Information System Risk Assessment and Analysis for VIC Government
VerifiedAdded on 2020/02/24
|14
|3488
|113
Report
AI Summary
This report presents a risk assessment and analysis of the information system used by the VIC government. It begins with an illustration of security risks and threats, categorizing them into accidental and deliberate types, as well as internal and external threats. The report then details the components of a risk diagram, classifying risk exposure areas based on their potential impact. A comparison and ranking of accidental and deliberate threats is provided, followed by a discussion of security and risk management challenges faced by the VIC government. The document further explores the differences between risk and uncertainty, outlines risk mitigation and management strategies, and concludes with a summary of key findings. The report aims to provide a comprehensive understanding of the risks associated with information systems and suggests strategies for effective risk management within the VIC government. It includes a diagram and a table to support the analysis.

Running head: RISK ASSESSMENT AND ANALYSIS
Risk Assessment and Analysis
Name of the Student:
Student ID:
Name of the University:
Author’s note:
Risk Assessment and Analysis
Name of the Student:
Student ID:
Name of the University:
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction......................................................................................................................................3
1. Illustration of Security Risks and Threats in VIC Government..................................................4
2. Explanation of the Diagram and Categorization of Risk Factors................................................4
2.1 Description of the components of diagram............................................................................4
2.2 Classification of Risk Exposure Areas..................................................................................7
3. Comparison and Ranking of Accidental and Deliberate Threats................................................8
4. Security and Risk Management Challenges for VIC government...............................................9
5. Comparing Risk and Uncertainty..............................................................................................10
6. Risk Mitigation and Management.............................................................................................11
Conclusion.....................................................................................................................................12
References......................................................................................................................................13
Introduction......................................................................................................................................3
1. Illustration of Security Risks and Threats in VIC Government..................................................4
2. Explanation of the Diagram and Categorization of Risk Factors................................................4
2.1 Description of the components of diagram............................................................................4
2.2 Classification of Risk Exposure Areas..................................................................................7
3. Comparison and Ranking of Accidental and Deliberate Threats................................................8
4. Security and Risk Management Challenges for VIC government...............................................9
5. Comparing Risk and Uncertainty..............................................................................................10
6. Risk Mitigation and Management.............................................................................................11
Conclusion.....................................................................................................................................12
References......................................................................................................................................13

Introduction
The development of the information system is very helpful for integrating the
development of the operations for the organization. According to Healey (2016), it is very
helpful for integrating the advanced processes of VIC government for forming the effective and
improved system integration of the organization. The system developed would help in forming
the supportive development of the operations and implicit development of faster and effective
information processing in the organization. The systematic flow of the information and ease of
operations is another major benefit of implementing the information system in VIC.
The following report had been developed for integrating the benefit of risk assessment in
information system. The case of VIC Australian Government had been considered for classifying
the factors of risk and develops the effective and improved functions within the organization.
The various threats of using the information system in VIC government would be classified into
their exposure areas and analysed. The analytical comparison of internal and external risk factors
would be helpful for forming the risk prioritization. The risk assessment and mitigation strategies
are also highlighted in the report so that VIC Government can implement such strategies for
getting the benefit of secured and error-free information system.
The development of the information system is very helpful for integrating the
development of the operations for the organization. According to Healey (2016), it is very
helpful for integrating the advanced processes of VIC government for forming the effective and
improved system integration of the organization. The system developed would help in forming
the supportive development of the operations and implicit development of faster and effective
information processing in the organization. The systematic flow of the information and ease of
operations is another major benefit of implementing the information system in VIC.
The following report had been developed for integrating the benefit of risk assessment in
information system. The case of VIC Australian Government had been considered for classifying
the factors of risk and develops the effective and improved functions within the organization.
