Comprehensive Risk Management Report: CobWeb Security Analysis
VerifiedAdded on 2019/09/20
|6
|1018
|119
Report
AI Summary
This report provides a comprehensive analysis of CobWeb's security problems and risk management strategies. It begins with an introduction to CobWeb, a cloud services provider, and then identifies key security issues, including physical break-ins, hacking incidents, and data loss due to employee negligence. A vulnerability assessment matrix is presented, evaluating hazards, risks, and control measures. The report then outlines security control measures such as anti-virus software and logical access control. Furthermore, the report proposes countermeasures to mitigate the identified risks, including staff training, IP address changes, password protection, and stricter access controls. The conclusion emphasizes the importance of robust security measures for CobWeb's continued success and competitive advantage, recommending the implementation of the suggested solutions to ensure data protection and business continuity. The report also includes a list of relevant references to support the analysis and recommendations.

Running Head: Risk Management
Risk management
CobWeb
Risk management
CobWeb
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Risk Management 1
Introduction
Cobweb is considered as a famous cloud services expert and also consider the largest hosted
exchange provider of the Europe. It was situated in 1996. In this paper, we will study the security
problems of the organization. This will help us in determining proper solution to avoid these
security problems. Its wide experience is empowering the different organizations to grow their
business with high-level flexibility by best-of-breed cloud technologies. It was the first
organization of the Europe dealing in the Microsoft Cloud Solution Provider program. It is
mainly dealing with Microsoft office 365, Microsoft Dynamics CRM, Email Encryption,
Professional consulting, Microsoft Enterprise Mobility Suite, and Email Archiving.
Security Problems of CobWeb
CobWeb is facing different types of security problem. Some of them are following:
Physical break-ins: It brings greater risk to the physical security of the organization than
hackers. Due to the break-in employees of the organization leave the office and move on
to other competitor’s organization (Alhawari, 2012). On the other hand, physical break-
ins lost the important data which may fall into the wrong hands and can misuse by the
others.
The homepage of the CobWeb was hacked recently: Hacking brings serious problems for
the working of the organization. The homepage of the organization is recently hacked due
to which sensitive information of the organization leaked. This will damage the credit
ratings of the organization from different consumer agencies (Whitman, 2013).
Data loss due to large employee negligence: Loss of necessary data due to the employee
negligence brings serious problem in the success of the organization. In the absence of
Introduction
Cobweb is considered as a famous cloud services expert and also consider the largest hosted
exchange provider of the Europe. It was situated in 1996. In this paper, we will study the security
problems of the organization. This will help us in determining proper solution to avoid these
security problems. Its wide experience is empowering the different organizations to grow their
business with high-level flexibility by best-of-breed cloud technologies. It was the first
organization of the Europe dealing in the Microsoft Cloud Solution Provider program. It is
mainly dealing with Microsoft office 365, Microsoft Dynamics CRM, Email Encryption,
Professional consulting, Microsoft Enterprise Mobility Suite, and Email Archiving.
Security Problems of CobWeb
CobWeb is facing different types of security problem. Some of them are following:
Physical break-ins: It brings greater risk to the physical security of the organization than
hackers. Due to the break-in employees of the organization leave the office and move on
to other competitor’s organization (Alhawari, 2012). On the other hand, physical break-
ins lost the important data which may fall into the wrong hands and can misuse by the
others.
The homepage of the CobWeb was hacked recently: Hacking brings serious problems for
the working of the organization. The homepage of the organization is recently hacked due
to which sensitive information of the organization leaked. This will damage the credit
ratings of the organization from different consumer agencies (Whitman, 2013).
Data loss due to large employee negligence: Loss of necessary data due to the employee
negligence brings serious problem in the success of the organization. In the absence of
Risk Management 2
necessary data, they cannot proceed further which will bring big monetary loss to the
organization.
The network administrator of the organization complains that the organization permits
free access to anything on the network for everyone who asks for it: Due to this offer of
the organization, everyone can access to the website of the organization (Stoneburner,
2013). In such case hacking chances are more which ultimately influence the
performance of the organization in a negative context.
