Risk Assessment Report for Walmart: BUS7011 Module, Semester 1
VerifiedAdded on 2022/08/26
|14
|3685
|22
Report
AI Summary
This report provides a comprehensive risk assessment of a data breach suffered by Walmart. The report begins with a critical consideration of key risk management concepts and principles, offering insights to prevent future crises. It then delves into Enterprise Risk Management (ERM), outlining its different aspects and differentiating between operational and strategic risks. The report evaluates specific strategic risks applicable to Walmart and assesses how IT can mitigate these risks. Furthermore, the report discusses the application of the ISO 31000 standard for IT risk management, exploring risk identification, analysis, and evaluation. The report concludes by emphasizing the importance of cybersecurity and the use of risk registers to control and manage risks effectively. The report provides recommendations for Walmart to improve its security posture and avoid future data breaches, covering topics from risk assessment, ERM, IT risk, and strategic risk.

1/10/2020
Running Head: RISK ASSESSMENT 0
Risk Assessment
Report
Student name
Running Head: RISK ASSESSMENT 0
Risk Assessment
Report
Student name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RISK ASSESSMENT 1
Table of Contents
Task -1........................................................................................................................................1
Task-2.........................................................................................................................................2
Task-3.........................................................................................................................................6
References..................................................................................................................................7
Table of Contents
Task -1........................................................................................................................................1
Task-2.........................................................................................................................................2
Task-3.........................................................................................................................................6
References..................................................................................................................................7

RISK ASSESSMENT 2
Task -1
Information security is necessary for a firm, as there is a large amount of data on various
business functions. Risk assessment is necessary to know about the threats of a firm. In
addition, large scale organizations have used cybersecurity tools and techniques. Most of the
companies have used audits and other standards to avoid various Information Technology
(IT) asset’s security. It is a risk for a firm if there are some vulnerabilities present in the
system of an organization. In addition, the business has based on trust as well, thus the
company should provide security to the data of customers, such as passwords, credit card
details, and others. Data security is an important aspect of the business of a firm (Bhagat,
2012).
In addition, Walmart has analyzed that its customer’s personal data is available at another
place, which is not under their control. In addition, a data breach has identified by the
researchers at Kromtech security. Kromtech security came across another publicly accessible
data storage, which is Amazon s3 bucket. It contains a MySQL database backup file, which
contains personal information of customers. It has included the user’s name, addresses, is
address, zip codes, email id, phone numbers, and plain text passwords. It is a combined file,
which has contained information of 1.3 million people, which are from the US and Canada.
Besides, public access data should be managed using tools and techniques (Bird, 2018).
It is a huge risk for the company, as it creates a bad image of the company in the market
place. Thus, it is necessary to avoid such types of issues in the future. It is the matter of data
breach; the file was stored as named ‘Walmart’s’. It has confused all the companies and
researchers. After father investigation of that file. It was found that it belongs to MBM
Company Inc., which is a jewelry company based in Chicago, IL. The company is known as
Limoges Jewellery in the market. However, Walmart should use IT security services to
secure their data from such types of incidents. IT risk management is necessary for large
scale organizations, as it has provided better strategies to secure the whole system (Bridges,
2019).
The backup was named MBMWEB_backup_2018_01_13_003008_2864410.bak that
indicates about the public access data since January 13, 2018. There are many things to avoid
in this file, as it has shared encrypted credit card details, promo codes, payment details, which
provides the same filed in the customer database of the MBM company Inc. all the records
Task -1
Information security is necessary for a firm, as there is a large amount of data on various
business functions. Risk assessment is necessary to know about the threats of a firm. In
addition, large scale organizations have used cybersecurity tools and techniques. Most of the
companies have used audits and other standards to avoid various Information Technology
(IT) asset’s security. It is a risk for a firm if there are some vulnerabilities present in the
system of an organization. In addition, the business has based on trust as well, thus the
company should provide security to the data of customers, such as passwords, credit card
details, and others. Data security is an important aspect of the business of a firm (Bhagat,
2012).
In addition, Walmart has analyzed that its customer’s personal data is available at another
place, which is not under their control. In addition, a data breach has identified by the
researchers at Kromtech security. Kromtech security came across another publicly accessible
data storage, which is Amazon s3 bucket. It contains a MySQL database backup file, which
contains personal information of customers. It has included the user’s name, addresses, is
address, zip codes, email id, phone numbers, and plain text passwords. It is a combined file,
which has contained information of 1.3 million people, which are from the US and Canada.
