CO4512 Information Security Management: Risk Assessment Report CONVXYZ
VerifiedAdded on 2023/01/19
|9
|2997
|41
Report
AI Summary
This report provides a comprehensive risk assessment for CONVXYZ, a UK-based conveyancing and real estate organization planning to establish an IT network. The report begins with an introduction to information security management, emphasizing the importance of preventing business losses through measures like protecting against data theft, modification, and destruction. It describes the organization's structure and the role of its website for client interaction. The report then details the risk assessment process, including owner specification, asset classification (primary and secondary assets like personal computers, web servers, and firewalls), and the identification of threats (e.g., DDoS attacks, wireless access point vulnerabilities, email misuse) and vulnerabilities. The report uses the Boston grid for likelihood level computation and identifies various risks along with their levels. The report includes recommendations for risk control and mitigation strategies. The report also includes a conclusion and references.

Running head: INFORMATION SECURITY MANAGEMENT
Information Security Management
Name of the Student
Name of the University
Author Note:
Information Security Management
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION SECURITY MANAGEMENT
Table of Contents
Introduction.................................................................................................................................................2
Risk assessment...........................................................................................................................................2
Owner Specification................................................................................................................................2
Asset Classification..............................................................................................................................3
Threat for asset...................................................................................................................................4
Vulnerability of asset..........................................................................................................................4
Likelihood level Computation.............................................................................................................5
Risk identification with risk level.............................................................................................................8
Conclusion...................................................................................................................................................9
Recommendation......................................................................................................................................10
References.................................................................................................................................................11
Table of Contents
Introduction.................................................................................................................................................2
Risk assessment...........................................................................................................................................2
Owner Specification................................................................................................................................2
Asset Classification..............................................................................................................................3
Threat for asset...................................................................................................................................4
Vulnerability of asset..........................................................................................................................4
Likelihood level Computation.............................................................................................................5
Risk identification with risk level.............................................................................................................8
Conclusion...................................................................................................................................................9
Recommendation......................................................................................................................................10
References.................................................................................................................................................11

2INFORMATION SECURITY MANAGEMENT
Introduction
The following report is all about conveyancing and real estate organization named CONVXYZ
which is based in United Kingdom. The organization is planning to set up their IT network and system.
The organization aims to provide real estate service for both property buyers and vendors(Peltier 2016).
The main notion of security system is all about preventing or reducing the business loss that is caused as
a result of possible incidents. The situation can be any one of the following like stealing information,
modification of data, deletion and destruction. It is mainly inclusive of large number of things scam
which has many victims. This particular organization comes up with a website where the client of the
organization can easily look for property details and can easily contact for estate agents (Soomro, Shah
and Ahmed 2016). After making a registration to the conveyancing service, customers can easily get the
details of the account that is username and password to the website. For this report, we are going to
use checklist method of risk assessment. This particular risk assessment methods can provide a range of
benefits like identifying security vulnerabilities, making smart purchase, improved planning and many
other.
In the coming pages of the report, a risk assessment has been done where the specification of
the owner has been discussed in details. Both kind of assets that is primary and secondary has been
discussed in brief. One threat and one vulnerability for each of asset has been discussed in brief. After
that the likelihood level of computation has been done by making used of Boston grid.
Risk assessment
Owner Specification
UK based CONVXYZ organization is focusing on to hire team by which they can set up their IT
network. The real estate organization aims to provide real estate services for both property vendors and
buyers. The service is mainly employed by different kind of lawyers. The main notion of the organization
is to reduce the overall loss which is caused due to possible incident. The main focus of authenticate
server is to authenticate the username and password for both customer and staff members (Safa et al.
2016). At the time of authenticating of task, the server needs to communicate at both end that is
database of staff and server where all the required information is stored. By the help of proper
authentication, both customers and staff can easily access the property details and present
documentation. The organization makes use of employees like lawyers, real estate agents where they
can make use of system for login into the website of the organization or even browse for internet
services (Hoffmann, Kiedrowicz and Stanik, 2016). In this organization, prior to any kind of exchange
between the buyer and vendor, buyer needs to request for money to the bank account of this real
estate organization. All the details like bank account number is provided by the help of email and post.
Asset Classification
In CONVXYZ organization, primary asset can be stated as the asset which needs to be
incorporated in the begin for importing certain kind of assets. Primary asset can state as the default kind
of scope which is needed for importing other kind of asset (Safa, and Von Solms 2016). There are certain
Introduction
The following report is all about conveyancing and real estate organization named CONVXYZ
which is based in United Kingdom. The organization is planning to set up their IT network and system.
