Risk Management: Risk Assessment, Mitigation, and Project Continuity
VerifiedAdded on 2020/03/01
|12
|2454
|136
Homework Assignment
AI Summary
This assignment delves into the core principles of risk management within an organizational context, emphasizing the identification, analysis, and mitigation of project-related risks. It explores various techniques for risk identification, such as brainstorming and questionnaires, and highlights the importance of a comprehensive risk management plan. The assignment covers the documentation of project risks, qualitative analysis, and the significance of proactive measures, including the preparation of opportunities alongside threats. It discusses risk response strategies like avoidance, mitigation, transfer, and acceptance, providing real-world examples such as software release strategies and insurance for risk transfer. The assignment emphasizes the importance of identifying, analyzing, and establishing controls for project risks, including the use of databases and questionnaires for identifying and assessing risks. Furthermore, it provides a risk matrix, outlining various risk categories, likelihood, impact, and mitigation strategies, along with risk action plans for top risks. The assignment also explores the evaluation of risk management outcomes, emphasizing the effectiveness of techniques and the accuracy of information gathered through reviews and analyses.

RISK MANAGEMENT 1
The Risk Management in an Organization
Name:
Course:
Professor:
University:
The Risk Management in an Organization
Name:
Course:
Professor:
University:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RISK MANAGEMENT 2
Question 1
In any project undertaken in the market, uncertainties may exist and the unexpected could
happen. Risk identification therefore involves accessing the inessentials or threats and by
considering the risks that might affect the project, a project manager undertaking risk
identification and activities can filter unnecessary threats to focus on project related risks in order
to make the project less prone to risk. Moreover, the process involves going through the
company and finding the any negative events that might interfere with the operations that are
being carried. The process may involve the use of various techniques like the brainstorming
which entails taking the experts to be in the decision making panel of effective and also through
the use of questionnaire spreadsheet to acquire information from the immediate respondents.
Question 2
Project risks are documented in the risk management plan. (c)
Question 3
The qualitative analysis identifies the cost and time of the risk expected (b)
Question 4
The warning signs involves the events that results in the risk actually occurring. (c)
Question 5
The project manager should also prepare the opportunities apart from the threats. (c)
Question 6
Question 1
In any project undertaken in the market, uncertainties may exist and the unexpected could
happen. Risk identification therefore involves accessing the inessentials or threats and by
considering the risks that might affect the project, a project manager undertaking risk
identification and activities can filter unnecessary threats to focus on project related risks in order
to make the project less prone to risk. Moreover, the process involves going through the
company and finding the any negative events that might interfere with the operations that are
being carried. The process may involve the use of various techniques like the brainstorming
which entails taking the experts to be in the decision making panel of effective and also through
the use of questionnaire spreadsheet to acquire information from the immediate respondents.
Question 2
Project risks are documented in the risk management plan. (c)
Question 3
The qualitative analysis identifies the cost and time of the risk expected (b)
Question 4
The warning signs involves the events that results in the risk actually occurring. (c)
Question 5
The project manager should also prepare the opportunities apart from the threats. (c)
Question 6
RISK MANAGEMENT 3
To assign an owner to each risk identified develop a probability impact matrix. (a)
Question 7
Tools and techniques used to identify risk process is brainstorming (a)
Question 8
Ineffective risk management tool is the excel spreadsheet. (b)
Question 9
The phase at which phase does the project manager implements approved actions is the
monitoring and controlling phase (d).
Question 10
High level of risk register is to identify risk. (c)
Question 11
After risk management plan is prepared the next important step is to identify the risks. (c)
Question 12
The valid response to the negative risks is to mitigate. (b)
Question 13
The step missing in the plan is the risk mitigation. (c)
Question 14
The technique that john is using is the Delphi technique. (a)
To assign an owner to each risk identified develop a probability impact matrix. (a)
Question 7
Tools and techniques used to identify risk process is brainstorming (a)
Question 8
Ineffective risk management tool is the excel spreadsheet. (b)
Question 9
The phase at which phase does the project manager implements approved actions is the
monitoring and controlling phase (d).
Question 10
High level of risk register is to identify risk. (c)
Question 11
After risk management plan is prepared the next important step is to identify the risks. (c)
Question 12
The valid response to the negative risks is to mitigate. (b)
Question 13
The step missing in the plan is the risk mitigation. (c)
Question 14
The technique that john is using is the Delphi technique. (a)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

RISK MANAGEMENT 4
Question 15
The type of risk response is the accept. (a)
Question 16
Share (d)
Question 17
The quantitative risk analysis will evaluate the probability and impact. (d)
Question 18
Risk response plan is another name of the Risk management plan. (d)
Managing project risks
Business risks come in variety of the tangible and intangible forms over the course of the
operation cycle. For example the tender offered to the National archives of Australia to offer
computer services to the ACT Canberra (Raspotnig and Opdahl, 2013). In real times and
analysis, some of the risk occurs during the ordinary course of the business while others occur
during the extraordinary courses. As an aspect in business planning it is important for the firm to
identify the risks and then takes its time to manage them to protect the business from the mess.
