Risk Management Strategy for Financial Investment and Insurance
VerifiedAdded on 2022/12/27
|12
|4047
|1
Report
AI Summary
This report provides a comprehensive risk management strategy designed for the finance and mortgage broking sector. It begins with an analysis of various risk factors associated with financial investments and insurance products, including credit risk, governance risk, and operational risk. The report then outlines appropriate risk exposure management strategies, emphasizing the importance of a risk-aware culture, decentralized decision-making, and adherence to standards like AS/NZS ISO 31000:2009. It also details communication strategies for relevant staff and intermediaries, focusing on clear, frequent, and well-engaged communication methods. Furthermore, the report addresses personal risk assessment strategies, emphasizing the importance of documentation, contingency planning, and continuous evaluation. The implementation plan includes strategies for senior administrators, monitoring methods, and evaluation methods. The report also covers risk acceptance and rejection criteria, and the documentation of a clear risk acceptance strategy. It concludes with feedback and finalized risk acceptance criteria, providing a holistic approach to risk management within the financial industry.

Diploma of Finance and
Mortgage Broking
management
1
Mortgage Broking
management
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Contents...........................................................................................................................................2
Activity 1.........................................................................................................................................3
1. Analyse risk factors for the financial investment as well as insurance products in that
service:.........................................................................................................................................3
2. Determine appropriate risk exposure management strategies:................................................3
4. Personally manage the risk assessment strategies...................................................................5
5. Exposure factors and evaluate the risk acceptability factors...................................................5
6. Risk acceptance and rejection criteria.....................................................................................6
7. Document a clear outline of the risk acceptance strategy........................................................6
8. Feedback on and finalised the risk acceptance criteria............................................................7
Activity 2.........................................................................................................................................7
1. Implementation plan:...............................................................................................................7
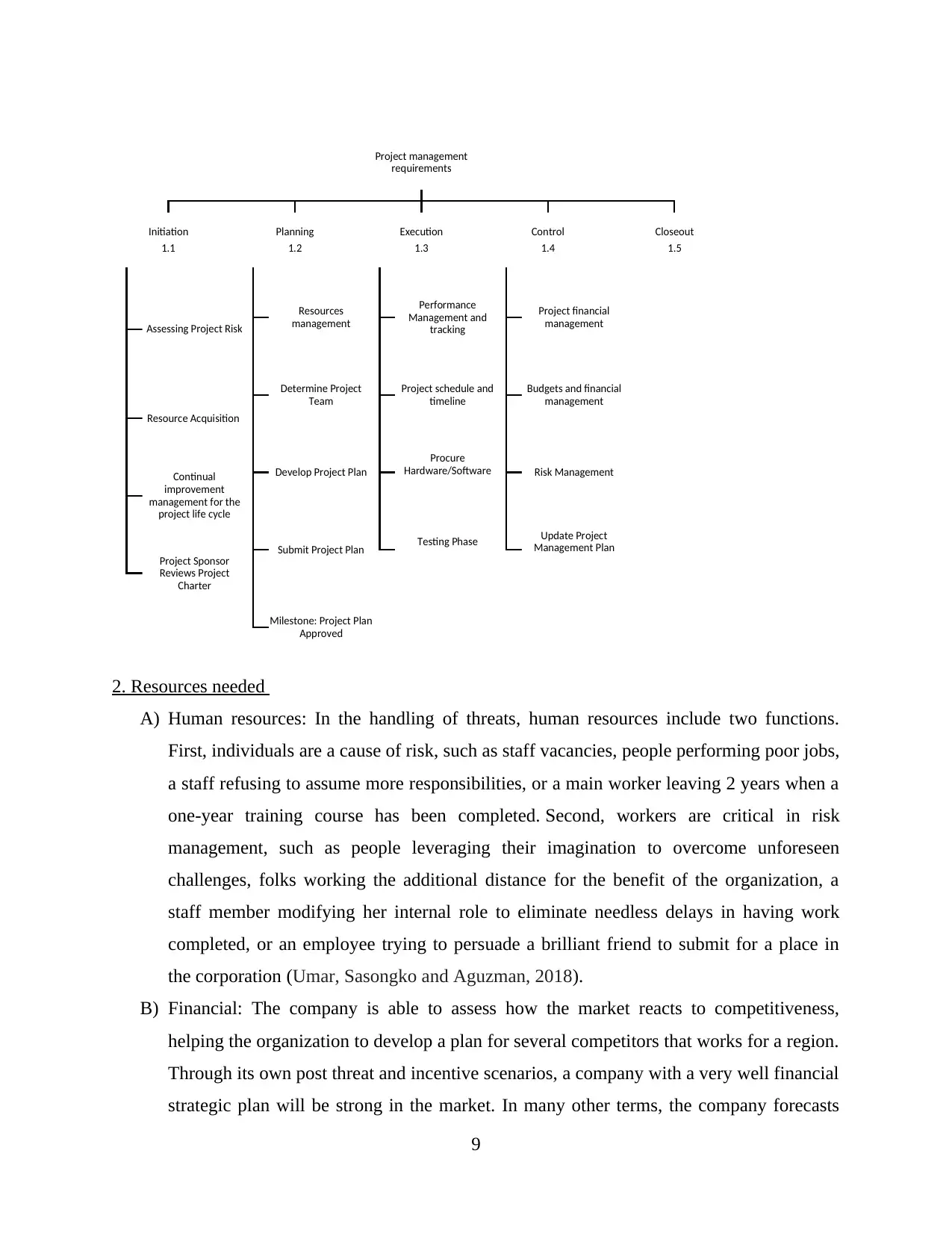
2. Work breakdown structure......................................................................................................8
2. Resources needed.....................................................................................................................9
4. Procedures for staff member..................................................................................................10
5. Monitor, Evaluate and Review..............................................................................................11
REFERENCES..............................................................................................................................12
2
Contents...........................................................................................................................................2
Activity 1.........................................................................................................................................3
1. Analyse risk factors for the financial investment as well as insurance products in that
service:.........................................................................................................................................3
2. Determine appropriate risk exposure management strategies:................................................3
4. Personally manage the risk assessment strategies...................................................................5
5. Exposure factors and evaluate the risk acceptability factors...................................................5
6. Risk acceptance and rejection criteria.....................................................................................6
7. Document a clear outline of the risk acceptance strategy........................................................6
8. Feedback on and finalised the risk acceptance criteria............................................................7
Activity 2.........................................................................................................................................7
1. Implementation plan:...............................................................................................................7
2. Work breakdown structure......................................................................................................8