The organization aims to provide real estate service for both property buyers and vendors(Peltier 2016).
The main notion of security system is all about preventing or reducing the business loss that is caused as
a result of possible incidents. The situation can be any one of the following like stealing information,
modification of data, deletion and destruction. It is mainly inclusive of large number of things scam
which has many victims. This particular organization comes up with a website where the client of the
organization can easily look for property details and can easily contact for estate agents (Soomro, Shah
and Ahmed 2016). After making a registration to the conveyancing service, customers can easily get the
details of the account that is username and password to the website. For this report, we are going to
use checklist method of risk assessment. This particular risk assessment methods can provide a range of
benefits like identifying security vulnerabilities, making smart purchase, improved planning and many
other.
In the coming pages of the report, a risk assessment has been done where the specification of
the owner has been discussed in details. Both kind of assets that is primary and secondary has been
discussed in brief. One threat and one vulnerability for each of asset has been discussed in brief. After
that the likelihood level of computation has been done by making used of Boston grid.
Risk assessment
Owner Specification
UK based CONVXYZ organization is focusing on to hire team by which they can set up their IT
network. The real estate organization aims to provide real estate services for both property vendors and
buyers. The service is mainly employed by different kind of lawyers. The main notion of the organization
is to reduce the overall loss which is caused due to possible incident. The main focus of authenticate
server is to authenticate the username and password for both customer and staff members (Safa et al.
2016). At the time of authenticating of task, the server needs to communicate at both end that is
database of staff and server where all the required information is stored. By the help of proper
authentication, both customers and staff can easily access the property details and present
documentation. The organization makes use of employees like lawyers, real estate agents where they
can make use of system for login into the website of the organization or even browse for internet
services (Hoffmann, Kiedrowicz and Stanik, 2016). In this organization, prior to any kind of exchange
between the buyer and vendor, buyer needs to request for money to the bank account of this real
estate organization. All the details like bank account number is provided by the help of email and post.
Asset Classification
In CONVXYZ organization, primary asset can be stated as the asset which needs to be
incorporated in the begin for importing certain kind of assets. Primary asset can state as the default kind
of scope which is needed for importing other kind of asset (Safa, and Von Solms 2016). There are certain
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INFORMATION SECURITY MANAGEMENT
number of assets that are mainly imported right after the primary assets like secondary assets. Primary
assets comprise of super set that are considered to secondary assets.
In asset system, site is known to be primary asset which is needed for various type of assets.
When the individual imports the assets for any kind then it can make use of site. It is not generally
recommended for use of site like a scope even if it is supported in case of most of the assets. The assets
in the given scenario are personal computers, web server, mail server, switch, database for staff,
authenticated server, router, firewall, internet. ISO 27005 aims to provide proper meaning to the
organization for access risk in the information security (Safa et al. 2015). The standard aims in
understanding of risk and treating it in required ways. Dealing with information risk makes use of
practical implementation and management of the given perspectives. The main notion of this standard
is all about providing proper guidelines which is needed for information risk management and promote
the general concept and idea (Almorsy, Grundy and Müller, 2016). It has been mainly designed for
assisting the overall implementation of information security depending on the approach of risk
assessment.
Threat for asset
Firewall is considered to as a part of the cybersecurity infrastructure which makes is a huge issue
for protecting the business of this organization. There are huge number of issues with respect to firewall
which can make it a bad logic for protecting the organization. The biggest threat in vulnerability is
Distributed Denial of Services attacks (Shameli-Sendi, Aghababaei-Barzegar and Cheriet, 2016). It can
mainly result in frequent attacks which is very much effective and low cost in nature. The main goal is all
defending the resources and can result in shutdown for delivering services.
Wireless access point can be considered to be immediate connectivity where the user can easily
go beyond the connectivity within the given network. Wireless attacks are mainly driven by common in
nature (Haufe et al. 2016). Wireless access point is considered to be highly insecure in nature regardless
of the kind of encryption that is being used. There are certain number of protocols that comes up with
vulnerability and can compromise with the attack framework.
Email can be considered to as one of the frequent data which is used for sending and receiving
data. But in most of the cases it is misused (Laudon, and Laudon 2016). In most of the cases, confidential
information can be easily forwarded to external target. E-mails tend to carry nasty virus of the user.
