IS Security and Risk Management Report for Telstra Organization
VerifiedAdded on 2021/06/17
|16
|3847
|48
Report
AI Summary
This report provides a comprehensive analysis of information system (IS) security and risk management practices within Telstra Corporation Ltd., a major telecommunications company in Australia. The report begins with an introduction to IS and its importance, followed by a detailed discussion of the most common malware affecting organizational operations, including adware, bots, bugs, and ransomware. It then identifies and describes three types of network devices used by Telstra: routers, Ethernet hubs, and modems, highlighting their vulnerabilities. The report assesses the reliability and availability of Telstra's web services, along with measures to ensure the confidentiality and integrity of staff emails using Microsoft Exchange Server. Furthermore, it prioritizes various threats, malware types, and security issues affecting web servers and webmail, such as computer viruses, phishing, email spoofing, and spamming. Two approaches for improving the availability of web and email servers, including the implementation of a Sender Policy Framework (SPF) and securing applications, are also presented. The report also explores the impact of organizational issues and human factors on IS management. Finally, it includes an illustration of log records, the utilization of audit log records for email and web server issues, and a discussion of five types of network security devices for controlling security, concluding with recommendations for improving Telstra's IS security posture.

Running head: IS SECURITY AND RISK MANAGEMENT
IS Security and Risk Management: Telstra Organization
Name of the Student
Name of the University
Author’s Note:
IS Security and Risk Management: Telstra Organization
Name of the Student
Name of the University
Author’s Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IS SECURITY AND RISK MANAGEMENT
Table of Contents
Introduction................................................................................................................................2
Discussion..................................................................................................................................3
1. Most Common Malware Affecting Organizational Operations.........................................3
2. Three Types of Network Devices Used by Telstra............................................................4
3. Reliability and Availability of Web Service......................................................................5
4. Ensuring Confidentiality and Integrity for Staff Email......................................................6
5. Prioritization of Threats, Malware Types and Security Issues..........................................7
6. Two Approaches for Improving Availability of Web and Email Servers.........................8
7. Impact of Organizational Issues and Human Factors on IS Management.........................9
8. Illustration of Log Records..............................................................................................10
9. Utilization of Audit Log Records for Email and Web Server Issues...............................10
10. Five types of Network Security Devices for Controlling Security................................10
Conclusions and Recommendations........................................................................................11
References................................................................................................................................13
IS SECURITY AND RISK MANAGEMENT
Table of Contents
Introduction................................................................................................................................2
Discussion..................................................................................................................................3
1. Most Common Malware Affecting Organizational Operations.........................................3
2. Three Types of Network Devices Used by Telstra............................................................4
3. Reliability and Availability of Web Service......................................................................5
4. Ensuring Confidentiality and Integrity for Staff Email......................................................6
5. Prioritization of Threats, Malware Types and Security Issues..........................................7
6. Two Approaches for Improving Availability of Web and Email Servers.........................8
7. Impact of Organizational Issues and Human Factors on IS Management.........................9
8. Illustration of Log Records..............................................................................................10
9. Utilization of Audit Log Records for Email and Web Server Issues...............................10
10. Five types of Network Security Devices for Controlling Security................................10
Conclusions and Recommendations........................................................................................11
References................................................................................................................................13

2
IS SECURITY AND RISK MANAGEMENT
Introduction
An information system or simply IS can be defined as the significant organized
system, which is being used to properly collect, organize, store, interpret, manipulate and
finally communicate the confidential information or data (Cheminod, Durante & Valenzano,
2013). This can be termed as the specific collection of several complementary networks that
an individual or an organization uses for filtering, creation, processing, collection and evenly
distributing information or data. Information system is considered as one of the most
important and vital requirements that help any organization to produce information perfectly
and accurately. All the internal information are majorly targeted with the IS or information
system and the external information is discarded. This particular software is being utilized to
properly run the completely computerized and systematic database or a specific computer
system (Hashizume et al., 2013). Each and every operation of data is extremely easy with this
information system or IS. The entire management, process of decision making and the
various business operations are being supported by this information system and hence it is
termed as the proper subset of ICT or information and communications technology.
This report will be outlining a detailed description on the significant concept of IS or
information system for the most popular organization of telecommunications in Australia,
namely, Telstra Corporation Ltd. This particular company helps its clients or customers in
operating and building the various networks of telecommunication, entertainment services,
entertainment products, access of the Internet, access of the mobile phones and many others.
The organization of Telstra Corporation Ltd is the largest company of telecommunications
within Australia. This organization is responsible for providing services of information
system for the customers and employees. The following report would be depicting about the
several threats or malware, which are dangerous for the organization.