2. Resources needed.....................................................................................................................9
4. Procedures for staff member..................................................................................................10
5. Monitor, Evaluate and Review..............................................................................................11
REFERENCES..............................................................................................................................12
2

Activity 1
1. Analyse risk factors for the financial investment as well as insurance products in that service:
There are many risk factors to which any business exposed to fiscal investments and insurance
product lines are exposed. Crediting risk, governance risk, developments risk, liquidity risk,
operating risk and tactical risk are included in these threats (Gumusluoglu and Acur, 2016).
Like Westpac Group plc is subject to such numerous kinds of threats where credit
risks of financial corporation 's clients is linked to risks of financial loss arising from financial
liability failure. So there is a risk-based liquidity risk whenever the corporation is incapable to
finance assets and satisfy obligations whereas Governance risk is linked to rules, laws, processes
and regulations determining company's operations administration as well as management. The
collection of guidelines and procedures the company uses to assess level of risk which the
organization is able to consider are key risk acceptability factors within organization. This is pre-
determined risk extent to which the organization is prepared to submit itself.
The emphasis here is towards risk management and adherence. Development risk
is category that covers various risks associated with promotion and communications to
prospective consumers of product lines and services as well as operational risk relates to losses
due to failures of internal procedures. Ultimately, corporations with finance investments and
insurance products such as Westpac are exposed to the strategic risk that covers the possible loss
resulting from an ineffective corporate strategy. And need for the business to concentrate
towards each of such risks while characterizing the risk management strategy at company.
2. Determine appropriate risk exposure management strategies:
Risk exposure management approach will concentrate on focusing on most significant risks
which can assert to be higher risk to the business. Through steering back from purchasing the
risky techniques, there must be riskier inured culture introduced across organization.
Through decentralized decision making framework with centralized ownership of process, risk
management strategy must be implemented across organization. It would ensure safeguard
against undesired risk and better approach towards risk management processes. There
is Australian Standards in Australia: AS/NZS ISO 31000:2009 Risk Management-Principles and
Guidelines. Such criteria map out set of principles, procedures and standards which must be
adopted by organizations when planning and implementing organizational risk managing
3
1. Analyse risk factors for the financial investment as well as insurance products in that service:
There are many risk factors to which any business exposed to fiscal investments and insurance
product lines are exposed. Crediting risk, governance risk, developments risk, liquidity risk,
operating risk and tactical risk are included in these threats (Gumusluoglu and Acur, 2016).
Like Westpac Group plc is subject to such numerous kinds of threats where credit
risks of financial corporation 's clients is linked to risks of financial loss arising from financial
liability failure. So there is a risk-based liquidity risk whenever the corporation is incapable to
finance assets and satisfy obligations whereas Governance risk is linked to rules, laws, processes
and regulations determining company's operations administration as well as management. The
collection of guidelines and procedures the company uses to assess level of risk which the
organization is able to consider are key risk acceptability factors within organization. This is pre-
determined risk extent to which the organization is prepared to submit itself.
The emphasis here is towards risk management and adherence. Development risk
is category that covers various risks associated with promotion and communications to
prospective consumers of product lines and services as well as operational risk relates to losses
due to failures of internal procedures. Ultimately, corporations with finance investments and
insurance products such as Westpac are exposed to the strategic risk that covers the possible loss
resulting from an ineffective corporate strategy. And need for the business to concentrate
towards each of such risks while characterizing the risk management strategy at company.
2. Determine appropriate risk exposure management strategies:
Risk exposure management approach will concentrate on focusing on most significant risks
which can assert to be higher risk to the business. Through steering back from purchasing the
risky techniques, there must be riskier inured culture introduced across organization.