Vulnerability of asset
Vulnerability can be stated as any kind of weakness in the network in the present network which
can be exploited by a threat. At present, it is being applied in almost every area of network technology
like banking and E-commerce. The application mainly comprises of various type of network and devices
for malicious attack (Ahmad, Maynard and Shank 2015). The hackers come up with the option of
exploiting the vulnerability which can be reduced. At present, there are large number of hardware and
software tools available in protecting these kinds of attacks like firewall, Intrusion Detection System.
There are many different kinds of software available for scanning the vulnerability in the network
number of assets that are mainly imported right after the primary assets like secondary assets. Primary
assets comprise of super set that are considered to secondary assets.
In asset system, site is known to be primary asset which is needed for various type of assets.
When the individual imports the assets for any kind then it can make use of site. It is not generally
recommended for use of site like a scope even if it is supported in case of most of the assets. The assets
in the given scenario are personal computers, web server, mail server, switch, database for staff,
authenticated server, router, firewall, internet. ISO 27005 aims to provide proper meaning to the
organization for access risk in the information security (Safa et al. 2015). The standard aims in
understanding of risk and treating it in required ways. Dealing with information risk makes use of
practical implementation and management of the given perspectives. The main notion of this standard
is all about providing proper guidelines which is needed for information risk management and promote
the general concept and idea (Almorsy, Grundy and Müller, 2016). It has been mainly designed for
assisting the overall implementation of information security depending on the approach of risk
assessment.
Threat for asset
Firewall is considered to as a part of the cybersecurity infrastructure which makes is a huge issue
for protecting the business of this organization. There are huge number of issues with respect to firewall
which can make it a bad logic for protecting the organization. The biggest threat in vulnerability is
Distributed Denial of Services attacks (Shameli-Sendi, Aghababaei-Barzegar and Cheriet, 2016). It can
mainly result in frequent attacks which is very much effective and low cost in nature. The main goal is all
defending the resources and can result in shutdown for delivering services.
Wireless access point can be considered to be immediate connectivity where the user can easily
go beyond the connectivity within the given network. Wireless attacks are mainly driven by common in
nature (Haufe et al. 2016). Wireless access point is considered to be highly insecure in nature regardless
of the kind of encryption that is being used. There are certain number of protocols that comes up with
vulnerability and can compromise with the attack framework.
Email can be considered to as one of the frequent data which is used for sending and receiving
data. But in most of the cases it is misused (Laudon, and Laudon 2016). In most of the cases, confidential
information can be easily forwarded to external target. E-mails tend to carry nasty virus of the user.
Vulnerability of asset
Vulnerability can be stated as any kind of weakness in the network in the present network which
can be exploited by a threat. At present, it is being applied in almost every area of network technology
like banking and E-commerce. The application mainly comprises of various type of network and devices
for malicious attack (Ahmad, Maynard and Shank 2015). The hackers come up with the option of
exploiting the vulnerability which can be reduced. At present, there are large number of hardware and
software tools available in protecting these kinds of attacks like firewall, Intrusion Detection System.
There are many different kinds of software available for scanning the vulnerability in the network
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4INFORMATION SECURITY MANAGEMENT
(Sadeghi, Wachsmann and Waidner 2015). Use of proper hardware and software does not provide
guarantee against these attacks. The only system which is secured in the one which is powered off.
Unauthorized kind of access comes into picture when the user tries to have an access to the
given resources which is not permitted at all. This particular scenario can come into picture as the
administration is completely assigned any kind of resources (Line and Albrechtsen 2016). Organization
can make use of list of department and users where some have inappropriate access to any of the
network resources. It is mainly because user is not from same department or may such one which is
outside the organization.