The various threats of using the information system in VIC government would be classified into
their exposure areas and analysed. The analytical comparison of internal and external risk factors
would be helpful for forming the risk prioritization. The risk assessment and mitigation strategies
are also highlighted in the report so that VIC Government can implement such strategies for
getting the benefit of secured and error-free information system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
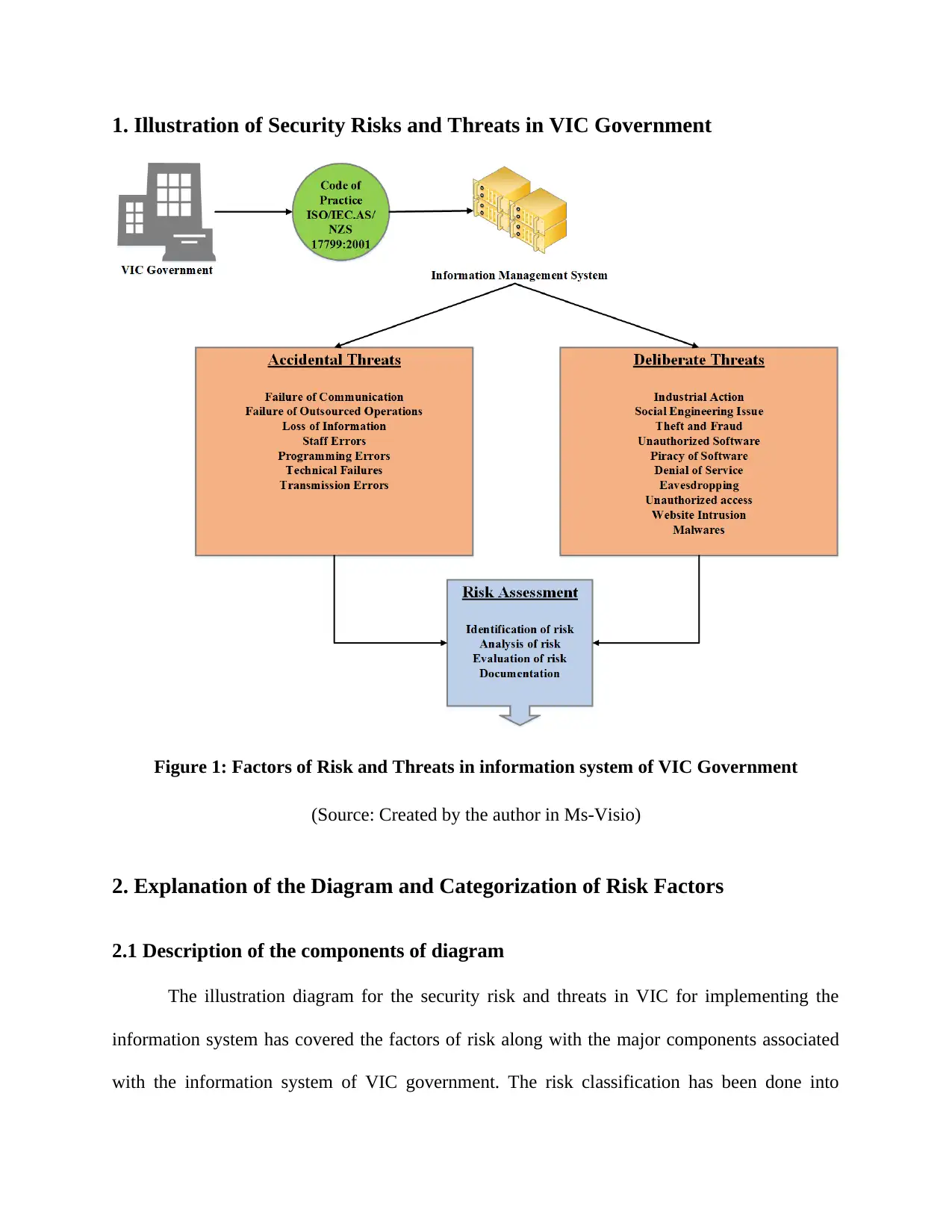
1. Illustration of Security Risks and Threats in VIC Government
Figure 1: Factors of Risk and Threats in information system of VIC Government
(Source: Created by the author in Ms-Visio)
2. Explanation of the Diagram and Categorization of Risk Factors
2.1 Description of the components of diagram
The illustration diagram for the security risk and threats in VIC for implementing the
information system has covered the factors of risk along with the major components associated
with the information system of VIC government. The risk classification has been done into
Figure 1: Factors of Risk and Threats in information system of VIC Government
(Source: Created by the author in Ms-Visio)
2. Explanation of the Diagram and Categorization of Risk Factors
2.1 Description of the components of diagram
The illustration diagram for the security risk and threats in VIC for implementing the
information system has covered the factors of risk along with the major components associated
with the information system of VIC government. The risk classification has been done into
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

accidental and deliberate threats in the diagram. However, these risks can be divided into internal
and external threats too. The description of the diagram has been given in the following points,
VIC government: The VIC government is the most important factor that comprises of
the owners of the information system. The storage of the information, data processing, system
implementation and other major activities are all done by the users in VIC government (Von
Solms & Van Niekerk, 2013). The VIC government is the organization that has the supreme
rights and control of the information and data of the information system. The users of the
information system are the members of the VIC government that operates and access the
information stored in the system.