Through decentralized decision making framework with centralized ownership of process, risk
management strategy must be implemented across organization. It would ensure safeguard
against undesired risk and better approach towards risk management processes. There
is Australian Standards in Australia: AS/NZS ISO 31000:2009 Risk Management-Principles and
Guidelines. Such criteria map out set of principles, procedures and standards which must be
adopted by organizations when planning and implementing organizational risk managing
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

strategies. The aim of standards for risk management here is to provide standardized collection
of principles to help organizations better handle their exposures to risk (Hakanen, Helander and
Valkokari, 2017).
In addition, the approach is to guide process through specific duties and responsibilities
where that's the responsibility of any employee throughout organization to recognize every
potential risk and ensuring that the business avoids any greater risk. Going forward, it should be
observed that, together with quantification of net gains a consistent as well as comprehensive
risk evaluation is expected. In order to minimize the risks of losses and avoid the risk linked with
working with complex instruments, such strategy is appropriate. There will be variety of policies,
practices and guidelines for a company, including authorities which are connected within an
organization to the risk management. Entire Risk management is company-wide practice and the
existing policies, practices and authorities which exist within organization must be investigated
such that one can be confident that the latest risk managing strategies which are being
implemented would be in accordance with existing policies or these policies could be altered. 3.
Communicate these strategies to relevant staff and intermediaries:
Communication within context of the risk management strategies would be achieved by
means of clear and efficient communication primarily defined for various parties. To prevent any
misunderstanding and prevent any missed communication, techniques would be communicated
frequently in well-engaged manner herein. The procedure will begin here
with systematically listing of different audiences such as employee personnel and organization
intermediaries.
Communication would be carried out via email messages and newsletters, reinforced by
notice boards and continual social media activities. Additional informal discussions among
managing personnel and staff personnel acting as source will be empowered to prevent any
misunderstanding and have a concept of comprehending strategies of staff personnel working
across organization at different levels.
The communication strategy would be focused on communication priorities; such as aim
for team members to facilitate risk avoidance including early detection of risk to take appropriate
measures. The contact goal for intermediaries, on other hand, is just to create trust
between organization and intermediaries in order to ensure longer-term association. A frequent
review on the efficacy of existing communication plan must also be conducted. It'll be conducted
4
of principles to help organizations better handle their exposures to risk (Hakanen, Helander and
Valkokari, 2017).
In addition, the approach is to guide process through specific duties and responsibilities
where that's the responsibility of any employee throughout organization to recognize every
potential risk and ensuring that the business avoids any greater risk. Going forward, it should be
observed that, together with quantification of net gains a consistent as well as comprehensive
risk evaluation is expected. In order to minimize the risks of losses and avoid the risk linked with
working with complex instruments, such strategy is appropriate. There will be variety of policies,
practices and guidelines for a company, including authorities which are connected within an
organization to the risk management. Entire Risk management is company-wide practice and the
existing policies, practices and authorities which exist within organization must be investigated
such that one can be confident that the latest risk managing strategies which are being
implemented would be in accordance with existing policies or these policies could be altered. 3.
Communicate these strategies to relevant staff and intermediaries:
Communication within context of the risk management strategies would be achieved by
means of clear and efficient communication primarily defined for various parties. To prevent any
misunderstanding and prevent any missed communication, techniques would be communicated
frequently in well-engaged manner herein. The procedure will begin here
with systematically listing of different audiences such as employee personnel and organization
intermediaries.
Communication would be carried out via email messages and newsletters, reinforced by
notice boards and continual social media activities. Additional informal discussions among
managing personnel and staff personnel acting as source will be empowered to prevent any
misunderstanding and have a concept of comprehending strategies of staff personnel working
across organization at different levels.
The communication strategy would be focused on communication priorities; such as aim
for team members to facilitate risk avoidance including early detection of risk to take appropriate
measures. The contact goal for intermediaries, on other hand, is just to create trust
between organization and intermediaries in order to ensure longer-term association. A frequent
review on the efficacy of existing communication plan must also be conducted. It'll be conducted
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

in the open-house meetings by informal contact and group meetings with employees and
frequent formal conversations with CEO. This will help us explain how each person
views message and obtain feedback from him/her to make strategic communication much more
successful in future
Feedback obtained from the employees and intermediaries would be incorporated as final step to
render communication even more efficient and simple for different stakeholders
to understand risk management strategy. It will insure that, in collaboration with group member
including intermediaries, communication strategy is carried out to ensure the consistency of the
goals in place (Julien, 2018).
4. Personally manage the risk assessment strategies
Risk management techniques are handled on the basis of a thorough review of previous
situation, present situation and the potential situation of projects. Here, main emphasis will
remain mostly on development of documents according to the anticipated costs and advantages
contingency planning, scheduling of work breakdowns, as well as priorities and targets. Three
main measures will be included in management plan or risks evaluation strategy: the analysis of
intended performance, the gathering of information as well as assessment of progress. Such a
procedure accompanied by the sharing of findings from analyses and assessments will ensure
effective follow-up measures for the organization-wide introduction of risk management
strategies in an adequate and productive manner. Maintaining responsibility and influence over
the results. It is crucial that their consistent representatives of the enterprise responsible for
maintaining and controlling the results and managing risk acceptability. To insure that this sense
of obligation is passed across the whole organization. This would be important to ensure
that entire organization is functioning appropriately to maintain and manage the structure to
ensure that organization will completely benefit from strategy as expected.
