PRJM 6003 Assignment 1 - Project Risk Management for Cloud Platforms
VerifiedAdded on 2023/04/23
|7
|3957
|483
Report
AI Summary
This report assesses the risks associated with implementing a cloud platform within a business organization, focusing on data breaching as a primary concern. It details how cybercriminals can exploit vulnerabilities in cloud systems to access sensitive data, including methods like network bypassing and social engineering. The report identifies unpatched security vulnerabilities and malware as key causes of data breaches, emphasizing the importance of regular patching and robust security measures. A qualitative risk analysis is conducted, evaluating the consequences and probabilities of risks such as bandwidth costs, data breaching, service quality, and governance. Finally, the report proposes risk treatment strategies, including regular password changes, data encryption, and the implementation of antivirus software, to mitigate these risks and enhance data security. Desklib provides access to similar solved assignments and resources for students.

PRJM 6003 ASSIGNMENT 1
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
Part 1
A. Data breaching will be the main issue that might act as a risk in case of implementation of
the cloud platform in the business organization. Losing of important data will be the major
issue in the prosecution of the data breaching. In case of using the cloud platform the data
will be stored in the database of the cloud system. This will insist the circumstance that the
management of the data that are stored will be performed as per the protocols of the cloud
based platform. The criminals can infiltrate the data that are stored in the database of the
cloud system. This data infiltrating can be performed with the help of the accessing of the
local files that are stored in the computer network system. With the help of network
bypassing the prosecution of the data that are stored in the database can also be performed.
Network bypassing is the major method that is used by the cyber criminals to gain
admittance to the statistics that are warehoused in the cloud database. This processing is
performed with the help of the remote system. With the help of the remote system the
main advantage that will be enjoyed includes the aspect that the management of the data
breaching gets easier for the imposters. The steps that are mainly followed by the cyber
criminals include research regarding the loop holes that are present in the system. This
system includes the fact that the cloud system is thoroughly discussed. With proper analysis
of the details pros and cons of the security of the business organization can be well
measured. After understanding of the issues present, the cyber-criminal makes the first
contact with the network using the social attack mechanism. After establishing the initial
contact with the system, the main target victim in this case is the employees of the
organization. The log in credentials of the employees are initially accessed. With the help of
the data that are gathered from the employees of the organization. After getting into the
cloud network, the imposter can attack the data that are present in the cloud networking
system. After gaining access to the data, tunnelling of data is done. In case tunnelling of data
is performed in an efficient manner, the cybercriminal attack is considered to be successful.
The main causes of performing data breaching is to fetch informations that are private in
nature. Gaining financial information is also another major aspect of the system. With the
help of the data breaching the foremost improvement that will be appreciated includes
gaining data of the competitors of the business organization. Gaining of legal information
will act harmful in the prosecution of the data management as the legal data can be pirated.
This piracy of data will lead to legal issues in the business organization.
B. 2 key causes are as follows: -
Unpatched security vulnerabilities: Leaving the software in an unpatched manner
leads to the unforced errors. This issue can be present in both small and big
companies. This issue is also termed as the zero day computer issue. This leads to
the fact that the patching of the data that are present in the database f the cloud
system includes better fixing of the law loops that are present in the database. This
issue is termed to be zero day because the outcome of the attack that will affect the
system has a tenure of less than a day. In case any personnel finds a potential
security threat he or she might inform he organization regarding the present issue.
This issue can be mitigated with the help of patching the data. Sometimes the
hackers are the first person to know about the issue that is present in the
networking system. In that case the imposter will attack the cloud database and tis
attack will occur without any prior notice. This N-day vulnerability can be fixed only
with the help of patching, In case the data that are stored in the cloud computing
system are unpatched updating of the software will not be provided. In this case the
loop-hole that are present in the commencement of the scheme he min issue that is
contemporary embraces the fact that the management of the project gets
performed as per the unpatched data gaining access to the data centre gets easier.
Implementation of proper password is very important. In case proper password
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
Part 1
A. Data breaching will be the main issue that might act as a risk in case of implementation of
the cloud platform in the business organization. Losing of important data will be the major
issue in the prosecution of the data breaching. In case of using the cloud platform the data
will be stored in the database of the cloud system. This will insist the circumstance that the
management of the data that are stored will be performed as per the protocols of the cloud
based platform. The criminals can infiltrate the data that are stored in the database of the
cloud system. This data infiltrating can be performed with the help of the accessing of the
local files that are stored in the computer network system. With the help of network
bypassing the prosecution of the data that are stored in the database can also be performed.
Network bypassing is the major method that is used by the cyber criminals to gain
admittance to the statistics that are warehoused in the cloud database. This processing is
performed with the help of the remote system. With the help of the remote system the
main advantage that will be enjoyed includes the aspect that the management of the data
breaching gets easier for the imposters. The steps that are mainly followed by the cyber
criminals include research regarding the loop holes that are present in the system. This
system includes the fact that the cloud system is thoroughly discussed. With proper analysis
of the details pros and cons of the security of the business organization can be well
measured. After understanding of the issues present, the cyber-criminal makes the first
contact with the network using the social attack mechanism. After establishing the initial
contact with the system, the main target victim in this case is the employees of the
organization. The log in credentials of the employees are initially accessed. With the help of
the data that are gathered from the employees of the organization. After getting into the
cloud network, the imposter can attack the data that are present in the cloud networking
system. After gaining access to the data, tunnelling of data is done. In case tunnelling of data
is performed in an efficient manner, the cybercriminal attack is considered to be successful.
The main causes of performing data breaching is to fetch informations that are private in
nature. Gaining financial information is also another major aspect of the system. With the
help of the data breaching the foremost improvement that will be appreciated includes
gaining data of the competitors of the business organization. Gaining of legal information
will act harmful in the prosecution of the data management as the legal data can be pirated.
This piracy of data will lead to legal issues in the business organization.
B. 2 key causes are as follows: -
Unpatched security vulnerabilities: Leaving the software in an unpatched manner
leads to the unforced errors. This issue can be present in both small and big
companies. This issue is also termed as the zero day computer issue. This leads to
the fact that the patching of the data that are present in the database f the cloud
system includes better fixing of the law loops that are present in the database. This
issue is termed to be zero day because the outcome of the attack that will affect the
system has a tenure of less than a day. In case any personnel finds a potential
security threat he or she might inform he organization regarding the present issue.
