Risk Management: Cybersecurity Plan for New IT Business Venture
VerifiedAdded on 2023/03/23
|7
|855
|60
Report
AI Summary
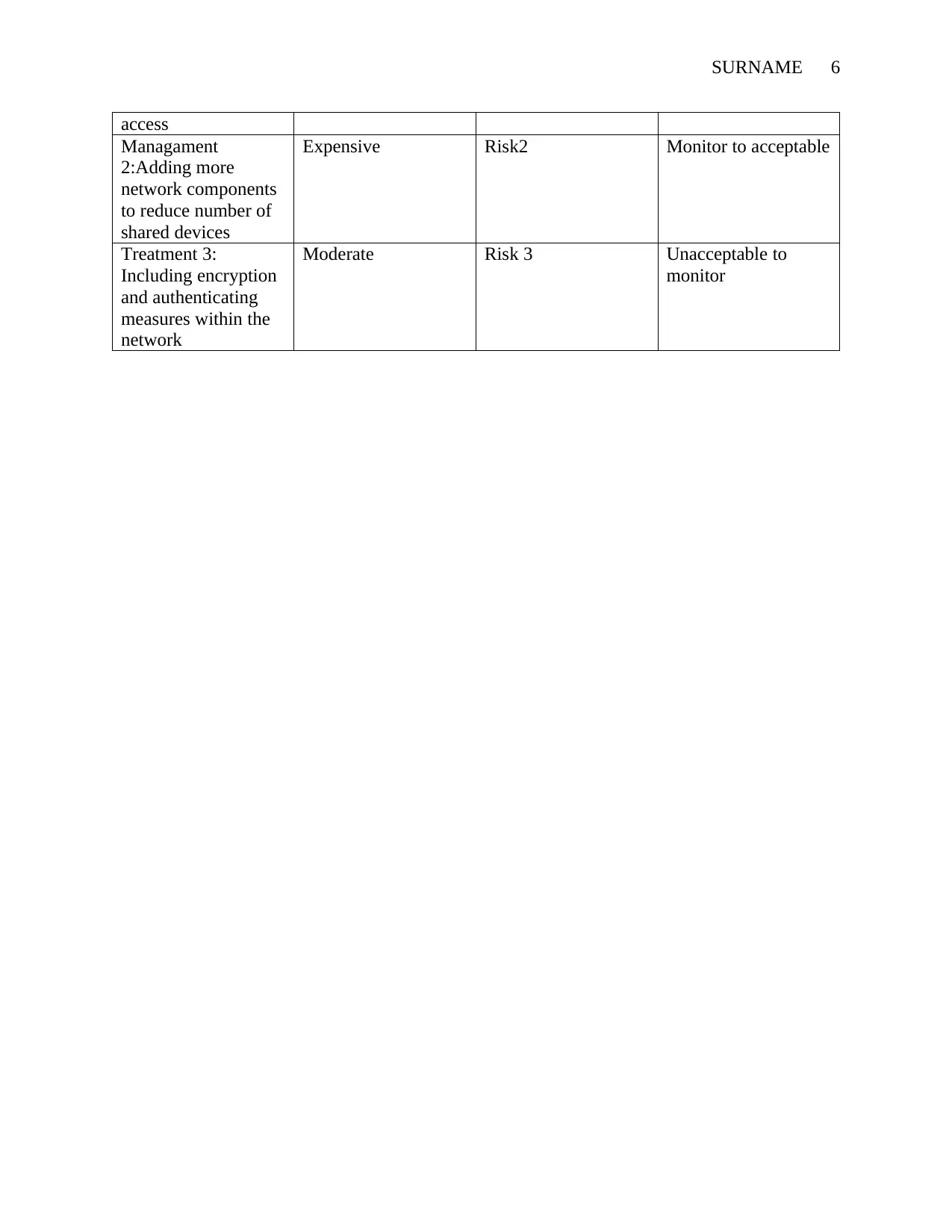
This cybersecurity risk management plan for a new IT business focuses on identifying and mitigating potential risks to protect intellectual property, financial data, and client information. The plan emphasizes defining the scope and focus of the business information system, including asset identification and data storage considerations. It involves analyzing the threat landscape, categorizing assets based on vulnerability to internal and external threats, and developing a common understanding of risk across business units. The plan incorporates cybersecurity measures using products from companies like Cisco, and addresses specific threats such as hacking, denial of service, spoofing, and tampering. It also includes a risk assessment matrix, outlining the likelihood and consequence of each threat, and proposes risk treatment strategies, such as setting up firewalls, enhancing network components, and implementing encryption and authentication measures. The goal is to create a dynamic and understandable plan that ensures data security and builds client confidence.
1 out of 7









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)