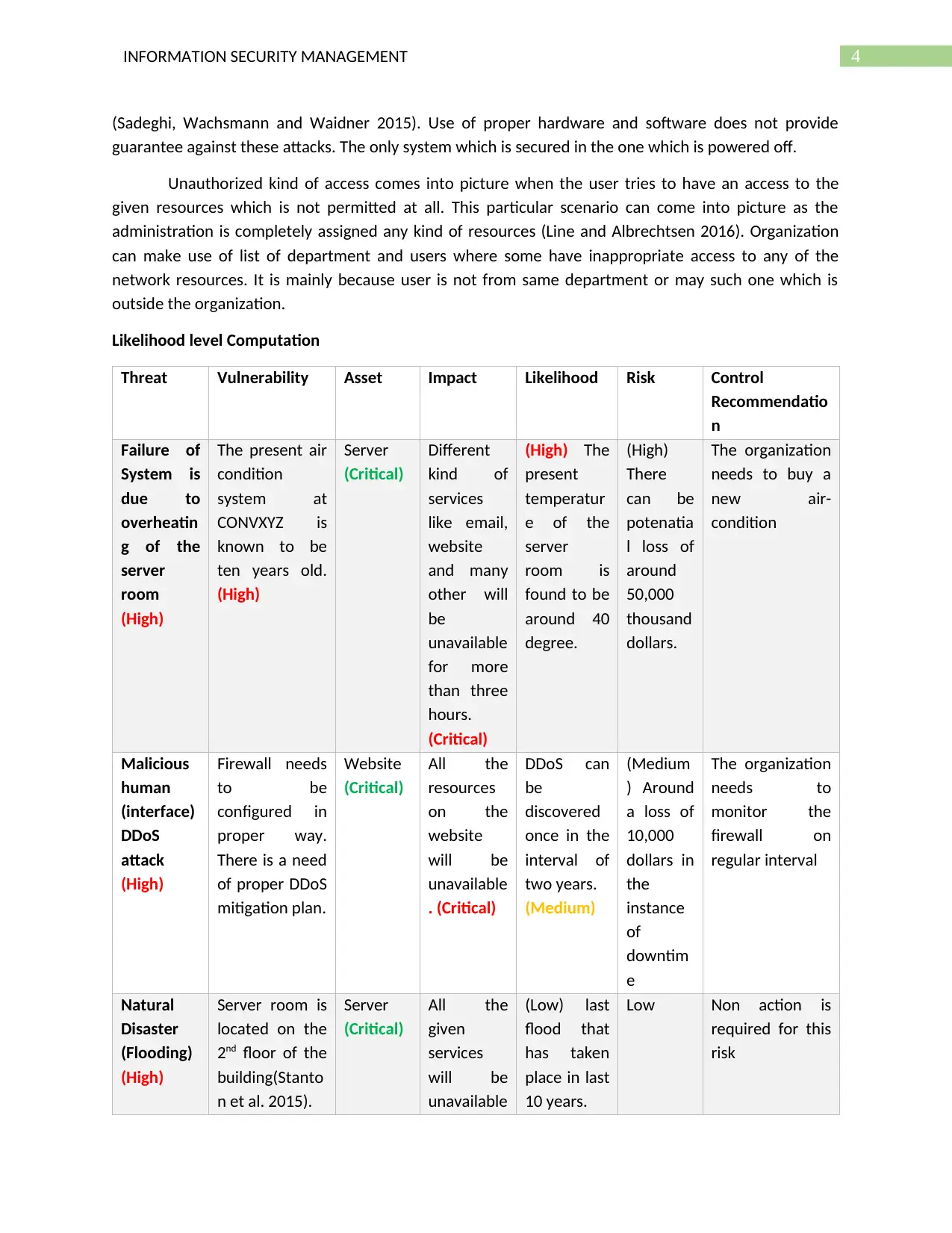
Likelihood level Computation
Threat Vulnerability Asset Impact Likelihood Risk Control
Recommendatio
n
Failure of
System is
due to
overheatin
g of the
server
room
(High)
The present air
condition
system at
CONVXYZ is
known to be
ten years old.
(High)
Server
(Critical)
Different
kind of
services
like email,
website
and many
other will
be
unavailable
for more
than three
hours.
(Critical)
(High) The
present
temperatur
e of the
server
room is
found to be
around 40
degree.
(High)
There
can be
potenatia
l loss of
around
50,000
thousand
dollars.
The organization
needs to buy a
new air-
condition
Malicious
human
(interface)
DDoS
attack
(High)
Firewall needs
to be
configured in
proper way.
There is a need
of proper DDoS
mitigation plan.
Website
(Critical)
All the
resources
on the
website
will be
unavailable
. (Critical)
DDoS can
be
discovered
once in the
interval of
two years.
(Medium)
(Medium
) Around
a loss of
10,000
dollars in
the
instance
of
downtim
e
The organization
needs to
monitor the
firewall on
regular interval
Natural
Disaster
(Flooding)
(High)
Server room is
located on the
2nd floor of the
building(Stanto
n et al. 2015).