5. Exposure factors and evaluate the risk acceptability factors
All organizations would need to step up with set of specific risk acceptability variables and
requirements as aspect of risk exposure plan which will assess amount of risk that company is
able to accept. This is crucial to take into account that more effective an organization is to
manage risks, the greater the degree of the risk acceptability that organization can sustain. It is
also considered that greater risk exposure rates can contribute to better development and
outcomes for the organization when controlled and sustained well within organization. However,
5
frequent formal conversations with CEO. This will help us explain how each person
views message and obtain feedback from him/her to make strategic communication much more
successful in future
Feedback obtained from the employees and intermediaries would be incorporated as final step to
render communication even more efficient and simple for different stakeholders
to understand risk management strategy. It will insure that, in collaboration with group member
including intermediaries, communication strategy is carried out to ensure the consistency of the
goals in place (Julien, 2018).
4. Personally manage the risk assessment strategies
Risk management techniques are handled on the basis of a thorough review of previous
situation, present situation and the potential situation of projects. Here, main emphasis will
remain mostly on development of documents according to the anticipated costs and advantages
contingency planning, scheduling of work breakdowns, as well as priorities and targets. Three
main measures will be included in management plan or risks evaluation strategy: the analysis of
intended performance, the gathering of information as well as assessment of progress. Such a
procedure accompanied by the sharing of findings from analyses and assessments will ensure
effective follow-up measures for the organization-wide introduction of risk management
strategies in an adequate and productive manner. Maintaining responsibility and influence over
the results. It is crucial that their consistent representatives of the enterprise responsible for
maintaining and controlling the results and managing risk acceptability. To insure that this sense
of obligation is passed across the whole organization. This would be important to ensure
that entire organization is functioning appropriately to maintain and manage the structure to
ensure that organization will completely benefit from strategy as expected.
5. Exposure factors and evaluate the risk acceptability factors
All organizations would need to step up with set of specific risk acceptability variables and
requirements as aspect of risk exposure plan which will assess amount of risk that company is
able to accept. This is crucial to take into account that more effective an organization is to
manage risks, the greater the degree of the risk acceptability that organization can sustain. It is
also considered that greater risk exposure rates can contribute to better development and
outcomes for the organization when controlled and sustained well within organization. However,
5

this is delicate balancing act, like an organization is exposed to more danger than it can manage
efficiently, then the harm can be extensive.
This is also essential that organization's IT systems be used to promote the processes of risk
management. With growing importance of IT framework there's any need to build systems
which are powered by consumers and aid in consistent control and tracking the enforcement with
various laws and policies aligned with industry (Kandachar and Halme, 2017).
After that, company's risk management approach will concentrate on establishing and
sustaining risk management culture by relevant training programs on organizational risk
management, constructive communication as well as discussion of risks management status via
management review conferences and the addition of opportunities and performance guidance.
Accountability must be improved by identifying concrete rewards and performance indicators
relevant to the risk management and integrating particular risk management objectives into
performance evaluation processes.
6. Risk acceptance and rejection criteria
It includes identifying individuals with sufficient expertise, so that knowledge can be gathered
that can enable the program manager recognize the danger and identify a potential solution.
Another strategy is to visualize the latest project and learn of the various reasons that may go
incorrect. When a main team member is ill, what should you do? If the content does not come
inside the given timeline, what will you do? Any help at this point is indeed to attend lectures
from similar ventures in the background, to check the existence of any issues found along the
road, and seeing if they have been overcome.
7. Document a clear outline of the risk acceptance strategy.
Project dangers are unforeseen by default. However that doesn't imply that they really are
unknown all the time. Recognizing how much you are expected to know heading in would be
just way of managing risk control. Risks come below three layers of knowledge:
An established danger is one that a stockholder, colleague, or oneself has already posed. Perhaps
it came about but was expressed by an advisor at the planning stage period. It is important to
closely examine these and log them.
An unknown danger is something that has not come about automatically and may only be
understood or accepted by a few persons, including an experienced practitioner. When preparing
6
efficiently, then the harm can be extensive.
This is also essential that organization's IT systems be used to promote the processes of risk
management. With growing importance of IT framework there's any need to build systems
which are powered by consumers and aid in consistent control and tracking the enforcement with
various laws and policies aligned with industry (Kandachar and Halme, 2017).
After that, company's risk management approach will concentrate on establishing and
sustaining risk management culture by relevant training programs on organizational risk
management, constructive communication as well as discussion of risks management status via
management review conferences and the addition of opportunities and performance guidance.
Accountability must be improved by identifying concrete rewards and performance indicators
relevant to the risk management and integrating particular risk management objectives into
performance evaluation processes.
6. Risk acceptance and rejection criteria
It includes identifying individuals with sufficient expertise, so that knowledge can be gathered
that can enable the program manager recognize the danger and identify a potential solution.