Information Management System: Information Management System comprises of the
information storage system for the VIC government and it helps in managing the flow of the data
and information within the organization. According to Bommer, Crowley and Pinho (2015), the
users would have to be able to access the information management system for easing the flow of
the information and develop the effective information processing for the VIC government. The
effective and smart management of the information have been possible due to the implication of
the information management system.
Codes of Practices: The Code of Practices is a set of norm that is followed by the users
for the information system. The code of practices would comply the following of
ISO/IEC.AC/AZS 17799:2001 as declared by the ACS code of ethics. The practices would
declare that the information system and its content would not be used for any personal use and
the privacy of an individual would not be attacked by intruding or misusing the information
stored in the information system.
and external threats too. The description of the diagram has been given in the following points,
VIC government: The VIC government is the most important factor that comprises of
the owners of the information system. The storage of the information, data processing, system
implementation and other major activities are all done by the users in VIC government (Von
Solms & Van Niekerk, 2013). The VIC government is the organization that has the supreme
rights and control of the information and data of the information system. The users of the
information system are the members of the VIC government that operates and access the
information stored in the system.
Information Management System: Information Management System comprises of the
information storage system for the VIC government and it helps in managing the flow of the data
and information within the organization. According to Bommer, Crowley and Pinho (2015), the
users would have to be able to access the information management system for easing the flow of
the information and develop the effective information processing for the VIC government. The
effective and smart management of the information have been possible due to the implication of
the information management system.
Codes of Practices: The Code of Practices is a set of norm that is followed by the users
for the information system. The code of practices would comply the following of
ISO/IEC.AC/AZS 17799:2001 as declared by the ACS code of ethics. The practices would
declare that the information system and its content would not be used for any personal use and
the privacy of an individual would not be attacked by intruding or misusing the information
stored in the information system.

Risks and Threats: There are a number of factors of risk and threat for the
implementation of the information system in VIC government. The security risk and threats in
VIC for implementing the information system has covered the factors of risk along with the
major components associated with the information system of VIC government. The risk
classification has been done into accidental and deliberate threats in the diagram (Bommer,
Crowley & Pinho, 2015). These threats are being the major factor that can harm the development
of the information system in the organization of VIC government. The risk factors would have
been a major factor for harming the flow of information in the organization.
Accidental Threats: The accidental threats can be defined as those factors of risk that
have aroused without any specific motive of gain (Alcorn, Good & Pain, 2013). Accidental
threats are formed for harming the flow of information and resulting in the development of the
some hindrances in the processing of the information at VIC government. The accidental threats
of implementing the information system in VIC includes failure of communication, failure of
outsourced operations, loss of information, staff errors, programming errors, technical failures,
and transmission errors.
Deliberate Threats: The deliberate threats can be defined as those factors of risk that
have been done with full intention and purpose (Von Solms & Van Niekerk, 2013). This type of
threat is more crucial and has more impact on the operations of the organization. The deliberate
threats have been aroused especially either for harming the users or benefitting the attacker. The
deliberate threats of implementing the information system in VIC includes industrial action,
social engineering issue, theft and fraud, unauthorized software, piracy of software, denial of
service, eavesdropping, unauthorized access, website intrusion, and malwares.
implementation of the information system in VIC government. The security risk and threats in
VIC for implementing the information system has covered the factors of risk along with the
major components associated with the information system of VIC government. The risk
classification has been done into accidental and deliberate threats in the diagram (Bommer,
Crowley & Pinho, 2015). These threats are being the major factor that can harm the development
of the information system in the organization of VIC government. The risk factors would have
been a major factor for harming the flow of information in the organization.
