Asia Pacific College: SBM4304 IS Security and Risk Management Report
VerifiedAdded on 2022/09/13
|12
|2651
|15
Report
AI Summary
This report delves into the critical aspects of IS security and risk management within the realm of the Internet of Things (IoT). It examines various attacks, including unsecured devices, hijacking, and privacy leaks, highlighting the vulnerabilities inherent in IoT systems. The report provides a detailed analysis of security protection measures, emphasizing the importance of device individuality, verification, and appropriate default outlines. It explores authentication protocols such as M2M, IoV, and EMAP, assessing their effectiveness in securing communications and managing risks. The discussion also covers the significance of user control, remote access, and security updates in maintaining a robust security posture. The report concludes by underscoring the need for IoT constructors to embed security into the architecture and functionality of their products, advocating for proactive measures to safeguard against emerging threats and ensure the continued viability of IoT technologies. It emphasizes the importance of a layered security approach, encompassing hardware, firmware, OS, and software to withstand aggressive environments and ensure longevity. The report stresses the significance of authentication protocols and their role in establishing secure connections and preventing unauthorized access. This report provides a comprehensive overview of IoT security challenges and offers insights into practical strategies for mitigating risks and safeguarding data.

0Running head: IS SECURITY AND RISK MANAGEMENT
IS SECURITY AND RISK MANAGEMENT
Name of the Student:
Name of the University:
Author’s Note:
IS SECURITY AND RISK MANAGEMENT
Name of the Student:
Name of the University:
Author’s Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1IS SECURITY AND RISK MANAGEMENT
Introduction:-
The term internet of things is the very essential for the current society. With the help of
IoT many organization are recently evolved huge applications for the benefit. IoT applications
potential to bring huge value into human lives. With innovative superior sensors wireless
networks and radical computing abilities, the Internet of Things might be the next frontline in the
contest for its portion of the wallet. ABC organizations are trying to launch some security and
privacy appliances for company betterment. IoT applications are very basic applications which
can be essential for the current society. Wearable technology is a symbol of IoT devices and
possibly is one of the original businesses to have organized the IoT at its facility (Chen et al.
2018). The people happen to understand heart rate monitors, Fit Bits and smart watches
universally these days. These IoT tools are morally integrated with HD technology which creates
it probable for them to connect or cooperate over the internet effortlessly and can also be coped
and measured distantly when compulsory. Around there are around 8 billion persons on this
planet, but surprisingly by the year 2022 with a growing graph of IoT tools, there might be
around 25 billion IoT smart devices implementing with a rise in the request of fifth generation
network.
Discussion:-
Attacks:-
In current years, IoT has become involved in argument related to safety issues. Many of
the difficulties have been formerly knowledgeable by other key internet mechanisms. The
difficulties with IoT safety is connected to the extremely fast development of smart home
Introduction:-
The term internet of things is the very essential for the current society. With the help of
IoT many organization are recently evolved huge applications for the benefit. IoT applications
potential to bring huge value into human lives. With innovative superior sensors wireless
networks and radical computing abilities, the Internet of Things might be the next frontline in the
contest for its portion of the wallet. ABC organizations are trying to launch some security and
privacy appliances for company betterment. IoT applications are very basic applications which
can be essential for the current society. Wearable technology is a symbol of IoT devices and
possibly is one of the original businesses to have organized the IoT at its facility (Chen et al.
2018). The people happen to understand heart rate monitors, Fit Bits and smart watches
universally these days. These IoT tools are morally integrated with HD technology which creates
it probable for them to connect or cooperate over the internet effortlessly and can also be coped
and measured distantly when compulsory. Around there are around 8 billion persons on this
planet, but surprisingly by the year 2022 with a growing graph of IoT tools, there might be
around 25 billion IoT smart devices implementing with a rise in the request of fifth generation
network.
Discussion:-
Attacks:-
In current years, IoT has become involved in argument related to safety issues. Many of
the difficulties have been formerly knowledgeable by other key internet mechanisms. The
difficulties with IoT safety is connected to the extremely fast development of smart home

2IS SECURITY AND RISK MANAGEMENT
computerization devices linking to the network. As of 2019, the technology rising pains have
become principally excruciating with some issues at play.
Privacy leaks:-
Capable hackers can cause significant injury just by identifying an unsafe IoT device that
is dripping the IP address, which can, in turn, be applied to identify a built-up location.