This medium can be done through using various techniques;
Avoidance of the risk
One of the strategies of managing the identified risk is to avoid it all the same. In most of
the cases, the avoidance takes place where the business shuns taking part in activities that are
Question 15
The type of risk response is the accept. (a)
Question 16
Share (d)
Question 17
The quantitative risk analysis will evaluate the probability and impact. (d)
Question 18
Risk response plan is another name of the Risk management plan. (d)
Managing project risks
Business risks come in variety of the tangible and intangible forms over the course of the
operation cycle. For example the tender offered to the National archives of Australia to offer
computer services to the ACT Canberra (Raspotnig and Opdahl, 2013). In real times and
analysis, some of the risk occurs during the ordinary course of the business while others occur
during the extraordinary courses. As an aspect in business planning it is important for the firm to
identify the risks and then takes its time to manage them to protect the business from the mess.
This medium can be done through using various techniques;
Avoidance of the risk
One of the strategies of managing the identified risk is to avoid it all the same. In most of
the cases, the avoidance takes place where the business shuns taking part in activities that are
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RISK MANAGEMENT 5
known or perceived to have risks of any kind (Raspotnig and Opdahl, 2013). For example the
website might avoid sourcing and storing its data from the archives due to the issue of security
that might take place hence rendering the project outcome to be at bay. Similarly, the building of
the hosted website application should not be done externally but rather internally in the database
of the user in the archives. Moreover, the website security issue that is appropriate to support the
administration should be hidden.
Risk mitigation
The risks can also be managed through mitigation or perhaps the reduction process which
exist to lessen or reduce any negative consequences that might affect the operation of the firm.
For example the software company like the national archives would chose to release the
programs which are not performing effectively in the marker by making releasing the programs
in bits to the market to get the feedback correctly and rectify the situation (Raspotnig and
Opdahl, 2013).
The transfer of risk
This technique involves the firm moving the identified risks away from the company. In
most of the cases in will involve the company paying some amount of premiums to the insurance
company who will assist in paying for the project when the item insured has occurred. The
company should be able to insure all the products that are necessary to the insurance company to
ensure that the solution is found in the case the subjected risk appears (Raspotnig and Opdahl,
2013). For example in the case of fire at the storage facilities of the company, the risk can be
transferred to the insurance company.
Risk acceptance
known or perceived to have risks of any kind (Raspotnig and Opdahl, 2013). For example the
website might avoid sourcing and storing its data from the archives due to the issue of security
that might take place hence rendering the project outcome to be at bay. Similarly, the building of
the hosted website application should not be done externally but rather internally in the database
of the user in the archives. Moreover, the website security issue that is appropriate to support the
administration should be hidden.
Risk mitigation
The risks can also be managed through mitigation or perhaps the reduction process which
exist to lessen or reduce any negative consequences that might affect the operation of the firm.
For example the software company like the national archives would chose to release the
programs which are not performing effectively in the marker by making releasing the programs
in bits to the market to get the feedback correctly and rectify the situation (Raspotnig and
Opdahl, 2013).
The transfer of risk
This technique involves the firm moving the identified risks away from the company. In
most of the cases in will involve the company paying some amount of premiums to the insurance
company who will assist in paying for the project when the item insured has occurred. The
company should be able to insure all the products that are necessary to the insurance company to
ensure that the solution is found in the case the subjected risk appears (Raspotnig and Opdahl,
2013). For example in the case of fire at the storage facilities of the company, the risk can be
transferred to the insurance company.
Risk acceptance

RISK MANAGEMENT 6
The risk management can also be implemented through the acceptance of risk techniques.
The company can choose to retain a certain aspect of risk that is brought by a given project in the
system. The company through compatibility measure would seek to maintain the risks and think
of how manage it through monitoring and control process. For example the company must work
with the former website since the tender is on the basis of making an improvement. The
company should be prepared for the risk that will take place in the case the system fails to be
compatible with the earlier and this will force the company to involve some of the technicians for
a recap of the work. The risk can also be noticed during the testing process.
Identify project risks, Analyze project risks and Establish risk treatments and controls
Question 1
The project is operating under various contexts and one of the common one is the nature
of the product. The company deals with a product service provider on the basis of website that
itself has faced a number of challenges like for example the failure of the program to function,
the process failing to meet the client’s needs and speculations and purposely the product failing
to be compatible with the current website for the purposes of efficiency (Tang and Musa, 2011)).
The issue of compatibility can be solved through hiring skilled persons on that field even in the
expense of the company to make sure that the risk is managed adequately. The whole process
will entail the use of additional funds that perhaps may be taken out of the prescribed budget.
Question 2
There are various approaches that were used to identify the risk that might take place on
the project. This includes the use of the comprehensive databases of the past events which lies
basically in the minds of the people especially in the minds of the project manager. This risk will
The risk management can also be implemented through the acceptance of risk techniques.
The company can choose to retain a certain aspect of risk that is brought by a given project in the
system. The company through compatibility measure would seek to maintain the risks and think
of how manage it through monitoring and control process. For example the company must work
with the former website since the tender is on the basis of making an improvement. The
company should be prepared for the risk that will take place in the case the system fails to be
compatible with the earlier and this will force the company to involve some of the technicians for
a recap of the work. The risk can also be noticed during the testing process.