This issue can be mitigated with the help of patching the data. Sometimes the
hackers are the first person to know about the issue that is present in the
networking system. In that case the imposter will attack the cloud database and tis
attack will occur without any prior notice. This N-day vulnerability can be fixed only
with the help of patching, In case the data that are stored in the cloud computing
system are unpatched updating of the software will not be provided. In this case the
loop-hole that are present in the commencement of the scheme he min issue that is
contemporary embraces the fact that the management of the project gets
performed as per the unpatched data gaining access to the data centre gets easier.
Implementation of proper password is very important. In case proper password
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
PRJM 6003 ASSIGNMENT 1
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
setting is not done un-patching the patched data gets easier for the imposters.
Hence unpatched data prosecution can be one of the major issue. These are the
main reason that unpatched data is considered to be data breaching terminology.
Malware: Malicious software presence also leads to data breaching. Malware are a
common form of worm that is injected in the computing system for gaining
unauthenticated access to the data set that are present in the cloud system. This
malware worms are mainly transmitted once usage of internet is done in a regular
manner without proper security measures. With the help of the cloud computing
platform the core shortcoming that is contemporary embraces the statistic that the
commencement of the project will be performed in a negative manner. The worms
and the viruses are treated differentially but this process falls under the subheading
of the malware. This introduction of the malware will introduce the aspect that the
prosecution of the spyware and the adware. This introduction of the spyware and
the adware increases the data breaching of the data that are present in the cloud
computation platform. With the introduction of the malware it gets easy for the
imposters to corrupt the data that are present in the cloud computing platform. This
corruption of data leads to violation of the company policies. This violation of the
company policy leads to data breaching. With help of malware alteration of the data
can be performed and this reduces the robustness in the management of the
protocol. Hence introduction can be considered as a key cause of data breaching in
the cloud computing system through the cloud computing.
Part 2
A.
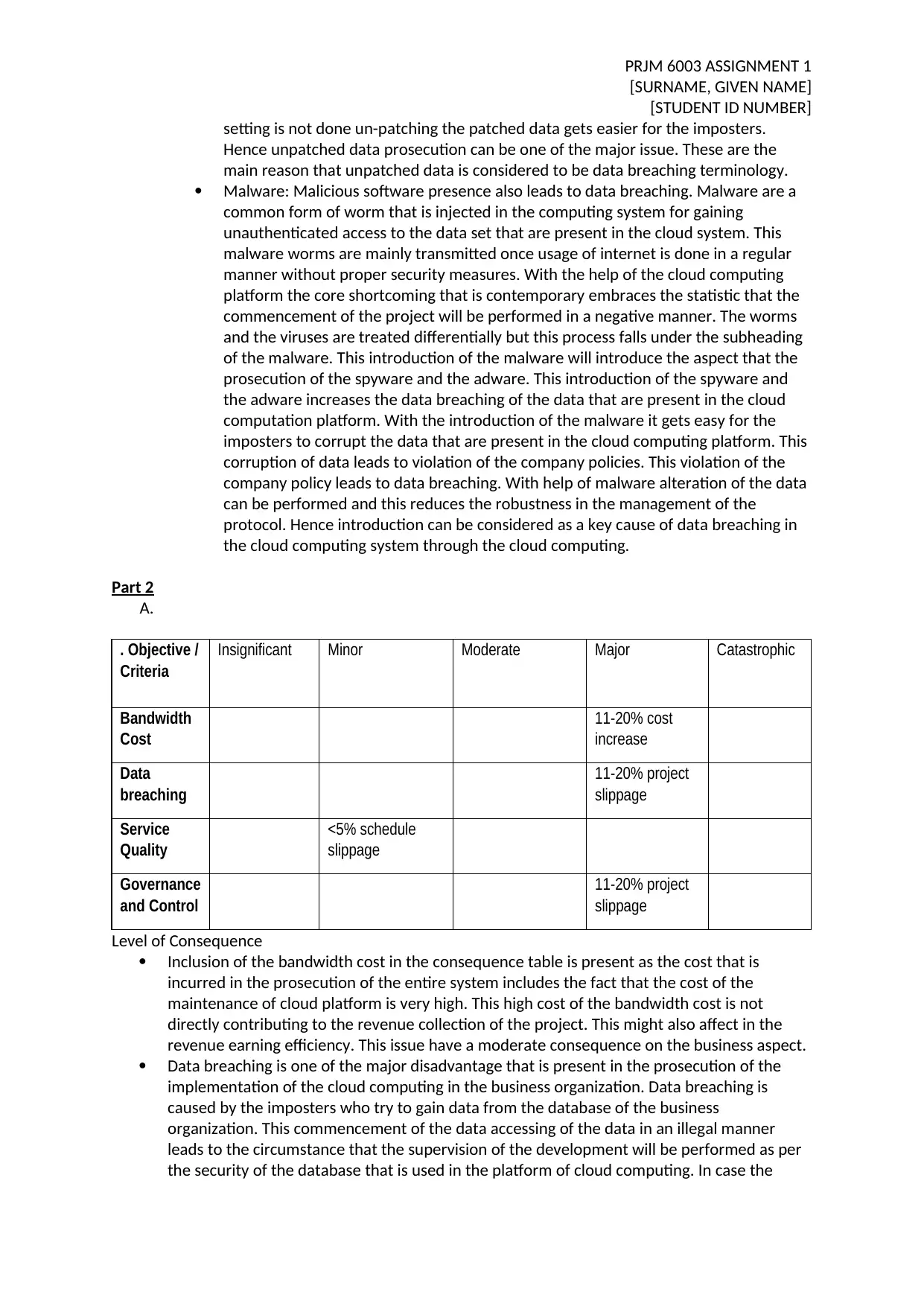
. Objective /
Criteria
Insignificant Minor Moderate Major Catastrophic
Bandwidth
Cost
11-20% cost
increase
Data
breaching
11-20% project
slippage
Service
Quality
<5% schedule
slippage
Governance
and Control
11-20% project
slippage
Level of Consequence
Inclusion of the bandwidth cost in the consequence table is present as the cost that is
incurred in the prosecution of the entire system includes the fact that the cost of the
maintenance of cloud platform is very high. This high cost of the bandwidth cost is not
directly contributing to the revenue collection of the project. This might also affect in the
revenue earning efficiency. This issue have a moderate consequence on the business aspect.