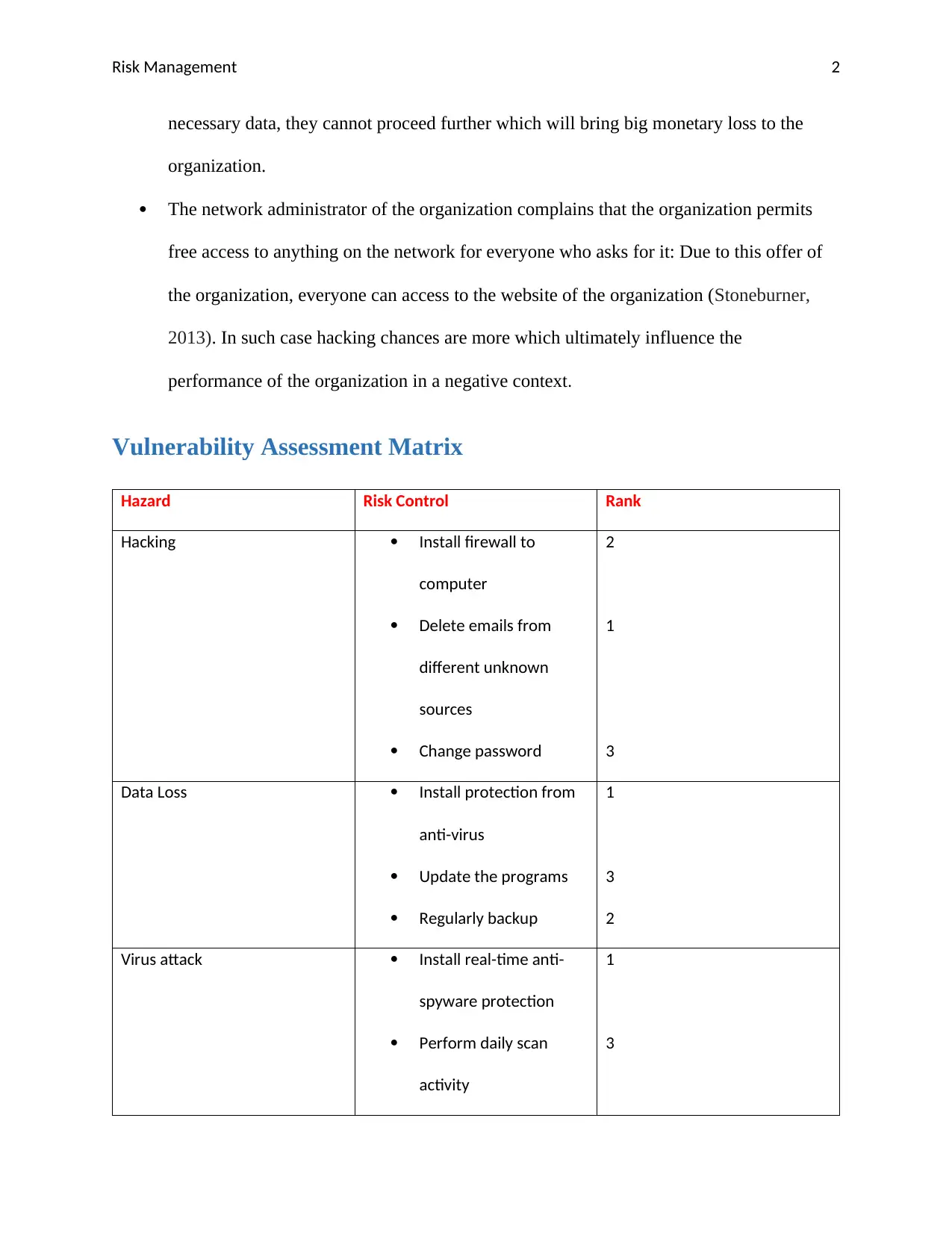
Vulnerability Assessment Matrix
Hazard Risk Control Rank
Hacking Install firewall to
computer
Delete emails from
different unknown
sources
Change password
2
1
3
Data Loss Install protection from
anti-virus
Update the programs
Regularly backup
1
3
2
Virus attack Install real-time anti-
spyware protection
Perform daily scan
activity
1
3
necessary data, they cannot proceed further which will bring big monetary loss to the
organization.
The network administrator of the organization complains that the organization permits
free access to anything on the network for everyone who asks for it: Due to this offer of
the organization, everyone can access to the website of the organization (Stoneburner,
2013). In such case hacking chances are more which ultimately influence the
performance of the organization in a negative context.
Vulnerability Assessment Matrix
Hazard Risk Control Rank
Hacking Install firewall to
computer
Delete emails from
different unknown
sources
Change password
2
1
3
Data Loss Install protection from
anti-virus
Update the programs
Regularly backup
1
3
2
Virus attack Install real-time anti-
spyware protection
Perform daily scan
activity
1
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Risk Management 3
Use of hardware-based
firewall technology
2
Security control measures
Security in the Cobweb organization can also maintain by adopting following measures:
Anti-Virus Software: It works as the policeman at the gate of the computer system. It
helps the management of the CabWeb in protecting their computers from different types
of incoming threats. It is the job of the antivirus software to keep up with the recent
threats which may cause heavy loss to the organization (Willcocks, 2013).
