ITC596 IT Risk Management: Biometrics, PETs, and WSN Network Attacks
VerifiedAdded on 2024/07/01
|14
|2633
|452
Report
AI Summary
This report provides an assessment of IT risk management, focusing on biometrics systems, privacy-enhancing technologies (PETs), and wireless sensor network (WSN) security. It begins with an overview of various biometrics systems such as Iris Recognition, Hand Geometry, and Fingerprint, detailing their advantages and disadvantages. The report then discusses PETs, including metadata with digital rights management, identity management, and encryption, highlighting their role in enhancing data privacy and security within networks. Furthermore, it examines WSN architecture, protocol stack, and potential network attacks like Denial of Service (DoS), Wormhole, and Sybil attacks, along with risk mitigation strategies. This document is available on Desklib, a platform offering a wide array of study resources for students.

ITC596
IT RISK MANAGEMENT
ASSESSMENT 2
IT RISK MANAGEMENT
ASSESSMENT 2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Part 2 Answer 2............................................................................................................................. 2
Part 2 Answer 3:............................................................................................................................ 6
Part 2 Answer 4:............................................................................................................................ 8
Reference:................................................................................................................................... 13
List of figure:
Figure 1: Iris Recognition Biometrics system.................................................................................2
Figure 2: Hand Geometry Biometrics system................................................................................ 3
Figure 3: Fingerprint Biometrics system........................................................................................ 4
Figure 4: Wireless network Sensor Node....................................................................................... 8
Figure 5: Wireless sensor network Architecture............................................................................9
Figure 6: Protocol Stack of WSN.................................................................................................. 10
List of Table:
Table 1: Iris Recognition Biometrics system Advantage and disadvantage....................................3
Table 2: Hand Geometry Biometrics system Advantage and disadvantage...................................4
Table 3: Fingerprint Biometrics system Advantage and disadvantage...........................................5
1
Part 2 Answer 2............................................................................................................................. 2
Part 2 Answer 3:............................................................................................................................ 6
Part 2 Answer 4:............................................................................................................................ 8
Reference:................................................................................................................................... 13
List of figure:
Figure 1: Iris Recognition Biometrics system.................................................................................2
Figure 2: Hand Geometry Biometrics system................................................................................ 3
Figure 3: Fingerprint Biometrics system........................................................................................ 4
Figure 4: Wireless network Sensor Node....................................................................................... 8
Figure 5: Wireless sensor network Architecture............................................................................9
Figure 6: Protocol Stack of WSN.................................................................................................. 10
List of Table:
Table 1: Iris Recognition Biometrics system Advantage and disadvantage....................................3
Table 2: Hand Geometry Biometrics system Advantage and disadvantage...................................4
Table 3: Fingerprint Biometrics system Advantage and disadvantage...........................................5
1

Part 2 Answer 2
Biometrics word creation forms the Greek word which meaning identifies the user
characteristics, behaviour, and physical activity. This is used for the authentication process in
the organization. Identification system and authentication system are another names of the
biometric system. It is two types such as Physiological Biometrics and Behavioural Biometrics.
Iris recognition, Face recognition, Hand Geometry, voice and signature recognition, and
fingerprinting are the common example of the biometric system. There is defined various types
of Biometrics system for example
Iris Recognition: it is a Biometrics system that used to recognize the user with the help of
pattern techniques. This technique is used in the mathematical process to match the iris of one
person eyes to another person's eyes. There is represented the block diagram of the Iris
Recognition Biometrics system. it used the 750mm wavelength light to search out the image
which is placed near the infrared. This allows chunking the light reflection from the eye’s cornea
and catching the picture that highpoints the iris assembly. It contained 3 phases such as
Picture capture
Trace image and the Iris optimization
identical or Storing the biometric template (Bhalerao, 2013)
Illustration: ATM Application
2
Biometrics word creation forms the Greek word which meaning identifies the user
characteristics, behaviour, and physical activity. This is used for the authentication process in
the organization. Identification system and authentication system are another names of the
biometric system. It is two types such as Physiological Biometrics and Behavioural Biometrics.