Information safety experts mention safeguarding IoT networks by means of computer-generated
VPN technology. It’s now probable to encode whole traffic over user ISP by connecting a VPN
on user router, and the similar functionality isn’t distant for other IoT tools. With the correct
VPN, user can defend a complete smart household network and keep user IP private.
The quantity of IoT devices is fairly large. IoT devices are classically discrete across the
sphere, permitting for instant message between associated devices. Domestic uses, automobiles,
TVs and other devices are accumulating and communicating their documents through the
internet in order to finish a diversity of tasks. Operators are characteristically ignorant of how
much documents is essentially collected and how the documents is applied with another. As a
consequence of the gathering, passing and distributing of information among these networked
tools and data receivers there is an apprehension among safety and privacy specialists about how
this documents is collected, shared and applied.
Unsecured devices:-
This risk has been the most deceptive since the beginning of IoT, and device builders
have been partially complicit. When IoT tools are shipped to stocks with default “management”
usernames and “5784” PINs customers cannot be sensibly expected to modify and protected the
identifications unless the producer claims upon it over directions and reference resources. One of
computerization devices linking to the network. As of 2019, the technology rising pains have
become principally excruciating with some issues at play.
Privacy leaks:-
Capable hackers can cause significant injury just by identifying an unsafe IoT device that
is dripping the IP address, which can, in turn, be applied to identify a built-up location.
Information safety experts mention safeguarding IoT networks by means of computer-generated
VPN technology. It’s now probable to encode whole traffic over user ISP by connecting a VPN
on user router, and the similar functionality isn’t distant for other IoT tools. With the correct
VPN, user can defend a complete smart household network and keep user IP private.
The quantity of IoT devices is fairly large. IoT devices are classically discrete across the
sphere, permitting for instant message between associated devices. Domestic uses, automobiles,
TVs and other devices are accumulating and communicating their documents through the
internet in order to finish a diversity of tasks. Operators are characteristically ignorant of how
much documents is essentially collected and how the documents is applied with another. As a
consequence of the gathering, passing and distributing of information among these networked
tools and data receivers there is an apprehension among safety and privacy specialists about how
this documents is collected, shared and applied.
Unsecured devices:-
This risk has been the most deceptive since the beginning of IoT, and device builders
have been partially complicit. When IoT tools are shipped to stocks with default “management”
usernames and “5784” PINs customers cannot be sensibly expected to modify and protected the
identifications unless the producer claims upon it over directions and reference resources. One of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3IS SECURITY AND RISK MANAGEMENT
the greatest public susceptibilities in firmware, unauthenticated access permits risk performers to
gain access to an IoT device, which creates it easy to achieve device documents and any controls
delivered by it. Threat performers can effortlessly gain access to tools when the firmware has a
feeble verification mechanism (Khan and Salah 2018). These appliances can sort from password-
based and single-factor verification to structures based on feeble cryptographic procedures that
can be wrecked into with brute-force occurrences. Repairing information in beta forms of IoT
devices prepares designers with internal systems information of a device. Inappropriately,
debugging structures are frequently left in manufacture devices, giving attackers allows to the
similar inside acquaintance of a device.
Hijacking:-
Smart applications, like as many secure IoT systems and appliances, have the similar
computing power and functionality of a current tablet, which denotes they can be stolen and
turned into email servers (Huh, Cho and Kim 2017). In a 2014 examination by info safety
research firm Proof point, a smart icebox was originate to have directed thousands of email junk
messages lacking its proprietors being conscious of the problem. Aggressors spend a huge time
observing at the code inside a device's software, trying to navigate how to root unpredictable
application behavior or smashes that can open a track to a safety breach. Buffer excesses can
permit hackers to distantly access devices and can be weapon zed to make code-injection attacks
and denial-of-service.