Besides, public access data should be managed using tools and techniques (Bird, 2018).
It is a huge risk for the company, as it creates a bad image of the company in the market
place. Thus, it is necessary to avoid such types of issues in the future. It is the matter of data
breach; the file was stored as named ‘Walmart’s’. It has confused all the companies and
researchers. After father investigation of that file. It was found that it belongs to MBM
Company Inc., which is a jewelry company based in Chicago, IL. The company is known as
Limoges Jewellery in the market. However, Walmart should use IT security services to
secure their data from such types of incidents. IT risk management is necessary for large
scale organizations, as it has provided better strategies to secure the whole system (Bridges,
2019).
The backup was named MBMWEB_backup_2018_01_13_003008_2864410.bak that
indicates about the public access data since January 13, 2018. There are many things to avoid
in this file, as it has shared encrypted credit card details, promo codes, payment details, which
provides the same filed in the customer database of the MBM company Inc. all the records
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

RISK ASSESSMENT 3
are from 2000 to early 2018. Risk management is necessary to secure the company from data
breaches and other issues (Cole, 2015).
It is a good thing to notify by the Kromtech about the public Amazon S3 bucket immediately
based on their research. However, Walmart has used a high level of security for its storage
bucket. Based on the information, Walmart should check their storages to avoid any type of
risk from cyber-attacks. Data breach makes a huge impact on the reputation and financial
conditions of the company. Walmart should adopt international frameworks for securing their
IT assets and resources, such as data, information, and many more. It is a common process to
secure data from different types of risks. In addition, there are many things to manage in a
company, which can be a reason of risk for data storages (DISSENT, 2018). Walmart should
protect their data from different things, such as legal, social, and ethical. It is a basic need for
a retail company to secure its customer's data from data breaches, which can make huge
financial losses (Andrijcic & Horowitz, 2016).
Furthermore, Walmart can be faced with such types of issues in their future. Thus, it is
necessary to implement new policies and legal actions for such types of issues with the data
of the company. There are many Information Security Management Systems (ISMS) are
available for securing the IT assets of the organosilicon. Moreover, Risk assessment is
necessary to secure various resources of the company and it is helpful in the identification of
vulnerabilities of the company as well (Humphreys, 2008).
Furthermore, Walmart can use security services for its cloud services, as most of the services
can be used for managing logistics and supply chain. There are many things to change in the
business strategies and operations, as cyber-attacks have increased because of various reasons
in the security. Most of the IT assets can be compromised from malicious programs. Thus, it
is necessary to avoid such type of devices, which are risky from security and privacy point of
view.
are from 2000 to early 2018. Risk management is necessary to secure the company from data
breaches and other issues (Cole, 2015).
It is a good thing to notify by the Kromtech about the public Amazon S3 bucket immediately
based on their research. However, Walmart has used a high level of security for its storage
bucket. Based on the information, Walmart should check their storages to avoid any type of
risk from cyber-attacks. Data breach makes a huge impact on the reputation and financial
conditions of the company. Walmart should adopt international frameworks for securing their
IT assets and resources, such as data, information, and many more. It is a common process to
secure data from different types of risks. In addition, there are many things to manage in a
company, which can be a reason of risk for data storages (DISSENT, 2018). Walmart should
protect their data from different things, such as legal, social, and ethical. It is a basic need for
a retail company to secure its customer's data from data breaches, which can make huge
financial losses (Andrijcic & Horowitz, 2016).
Furthermore, Walmart can be faced with such types of issues in their future. Thus, it is
necessary to implement new policies and legal actions for such types of issues with the data
of the company. There are many Information Security Management Systems (ISMS) are
available for securing the IT assets of the organosilicon. Moreover, Risk assessment is
necessary to secure various resources of the company and it is helpful in the identification of
vulnerabilities of the company as well (Humphreys, 2008).
Furthermore, Walmart can use security services for its cloud services, as most of the services
can be used for managing logistics and supply chain. There are many things to change in the
business strategies and operations, as cyber-attacks have increased because of various reasons
in the security. Most of the IT assets can be compromised from malicious programs. Thus, it
is necessary to avoid such type of devices, which are risky from security and privacy point of
view.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RISK ASSESSMENT 4
Task-2
Enterprise Risk Management (ERM) is the best way to handle the risks of firms, which can
occur in the systems because of a lack of security and privacy. There are many important
factors in the ERM, which are beneficial for risk assessment and management. In addition,
most of the processes. Walmart should adopt ISO 27001, and ISO 31000 standards.