Identify project risks, Analyze project risks and Establish risk treatments and controls
Question 1
The project is operating under various contexts and one of the common one is the nature
of the product. The company deals with a product service provider on the basis of website that
itself has faced a number of challenges like for example the failure of the program to function,
the process failing to meet the client’s needs and speculations and purposely the product failing
to be compatible with the current website for the purposes of efficiency (Tang and Musa, 2011)).
The issue of compatibility can be solved through hiring skilled persons on that field even in the
expense of the company to make sure that the risk is managed adequately. The whole process
will entail the use of additional funds that perhaps may be taken out of the prescribed budget.
Question 2
There are various approaches that were used to identify the risk that might take place on
the project. This includes the use of the comprehensive databases of the past events which lies
basically in the minds of the people especially in the minds of the project manager. This risk will
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
RISK MANAGEMENT 7
be identified through the brainstorming techniques of the project team concerning the past events
to find out how the issue affected the whole process through a failure of the systems. In addition
to this, the companies experience will be a major factor that assisted in the identification of the
risk involved in the project (Manuj and Mentzer, 2008). For example there have been some past
issues on the compatibility failure that resulted for the company to repeat the whole process and
furthermore involve some experienced technicians to rectify the situation. The factors were very
vital for making sure that the same risk is managed by technically accepting and financing the all
process. This process also applied the techniques like the questionnaires worksheets to provide
them with essential information concerning the same. The response that contained both the
negative and the positive effects were discussed by the managers of the company in the provision
of the right way for effective preparation of risk that might occur.
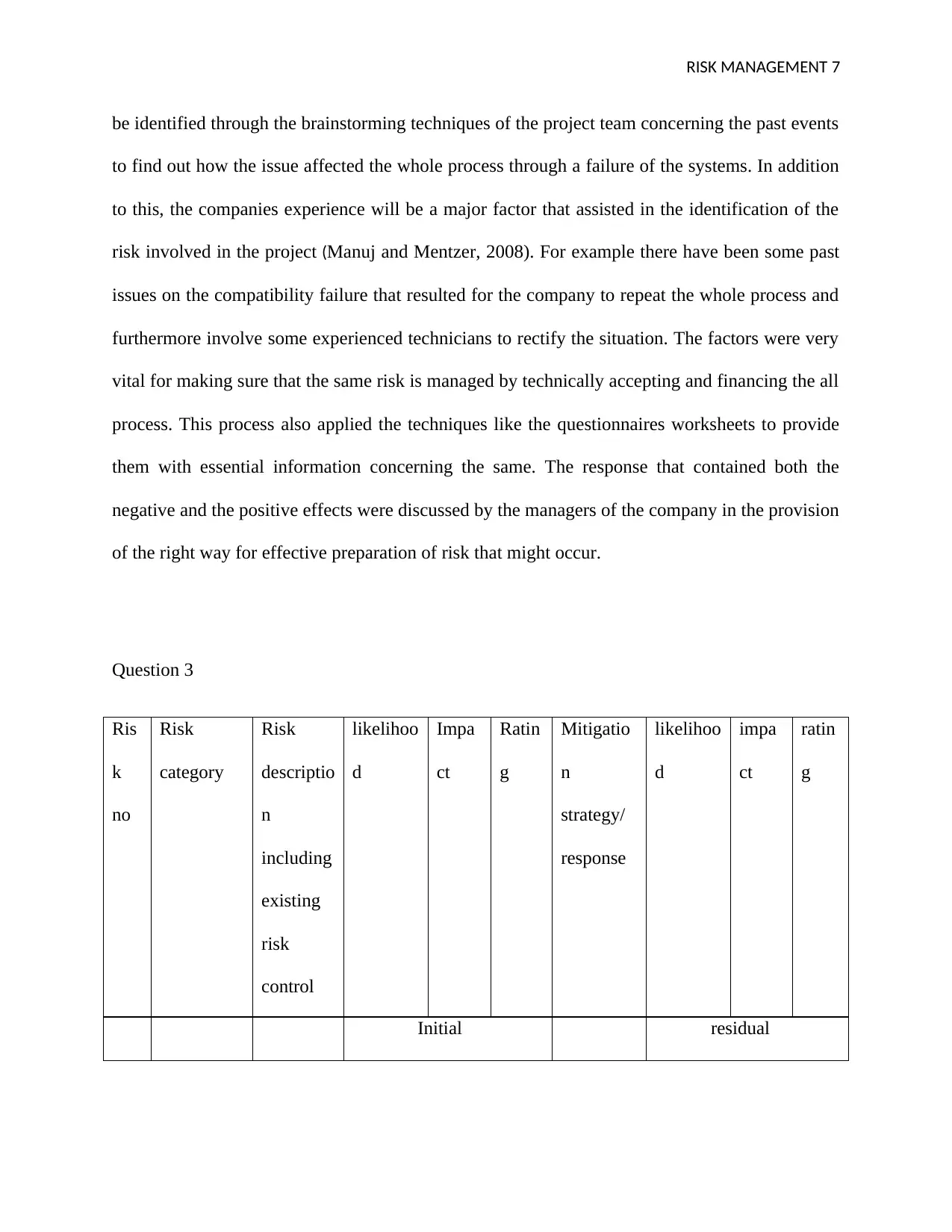
Question 3
Ris
k
no
Risk
category
Risk
descriptio
n
including
existing
risk
control
likelihoo
d
Impa
ct
Ratin
g
Mitigatio
n
strategy/
response
likelihoo
d
impa
ct
ratin
g
Initial residual
be identified through the brainstorming techniques of the project team concerning the past events
to find out how the issue affected the whole process through a failure of the systems. In addition
to this, the companies experience will be a major factor that assisted in the identification of the
risk involved in the project (Manuj and Mentzer, 2008). For example there have been some past
issues on the compatibility failure that resulted for the company to repeat the whole process and
furthermore involve some experienced technicians to rectify the situation. The factors were very
vital for making sure that the same risk is managed by technically accepting and financing the all
process. This process also applied the techniques like the questionnaires worksheets to provide
them with essential information concerning the same. The response that contained both the
negative and the positive effects were discussed by the managers of the company in the provision
of the right way for effective preparation of risk that might occur.