Iris recognition, Face recognition, Hand Geometry, voice and signature recognition, and
fingerprinting are the common example of the biometric system. There is defined various types
of Biometrics system for example
Iris Recognition: it is a Biometrics system that used to recognize the user with the help of
pattern techniques. This technique is used in the mathematical process to match the iris of one
person eyes to another person's eyes. There is represented the block diagram of the Iris
Recognition Biometrics system. it used the 750mm wavelength light to search out the image
which is placed near the infrared. This allows chunking the light reflection from the eye’s cornea
and catching the picture that highpoints the iris assembly. It contained 3 phases such as
Picture capture
Trace image and the Iris optimization
identical or Storing the biometric template (Bhalerao, 2013)
Illustration: ATM Application
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
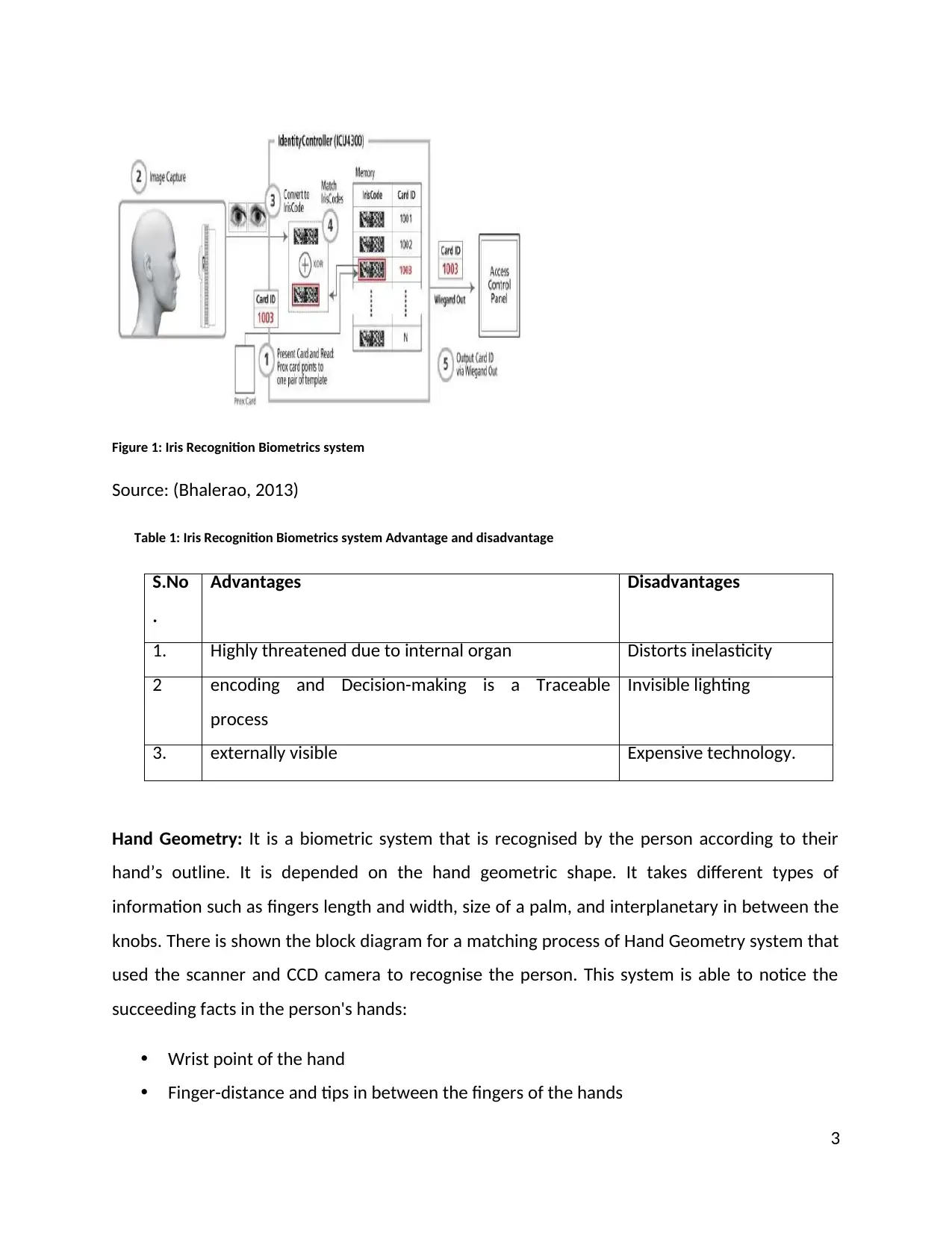
Figure 1: Iris Recognition Biometrics system
Source: (Bhalerao, 2013)
Table 1: Iris Recognition Biometrics system Advantage and disadvantage
S.No
.
Advantages Disadvantages
1. Highly threatened due to internal organ Distorts inelasticity
2 encoding and Decision-making is a Traceable
process
Invisible lighting
3. externally visible Expensive technology.
Hand Geometry: It is a biometric system that is recognised by the person according to their
hand’s outline. It is depended on the hand geometric shape. It takes different types of
information such as fingers length and width, size of a palm, and interplanetary in between the
knobs. There is shown the block diagram for a matching process of Hand Geometry system that
used the scanner and CCD camera to recognise the person. This system is able to notice the
succeeding facts in the person's hands:
Wrist point of the hand
Finger-distance and tips in between the fingers of the hands
3
Source: (Bhalerao, 2013)
Table 1: Iris Recognition Biometrics system Advantage and disadvantage
S.No
.
Advantages Disadvantages
1. Highly threatened due to internal organ Distorts inelasticity
2 encoding and Decision-making is a Traceable
process
Invisible lighting
3. externally visible Expensive technology.