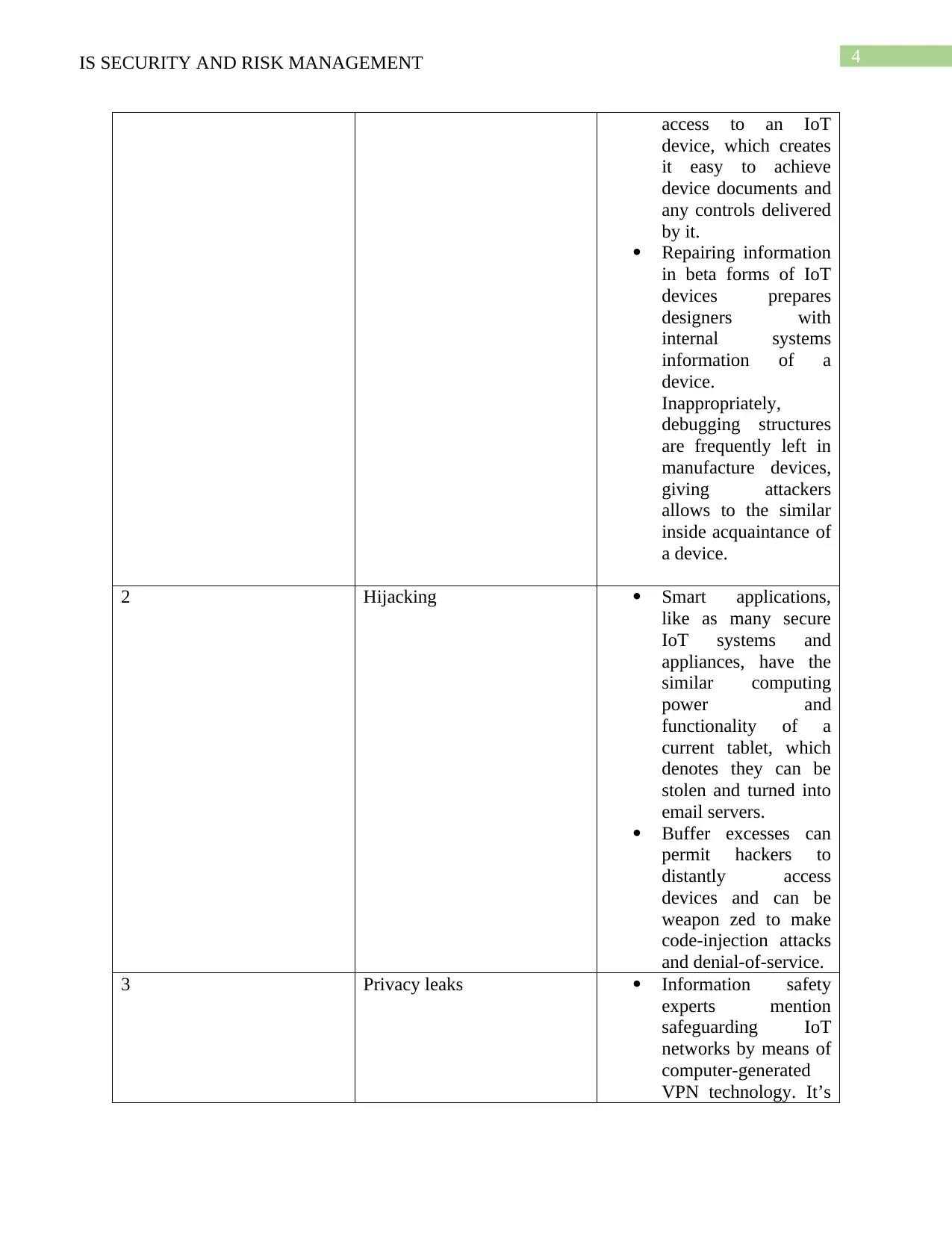
Sl, No Attack Point
1 Unsecured devices One of the greatest
public susceptibilities
in firmware,
unauthenticated
access permits risk
performers to gain
the greatest public susceptibilities in firmware, unauthenticated access permits risk performers to
gain access to an IoT device, which creates it easy to achieve device documents and any controls
delivered by it. Threat performers can effortlessly gain access to tools when the firmware has a
feeble verification mechanism (Khan and Salah 2018). These appliances can sort from password-
based and single-factor verification to structures based on feeble cryptographic procedures that
can be wrecked into with brute-force occurrences. Repairing information in beta forms of IoT
devices prepares designers with internal systems information of a device. Inappropriately,
debugging structures are frequently left in manufacture devices, giving attackers allows to the
similar inside acquaintance of a device.