Server
(Critical)
All the
given
services
will be
unavailable
(Low) last
flood that
has taken
place in last
10 years.
Low Non action is
required for this
risk
(Sadeghi, Wachsmann and Waidner 2015). Use of proper hardware and software does not provide
guarantee against these attacks. The only system which is secured in the one which is powered off.
Unauthorized kind of access comes into picture when the user tries to have an access to the
given resources which is not permitted at all. This particular scenario can come into picture as the
administration is completely assigned any kind of resources (Line and Albrechtsen 2016). Organization
can make use of list of department and users where some have inappropriate access to any of the
network resources. It is mainly because user is not from same department or may such one which is
outside the organization.
Likelihood level Computation
Threat Vulnerability Asset Impact Likelihood Risk Control
Recommendatio
n
Failure of
System is
due to
overheatin
g of the
server
room
(High)
The present air
condition
system at
CONVXYZ is
known to be
ten years old.
(High)
Server
(Critical)
Different
kind of
services
like email,
website
and many
other will
be
unavailable
for more
than three
hours.
(Critical)
(High) The
present
temperatur
e of the
server
room is
found to be
around 40
degree.
(High)
There
can be
potenatia
l loss of
around
50,000
thousand
dollars.
The organization
needs to buy a
new air-
condition
Malicious
human
(interface)
DDoS
attack
(High)
Firewall needs
to be
configured in
proper way.
There is a need
of proper DDoS
mitigation plan.
Website
(Critical)
All the
resources
on the
website
will be
unavailable
. (Critical)
DDoS can
be
discovered
once in the
interval of
two years.
(Medium)
(Medium
) Around
a loss of
10,000
dollars in
the
instance
of
downtim
e
The organization
needs to
monitor the
firewall on
regular interval
Natural
Disaster
(Flooding)
(High)
Server room is
located on the
2nd floor of the
building(Stanto
n et al. 2015).
Server
(Critical)
All the
given
services
will be
unavailable
(Low) last
flood that
has taken
place in last
10 years.
Low Non action is
required for this
risk
5INFORMATION SECURITY MANAGEMENT
(Critical)
Any kind
of
accidental
human
interface
can result
in
accidental
file
deletion.
(High)
There is a need
of proper
configuration
of IT system.
There is a need
of proper IT
editing
software like
backups needs
to be taken in
regular interval
(Baek et al.
2015).
Shared
files on
the
network
(Medium
)
All the
important
data can
be lost but
most of
them can
be easily
restored
from the
backup
option.
(Low)
(Medium) Low There is a need
of monitoring
permission
which can
change the
privilege back up
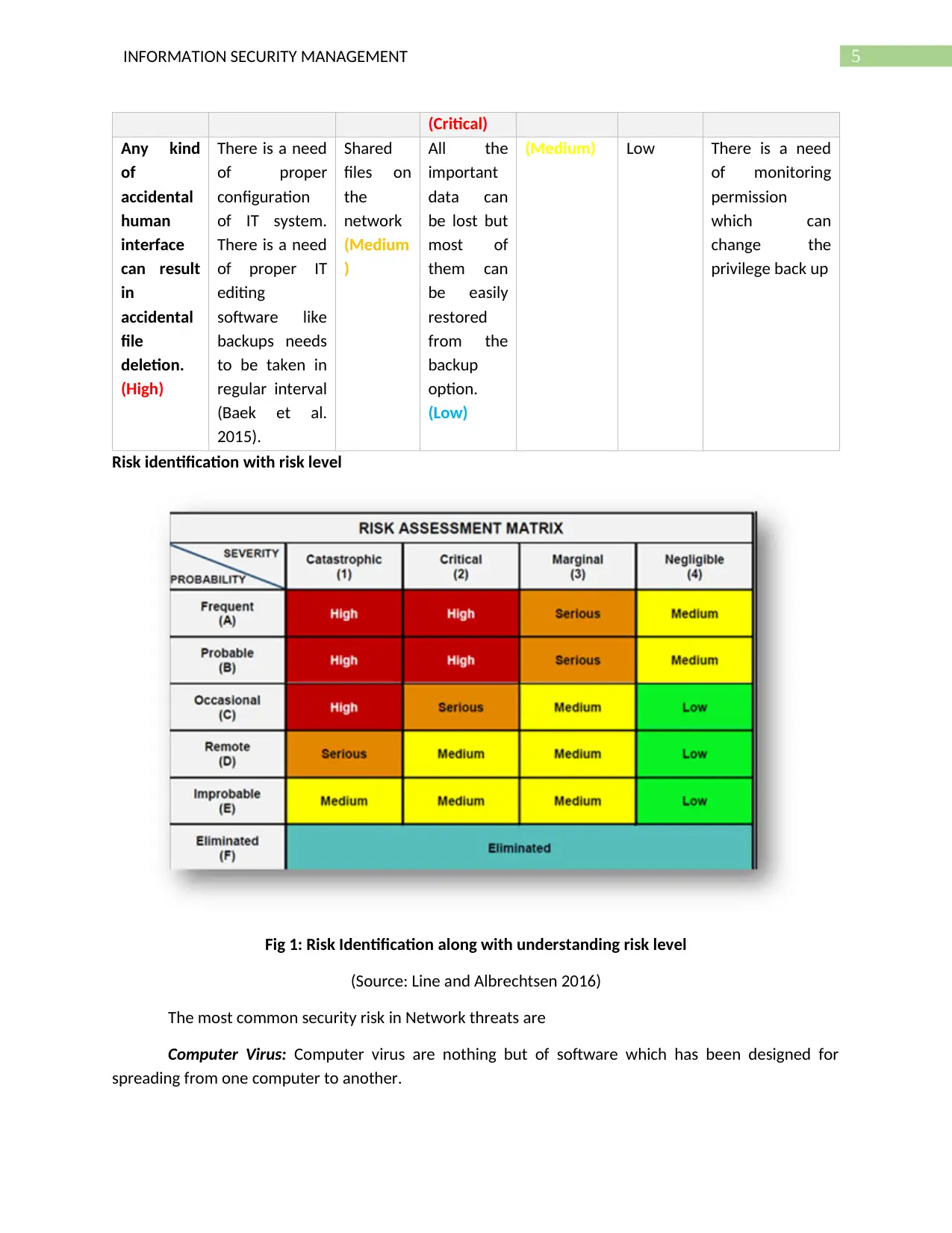
Risk identification with risk level
Fig 1: Risk Identification along with understanding risk level
(Source: Line and Albrechtsen 2016)
The most common security risk in Network threats are
Computer Virus: Computer virus are nothing but of software which has been designed for
spreading from one computer to another.
(Critical)
Any kind
of
accidental
human
interface
can result
in
accidental
file
deletion.
(High)
There is a need
of proper
configuration
of IT system.
There is a need
of proper IT