Data breaching is one of the major disadvantage that is present in the prosecution of the
implementation of the cloud computing in the business organization. Data breaching is
caused by the imposters who try to gain data from the database of the business
organization. This commencement of the data accessing of the data in an illegal manner
leads to the circumstance that the supervision of the development will be performed as per
the security of the database that is used in the platform of cloud computing. In case the
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
setting is not done un-patching the patched data gets easier for the imposters.
Hence unpatched data prosecution can be one of the major issue. These are the
main reason that unpatched data is considered to be data breaching terminology.
Malware: Malicious software presence also leads to data breaching. Malware are a
common form of worm that is injected in the computing system for gaining
unauthenticated access to the data set that are present in the cloud system. This
malware worms are mainly transmitted once usage of internet is done in a regular
manner without proper security measures. With the help of the cloud computing
platform the core shortcoming that is contemporary embraces the statistic that the
commencement of the project will be performed in a negative manner. The worms
and the viruses are treated differentially but this process falls under the subheading
of the malware. This introduction of the malware will introduce the aspect that the
prosecution of the spyware and the adware. This introduction of the spyware and
the adware increases the data breaching of the data that are present in the cloud
computation platform. With the introduction of the malware it gets easy for the
imposters to corrupt the data that are present in the cloud computing platform. This
corruption of data leads to violation of the company policies. This violation of the
company policy leads to data breaching. With help of malware alteration of the data
can be performed and this reduces the robustness in the management of the
protocol. Hence introduction can be considered as a key cause of data breaching in
the cloud computing system through the cloud computing.
Part 2
A.
. Objective /
Criteria
Insignificant Minor Moderate Major Catastrophic
Bandwidth
Cost
11-20% cost
increase
Data
breaching
11-20% project
slippage
Service
Quality
<5% schedule
slippage
Governance
and Control
11-20% project
slippage
Level of Consequence
Inclusion of the bandwidth cost in the consequence table is present as the cost that is
incurred in the prosecution of the entire system includes the fact that the cost of the
maintenance of cloud platform is very high. This high cost of the bandwidth cost is not
directly contributing to the revenue collection of the project. This might also affect in the
revenue earning efficiency. This issue have a moderate consequence on the business aspect.
Data breaching is one of the major disadvantage that is present in the prosecution of the
implementation of the cloud computing in the business organization. Data breaching is
caused by the imposters who try to gain data from the database of the business
organization. This commencement of the data accessing of the data in an illegal manner
leads to the circumstance that the supervision of the development will be performed as per
the security of the database that is used in the platform of cloud computing. In case the
PRJM 6003 ASSIGNMENT 1
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
cloud computing platform is highly robust then occurrence of this issue will not exist. This
issue have a major consequence.
Service quality is another risk as the data that are stored in the database of the cloud
platform is monitored by the third party organizations. The organizations that provides the
cloud platform is in charge of the data storage of the organization. Hence management of
the data will remain an issue in the projection of completion of the project. Hence the
quality of the service that will be refrained from the database of the cloud computing can be
prosecuted as per the management of the cloud computing system. This system has a minor
consequence.
Governance of the data that are deposited in the database of the cloud is not possible by the
business organization whose data is being stored in the data base, the foremost purpose of
this issue is that the management of the project will be performed by a third party business
organization. This process has a high consequence.
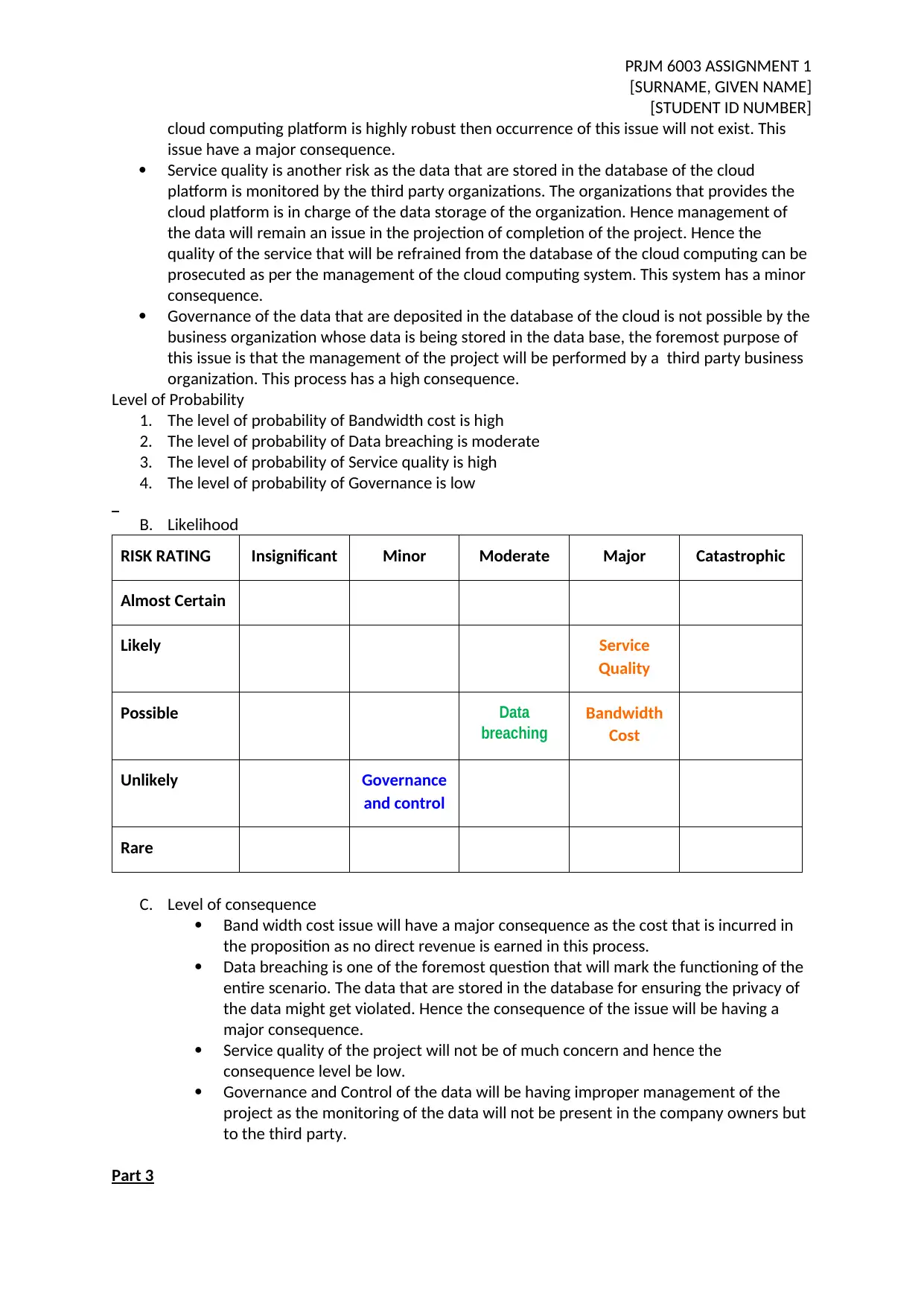
Level of Probability
1. The level of probability of Bandwidth cost is high
2. The level of probability of Data breaching is moderate
3. The level of probability of Service quality is high
4. The level of probability of Governance is low
B. Likelihood
RISK RATING Insignificant Minor Moderate Major Catastrophic
Almost Certain
Likely Service
Quality
Possible Data
breaching
Bandwidth
Cost
Unlikely Governance
and control
Rare
C. Level of consequence
Band width cost issue will have a major consequence as the cost that is incurred in
the proposition as no direct revenue is earned in this process.
Data breaching is one of the foremost question that will mark the functioning of the
entire scenario. The data that are stored in the database for ensuring the privacy of
the data might get violated. Hence the consequence of the issue will be having a
major consequence.
Service quality of the project will not be of much concern and hence the