Logical Access Control: Unauthorized acts can bring devastating effects on the
organization. It helps the organization in controlling its access measures for system,
information, processes, and programs. It controls the security with the help of
applications, operating systems, and security packages.
Countermeasures for controlling risk
All the above-mentioned security problems can resolve by the organization with the help of
below-mentioned provisions:
To resolve the security problem due to the physical break-ins, the organization need to
train its staff in the social engineering (Cavusoglu, 2015). This will give them knowledge
about the email or social networking sites with which they can stop the security attack on
the organization.
Use of hardware-based
firewall technology
2
Security control measures
Security in the Cobweb organization can also maintain by adopting following measures:
Anti-Virus Software: It works as the policeman at the gate of the computer system. It
helps the management of the CabWeb in protecting their computers from different types
of incoming threats. It is the job of the antivirus software to keep up with the recent
threats which may cause heavy loss to the organization (Willcocks, 2013).
Logical Access Control: Unauthorized acts can bring devastating effects on the
organization. It helps the organization in controlling its access measures for system,
information, processes, and programs. It controls the security with the help of
applications, operating systems, and security packages.
Countermeasures for controlling risk
All the above-mentioned security problems can resolve by the organization with the help of
below-mentioned provisions:
To resolve the security problem due to the physical break-ins, the organization need to
train its staff in the social engineering (Cavusoglu, 2015). This will give them knowledge
about the email or social networking sites with which they can stop the security attack on
the organization.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Risk Management 4
To resolve the problems related to the hacking, the organization should change the IP
address of their systems, and this proves a significant tool for preventing hacking. In
addition, the organization should set a password and should keep it secret. This will
prevent unnecessary access to the server (Peltier, 2016).
To prevent the data losses situations, the organization need to train its employees and
should take strict actions against the employees who are not behaving properly.
Furthermore, the organization need not give the free access to its private things. This will
influence the performance of the organization negatively.
Conclusion
After studying all this, it can be concluded that security of data and the other important assets are
necessary to the success of CobWeb. If it wants to maintain its competitive advantage, strong
actions should take to resolve security problems. All suggested measures help the organization in
resolving its security problems and ensure the larger security of data.
To resolve the problems related to the hacking, the organization should change the IP
address of their systems, and this proves a significant tool for preventing hacking. In
addition, the organization should set a password and should keep it secret. This will
prevent unnecessary access to the server (Peltier, 2016).
To prevent the data losses situations, the organization need to train its employees and
should take strict actions against the employees who are not behaving properly.
Furthermore, the organization need not give the free access to its private things. This will
influence the performance of the organization negatively.
Conclusion
After studying all this, it can be concluded that security of data and the other important assets are
necessary to the success of CobWeb. If it wants to maintain its competitive advantage, strong
actions should take to resolve security problems. All suggested measures help the organization in
resolving its security problems and ensure the larger security of data.

Risk Management 5
References
Alhawari, S., Karadsheh, L., Talet, A. N., & Mansour, E. (2012). Knowledge-based risk
management framework for information technology project. International Journal of
Information Management, 32(1), 50-65.
Stoneburner, G., Goguen, A., & Feringa, A. (2013). Risk management guide for information
technology systems. NIST.
Willcocks, L. (2013). Information management: the evaluation of information systems
investments. Springer.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Cavusoglu, H., Cavusoglu, H., Son, J. Y., & Benbasat, I. (2015). Institutional pressures in
security management: Direct and indirect influences on organizational investment in information
security control resources. Information & Management, 52(4), 385-400.
Whitman, M. E., & Mattord, H. J. (2013). Management of information security. Nelson
Education.
References
Alhawari, S., Karadsheh, L., Talet, A. N., & Mansour, E. (2012). Knowledge-based risk
management framework for information technology project. International Journal of
Information Management, 32(1), 50-65.
Stoneburner, G., Goguen, A., & Feringa, A. (2013). Risk management guide for information
technology systems. NIST.
Willcocks, L. (2013). Information management: the evaluation of information systems
investments. Springer.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Cavusoglu, H., Cavusoglu, H., Son, J. Y., & Benbasat, I. (2015). Institutional pressures in
security management: Direct and indirect influences on organizational investment in information
security control resources. Information & Management, 52(4), 385-400.
Whitman, M. E., & Mattord, H. J. (2013). Management of information security. Nelson
Education.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