Hijacking:-
Smart applications, like as many secure IoT systems and appliances, have the similar
computing power and functionality of a current tablet, which denotes they can be stolen and
turned into email servers (Huh, Cho and Kim 2017). In a 2014 examination by info safety
research firm Proof point, a smart icebox was originate to have directed thousands of email junk
messages lacking its proprietors being conscious of the problem. Aggressors spend a huge time
observing at the code inside a device's software, trying to navigate how to root unpredictable
application behavior or smashes that can open a track to a safety breach. Buffer excesses can
permit hackers to distantly access devices and can be weapon zed to make code-injection attacks
and denial-of-service.
Sl, No Attack Point
1 Unsecured devices One of the greatest
public susceptibilities
in firmware,
unauthenticated
access permits risk
performers to gain
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4IS SECURITY AND RISK MANAGEMENT
access to an IoT
device, which creates
it easy to achieve
device documents and
any controls delivered
by it.
Repairing information
in beta forms of IoT
devices prepares
designers with
internal systems
information of a
device.
Inappropriately,
debugging structures
are frequently left in
manufacture devices,
giving attackers
allows to the similar
inside acquaintance of
a device.
2 Hijacking Smart applications,
like as many secure
IoT systems and
appliances, have the
similar computing
power and
functionality of a
current tablet, which
denotes they can be
stolen and turned into
email servers.
Buffer excesses can
permit hackers to
distantly access
devices and can be
weapon zed to make
code-injection attacks
and denial-of-service.
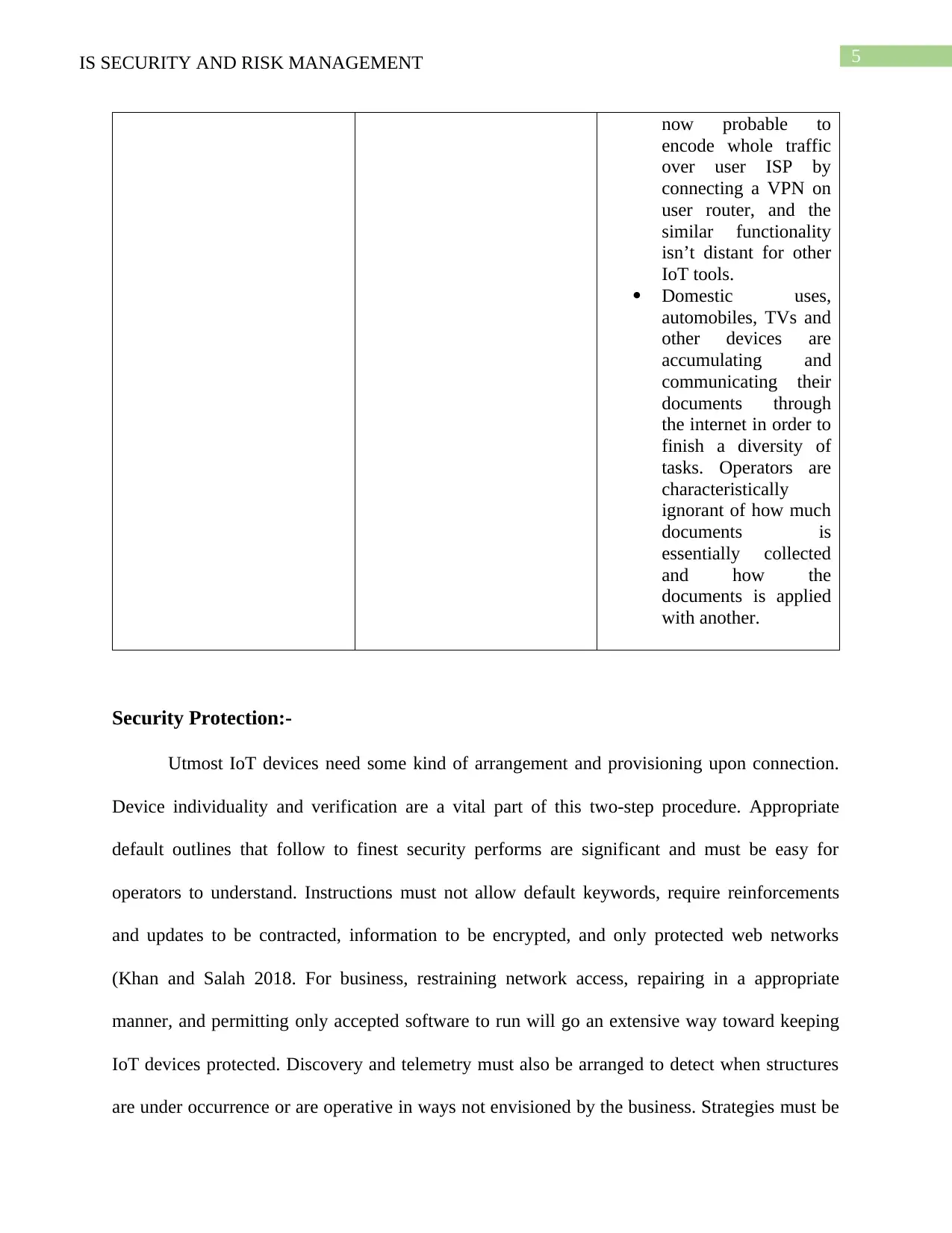
3 Privacy leaks Information safety
experts mention
safeguarding IoT
networks by means of
computer-generated
VPN technology. It’s
access to an IoT
device, which creates
it easy to achieve
device documents and
any controls delivered
by it.