Question 3
Ris
k
no
Risk
category
Risk
descriptio
n
including
existing
risk
control
likelihoo
d
Impa
ct
Ratin
g
Mitigatio
n
strategy/
response
likelihoo
d
impa
ct
ratin
g
Initial residual
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
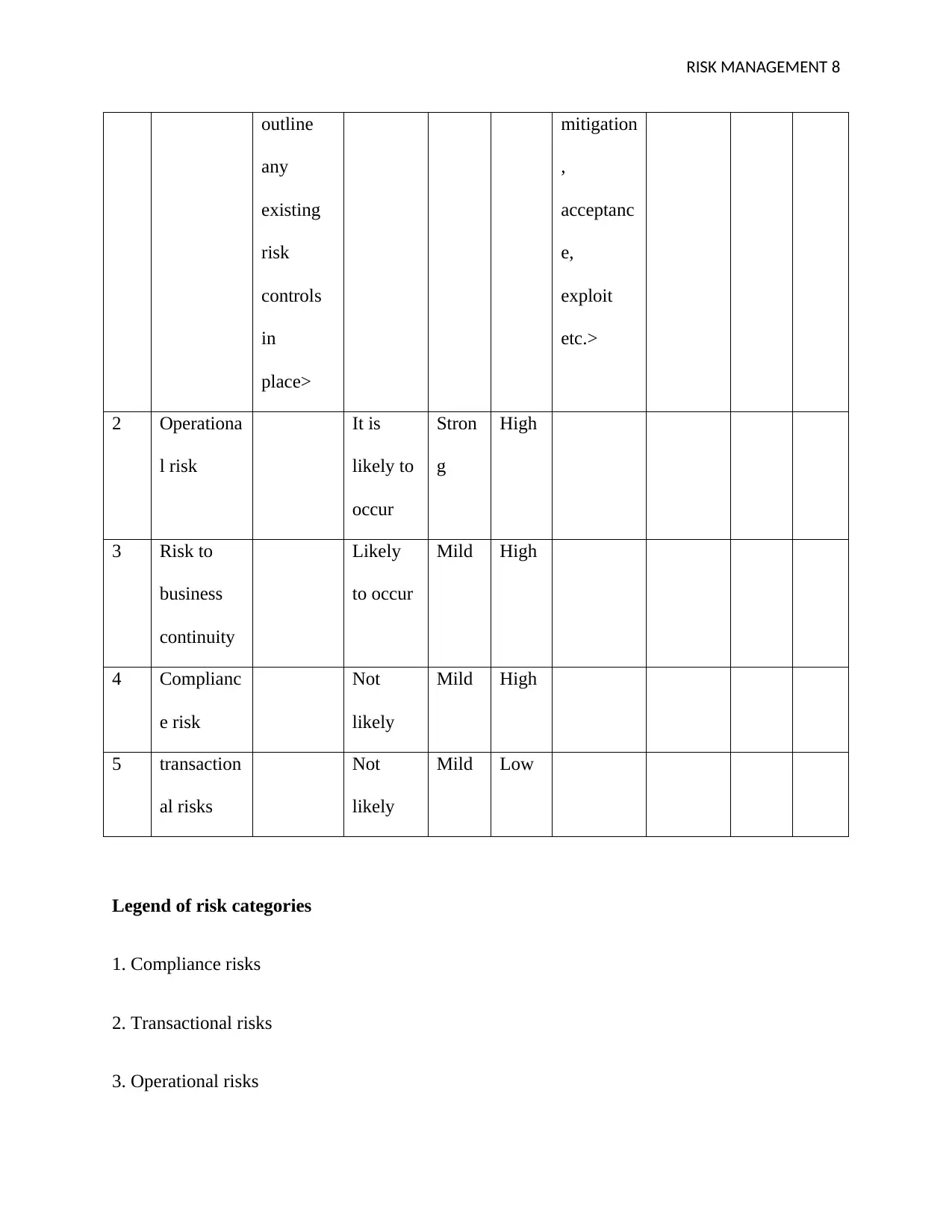
RISK MANAGEMENT 8
outline
any
existing
risk
controls
in
place>
mitigation
,
acceptanc
e,
exploit
etc.>
2 Operationa
l risk
It is
likely to
occur
Stron
g
High
3 Risk to
business
continuity
Likely
to occur
Mild High
4 Complianc
e risk
Not
likely
Mild High
5 transaction
al risks
Not
likely
Mild Low
Legend of risk categories
1. Compliance risks
2. Transactional risks
3. Operational risks
outline
any
existing
risk
controls
in
place>
mitigation
,
acceptanc
e,
exploit
etc.>
2 Operationa
l risk
It is
likely to
occur
Stron
g
High
3 Risk to
business
continuity
Likely
to occur
Mild High
4 Complianc
e risk
Not
likely
Mild High
5 transaction
al risks
Not
likely
