CO4512 - Information Security Risk Assessment of CONVXYZ Network
VerifiedAdded on 2023/04/24
|16
|3227
|104
Report
AI Summary
This report presents a comprehensive risk assessment of the internal IT network of CONVXYZ, a conveyance and real estate firm. It begins by outlining the system parameters, including hardware and software specifications of various network components such as servers, routers, firewalls, and databases. The report then identifies and analyzes potential threats, including protocol attacks, VPNFilter, phishing, social engineering, database privilege misuse, and malware, alongside corresponding vulnerabilities, referencing CVEs like CVE-2018-0101, CVE-2019-1653, and others, detailing their potential impact. The assessment employs threat and vulnerability assessment tables to evaluate the attractiveness of threats and the severity of vulnerabilities. The report then calculates risk levels using likelihood and impact assessments, followed by impact tables and BCG matrices to visualize the risk profile. Finally, the report concludes with an executive summary highlighting key findings and recommendations for mitigating identified risks, with a focus on the most critical vulnerabilities and their implications for CONVXYZ's network security.

1RISK ASSESSMENT ON NETWORK OF CONVXYZ
1. Introduction
The study involves identification of security risks, likely to affect internal IT network of the conveyance
and real estate firm CONVXYZ. Thus, CONVXYZ must prevent incidents like malfunction, data theft, data
manipulation and deletion including recent conveyancing scams like “Friday afternoon fraud”. Threats and
vulnerabilities for each of the assets are discussed by referring to NVD for CVE and definition. The report
begins with asset specifications and then discusses about threats to CONVXYZ with the Threat assessment
table and vulnerabilities for CONVXYZ with the Vulnerability assessment table after which the calculations
are provided and observations are given in concluding notes.
1.1 Risk Management
Risk management is the most necessary factor for the different versions of the various important
cyber security standards or associated frameworks. Because of the sensitivity and nature of business
activities, compliances for the different frameworks are required for private as well as public sector
businesses that aim to conduct services for public sector.
1.2 Risk Standards
ISO 27005:2018 aims to assist in implementing satisfactory information security based on risk
management approaches. Compared to easily understandable ISO 31000:2018 risk-management guidelines
for top level executives or board of directors, ISO 27005:2018 is long, dense as also technically aimed
towards Chief Information Security Officers or CISOs with emphasis on systematic approaches to develop
and maintain ISRM processes.
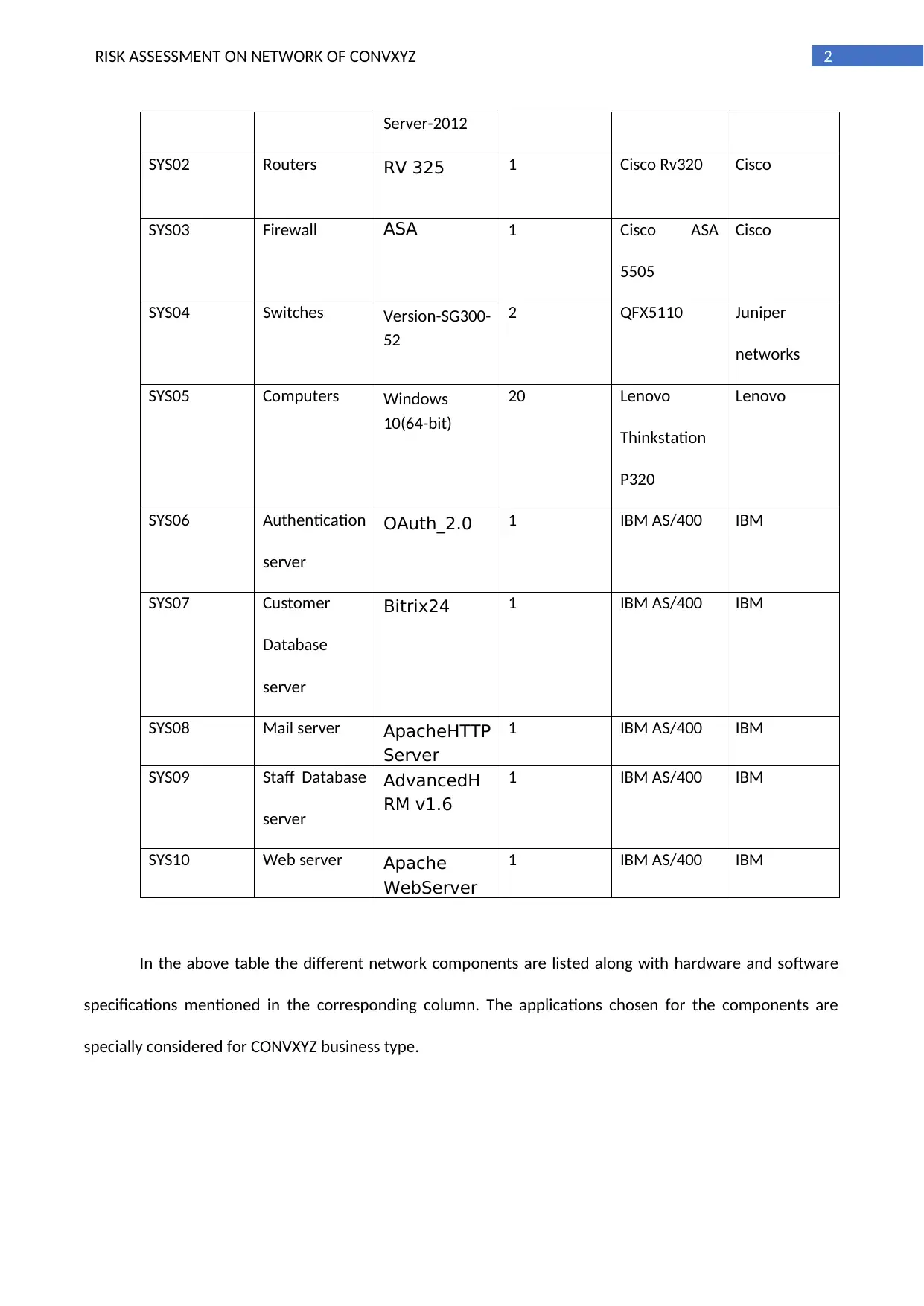
2. System parameters, table
SysNo# Network
Component
Platforms used Number of
Devices
Product
Information
Vendor
SYS01 Servers Windows- 5 IBM AS/400 IBM
1. Introduction
The study involves identification of security risks, likely to affect internal IT network of the conveyance
and real estate firm CONVXYZ. Thus, CONVXYZ must prevent incidents like malfunction, data theft, data
manipulation and deletion including recent conveyancing scams like “Friday afternoon fraud”. Threats and
vulnerabilities for each of the assets are discussed by referring to NVD for CVE and definition. The report
begins with asset specifications and then discusses about threats to CONVXYZ with the Threat assessment
table and vulnerabilities for CONVXYZ with the Vulnerability assessment table after which the calculations
are provided and observations are given in concluding notes.
