestions for improving the internal structure of
a firm. There are many responsibilities if a CIO. There are many ways to analyse different
resources of a company, which is the best way to reduce risk from a company. I will provide some
suggestions to the firm about an audit for all the IT assets. In addition, there are many risks of a
firm, which must know about the risks (Anthony (Tony) Cox Jr, 2008).
Source: (Svantesson & Clarke, 2010)
Brief Overview
Many companies have used risk assessment for analysing their threats and risks from various
internal and external issues. In addition, Risk Register (RR) has used for managing all the risks of
various processes using proper controls and mitigation strategies. This report will identify all the
risks of Regional Gardens Ltd. It will analyse different risks in their functions based on the case
study. Thus, risk analysis is necessary for managing various issues in a firm. This report will
provide risk factors of the company and its impact on the various things. It is necessary to
improve the outcomes of a firm. This report will analyse the case study to find risks for the
company.
Policy Purpose and Rationale
There is various internal and external risk in a company, which can be managed using avoidance
and preventions of risks and threats. Thus, a company can avoid various issues and challenges,
which has raised because of technical issues. Thus, basic functions can reduce the risks of a
company as well. Thus, there are many things to reduce from a firm, which can damage a firm
financially and reputationally (Sotnikov, 2018).
A Chief Information Officer (CIO) can provide suggestions for improving the internal structure of
a firm. There are many responsibilities if a CIO. There are many ways to analyse different
resources of a company, which is the best way to reduce risk from a company. I will provide some
suggestions to the firm about an audit for all the IT assets. In addition, there are many risks of a
firm, which must know about the risks (Anthony (Tony) Cox Jr, 2008).
Source: (Svantesson & Clarke, 2010)
RISK ASSESSMENT
The company provides various services that are related to gardens, such as consultancy services,
design, garden advice, and many more. In addition, the firm has used different types of hardware
and software to manage all those services, such as laptops, data centres, and personal computer
systems.
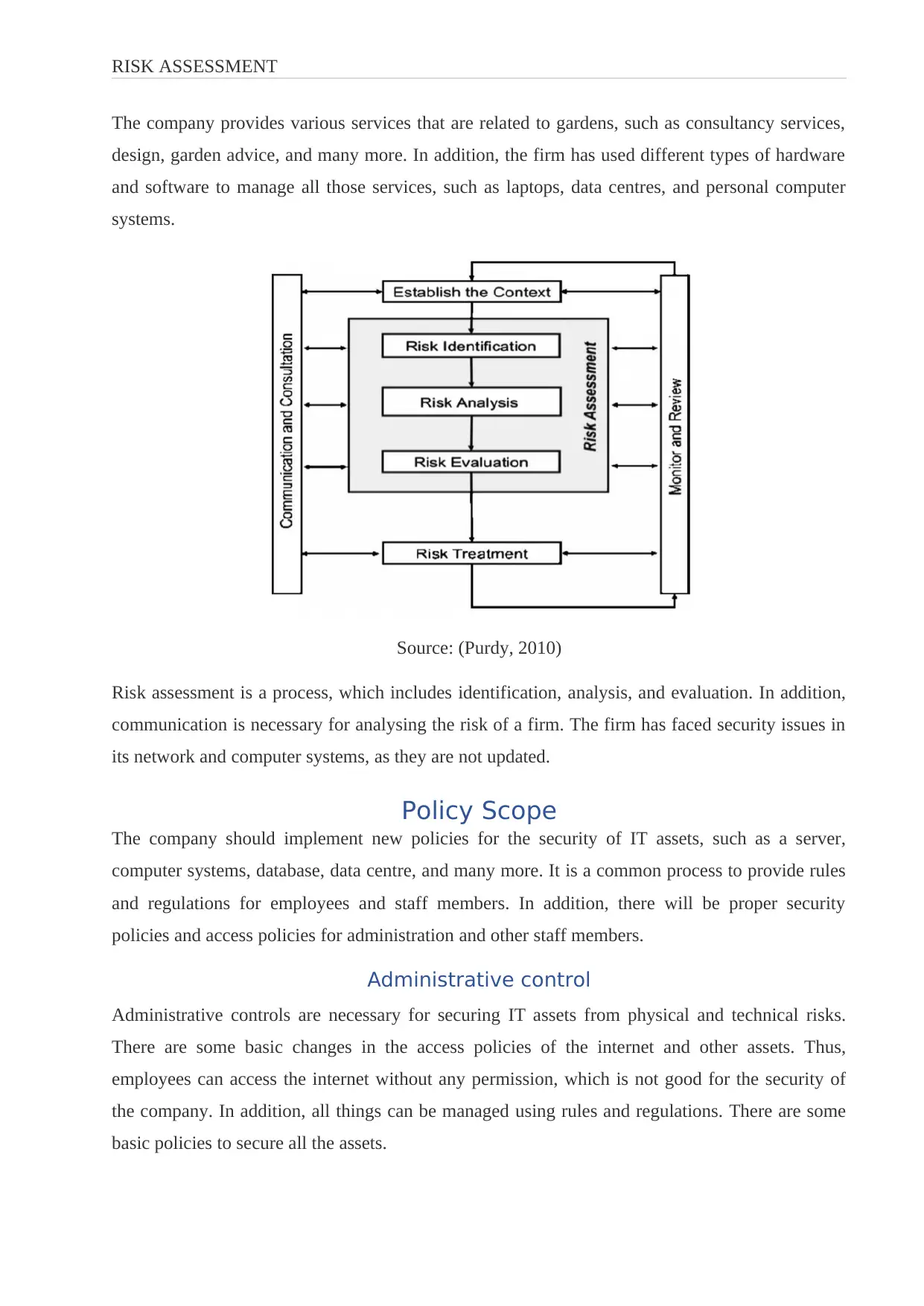
Source: (Purdy, 2010)
Risk assessment is a process, which includes identification, analysis, and evaluation. In addition,
communication is necessary for analysing the risk of a firm. The firm has faced security issues in
its network and computer systems, as they are not updated.
Policy Scope
The company should implement new policies for the security of IT assets, such as a server,
computer systems, database, data centre, and many more. It is a common process to provide rules
and regulations for employees and staff members. In addition, there will be proper security
policies and access policies for administration and other staff members.
Administrative control
Administrative controls are necessary for securing IT assets from physical and technical risks.
There are some basic changes in the access policies of the internet and other assets. Thus,
employees can access the internet without any permission, which is not good for the security of