IS SECURITY AND RISK MANAGEMENT
Introduction
An information system or simply IS can be defined as the significant organized
system, which is being used to properly collect, organize, store, interpret, manipulate and
finally communicate the confidential information or data (Cheminod, Durante & Valenzano,
2013). This can be termed as the specific collection of several complementary networks that
an individual or an organization uses for filtering, creation, processing, collection and evenly
distributing information or data. Information system is considered as one of the most
important and vital requirements that help any organization to produce information perfectly
and accurately. All the internal information are majorly targeted with the IS or information
system and the external information is discarded. This particular software is being utilized to
properly run the completely computerized and systematic database or a specific computer
system (Hashizume et al., 2013). Each and every operation of data is extremely easy with this
information system or IS. The entire management, process of decision making and the
various business operations are being supported by this information system and hence it is
termed as the proper subset of ICT or information and communications technology.
This report will be outlining a detailed description on the significant concept of IS or
information system for the most popular organization of telecommunications in Australia,
namely, Telstra Corporation Ltd. This particular company helps its clients or customers in
operating and building the various networks of telecommunication, entertainment services,
entertainment products, access of the Internet, access of the mobile phones and many others.
The organization of Telstra Corporation Ltd is the largest company of telecommunications
within Australia. This organization is responsible for providing services of information
system for the customers and employees. The following report would be depicting about the
several threats or malware, which are dangerous for the organization.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
IS SECURITY AND RISK MANAGEMENT
Discussion
1. Most Common Malware Affecting Organizational Operations
The malicious software of malware is the specific variety of various hostile forms or
intrusive software. There are various types of this intrusive software. They are Trojan horses,
ransom ware, spyware, computer viruses and several others. Malware can be defined as the
most threatening or dangerous software, which could cause problems or issues for any
business operation (Peltier, 2013). Any kind of malicious activities can take the form of the
executable scripts or code. This malware consists of the malicious intent, which could be
subsequently acting against the various kinds of requirements for any computer utilizations.
Malware is extremely vulnerable for any organization or business and hence Telstra
Corporation Ltd. has also faced this situation. The most dangerous malware threat, which can
be vulnerable to the IS or information system and also for the business operations of Telstra
Corporation Ltd. are given below:
i) Adware: This is the most dangerous kind of malware, which could be extremely
dangerous for any organizational operation of Telstra Corporation Ltd. Adware is the
abbreviation of advertising supported software. This particular software is solely responsible
to automatically providing advertisements (Willcocks, 2013). Various important examples of
the adware malware are pop up advertisements, which come up on websites, displayed by this
software. The business operations or processes are dangerously affected with this particular
malware.
ii) Bots: This is the second significant malware program dangerous for Telstra
Corporation Ltd. Bots are certain software programs, which are made to perform the various
operations (Crossler et al., 2014). Although, few bots are created for harmless purposes like
IS SECURITY AND RISK MANAGEMENT
Discussion
1. Most Common Malware Affecting Organizational Operations
The malicious software of malware is the specific variety of various hostile forms or
intrusive software. There are various types of this intrusive software. They are Trojan horses,
ransom ware, spyware, computer viruses and several others. Malware can be defined as the
most threatening or dangerous software, which could cause problems or issues for any
business operation (Peltier, 2013). Any kind of malicious activities can take the form of the
executable scripts or code. This malware consists of the malicious intent, which could be
subsequently acting against the various kinds of requirements for any computer utilizations.
Malware is extremely vulnerable for any organization or business and hence Telstra
Corporation Ltd. has also faced this situation. The most dangerous malware threat, which can
be vulnerable to the IS or information system and also for the business operations of Telstra
Corporation Ltd. are given below:
i) Adware: This is the most dangerous kind of malware, which could be extremely
dangerous for any organizational operation of Telstra Corporation Ltd. Adware is the
abbreviation of advertising supported software. This particular software is solely responsible
to automatically providing advertisements (Willcocks, 2013). Various important examples of
the adware malware are pop up advertisements, which come up on websites, displayed by this
software. The business operations or processes are dangerously affected with this particular
malware.
ii) Bots: This is the second significant malware program dangerous for Telstra
Corporation Ltd. Bots are certain software programs, which are made to perform the various
operations (Crossler et al., 2014). Although, few bots are created for harmless purposes like
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
IS SECURITY AND RISK MANAGEMENT
internet auctions or video gaming, most of them are created for introducing vulnerabilities
within the systems. the main usability of this bot is for denial of service attacks as botnets.
iii) Bugs: The bugs are the certain flaws, which is solely responsible to produce any
undesired outcome. There are various flaws like human errors and these exist in the compiler
and source code (Li, Hsieh & Rai, 2013). All the business operations are extremely affected
with this particular malware. The most significant amongst all the kinds of bugs, security
bugs are considered as the most vulnerable. It allows the hackers in stopping the user
authentication.
iv) Ransom ware: The fourth type of malware is ransom ware. It is the basic form of
malware that holds any particular system captive to demand any ransom. The user access is
blocked in this way and it is done by encrypting the files.