1.1 Risk Management
Risk management is the most necessary factor for the different versions of the various important
cyber security standards or associated frameworks. Because of the sensitivity and nature of business
activities, compliances for the different frameworks are required for private as well as public sector
businesses that aim to conduct services for public sector.
1.2 Risk Standards
ISO 27005:2018 aims to assist in implementing satisfactory information security based on risk
management approaches. Compared to easily understandable ISO 31000:2018 risk-management guidelines
for top level executives or board of directors, ISO 27005:2018 is long, dense as also technically aimed
towards Chief Information Security Officers or CISOs with emphasis on systematic approaches to develop
and maintain ISRM processes.
2. System parameters, table
SysNo# Network
Component
Platforms used Number of
Devices
Product
Information
Vendor
SYS01 Servers Windows- 5 IBM AS/400 IBM
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
2RISK ASSESSMENT ON NETWORK OF CONVXYZ
Server-2012
SYS02 Routers RV 325 1 Cisco Rv320 Cisco
SYS03 Firewall ASA 1 Cisco ASA
5505
Cisco
SYS04 Switches Version-SG300-
52
2 QFX5110 Juniper
networks
SYS05 Computers Windows
10(64-bit)
20 Lenovo
Thinkstation
P320
Lenovo
SYS06 Authentication
server
OAuth_2.0 1 IBM AS/400 IBM
SYS07 Customer
Database
server
Bitrix24 1 IBM AS/400 IBM
SYS08 Mail server ApacheHTTP
Server
1 IBM AS/400 IBM
SYS09 Staff Database
server
AdvancedH
RM v1.6
1 IBM AS/400 IBM
SYS10 Web server Apache
WebServer
1 IBM AS/400 IBM
In the above table the different network components are listed along with hardware and software
specifications mentioned in the corresponding column. The applications chosen for the components are
specially considered for CONVXYZ business type.
Server-2012
SYS02 Routers RV 325 1 Cisco Rv320 Cisco
SYS03 Firewall ASA 1 Cisco ASA
5505
Cisco
SYS04 Switches Version-SG300-
52
2 QFX5110 Juniper
networks
SYS05 Computers Windows
10(64-bit)
20 Lenovo
Thinkstation
P320
Lenovo
SYS06 Authentication
server
OAuth_2.0 1 IBM AS/400 IBM
SYS07 Customer
Database
server
Bitrix24 1 IBM AS/400 IBM
SYS08 Mail server ApacheHTTP
Server
1 IBM AS/400 IBM
SYS09 Staff Database
server
AdvancedH
RM v1.6
1 IBM AS/400 IBM
SYS10 Web server Apache
WebServer
1 IBM AS/400 IBM
In the above table the different network components are listed along with hardware and software
specifications mentioned in the corresponding column. The applications chosen for the components are
specially considered for CONVXYZ business type.

3RISK ASSESSMENT ON NETWORK OF CONVXYZ
3. Risk Assessment Process
Threats
Threat to Firewalls (ASA5505): Protocol attacks belong to the family of DDoS attacks which drain load
balancer along with resources of firewall, thus preventing process of legitimate traffic (Šimon, Huraj and
Čerňanský 2015). CONVXYZ can suffer massively from this as although firewalls provide security from almost
all DDoS attacks, they are ineffective versus any protocol-attack.
Threat to Routers (RV320): Routers are often targeted by VPNFilter (Rouveyrol, Raveneau and Cunche
2015). This cannot be erased by rebooting the system causing disruption of operations over CONVXYZ’s
network as well as turning infected devices into a bot.
Threat to Web Server: Phishing attacks, redirect victims towards infected websites by making them click on
malicious links using Cookie tampering, Parameter form tampering, non-validated inputs, buffer overflow
attacks and even SQL injection (Sarma 2017).
Threat to E-mail Server: In Social engineering attacks like e-mail spoofing attackers masquerade as
legitimate sources by carrying false sender information in the e-mails to hide their actual origin (Krombholz
et al. 2015). These attacks are similar to e-mail hacking scams dealing with theft of property purchasing cash
like the “Friday afternoon fraud”.
Threat to Database: Users and applications are granted privileges to database exceeding requirements of
specific job functions which can be used for malicious practises. (Elshaafi, McGibney and Botvich 2017). For
CONVXYZ, a database administrator requiring read-only access for customer records can use ‘update’
privileges to manipulate the respective property information.
Threat to Authentication Server: Bypass attacks are caused from absence of access policies in software level
or ineffective authentication systems (Miu et al. 2013). Custom web code enforcing strict password policies
for businesses like CONVXYZ to perform authentication through user credentials but might allow blank
passwords thereby creating serious loopholes.