Moreover, the organization can be used cybersecurity for managing all the things. In addition,
basic services can be improved using proper security policies and services.
Source: (Parker, 2019)
Risk assessments: the company should create an audit for all the IT assets, which has used
for the identification of various things. There are various assets, which contain vulnerabilities
in them. Those vulnerabilities can be a reason of risk and threat for the firm. Walmart should
use risk assessment to analyse vulnerabilities and threats of the company.
Control Assessments: the company should set some controls on the risks, which can be
managed and control using proper controls. In addition, controls can be created based on the
risk of the level.
Monitoring and reporting: monitoring is necessary for network and computer systems as
well as other peripherals. There are many monitoring software’s in the market, which can be
Task-2
Enterprise Risk Management (ERM) is the best way to handle the risks of firms, which can
occur in the systems because of a lack of security and privacy. There are many important
factors in the ERM, which are beneficial for risk assessment and management. In addition,
most of the processes. Walmart should adopt ISO 27001, and ISO 31000 standards.
Moreover, the organization can be used cybersecurity for managing all the things. In addition,
basic services can be improved using proper security policies and services.
Source: (Parker, 2019)
Risk assessments: the company should create an audit for all the IT assets, which has used
for the identification of various things. There are various assets, which contain vulnerabilities
in them. Those vulnerabilities can be a reason of risk and threat for the firm. Walmart should
use risk assessment to analyse vulnerabilities and threats of the company.
Control Assessments: the company should set some controls on the risks, which can be
managed and control using proper controls. In addition, controls can be created based on the
risk of the level.
Monitoring and reporting: monitoring is necessary for network and computer systems as
well as other peripherals. There are many monitoring software’s in the market, which can be

RISK ASSESSMENT 5
used for monitoring and reporting servers and other devices as well as networks. IT service
management is the best option for the firm.
Issue Remediation: it is necessary to get a response of any risk and attack from the system
or person. Therefore, proper action can take before any big loss in the firm.
Risk identification and documentation: the firm should know about the risks and threats of
their IT systems. Moreover, the company should create a risk register to identify the level of
the risk and its controls.
There are many methods for managing risks including identification, monitoring, audit, and
many more. In addition, the risk matrix is necessary to know about the consequences and
likelihood of the risks (Zhou, et al., 2008). ERM systems are beneficial for managing risks of
the firm, as strategic and operational risks can damage the company in the future. Thus, it is
necessary to avoid such types of things from the firm.
Source: (Parsons , 2016)
Risk analysis can be used for managing the various levels of risks and threats. It will be easy
for the firm. In addition, risks can be divided into three levels, such as low, medium and high.
In addition, Walmart can manage all the things using the level of risk. It can be better with
the analysis of various processes of business (Svantesson & Clarke, 2010). There is some
basic difference between operational risk from strategic risk. There are some problems have
raised between various things, such as cyberattacks and cybercrime. Moreover, the
organization has failed in the basic performance of service management. Thus, it is an
internal and external impact on business strategies. Operational risks are riskier than many
used for monitoring and reporting servers and other devices as well as networks. IT service
management is the best option for the firm.
Issue Remediation: it is necessary to get a response of any risk and attack from the system
or person. Therefore, proper action can take before any big loss in the firm.
Risk identification and documentation: the firm should know about the risks and threats of
their IT systems. Moreover, the company should create a risk register to identify the level of
the risk and its controls.
There are many methods for managing risks including identification, monitoring, audit, and
many more. In addition, the risk matrix is necessary to know about the consequences and
likelihood of the risks (Zhou, et al., 2008). ERM systems are beneficial for managing risks of
the firm, as strategic and operational risks can damage the company in the future. Thus, it is
necessary to avoid such types of things from the firm.
Source: (Parsons , 2016)
Risk analysis can be used for managing the various levels of risks and threats. It will be easy
for the firm. In addition, risks can be divided into three levels, such as low, medium and high.
In addition, Walmart can manage all the things using the level of risk. It can be better with
the analysis of various processes of business (Svantesson & Clarke, 2010). There is some
basic difference between operational risk from strategic risk. There are some problems have
raised between various things, such as cyberattacks and cybercrime. Moreover, the
organization has failed in the basic performance of service management. Thus, it is an
internal and external impact on business strategies. Operational risks are riskier than many
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
RISK ASSESSMENT 6
other risks. However, strategic risk can be optimized using basic things. In addition, strategic
risk is a failure in decision making in the business (Zhang, et al., 2010).