Repairing information
in beta forms of IoT
devices prepares
designers with
internal systems
information of a
device.
Inappropriately,
debugging structures
are frequently left in
manufacture devices,
giving attackers
allows to the similar
inside acquaintance of
a device.
2 Hijacking Smart applications,
like as many secure
IoT systems and
appliances, have the
similar computing
power and
functionality of a
current tablet, which
denotes they can be
stolen and turned into
email servers.
Buffer excesses can
permit hackers to
distantly access
devices and can be
weapon zed to make
code-injection attacks
and denial-of-service.
3 Privacy leaks Information safety
experts mention
safeguarding IoT
networks by means of
computer-generated
VPN technology. It’s
5IS SECURITY AND RISK MANAGEMENT
now probable to
encode whole traffic
over user ISP by
connecting a VPN on
user router, and the
similar functionality
isn’t distant for other
IoT tools.
Domestic uses,
automobiles, TVs and
other devices are
accumulating and
communicating their
documents through
the internet in order to
finish a diversity of
tasks. Operators are
characteristically
ignorant of how much
documents is
essentially collected
and how the
documents is applied
with another.
Security Protection:-
Utmost IoT devices need some kind of arrangement and provisioning upon connection.
Device individuality and verification are a vital part of this two-step procedure. Appropriate
default outlines that follow to finest security performs are significant and must be easy for
operators to understand. Instructions must not allow default keywords, require reinforcements
and updates to be contracted, information to be encrypted, and only protected web networks
(Khan and Salah 2018. For business, restraining network access, repairing in a appropriate
manner, and permitting only accepted software to run will go an extensive way toward keeping
IoT devices protected. Discovery and telemetry must also be arranged to detect when structures
are under occurrence or are operative in ways not envisioned by the business. Strategies must be
now probable to
encode whole traffic
over user ISP by
connecting a VPN on
user router, and the
similar functionality
isn’t distant for other
IoT tools.
Domestic uses,
automobiles, TVs and
other devices are
accumulating and
communicating their
documents through
the internet in order to
finish a diversity of
tasks. Operators are
characteristically
ignorant of how much
documents is
essentially collected
and how the
documents is applied
with another.
Security Protection:-
Utmost IoT devices need some kind of arrangement and provisioning upon connection.
Device individuality and verification are a vital part of this two-step procedure. Appropriate
default outlines that follow to finest security performs are significant and must be easy for
operators to understand. Instructions must not allow default keywords, require reinforcements
and updates to be contracted, information to be encrypted, and only protected web networks
(Khan and Salah 2018. For business, restraining network access, repairing in a appropriate
manner, and permitting only accepted software to run will go an extensive way toward keeping
IoT devices protected. Discovery and telemetry must also be arranged to detect when structures
are under occurrence or are operative in ways not envisioned by the business. Strategies must be
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6IS SECURITY AND RISK MANAGEMENT
recognized for confidentiality, data holding, remote access, key safety, and cancelation
procedures.
For devices possessed by clients, they unaccompanied must uphold the concluding say in how
the tool is managed. Constructors and online service suppliers maintain a role in provisioning,
but the proprietors must recall control of what the plans will do. Provisioning is dissimilar than
management.
