Risk Assessment, Data Protection, Security Policy & Disaster Recovery
VerifiedAdded on 2021/09/08
|46
|15259
|371
Report
AI Summary
This report provides a comprehensive overview of critical aspects of organizational security and business continuity. It begins with a detailed examination of risk assessment procedures, including defining risk, identifying assets and threats, and outlining the steps involved in a thorough risk assessment. The report then delves into data protection processes and regulations, emphasizing their importance and how they apply to an organization. Next, it explores the design and implementation of a security policy, covering its definition, various examples, and the key elements and steps required for its creation. Finally, the report examines the main components of an organizational disaster recovery plan, justifying their inclusion and outlining the disaster recovery process steps and essential policies and procedures for business continuity. The report utilizes figures and tables to illustrate key concepts and provides a structured approach to understanding and managing organizational risks and ensuring business resilience.

Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
I. Risk Assessment Procedures (P5): ............................................................................................................................ 5
1. Definition of risk and risk assessment: ................................................................................................................ 5
2. Asset and threat identification procedures: ........................................................................................................ 7
2.1. Asset and threat: ........................................................................................................................................... 7
2.2. Threat identification procedures: ................................................................................................................. 8
3. Risk assessment procedure: ................................................................................................................................ 8
4. Risk identification steps: .................................................................................................................................... 10
II. Data protection processes and regulations as applicable to an organization (P6): ............................................... 11
1. Definition of data protection: ............................................................................................................................ 11
2. Data protection processes with relations to organization: ............................................................................... 12
3. The importance of data protection regulation: ................................................................................................. 13
III. Design and implement a security policy for an organization (P7): ....................................................................... 16
1. Definition and discussion of security policy: ..................................................................................................... 16
2. Examples of security policies: ............................................................................................................................ 18
3. The elements of creating security policy: .......................................................................................................... 32
4. Steps to design a policy: .................................................................................................................................... 34
IV. Main components of an organizational disaster recovery plan, justifying the reasons for inclusion (P8): .......... 37
1. Business continuity: ........................................................................................................................................... 37
2. Components of recovery plan: .......................................................................................................................... 38
3. Disaster recovery process steps: ....................................................................................................................... 41
4. Some of the policies and procedures required for business continuity: ........................................................... 44
I. Risk Assessment Procedures (P5): ............................................................................................................................ 5
1. Definition of risk and risk assessment: ................................................................................................................ 5
2. Asset and threat identification procedures: ........................................................................................................ 7
2.1. Asset and threat: ........................................................................................................................................... 7
2.2. Threat identification procedures: ................................................................................................................. 8
3. Risk assessment procedure: ................................................................................................................................ 8
4. Risk identification steps: .................................................................................................................................... 10
II. Data protection processes and regulations as applicable to an organization (P6): ............................................... 11
1. Definition of data protection: ............................................................................................................................ 11
2. Data protection processes with relations to organization: ............................................................................... 12
3. The importance of data protection regulation: ................................................................................................. 13
III. Design and implement a security policy for an organization (P7): ....................................................................... 16
1. Definition and discussion of security policy: ..................................................................................................... 16
2. Examples of security policies: ............................................................................................................................ 18
3. The elements of creating security policy: .......................................................................................................... 32
4. Steps to design a policy: .................................................................................................................................... 34
IV. Main components of an organizational disaster recovery plan, justifying the reasons for inclusion (P8): .......... 37
1. Business continuity: ........................................................................................................................................... 37
2. Components of recovery plan: .......................................................................................................................... 38
3. Disaster recovery process steps: ....................................................................................................................... 41
4. Some of the policies and procedures required for business continuity: ........................................................... 44
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Figure 1: What is risk? ............................................................................................................................................. 4
Figure 2: IT risk assessment ..................................................................................................................................... 5
Figure 3: Asset and threat identification .................................................................................................................. 6
Figure 4: Data protection ...................................................................................................................................... 10
Figure 5: Data protection process .......................................................................................................................... 11
Figure 6: IT security policy ..................................................................................................................................... 14
Figure 7: Business Continuity Plan ......................................................................................................................... 30
Figure 8: Components of disaster recovery plan .................................................................................................... 33
Figure 9: BCP Lifecycle ........................................................................................................................................... 37
Figure 2: IT risk assessment ..................................................................................................................................... 5
Figure 3: Asset and threat identification .................................................................................................................. 6
Figure 4: Data protection ...................................................................................................................................... 10
Figure 5: Data protection process .......................................................................................................................... 11
Figure 6: IT security policy ..................................................................................................................................... 14
Figure 7: Business Continuity Plan ......................................................................................................................... 30
Figure 8: Components of disaster recovery plan .................................................................................................... 33
Figure 9: BCP Lifecycle ........................................................................................................................................... 37
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
I. Risk Assessment Procedures (P5):
1. Definition of risk and risk assessment:
a) Security risk
Security risk encompasses the consequences that could arise due to the risks and weaknesses associated with the
operation and use of information systems and the environments under which such systems function for an entity
and its stakeholders. In terms of the types of effect that may arise from the occurrence of a security-related
event, security risk overlaps with many other types of risk. Factors attributed to other risk categories, including
strategic, budgetary, program management, investment, political, legal, supply chain, and enforcement risk, also
affect it. Financial losses, loss of privacy, reputational damage, legal consequences, and even loss of life are
examples of risk.
b) Risk assessment
A Security Risk Assessment (or SRA) is an assessment that includes defining the risks in your company, your
technology, and your processes to verify that security threats are covered by controls in place. Compliance norms,
such as PCI-DSS requirements for payment card authentication, usually include security risk assessments. As part
of a SOC II audit for service organizations, they are mandated by the AICPA and are also, just to name a few,
criteria for ISO 27001, HITRUST CSF and HIPAA compliance. Because of this, security risk assessments can go by
several names, often referred to as a risk assessment, a risk assessment of IT infrastructure, a safety risk audit, or
a safety audit.