consequence level be low.
Governance and Control of the data will be having improper management of the
project as the monitoring of the data will not be present in the company owners but
to the third party.
Part 3
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
cloud computing platform is highly robust then occurrence of this issue will not exist. This
issue have a major consequence.
Service quality is another risk as the data that are stored in the database of the cloud
platform is monitored by the third party organizations. The organizations that provides the
cloud platform is in charge of the data storage of the organization. Hence management of
the data will remain an issue in the projection of completion of the project. Hence the
quality of the service that will be refrained from the database of the cloud computing can be
prosecuted as per the management of the cloud computing system. This system has a minor
consequence.
Governance of the data that are deposited in the database of the cloud is not possible by the
business organization whose data is being stored in the data base, the foremost purpose of
this issue is that the management of the project will be performed by a third party business
organization. This process has a high consequence.
Level of Probability
1. The level of probability of Bandwidth cost is high
2. The level of probability of Data breaching is moderate
3. The level of probability of Service quality is high
4. The level of probability of Governance is low
B. Likelihood
RISK RATING Insignificant Minor Moderate Major Catastrophic
Almost Certain
Likely Service
Quality
Possible Data
breaching
Bandwidth
Cost
Unlikely Governance
and control
Rare
C. Level of consequence
Band width cost issue will have a major consequence as the cost that is incurred in
the proposition as no direct revenue is earned in this process.
Data breaching is one of the foremost question that will mark the functioning of the
entire scenario. The data that are stored in the database for ensuring the privacy of
the data might get violated. Hence the consequence of the issue will be having a
major consequence.
Service quality of the project will not be of much concern and hence the
consequence level be low.
Governance and Control of the data will be having improper management of the
project as the monitoring of the data will not be present in the company owners but
to the third party.
Part 3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

PRJM 6003 ASSIGNMENT 1
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
A. 3 possible treatments are as follows: -
Changing of the cloud user password in regular intervals. With the help of
implementation of the secret questions in the cloud system database. With the help
of the reference set of questionnaire the main benefit that is present is that the
answers that will be present in the security section will be having the answers to the
questions that will have to be answered before entering the cloud system. The
answers that are to be provided must be kept secretive and hence the management
of the project is performed with high robustness in aspect of security. For gaining
access to the cloud data base every personnel needs to answer the set questions. In
case the personnel fails to answer these question correctly accessing to cloud
database is denied.
Encryption of the data is also one of the most important aspect that will be required
for securing the data and increase the privacy of the data that are warehoused in
the cloud database. The data that are being transacted from one platform to
another are performed with the help of the data encryption key. This is one of the
main reason that the prosecution of the project will not allow other means to access
the data that are encrypted. Due to this method of security the main advantage that
is because even after gaining access to the data the information that are encrypted
cannot be read or altered and hence the motive of the imposters fail,
Implementation of antivirus and other malware software: Implementation of
malware and antivirus leads to the fact that the administration of the development
will get more secured. With the help of the usage of the antivirus the data that are
stored n the cloud based platform can be protected from the introduction of the
viruses. The virus, malware and Trojan horses are introduced in the cloud computing
device to alter the data in an undesired manner. Blocking e data from being used by
the authentic user is also another major issue. Hence implementation of anti-virus
will act beneficial
B. The residual risk that is present after implementation of the risk treatments are not very
high. The main residual risk that remains is that the imposter who has been trying to gain
access to the data in an unauthorized manner can be present in the team itself. This will lead
to the fact that security measures might fail to protect the data that are to be protected with
the help of encrypt of the data. In case an employee of the organization betrays the security
system and shares the encryption key to the competitors of the organization. Another
residual risk that will remain in the system is that despite the implementation of the proper
password and questionnaire gaining access to the database of the cloud computing is
possible. With the help of the VPN system, hoaxing of the IP addressing can be performed
and hence gaining of the data from blocked URL will be possible which will be acting as one
of the main issue.