the company. In addition, all things can be managed using rules and regulations. There are some
basic policies to secure all the assets.
The company provides various services that are related to gardens, such as consultancy services,
design, garden advice, and many more. In addition, the firm has used different types of hardware
and software to manage all those services, such as laptops, data centres, and personal computer
systems.
Source: (Purdy, 2010)
Risk assessment is a process, which includes identification, analysis, and evaluation. In addition,
communication is necessary for analysing the risk of a firm. The firm has faced security issues in
its network and computer systems, as they are not updated.
Policy Scope
The company should implement new policies for the security of IT assets, such as a server,
computer systems, database, data centre, and many more. It is a common process to provide rules
and regulations for employees and staff members. In addition, there will be proper security
policies and access policies for administration and other staff members.
Administrative control
Administrative controls are necessary for securing IT assets from physical and technical risks.
There are some basic changes in the access policies of the internet and other assets. Thus,
employees can access the internet without any permission, which is not good for the security of
the company. In addition, all things can be managed using rules and regulations. There are some
basic policies to secure all the assets.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
RISK ASSESSMENT
Mobile access risk
In addition, the company has faced issues because of mobile applications, which can make
different services of the firm, which are Web page data, Customer planning data, Strategic
planning data, Personnel data, Nursery supplies data, Nursery product data, and others. In
addition, there are some basic needs of security policies, which are necessary for securing all the
services and assets of the firm.
Roles and Responsibilities
The risk register can be used for mitigation of different risks of the firm, which can be occurred in
the firm because of vulnerabilities.
Risk type Reason of
Risk
Impact of risk Assessment Controls Residual
Risk
Priority
IT assets Outdated IT
assets
Reputational risk
and Financial
losses
Proper
updates of
IT assets
Use update
policies for all the
assets
Medium 3
Governance Administrat
ive controls
Access of data and
information
Identify
resources,
which have
open access
Apply access
policy for IT assets
High 4
Security Lack of
security
access
Data breaches and
cyber-attacks
Audit of all
the IT assets
and
framework
Improve security
levels using
firewalls and
monitoring
systems
Medium 3
Asset
Security
Lack of
backup
Issues and
challenges in
business continuity
Implement
backup and
recovery
systems
Design Disaster
Recovery Plan
High 2
Networks
Security
Free access
to network
and server
Data breach and
loss of confidential
data
IDS and IPS
systems for
security
Create network
security regulation
Medium 4
Mobile access risk
In addition, the company has faced issues because of mobile applications, which can make
different services of the firm, which are Web page data, Customer planning data, Strategic
planning data, Personnel data, Nursery supplies data, Nursery product data, and others. In
addition, there are some basic needs of security policies, which are necessary for securing all the
services and assets of the firm.