Accidental Threats: The accidental threats can be defined as those factors of risk that
have aroused without any specific motive of gain (Alcorn, Good & Pain, 2013). Accidental
threats are formed for harming the flow of information and resulting in the development of the
some hindrances in the processing of the information at VIC government. The accidental threats
of implementing the information system in VIC includes failure of communication, failure of
outsourced operations, loss of information, staff errors, programming errors, technical failures,
and transmission errors.
Deliberate Threats: The deliberate threats can be defined as those factors of risk that
have been done with full intention and purpose (Von Solms & Van Niekerk, 2013). This type of
threat is more crucial and has more impact on the operations of the organization. The deliberate
threats have been aroused especially either for harming the users or benefitting the attacker. The
deliberate threats of implementing the information system in VIC includes industrial action,
social engineering issue, theft and fraud, unauthorized software, piracy of software, denial of
service, eavesdropping, unauthorized access, website intrusion, and malwares.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

External and Internal Threats: Apart from accidental and deliberate classification of
the risk factors, the risk and threats of the security in implementing the information system at
VIC government can be classified into External and Internal threat factors (Lam, 2014). The
factors of risk in the implementation of the information system in VIC government includes
failure of communication, failure of outsourced operations, loss of information, staff errors,
programming errors, technical failures, transmission errors, industrial action, social engineering
issue, theft and fraud, unauthorized software, piracy of software, denial of service,
eavesdropping, unauthorized access, website intrusion, and malwares. Man et al. (2013) stated
that the external threat factors define those factors of risk and threat that have been impacting the
information system from external source. These factors have more critical impact on the
development of the operations and significance for harming the flow of operations. The external
factors of risk in VIC information system are programming errors, technical failures, and
transmission errors, denial of service, eavesdropping, unauthorized access, website intrusion, and
malwares. The internal factors are those factors of risk and threat that have been impacting the
information system due to the internal combustion (Alcorn, Good & Pain, 2013). These factors
have comparatively lower impact on the operations of the information system of VIC
government. The internal factors of risk in VIC information system are failure of
communication, failure of outsourced operations, loss of information, staff errors, industrial
action, social engineering issue, theft and fraud, unauthorized software, and piracy of software.
2.2 Classification of Risk Exposure Areas
The risk exposure areas are the factors of risk being classified in the terms of their impact
on the operations of information system at VIC. The risk exposure areas have been classified into
high risk exposure areas, medium risk exposure areas, medium low risk exposure areas, and low
the risk factors, the risk and threats of the security in implementing the information system at
VIC government can be classified into External and Internal threat factors (Lam, 2014). The
factors of risk in the implementation of the information system in VIC government includes
failure of communication, failure of outsourced operations, loss of information, staff errors,
programming errors, technical failures, transmission errors, industrial action, social engineering
issue, theft and fraud, unauthorized software, piracy of software, denial of service,
eavesdropping, unauthorized access, website intrusion, and malwares. Man et al. (2013) stated
that the external threat factors define those factors of risk and threat that have been impacting the
information system from external source. These factors have more critical impact on the
development of the operations and significance for harming the flow of operations. The external
factors of risk in VIC information system are programming errors, technical failures, and
transmission errors, denial of service, eavesdropping, unauthorized access, website intrusion, and
malwares. The internal factors are those factors of risk and threat that have been impacting the
information system due to the internal combustion (Alcorn, Good & Pain, 2013). These factors
have comparatively lower impact on the operations of the information system of VIC
government. The internal factors of risk in VIC information system are failure of
communication, failure of outsourced operations, loss of information, staff errors, industrial
action, social engineering issue, theft and fraud, unauthorized software, and piracy of software.