Mild Low
Legend of risk categories
1. Compliance risks
2. Transactional risks
3. Operational risks
RISK MANAGEMENT 9
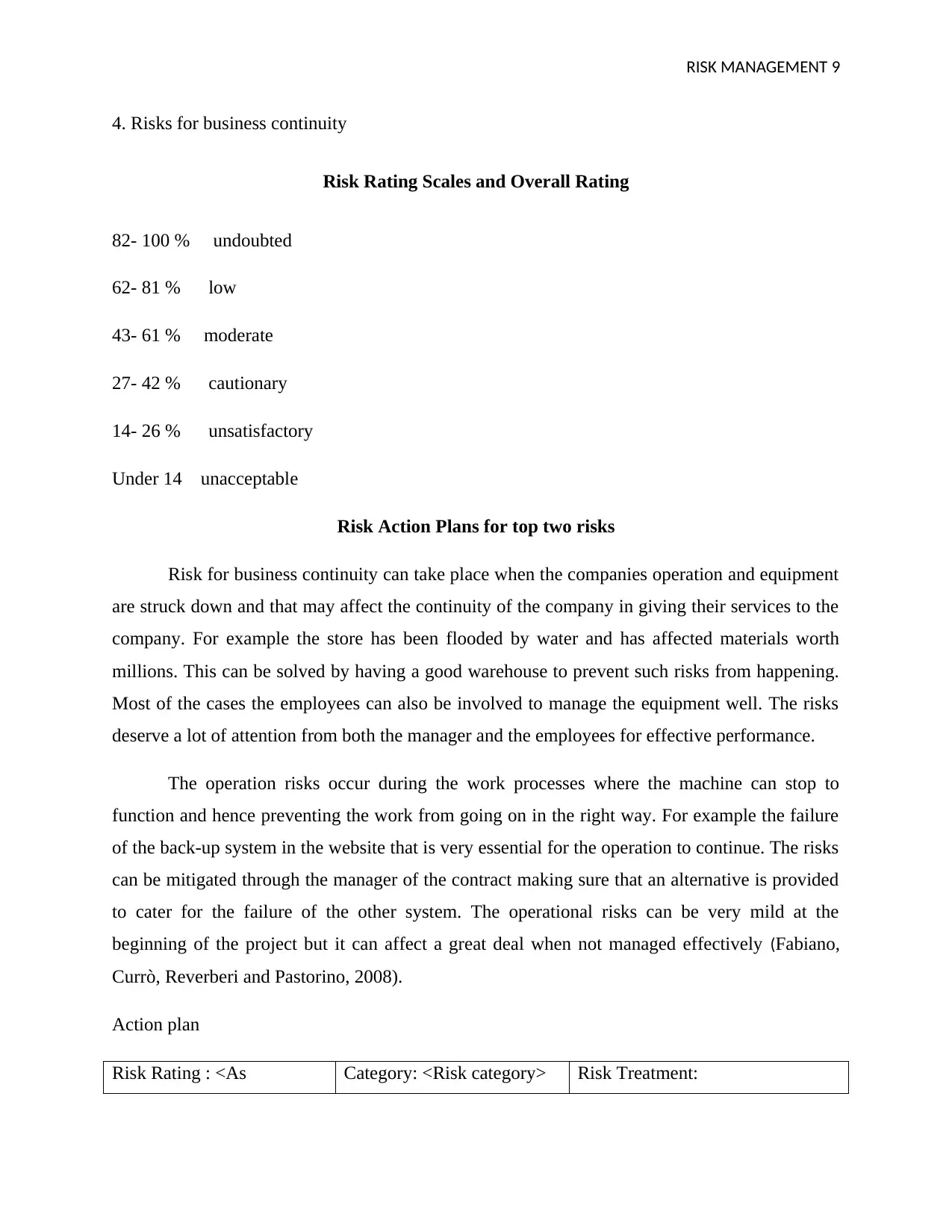
4. Risks for business continuity
Risk Rating Scales and Overall Rating
82- 100 % undoubted
62- 81 % low
43- 61 % moderate
27- 42 % cautionary
14- 26 % unsatisfactory
Under 14 unacceptable
Risk Action Plans for top two risks
Risk for business continuity can take place when the companies operation and equipment
are struck down and that may affect the continuity of the company in giving their services to the
company. For example the store has been flooded by water and has affected materials worth
millions. This can be solved by having a good warehouse to prevent such risks from happening.
Most of the cases the employees can also be involved to manage the equipment well. The risks
deserve a lot of attention from both the manager and the employees for effective performance.