2. Three Types of Network Devices Used by Telstra
Telstra Corporation Ltd. is responsible for providing services of information system to
their employees and users. Hence, there is always a high chance that these services could be
exploited by several attacks (Gallagher & Sixsmith, 2014). Furthermore, this organization is
using three specific kinds of network security devices in the businesses. The three important
network security devices used by Telstra Corporation Ltd. are given below:
i) Routers: This is the first network security device that the organization is using.
Routers are certain devices, helping to forward various data packets within the computer
networks. All these routers are solely responsible to perform the functions of traffic on the
Internet connection (Ifinedo, 2014). The data packets are forwarded from one router to
another router. These routers are linked with various data lines from the several networks.
IS SECURITY AND RISK MANAGEMENT
internet auctions or video gaming, most of them are created for introducing vulnerabilities
within the systems. the main usability of this bot is for denial of service attacks as botnets.
iii) Bugs: The bugs are the certain flaws, which is solely responsible to produce any
undesired outcome. There are various flaws like human errors and these exist in the compiler
and source code (Li, Hsieh & Rai, 2013). All the business operations are extremely affected
with this particular malware. The most significant amongst all the kinds of bugs, security
bugs are considered as the most vulnerable. It allows the hackers in stopping the user
authentication.
iv) Ransom ware: The fourth type of malware is ransom ware. It is the basic form of
malware that holds any particular system captive to demand any ransom. The user access is
blocked in this way and it is done by encrypting the files.
2. Three Types of Network Devices Used by Telstra
Telstra Corporation Ltd. is responsible for providing services of information system to
their employees and users. Hence, there is always a high chance that these services could be
exploited by several attacks (Gallagher & Sixsmith, 2014). Furthermore, this organization is
using three specific kinds of network security devices in the businesses. The three important
network security devices used by Telstra Corporation Ltd. are given below:
i) Routers: This is the first network security device that the organization is using.
Routers are certain devices, helping to forward various data packets within the computer
networks. All these routers are solely responsible to perform the functions of traffic on the
Internet connection (Ifinedo, 2014). The data packets are forwarded from one router to
another router. These routers are linked with various data lines from the several networks.

5
IS SECURITY AND RISK MANAGEMENT
Routers are extremely important for the organization of Telstra Corporation Ltd. and thus
they help to perform any operation of networking.
ii) Ethernet Hubs: The next network security device of Telstra Corporation Ltd. is
Ethernet hub. This is the specific network hardware device that helps in connection of various
Ethernet devices to make each of them acting altogether as one single segment of network.
iii) Modems: The third network security device of Telstra Corporation Ltd. is modem
(Power, Sharda & Burstein, 2015). Modems are responsible for modulating every single
signal of carrier wave to properly encode the digital information and transmitting or
demodulating the signal. This helps to decode the previous data or information.
All the above mentioned network security devices are extremely vulnerable for any
type of threat, abuse, destruction, issues or errors of system quality (Lee, 2014). The most
significant reason of these vulnerabilities mainly includes the absence of firewalls and
antivirus in the devices. Moreover, proper measures for security are also not taken and hence
the network security devices are extremely vulnerable to the above mentioned issues.
3. Reliability and Availability of Web Service
The organization of Telstra Corporation Ltd. is using the Windows Server 2012 to
properly host their particular web site. There are various important requirements for any web
server and amongst them, reliability as well as availability are the most important ones.
Reliability solely refers to the specific capability to the computer aided hardware and
computer aided software (Rong, Nguyen & Jaatun, 2013). This helps to perform consistently
according to the requirements. Reliability of Windows Server 2012 significantly is dependent
on the web site performance. There are few factors that determine the reliability of the web
server. They are given below:
IS SECURITY AND RISK MANAGEMENT
Routers are extremely important for the organization of Telstra Corporation Ltd. and thus
they help to perform any operation of networking.
ii) Ethernet Hubs: The next network security device of Telstra Corporation Ltd. is
Ethernet hub. This is the specific network hardware device that helps in connection of various
Ethernet devices to make each of them acting altogether as one single segment of network.
iii) Modems: The third network security device of Telstra Corporation Ltd. is modem
(Power, Sharda & Burstein, 2015). Modems are responsible for modulating every single
signal of carrier wave to properly encode the digital information and transmitting or
demodulating the signal. This helps to decode the previous data or information.