C. Providing of the passwords in each step of the data protection might act as a secondary risk.
Main reason of this security measure being a secondary risk is that the password might be
forgotten and saving of the password options are not provided for increasing the security of
the project. In case password of a single stage is unavailable, gaining data of that particular
department is required it gets impossible to gain access to the data. To mitigate this issue
implementation of the biometric system in the cloud computing platform must be done. This
will ensure the aspect that the statistics that are deposited in the database of the cloud
system will stay protected and no passwords will be required. This is one of the security
measure that can be implemented. Despite the management of the entire project without
the usage of the password, protection of the data will be very easy and the authenticity of
the usage of the data will be very high as well.
Part 4
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
A. 3 possible treatments are as follows: -
Changing of the cloud user password in regular intervals. With the help of
implementation of the secret questions in the cloud system database. With the help
of the reference set of questionnaire the main benefit that is present is that the
answers that will be present in the security section will be having the answers to the
questions that will have to be answered before entering the cloud system. The
answers that are to be provided must be kept secretive and hence the management
of the project is performed with high robustness in aspect of security. For gaining
access to the cloud data base every personnel needs to answer the set questions. In
case the personnel fails to answer these question correctly accessing to cloud
database is denied.
Encryption of the data is also one of the most important aspect that will be required
for securing the data and increase the privacy of the data that are warehoused in
the cloud database. The data that are being transacted from one platform to
another are performed with the help of the data encryption key. This is one of the
main reason that the prosecution of the project will not allow other means to access
the data that are encrypted. Due to this method of security the main advantage that
is because even after gaining access to the data the information that are encrypted
cannot be read or altered and hence the motive of the imposters fail,
Implementation of antivirus and other malware software: Implementation of
malware and antivirus leads to the fact that the administration of the development
will get more secured. With the help of the usage of the antivirus the data that are
stored n the cloud based platform can be protected from the introduction of the
viruses. The virus, malware and Trojan horses are introduced in the cloud computing
device to alter the data in an undesired manner. Blocking e data from being used by
the authentic user is also another major issue. Hence implementation of anti-virus
will act beneficial
B. The residual risk that is present after implementation of the risk treatments are not very
high. The main residual risk that remains is that the imposter who has been trying to gain
access to the data in an unauthorized manner can be present in the team itself. This will lead
to the fact that security measures might fail to protect the data that are to be protected with
the help of encrypt of the data. In case an employee of the organization betrays the security
system and shares the encryption key to the competitors of the organization. Another
residual risk that will remain in the system is that despite the implementation of the proper
password and questionnaire gaining access to the database of the cloud computing is
possible. With the help of the VPN system, hoaxing of the IP addressing can be performed
and hence gaining of the data from blocked URL will be possible which will be acting as one
of the main issue.
C. Providing of the passwords in each step of the data protection might act as a secondary risk.
Main reason of this security measure being a secondary risk is that the password might be
forgotten and saving of the password options are not provided for increasing the security of
the project. In case password of a single stage is unavailable, gaining data of that particular
department is required it gets impossible to gain access to the data. To mitigate this issue
implementation of the biometric system in the cloud computing platform must be done. This
will ensure the aspect that the statistics that are deposited in the database of the cloud
system will stay protected and no passwords will be required. This is one of the security
measure that can be implemented. Despite the management of the entire project without
the usage of the password, protection of the data will be very easy and the authenticity of
the usage of the data will be very high as well.
Part 4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
PRJM 6003 ASSIGNMENT 1
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
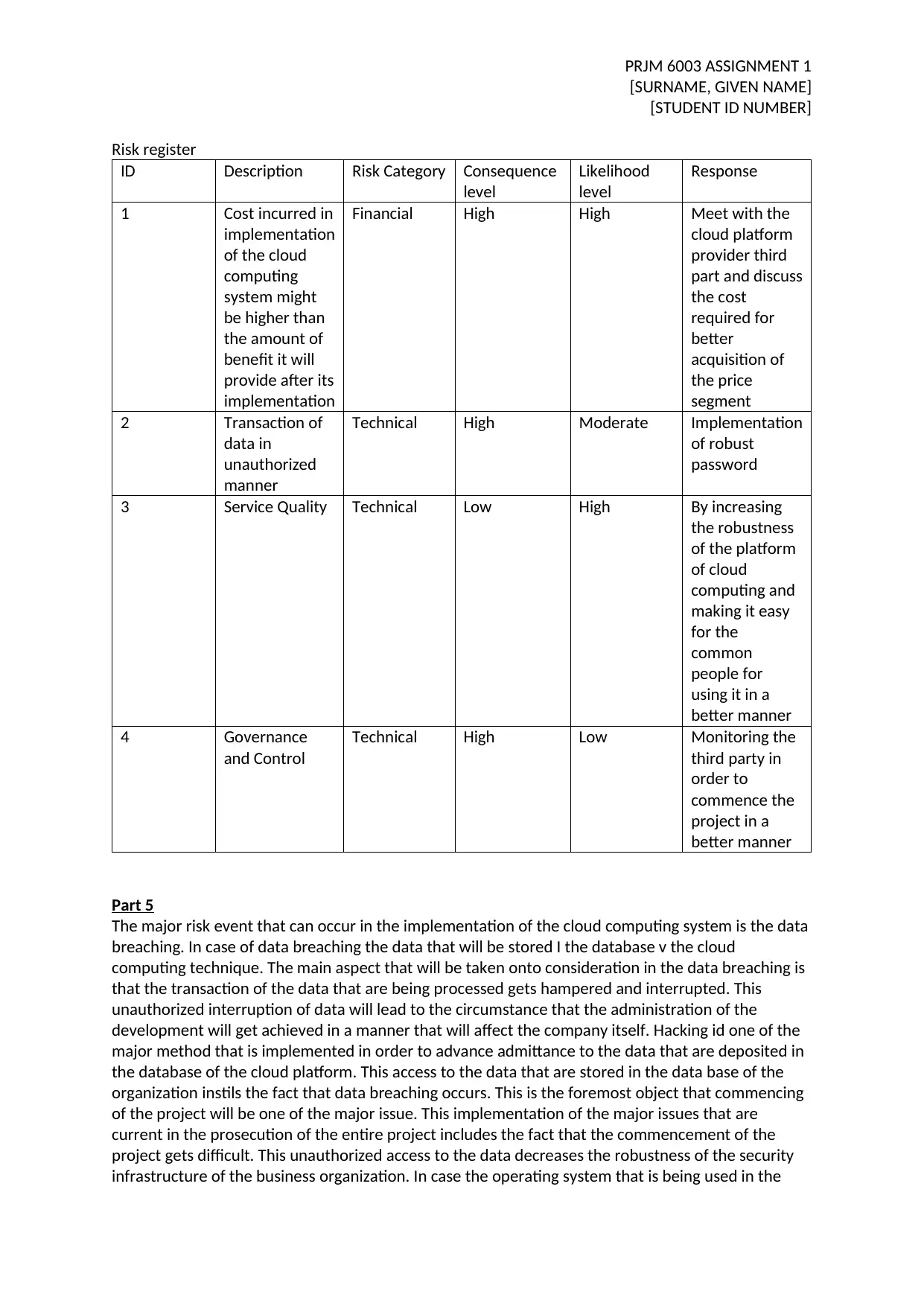
Risk register
ID Description Risk Category Consequence
level
Likelihood
level
Response
1 Cost incurred in
implementation
of the cloud
computing
system might
be higher than
the amount of
benefit it will
provide after its
implementation
Financial High High Meet with the
cloud platform
provider third
part and discuss
the cost
required for
better
acquisition of
the price
segment
2 Transaction of
data in
unauthorized
manner
Technical High Moderate Implementation
of robust
password
3 Service Quality Technical Low High By increasing
the robustness
of the platform
of cloud
computing and
making it easy
for the
common
people for
using it in a
better manner
4 Governance
and Control
Technical High Low Monitoring the
third party in
order to
commence the
project in a
better manner
Part 5
The major risk event that can occur in the implementation of the cloud computing system is the data