3. Risk Assessment Process
Threats
Threat to Firewalls (ASA5505): Protocol attacks belong to the family of DDoS attacks which drain load
balancer along with resources of firewall, thus preventing process of legitimate traffic (Šimon, Huraj and
Čerňanský 2015). CONVXYZ can suffer massively from this as although firewalls provide security from almost
all DDoS attacks, they are ineffective versus any protocol-attack.
Threat to Routers (RV320): Routers are often targeted by VPNFilter (Rouveyrol, Raveneau and Cunche
2015). This cannot be erased by rebooting the system causing disruption of operations over CONVXYZ’s
network as well as turning infected devices into a bot.
Threat to Web Server: Phishing attacks, redirect victims towards infected websites by making them click on
malicious links using Cookie tampering, Parameter form tampering, non-validated inputs, buffer overflow
attacks and even SQL injection (Sarma 2017).
Threat to E-mail Server: In Social engineering attacks like e-mail spoofing attackers masquerade as
legitimate sources by carrying false sender information in the e-mails to hide their actual origin (Krombholz
et al. 2015). These attacks are similar to e-mail hacking scams dealing with theft of property purchasing cash
like the “Friday afternoon fraud”.
Threat to Database: Users and applications are granted privileges to database exceeding requirements of
specific job functions which can be used for malicious practises. (Elshaafi, McGibney and Botvich 2017). For
CONVXYZ, a database administrator requiring read-only access for customer records can use ‘update’
privileges to manipulate the respective property information.
Threat to Authentication Server: Bypass attacks are caused from absence of access policies in software level
or ineffective authentication systems (Miu et al. 2013). Custom web code enforcing strict password policies
for businesses like CONVXYZ to perform authentication through user credentials but might allow blank
passwords thereby creating serious loopholes.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4RISK ASSESSMENT ON NETWORK OF CONVXYZ
Threat to Computers: Malware or malicious software can be viruses, Trojan horses, spywares and potentially
unwanted programs (Dahl 2013). Such threats require user inputs which can be opening of unnsolicited e-
mails or download of malicious files.
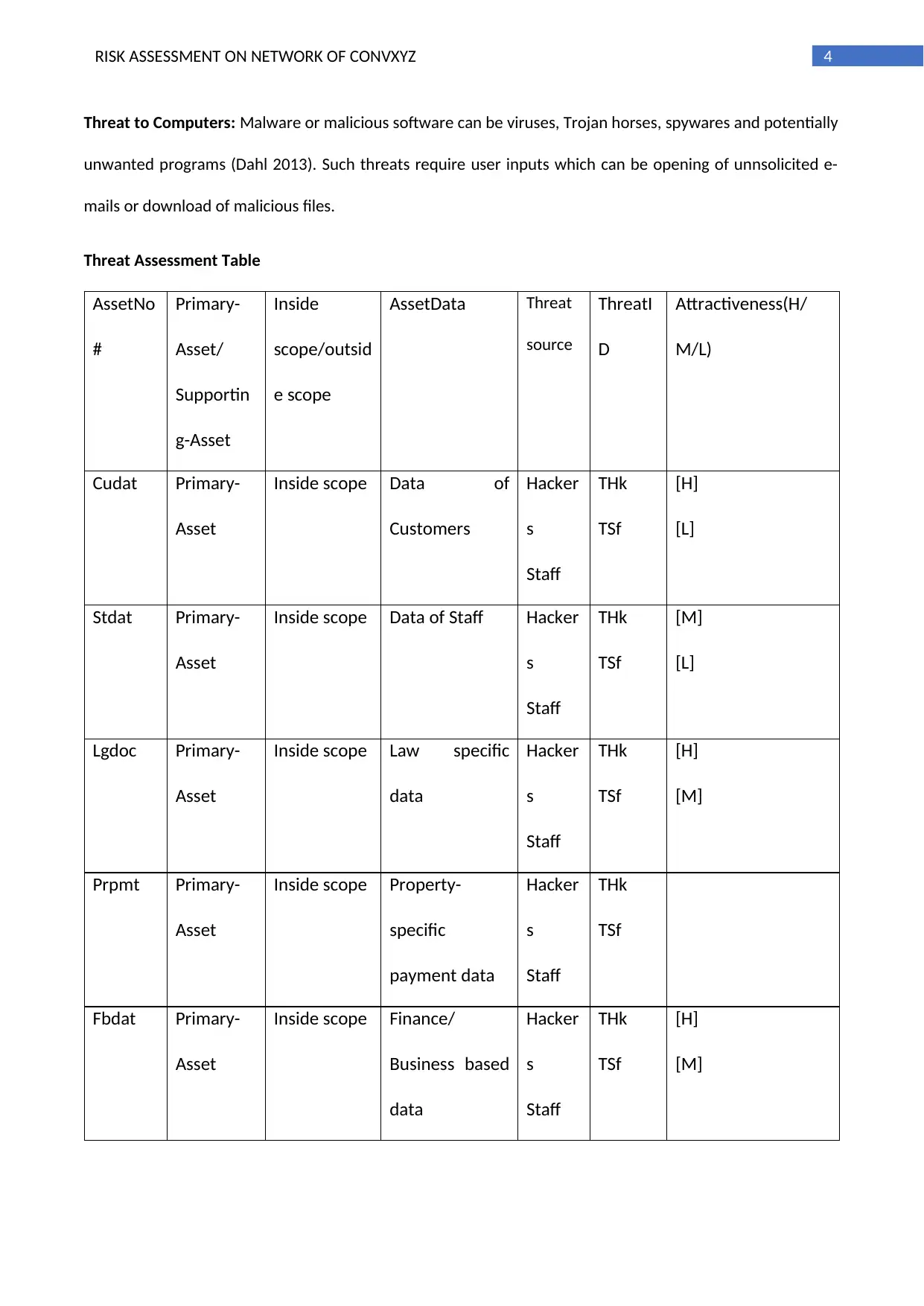
Threat Assessment Table
AssetNo
#
Primary-
Asset/
Supportin
g-Asset
Inside
scope/outsid
e scope
AssetData Threat
source
ThreatI
D
Attractiveness(H/
M/L)
Cudat Primary-
Asset
Inside scope Data of
Customers
Hacker
s
Staff
THk
TSf
[H]
[L]
Stdat Primary-
Asset
Inside scope Data of Staff Hacker
s
Staff
THk
TSf
[M]
[L]
Lgdoc Primary-
Asset
Inside scope Law specific
data
Hacker
s
Staff
THk
TSf
[H]
[M]
Prpmt Primary-
Asset
Inside scope Property-
specific
payment data
Hacker
s
Staff
THk
TSf
Fbdat Primary-
Asset
Inside scope Finance/
Business based
data
Hacker
s
Staff
THk
TSf
[H]
[M]
Threat to Computers: Malware or malicious software can be viruses, Trojan horses, spywares and potentially
unwanted programs (Dahl 2013). Such threats require user inputs which can be opening of unnsolicited e-
mails or download of malicious files.
