University of Cumberlands - Risk Management in Business Model Report
VerifiedAdded on 2022/09/07
|5
|742
|16
Report
AI Summary
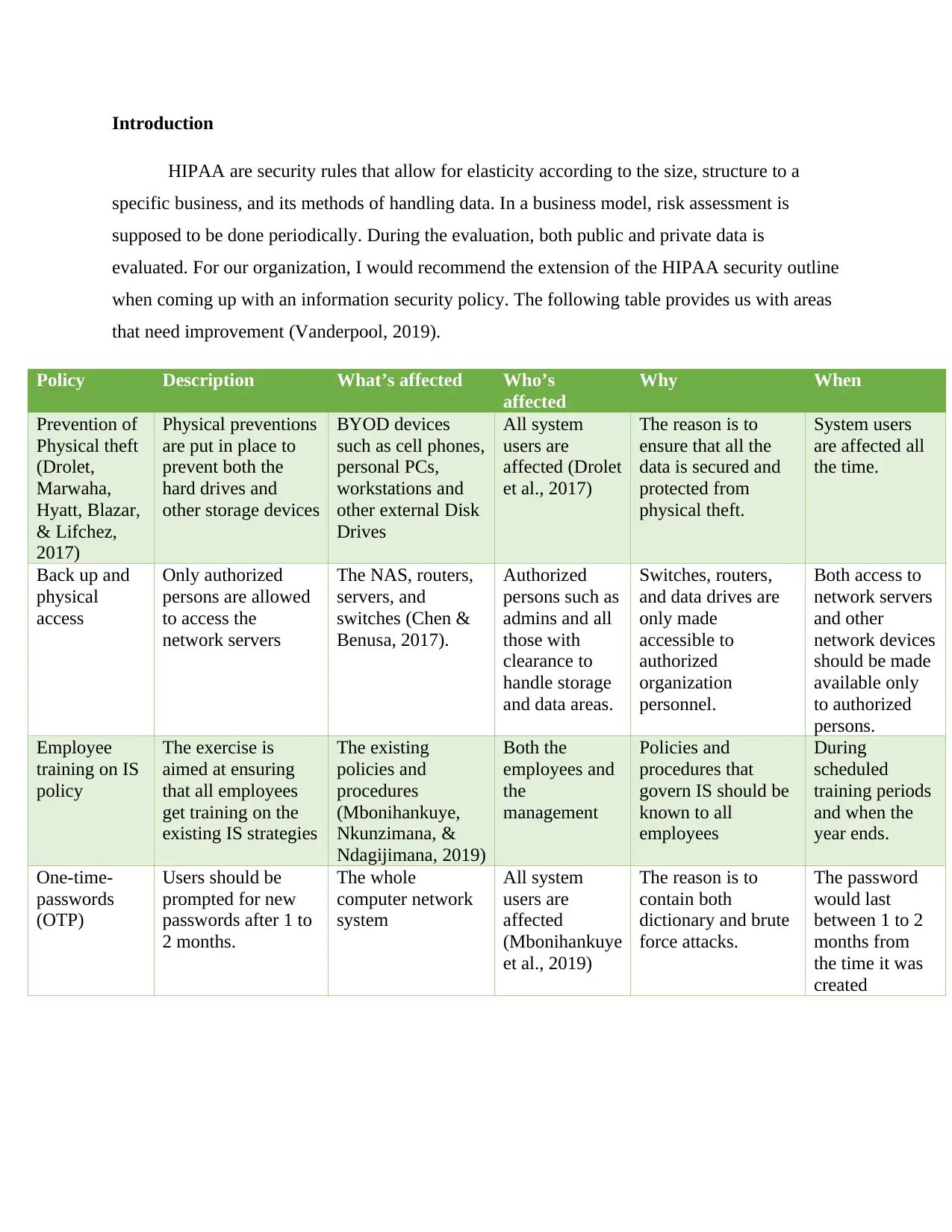
This report examines the current state of risk management within a healthcare organization, highlighting deficiencies in information security and the absence of critical security components. It identifies risks related to the organization's computer network and data security, while acknowledging its compliance with HIPAA and other external regulations. The report recommends extending HIPAA security guidelines to create a comprehensive information security policy and provides a table detailing areas needing improvement, such as physical security, network access control, and employee training on information security policies. The report emphasizes the importance of ongoing risk assessment and proposes specific measures to enhance the security of patient, employee, and supplier data. The conclusion emphasizes the need for improved security procedures and suggests that the implementation of these recommendations will lead to a more secure system.
1 out of 5











![[object Object]](/_next/static/media/star-bottom.7253800d.svg)