Hand Geometry: It is a biometric system that is recognised by the person according to their
hand’s outline. It is depended on the hand geometric shape. It takes different types of
information such as fingers length and width, size of a palm, and interplanetary in between the
knobs. There is shown the block diagram for a matching process of Hand Geometry system that
used the scanner and CCD camera to recognise the person. This system is able to notice the
succeeding facts in the person's hands:
Wrist point of the hand
Finger-distance and tips in between the fingers of the hands
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
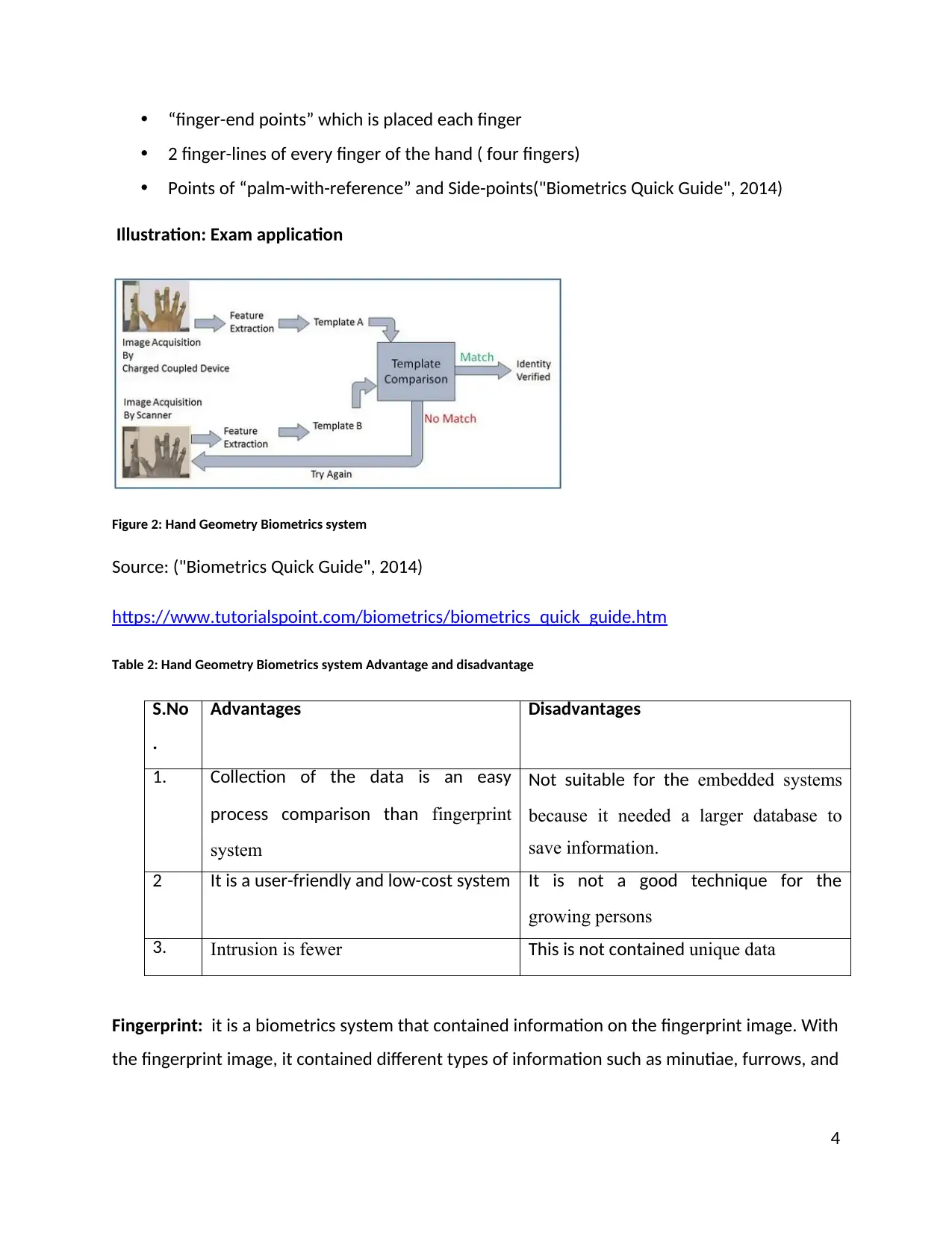
“finger-end points” which is placed each finger
2 finger-lines of every finger of the hand ( four fingers)
Points of “palm-with-reference” and Side-points("Biometrics Quick Guide", 2014)
Illustration: Exam application
Figure 2: Hand Geometry Biometrics system
Source: ("Biometrics Quick Guide", 2014)
https://www.tutorialspoint.com/biometrics/biometrics_quick_guide.htm
Table 2: Hand Geometry Biometrics system Advantage and disadvantage
S.No
.
Advantages Disadvantages
1. Collection of the data is an easy
process comparison than fingerprint
system
Not suitable for the embedded systems
because it needed a larger database to
save information.
2 It is a user-friendly and low-cost system It is not a good technique for the
growing persons
3. Intrusion is fewer This is not contained unique data
Fingerprint: it is a biometrics system that contained information on the fingerprint image. With
the fingerprint image, it contained different types of information such as minutiae, furrows, and
4
2 finger-lines of every finger of the hand ( four fingers)
Points of “palm-with-reference” and Side-points("Biometrics Quick Guide", 2014)
Illustration: Exam application
Figure 2: Hand Geometry Biometrics system
Source: ("Biometrics Quick Guide", 2014)
https://www.tutorialspoint.com/biometrics/biometrics_quick_guide.htm
Table 2: Hand Geometry Biometrics system Advantage and disadvantage
S.No
.