Threat Assessment Table
AssetNo
#
Primary-
Asset/
Supportin
g-Asset
Inside
scope/outsid
e scope
AssetData Threat
source
ThreatI
D
Attractiveness(H/
M/L)
Cudat Primary-
Asset
Inside scope Data of
Customers
Hacker
s
Staff
THk
TSf
[H]
[L]
Stdat Primary-
Asset
Inside scope Data of Staff Hacker
s
Staff
THk
TSf
[M]
[L]
Lgdoc Primary-
Asset
Inside scope Law specific
data
Hacker
s
Staff
THk
TSf
[H]
[M]
Prpmt Primary-
Asset
Inside scope Property-
specific
payment data
Hacker
s
Staff
THk
TSf
Fbdat Primary-
Asset
Inside scope Finance/
Business based
data
Hacker
s
Staff
THk
TSf
[H]
[M]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
5RISK ASSESSMENT ON NETWORK OF CONVXYZ
Db Supportin
g-Asset
Inside scope Database-
server
Hacker
s
Staff
THk
TSf
[H]
[M]
Ws Supportin
g-Asset
Inside scope WebServer Hacker
s
Staff
THk
TSf
[M]
[L]
FWD Supportin
g-Asset
Inside scope Firewall
Hardware
Hacker
s
Staff
THk
TSf
[H]
[L]
BeC Supportin
g-Asset
Inside scope Back-end-
computers
Hacker
s
Staff
THk
TSf
[M]
[L]
FeC Supportin
g-Asset
Inside scope Front-end-
computers
Hacker
s
Staff
THk
TSf
[M]
[L]
Ro Supportin
g-Asset
Inside scope Routers Hacker
s
Staff
THk
TSf
[H]
[M]
GC Supportin
g-Asset
Outside
scope
Guest-
Computers
Hacker
s
Staff
THk
TSf
Db Supportin
g-Asset
Inside scope Database-
server
Hacker
s
Staff
THk
TSf
[H]
[M]
Ws Supportin
g-Asset
Inside scope WebServer Hacker
s
Staff
THk
TSf
[M]
[L]
FWD Supportin
g-Asset
Inside scope Firewall
Hardware
Hacker
s
Staff
THk
TSf
[H]
[L]
BeC Supportin
g-Asset
Inside scope Back-end-
computers
Hacker
s
Staff
THk
TSf
[M]
[L]
FeC Supportin
g-Asset
Inside scope Front-end-
computers
Hacker
s
Staff
THk
TSf
[M]
[L]
Ro Supportin
g-Asset
Inside scope Routers Hacker
s
Staff
THk
TSf
[H]
[M]
GC Supportin
g-Asset
Outside
scope
Guest-
Computers
Hacker
s
Staff
THk
TSf

6RISK ASSESSMENT ON NETWORK OF CONVXYZ
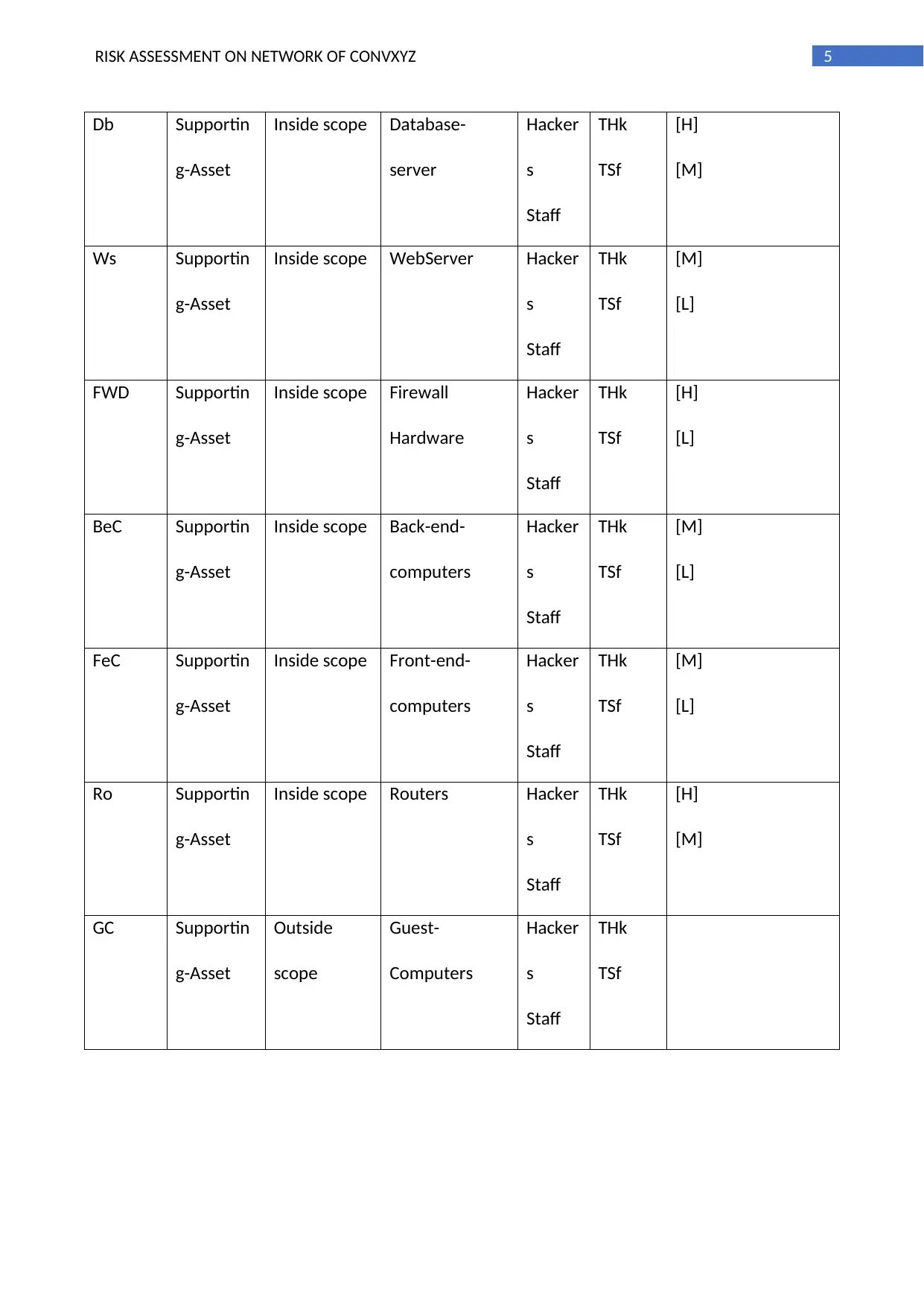
The above table specifies the assets with their respective IDs and mentions the attractiveness level
with respect to the source of threats. It also mentions the scope of the threats for primary as well as
secondary assets.
Vulnerabilities
Vulnerability for Firewalls (ASA5505): CVE-2018-0101 for Cisco Adaptive Security Appliance (ASA) allow
remote attackers reading and running of random files with unknown vectors like bugs as well as denying
services (Andreeva et al. 2016). Firewall services built around Cisco ASA framework are commonly used by
CONVXYZ and similar sized companies demanding mandatory action for addressing the loophole.
Vulnerability for Routers (RV325): A vulnerability CVE-2019-1653 exists in web based interfaces of Dual
Gigabit WAN VPN routers Cisco RV325 with firmware releases 1.4.2.17 allowing unauthenticated remote
attackers in retrieving confidential information. These routers are commonly used by businesses like
CONVXYZ.
Vulnerability for Web (Apache): CVE-2019-0190 is the vulnerability for Apache web server where use of
mod_ssl lets attackers handle client renegotiations, here custom requests are transferred making mod_ssl
loop indefinitely resulting in denying of services (Jerca 2014). This exploit only can get triggered in Apache-
HTTP-Server if operated along Open SSL. CONVXYZ can suffer severe inconveniences from the vulnerability.
Vulnerability for Email Servers (Apache-HTTP-Server): Vulnerability CVE-2018-6789, for email servers on