All the above mentioned network security devices are extremely vulnerable for any
type of threat, abuse, destruction, issues or errors of system quality (Lee, 2014). The most
significant reason of these vulnerabilities mainly includes the absence of firewalls and
antivirus in the devices. Moreover, proper measures for security are also not taken and hence
the network security devices are extremely vulnerable to the above mentioned issues.
3. Reliability and Availability of Web Service
The organization of Telstra Corporation Ltd. is using the Windows Server 2012 to
properly host their particular web site. There are various important requirements for any web
server and amongst them, reliability as well as availability are the most important ones.
Reliability solely refers to the specific capability to the computer aided hardware and
computer aided software (Rong, Nguyen & Jaatun, 2013). This helps to perform consistently
according to the requirements. Reliability of Windows Server 2012 significantly is dependent
on the web site performance. There are few factors that determine the reliability of the web
server. They are given below:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
IS SECURITY AND RISK MANAGEMENT
i) The constant connection of Internet is the most important factor to determine
reliability.
ii) Maintaining the server hardware stability is the next important factor. The systems
software is also maintained.
iii) The third factor includes power and environmental stabilities within the hosting
facility. This would help in determining the Windows Server 2012 reliability (Willcocks,
2013).
The availability of Windows Server 2012 could be determined by the following
factors:
i) The constant availability of web server is the most important factor to determine
availability.
ii) Periodical maintenance of the Windows Server 2012 is the next significant factor
to determine availability.
4. Ensuring Confidentiality and Integrity for Staff Email
Microsoft Exchange server is being utilized by the organization of Telstra
Corporation Ltd. to provide email services for their staffs. This particular software is
extremely important as well as effective, which was developed by the Microsoft organization
(Bajdor & Grabara, 2014). Operating system of this server is Windows Server. Several
versions of the Microsoft Exchange Server are present. There are few factors of the mail
server that help i0n ensuring the confidentiality and integrity for the emails of staffs.
The confidentiality is ensured by few factors. Amongst them, the most important
factor for ensuring confidentiality of the Microsoft Exchange Server is to be sure that none of
IS SECURITY AND RISK MANAGEMENT
i) The constant connection of Internet is the most important factor to determine
reliability.
ii) Maintaining the server hardware stability is the next important factor. The systems
software is also maintained.
iii) The third factor includes power and environmental stabilities within the hosting
facility. This would help in determining the Windows Server 2012 reliability (Willcocks,
2013).
The availability of Windows Server 2012 could be determined by the following
factors:
i) The constant availability of web server is the most important factor to determine
availability.
ii) Periodical maintenance of the Windows Server 2012 is the next significant factor
to determine availability.
4. Ensuring Confidentiality and Integrity for Staff Email
Microsoft Exchange server is being utilized by the organization of Telstra
Corporation Ltd. to provide email services for their staffs. This particular software is
extremely important as well as effective, which was developed by the Microsoft organization
(Bajdor & Grabara, 2014). Operating system of this server is Windows Server. Several
versions of the Microsoft Exchange Server are present. There are few factors of the mail
server that help i0n ensuring the confidentiality and integrity for the emails of staffs.
The confidentiality is ensured by few factors. Amongst them, the most important
factor for ensuring confidentiality of the Microsoft Exchange Server is to be sure that none of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
IS SECURITY AND RISK MANAGEMENT
the emails are read by the unauthenticated user. The authentication can be maintained by
keeping encryption within the server.
Integrity is ensured by only one important factor that the confidential data is not
changed by the hackers or attacks and thus data integrity is maintained.
5. Prioritization of Threats, Malware Types and Security Issues
All the staffs of the department of information technology for this particular
organization of Telstra Corporation Ltd have solely reported the fact that there are various
problems within the web server and web mail (Singhal et al., 2013). Several significant
malware, threats and security issues are present that could be vulnerable for the web server
and web mail. The prioritization of all these threats, types of malware and security issues is
given below:
i) Computer Virus: The first and the foremost threat of the web mail and web server
is computer virus (Arvidsson, Holmström & Lyytinen, 2014). This is the specific type of
malicious software program and malware that when being executed, subsequently replicates
itself by modification of the computer programs and hence inserting their own code.
ii) Phishing: The second important type of threat is phishing of emails. It can be
defined as the specific attempt that helps in obtaining any type of confidential information or
data such as passwords, usernames or the details of emails, which disguised as trustworthy
entities.
iii) Email Spoofing: The third important type of threat in Telstra Corporation Ltd. is
email spoofing (Willcocks, 2013). These types of emails are created by fake sender address
and thus authenticity is lost.