Advantages Disadvantages
1. Collection of the data is an easy
process comparison than fingerprint
system
Not suitable for the embedded systems
because it needed a larger database to
save information.
2 It is a user-friendly and low-cost system It is not a good technique for the
growing persons
3. Intrusion is fewer This is not contained unique data
Fingerprint: it is a biometrics system that contained information on the fingerprint image. With
the fingerprint image, it contained different types of information such as minutiae, furrows, and
4
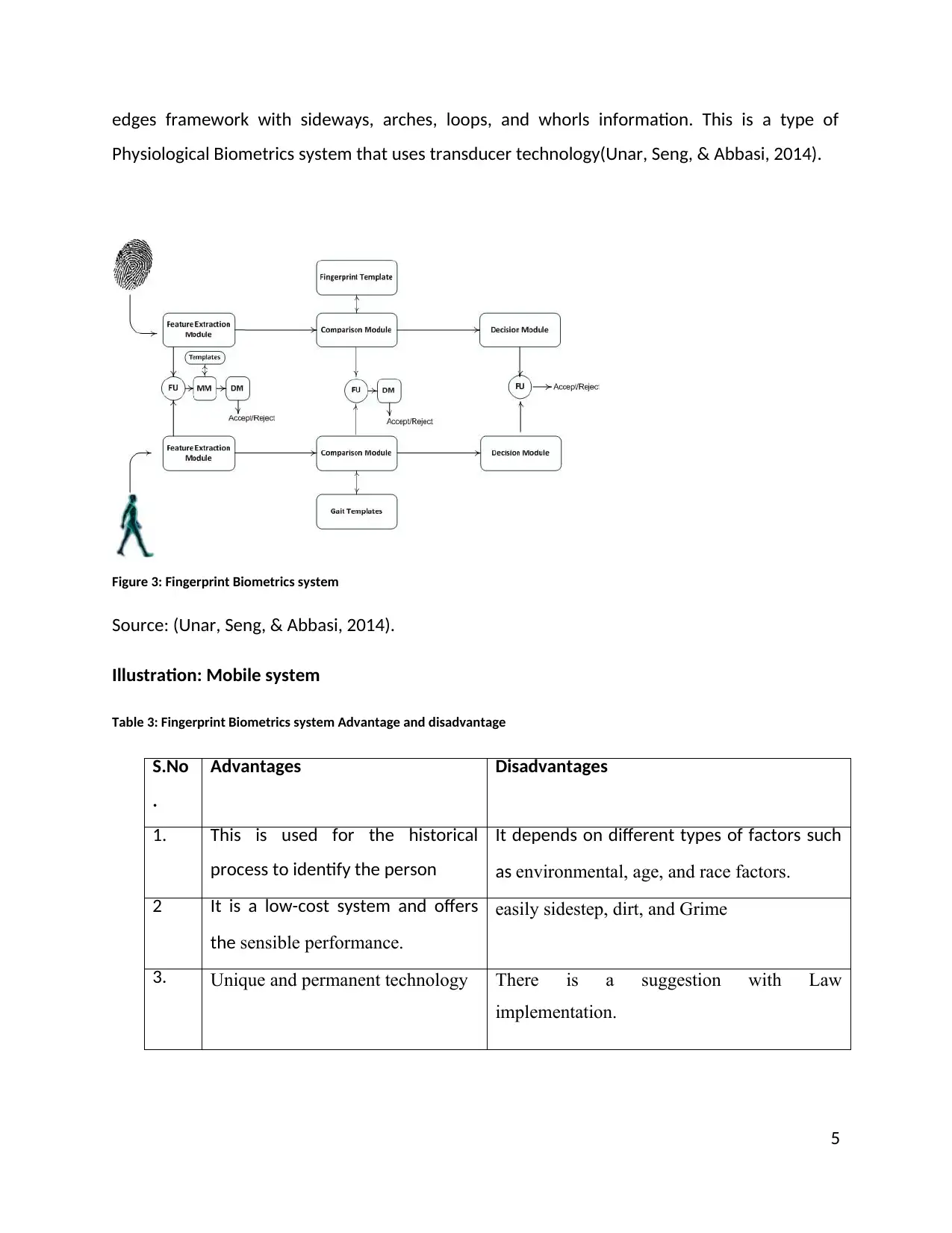
edges framework with sideways, arches, loops, and whorls information. This is a type of
Physiological Biometrics system that uses transducer technology(Unar, Seng, & Abbasi, 2014).
Figure 3: Fingerprint Biometrics system
Source: (Unar, Seng, & Abbasi, 2014).
Illustration: Mobile system
Table 3: Fingerprint Biometrics system Advantage and disadvantage
S.No
.
Advantages Disadvantages
1. This is used for the historical
process to identify the person
It depends on different types of factors such
as environmental, age, and race factors.