Another strategy is to visualize the latest project and learn of the various reasons that may go
incorrect. When a main team member is ill, what should you do? If the content does not come
inside the given timeline, what will you do? Any help at this point is indeed to attend lectures
from similar ventures in the background, to check the existence of any issues found along the
road, and seeing if they have been overcome.
7. Document a clear outline of the risk acceptance strategy.
Project dangers are unforeseen by default. However that doesn't imply that they really are
unknown all the time. Recognizing how much you are expected to know heading in would be
just way of managing risk control. Risks come below three layers of knowledge:
An established danger is one that a stockholder, colleague, or oneself has already posed. Perhaps
it came about but was expressed by an advisor at the planning stage period. It is important to
closely examine these and log them.
An unknown danger is something that has not come about automatically and may only be
understood or accepted by a few persons, including an experienced practitioner. When preparing
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

the task risk management strategy, they have to invest a reasonable period of time wanting to
locate these (Kasseeah, 2016).
An unfathomable risk, like complete device breakdown, a market collapse, or an incident, is one
which they can't realistically hope to predict. Although there is no sense in the strategy pointing
all of these separately, it is necessary to recognize that manager will not predict every danger.
8. Feedback on and finalised the risk acceptance criteria.
They really had to devote a decent amount of time hoping to find these while planning the
mission risk management plan. One that they could not expect to foresee is an unimaginable risk,
such as a total device malfunction, a market crash, or an incident (Phillips, Ray and Phillips,
2016). While there is no meaning to pointing all of these independently in the plan, it is
important to consider that manager can not foresee all hazards. That doesn't mean, though, that
they're not down.
Activity 2
1. Implementation plan:
A). Senior administrators ought to think about ways to effectively handle threat around the
organisation. It was about associating corporate governance with overarching company priorities
and trying to install a performance development philosophy. Without this, corporations suffer
from lack of joint-up thinking and a problem-solving and fighting fires attitude. Things cost
money for organizations, but strategies for avoidance and comprehensive risk control do not. The
Risk Assessment strategy will help companies handle risks more efficiently quickly by
incorporating the AXELOS collection of recommendations. The corporate priorities list also
increases risk and sees it not just as a danger, but as an incentive. Risk analyses for a large
programme, like risk workshops involving key partners, can be carried out on a regular basis.
B). Monitoring methods
Check to confirm the company prior risk evaluations based on the probability and effect of
vulnerability by evaluating the hazards that the manager has recently defined and taken any
action against. Alterations to one’s danger may cause changes to one of these or both. Also it is
important to change the priority of that same risk appropriately. Validating basic theories and
stating any original product is also a great idea, because this will assist people supervise one’s
threat alongside a red moment (Srhoj, Škrinjarić and Radas, 2019).
7
locate these (Kasseeah, 2016).
An unfathomable risk, like complete device breakdown, a market collapse, or an incident, is one
which they can't realistically hope to predict. Although there is no sense in the strategy pointing
all of these separately, it is necessary to recognize that manager will not predict every danger.
8. Feedback on and finalised the risk acceptance criteria.
They really had to devote a decent amount of time hoping to find these while planning the
mission risk management plan. One that they could not expect to foresee is an unimaginable risk,
such as a total device malfunction, a market crash, or an incident (Phillips, Ray and Phillips,
2016). While there is no meaning to pointing all of these independently in the plan, it is
important to consider that manager can not foresee all hazards. That doesn't mean, though, that
they're not down.
Activity 2
1. Implementation plan:
A). Senior administrators ought to think about ways to effectively handle threat around the
organisation. It was about associating corporate governance with overarching company priorities
and trying to install a performance development philosophy. Without this, corporations suffer
from lack of joint-up thinking and a problem-solving and fighting fires attitude. Things cost
money for organizations, but strategies for avoidance and comprehensive risk control do not. The
Risk Assessment strategy will help companies handle risks more efficiently quickly by
incorporating the AXELOS collection of recommendations. The corporate priorities list also
increases risk and sees it not just as a danger, but as an incentive. Risk analyses for a large
programme, like risk workshops involving key partners, can be carried out on a regular basis.
B). Monitoring methods
Check to confirm the company prior risk evaluations based on the probability and effect of
vulnerability by evaluating the hazards that the manager has recently defined and taken any
action against. Alterations to one’s danger may cause changes to one of these or both. Also it is
important to change the priority of that same risk appropriately. Validating basic theories and
stating any original product is also a great idea, because this will assist people supervise one’s
threat alongside a red moment (Srhoj, Škrinjarić and Radas, 2019).
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

C). Evaluation Methods:
Confirm if a risk assessment policy's possible results have been in conjunction including
its pre-defined goals. In evaluating unless the strategy in activity is great, it plays an important
role. It does not have to be altered if it achieves the best results. Although it can be a truly serious
problem if it fails to find what is needed. A company, after all, implements its tools, like time,
resources and social resources, and most of all, that organization's key objective is often
overcome. Each operation in a project management plan needs a comprehensive investigation.
They will thoroughly evaluate the entire strategy by testing the success of all of the other
initiatives and finding the shortcomings in their execution.