Moreover, a data breach is an operational risk, which makes many impacts on the financial
condition of a firm. Besides, the firm can use basic tools and techniques to reduce operational
risks. Moreover, strategic risks make a huge impact on various fields. There are many
benefits of risk assessment, as it can handle different types of risks, such as operational, and
strategic risks. However, risk management will provide better results to reduce the risk of all
the things.
Mitigation strategies have provided by government agencies (ACSC, 2019). However,
Walmart has used its own mitigation strategies to improve the various risks from its
environment. Moreover, all the processes can be secured using mitigate many risks using
basic services (Security-Center, 2018).
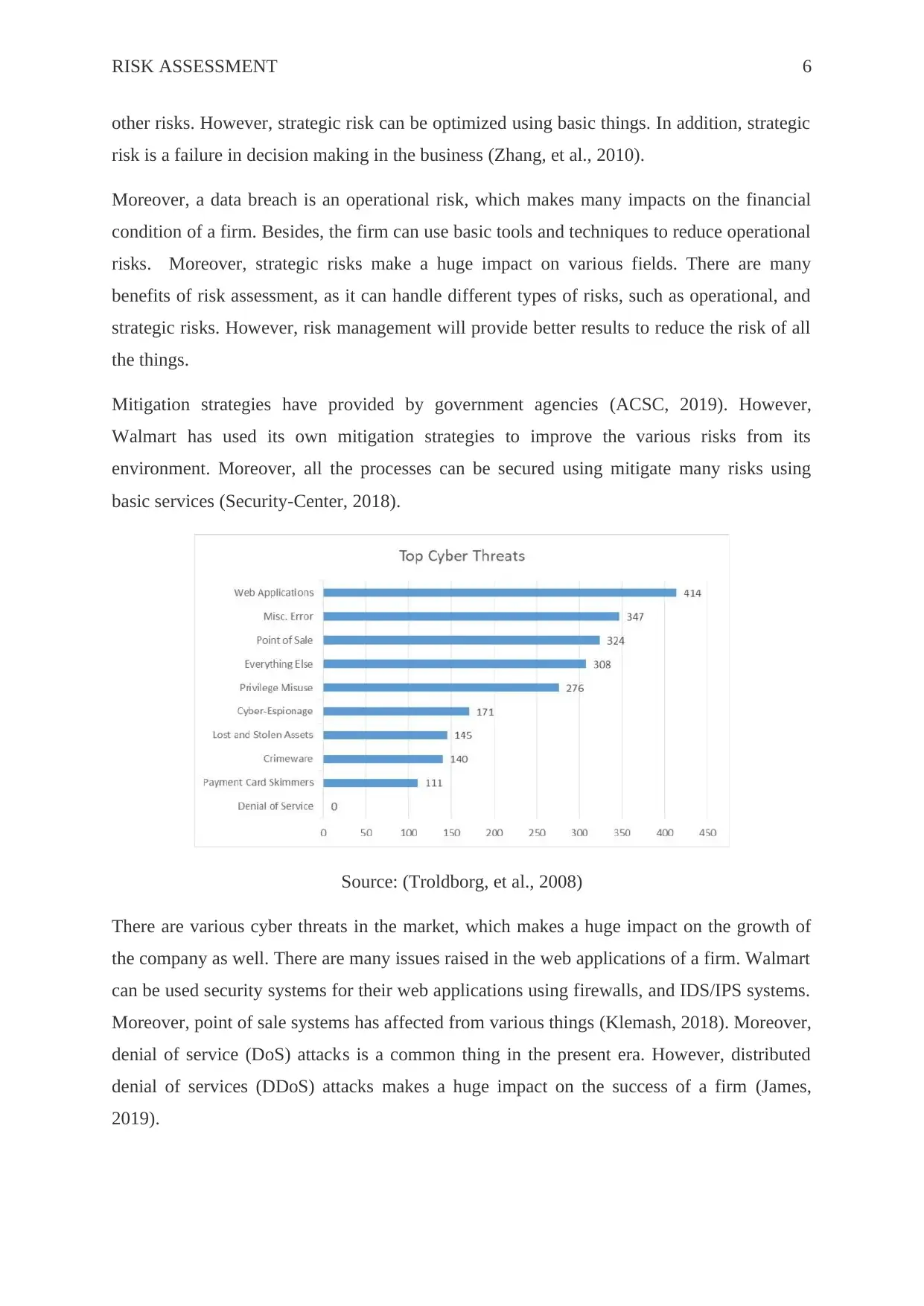
Source: (Troldborg, et al., 2008)
There are various cyber threats in the market, which makes a huge impact on the growth of
the company as well. There are many issues raised in the web applications of a firm. Walmart
can be used security systems for their web applications using firewalls, and IDS/IPS systems.
