Security Risk Assessment, Cloud Disaster Recovery Plan & ISO Audit
VerifiedAdded on 2023/06/10
|6
|1111
|346
Report
AI Summary
This report presents a security risk assessment conducted to address network performance issues and potential security breaches. It recommends penetration testing using Acunetix to identify vulnerabilities such as SQL injection and Cross-Site Scripting. The report proposes enhancing network security by implementing a three-homed host firewall architecture and advanced DMZ configurations to monitor and control external connections. It also includes a disaster recovery plan with cloud options and an audit of the organization using the ISO 17799 checklist, focusing on improving business productivity and prioritizing customer data security through modern DMZ utilization and proactive threat monitoring. This document is available on Desklib, a platform offering a wide range of study resources including past papers and solved assignments.

Running Head: SECURITY RISK ASSESSMENT 1
Security Risk Assessment
Name
Affiliation
Security Risk Assessment
Name
Affiliation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SECURITY RISK ASSESSMENT
When the interest on how the HTTP request is being processed within the network it
shows that internet usage within the system remained the same. The main question is why
dropping in the performance of business yet customers are still accessing the internet
accordingly? This is an indication that there is a problem in the network security because that
is a sign that a foreigner has got access to the network resources at this point. The meetings
convened by the managers could not be of much help, but instead, the solution lies in
between the network administrator. Network Admin should carry bout duties that will be
directed to ensuring the security of the network is upgraded and analyze the bridge the gap of
network success.
To clearly get the finer details of the network performance a pen testing should be
carried out since there are indications that the competitor has directed new clients POST to
their website. In this case, the best tool to use the Acunetix. This is a penetration testing that
comes in free and paid flavors. Acunetix is hacking tool with variety uses, but it majors in the
testing and reporting on SQL injection and also testing of Cross Site Scripting (Daud, Bakar,
Azmi, Hasan, & Shafeq 2014, August). The state of art crawler technology is utilized in this
tool. The technology includes client scripting analyzes engine. The benefit that is accrued
from using of this network is the detailed report of all identified security issues and threats.
With The latest version of this tool that includes multiple security features with a good
example being a new module that is involved in the testing of slow HTTP DOS. The latest
version makes the shipment with ISO 27001compliance report template. The tool helps the
organization validate the web applications.
There are some computers that will also be outside of the firewall on the network to
intercept traffic and man-in-the-middle requests for the remaining part of the network which
will be an advantage to the other devices inside the firewall (Dart, Rotman, Tierney, Hester &
Zurawski 2014). Having known that there is hacking in the network what need to be done is
When the interest on how the HTTP request is being processed within the network it
shows that internet usage within the system remained the same. The main question is why
dropping in the performance of business yet customers are still accessing the internet
accordingly? This is an indication that there is a problem in the network security because that
is a sign that a foreigner has got access to the network resources at this point. The meetings
convened by the managers could not be of much help, but instead, the solution lies in
between the network administrator. Network Admin should carry bout duties that will be
directed to ensuring the security of the network is upgraded and analyze the bridge the gap of
network success.
To clearly get the finer details of the network performance a pen testing should be
carried out since there are indications that the competitor has directed new clients POST to
their website. In this case, the best tool to use the Acunetix. This is a penetration testing that
comes in free and paid flavors. Acunetix is hacking tool with variety uses, but it majors in the
testing and reporting on SQL injection and also testing of Cross Site Scripting (Daud, Bakar,
Azmi, Hasan, & Shafeq 2014, August). The state of art crawler technology is utilized in this
tool. The technology includes client scripting analyzes engine. The benefit that is accrued
from using of this network is the detailed report of all identified security issues and threats.
With The latest version of this tool that includes multiple security features with a good
example being a new module that is involved in the testing of slow HTTP DOS. The latest
version makes the shipment with ISO 27001compliance report template. The tool helps the
organization validate the web applications.