The operation risks occur during the work processes where the machine can stop to
function and hence preventing the work from going on in the right way. For example the failure
of the back-up system in the website that is very essential for the operation to continue. The risks
can be mitigated through the manager of the contract making sure that an alternative is provided
to cater for the failure of the other system. The operational risks can be very mild at the
beginning of the project but it can affect a great deal when not managed effectively (Fabiano,
Currò, Reverberi and Pastorino, 2008).
Action plan
Risk Rating : <As Category: <Risk category> Risk Treatment:
4. Risks for business continuity
Risk Rating Scales and Overall Rating
82- 100 % undoubted
62- 81 % low
43- 61 % moderate
27- 42 % cautionary
14- 26 % unsatisfactory
Under 14 unacceptable
Risk Action Plans for top two risks
Risk for business continuity can take place when the companies operation and equipment
are struck down and that may affect the continuity of the company in giving their services to the
company. For example the store has been flooded by water and has affected materials worth
millions. This can be solved by having a good warehouse to prevent such risks from happening.
Most of the cases the employees can also be involved to manage the equipment well. The risks
deserve a lot of attention from both the manager and the employees for effective performance.
The operation risks occur during the work processes where the machine can stop to
function and hence preventing the work from going on in the right way. For example the failure
of the back-up system in the website that is very essential for the operation to continue. The risks
can be mitigated through the manager of the contract making sure that an alternative is provided
to cater for the failure of the other system. The operational risks can be very mild at the
beginning of the project but it can affect a great deal when not managed effectively (Fabiano,
Currò, Reverberi and Pastorino, 2008).
Action plan
Risk Rating : <As Category: <Risk category> Risk Treatment:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
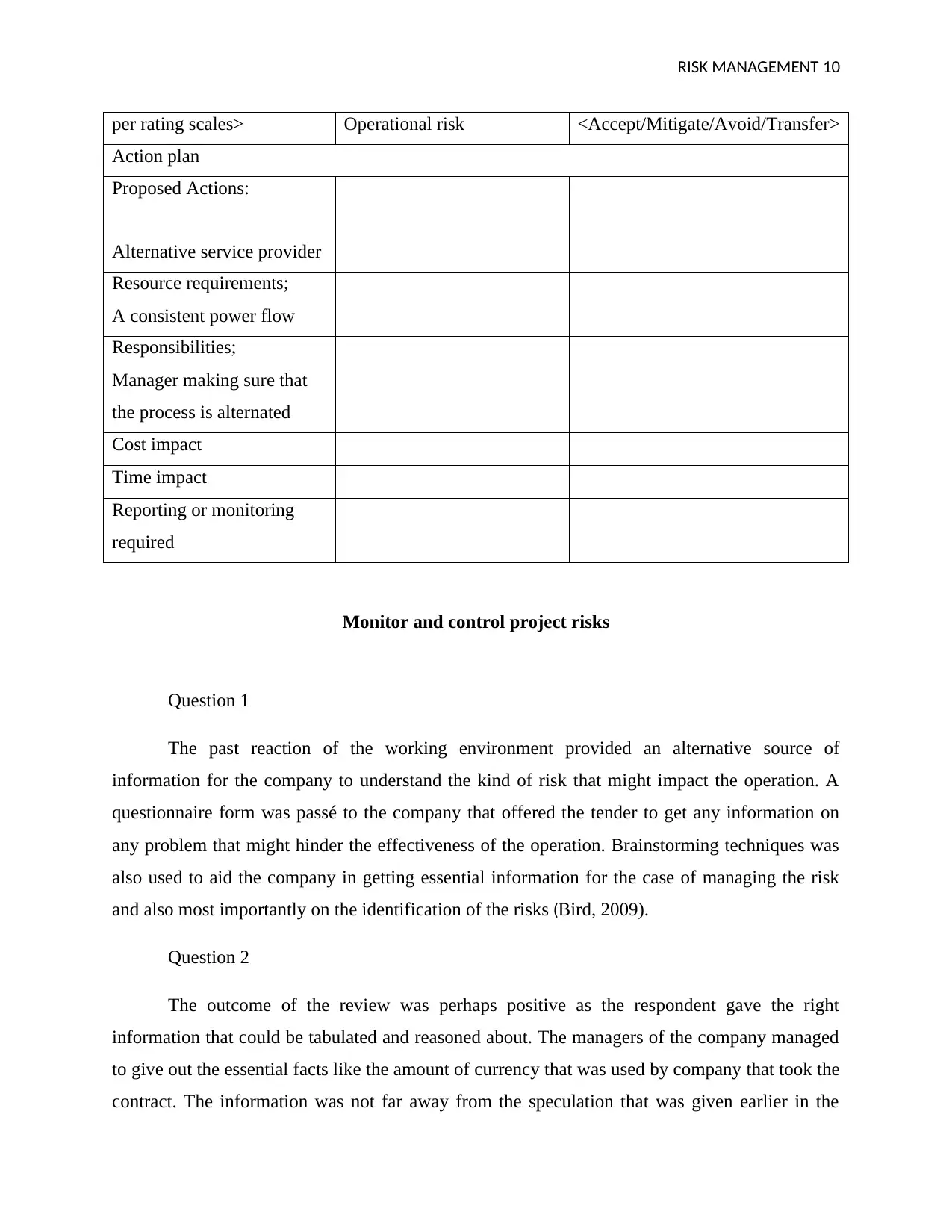
RISK MANAGEMENT 10
per rating scales> Operational risk <Accept/Mitigate/Avoid/Transfer>
Action plan
Proposed Actions:
Alternative service provider
Resource requirements;
A consistent power flow
Responsibilities;
Manager making sure that
the process is alternated
Cost impact
Time impact
Reporting or monitoring
required
Monitor and control project risks
Question 1
The past reaction of the working environment provided an alternative source of
information for the company to understand the kind of risk that might impact the operation. A
questionnaire form was passé to the company that offered the tender to get any information on
any problem that might hinder the effectiveness of the operation. Brainstorming techniques was
also used to aid the company in getting essential information for the case of managing the risk
and also most importantly on the identification of the risks (Bird, 2009).