breaching. In case of data breaching the data that will be stored I the database v the cloud
computing technique. The main aspect that will be taken onto consideration in the data breaching is
that the transaction of the data that are being processed gets hampered and interrupted. This
unauthorized interruption of data will lead to the circumstance that the administration of the
development will get achieved in a manner that will affect the company itself. Hacking id one of the
major method that is implemented in order to advance admittance to the data that are deposited in
the database of the cloud platform. This access to the data that are stored in the data base of the
organization instils the fact that data breaching occurs. This is the foremost object that commencing
of the project will be one of the major issue. This implementation of the major issues that are
current in the prosecution of the entire project includes the fact that the commencement of the
project gets difficult. This unauthorized access to the data decreases the robustness of the security
infrastructure of the business organization. In case the operating system that is being used in the
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
Risk register
ID Description Risk Category Consequence
level
Likelihood
level
Response
1 Cost incurred in
implementation
of the cloud
computing
system might
be higher than
the amount of
benefit it will
provide after its
implementation
Financial High High Meet with the
cloud platform
provider third
part and discuss
the cost
required for
better
acquisition of
the price
segment
2 Transaction of
data in
unauthorized
manner
Technical High Moderate Implementation
of robust
password
3 Service Quality Technical Low High By increasing
the robustness
of the platform
of cloud
computing and
making it easy
for the
common
people for
using it in a
better manner
4 Governance
and Control
Technical High Low Monitoring the
third party in
order to
commence the
project in a
better manner
Part 5
The major risk event that can occur in the implementation of the cloud computing system is the data
breaching. In case of data breaching the data that will be stored I the database v the cloud
computing technique. The main aspect that will be taken onto consideration in the data breaching is
that the transaction of the data that are being processed gets hampered and interrupted. This
unauthorized interruption of data will lead to the circumstance that the administration of the
development will get achieved in a manner that will affect the company itself. Hacking id one of the
major method that is implemented in order to advance admittance to the data that are deposited in
the database of the cloud platform. This access to the data that are stored in the data base of the
organization instils the fact that data breaching occurs. This is the foremost object that commencing
of the project will be one of the major issue. This implementation of the major issues that are
current in the prosecution of the entire project includes the fact that the commencement of the
project gets difficult. This unauthorized access to the data decreases the robustness of the security
infrastructure of the business organization. In case the operating system that is being used in the
PRJM 6003 ASSIGNMENT 1
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
cloud platform is not the latest OS, finding the loop holes pf the platform gets easier for them. This is
the sole reason that the projection of the data breaching gets easier for the business organization.
Implementation of proper passwords and the biometric system will act helpful in the prosecution of
the data management that are stored in the database of the cloud computing system. This tips to
the fact that the organization of the statistics that are deposited in the database of the cloud
computing system stays protected and the imposters do to gain the access to the data that are
stored in the database of the cloud computing system. With the help of the encryption of the data
that are being transacted thorough the cloud computing platform the entre process gets easier.
With the help of the encryption of the data, even if the imposter’s expansion admittance to the
figures that are stored on the database of the organization no information can be found in case
decryption of the data is not performed. For performing the decryption of the data decryption key
will be required. This will require the admin access. Hence securing the data will stay intact.
Strategic risk management process is used in this process. With the help of the strategic risk
management the main advantage that is present includes the act that the processing of the data
management will get prosecuted and this is the main reason that prosecution of the risks that are
present are calculated initially before implementing of the process. After implementation of the
strategic risk management, the risks are identified and hence the steps that are to be taken for
mitigating the same are also processed. This indications to the fact that the intensity of the risk
affects gets reduced.
The entire process is performed with accuracy and intensity. This leads to the fact that the
organization of the development gets achieved keeping in mind the statistic that the prosecution of
the project will get performed in a manner that will prosecute the risk management in a better
manner. This implementation of the risk management will incur the aspect that the prosecution of
the entire business organization will be managed. With the help of this risk management the risks
that might affect the business organization is detected and hence the prosecution of these risks can
be taken. With the help of the risk management processing the main advantage that is performed is
that risk retention and risk mitigation techniques can be analysed and proper decision making can be
performed.
Hence it can be stated that this risk management is well performed.