base64d function in SMTP listener in mail transfer agents before 4.90.1 results in buffer overflow through
sending of customized messages and remote running arbitrary programs (Breyha et al. 2014). As the
operating systems are widely used among small sized businesses such as CONVXYZ, this vulnerability poses
considerable threat.
Vulnerability for Databases: CVE-2018-1834 refers to the vulnerability in IBM DB2 in most operating systems
except Mac operating systems allowing local users in escalating their privileges to root using symbolic link
The above table specifies the assets with their respective IDs and mentions the attractiveness level
with respect to the source of threats. It also mentions the scope of the threats for primary as well as
secondary assets.
Vulnerabilities
Vulnerability for Firewalls (ASA5505): CVE-2018-0101 for Cisco Adaptive Security Appliance (ASA) allow
remote attackers reading and running of random files with unknown vectors like bugs as well as denying
services (Andreeva et al. 2016). Firewall services built around Cisco ASA framework are commonly used by
CONVXYZ and similar sized companies demanding mandatory action for addressing the loophole.
Vulnerability for Routers (RV325): A vulnerability CVE-2019-1653 exists in web based interfaces of Dual
Gigabit WAN VPN routers Cisco RV325 with firmware releases 1.4.2.17 allowing unauthenticated remote
attackers in retrieving confidential information. These routers are commonly used by businesses like
CONVXYZ.
Vulnerability for Web (Apache): CVE-2019-0190 is the vulnerability for Apache web server where use of
mod_ssl lets attackers handle client renegotiations, here custom requests are transferred making mod_ssl
loop indefinitely resulting in denying of services (Jerca 2014). This exploit only can get triggered in Apache-
HTTP-Server if operated along Open SSL. CONVXYZ can suffer severe inconveniences from the vulnerability.
Vulnerability for Email Servers (Apache-HTTP-Server): Vulnerability CVE-2018-6789, for email servers on
base64d function in SMTP listener in mail transfer agents before 4.90.1 results in buffer overflow through
sending of customized messages and remote running arbitrary programs (Breyha et al. 2014). As the
operating systems are widely used among small sized businesses such as CONVXYZ, this vulnerability poses
considerable threat.
Vulnerability for Databases: CVE-2018-1834 refers to the vulnerability in IBM DB2 in most operating systems
except Mac operating systems allowing local users in escalating their privileges to root using symbolic link
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
7RISK ASSESSMENT ON NETWORK OF CONVXYZ
attacks. This makes stored data of CONVXYZ insecure including lawyer specific data that are securely
transferred through the VPN.
Vulnerability for Authentication Servers (OAuth): In vulnerability CVE-2018-16875 regarding TLS Golang
authentication, User input gets formulated by attackers in a way that verification algorithm in crypto x509
repository for Go which helps eat up every CPU resource in validating vast series of TLS instructions assigned
by attackers (Mshangi, Nfuka and Sanga 2015). Since the authentication technique is very popular and most
surely in use by CONVXYZ servers, the loophole must be addressed.