2. Work breakdown structure
The primary goal of a WBS would be to simplify complex processes to a series of tasks. For the
systems engineer, this really is critical so she can supervise the job more quickly than
complicated operations (Strielkowski and Chigisheva, 2018). The functions, with precisely
defined constraints, must be observable and autonomous. Both the project activity should be
included in several of the activities and no non-project research should be included with the
assignments. For tracking performance throughout the project timeline, the WBS is crucial.
Since the WBS assignments have clearly stated limitations, by testing whether any of the tasks
are done, project managers can assess how progressed the task becomes easy to make results.
8
Confirm if a risk assessment policy's possible results have been in conjunction including
its pre-defined goals. In evaluating unless the strategy in activity is great, it plays an important
role. It does not have to be altered if it achieves the best results. Although it can be a truly serious
problem if it fails to find what is needed. A company, after all, implements its tools, like time,
resources and social resources, and most of all, that organization's key objective is often
overcome. Each operation in a project management plan needs a comprehensive investigation.
They will thoroughly evaluate the entire strategy by testing the success of all of the other
initiatives and finding the shortcomings in their execution.
2. Work breakdown structure
The primary goal of a WBS would be to simplify complex processes to a series of tasks. For the
systems engineer, this really is critical so she can supervise the job more quickly than
complicated operations (Strielkowski and Chigisheva, 2018). The functions, with precisely
defined constraints, must be observable and autonomous. Both the project activity should be
included in several of the activities and no non-project research should be included with the
assignments. For tracking performance throughout the project timeline, the WBS is crucial.
Since the WBS assignments have clearly stated limitations, by testing whether any of the tasks
are done, project managers can assess how progressed the task becomes easy to make results.
8
2. Resources needed
A) Human resources: In the handling of threats, human resources include two functions.
First, individuals are a cause of risk, such as staff vacancies, people performing poor jobs,
a staff refusing to assume more responsibilities, or a main worker leaving 2 years when a
one-year training course has been completed. Second, workers are critical in risk
management, such as people leveraging their imagination to overcome unforeseen
challenges, folks working the additional distance for the benefit of the organization, a
staff member modifying her internal role to eliminate needless delays in having work
completed, or an employee trying to persuade a brilliant friend to submit for a place in
the corporation (Umar, Sasongko and Aguzman, 2018).
B) Financial: The company is able to assess how the market reacts to competitiveness,
helping the organization to develop a plan for several competitors that works for a region.
Through its own post threat and incentive scenarios, a company with a very well financial
strategic plan will be strong in the market. In many other terms, the company forecasts
9
Project management
requirements
Initiation
1.1
Assessing Project Risk
Resource Acquisition
Continual
improvement
management for the
project life cycle
Project Sponsor
Reviews Project
Charter
Planning
1.2
Resources
management
Determine Project
Team
Develop Project Plan
Submit Project Plan
Milestone: Project Plan
Approved
Execution
1.3
Performance
Management and
tracking
Project schedule and
timeline
Procure
Hardware/Software
Testing Phase
Control
1.4
Project financial
management
Budgets and financial
management
Risk Management
Update Project
Management Plan
Closeout
1.5
A) Human resources: In the handling of threats, human resources include two functions.
First, individuals are a cause of risk, such as staff vacancies, people performing poor jobs,
a staff refusing to assume more responsibilities, or a main worker leaving 2 years when a
one-year training course has been completed. Second, workers are critical in risk
management, such as people leveraging their imagination to overcome unforeseen
challenges, folks working the additional distance for the benefit of the organization, a
staff member modifying her internal role to eliminate needless delays in having work
completed, or an employee trying to persuade a brilliant friend to submit for a place in
the corporation (Umar, Sasongko and Aguzman, 2018).
B) Financial: The company is able to assess how the market reacts to competitiveness,
helping the organization to develop a plan for several competitors that works for a region.
Through its own post threat and incentive scenarios, a company with a very well financial
strategic plan will be strong in the market. In many other terms, the company forecasts
9
Project management
requirements
Initiation
1.1
Assessing Project Risk
Resource Acquisition
Continual
improvement
management for the
project life cycle
Project Sponsor
Reviews Project
Charter
Planning
1.2
Resources
management
Determine Project
Team
Develop Project Plan
Submit Project Plan
Milestone: Project Plan
Approved
Execution
1.3
Performance
Management and
tracking
Project schedule and
timeline
Procure
Hardware/Software
Testing Phase
Control
1.4
Project financial
management
Budgets and financial
management
Risk Management
Update Project
Management Plan
Closeout
1.5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

whatever is most probable to result in the stock market which, considering those
uncertainties, establishes a plan to expand the company.
C) Technology: Manager should start designing plans to monitor the effects of threats and
evaluate them. These are achieved by knowing what the risk will have on the venture,
which defines the chance and the extent of its effect of it happening. Then, by trying to
blame the entire project, they might conclude that the threat should be resolved or can be
overlooked. Again, the risk analysis will be applied to these ratings.
D) Physical: Both visible physical properties, like vehicles, materials, structures and
corporate headquarters, are included that support company to reach the desired results in
specific time.
E) Reputation: This involves the organization's views which can be calculated by budgets
for coverage and public affairs that will need to be managed in system to continue this
ongoing.