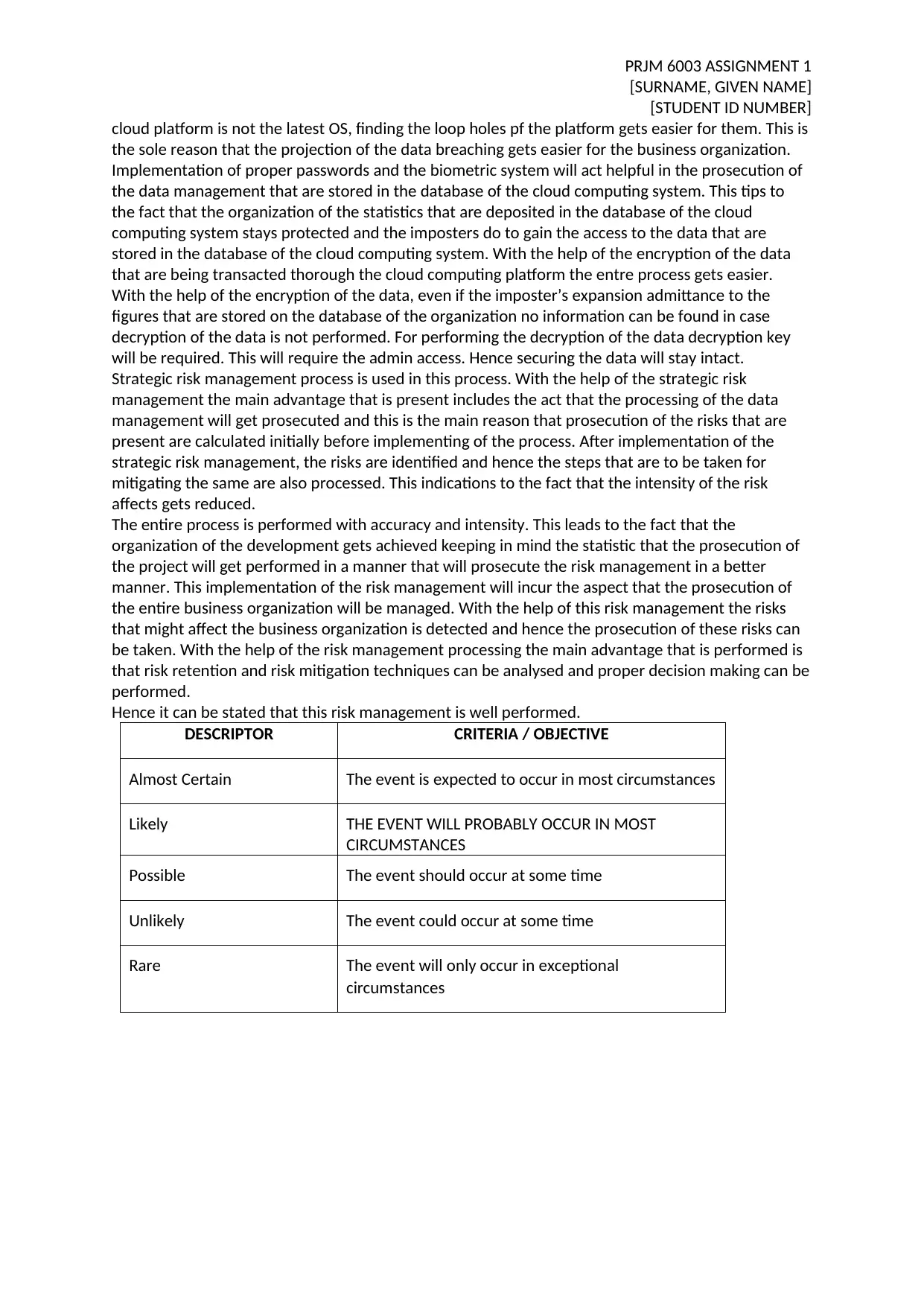
DESCRIPTOR CRITERIA / OBJECTIVE
Almost Certain The event is expected to occur in most circumstances
Likely THE EVENT WILL PROBABLY OCCUR IN MOST
CIRCUMSTANCES
Possible The event should occur at some time
Unlikely The event could occur at some time
Rare The event will only occur in exceptional
circumstances
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
cloud platform is not the latest OS, finding the loop holes pf the platform gets easier for them. This is
the sole reason that the projection of the data breaching gets easier for the business organization.
Implementation of proper passwords and the biometric system will act helpful in the prosecution of
the data management that are stored in the database of the cloud computing system. This tips to
the fact that the organization of the statistics that are deposited in the database of the cloud
computing system stays protected and the imposters do to gain the access to the data that are
stored in the database of the cloud computing system. With the help of the encryption of the data
that are being transacted thorough the cloud computing platform the entre process gets easier.
With the help of the encryption of the data, even if the imposter’s expansion admittance to the
figures that are stored on the database of the organization no information can be found in case
decryption of the data is not performed. For performing the decryption of the data decryption key
will be required. This will require the admin access. Hence securing the data will stay intact.
Strategic risk management process is used in this process. With the help of the strategic risk
management the main advantage that is present includes the act that the processing of the data
management will get prosecuted and this is the main reason that prosecution of the risks that are
present are calculated initially before implementing of the process. After implementation of the
strategic risk management, the risks are identified and hence the steps that are to be taken for
mitigating the same are also processed. This indications to the fact that the intensity of the risk
affects gets reduced.
The entire process is performed with accuracy and intensity. This leads to the fact that the
organization of the development gets achieved keeping in mind the statistic that the prosecution of
the project will get performed in a manner that will prosecute the risk management in a better
manner. This implementation of the risk management will incur the aspect that the prosecution of
the entire business organization will be managed. With the help of this risk management the risks
that might affect the business organization is detected and hence the prosecution of these risks can
be taken. With the help of the risk management processing the main advantage that is performed is
that risk retention and risk mitigation techniques can be analysed and proper decision making can be
performed.
Hence it can be stated that this risk management is well performed.
DESCRIPTOR CRITERIA / OBJECTIVE
Almost Certain The event is expected to occur in most circumstances
Likely THE EVENT WILL PROBABLY OCCUR IN MOST
CIRCUMSTANCES
Possible The event should occur at some time
Unlikely The event could occur at some time
Rare The event will only occur in exceptional
circumstances
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

PRJM 6003 ASSIGNMENT 1
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
Bibliography
Aljawarneh, Shadi A., Ali Alawneh, and Reem Jaradat. "Cloud security engineering: Early stages of
SDLC." Future Generation Computer Systems 74 (2017): 385-392.