2.2 Classification of Risk Exposure Areas
The risk exposure areas are the factors of risk being classified in the terms of their impact
on the operations of information system at VIC. The risk exposure areas have been classified into
high risk exposure areas, medium risk exposure areas, medium low risk exposure areas, and low
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

risk exposure areas (Lam, 2014). The High Risk Exposure Areas can be explained as those
factors of risk that have serious concerns of effecting the operations of the information and
would form catastrophic impact for VIC government. It includes the external risk factors like
data theft, intrusion, malware, and phishing. The VIC government has no control over these
issues of risk and threat. The Medium Risk Exposure Areas can be explained as those factors
of risk that have a considerable amount of impact (less than high risk exposure areas) and it
would form major impact on the operations of information system at VIC government. The
factors of medium risk exposure areas are data misinterpretation, issues of design, or any other
technical related issues of software (Man et al., 2013). The Medium Low Risk Exposure Areas
can be defined as those factors that have minimal impact on the operations of the information
system in VIC government. The medium low risk exposure areas would be easily sorted by using
monitoring and control strategies. The factors of medium low risk exposure areas are integration
issue, data incompatibility, and wrong data entry. The Low Risk Exposure Areas can be
defined as those factors that have no impact on the operations of the information system in VIC
government (Bommer, Crowley & Pinho, 2015). These factors do not form any impact on the
operations of the information system. The user generated errors and issues of social engineering
are classified under low risk exposure areas.
3. Comparison and Ranking of Accidental and Deliberate Threats
The comparison of the accidental and deliberate threat for the implementation of the
information system within the organization had been given in the table below,
Deliberate Threats Accidental Threats
factors of risk that have serious concerns of effecting the operations of the information and
would form catastrophic impact for VIC government. It includes the external risk factors like
data theft, intrusion, malware, and phishing. The VIC government has no control over these
issues of risk and threat. The Medium Risk Exposure Areas can be explained as those factors
of risk that have a considerable amount of impact (less than high risk exposure areas) and it
would form major impact on the operations of information system at VIC government. The
factors of medium risk exposure areas are data misinterpretation, issues of design, or any other
technical related issues of software (Man et al., 2013). The Medium Low Risk Exposure Areas
can be defined as those factors that have minimal impact on the operations of the information
system in VIC government. The medium low risk exposure areas would be easily sorted by using