editing
software like
backups needs
to be taken in
regular interval
(Baek et al.
2015).
Shared
files on
the
network
(Medium
)
All the
important
data can
be lost but
most of
them can
be easily
restored
from the
backup
option.
(Low)
(Medium) Low There is a need
of monitoring
permission
which can
change the
privilege back up
Risk identification with risk level
Fig 1: Risk Identification along with understanding risk level
(Source: Line and Albrechtsen 2016)
The most common security risk in Network threats are
Computer Virus: Computer virus are nothing but of software which has been designed for
spreading from one computer to another.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6INFORMATION SECURITY MANAGEMENT
Rouge security malware: Rouge security software is known to be a malicious software which
can lead to much better believing of system.
Trojan Horse: This particular virus aims to spread by the help of email when the user click on the
attachment.
Adware and Spyware: Adware aims to collect data that allow the user to make use of software
for free.
Computer worm: It can be defined as a piece of malware programs which can replicate at much
faster rate.
DDoS attack: DoS attack is mainly carried by one machine by making use of internet connection.
Phishing: It can be stated as method in social engineering which comes up with a goal of
collecting some of important data like credit card details.
Rootkit: It can be defined as a method of collection of software tools which helps in remote
control and administration level access in computer networks.
SQL Injection: This particular attack is mainly designed for various data driven application that is
achieved by exploiting the security vulnerabilities in the software-based application.
Man-in the middle attacks: It can be defined as a cyber security attack which helps the attacker
to keep a track of communication between the targets.
Conclusion
The above pages of the report help us in concluding the fact that this report is all about
conveyancing and estate service named as CONVXYZ that is UK based. The main focus of the
organization is to provide real estate services for both property vendor and buyers. The act of
conveyancing service is mainly employed by the employed layers. The main focus of the security system
is all about providing any kind of loss by business incidents. They want to stop a range of activities like
malfunction, information sharing, modification of data, destruction which is inclusive of scam. This
particular real company comes up with website where customers can easily look for properties and can
contact real estate agents. After registering in the website, customers can have all details like username
and password of website. It is the location to which client can login and can keep a track of their buying
and selling activities. In the above pages a complete idea has been provided with respect to one threat
and vulnerability for each of the asset. The vulnerability has been taken from the vulnerability database
and has an official CVE number. The likelihood level of computation has been discussed by making use of
Boston grid in details. The impact level table specification has been discussed in details.