There are some computers that will also be outside of the firewall on the network to
intercept traffic and man-in-the-middle requests for the remaining part of the network which
will be an advantage to the other devices inside the firewall (Dart, Rotman, Tierney, Hester &
Zurawski 2014). Having known that there is hacking in the network what need to be done is
SECURITY RISK ASSESSMENT
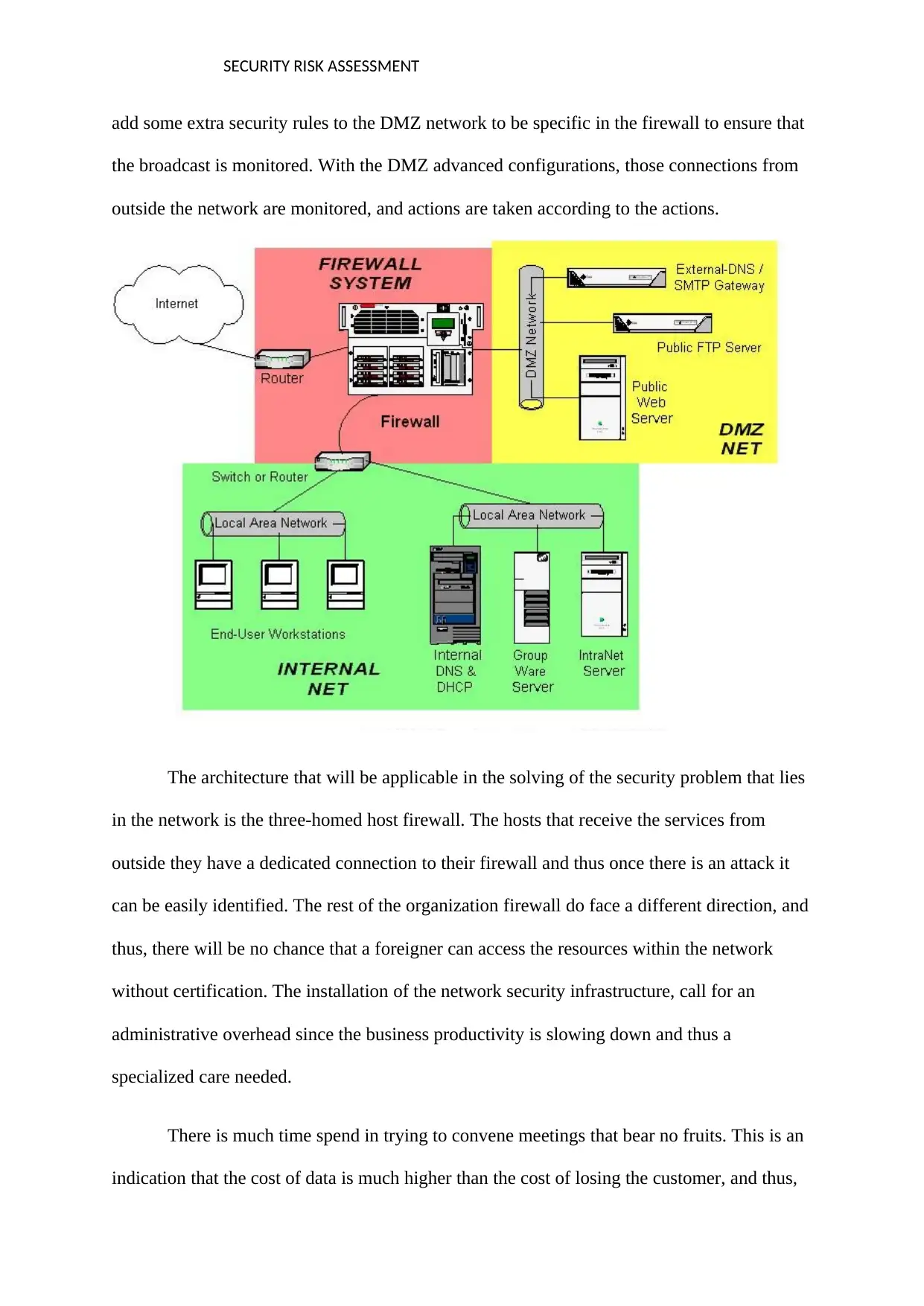
add some extra security rules to the DMZ network to be specific in the firewall to ensure that
the broadcast is monitored. With the DMZ advanced configurations, those connections from
outside the network are monitored, and actions are taken according to the actions.
The architecture that will be applicable in the solving of the security problem that lies
in the network is the three-homed host firewall. The hosts that receive the services from
outside they have a dedicated connection to their firewall and thus once there is an attack it
can be easily identified. The rest of the organization firewall do face a different direction, and
thus, there will be no chance that a foreigner can access the resources within the network
without certification. The installation of the network security infrastructure, call for an
administrative overhead since the business productivity is slowing down and thus a
specialized care needed.
There is much time spend in trying to convene meetings that bear no fruits. This is an
indication that the cost of data is much higher than the cost of losing the customer, and thus,
add some extra security rules to the DMZ network to be specific in the firewall to ensure that
the broadcast is monitored. With the DMZ advanced configurations, those connections from
outside the network are monitored, and actions are taken according to the actions.
The architecture that will be applicable in the solving of the security problem that lies
in the network is the three-homed host firewall. The hosts that receive the services from
outside they have a dedicated connection to their firewall and thus once there is an attack it
can be easily identified. The rest of the organization firewall do face a different direction, and
thus, there will be no chance that a foreigner can access the resources within the network
without certification. The installation of the network security infrastructure, call for an
administrative overhead since the business productivity is slowing down and thus a
specialized care needed.