Moreover, point of sale systems has affected from various things (Klemash, 2018). Moreover,
denial of service (DoS) attacks is a common thing in the present era. However, distributed
denial of services (DDoS) attacks makes a huge impact on the success of a firm (James,
2019).
other risks. However, strategic risk can be optimized using basic things. In addition, strategic
risk is a failure in decision making in the business (Zhang, et al., 2010).
Moreover, a data breach is an operational risk, which makes many impacts on the financial
condition of a firm. Besides, the firm can use basic tools and techniques to reduce operational
risks. Moreover, strategic risks make a huge impact on various fields. There are many
benefits of risk assessment, as it can handle different types of risks, such as operational, and
strategic risks. However, risk management will provide better results to reduce the risk of all
the things.
Mitigation strategies have provided by government agencies (ACSC, 2019). However,
Walmart has used its own mitigation strategies to improve the various risks from its
environment. Moreover, all the processes can be secured using mitigate many risks using
basic services (Security-Center, 2018).
Source: (Troldborg, et al., 2008)
There are various cyber threats in the market, which makes a huge impact on the growth of
the company as well. There are many issues raised in the web applications of a firm. Walmart
can be used security systems for their web applications using firewalls, and IDS/IPS systems.
Moreover, point of sale systems has affected from various things (Klemash, 2018). Moreover,
denial of service (DoS) attacks is a common thing in the present era. However, distributed
denial of services (DDoS) attacks makes a huge impact on the success of a firm (James,
2019).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RISK ASSESSMENT 7
Furthermore, most of the things can be managed using this framework. In addition, there are
many things to optimizes in the supply chain and logistics, as it can be a recession of security
breach. In addition, there are some changes in the main databases using agile methodologies.
Walmart has used Internet of Things (IoT) devices, which is a basic need of a system.
Moreover, Walmart can choose different things for managing different processes (Sotnikov,
2018).
Furthermore, most of the things can be managed using this framework. In addition, there are
many things to optimizes in the supply chain and logistics, as it can be a recession of security
breach. In addition, there are some changes in the main databases using agile methodologies.
Walmart has used Internet of Things (IoT) devices, which is a basic need of a system.
Moreover, Walmart can choose different things for managing different processes (Sotnikov,
2018).
RISK ASSESSMENT 8
Task-3
Walmart has used a large scale of data and information. In addition, the ISO 31000 standard
can be used for IT risk management. It is the best way to manage the security of the system.
Moreover, the risk register has provided many benefits for risk controls (Mutton, 2012). Risk
analysis is necessary for large-scale organizations, as most of the companies have used risk
analysis to avoid financial and reputational losses.