Vulnerability for Computers: The Windows vulnerability CVE-2019-0555 involves elevation of privileges of
the attacker (Kulenovic and Donko 2014). The vulnerability can jeopardise CONVXYZ operations as the
exploit leads to considerable information disclosure along with system file tampering.
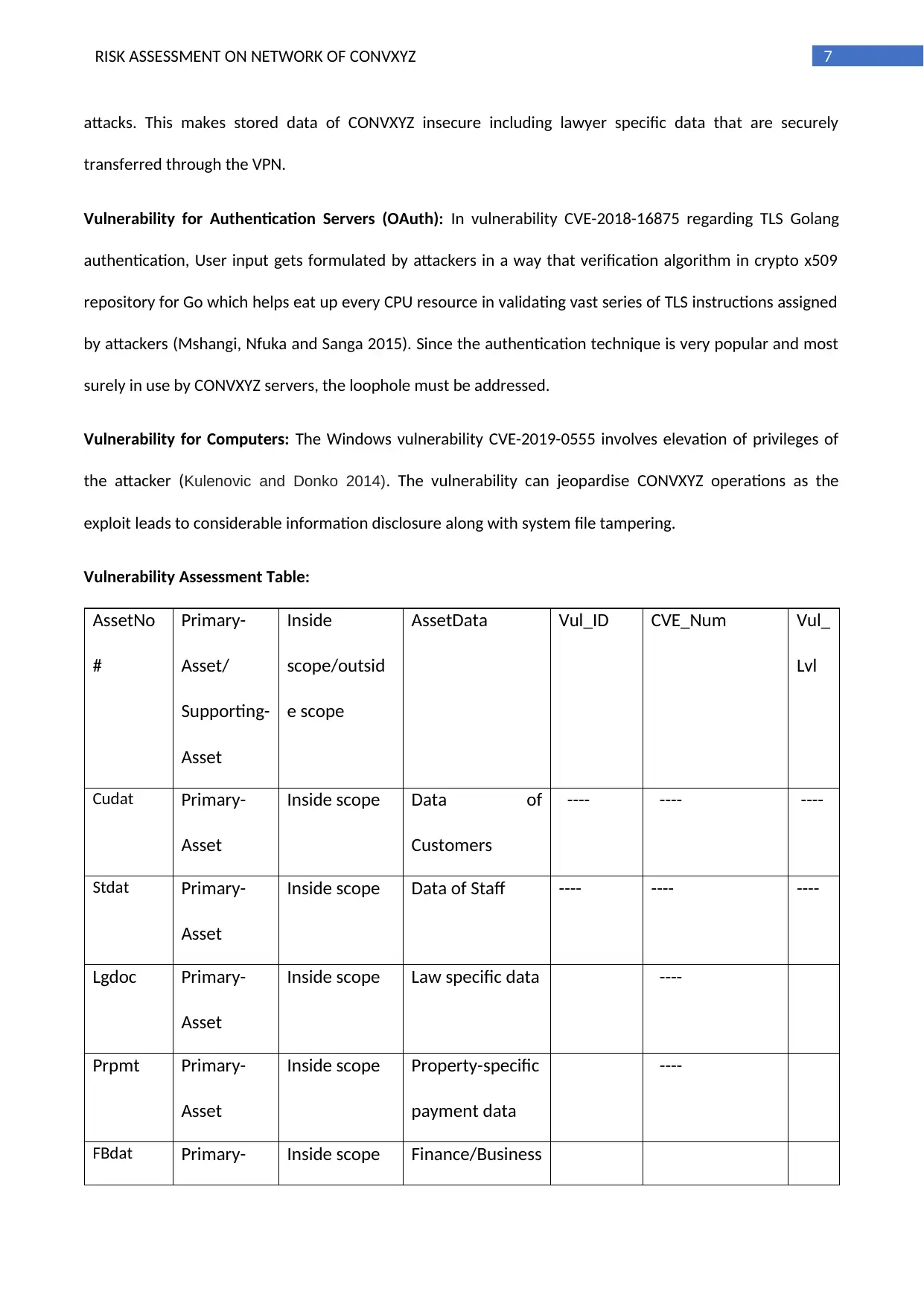
Vulnerability Assessment Table:
AssetNo
#
Primary-
Asset/
Supporting-
Asset
Inside
scope/outsid
e scope
AssetData Vul_ID CVE_Num Vul_
Lvl
Cudat Primary-
Asset
Inside scope Data of
Customers
---- ---- ----
Stdat Primary-
Asset
Inside scope Data of Staff ---- ---- ----
Lgdoc Primary-
Asset
Inside scope Law specific data ----
Prpmt Primary-
Asset
Inside scope Property-specific
payment data
----
FBdat Primary- Inside scope Finance/Business
attacks. This makes stored data of CONVXYZ insecure including lawyer specific data that are securely
transferred through the VPN.
Vulnerability for Authentication Servers (OAuth): In vulnerability CVE-2018-16875 regarding TLS Golang
authentication, User input gets formulated by attackers in a way that verification algorithm in crypto x509
repository for Go which helps eat up every CPU resource in validating vast series of TLS instructions assigned
by attackers (Mshangi, Nfuka and Sanga 2015). Since the authentication technique is very popular and most
surely in use by CONVXYZ servers, the loophole must be addressed.
Vulnerability for Computers: The Windows vulnerability CVE-2019-0555 involves elevation of privileges of
the attacker (Kulenovic and Donko 2014). The vulnerability can jeopardise CONVXYZ operations as the
exploit leads to considerable information disclosure along with system file tampering.