They must not have the capability to function devices external of the buyers’ specialist.
Owners must recall the power to turn on or off their products and select which online facilities
they allow to attach. This skill needs proper user documentation and verification. Allowing a
mutual default keyword is not good preparation because anyone can take over as the manager.
Imagine if Microsoft Windows came with an avoidance login password for each system. It
would make a safety nightmare because many operators would never modification it and
attackers could access as users. IoT structures must first be capable to validate their owners.
Organization functionality must also spread to authorize the proprietors to set restrictions, data
strategies, and privacy limitations that are more obstructive than those of any possible third-party
retailer (Lee and Lee 2015). Contracted security apprises should be mechanically connected as
they become accessible. The owners must be able to arrange limits for incoming and outbound
contacts, data categories, ports, and safety settings. Logs that can be lacking to a right-hand
system or observed locally should detention mistakes, as well as unanticipated and uncommon
activities. A classification for remote-warning announcements, via text, is a comfy feature on
certain devices. Lastly, a reset competence is obligatory in the occasion of an unrecoverable
cooperation or transmission of ownership.
recognized for confidentiality, data holding, remote access, key safety, and cancelation
procedures.
For devices possessed by clients, they unaccompanied must uphold the concluding say in how
the tool is managed. Constructors and online service suppliers maintain a role in provisioning,
but the proprietors must recall control of what the plans will do. Provisioning is dissimilar than
management.
They must not have the capability to function devices external of the buyers’ specialist.
Owners must recall the power to turn on or off their products and select which online facilities
they allow to attach. This skill needs proper user documentation and verification. Allowing a
mutual default keyword is not good preparation because anyone can take over as the manager.
Imagine if Microsoft Windows came with an avoidance login password for each system. It
would make a safety nightmare because many operators would never modification it and
attackers could access as users. IoT structures must first be capable to validate their owners.
Organization functionality must also spread to authorize the proprietors to set restrictions, data
strategies, and privacy limitations that are more obstructive than those of any possible third-party
retailer (Lee and Lee 2015). Contracted security apprises should be mechanically connected as
they become accessible. The owners must be able to arrange limits for incoming and outbound
contacts, data categories, ports, and safety settings. Logs that can be lacking to a right-hand
system or observed locally should detention mistakes, as well as unanticipated and uncommon
activities. A classification for remote-warning announcements, via text, is a comfy feature on
certain devices. Lastly, a reset competence is obligatory in the occasion of an unrecoverable
cooperation or transmission of ownership.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7IS SECURITY AND RISK MANAGEMENT
IoT constructors must embed safety into the architecture, boundaries, and enterprises of
their merchandises. Found and test basic safety concepts and capabilities like as
compartmentalization of documents and code, message between reliable parties, data defense
both in apply and at rest, and verification of users. Products in the upcoming will be more
influential, stock more data, and take more functionality. This denotes products must have the
ability for safety updates, feature securing, build authentication, software selection, and default
arrangements that trail industry best performs (Mahmoud et al. 2015). It all starts with the
constructor; future proofing begins at the basics. The hardware, firmware, OS, and software need
be planned to go into an aggressive atmosphere and last. IoT device consumers should inspect a
possible acquisition with this in concentration.
Authentication protocol:-
M2M:-
In order to haste up the procedure of verification and avoid validation signaling excess. It mainly
concentrated on the difficulties of group verification and key arrangement for resource-
constrained M2M tools in 3GPP networks. Exactly, the report writer planned a novel group-
based trivial authentication arrangement for resource forced M2M. The network model applied
in is based on 3GPP structure with three provinces, counting access networks, progressed packet
core, and non-3GPP province, for instance, Internet (Farooq et al. 2015). To assure the entity
communal authentication and secure key arrangement, the arrangement uses two key phases,
explicitly, (1) Initialization stage and (2) Group verification and key arrangement phase. In
addition, the scheme can confirm QoS for machine-type infrastructures devices, but the
calculation complexity is far less than schemes. In order to differentiate between dissimilar
IoT constructors must embed safety into the architecture, boundaries, and enterprises of
their merchandises. Found and test basic safety concepts and capabilities like as
compartmentalization of documents and code, message between reliable parties, data defense
both in apply and at rest, and verification of users. Products in the upcoming will be more
influential, stock more data, and take more functionality. This denotes products must have the
ability for safety updates, feature securing, build authentication, software selection, and default
arrangements that trail industry best performs (Mahmoud et al. 2015). It all starts with the
constructor; future proofing begins at the basics. The hardware, firmware, OS, and software need
be planned to go into an aggressive atmosphere and last. IoT device consumers should inspect a
possible acquisition with this in concentration.