Recommendation
CONVXYZ organization need to invest on IT security because of this of factors like
Cybercrimes are taking around the globe.
Cybercrimes can result in huge amount of loss.
Rouge security malware: Rouge security software is known to be a malicious software which
can lead to much better believing of system.
Trojan Horse: This particular virus aims to spread by the help of email when the user click on the
attachment.
Adware and Spyware: Adware aims to collect data that allow the user to make use of software
for free.
Computer worm: It can be defined as a piece of malware programs which can replicate at much
faster rate.
DDoS attack: DoS attack is mainly carried by one machine by making use of internet connection.
Phishing: It can be stated as method in social engineering which comes up with a goal of
collecting some of important data like credit card details.
Rootkit: It can be defined as a method of collection of software tools which helps in remote
control and administration level access in computer networks.
SQL Injection: This particular attack is mainly designed for various data driven application that is
achieved by exploiting the security vulnerabilities in the software-based application.
Man-in the middle attacks: It can be defined as a cyber security attack which helps the attacker
to keep a track of communication between the targets.
Conclusion
The above pages of the report help us in concluding the fact that this report is all about
conveyancing and estate service named as CONVXYZ that is UK based. The main focus of the
organization is to provide real estate services for both property vendor and buyers. The act of
conveyancing service is mainly employed by the employed layers. The main focus of the security system
is all about providing any kind of loss by business incidents. They want to stop a range of activities like
malfunction, information sharing, modification of data, destruction which is inclusive of scam. This
particular real company comes up with website where customers can easily look for properties and can
contact real estate agents. After registering in the website, customers can have all details like username
and password of website. It is the location to which client can login and can keep a track of their buying
and selling activities. In the above pages a complete idea has been provided with respect to one threat
and vulnerability for each of the asset. The vulnerability has been taken from the vulnerability database
and has an official CVE number. The likelihood level of computation has been discussed by making use of
Boston grid in details. The impact level table specification has been discussed in details.
Recommendation
CONVXYZ organization need to invest on IT security because of this of factors like
Cybercrimes are taking around the globe.
Cybercrimes can result in huge amount of loss.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INFORMATION SECURITY MANAGEMENT
Cybercrimes can easily target most of the critical systems.
Cloud infrastructure is very vulnerable to security attacks.
Raising security threats within the organization.
CONVXYZ organization need to follow ISO-27001 standard because of following aspects like
Helps in wining new business and improving the competitive advantage.
Proper protection and improvisation of overall reputation.
Improving the overall structure and aims to focus on certain aspects.
Minimizes the time needed for frequent audits.
References
Ahmad, A., Maynard, S.B. and Shanks, G., 2015. A case analysis of information systems and security
incident responses. International Journal of Information Management, 35(6), pp.717-723.
Almorsy, M., Grundy, J. and Müller, I., 2016. An analysis of the cloud computing security problem. arXiv
preprint arXiv:1609.01107.
Baek, J., Vu, Q.H., Liu, J.K., Huang, X. and Xiang, Y., 2015. A secure cloud computing based framework for
big data information management of smart grid. IEEE transactions on cloud computing, 3(2), pp.233-244.
Haufe, K., Colomo-Palacios, R., Dzombeta, S., Brandis, K. and Stantchev, V., 2016. Security management
standards: a mapping. Procedia Computer Science, 100, pp.755-761.
Hoffmann, R., Kiedrowicz, M. and Stanik, J., 2016. Risk management system as the basic paradigm of the
information security management system in an organization. In MATEC Web of Conferences (Vol. 76, p.
04010). EDP Sciences.
Laudon, K.C. and Laudon, J.P., 2016. Management information system. Pearson Education India.
Line, M.B. and Albrechtsen, E., 2016. Examining the suitability of industrial safety management
approaches for information security incident management. Information & Computer Security, 24(1),
pp.20-37.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for effective
information security management. Auerbach Publications.
Sadeghi, A.R., Wachsmann, C. and Waidner, M., 2015, June. Security and privacy challenges in industrial
internet of things. In 2015 52nd ACM/EDAC/IEEE Design Automation Conference (DAC) (pp. 1-6). IEEE.