IS SECURITY AND RISK MANAGEMENT
the emails are read by the unauthenticated user. The authentication can be maintained by
keeping encryption within the server.
Integrity is ensured by only one important factor that the confidential data is not
changed by the hackers or attacks and thus data integrity is maintained.
5. Prioritization of Threats, Malware Types and Security Issues
All the staffs of the department of information technology for this particular
organization of Telstra Corporation Ltd have solely reported the fact that there are various
problems within the web server and web mail (Singhal et al., 2013). Several significant
malware, threats and security issues are present that could be vulnerable for the web server
and web mail. The prioritization of all these threats, types of malware and security issues is
given below:
i) Computer Virus: The first and the foremost threat of the web mail and web server
is computer virus (Arvidsson, Holmström & Lyytinen, 2014). This is the specific type of
malicious software program and malware that when being executed, subsequently replicates
itself by modification of the computer programs and hence inserting their own code.
ii) Phishing: The second important type of threat is phishing of emails. It can be
defined as the specific attempt that helps in obtaining any type of confidential information or
data such as passwords, usernames or the details of emails, which disguised as trustworthy
entities.
iii) Email Spoofing: The third important type of threat in Telstra Corporation Ltd. is
email spoofing (Willcocks, 2013). These types of emails are created by fake sender address
and thus authenticity is lost.
8
IS SECURITY AND RISK MANAGEMENT
iv) Spamming: The final threat is email spamming, where every unsolicited message
is sent.
6. Two Approaches for Improving Availability of Web and Email Servers
The business continuity of IT department is solely ensured by simply providing fault
tolerance as well as redundancy. The web servers and the email servers are made available
for the organization of Telstra Corporation Ltd. These two servers can be improvised by
taking the help of two important approaches. These approaches are given below:
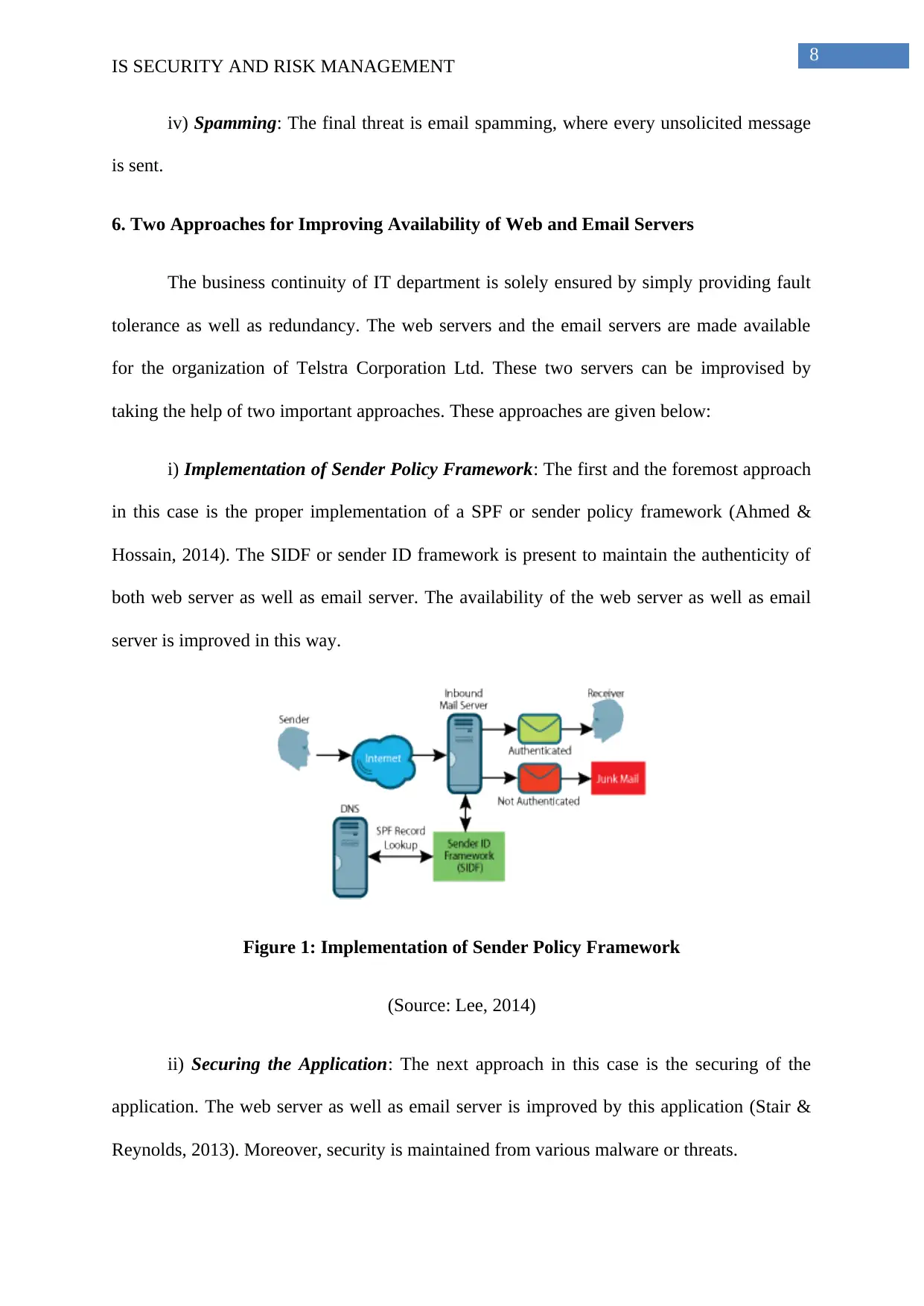
i) Implementation of Sender Policy Framework: The first and the foremost approach
in this case is the proper implementation of a SPF or sender policy framework (Ahmed &
Hossain, 2014). The SIDF or sender ID framework is present to maintain the authenticity of
both web server as well as email server. The availability of the web server as well as email
server is improved in this way.
Figure 1: Implementation of Sender Policy Framework
(Source: Lee, 2014)
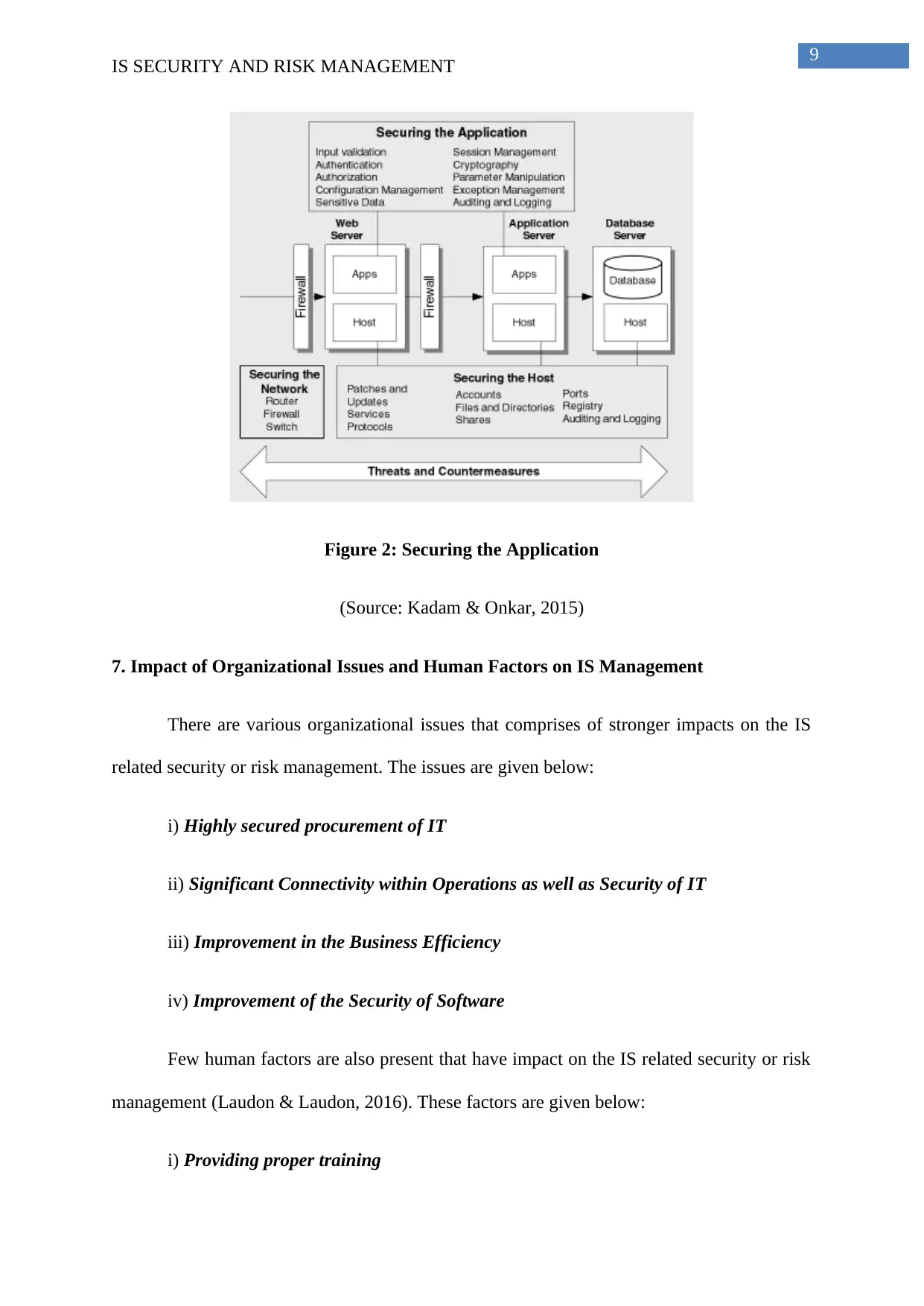
ii) Securing the Application: The next approach in this case is the securing of the
application. The web server as well as email server is improved by this application (Stair &
Reynolds, 2013). Moreover, security is maintained from various malware or threats.
IS SECURITY AND RISK MANAGEMENT
iv) Spamming: The final threat is email spamming, where every unsolicited message
is sent.
6. Two Approaches for Improving Availability of Web and Email Servers
The business continuity of IT department is solely ensured by simply providing fault
tolerance as well as redundancy. The web servers and the email servers are made available
for the organization of Telstra Corporation Ltd. These two servers can be improvised by
taking the help of two important approaches. These approaches are given below:
i) Implementation of Sender Policy Framework: The first and the foremost approach
in this case is the proper implementation of a SPF or sender policy framework (Ahmed &
Hossain, 2014). The SIDF or sender ID framework is present to maintain the authenticity of
both web server as well as email server. The availability of the web server as well as email
server is improved in this way.
Figure 1: Implementation of Sender Policy Framework
(Source: Lee, 2014)
ii) Securing the Application: The next approach in this case is the securing of the
application. The web server as well as email server is improved by this application (Stair &
Reynolds, 2013). Moreover, security is maintained from various malware or threats.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
IS SECURITY AND RISK MANAGEMENT
Figure 2: Securing the Application