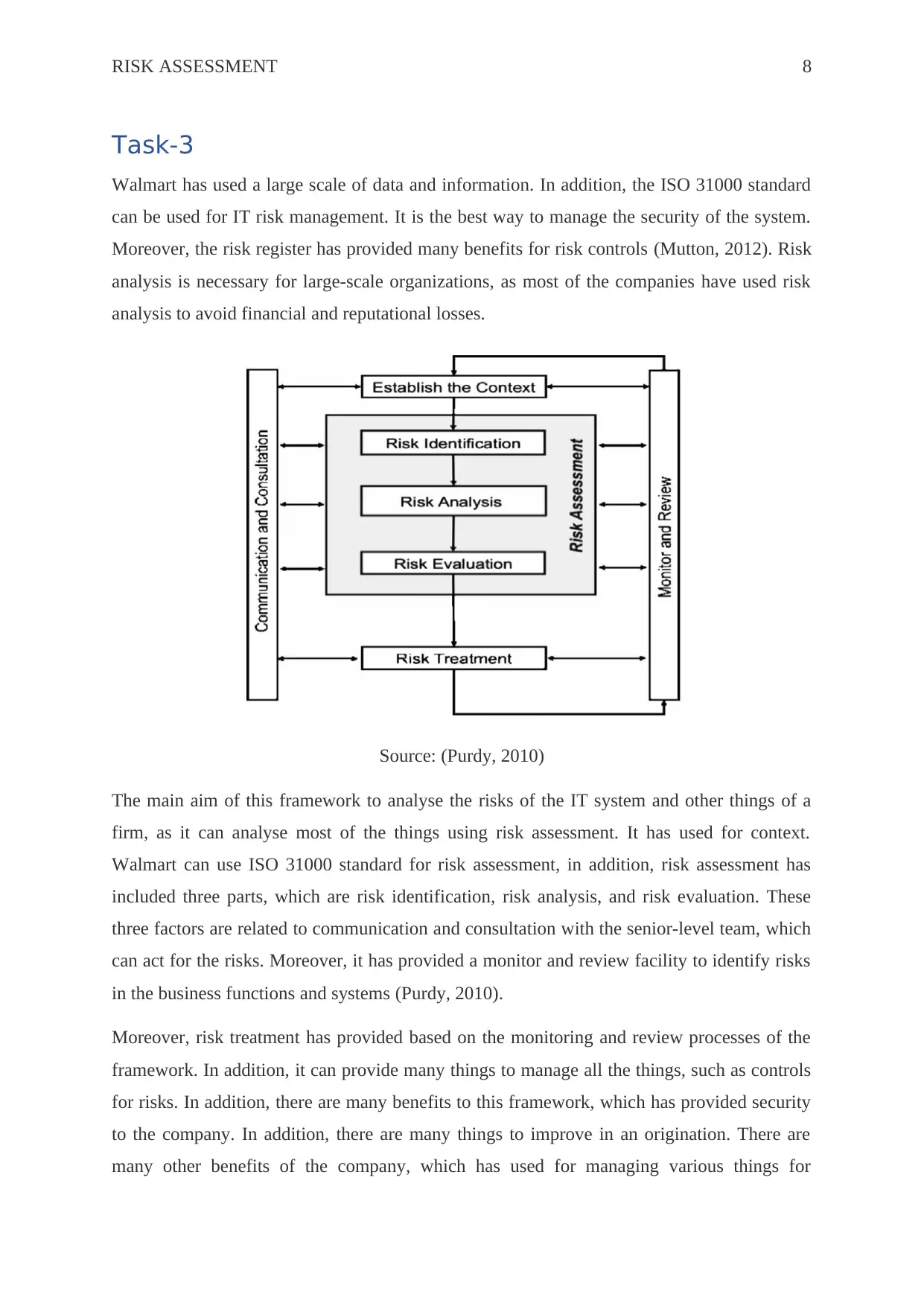
Source: (Purdy, 2010)
The main aim of this framework to analyse the risks of the IT system and other things of a
firm, as it can analyse most of the things using risk assessment. It has used for context.
Walmart can use ISO 31000 standard for risk assessment, in addition, risk assessment has
included three parts, which are risk identification, risk analysis, and risk evaluation. These
three factors are related to communication and consultation with the senior-level team, which
can act for the risks. Moreover, it has provided a monitor and review facility to identify risks
in the business functions and systems (Purdy, 2010).
Moreover, risk treatment has provided based on the monitoring and review processes of the
framework. In addition, it can provide many things to manage all the things, such as controls
for risks. In addition, there are many benefits to this framework, which has provided security
to the company. In addition, there are many things to improve in an origination. There are
many other benefits of the company, which has used for managing various things for
Task-3
Walmart has used a large scale of data and information. In addition, the ISO 31000 standard
can be used for IT risk management. It is the best way to manage the security of the system.
Moreover, the risk register has provided many benefits for risk controls (Mutton, 2012). Risk
analysis is necessary for large-scale organizations, as most of the companies have used risk
analysis to avoid financial and reputational losses.
Source: (Purdy, 2010)
The main aim of this framework to analyse the risks of the IT system and other things of a
firm, as it can analyse most of the things using risk assessment. It has used for context.
Walmart can use ISO 31000 standard for risk assessment, in addition, risk assessment has
included three parts, which are risk identification, risk analysis, and risk evaluation. These
three factors are related to communication and consultation with the senior-level team, which
can act for the risks. Moreover, it has provided a monitor and review facility to identify risks
in the business functions and systems (Purdy, 2010).
Moreover, risk treatment has provided based on the monitoring and review processes of the
framework. In addition, it can provide many things to manage all the things, such as controls
for risks. In addition, there are many benefits to this framework, which has provided security
to the company. In addition, there are many things to improve in an origination. There are
many other benefits of the company, which has used for managing various things for
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

RISK ASSESSMENT 9
improvement in the processes. Besides, strategic planning is necessary for a firm (Mayhey,
2019).
Moreover, Walmart must use risk analysis to modify all the things (Svantesson & Clarke,
2010). Furthermore, IT service management is a better option to manage strategic and
operational risks of Walmart. Moreover, there are many other international standards for
managing service to reduce risks. In addition, there are many features of ISO standards,
which can be used for audit as well, such as ISO 27001, and others (Sotnikov, 2018).