monitoring and control strategies. The factors of medium low risk exposure areas are integration
issue, data incompatibility, and wrong data entry. The Low Risk Exposure Areas can be
defined as those factors that have no impact on the operations of the information system in VIC
government (Bommer, Crowley & Pinho, 2015). These factors do not form any impact on the
operations of the information system. The user generated errors and issues of social engineering
are classified under low risk exposure areas.
3. Comparison and Ranking of Accidental and Deliberate Threats
The comparison of the accidental and deliberate threat for the implementation of the
information system within the organization had been given in the table below,
Deliberate Threats Accidental Threats
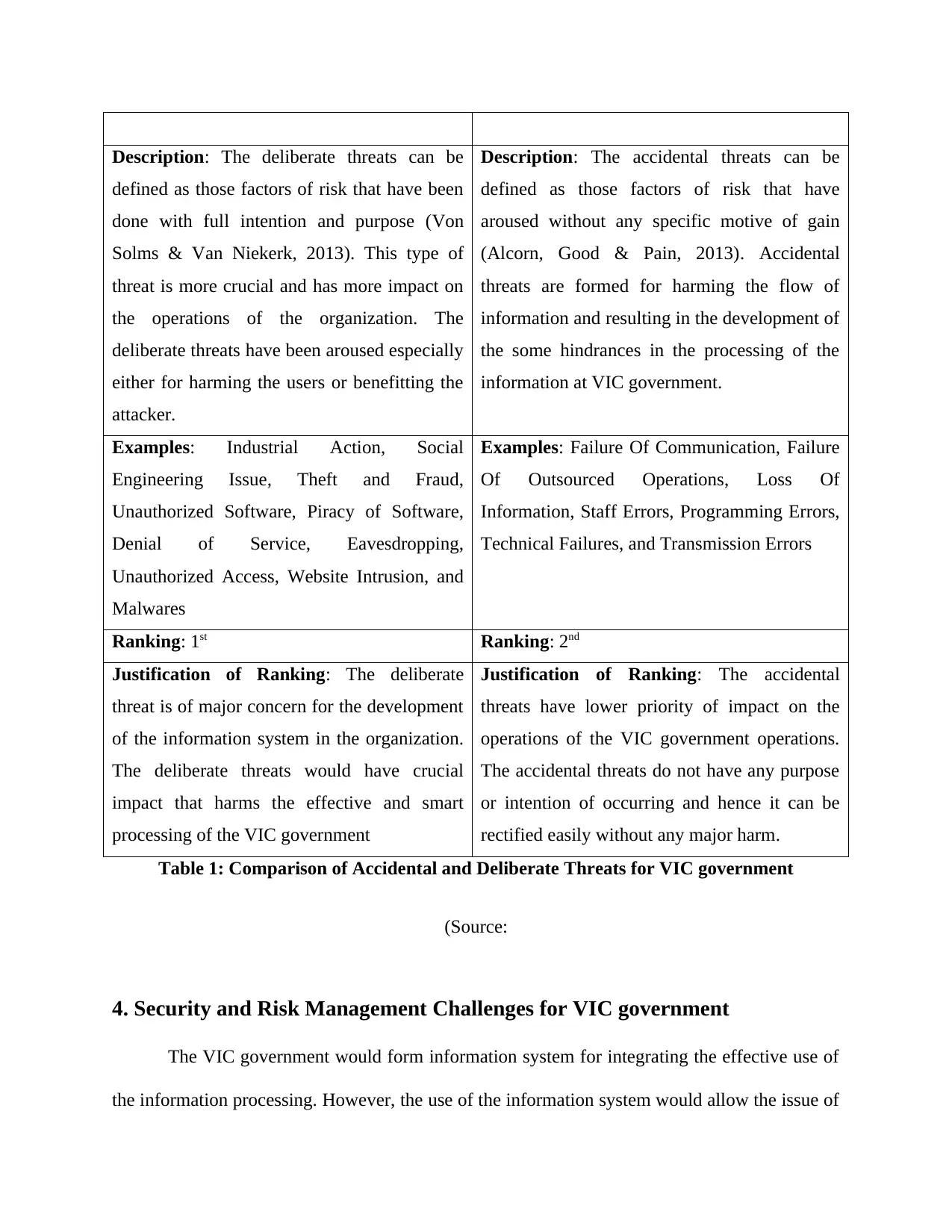
Description: The deliberate threats can be
defined as those factors of risk that have been
done with full intention and purpose (Von
Solms & Van Niekerk, 2013). This type of
threat is more crucial and has more impact on
the operations of the organization. The
deliberate threats have been aroused especially
either for harming the users or benefitting the
attacker.
Description: The accidental threats can be
defined as those factors of risk that have
aroused without any specific motive of gain
(Alcorn, Good & Pain, 2013). Accidental
threats are formed for harming the flow of
information and resulting in the development of
the some hindrances in the processing of the
information at VIC government.
Examples: Industrial Action, Social
Engineering Issue, Theft and Fraud,
Unauthorized Software, Piracy of Software,
Denial of Service, Eavesdropping,
Unauthorized Access, Website Intrusion, and
Malwares
Examples: Failure Of Communication, Failure
Of Outsourced Operations, Loss Of
Information, Staff Errors, Programming Errors,
Technical Failures, and Transmission Errors
Ranking: 1st Ranking: 2nd
Justification of Ranking: The deliberate
threat is of major concern for the development
of the information system in the organization.
The deliberate threats would have crucial
impact that harms the effective and smart
processing of the VIC government
Justification of Ranking: The accidental
threats have lower priority of impact on the
operations of the VIC government operations.
The accidental threats do not have any purpose
or intention of occurring and hence it can be
rectified easily without any major harm.
Table 1: Comparison of Accidental and Deliberate Threats for VIC government
(Source:
4. Security and Risk Management Challenges for VIC government
The VIC government would form information system for integrating the effective use of
the information processing. However, the use of the information system would allow the issue of
defined as those factors of risk that have been
done with full intention and purpose (Von
Solms & Van Niekerk, 2013). This type of
threat is more crucial and has more impact on
the operations of the organization. The
deliberate threats have been aroused especially
either for harming the users or benefitting the
attacker.