(Source: Kadam & Onkar, 2015)
7. Impact of Organizational Issues and Human Factors on IS Management
There are various organizational issues that comprises of stronger impacts on the IS
related security or risk management. The issues are given below:
i) Highly secured procurement of IT
ii) Significant Connectivity within Operations as well as Security of IT
iii) Improvement in the Business Efficiency
iv) Improvement of the Security of Software
Few human factors are also present that have impact on the IS related security or risk
management (Laudon & Laudon, 2016). These factors are given below:
i) Providing proper training
IS SECURITY AND RISK MANAGEMENT
Figure 2: Securing the Application
(Source: Kadam & Onkar, 2015)
7. Impact of Organizational Issues and Human Factors on IS Management
There are various organizational issues that comprises of stronger impacts on the IS
related security or risk management. The issues are given below:
i) Highly secured procurement of IT
ii) Significant Connectivity within Operations as well as Security of IT
iii) Improvement in the Business Efficiency
iv) Improvement of the Security of Software
Few human factors are also present that have impact on the IS related security or risk
management (Laudon & Laudon, 2016). These factors are given below:
i) Providing proper training
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
IS SECURITY AND RISK MANAGEMENT
ii) Awareness
iii) Influence of security culture
iv) Learning about the various strengths and weaknesses of the organization.
8. Illustration of Log Records
Several log records are present within the company of Telstra Corporation Ltd. that
are being used to properly monitor as well as analyze the email server and web server. All of
these log records involve the access, event and security. Some of the most significant log
record functionalities are AllocReservedLog, CreateLogFile, AlignReservedLog, and
DeleteLogFile (Kadam & Onkar, 2015). All of these log records are utilized for various
purposes like creation, deletion, allocating and aligning the logs. The access, event and
security are used for helping to monitor as well as analyze the various issues of email server
and web server.