Authentication protocol:-
M2M:-
In order to haste up the procedure of verification and avoid validation signaling excess. It mainly
concentrated on the difficulties of group verification and key arrangement for resource-
constrained M2M tools in 3GPP networks. Exactly, the report writer planned a novel group-
based trivial authentication arrangement for resource forced M2M. The network model applied
in is based on 3GPP structure with three provinces, counting access networks, progressed packet
core, and non-3GPP province, for instance, Internet (Farooq et al. 2015). To assure the entity
communal authentication and secure key arrangement, the arrangement uses two key phases,
explicitly, (1) Initialization stage and (2) Group verification and key arrangement phase. In
addition, the scheme can confirm QoS for machine-type infrastructures devices, but the
calculation complexity is far less than schemes. In order to differentiate between dissimilar

8IS SECURITY AND RISK MANAGEMENT
physical plans running the similar software and perceiving mimic occurrences. Many researchers
proposed a verification protocol for the IoT, named S2M.
This applies tree key phases, explicitly, (1) audio-handshake stage, (2) mixed-signal unit
stage, and (3) feature withdrawal and storage stage. S2M can realize variable distance
verification and active attack discovery using auditory hardware fingerprints. The presentation of
the methods in terms of confidentiality preservation is not examined, especially in contrast to the
M2M arrangement. Based on the delivery verification phase, the work is effective in terms of the
computational and message overhead associated to three structures but the confrontation to
attacks is not deliberate and no threat prototype is accessible.
IoV:-
IoV authentication protocol measured the safety association between unequal links during
V2V communications. More exactly, the proxy mobile IP arrangement, called MA-PMIP. Built
on verification phase and mobile router revocation, It can realize less location update cost
likened with the scheme and the delivery delay lower than the arrangement. In addition, it can
achieve mutual verification against verification attacks but the privacy-preserving is not
investigated compared to the M2M scheme. In order to accelerate message verification in
proposed an accelerate message confirmation protocol, named EMAP (Lee and Lee 2015).
Constructed on the withdrawal checking procedure, EMAP can overwhelmed the difficulties of
the long postponement incurred in inspecting the revocation standing of a certificate using a
credential cancelation list.
EMAP is effective in terms of computational difficulty of revocation status inspection
and the verification delay is continuous and sovereign of the number of cancelled certificates.
physical plans running the similar software and perceiving mimic occurrences. Many researchers
proposed a verification protocol for the IoT, named S2M.
This applies tree key phases, explicitly, (1) audio-handshake stage, (2) mixed-signal unit
stage, and (3) feature withdrawal and storage stage. S2M can realize variable distance
verification and active attack discovery using auditory hardware fingerprints. The presentation of
the methods in terms of confidentiality preservation is not examined, especially in contrast to the
M2M arrangement. Based on the delivery verification phase, the work is effective in terms of the
computational and message overhead associated to three structures but the confrontation to
attacks is not deliberate and no threat prototype is accessible.
IoV:-
IoV authentication protocol measured the safety association between unequal links during
V2V communications. More exactly, the proxy mobile IP arrangement, called MA-PMIP. Built
on verification phase and mobile router revocation, It can realize less location update cost
likened with the scheme and the delivery delay lower than the arrangement. In addition, it can
achieve mutual verification against verification attacks but the privacy-preserving is not
investigated compared to the M2M scheme. In order to accelerate message verification in
proposed an accelerate message confirmation protocol, named EMAP (Lee and Lee 2015).
Constructed on the withdrawal checking procedure, EMAP can overwhelmed the difficulties of
the long postponement incurred in inspecting the revocation standing of a certificate using a
credential cancelation list.
EMAP is effective in terms of computational difficulty of revocation status inspection
and the verification delay is continuous and sovereign of the number of cancelled certificates.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9IS SECURITY AND RISK MANAGEMENT
Consequently, the question rise here is can these IP work fine in the regionalized group model.