Furthermore, risk assessment is helpful for finding vulnerabilities and threats of the firm.
Moreover, Walmart can be used cybersecurity to secure all the IT-assets. It is a basic need of
the company to update all the systems on time to avoid the security risks. In addition, there
are many benefits risk assessment, such as finical losses, reputation, marketing, sales, and
many more. In addition, CC is not secure from external threats, as it can access using a
private network (Mather, et al., 2009).
There are many good things in the firm, which has provided better services to their
customers. Moreover, it is necessary to secure all the things using cybersecurity, such as
computer systems, mobile phones, tablets, information systems, ERP, and many others. There
are various things to manage for securing all the data and information. Walmart is using
various services source for securing all the assets. There are many assets in the company,
which can be used for managing the security of the company. There are some risks in the
company, which can make financial losses.
Most of the risks can be managed using mitigation strategies, which are part of the business
strategies. Moreover, business processes can be managed using proper IS strategies, as
Walmart has used digital technologies for managing most of the processes. A data breach can
be avoided using monitoring and control processes. Walmart should use server and network
monitoring software to analyse suspicious processes (Zhang, et al., 2010), such as
unauthorized login, database access, and many others. Moreover, the company can improve
the security of the access level of data and data centres. It will secure all the data and
information of the company and its customers. This will provide better results in the future.
Moreover, security policies must be updated based on the changes in the environment
(Svantesson & Clarke, 2010). Walmart has used emerging technologies for managing their
business functions, such as inventory, supply-chain, financial, human resource, and many
more (Manuj & Mentzer, 2008). It has used cloud computing, artificial intelligence (AI), big
improvement in the processes. Besides, strategic planning is necessary for a firm (Mayhey,
2019).
Moreover, Walmart must use risk analysis to modify all the things (Svantesson & Clarke,
2010). Furthermore, IT service management is a better option to manage strategic and
operational risks of Walmart. Moreover, there are many other international standards for
managing service to reduce risks. In addition, there are many features of ISO standards,
which can be used for audit as well, such as ISO 27001, and others (Sotnikov, 2018).
Furthermore, risk assessment is helpful for finding vulnerabilities and threats of the firm.
Moreover, Walmart can be used cybersecurity to secure all the IT-assets. It is a basic need of
the company to update all the systems on time to avoid the security risks. In addition, there
are many benefits risk assessment, such as finical losses, reputation, marketing, sales, and
many more. In addition, CC is not secure from external threats, as it can access using a
private network (Mather, et al., 2009).
There are many good things in the firm, which has provided better services to their
customers. Moreover, it is necessary to secure all the things using cybersecurity, such as
computer systems, mobile phones, tablets, information systems, ERP, and many others. There
are various things to manage for securing all the data and information. Walmart is using
various services source for securing all the assets. There are many assets in the company,
which can be used for managing the security of the company. There are some risks in the
company, which can make financial losses.
Most of the risks can be managed using mitigation strategies, which are part of the business
strategies. Moreover, business processes can be managed using proper IS strategies, as
Walmart has used digital technologies for managing most of the processes. A data breach can
be avoided using monitoring and control processes. Walmart should use server and network
monitoring software to analyse suspicious processes (Zhang, et al., 2010), such as
unauthorized login, database access, and many others. Moreover, the company can improve
the security of the access level of data and data centres. It will secure all the data and
information of the company and its customers. This will provide better results in the future.
Moreover, security policies must be updated based on the changes in the environment
(Svantesson & Clarke, 2010). Walmart has used emerging technologies for managing their
business functions, such as inventory, supply-chain, financial, human resource, and many
more (Manuj & Mentzer, 2008). It has used cloud computing, artificial intelligence (AI), big
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RISK ASSESSMENT 10
data, machine learning, many others to manage their logistics and other operations.
Moreover, business processes can be used for managing all the things (Grossberg, 2016).
Furthermore, Walmart should implement new policies, which can avoid data breaches in the
future. Moreover, risk assessment is the best way to prevent the system form various things
(Parsons , 2016). In addition, there are many things to prevent in the firm from cyber-attacks
and cybercrime. It will improve the basic things in the firm, which will improve the growth of
the company. Moreover, technological innovations will improve the growth and performance
of the company in the future. It will improve security and privacy of the system as well
(Sotnikov, 2018). Most of the risks can be avoided using the basic and advance cybersecurity
systems and risk assessment. Besides, risk assessment has used for identification of the risks
and threats of the firm, which is useful in the avoiding critical conditions in the future.
data, machine learning, many others to manage their logistics and other operations.
