Risk Management in E-commerce: A Case Study of Birchbox Company Report
VerifiedAdded on 2023/04/24
|10
|1340
|67
Report
AI Summary
This report provides a comprehensive analysis of risk management practices within Birchbox, an e-commerce company. The report begins by introducing the concept of risk management and its importance for businesses, particularly those operating online. It then provides background information on Birchbox, a subscription-based online retailer of beauty products. The core of the report focuses on risk identification, asset classification, and the implementation of risk control measures. The report outlines the process of identifying potential threats, classifying information assets based on their sensitivity and impact, and implementing various control techniques to mitigate risks. The analysis includes a detailed inventory of Birchbox's IT system components, people, procedures, data, hardware, software, and networking elements. The report also presents a classification worksheet to categorize assets based on their security needs and impact on profitability. Finally, the report concludes by emphasizing the critical role of risk management in preventing threats, minimizing disruptions, and ensuring the success of the business. The report references several academic sources to support its findings and recommendations.

Risk Management 1
Risk Management: Identifying and Assessing Risk
Risk Management: Identifying and Assessing Risk
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Risk Management 2
Table of Contents
Introduction:....................................................................................................................................1
Birchbox Background......................................................................................................................2
Risk Management........................................................................................................................2
Risk Identification.......................................................................................................................3
Creating Information Assets Inventory.......................................................................................4
Classification of Assets................................................................................................................4
Conclusion.......................................................................................................................................7
References........................................................................................................................................8
Table of Contents
Introduction:....................................................................................................................................1
Birchbox Background......................................................................................................................2
Risk Management........................................................................................................................2
Risk Identification.......................................................................................................................3
Creating Information Assets Inventory.......................................................................................4
Classification of Assets................................................................................................................4
Conclusion.......................................................................................................................................7
References........................................................................................................................................8

Risk Management 1
Introduction:
Risk management refer to the evaluation, identification and prioritisation of threats followed by
economical application and coordinated resources in order to monitor, minimise and control the
possibilities or influence adverse incidents or to reduce the opportunities realisation (Reason
(2016). The assignment will study different risk management techniques used by Birchbox
which is an online trader company based on New York City which delivers its subscribers or
users a box full of 4 -5 selected makeup samples or other products. Assignment will evaluate
identification of risk management and assessment of chosen company.
Introduction:
Risk management refer to the evaluation, identification and prioritisation of threats followed by
economical application and coordinated resources in order to monitor, minimise and control the
possibilities or influence adverse incidents or to reduce the opportunities realisation (Reason
(2016). The assignment will study different risk management techniques used by Birchbox
which is an online trader company based on New York City which delivers its subscribers or
users a box full of 4 -5 selected makeup samples or other products. Assignment will evaluate
identification of risk management and assessment of chosen company.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Risk Management 2
Birchbox Background
Birchbox is a monthly subscription based online trader who deliver their consumer samples of
their makeup, cosmetic and other products. Organisation sells numerous cosmetics products
including perfume, organics based beauty products, skincare items and numerous other
cosmetics. The company was initially founded in September 2010 by Hayley Barna and Katia
Beauchamp. The company has approximate 300 workers and over million users or subscribers.
Enterprise provide numerous exotic offers and plans to retain their consumer such as social
commerce service, Birchbox points etc. (Sadgrove (2016)) As the company is based on e-
commerce service, this is requisite for enterprise to manage their risk in order to prevent
upcoming threats to growth of the enterprise.
Risk Management
Risk management is the procedure of assessing, identifying and controlling hazards or threats to
a company’s earnings and capital. According to Sun Tzu, this is required to understand yourself
and your rivals to accomplish the target. Process of risk management focuses on identification of
control and safeguards which are devised and executed but are not establish-and-forget tool. On
the other hand, the procedure also emphasise its focus on examining, identifying and considering
the risks facing the enterprise’s information assets. Birchbox is an emerging cosmetic e-
commerce company which is focusing on its growth and expansion worldwide. Whole
communities of interest of Birchbox must work in a united form for risk management
accountability. This is essential to analyse the controls of threats, installing and acquiring the
relevant controls, overseeing procedure to ascertain sustainable controls and determining the cost
Birchbox Background
Birchbox is a monthly subscription based online trader who deliver their consumer samples of
their makeup, cosmetic and other products. Organisation sells numerous cosmetics products
including perfume, organics based beauty products, skincare items and numerous other
cosmetics. The company was initially founded in September 2010 by Hayley Barna and Katia
Beauchamp. The company has approximate 300 workers and over million users or subscribers.