The verification scheme projected newly by researcher can response this question where it can
realize two necessities for threshold confirmation, explicitly, distinguishability and effective
traceability.
Summary and Conclusion:-
The IoT has the prospective to melodramatically increase the accessibility
of information, and is probable to transform businesses and organizations
in nearly every business everywhere the world. As such, discovery techniques to influence the
influence of the IoT is expected to
feature into the planned purposes of most knowledge companies,
irrespective of their manufacturing focus. The number of dissimilar technologies compulsory to
support the placement and additional growth of the IoT places a quality on
interoperability, and has occasioned in extensive efforts to progress
standards and practical stipulations that support unified
message between IoT components and devices. Collaboration
between several standards expansion groups and consolidation
of some present efforts will ultimately result in better clearness for IoT
technology businesses.
Consequently, the question rise here is can these IP work fine in the regionalized group model.
The verification scheme projected newly by researcher can response this question where it can
realize two necessities for threshold confirmation, explicitly, distinguishability and effective
traceability.
Summary and Conclusion:-
The IoT has the prospective to melodramatically increase the accessibility
of information, and is probable to transform businesses and organizations
in nearly every business everywhere the world. As such, discovery techniques to influence the
influence of the IoT is expected to
feature into the planned purposes of most knowledge companies,
irrespective of their manufacturing focus. The number of dissimilar technologies compulsory to
support the placement and additional growth of the IoT places a quality on
interoperability, and has occasioned in extensive efforts to progress
standards and practical stipulations that support unified
message between IoT components and devices. Collaboration
between several standards expansion groups and consolidation
of some present efforts will ultimately result in better clearness for IoT
technology businesses.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10IS SECURITY AND RISK MANAGEMENT
References:-
Chen, S., Xu, H., Liu, D., Hu, B. and Wang, H., 2014. A vision of IoT: Applications, challenges,
and opportunities with china perspective. IEEE Internet of Things journal, 1(4), pp.349-359.
Farooq, M.U., Waseem, M., Mazhar, S., Khairi, A. and Kamal, T., 2015. A review on internet of
things (IoT). International Journal of Computer Applications, 113(1), pp.1-7.
Huh, S., Cho, S. and Kim, S., 2017, February. Managing IoT devices using blockchain platform.
In 2017 19th international conference on advanced communication technology (ICACT) (pp.
464-467). IEEE.
Khan, M.A. and Salah, K., 2018. IoT security: Review, blockchain solutions, and open
challenges. Future Generation Computer Systems, 82, pp.395-411.
Lee, I. and Lee, K., 2015. The Internet of Things (IoT): Applications, investments, and
challenges for enterprises. Business Horizons, 58(4), pp.431-440.
Mahmoud, R., Yousuf, T., Aloul, F. and Zualkernan, I., 2015, December. Internet of things (IoT)
security: Current status, challenges and prospective measures. In 2015 10th International
Conference for Internet Technology and Secured Transactions (ICITST) (pp. 336-341). IEEE.
References:-
Chen, S., Xu, H., Liu, D., Hu, B. and Wang, H., 2014. A vision of IoT: Applications, challenges,
and opportunities with china perspective. IEEE Internet of Things journal, 1(4), pp.349-359.
Farooq, M.U., Waseem, M., Mazhar, S., Khairi, A. and Kamal, T., 2015. A review on internet of
things (IoT). International Journal of Computer Applications, 113(1), pp.1-7.
Huh, S., Cho, S. and Kim, S., 2017, February. Managing IoT devices using blockchain platform.
In 2017 19th international conference on advanced communication technology (ICACT) (pp.
464-467). IEEE.
Khan, M.A. and Salah, K., 2018. IoT security: Review, blockchain solutions, and open
challenges. Future Generation Computer Systems, 82, pp.395-411.
Lee, I. and Lee, K., 2015. The Internet of Things (IoT): Applications, investments, and
challenges for enterprises. Business Horizons, 58(4), pp.431-440.
Mahmoud, R., Yousuf, T., Aloul, F. and Zualkernan, I., 2015, December. Internet of things (IoT)
security: Current status, challenges and prospective measures. In 2015 10th International
Conference for Internet Technology and Secured Transactions (ICITST) (pp. 336-341). IEEE.

11IS SECURITY AND RISK MANAGEMENT
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