2 It is a low-cost system and offers
the sensible performance.
easily sidestep, dirt, and Grime
3. Unique and permanent technology There is a suggestion with Law
implementation.
5
Physiological Biometrics system that uses transducer technology(Unar, Seng, & Abbasi, 2014).
Figure 3: Fingerprint Biometrics system
Source: (Unar, Seng, & Abbasi, 2014).
Illustration: Mobile system
Table 3: Fingerprint Biometrics system Advantage and disadvantage
S.No
.
Advantages Disadvantages
1. This is used for the historical
process to identify the person
It depends on different types of factors such
as environmental, age, and race factors.
2 It is a low-cost system and offers
the sensible performance.
easily sidestep, dirt, and Grime
3. Unique and permanent technology There is a suggestion with Law
implementation.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Part 2 Answer 3:
Privacy-Enhancing Technologies is known as the ICT system that works on the information
privacy, data protection, and network security with the help of the minimising or excluding
private data. PETs avoid the unauthorized or unnecessary operation on the private data of the
network. It concentrated information system (IS) functionality which is occurring the data loss
in the network. WSN networks used the PET for recognized the human right in the network as
either implicitly or explicitly manner. In the WSN Network, this is gathering of the technologies
that appliance certified privacy integrities in order to increase and protect the privacy of the
info technology. It controls online service providers, and data transmit.
There is defined the Privacy-Enhancing Technologies that provides the network security, data
privacy and data integrity such as
1. Metadata with the Digital rights management: this is a novel PET technology. There is
used the Metadata which represents the info about the data. It also contained a
framework that recitation the semantics for the data. This process is used for the DRM
(digital right management) for the data protection in the network. PET technology is
successfully worked on the submission data in the network. It is easily differentiated
between personal information, awfully sensitive data, and general data. DRM is PET
technology that offers the high control on the network users concluded their private
info. This also offers the ACT in the network such as audibility, Controllability, and
Transparency that are represented ICA term (Integrity, Confidentiality, and Availability).
ICA is a represented privacy term in the network. As related to other PETs technology,
metadata is moderately easy to the appliance the collection of organized facts and can
be extra effective and efficient
For illustration: Whatsup, Facebook, Instagram
2. Identity Management: the Online transaction is a common process for every
organization. They want to recognize their customer so there is used in the
authentication process. During the authentication process, there is used the Identity
Management (IM) that built a trust in between agencies, organizations, and individuals.
6
Privacy-Enhancing Technologies is known as the ICT system that works on the information
privacy, data protection, and network security with the help of the minimising or excluding
private data. PETs avoid the unauthorized or unnecessary operation on the private data of the
network. It concentrated information system (IS) functionality which is occurring the data loss
in the network. WSN networks used the PET for recognized the human right in the network as
either implicitly or explicitly manner. In the WSN Network, this is gathering of the technologies
that appliance certified privacy integrities in order to increase and protect the privacy of the
info technology. It controls online service providers, and data transmit.
There is defined the Privacy-Enhancing Technologies that provides the network security, data
privacy and data integrity such as
1. Metadata with the Digital rights management: this is a novel PET technology. There is
used the Metadata which represents the info about the data. It also contained a
framework that recitation the semantics for the data. This process is used for the DRM
(digital right management) for the data protection in the network. PET technology is
successfully worked on the submission data in the network. It is easily differentiated
between personal information, awfully sensitive data, and general data. DRM is PET
technology that offers the high control on the network users concluded their private
info. This also offers the ACT in the network such as audibility, Controllability, and
Transparency that are represented ICA term (Integrity, Confidentiality, and Availability).
ICA is a represented privacy term in the network. As related to other PETs technology,
metadata is moderately easy to the appliance the collection of organized facts and can
be extra effective and efficient
For illustration: Whatsup, Facebook, Instagram
2. Identity Management: the Online transaction is a common process for every
organization. They want to recognize their customer so there is used in the
authentication process. During the authentication process, there is used the Identity
Management (IM) that built a trust in between agencies, organizations, and individuals.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

This process used three phases. In the first phase, there is the creation of an identity
that can need the discrete details such as a select certain password for the confirmation
procedure to recognize the details. The second phase is using the identification
nevertheless previously using, identifications are compulsory for the verification
procedure. The third phase is identity annulment which is second-hand to diminish the
distinctiveness theft.
For illustration: Facebook, client-server application,
3. Encryption: Encryption is also known as the PET technique (Privacy-Enhancing
Technologies) which provides the data security. It used the data encryption and
decryption process for the data protection. It converted plaintext data into an encoded
data with the help of encryption key. This data is decoded with help of decryption key
and same encryption key. Encryption process supports the end-to-end data protection
in the network. it also provides the data security during data transmission process.
Symmetric and asymmetric cyphers key are used for the encryption process and
deception process. There is also a used hash function to the completed encryption
process. Authentication, data integrity, and non-repudiation are the major benefits of
the encryption PET process. Communication, digital certificates, and file systems are
some another illustrations of the encryption.
For illustration: Services Administration system.