Enterprise provide numerous exotic offers and plans to retain their consumer such as social
commerce service, Birchbox points etc. (Sadgrove (2016)) As the company is based on e-
commerce service, this is requisite for enterprise to manage their risk in order to prevent
upcoming threats to growth of the enterprise.
Risk Management
Risk management is the procedure of assessing, identifying and controlling hazards or threats to
a company’s earnings and capital. According to Sun Tzu, this is required to understand yourself
and your rivals to accomplish the target. Process of risk management focuses on identification of
control and safeguards which are devised and executed but are not establish-and-forget tool. On
the other hand, the procedure also emphasise its focus on examining, identifying and considering
the risks facing the enterprise’s information assets. Birchbox is an emerging cosmetic e-
commerce company which is focusing on its growth and expansion worldwide. Whole
communities of interest of Birchbox must work in a united form for risk management
accountability. This is essential to analyse the controls of threats, installing and acquiring the
relevant controls, overseeing procedure to ascertain sustainable controls and determining the cost
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Risk Management 3
effective control in order to manage, minimise and reduce the online and other threats from
Birchbox.
Risk Identification
The process of risk identification can be defined as the procedure of recording and identifying
the potential threat projects which can influence the delivery of the project (Harrison and Lock
(2017)). This begins with the self-examination process followed up with inventory
developments, asset identification and many other phases which is illustrated in the below
mentioned graph:
Figure 1: Risk identification process
Birchbox is emerging online cosmetic retailer which is currently aiming to identify the upcoming
risk to meet their desired outcome. Company has currently 1 million subscribers and have total
funding of $87 million. Market in which Birchbox trades in is US, UK, Spain, France and Porto
Rico. The enterprise has their Birchbox Point Loyalty program and has full size products sale.
effective control in order to manage, minimise and reduce the online and other threats from
Birchbox.
Risk Identification
The process of risk identification can be defined as the procedure of recording and identifying
the potential threat projects which can influence the delivery of the project (Harrison and Lock
(2017)). This begins with the self-examination process followed up with inventory
developments, asset identification and many other phases which is illustrated in the below
mentioned graph:
Figure 1: Risk identification process
Birchbox is emerging online cosmetic retailer which is currently aiming to identify the upcoming
risk to meet their desired outcome. Company has currently 1 million subscribers and have total