Safa, N.S. and Von Solms, R., 2016. An information security knowledge sharing model in
organizations. Computers in Human Behavior, 57, pp.442-451.
Safa, N.S., Sookhak, M., Von Solms, R., Furnell, S., Ghani, N.A. and Herawan, T., 2015. Information
security conscious care behaviour formation in organizations. Computers & Security, 53, pp.65-78.
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance model in
organizations. Computers & Security, 56, pp.70-82.
Cybercrimes can easily target most of the critical systems.
Cloud infrastructure is very vulnerable to security attacks.
Raising security threats within the organization.
CONVXYZ organization need to follow ISO-27001 standard because of following aspects like
Helps in wining new business and improving the competitive advantage.
Proper protection and improvisation of overall reputation.
Improving the overall structure and aims to focus on certain aspects.
Minimizes the time needed for frequent audits.
References
Ahmad, A., Maynard, S.B. and Shanks, G., 2015. A case analysis of information systems and security
incident responses. International Journal of Information Management, 35(6), pp.717-723.
Almorsy, M., Grundy, J. and Müller, I., 2016. An analysis of the cloud computing security problem. arXiv
preprint arXiv:1609.01107.
Baek, J., Vu, Q.H., Liu, J.K., Huang, X. and Xiang, Y., 2015. A secure cloud computing based framework for
big data information management of smart grid. IEEE transactions on cloud computing, 3(2), pp.233-244.
Haufe, K., Colomo-Palacios, R., Dzombeta, S., Brandis, K. and Stantchev, V., 2016. Security management
standards: a mapping. Procedia Computer Science, 100, pp.755-761.
Hoffmann, R., Kiedrowicz, M. and Stanik, J., 2016. Risk management system as the basic paradigm of the
information security management system in an organization. In MATEC Web of Conferences (Vol. 76, p.
04010). EDP Sciences.
Laudon, K.C. and Laudon, J.P., 2016. Management information system. Pearson Education India.
Line, M.B. and Albrechtsen, E., 2016. Examining the suitability of industrial safety management
approaches for information security incident management. Information & Computer Security, 24(1),
pp.20-37.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for effective
information security management. Auerbach Publications.
Sadeghi, A.R., Wachsmann, C. and Waidner, M., 2015, June. Security and privacy challenges in industrial
internet of things. In 2015 52nd ACM/EDAC/IEEE Design Automation Conference (DAC) (pp. 1-6). IEEE.
Safa, N.S. and Von Solms, R., 2016. An information security knowledge sharing model in
organizations. Computers in Human Behavior, 57, pp.442-451.
Safa, N.S., Sookhak, M., Von Solms, R., Furnell, S., Ghani, N.A. and Herawan, T., 2015. Information
security conscious care behaviour formation in organizations. Computers & Security, 53, pp.65-78.
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance model in
organizations. Computers & Security, 56, pp.70-82.

8INFORMATION SECURITY MANAGEMENT
Shameli-Sendi, A., Aghababaei-Barzegar, R. and Cheriet, M., 2016. Taxonomy of information security risk
assessment (ISRA). Computers & Security, 57, pp.14-30.
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016. Information security management needs more holistic
approach: A literature review. International Journal of Information Management, 36(2), pp.215-225.
Stanton, J., Stam, K., Mastrangelo, P. and Jolton, J., 2015. Behavioral information security. Human-
Computer Interaction and Management Information Systems: Foundations, p.262.
Tot, L., Grubor, G. and Marta, T., 2015. Introducing the information security management system in
cloud computing environment. Acta Polytechnica Hungarica, 12(3), pp.147-166.
Shameli-Sendi, A., Aghababaei-Barzegar, R. and Cheriet, M., 2016. Taxonomy of information security risk
assessment (ISRA). Computers & Security, 57, pp.14-30.
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016. Information security management needs more holistic
approach: A literature review. International Journal of Information Management, 36(2), pp.215-225.
Stanton, J., Stam, K., Mastrangelo, P. and Jolton, J., 2015. Behavioral information security. Human-
Computer Interaction and Management Information Systems: Foundations, p.262.
Tot, L., Grubor, G. and Marta, T., 2015. Introducing the information security management system in
cloud computing environment. Acta Polytechnica Hungarica, 12(3), pp.147-166.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