9. Utilization of Audit Log Records for Email and Web Server Issues
Each and every audit log record is utilized by the organization of Telstra Corporation
Ltd. to obtain better performance from audit analysis and hence supporting various internal
investigations within this company or indenting operational trends or the problems of log
term (Stojmenovic & Wen, 2014). The problems of email server and web server are easily
solved by the audit log records. The systems and accounts of the staffs could be easily
maintained and transactions would also be traced.
10. Five types of Network Security Devices for Controlling Security
Various network security devices are effective to control the security and privacy of
Telstra Corporation Ltd. Amongst them, the five network security devices are given below:
IS SECURITY AND RISK MANAGEMENT
ii) Awareness
iii) Influence of security culture
iv) Learning about the various strengths and weaknesses of the organization.
8. Illustration of Log Records
Several log records are present within the company of Telstra Corporation Ltd. that
are being used to properly monitor as well as analyze the email server and web server. All of
these log records involve the access, event and security. Some of the most significant log
record functionalities are AllocReservedLog, CreateLogFile, AlignReservedLog, and
DeleteLogFile (Kadam & Onkar, 2015). All of these log records are utilized for various
purposes like creation, deletion, allocating and aligning the logs. The access, event and
security are used for helping to monitor as well as analyze the various issues of email server
and web server.
9. Utilization of Audit Log Records for Email and Web Server Issues
Each and every audit log record is utilized by the organization of Telstra Corporation
Ltd. to obtain better performance from audit analysis and hence supporting various internal
investigations within this company or indenting operational trends or the problems of log
term (Stojmenovic & Wen, 2014). The problems of email server and web server are easily
solved by the audit log records. The systems and accounts of the staffs could be easily
maintained and transactions would also be traced.
10. Five types of Network Security Devices for Controlling Security
Various network security devices are effective to control the security and privacy of
Telstra Corporation Ltd. Amongst them, the five network security devices are given below:

11
IS SECURITY AND RISK MANAGEMENT
i) Network Switches: Network switches are responsible for working in the LAN layer
for packet filtering and them sending all the packets to respective interfaces.
ii) Bridges: The second network security device is bridge. Any particular router links
two different types of networks and thus a particular bridge is being utilized to connect two
sub networks (Klukas, Chen & Pape, 2014). The security is easily controlled by this device.
iii) Repeaters: The third network security device is repeater. This helps in amplifying
the respective signal, which is being received. Repeaters are extremely effective.
iv) Modems: Modem is the proper mixture of demodulator and modulator. The signal
is modulated and demodulated here.
v) Network Routers: This type of network device helps to route the traffic from any
one network to the other.
Conclusions and Recommendations
Therefore, from the above discussion, conclusion could be drawn that information
system or IS is the typical system, which is used by all companies to execute their business
processes or operations and perform all kinds of data or information operations. Several types
of IS or information systems are present. Amongst them, the most utilized or popular
information systems are ERP or enterprise resource planning system, DBMS or database
management system, GIS or geographic information system, ES or expert system and various
others. All these kinds of information systems could be easily used by all the several users to
attain the sole purpose of simplification of any information or data operation. Various
significant elements or components of the information system are present. These components
are software, complementary networks, hardware, procedures and databases. The four major
elements that are the software, complementary networks, hardware and databases together
IS SECURITY AND RISK MANAGEMENT
i) Network Switches: Network switches are responsible for working in the LAN layer
for packet filtering and them sending all the packets to respective interfaces.
ii) Bridges: The second network security device is bridge. Any particular router links
two different types of networks and thus a particular bridge is being utilized to connect two
sub networks (Klukas, Chen & Pape, 2014). The security is easily controlled by this device.
iii) Repeaters: The third network security device is repeater. This helps in amplifying
the respective signal, which is being received. Repeaters are extremely effective.
iv) Modems: Modem is the proper mixture of demodulator and modulator. The signal
is modulated and demodulated here.
v) Network Routers: This type of network device helps to route the traffic from any
one network to the other.
Conclusions and Recommendations
Therefore, from the above discussion, conclusion could be drawn that information
system or IS is the typical system, which is used by all companies to execute their business
processes or operations and perform all kinds of data or information operations. Several types
of IS or information systems are present. Amongst them, the most utilized or popular
information systems are ERP or enterprise resource planning system, DBMS or database
management system, GIS or geographic information system, ES or expert system and various
others. All these kinds of information systems could be easily used by all the several users to
attain the sole purpose of simplification of any information or data operation. Various
significant elements or components of the information system are present. These components
are software, complementary networks, hardware, procedures and databases. The four major
elements that are the software, complementary networks, hardware and databases together
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