funding of $87 million. Market in which Birchbox trades in is US, UK, Spain, France and Porto
Rico. The enterprise has their Birchbox Point Loyalty program and has full size products sale.
Risk Management 4
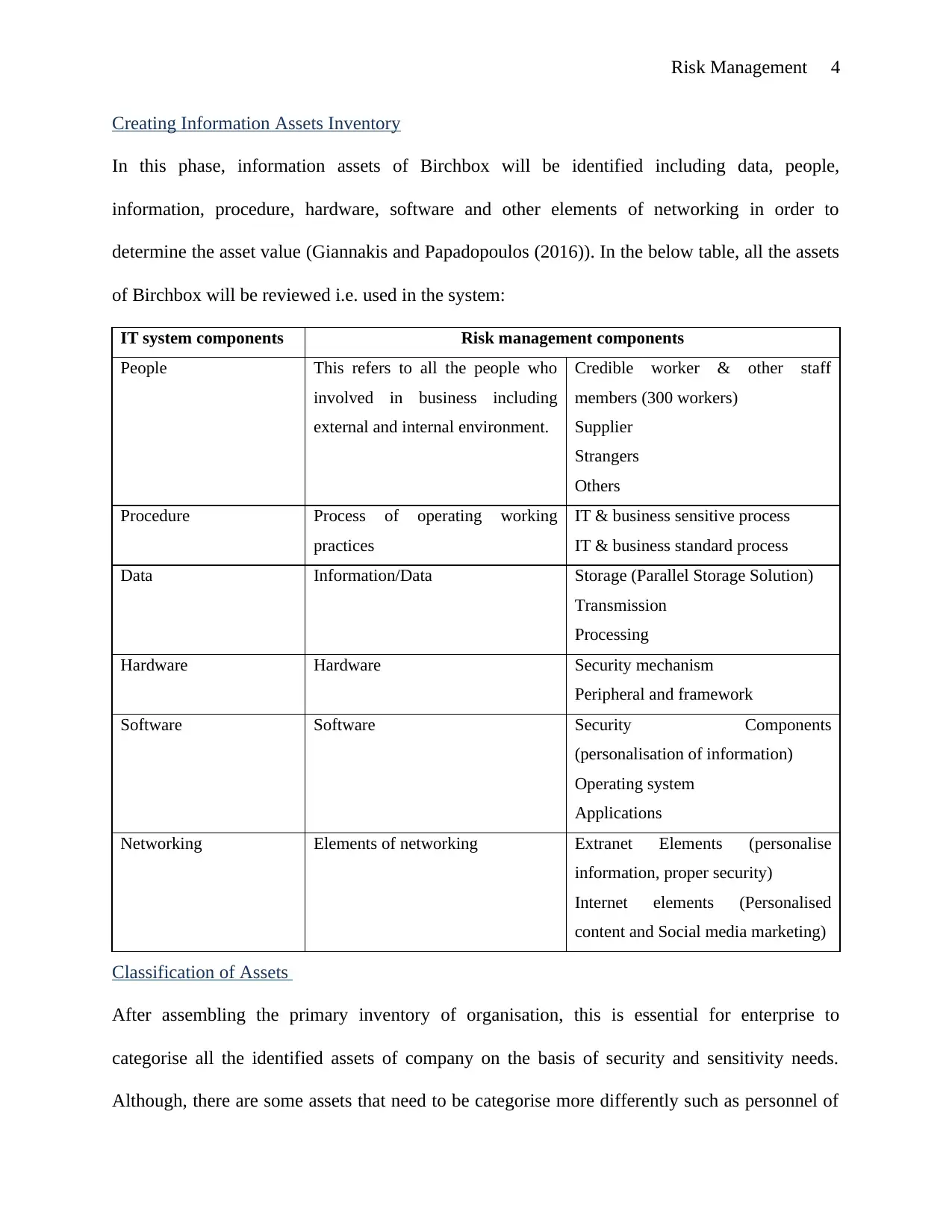
Creating Information Assets Inventory
In this phase, information assets of Birchbox will be identified including data, people,
information, procedure, hardware, software and other elements of networking in order to
determine the asset value (Giannakis and Papadopoulos (2016)). In the below table, all the assets
of Birchbox will be reviewed i.e. used in the system:
IT system components Risk management components
People This refers to all the people who
involved in business including
external and internal environment.
Credible worker & other staff
members (300 workers)
Supplier
Strangers
Others
Procedure Process of operating working
practices
IT & business sensitive process
IT & business standard process
Data Information/Data Storage (Parallel Storage Solution)
Transmission
Processing
Hardware Hardware Security mechanism
Peripheral and framework
Software Software Security Components
(personalisation of information)
Operating system
Applications
Networking Elements of networking Extranet Elements (personalise
information, proper security)
Internet elements (Personalised
content and Social media marketing)
Classification of Assets
After assembling the primary inventory of organisation, this is essential for enterprise to
categorise all the identified assets of company on the basis of security and sensitivity needs.
Although, there are some assets that need to be categorise more differently such as personnel of
Creating Information Assets Inventory
In this phase, information assets of Birchbox will be identified including data, people,
information, procedure, hardware, software and other elements of networking in order to
determine the asset value (Giannakis and Papadopoulos (2016)). In the below table, all the assets
of Birchbox will be reviewed i.e. used in the system:
IT system components Risk management components
People This refers to all the people who
involved in business including
external and internal environment.
Credible worker & other staff
members (300 workers)
Supplier
Strangers
Others
Procedure Process of operating working
practices
IT & business sensitive process
IT & business standard process
Data Information/Data Storage (Parallel Storage Solution)
Transmission
Processing
Hardware Hardware Security mechanism
Peripheral and framework
Software Software Security Components
(personalisation of information)
Operating system
Applications
Networking Elements of networking Extranet Elements (personalise
information, proper security)
Internet elements (Personalised
content and Social media marketing)
Classification of Assets
After assembling the primary inventory of organisation, this is essential for enterprise to
categorise all the identified assets of company on the basis of security and sensitivity needs.