7
that can need the discrete details such as a select certain password for the confirmation
procedure to recognize the details. The second phase is using the identification
nevertheless previously using, identifications are compulsory for the verification
procedure. The third phase is identity annulment which is second-hand to diminish the
distinctiveness theft.
For illustration: Facebook, client-server application,
3. Encryption: Encryption is also known as the PET technique (Privacy-Enhancing
Technologies) which provides the data security. It used the data encryption and
decryption process for the data protection. It converted plaintext data into an encoded
data with the help of encryption key. This data is decoded with help of decryption key
and same encryption key. Encryption process supports the end-to-end data protection
in the network. it also provides the data security during data transmission process.
Symmetric and asymmetric cyphers key are used for the encryption process and
deception process. There is also a used hash function to the completed encryption
process. Authentication, data integrity, and non-repudiation are the major benefits of
the encryption PET process. Communication, digital certificates, and file systems are
some another illustrations of the encryption.
For illustration: Services Administration system.
7

Part 2 Answer 4:
WSN means as Wireless Sensor Networks that works on the network sensors with the help of
the wireless communication. It is important to network because WSN increases the monitoring
capability in unreachable locations and remote where is not possible to install the wired
network infrastructure. This network worked medical applications, disaster relief and
prevention, military observation, logistics tracking, environmental monitoring, intelligence
gathering, and navigation. WSN network contained a limited function with low-cost hardware
such as the sensor node, and node operation with long time periods. It also contained a
different type of problems such as the multi-hop routing, self-configuration, medium access
control, and network discovery. It is a disturbed network that makes efficient protocol design
for the network (Gascón & Yarza, 2011).
Figure 4: Wireless network Sensor Node
Source: (Gascón & Yarza, 2011)
Architecture of WSN
WSN Architecture contained a wired and wireless device which are showed in the below
diagram. This Architecture works on the OSI model principle. It is a three layers Architecture
such as client-side layers, server side, and sensor Mote network side. These sides are managed
by the cross layers which contained three sides. task management, power management, and
8
WSN means as Wireless Sensor Networks that works on the network sensors with the help of
the wireless communication. It is important to network because WSN increases the monitoring
capability in unreachable locations and remote where is not possible to install the wired
network infrastructure. This network worked medical applications, disaster relief and
prevention, military observation, logistics tracking, environmental monitoring, intelligence
gathering, and navigation. WSN network contained a limited function with low-cost hardware
such as the sensor node, and node operation with long time periods. It also contained a