4. Procedures for staff member
A) Financial plan: It is guided to all staff that allotted financial resources are needed to be
used in a significant manner which will help to meet the requirement of risk management
strategy. The cost is needed to be controlled in significant manner so that no point can
create problem from the company.
B) Promotional strategy: In order to make better and extended promotion of company
policies within the staff member, senior manager prepared an internal email system
which will notify entire staff at any point of risk (Vithessonthi and Tongurai, 2016).
C) Resources requirement: Teams at each level, Managers, review staff for operations,
buildings, equipment’s.
D) Timelines: Each and every task are assigned to member as per their capacity and the
working performance so that work can be completed on deadlines.
E) Communication strategy: Throughout severe global health incidents, risk coordination
plays a vital role in maintaining health, ensuring integrity and saving people's lives.
Rumours or misleading news have tremendous capacity to cause fear and mistrust in
affected populations as emergency hits, and thereby to hinder public health activities.
Risk in crises, contact is thus the bridge among healthcare actors as well as the
10
uncertainties, establishes a plan to expand the company.
C) Technology: Manager should start designing plans to monitor the effects of threats and
evaluate them. These are achieved by knowing what the risk will have on the venture,
which defines the chance and the extent of its effect of it happening. Then, by trying to
blame the entire project, they might conclude that the threat should be resolved or can be
overlooked. Again, the risk analysis will be applied to these ratings.
D) Physical: Both visible physical properties, like vehicles, materials, structures and
corporate headquarters, are included that support company to reach the desired results in
specific time.
E) Reputation: This involves the organization's views which can be calculated by budgets
for coverage and public affairs that will need to be managed in system to continue this
ongoing.
4. Procedures for staff member
A) Financial plan: It is guided to all staff that allotted financial resources are needed to be
used in a significant manner which will help to meet the requirement of risk management
strategy. The cost is needed to be controlled in significant manner so that no point can
create problem from the company.
B) Promotional strategy: In order to make better and extended promotion of company
policies within the staff member, senior manager prepared an internal email system
which will notify entire staff at any point of risk (Vithessonthi and Tongurai, 2016).
C) Resources requirement: Teams at each level, Managers, review staff for operations,
buildings, equipment’s.
D) Timelines: Each and every task are assigned to member as per their capacity and the
working performance so that work can be completed on deadlines.
E) Communication strategy: Throughout severe global health incidents, risk coordination
plays a vital role in maintaining health, ensuring integrity and saving people's lives.
Rumours or misleading news have tremendous capacity to cause fear and mistrust in
affected populations as emergency hits, and thereby to hinder public health activities.
Risk in crises, contact is thus the bridge among healthcare actors as well as the
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

community and is one of the key capacities defined in the Framework Convention on risk
management (Zhang and Wen, 2017).
5. Monitor, Evaluate and Review
In regularly to secure that knowledge is used to guide decision-making, arrange accordingly
and submit to shareholders and judgment, reporting, monitoring and evaluation development is
important. There is a possibility that surveillance practices and services might be seen as a drain
on the economy and abandoned and without direct correlation between tracking and judgment.
Evaluation lets them benefit about what they expected or what was completed. In order to
achieve adaptation effects, it aims people clarify what improvements ought to be introduced to
company preparation strategy, the schedule and related tasks. Access provided could be
established and recorded and therefore can trigger the next step in a series when hit. They ought
to calculate the amount needed for the judgment to be taken and adopted when defining trigger
stages. This must include the time taken for stakeholder participation to be successful, plus every
research and the development, product development of measures. In particular, the cause
thresholds for climatic changes must be stable (e.g. they should not be based on a single extreme
event). The causes or because factors must be tangible, visible and understandable to all
participants to the fullest degree practicable (Wonglimpiyarat, 2016). This will serve to have the
collective license for acts to be enforced. In order to make sure that the gathered evidence and
data could be evaluated accurately until decisions are being made, it is essential to analyse the
comprehensiveness of the metrics. This also involves deciding how information from monitoring
should be viewed. It is important to provide reference data against which variable can be
measured in order to track any variable. For example, you could gather preliminary information
or pick reference locations (controls) to test improvements against them. When designing your
surveillance strategy, request expert input; inadequate monitoring will result in poor decisions
being taken. The extreme weather events mean that the reference starting points will not stay the
same and adjust overtime (shifting baselines), making it difficult to compare.
11
management (Zhang and Wen, 2017).
5. Monitor, Evaluate and Review
In regularly to secure that knowledge is used to guide decision-making, arrange accordingly
and submit to shareholders and judgment, reporting, monitoring and evaluation development is
important. There is a possibility that surveillance practices and services might be seen as a drain
on the economy and abandoned and without direct correlation between tracking and judgment.