Although, there are some assets that need to be categorise more differently such as personnel of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Risk Management 5
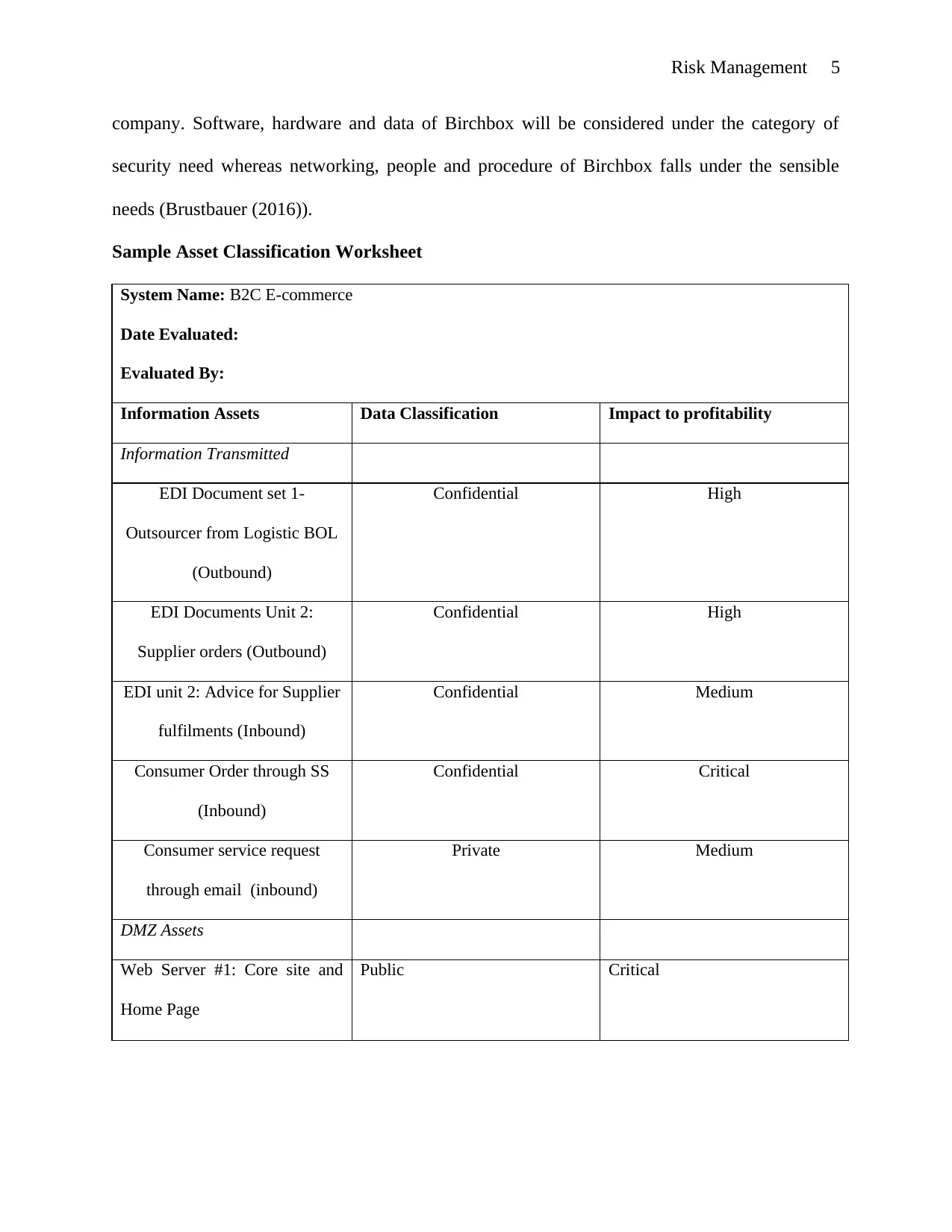
company. Software, hardware and data of Birchbox will be considered under the category of
security need whereas networking, people and procedure of Birchbox falls under the sensible
needs (Brustbauer (2016)).