Question 2
The outcome of the review was perhaps positive as the respondent gave the right
information that could be tabulated and reasoned about. The managers of the company managed
to give out the essential facts like the amount of currency that was used by company that took the
contract. The information was not far away from the speculation that was given earlier in the
per rating scales> Operational risk <Accept/Mitigate/Avoid/Transfer>
Action plan
Proposed Actions:
Alternative service provider
Resource requirements;
A consistent power flow
Responsibilities;
Manager making sure that
the process is alternated
Cost impact
Time impact
Reporting or monitoring
required
Monitor and control project risks
Question 1
The past reaction of the working environment provided an alternative source of
information for the company to understand the kind of risk that might impact the operation. A
questionnaire form was passé to the company that offered the tender to get any information on
any problem that might hinder the effectiveness of the operation. Brainstorming techniques was
also used to aid the company in getting essential information for the case of managing the risk
and also most importantly on the identification of the risks (Bird, 2009).
Question 2
The outcome of the review was perhaps positive as the respondent gave the right
information that could be tabulated and reasoned about. The managers of the company managed
to give out the essential facts like the amount of currency that was used by company that took the
contract. The information was not far away from the speculation that was given earlier in the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
RISK MANAGEMENT 11
management process that indicated the amount that the company should prepare to have (Ahmed,
Kayis, and Amornsawadwatana, 2007). Moreover, only a small significant amount was a
difference from the speculation and this the company could still make it at standby for the sake
of importance occurring in the company.
Assess risk-management outcomes
Question 1
The figure and the processes are very much effective since the unknown risks are very
uncertain. In the review there are consideration of both the unknown and the known risks that
could be taken care of in the case of occurrence. Therefore, based on the confirmation that took
place through the techniques to make sure that the accuracy is performed to provide the right
information to the company, the review should be accepted and confirmed. The effectiveness is
also capture in the fact that the past operation left and the risks encountered in the process made
possible for the company to accept any of the proposal based on the risk. The accuracy level of
the study and the speculation is paramount and this confirms the essentiality that should be
considered as part of the process.
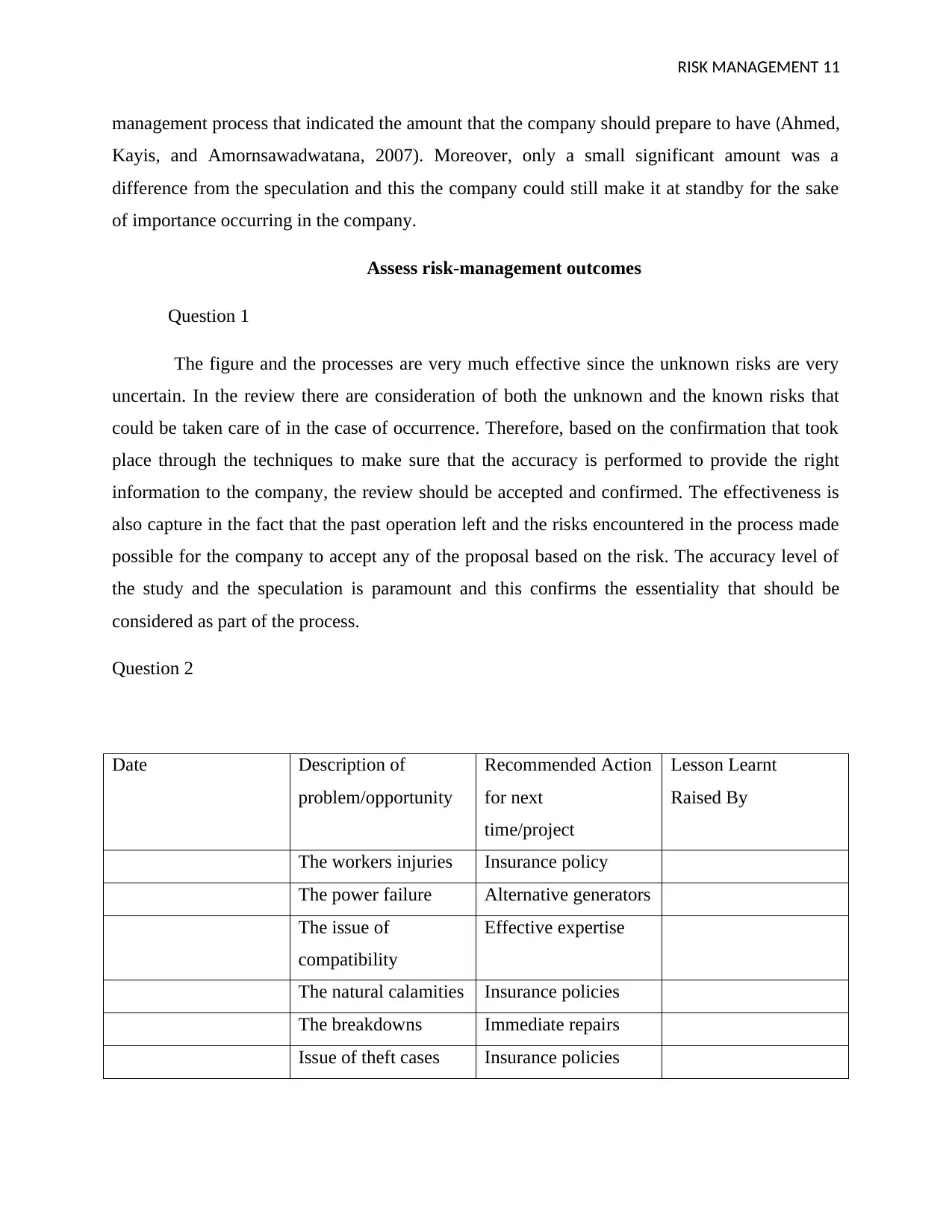
Question 2
Date Description of
problem/opportunity
Recommended Action
for next
time/project
Lesson Learnt
Raised By
The workers injuries Insurance policy
The power failure Alternative generators
The issue of
compatibility
Effective expertise
The natural calamities Insurance policies
The breakdowns Immediate repairs
Issue of theft cases Insurance policies
management process that indicated the amount that the company should prepare to have (Ahmed,
Kayis, and Amornsawadwatana, 2007). Moreover, only a small significant amount was a
difference from the speculation and this the company could still make it at standby for the sake
of importance occurring in the company.