Aljawarneh, Shadi A., and Muneer O. Bani Yassein. "A conceptual security framework for cloud
computing issues." International Journal of Intelligent Information Technologies (IJIIT) 12, no. 2
(2016): 12-24.
Almorsy, Mohamed, John Grundy, and Ingo Müller. "An analysis of the cloud computing security
problem." arXiv preprint arXiv:1609.01107 (2016).
Alrawais, Arwa, Abdulrahman Alhothaily, Chunqiang Hu, and Xiuzhen Cheng. "Fog computing for the
internet of things: Security and privacy issues." IEEE Internet Computing 21, no. 2 (2017): 34-42.
Botta, Alessio, Walter De Donato, Valerio Persico, and Antonio Pescapé. "Integration of cloud
computing and internet of things: a survey." Future generation computer systems 56 (2016): 684-700.
Chang, Victor, Yen-Hung Kuo, and Muthu Ramachandran. "Cloud computing adoption framework: A
security framework for business clouds." Future Generation Computer Systems57 (2016): 24-41.
Hashem, Ibrahim Abaker Targio, Ibrar Yaqoob, Nor Badrul Anuar, Salimah Mokhtar, Abdullah Gani,
and Samee Ullah Khan. "The rise of “big data” on cloud computing: Review and open research
issues." Information systems 47 (2015): 98-115.
Khan, Minhaj Ahmad. "A survey of security issues for cloud computing." Journal of network and
computer applications 71 (2016): 11-29.
Puthal, Deepak, B. P. S. Sahoo, Sambit Mishra, and Satyabrata Swain. "Cloud computing features,
issues, and challenges: a big picture." In 2015 International Conference on Computational
Intelligence and Networks, pp. 116-123. IEEE, 2015.
Rao, R. Velumadhava, and K. Selvamani. "Data security challenges and its solutions in cloud
computing." Procedia Computer Science 48 (2015): 204-209.
Rittinghouse, John W., and James F. Ransome. Cloud computing: implementation, management, and
security. CRC press, 2016.
Sen, Jaydip. "Security and privacy issues in cloud computing." In Cloud Technology: Concepts,
Methodologies, Tools, and Applications, pp. 1585-1630. IGI Global, 2015.
Stojmenovic, Ivan, Sheng Wen, Xinyi Huang, and Hao Luan. "An overview of fog computing and its
security issues." Concurrency and Computation: Practice and Experience 28, no. 10 (2016): 2991-
3005.
Yi, Shanhe, Cheng Li, and Qun Li. "A survey of fog computing: concepts, applications and issues."
In Proceedings of the 2015 workshop on mobile big data, pp. 37-42. ACM, 2015.
Yi, Shanhe, Zhengrui Qin, and Qun Li. "Security and privacy issues of fog computing: A survey."
In International conference on wireless algorithms, systems, and applications, pp. 685-695. Springer,
Cham, 2015.
[SURNAME, GIVEN NAME]
[STUDENT ID NUMBER]
Bibliography
Aljawarneh, Shadi A., Ali Alawneh, and Reem Jaradat. "Cloud security engineering: Early stages of
SDLC." Future Generation Computer Systems 74 (2017): 385-392.
Aljawarneh, Shadi A., and Muneer O. Bani Yassein. "A conceptual security framework for cloud
computing issues." International Journal of Intelligent Information Technologies (IJIIT) 12, no. 2
(2016): 12-24.
Almorsy, Mohamed, John Grundy, and Ingo Müller. "An analysis of the cloud computing security
problem." arXiv preprint arXiv:1609.01107 (2016).
Alrawais, Arwa, Abdulrahman Alhothaily, Chunqiang Hu, and Xiuzhen Cheng. "Fog computing for the
internet of things: Security and privacy issues." IEEE Internet Computing 21, no. 2 (2017): 34-42.
Botta, Alessio, Walter De Donato, Valerio Persico, and Antonio Pescapé. "Integration of cloud
computing and internet of things: a survey." Future generation computer systems 56 (2016): 684-700.
Chang, Victor, Yen-Hung Kuo, and Muthu Ramachandran. "Cloud computing adoption framework: A
security framework for business clouds." Future Generation Computer Systems57 (2016): 24-41.
Hashem, Ibrahim Abaker Targio, Ibrar Yaqoob, Nor Badrul Anuar, Salimah Mokhtar, Abdullah Gani,
and Samee Ullah Khan. "The rise of “big data” on cloud computing: Review and open research
issues." Information systems 47 (2015): 98-115.
Khan, Minhaj Ahmad. "A survey of security issues for cloud computing." Journal of network and
computer applications 71 (2016): 11-29.
Puthal, Deepak, B. P. S. Sahoo, Sambit Mishra, and Satyabrata Swain. "Cloud computing features,
issues, and challenges: a big picture." In 2015 International Conference on Computational
Intelligence and Networks, pp. 116-123. IEEE, 2015.
Rao, R. Velumadhava, and K. Selvamani. "Data security challenges and its solutions in cloud
computing." Procedia Computer Science 48 (2015): 204-209.
Rittinghouse, John W., and James F. Ransome. Cloud computing: implementation, management, and
security. CRC press, 2016.
Sen, Jaydip. "Security and privacy issues in cloud computing." In Cloud Technology: Concepts,
Methodologies, Tools, and Applications, pp. 1585-1630. IGI Global, 2015.
Stojmenovic, Ivan, Sheng Wen, Xinyi Huang, and Hao Luan. "An overview of fog computing and its
security issues." Concurrency and Computation: Practice and Experience 28, no. 10 (2016): 2991-
3005.
Yi, Shanhe, Cheng Li, and Qun Li. "A survey of fog computing: concepts, applications and issues."
In Proceedings of the 2015 workshop on mobile big data, pp. 37-42. ACM, 2015.
Yi, Shanhe, Zhengrui Qin, and Qun Li. "Security and privacy issues of fog computing: A survey."
In International conference on wireless algorithms, systems, and applications, pp. 685-695. Springer,
Cham, 2015.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