Roles and Responsibilities
The risk register can be used for mitigation of different risks of the firm, which can be occurred in
the firm because of vulnerabilities.
Risk type Reason of
Risk
Impact of risk Assessment Controls Residual
Risk
Priority
IT assets Outdated IT
assets
Reputational risk
and Financial
losses
Proper
updates of
IT assets
Use update
policies for all the
assets
Medium 3
Governance Administrat
ive controls
Access of data and
information
Identify
resources,
which have
open access
Apply access
policy for IT assets
High 4
Security Lack of
security
access
Data breaches and
cyber-attacks
Audit of all
the IT assets
and
framework
Improve security
levels using
firewalls and
monitoring
systems
Medium 3
Asset
Security
Lack of
backup
Issues and
challenges in
business continuity
Implement
backup and
recovery
systems
Design Disaster
Recovery Plan
High 2
Networks
Security
Free access
to network
and server
Data breach and
loss of confidential
data
IDS and IPS
systems for
security
Create network
security regulation
Medium 4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
RISK ASSESSMENT
Security of
external
devices
Mobile
access to
the system
Data redundancy The data
centre
should be
insecure
access
Implement BYOD
policy in the firm
Low 3
Personal
access
Security
Poor
passwords
Easily access to
credentials
Include
validations
and special
symbols in
the
password
Create and
implement a
password creation
system
Medium 3
There are many mitigation policies in most countries to secure data and information about the
company and its customers. The Australian government has developed mitigation strategies for all
the industries, which has collected data from their customers, which is confidential and sensitive
as well. Thus, the firm should know about the rules and regulations for collecting data from
customers.
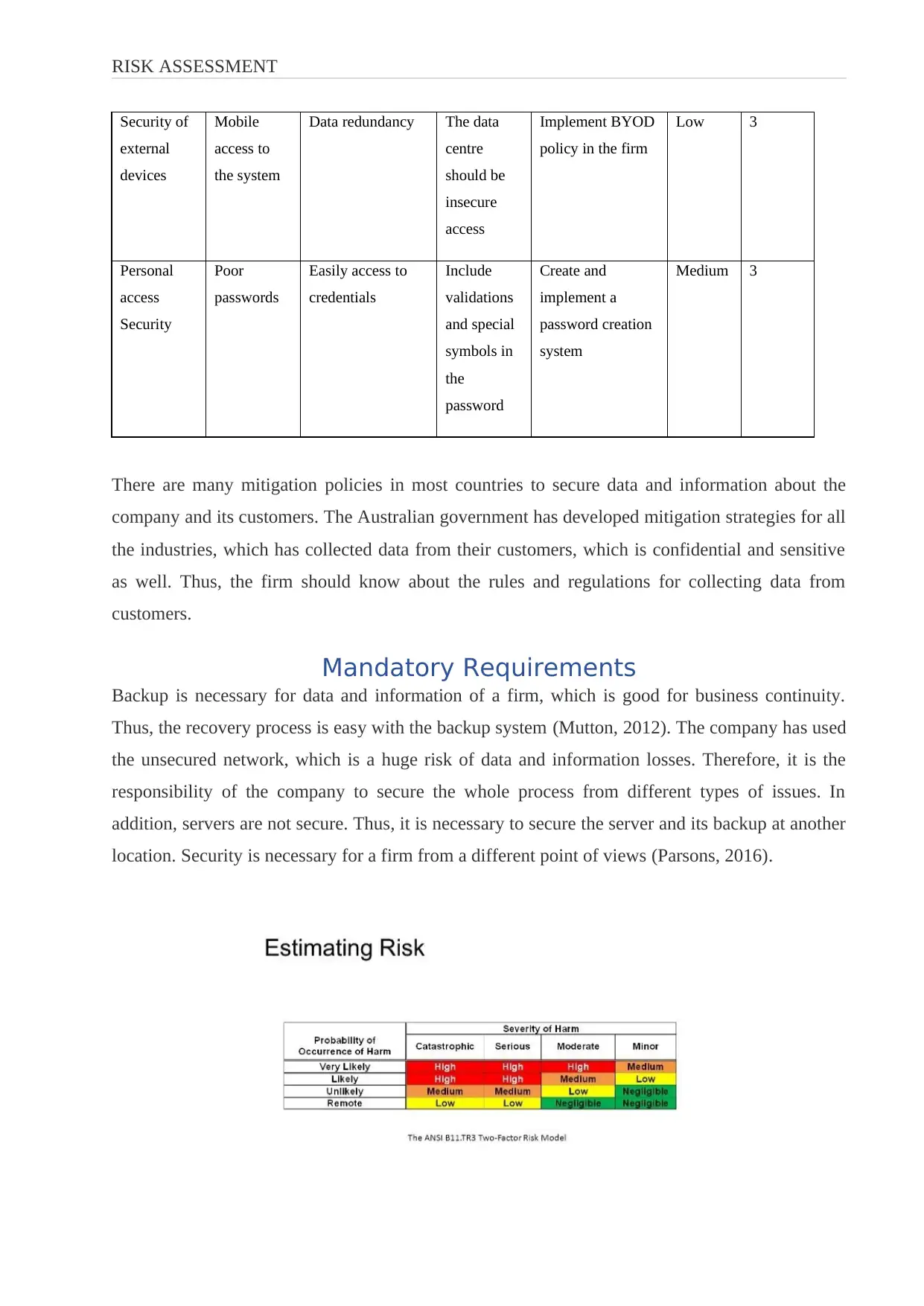
Mandatory Requirements