different type of problems such as the multi-hop routing, self-configuration, medium access
control, and network discovery. It is a disturbed network that makes efficient protocol design
for the network (Gascón & Yarza, 2011).
Figure 4: Wireless network Sensor Node
Source: (Gascón & Yarza, 2011)
Architecture of WSN
WSN Architecture contained a wired and wireless device which are showed in the below
diagram. This Architecture works on the OSI model principle. It is a three layers Architecture
such as client-side layers, server side, and sensor Mote network side. These sides are managed
by the cross layers which contained three sides. task management, power management, and
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
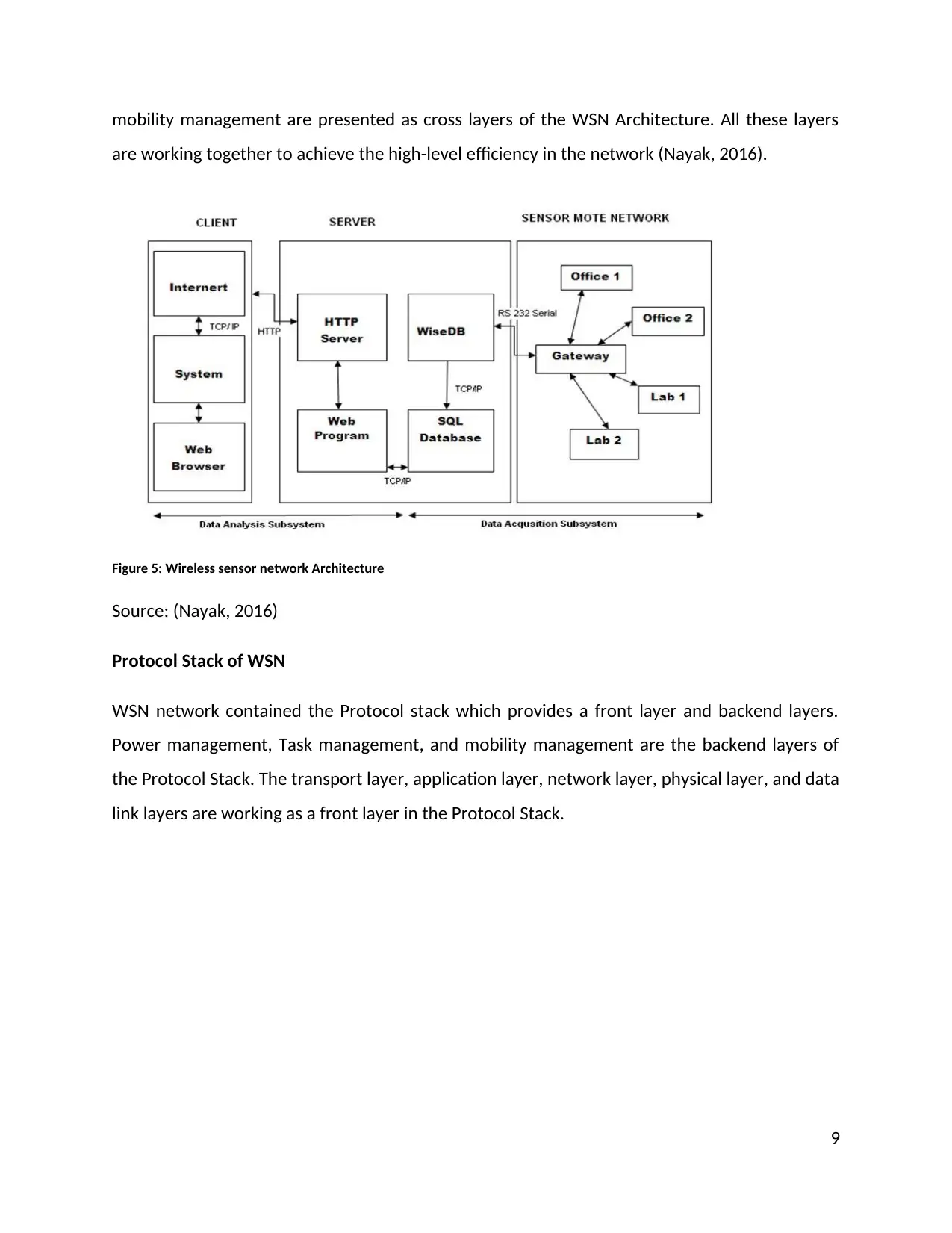
mobility management are presented as cross layers of the WSN Architecture. All these layers
are working together to achieve the high-level efficiency in the network (Nayak, 2016).
Figure 5: Wireless sensor network Architecture
Source: (Nayak, 2016)
Protocol Stack of WSN
WSN network contained the Protocol stack which provides a front layer and backend layers.
Power management, Task management, and mobility management are the backend layers of
the Protocol Stack. The transport layer, application layer, network layer, physical layer, and data
link layers are working as a front layer in the Protocol Stack.
9
are working together to achieve the high-level efficiency in the network (Nayak, 2016).
Figure 5: Wireless sensor network Architecture
Source: (Nayak, 2016)
Protocol Stack of WSN
WSN network contained the Protocol stack which provides a front layer and backend layers.
Power management, Task management, and mobility management are the backend layers of
the Protocol Stack. The transport layer, application layer, network layer, physical layer, and data
link layers are working as a front layer in the Protocol Stack.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
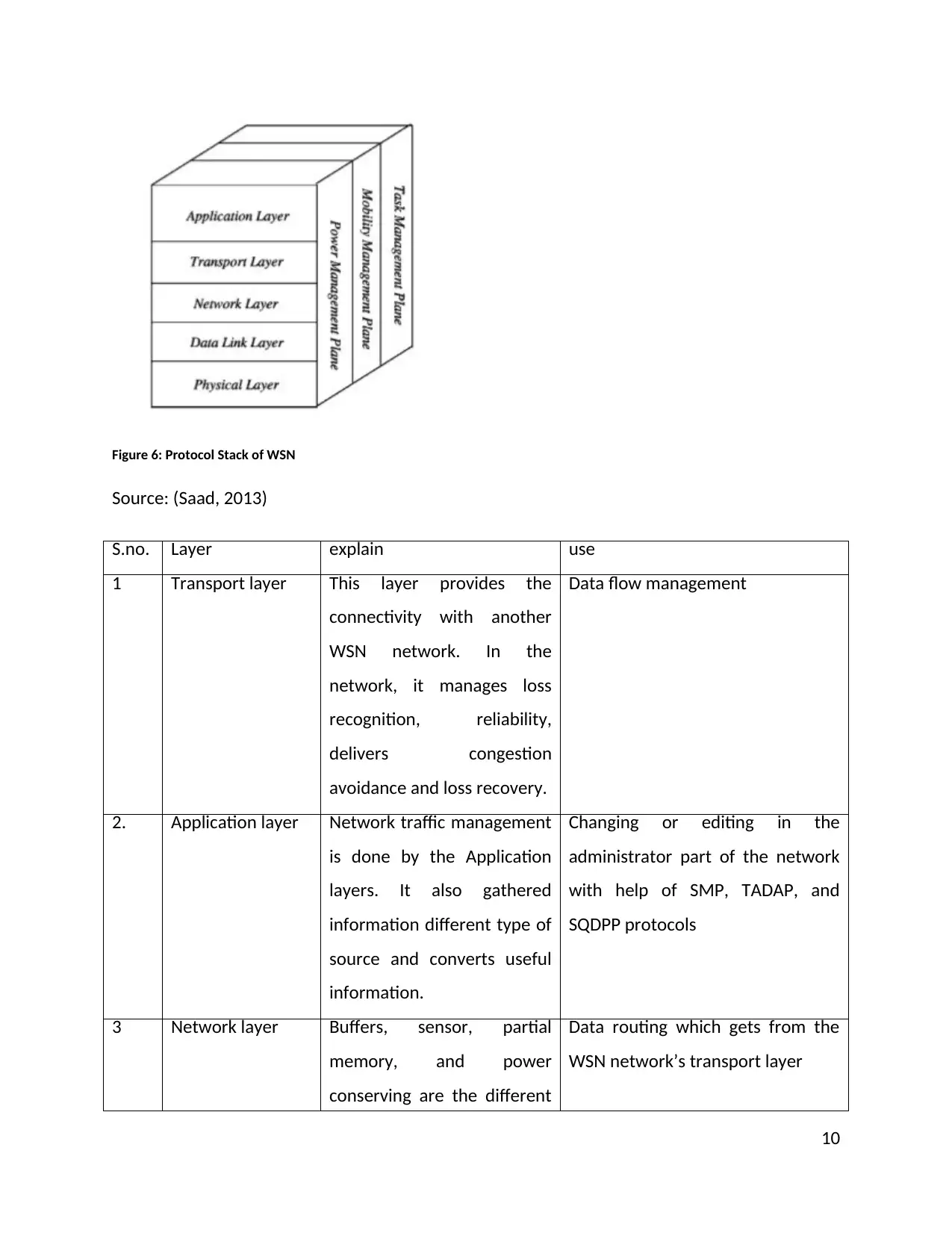
Figure 6: Protocol Stack of WSN
Source: (Saad, 2013)
S.no. Layer explain use
1 Transport layer This layer provides the
connectivity with another
WSN network. In the
network, it manages loss
recognition, reliability,
delivers congestion
avoidance and loss recovery.
Data flow management
2. Application layer Network traffic management
is done by the Application
layers. It also gathered
information different type of
source and converts useful
information.
Changing or editing in the
administrator part of the network
with help of SMP, TADAP, and
SQDPP protocols
3 Network layer Buffers, sensor, partial
memory, and power
conserving are the different
Data routing which gets from the
WSN network’s transport layer
10
Source: (Saad, 2013)
S.no. Layer explain use
1 Transport layer This layer provides the
connectivity with another
WSN network. In the
network, it manages loss
recognition, reliability,
delivers congestion
avoidance and loss recovery.
Data flow management
2. Application layer Network traffic management
is done by the Application
layers. It also gathered
information different type of
source and converts useful
information.
Changing or editing in the
administrator part of the network
with help of SMP, TADAP, and
SQDPP protocols