Moreover, business processes can be used for managing all the things (Grossberg, 2016).
Furthermore, Walmart should implement new policies, which can avoid data breaches in the
future. Moreover, risk assessment is the best way to prevent the system form various things
(Parsons , 2016). In addition, there are many things to prevent in the firm from cyber-attacks
and cybercrime. It will improve the basic things in the firm, which will improve the growth of
the company. Moreover, technological innovations will improve the growth and performance
of the company in the future. It will improve security and privacy of the system as well
(Sotnikov, 2018). Most of the risks can be avoided using the basic and advance cybersecurity
systems and risk assessment. Besides, risk assessment has used for identification of the risks
and threats of the firm, which is useful in the avoiding critical conditions in the future.

RISK ASSESSMENT 11
References
ACSC, 2019. Strategies to Mitigate Cyber Security Incidents. [Online]
Available at: https://acsc.gov.au/infosec/mitigationstrategies.htm
[Accessed 3 September 2019].
Andrijcic, E. & Horowitz, B., 2016. A Macro‐Economic Framework for Evaluation of Cyber
Security Risks Related to Protection of Intellectual Property. Risk analysis, 26(4), pp. 907-
923.
Bhagat, . B. C., 2012. Cloud computing governance, cyber security, risk, and compliance
business rules system and method. U. S., Patent No. 13/016,999.
Bird, D. A., 2018. Information Security risk considerations for the processing of IoT sourced
data in the Public Cloud.
Bridges, J., 2019. IT Risk Management Strategies and Best Practices. [Online]
Available at: https://www.projectmanager.com/training/it-risk-management-strategies
[Accessed 28 December 2019].
Cole, B., 2015. Risk management. [Online]
Available at: https://searchcompliance.techtarget.com/definition/risk-management
[Accessed 28 December 2019].
DISSENT, 2018. Walmart jewelry partner exposed 1.3 million customer details. [Online]
Available at: https://www.databreaches.net/walmart-jewelry-partner-exposed-1-3-million-
customer-details/
[Accessed 10 January 2020].
Grossberg, K. A., 2016. The new marketing solutions that will drive strategy
implementation.. Strategy & leadership, 44(3), pp. 20-26.
Humphreys, E., 2008. Information security management standards: Compliance, governance
and risk management. information security technical report, 13(4), pp. 247-255.
James, P., 2019. Information Security Risks That You Need to Careful With Vendors/3rd
Parties. [Online]
Available at: https://gbhackers.com/information-security-risks/
[Accessed 25 November 2019].
References
ACSC, 2019. Strategies to Mitigate Cyber Security Incidents. [Online]
Available at: https://acsc.gov.au/infosec/mitigationstrategies.htm
[Accessed 3 September 2019].
Andrijcic, E. & Horowitz, B., 2016. A Macro‐Economic Framework for Evaluation of Cyber
Security Risks Related to Protection of Intellectual Property. Risk analysis, 26(4), pp. 907-
923.
Bhagat, . B. C., 2012. Cloud computing governance, cyber security, risk, and compliance
business rules system and method. U. S., Patent No. 13/016,999.
Bird, D. A., 2018. Information Security risk considerations for the processing of IoT sourced
data in the Public Cloud.
Bridges, J., 2019. IT Risk Management Strategies and Best Practices. [Online]
Available at: https://www.projectmanager.com/training/it-risk-management-strategies
[Accessed 28 December 2019].
Cole, B., 2015. Risk management. [Online]
Available at: https://searchcompliance.techtarget.com/definition/risk-management
[Accessed 28 December 2019].
DISSENT, 2018. Walmart jewelry partner exposed 1.3 million customer details. [Online]
Available at: https://www.databreaches.net/walmart-jewelry-partner-exposed-1-3-million-
customer-details/
[Accessed 10 January 2020].
Grossberg, K. A., 2016. The new marketing solutions that will drive strategy
implementation.. Strategy & leadership, 44(3), pp. 20-26.
Humphreys, E., 2008. Information security management standards: Compliance, governance
and risk management. information security technical report, 13(4), pp. 247-255.
James, P., 2019. Information Security Risks That You Need to Careful With Vendors/3rd
Parties. [Online]
Available at: https://gbhackers.com/information-security-risks/
[Accessed 25 November 2019].
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