Sample Asset Classification Worksheet
System Name: B2C E-commerce
Date Evaluated:
Evaluated By:
Information Assets Data Classification Impact to profitability
Information Transmitted
EDI Document set 1-
Outsourcer from Logistic BOL
(Outbound)
Confidential High
EDI Documents Unit 2:
Supplier orders (Outbound)
Confidential High
EDI unit 2: Advice for Supplier
fulfilments (Inbound)
Confidential Medium
Consumer Order through SS
(Inbound)
Confidential Critical
Consumer service request
through email (inbound)
Private Medium
DMZ Assets
Web Server #1: Core site and
Home Page
Public Critical
company. Software, hardware and data of Birchbox will be considered under the category of
security need whereas networking, people and procedure of Birchbox falls under the sensible
needs (Brustbauer (2016)).
Sample Asset Classification Worksheet
System Name: B2C E-commerce
Date Evaluated:
Evaluated By:
Information Assets Data Classification Impact to profitability
Information Transmitted
EDI Document set 1-
Outsourcer from Logistic BOL
(Outbound)
Confidential High
EDI Documents Unit 2:
Supplier orders (Outbound)
Confidential High
EDI unit 2: Advice for Supplier
fulfilments (Inbound)
Confidential Medium
Consumer Order through SS
(Inbound)
Confidential Critical
Consumer service request
through email (inbound)
Private Medium
DMZ Assets
Web Server #1: Core site and
Home Page
Public Critical
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Risk Management 6
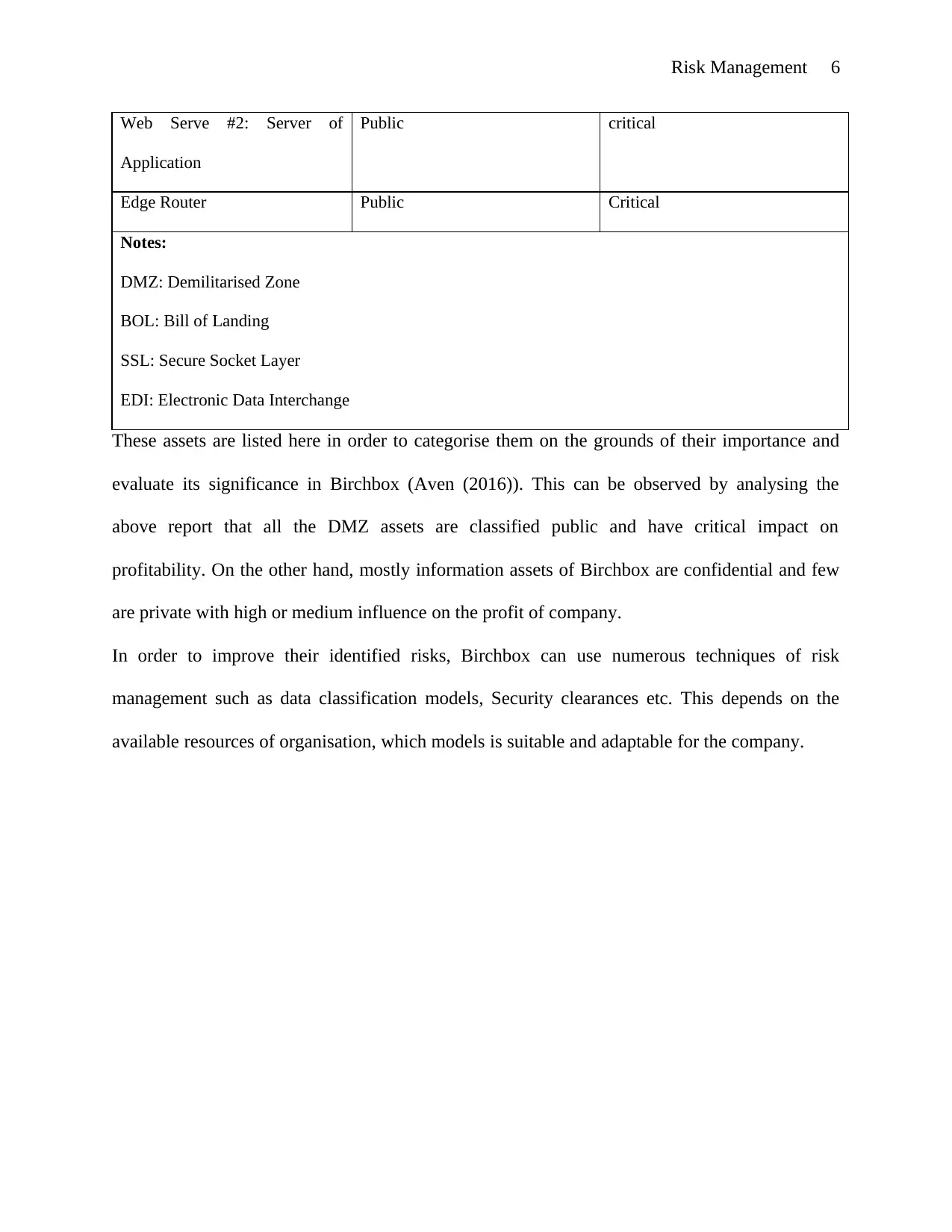
Web Serve #2: Server of
Application
Public critical
Edge Router Public Critical
Notes:
DMZ: Demilitarised Zone
BOL: Bill of Landing
SSL: Secure Socket Layer
EDI: Electronic Data Interchange
These assets are listed here in order to categorise them on the grounds of their importance and
evaluate its significance in Birchbox (Aven (2016)). This can be observed by analysing the
above report that all the DMZ assets are classified public and have critical impact on
profitability. On the other hand, mostly information assets of Birchbox are confidential and few
are private with high or medium influence on the profit of company.
In order to improve their identified risks, Birchbox can use numerous techniques of risk
management such as data classification models, Security clearances etc. This depends on the
available resources of organisation, which models is suitable and adaptable for the company.
Web Serve #2: Server of
Application
Public critical
Edge Router Public Critical
Notes:
DMZ: Demilitarised Zone
BOL: Bill of Landing
SSL: Secure Socket Layer
EDI: Electronic Data Interchange
These assets are listed here in order to categorise them on the grounds of their importance and
evaluate its significance in Birchbox (Aven (2016)). This can be observed by analysing the