Evaluation lets them benefit about what they expected or what was completed. In order to
achieve adaptation effects, it aims people clarify what improvements ought to be introduced to
company preparation strategy, the schedule and related tasks. Access provided could be
established and recorded and therefore can trigger the next step in a series when hit. They ought
to calculate the amount needed for the judgment to be taken and adopted when defining trigger
stages. This must include the time taken for stakeholder participation to be successful, plus every
research and the development, product development of measures. In particular, the cause
thresholds for climatic changes must be stable (e.g. they should not be based on a single extreme
event). The causes or because factors must be tangible, visible and understandable to all
participants to the fullest degree practicable (Wonglimpiyarat, 2016). This will serve to have the
collective license for acts to be enforced. In order to make sure that the gathered evidence and
data could be evaluated accurately until decisions are being made, it is essential to analyse the
comprehensiveness of the metrics. This also involves deciding how information from monitoring
should be viewed. It is important to provide reference data against which variable can be
measured in order to track any variable. For example, you could gather preliminary information
or pick reference locations (controls) to test improvements against them. When designing your
surveillance strategy, request expert input; inadequate monitoring will result in poor decisions
being taken. The extreme weather events mean that the reference starting points will not stay the
same and adjust overtime (shifting baselines), making it difficult to compare.
11

REFERENCES
Books and Journals
Gumusluoglu, L. and Acur, N., 2016. Fit among business strategy, strategy formality, and
dynamic capability development in new product development. European
Management Review. 13(2). pp. 107-123.
Hakanen, T., Helander, N. and Valkokari, K., 2017. Servitization in global business-to-business
distribution: The central activities of manufacturers. Industrial Marketing
Management. 63. pp. 167-178.
Julien, P. A. ed., 2018. The state of the art in small business and entrepreneurship. Routledge.
Kandachar, P. and Halme, M. eds., 2017. Sustainability challenges and solutions at the base of
the pyramid: Business, technology and the poor. Routledge.
Kasseeah, H., 2016. Investigating the impact of entrepreneurship on economic development: a
regional analysis. Journal of Small Business and Enterprise Development.
Phillips, P., Ray, R. and Phillips, J. J., 2016. How to capture the business value of leadership
development. People and Strategy. 39(2). p. 46.
Srhoj, S., Škrinjarić, B. and Radas, S., 2019. Bidding against the odds? The impact evaluation of
grants for young micro and small firms during the recession. Small Business
Economics, pp. 1-21.
Strielkowski, W. and Chigisheva, O., 2018. Social, economic, and academic leadership for
sustainable development of business and education in the future: an introduction.
In Leadership for the Future Sustainable Development of Business and
Education (pp. 3-8). Springer, Cham.
Umar, A., Sasongko, A. H. and Aguzman, G., 2018. Business model canvas as a solution for
competing strategy of small business in Indonesia. International Journal of
Entrepreneurship. 22(1). pp. 1-9.
Vithessonthi, C. and Tongurai, J., 2016. Financial markets development, business cycles, and
bank risk in South America. Research in International Business and Finance, 36, pp.
472-484.
Wonglimpiyarat, J., 2016. The innovation incubator, university business incubator and
technology transfer strategy: The case of Thailand. Technology in Society. 46. pp. 18-
27.
Zhang, Y. and Wen, J., 2017. The IoT electric business model: Using blockchain technology for
the internet of things. Peer-to-Peer Networking and Applications. 10(4). pp. 983-994.
12
Books and Journals
Gumusluoglu, L. and Acur, N., 2016. Fit among business strategy, strategy formality, and
dynamic capability development in new product development. European
Management Review. 13(2). pp. 107-123.
Hakanen, T., Helander, N. and Valkokari, K., 2017. Servitization in global business-to-business
distribution: The central activities of manufacturers. Industrial Marketing
Management. 63. pp. 167-178.
Julien, P. A. ed., 2018. The state of the art in small business and entrepreneurship. Routledge.
Kandachar, P. and Halme, M. eds., 2017. Sustainability challenges and solutions at the base of
the pyramid: Business, technology and the poor. Routledge.
Kasseeah, H., 2016. Investigating the impact of entrepreneurship on economic development: a
regional analysis. Journal of Small Business and Enterprise Development.
Phillips, P., Ray, R. and Phillips, J. J., 2016. How to capture the business value of leadership
development. People and Strategy. 39(2). p. 46.
Srhoj, S., Škrinjarić, B. and Radas, S., 2019. Bidding against the odds? The impact evaluation of
grants for young micro and small firms during the recession. Small Business
Economics, pp. 1-21.
Strielkowski, W. and Chigisheva, O., 2018. Social, economic, and academic leadership for
sustainable development of business and education in the future: an introduction.
In Leadership for the Future Sustainable Development of Business and
Education (pp. 3-8). Springer, Cham.
Umar, A., Sasongko, A. H. and Aguzman, G., 2018. Business model canvas as a solution for
competing strategy of small business in Indonesia. International Journal of
Entrepreneurship. 22(1). pp. 1-9.
Vithessonthi, C. and Tongurai, J., 2016. Financial markets development, business cycles, and
bank risk in South America. Research in International Business and Finance, 36, pp.
472-484.
Wonglimpiyarat, J., 2016. The innovation incubator, university business incubator and
technology transfer strategy: The case of Thailand. Technology in Society. 46. pp. 18-
27.
Zhang, Y. and Wen, J., 2017. The IoT electric business model: Using blockchain technology for
the internet of things. Peer-to-Peer Networking and Applications. 10(4). pp. 983-994.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