Description: The accidental threats can be
defined as those factors of risk that have
aroused without any specific motive of gain
(Alcorn, Good & Pain, 2013). Accidental
threats are formed for harming the flow of
information and resulting in the development of
the some hindrances in the processing of the
information at VIC government.
Examples: Industrial Action, Social
Engineering Issue, Theft and Fraud,
Unauthorized Software, Piracy of Software,
Denial of Service, Eavesdropping,
Unauthorized Access, Website Intrusion, and
Malwares
Examples: Failure Of Communication, Failure
Of Outsourced Operations, Loss Of
Information, Staff Errors, Programming Errors,
Technical Failures, and Transmission Errors
Ranking: 1st Ranking: 2nd
Justification of Ranking: The deliberate
threat is of major concern for the development
of the information system in the organization.
The deliberate threats would have crucial
impact that harms the effective and smart
processing of the VIC government
Justification of Ranking: The accidental
threats have lower priority of impact on the
operations of the VIC government operations.
The accidental threats do not have any purpose
or intention of occurring and hence it can be
rectified easily without any major harm.
Table 1: Comparison of Accidental and Deliberate Threats for VIC government
(Source:
4. Security and Risk Management Challenges for VIC government
The VIC government would form information system for integrating the effective use of
the information processing. However, the use of the information system would allow the issue of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

risk and threats for the organization. The risk and threats would form the major issues in forming
the effective operations of the VIC government. The challenges of the VIC government are
explained below,
Operational Challenges: The implementation of the information system would have to
face the issues of operation integration for VIC government (Rasmussen, 2013). The change of
the platform to the information system would result in forming some effective issues in
operations. The challenges of the operation would result in forming the major hindrance for
integrating the operations of the VIC organization. The operations of the VIC government would
have to face the major issues in forming the systematic and development operations.
Security Challenges: Man et al. (2013) have pointed that the security issues are the
major factor of challenge for the implementation of the information system at VIC government.
The risk and threats of the security in implementing the information system at VIC government
includes failure of communication, failure of outsourced operations, loss of information, staff
errors, programming errors, technical failures, transmission errors, industrial action, social
engineering issue, theft and fraud, unauthorized software, piracy of software, denial of service,
eavesdropping, unauthorized access, website intrusion, and malwares.
5. Comparing Risk and Uncertainty
Silbey (2013) has defined the risk as those factors that have major impact (either positive
or negative) on the operations of the organization and it results in harming the operations of the
organization. The improved operations of the organization would result in forming the major
hindrance for the operations of the VIC information system operations. Among the threats of the
implementation of the information system at VIC, the technical failures, transmission errors,
the effective operations of the VIC government. The challenges of the VIC government are
explained below,
Operational Challenges: The implementation of the information system would have to
face the issues of operation integration for VIC government (Rasmussen, 2013). The change of
the platform to the information system would result in forming some effective issues in
operations. The challenges of the operation would result in forming the major hindrance for
integrating the operations of the VIC organization. The operations of the VIC government would
have to face the major issues in forming the systematic and development operations.
Security Challenges: Man et al. (2013) have pointed that the security issues are the
major factor of challenge for the implementation of the information system at VIC government.
The risk and threats of the security in implementing the information system at VIC government
includes failure of communication, failure of outsourced operations, loss of information, staff
errors, programming errors, technical failures, transmission errors, industrial action, social
engineering issue, theft and fraud, unauthorized software, piracy of software, denial of service,
eavesdropping, unauthorized access, website intrusion, and malwares.
5. Comparing Risk and Uncertainty
Silbey (2013) has defined the risk as those factors that have major impact (either positive
or negative) on the operations of the organization and it results in harming the operations of the
organization. The improved operations of the organization would result in forming the major
hindrance for the operations of the VIC information system operations. Among the threats of the
implementation of the information system at VIC, the technical failures, transmission errors,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

theft and fraud, unauthorized access, website intrusion, and malwares are the factors of risk for
information system implementation.
Covello et al. (2013) has explained uncertainty as the unpredictability for the
implementation of the information processing. The VIC government would have to face the issue
of unsure event and outcome for the development of the operation. The uncertainty is a different
concept from the risk factor and it had formed the outcome of the operations being not estimated.