There is much time spend in trying to convene meetings that bear no fruits. This is an
indication that the cost of data is much higher than the cost of losing the customer, and thus,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

SECURITY RISK ASSESSMENT
security of the customers should be given priority. The use of modern DMZ should be
utilized to prevent the customer request outside Scripting. When the hackers are easily
monitored using advanced firewalls, then the productivity of the system will move much
higher. Initially the implementation of the network security infrastructure is costly but later
the company will regain and the network resources protected.
security of the customers should be given priority. The use of modern DMZ should be
utilized to prevent the customer request outside Scripting. When the hackers are easily
monitored using advanced firewalls, then the productivity of the system will move much
higher. Initially the implementation of the network security infrastructure is costly but later
the company will regain and the network resources protected.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SECURITY RISK ASSESSMENT
References
Alena, Buchalcevova, & Gala Libor. "Green ICT Adoption Survey Focused on ICT Life-
cycle from the Consumer’s Perspective (SMEs)." Journal of Competitiveness 4 (4):
(2012) 109-122.
Armbrust, Michael, et al. "A view of cloud computing." Communications of the ACM 53.4
(2010): 50-58.
Dart, E., Rotman, L., Tierney, B., Hester, M., & Zurawski, J. (2014). The science dmz: A
network design pattern for data-intensive science. Scientific Programming, 22(2),
173-185.
Daud, N. I., Bakar, A., Azmi, K., Hasan, M., & Shafeq, M. (2014, August). A case study on
web application vulnerability scanning tools. In Science and Information Conference
(SAI), 2014 (pp. 595-600). IEEE.
Gollmann, D. (2010). Computer security. Wiley Interdisciplinary Reviews: Computational
Statistics, 2(5), 544-554.
Khan, S., & Pathan, A. S. K. (Eds.). (2013). Wireless networks and security: issues,
challenges and research trends. Springer Science & Business Media.
Ramgovind, Sumant, Mariki M. Eloff, and Elme Smith. "The management of security in
cloud computing." Information Security for South Africa (ISSA), 2010. IEEE, 2010.
Seth, Ashish, Himanshu Agarwal, & AR Singla.. "Integrating SOA and Cloud Computing for
SME Business Objective." WSEAS Transactions on Computers, USA (3). (2012) (84)
Song, Malin, Ben-Chang Shia, Hailiang Yao, Wei Wang, and Kuangnan Fang.. "Small and
Medium Enterprises Risky Prediction System Based On Cloud Computing." Journal
of Software (1796217X) 7 (10) (2012) (87)
References
Alena, Buchalcevova, & Gala Libor. "Green ICT Adoption Survey Focused on ICT Life-
cycle from the Consumer’s Perspective (SMEs)." Journal of Competitiveness 4 (4):
(2012) 109-122.
Armbrust, Michael, et al. "A view of cloud computing." Communications of the ACM 53.4
(2010): 50-58.
Dart, E., Rotman, L., Tierney, B., Hester, M., & Zurawski, J. (2014). The science dmz: A
network design pattern for data-intensive science. Scientific Programming, 22(2),
173-185.
Daud, N. I., Bakar, A., Azmi, K., Hasan, M., & Shafeq, M. (2014, August). A case study on
web application vulnerability scanning tools. In Science and Information Conference
(SAI), 2014 (pp. 595-600). IEEE.
Gollmann, D. (2010). Computer security. Wiley Interdisciplinary Reviews: Computational
Statistics, 2(5), 544-554.
Khan, S., & Pathan, A. S. K. (Eds.). (2013). Wireless networks and security: issues,
challenges and research trends. Springer Science & Business Media.
Ramgovind, Sumant, Mariki M. Eloff, and Elme Smith. "The management of security in
cloud computing." Information Security for South Africa (ISSA), 2010. IEEE, 2010.
Seth, Ashish, Himanshu Agarwal, & AR Singla.. "Integrating SOA and Cloud Computing for
SME Business Objective." WSEAS Transactions on Computers, USA (3). (2012) (84)
Song, Malin, Ben-Chang Shia, Hailiang Yao, Wei Wang, and Kuangnan Fang.. "Small and
Medium Enterprises Risky Prediction System Based On Cloud Computing." Journal
of Software (1796217X) 7 (10) (2012) (87)

SECURITY RISK ASSESSMENT
The Future of Cloud Computing. http://pewresearch.org/pubs/1623/future cloud-computing-
technology-experts
Velte, Toby, Anthony Velte, and Robert Elsenpeter. Cloud computing, a practical approach.
McGraw-Hill, Inc., 2010.
Wang, George, and Jay Unger.. "A Strategy to Move Taiwan’s IT Industry From Commodity
Hardware Manufacturing to Competitive Cloud Solutions." environments 1:2169-
3536. (2013 ) 98
The Future of Cloud Computing. http://pewresearch.org/pubs/1623/future cloud-computing-
technology-experts
Velte, Toby, Anthony Velte, and Robert Elsenpeter. Cloud computing, a practical approach.
McGraw-Hill, Inc., 2010.
Wang, George, and Jay Unger.. "A Strategy to Move Taiwan’s IT Industry From Commodity
Hardware Manufacturing to Competitive Cloud Solutions." environments 1:2169-
3536. (2013 ) 98
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