3 Network layer Buffers, sensor, partial
memory, and power
conserving are the different
Data routing which gets from the
WSN network’s transport layer
10
types of tasks which are
managed by the network
layer.it also used the reliable
lane and redundant lanes for
the routing management.
4 Physical WSN network contained a
physical layer that supports
star topology and peers to
peer for the CSMA/CA. it also
works on communication
range, low cost, and density.
modulation, Frequency selection,
data & signal encryption, and
frequency carrier,
5 Data link layer It provides the linking
between the network layer
and physical.
error control, Multiplexing data
streams, detecting data frames,
and MAC (media access control)
(Saad, 2013)
WSN Network Attacks:
In this section, I have explained the different type of WSN Network Attacks such as
DoS: DoS Means as Denial of Service. It is the type of attack on the WSN network which
attacked during the data transmission process. It interrupts at the receiving side and
occurred noise, collision, and interference. With the help of this attack, network attacker is
able to access the network access points, server application, and network infrastructure.
Wormhole attack: Wormhole is a type of attack. In this attack, the attacker is monitoring the
packet (which carries useful information of the network) form the source location to
destination location. There is no needed to network sensor compromise. So it is easily
implemented in the network. When the network sensor is introduced then it provides
necessary information. The attacker used this information to implementation. There is
created a wormhole in between data (attacker attacks) and the sensor node.
11
managed by the network
layer.it also used the reliable
lane and redundant lanes for
the routing management.
4 Physical WSN network contained a
physical layer that supports
star topology and peers to
peer for the CSMA/CA. it also
works on communication
range, low cost, and density.
modulation, Frequency selection,
data & signal encryption, and
frequency carrier,
5 Data link layer It provides the linking
between the network layer
and physical.
error control, Multiplexing data
streams, detecting data frames,
and MAC (media access control)
(Saad, 2013)
WSN Network Attacks:
In this section, I have explained the different type of WSN Network Attacks such as
DoS: DoS Means as Denial of Service. It is the type of attack on the WSN network which
attacked during the data transmission process. It interrupts at the receiving side and
occurred noise, collision, and interference. With the help of this attack, network attacker is
able to access the network access points, server application, and network infrastructure.
Wormhole attack: Wormhole is a type of attack. In this attack, the attacker is monitoring the
packet (which carries useful information of the network) form the source location to
destination location. There is no needed to network sensor compromise. So it is easily
implemented in the network. When the network sensor is introduced then it provides
necessary information. The attacker used this information to implementation. There is
created a wormhole in between data (attacker attacks) and the sensor node.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