Backup is necessary for data and information of a firm, which is good for business continuity.
Thus, the recovery process is easy with the backup system (Mutton, 2012). The company has used
the unsecured network, which is a huge risk of data and information losses. Therefore, it is the
responsibility of the company to secure the whole process from different types of issues. In
addition, servers are not secure. Thus, it is necessary to secure the server and its backup at another
location. Security is necessary for a firm from a different point of views (Parsons, 2016).
Security of
external
devices
Mobile
access to
the system
Data redundancy The data
centre
should be
insecure
access
Implement BYOD
policy in the firm
Low 3
Personal
access
Security
Poor
passwords
Easily access to
credentials
Include
validations
and special
symbols in
the
password
Create and
implement a
password creation
system
Medium 3
There are many mitigation policies in most countries to secure data and information about the
company and its customers. The Australian government has developed mitigation strategies for all
the industries, which has collected data from their customers, which is confidential and sensitive
as well. Thus, the firm should know about the rules and regulations for collecting data from
customers.
Mandatory Requirements
Backup is necessary for data and information of a firm, which is good for business continuity.
Thus, the recovery process is easy with the backup system (Mutton, 2012). The company has used
the unsecured network, which is a huge risk of data and information losses. Therefore, it is the
responsibility of the company to secure the whole process from different types of issues. In
addition, servers are not secure. Thus, it is necessary to secure the server and its backup at another
location. Security is necessary for a firm from a different point of views (Parsons, 2016).
RISK ASSESSMENT
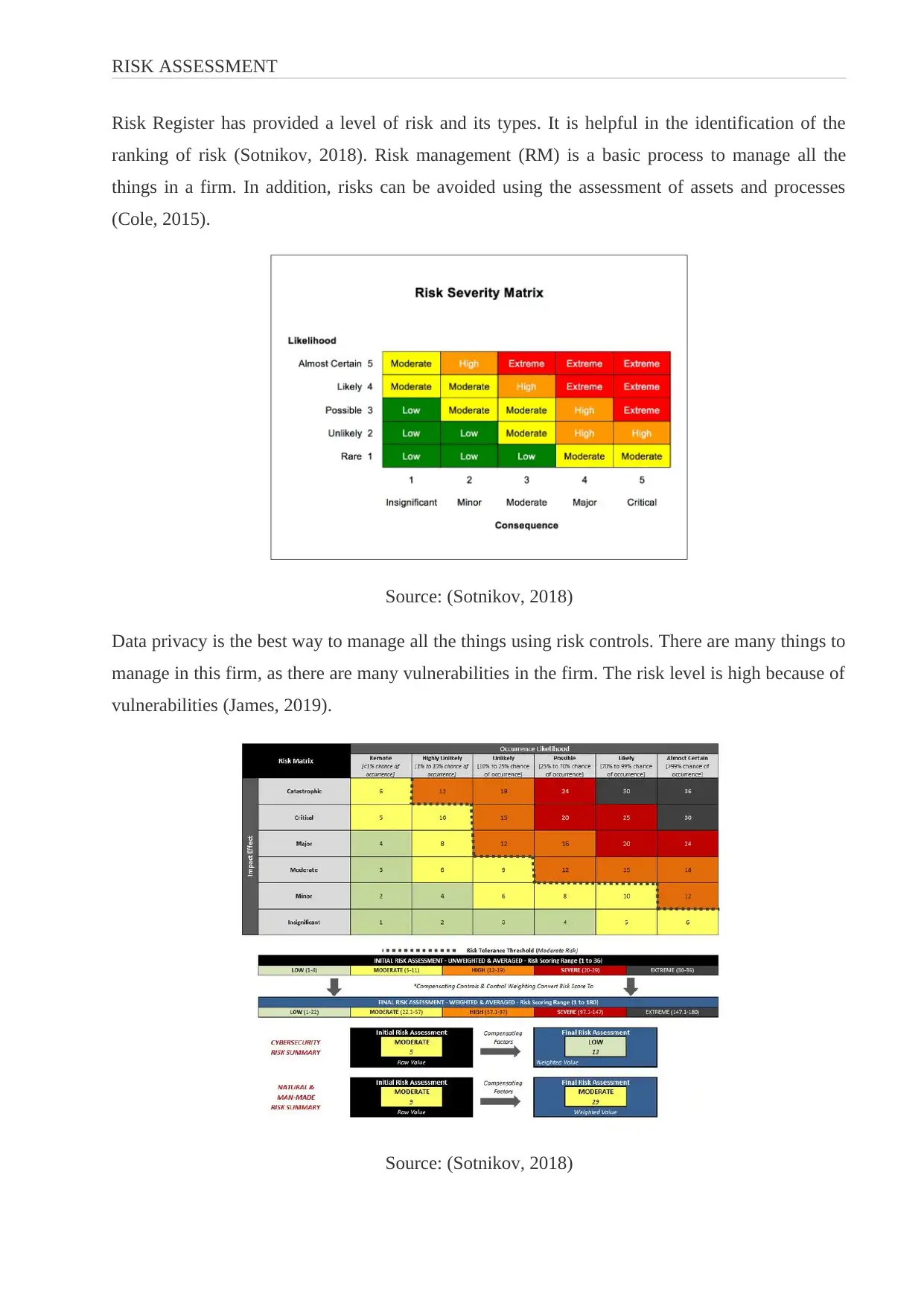