Vulnerability Assessment Table:
AssetNo
#
Primary-
Asset/
Supporting-
Asset
Inside
scope/outsid
e scope
AssetData Vul_ID CVE_Num Vul_
Lvl
Cudat Primary-
Asset
Inside scope Data of
Customers
---- ---- ----
Stdat Primary-
Asset
Inside scope Data of Staff ---- ---- ----
Lgdoc Primary-
Asset
Inside scope Law specific data ----
Prpmt Primary-
Asset
Inside scope Property-specific
payment data
----
FBdat Primary- Inside scope Finance/Business
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
8RISK ASSESSMENT ON NETWORK OF CONVXYZ
Asset based data
Db &
Cudat
Inside scope Database-with-
customer-data
Vd1 (CVE-2018-1834) [H]
Db &
Stdat
Inside scope Database-with-
staff-data
Vd2 (CVE-2018-18382) [M]
Db &
lgdat
Inside scope Database-with-
legal-data
Vd3 (CVE-2018-6861) [M]
Ws Supporting-
Asset
Inside scope Web-server Web (CVE-2018-6796) [L]
FWD Supporting-
Asset
Inside scope Firewall-device (CVE-2018-0101) [M]
BeC Supporting-
Asset
Inside scope Back-end-
Computers
(CVE-2019-0555) [M]
[L]
FeC Supporting-
Asset
Inside scope Front-end-
Computers
(CVE-2019-0555) [M]
[L]
Ro Supporting-
Asset
Inside scope Routers (CVE-2019-1653) [H]
GC Supporting-
Asset
Outside scope Guest-Computers (CVE-2019-0555)
The above table specifies the assets with their respective IDs and mentions the vulnerability levels
level with respect to the assets and vulnerability identified. It also mentions the scope of the vulnerability
for primary as well as secondary assets.
Asset based data
Db &
Cudat
Inside scope Database-with-
customer-data
Vd1 (CVE-2018-1834) [H]
Db &
Stdat
Inside scope Database-with-
staff-data
Vd2 (CVE-2018-18382) [M]
Db &
lgdat
Inside scope Database-with-
legal-data
Vd3 (CVE-2018-6861) [M]
Ws Supporting-
Asset
Inside scope Web-server Web (CVE-2018-6796) [L]
FWD Supporting-
Asset
Inside scope Firewall-device (CVE-2018-0101) [M]
BeC Supporting-
Asset
Inside scope Back-end-
Computers
(CVE-2019-0555) [M]
[L]
FeC Supporting-
Asset
Inside scope Front-end-
Computers
(CVE-2019-0555) [M]
[L]
Ro Supporting-
Asset
Inside scope Routers (CVE-2019-1653) [H]
GC Supporting-
Asset
Outside scope Guest-Computers (CVE-2019-0555)
The above table specifies the assets with their respective IDs and mentions the vulnerability levels
level with respect to the assets and vulnerability identified. It also mentions the scope of the vulnerability
for primary as well as secondary assets.

9RISK ASSESSMENT ON NETWORK OF CONVXYZ
i. Likelihood
Case 1: Db & Cudat Thk
RISK = LIKELIHOOD x IMPACT
LIKELIHOOD = Threat (attractiveness) * Vulnerability
Likelihood of Db & Cudat Thk= Threat attractiveness (H) * Vulnerability level (H)
= High * High = High
Case 2: Db & Cudat Tsf
Likelihood of Db & Cudat Tsf = Threat attractiveness (L) * Vulnerability level (H)
= Low * High = Medium
ii. Impact
Case 1: Db & Cudat Thk
Impact is High (H) since hackers can successfully attack the Databases and access the Customer information
along with legal information related to the associated properties.
Risk = Likelihood (High) * Impact (High) = High * High = High
Case 2: Db & Cudat Tsf
Impact is High (H) since attacks from staff computers can easily compromise databases and access the
Customer information along with legal information related to the associated properties.
Risk = Likelihood (Medium) * Impact (High) = Medium * High = Medium
i. Likelihood
Case 1: Db & Cudat Thk
RISK = LIKELIHOOD x IMPACT
LIKELIHOOD = Threat (attractiveness) * Vulnerability
Likelihood of Db & Cudat Thk= Threat attractiveness (H) * Vulnerability level (H)
= High * High = High
Case 2: Db & Cudat Tsf
Likelihood of Db & Cudat Tsf = Threat attractiveness (L) * Vulnerability level (H)
= Low * High = Medium
ii. Impact
Case 1: Db & Cudat Thk
Impact is High (H) since hackers can successfully attack the Databases and access the Customer information
along with legal information related to the associated properties.
Risk = Likelihood (High) * Impact (High) = High * High = High
Case 2: Db & Cudat Tsf
Impact is High (H) since attacks from staff computers can easily compromise databases and access the
Customer information along with legal information related to the associated properties.
Risk = Likelihood (Medium) * Impact (High) = Medium * High = Medium
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
10RISK ASSESSMENT ON NETWORK OF CONVXYZ
Impact Table Specifications
Risk Description Impact
DDoS Attack Targets the Firewall. High
Botnet Attack Targets and hijacks network
routers.
Severe
Phishing Gathers sensitive user
information by techniques like
cookie tampering.
Medium
Social Engineering Gathers sensitive user data by
baiting users open malicious
content.
Medium
Excess Privileges Misuse of database privileges to
serve personal interests.
High
Bypass Attack Hacking systems by exploiting
loopholes in user verification
process.
Severe
Malwares Malicious applications that infect
systems and cause damages.
High
CVE-2018-0101 A firewall exploit which drains
security resources leading to
denial of service.
High
CVE-2019-1653 Gains control and steals router
configuration and diagnostic
data.
High
CVE-2019-0190 Sends the mod_ssl handler into a Medium
Impact Table Specifications
Risk Description Impact
DDoS Attack Targets the Firewall. High
Botnet Attack Targets and hijacks network
routers.
Severe
Phishing Gathers sensitive user
information by techniques like
cookie tampering.
Medium
Social Engineering Gathers sensitive user data by
baiting users open malicious
content.