Among the threats of the implementation of the information system at VIC, thefailure of
communication, failure of outsourced operations, transmission errors, industrial action, and
social engineering issue.
6. Risk Mitigation and Management
The risk mitigation and management plays a significant role in the development of
effective operations for the organization. The development of the risk mitigation would imply the
effective and improved operations of the organization. The risk mitigation and management
includes the following steps,
Risk identification: The identification of the risk factors would be the first step in
developing the solution to the operations of the risk in VIC government. The identification of the
risk would form the analysis of the impact of the factors on the operations of the VIC
government.
Risk Analysis: The risk analysis would help in analysis of the impact and degree of
influence of risk on the factors of the operations of VIC government. The risk analysis would
help in prioritizing the risk for forming the plan of operations.
information system implementation.
Covello et al. (2013) has explained uncertainty as the unpredictability for the
implementation of the information processing. The VIC government would have to face the issue
of unsure event and outcome for the development of the operation. The uncertainty is a different
concept from the risk factor and it had formed the outcome of the operations being not estimated.
Among the threats of the implementation of the information system at VIC, thefailure of
communication, failure of outsourced operations, transmission errors, industrial action, and
social engineering issue.
6. Risk Mitigation and Management
The risk mitigation and management plays a significant role in the development of
effective operations for the organization. The development of the risk mitigation would imply the
effective and improved operations of the organization. The risk mitigation and management
includes the following steps,
Risk identification: The identification of the risk factors would be the first step in
developing the solution to the operations of the risk in VIC government. The identification of the
risk would form the analysis of the impact of the factors on the operations of the VIC
government.
Risk Analysis: The risk analysis would help in analysis of the impact and degree of
influence of risk on the factors of the operations of VIC government. The risk analysis would
help in prioritizing the risk for forming the plan of operations.

Risk Mitigation: The risk mitigation would include the effective development of the
operations to form the control of the systematic flow of operations. The control of the impact of
risk would be done by the implementation of the risk mitigation.
Risk Evaluation: The risk evaluation would be done for realizing the improved factors
and monitor the implemented risk mitigation strategies. The evaluation would consider the
approx development of the operations of the VIC government.
Conclusion
It can be concluded from the assignment that the report had considered the case of VIC
Australian Government and its various threats of using the information system. The description
of the diagram for the risk analysis of VIC government would comprise of information
management system, codes of practices (ISO/IEC.AC/AZS 17799:2001 as declared by the ACS
code of ethics), risks and threats, accidental threats, deliberate threats, and external and internal
threats. The risk exposure areas had been classified into high risk exposure areas, medium risk
exposure areas, medium low risk exposure areas, and low risk exposure areas. The accidental
threats have been ranked second and the deliberate threats have been ranked first while
comparing the two factors of threats. The challenges of the VIC government were Operational
Challenges and Security Challenges. The development of the risk mitigation had consisted of
risk identification, risk analysis, risk mitigation, and risk evaluation.
operations to form the control of the systematic flow of operations. The control of the impact of
risk would be done by the implementation of the risk mitigation.
Risk Evaluation: The risk evaluation would be done for realizing the improved factors
and monitor the implemented risk mitigation strategies. The evaluation would consider the
approx development of the operations of the VIC government.
Conclusion
It can be concluded from the assignment that the report had considered the case of VIC
Australian Government and its various threats of using the information system. The description
of the diagram for the risk analysis of VIC government would comprise of information
management system, codes of practices (ISO/IEC.AC/AZS 17799:2001 as declared by the ACS
code of ethics), risks and threats, accidental threats, deliberate threats, and external and internal
threats. The risk exposure areas had been classified into high risk exposure areas, medium risk
exposure areas, medium low risk exposure areas, and low risk exposure areas. The accidental
threats have been ranked second and the deliberate threats have been ranked first while
comparing the two factors of threats. The challenges of the VIC government were Operational
Challenges and Security Challenges. The development of the risk mitigation had consisted of
risk identification, risk analysis, risk mitigation, and risk evaluation.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