Risk Register has provided a level of risk and its types. It is helpful in the identification of the
ranking of risk (Sotnikov, 2018). Risk management (RM) is a basic process to manage all the
things in a firm. In addition, risks can be avoided using the assessment of assets and processes
(Cole, 2015).
Source: (Sotnikov, 2018)
Data privacy is the best way to manage all the things using risk controls. There are many things to
manage in this firm, as there are many vulnerabilities in the firm. The risk level is high because of
vulnerabilities (James, 2019).
Source: (Sotnikov, 2018)
Risk Register has provided a level of risk and its types. It is helpful in the identification of the
ranking of risk (Sotnikov, 2018). Risk management (RM) is a basic process to manage all the
things in a firm. In addition, risks can be avoided using the assessment of assets and processes
(Cole, 2015).
Source: (Sotnikov, 2018)
Data privacy is the best way to manage all the things using risk controls. There are many things to
manage in this firm, as there are many vulnerabilities in the firm. The risk level is high because of
vulnerabilities (James, 2019).
Source: (Sotnikov, 2018)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

RISK ASSESSMENT
IT management strategies can be used for the mitigation of different risks of the company
(Bridges, 2019).
Conclusion
It has concluded that risk assessment is necessary for the firm using a proper audit of all the IT
assets and the environment as well as culture. This report can be used for managing all the
resources of the firm with a high level of security. Besides, access control policies and network
security policy must implement in the firm to avoid huge risks in the future. Finally, the firm
should implement a risk framework, such as ISO 31000, which will provide a high level of
security.
IT management strategies can be used for the mitigation of different risks of the company
(Bridges, 2019).