Medium
Excess Privileges Misuse of database privileges to
serve personal interests.
High
Bypass Attack Hacking systems by exploiting
loopholes in user verification
process.
Severe
Malwares Malicious applications that infect
systems and cause damages.
High
CVE-2018-0101 A firewall exploit which drains
security resources leading to
denial of service.
High
CVE-2019-1653 Gains control and steals router
configuration and diagnostic
data.
High
CVE-2019-0190 Sends the mod_ssl handler into a Medium
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
11RISK ASSESSMENT ON NETWORK OF CONVXYZ
loop leading to denial of service.
CVE-2018-6789 Used for remotely executing
arbitrary codes of malicious
intent.
High
CVE-2018-1834 Allows local users to escalate
privileges to root through a
symbolic link attack.
Severe
CVE-2018-16875 Hogs CPU resources leading to
DoS.
High
CVE-2019-0555 Data theft, file tampering and
performance loss.
Medium
The above table describes the possible threats and vulnerabilities for the assets and mentions the
impact these risks can have on these assets.
loop leading to denial of service.
CVE-2018-6789 Used for remotely executing
arbitrary codes of malicious
intent.
High
CVE-2018-1834 Allows local users to escalate
privileges to root through a
symbolic link attack.
Severe
CVE-2018-16875 Hogs CPU resources leading to
DoS.
High
CVE-2019-0555 Data theft, file tampering and
performance loss.
Medium
The above table describes the possible threats and vulnerabilities for the assets and mentions the
impact these risks can have on these assets.
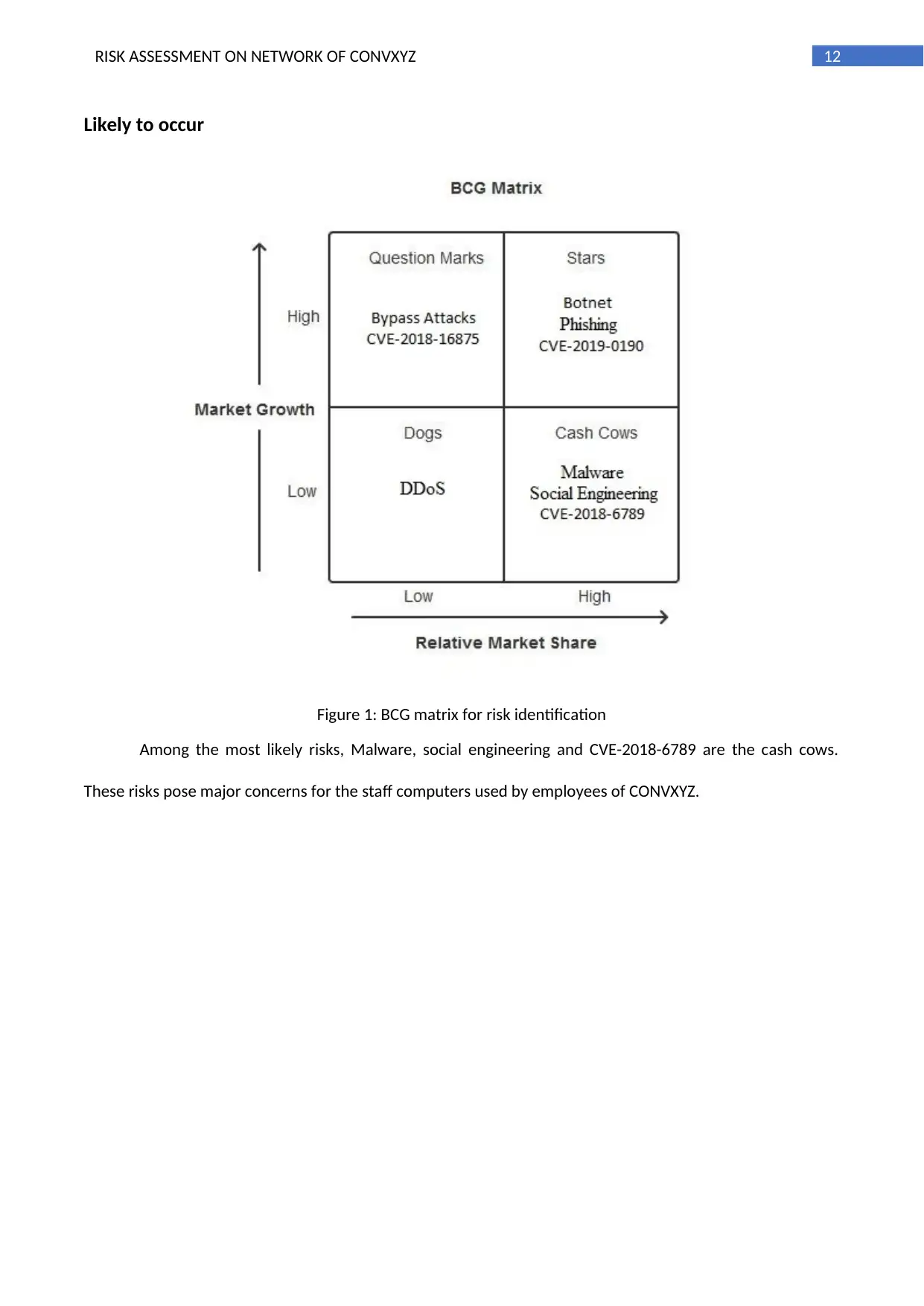
12RISK ASSESSMENT ON NETWORK OF CONVXYZ
Likely to occur
Figure 1: BCG matrix for risk identification
Among the most likely risks, Malware, social engineering and CVE-2018-6789 are the cash cows.
These risks pose major concerns for the staff computers used by employees of CONVXYZ.
Likely to occur
Figure 1: BCG matrix for risk identification
Among the most likely risks, Malware, social engineering and CVE-2018-6789 are the cash cows.
These risks pose major concerns for the staff computers used by employees of CONVXYZ.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