Assess risk-management outcomes
Question 1
The figure and the processes are very much effective since the unknown risks are very
uncertain. In the review there are consideration of both the unknown and the known risks that
could be taken care of in the case of occurrence. Therefore, based on the confirmation that took
place through the techniques to make sure that the accuracy is performed to provide the right
information to the company, the review should be accepted and confirmed. The effectiveness is
also capture in the fact that the past operation left and the risks encountered in the process made
possible for the company to accept any of the proposal based on the risk. The accuracy level of
the study and the speculation is paramount and this confirms the essentiality that should be
considered as part of the process.
Question 2
Date Description of
problem/opportunity
Recommended Action
for next
time/project
Lesson Learnt
Raised By
The workers injuries Insurance policy
The power failure Alternative generators
The issue of
compatibility
Effective expertise
The natural calamities Insurance policies
The breakdowns Immediate repairs
Issue of theft cases Insurance policies

RISK MANAGEMENT 12
Bibliographies
Ahmed, A., Kayis, B. and Amornsawadwatana, S., 2007. A review of techniques for risk
management in projects. Benchmarking: An International Journal, 14(1), pp.22-36.
Bird, D.K., 2009. The use of questionnaires for acquiring information on public perception of
natural hazards and risk mitigation-a review of current knowledge and practice. Natural
Hazards and Earth System Sciences, 9(4), p.1307.
Fabiano, B., Currò, F., Reverberi, A.P. and Pastorino, R., 2008. A statistical study on temporary
work and occupational accidents: specific risk factors and risk management strategies.
Safety Science, 46(3), pp.535-544.
Manuj, I. and Mentzer, J.T., 2008. Global supply chain risk management strategies. International
Journal of Physical Distribution & Logistics Management, 38(3), pp.192-223.
Raspotnig, C. and Opdahl, A., 2013. Comparing risk identification techniques for safety and
security requirements. Journal of Systems and Software, 86(4), pp.1124-1151.
Tang, O. and Musa, S.N., 2011. Identifying risk issues and research advancements in supply
chain risk management. International journal of production economics, 133(1), pp.25-34.
Bibliographies
Ahmed, A., Kayis, B. and Amornsawadwatana, S., 2007. A review of techniques for risk
management in projects. Benchmarking: An International Journal, 14(1), pp.22-36.
Bird, D.K., 2009. The use of questionnaires for acquiring information on public perception of
natural hazards and risk mitigation-a review of current knowledge and practice. Natural
Hazards and Earth System Sciences, 9(4), p.1307.
Fabiano, B., Currò, F., Reverberi, A.P. and Pastorino, R., 2008. A statistical study on temporary
work and occupational accidents: specific risk factors and risk management strategies.
Safety Science, 46(3), pp.535-544.
Manuj, I. and Mentzer, J.T., 2008. Global supply chain risk management strategies. International
Journal of Physical Distribution & Logistics Management, 38(3), pp.192-223.
Raspotnig, C. and Opdahl, A., 2013. Comparing risk identification techniques for safety and
security requirements. Journal of Systems and Software, 86(4), pp.1124-1151.
Tang, O. and Musa, S.N., 2011. Identifying risk issues and research advancements in supply
chain risk management. International journal of production economics, 133(1), pp.25-34.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