Conclusion
It has concluded that risk assessment is necessary for the firm using a proper audit of all the IT
assets and the environment as well as culture. This report can be used for managing all the
resources of the firm with a high level of security. Besides, access control policies and network
security policy must implement in the firm to avoid huge risks in the future. Finally, the firm
should implement a risk framework, such as ISO 31000, which will provide a high level of
security.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RISK ASSESSMENT
References
Anthony (Tony) Cox Jr, L., 2008. What's wrong with risk matrices?. Risk Analysis: An
International Journal, 28(2), pp. 497-512.
Bridges, J., 2019. IT Risk Management Strategies and Best Practices. [Online]
Available at: https://www.projectmanager.com/training/it-risk-management-strategies
[Accessed 28 December 2019].
Cole, B., 2015. Risk management. [Online]
Available at: https://searchcompliance.techtarget.com/definition/risk-management
[Accessed 28 December 2019].
James, P., 2019. Information Security Risks That You Need to Careful With Vendors/3rd Parties.
[Online]
Available at: https://gbhackers.com/information-security-risks/
[Accessed 25 November 2019].
Mutton, J., 2012. Do I really need a risk register?. Keeping good companies, 64(8), p. 469.
Parsons, E., 2016. Risk Assessment: A Practical Guide to Assessing Operational Risk. [Online]
Available at: https://slideplayer.com/slide/10726147/
[Accessed 28 December 2019].
Purdy, G., 2010. ISO 31000:2009 – setting a new standard for risk management. [Online]
Available at: http://broadleaf.com.au/resource-material/iso-31000-2009-setting-a-new-standard-
for-risk-management/
[Accessed 25 November 2019].
Sotnikov, I., 2018. How to Create an Effective Information Security Risk Management Program.
[Online]
Available at: https://blog.netwrix.com/2018/08/02/how-to-create-an-effective-information-
security-risk-management-program/
[Accessed 28 December 2019].
Sotnikov, I., 2018. How to Perform IT Risk Assessment. [Online]
Available at: https://blog.netwrix.com/2018/01/16/how-to-perform-it-risk-assessment/
[Accessed 25 November 2019].
References
Anthony (Tony) Cox Jr, L., 2008. What's wrong with risk matrices?. Risk Analysis: An
International Journal, 28(2), pp. 497-512.
Bridges, J., 2019. IT Risk Management Strategies and Best Practices. [Online]
Available at: https://www.projectmanager.com/training/it-risk-management-strategies
[Accessed 28 December 2019].
Cole, B., 2015. Risk management. [Online]
Available at: https://searchcompliance.techtarget.com/definition/risk-management
[Accessed 28 December 2019].
James, P., 2019. Information Security Risks That You Need to Careful With Vendors/3rd Parties.
[Online]
Available at: https://gbhackers.com/information-security-risks/
[Accessed 25 November 2019].
Mutton, J., 2012. Do I really need a risk register?. Keeping good companies, 64(8), p. 469.
Parsons, E., 2016. Risk Assessment: A Practical Guide to Assessing Operational Risk. [Online]
Available at: https://slideplayer.com/slide/10726147/
[Accessed 28 December 2019].
Purdy, G., 2010. ISO 31000:2009 – setting a new standard for risk management. [Online]
Available at: http://broadleaf.com.au/resource-material/iso-31000-2009-setting-a-new-standard-
for-risk-management/
[Accessed 25 November 2019].
Sotnikov, I., 2018. How to Create an Effective Information Security Risk Management Program.
[Online]
Available at: https://blog.netwrix.com/2018/08/02/how-to-create-an-effective-information-
security-risk-management-program/
[Accessed 28 December 2019].
Sotnikov, I., 2018. How to Perform IT Risk Assessment. [Online]
Available at: https://blog.netwrix.com/2018/01/16/how-to-perform-it-risk-assessment/
[Accessed 25 November 2019].

RISK ASSESSMENT
Svantesson, D. & Clarke, R., 2010. Privacy and consumer risks in cloud computing.. Computer
law & security review, 26(4), pp. 391-397.
Troldborg, M. et al., 2008. Risk assessment and prioritisation of contaminated sites on the
catchment scale. Journal of Contaminant Hydrology, 104(1-4), pp. 14-28.
Svantesson, D. & Clarke, R., 2010. Privacy and consumer risks in cloud computing.. Computer
law & security review, 26(4), pp. 391-397.
Troldborg, M. et al., 2008. Risk assessment and prioritisation of contaminated sites on the
catchment scale. Journal of Contaminant Hydrology, 104(1-4), pp. 14-28.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Running Head: RISK ASSESSMENT 0
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