above report that all the DMZ assets are classified public and have critical impact on
profitability. On the other hand, mostly information assets of Birchbox are confidential and few
are private with high or medium influence on the profit of company.
In order to improve their identified risks, Birchbox can use numerous techniques of risk
management such as data classification models, Security clearances etc. This depends on the
available resources of organisation, which models is suitable and adaptable for the company.

Risk Management 7
Conclusion
This can affirm from above report that this is paramount for an organisation to undertake the risk
management process in order to prevent further threats and minimise the obstruction from the
success. The company can use different risk management procedure, assessment techniques and
theory in order to cover hazards of enterprise.
Conclusion
This can affirm from above report that this is paramount for an organisation to undertake the risk
management process in order to prevent further threats and minimise the obstruction from the
success. The company can use different risk management procedure, assessment techniques and
theory in order to cover hazards of enterprise.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Risk Management 8
References
Aven, T., (2016) Risk assessment and risk management: Review of recent advances on their
foundation. European Journal of Operational Research, 253(1), pp.1-13.
Brustbauer, J., (2016) Enterprise risk management in SMEs: Towards a structural
model. International Small Business Journal, 34(1), pp.70-85.
Giannakis, M. and Papadopoulos, T., (2016) Supply chain sustainability: A risk management
approach. International Journal of Production Economics, 171, pp.455-470.
Harrison, F. and Lock, D., (2017) Advanced project management: a structured approach. UK:
Routledge.
Reason, J., (2016) Managing the risks of organizational accidents. London: Routledge.
Sadgrove, K., (2016) The complete guide to business risk management. London: Routledge.
References
Aven, T., (2016) Risk assessment and risk management: Review of recent advances on their
foundation. European Journal of Operational Research, 253(1), pp.1-13.
Brustbauer, J., (2016) Enterprise risk management in SMEs: Towards a structural
model. International Small Business Journal, 34(1), pp.70-85.
Giannakis, M. and Papadopoulos, T., (2016) Supply chain sustainability: A risk management
approach. International Journal of Production Economics, 171, pp.455-470.
Harrison, F. and Lock, D., (2017) Advanced project management: a structured approach. UK:
Routledge.
Reason, J., (2016) Managing the risks of organizational accidents. London: Routledge.
Sadgrove, K., (2016) The complete guide to business risk management. London: Routledge.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