Security Risk Assessments are carried out in order to locate risk areas by a security assessor who can analyze all
aspects of the business processes. These may be as basic as a poor password-enabled device, or may be more
complicated problems, such as insecure business processes. The appraiser is going to typically review everything
from HR policies to firewall configurations while working to identify potential risks.
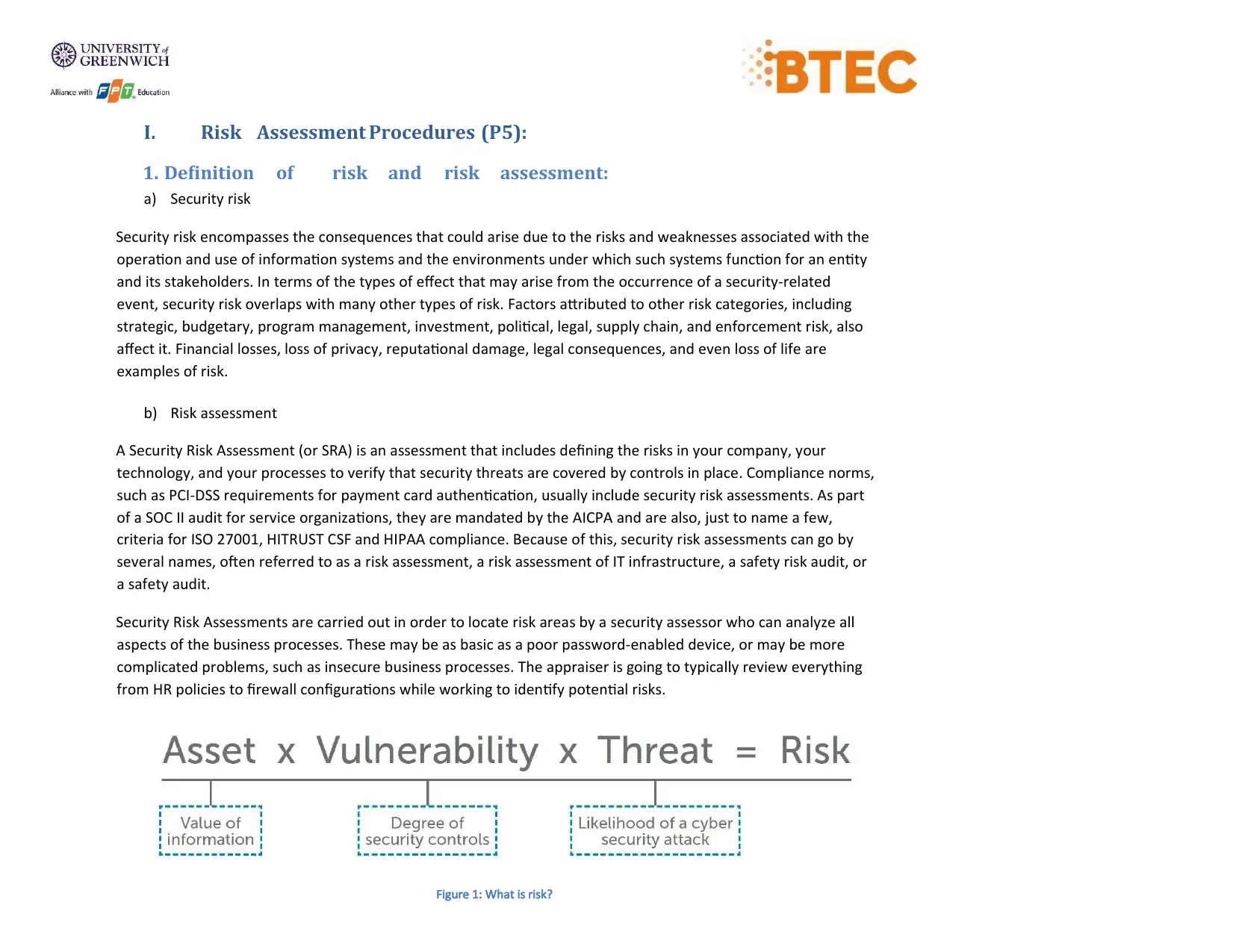
Figure 1: What is risk?
1. Definition of risk and risk assessment:
a) Security risk
Security risk encompasses the consequences that could arise due to the risks and weaknesses associated with the
operation and use of information systems and the environments under which such systems function for an entity
and its stakeholders. In terms of the types of effect that may arise from the occurrence of a security-related
event, security risk overlaps with many other types of risk. Factors attributed to other risk categories, including
strategic, budgetary, program management, investment, political, legal, supply chain, and enforcement risk, also
affect it. Financial losses, loss of privacy, reputational damage, legal consequences, and even loss of life are
examples of risk.
b) Risk assessment
A Security Risk Assessment (or SRA) is an assessment that includes defining the risks in your company, your
technology, and your processes to verify that security threats are covered by controls in place. Compliance norms,
such as PCI-DSS requirements for payment card authentication, usually include security risk assessments. As part
of a SOC II audit for service organizations, they are mandated by the AICPA and are also, just to name a few,
criteria for ISO 27001, HITRUST CSF and HIPAA compliance. Because of this, security risk assessments can go by
several names, often referred to as a risk assessment, a risk assessment of IT infrastructure, a safety risk audit, or
a safety audit.
Security Risk Assessments are carried out in order to locate risk areas by a security assessor who can analyze all
aspects of the business processes. These may be as basic as a poor password-enabled device, or may be more
complicated problems, such as insecure business processes. The appraiser is going to typically review everything
from HR policies to firewall configurations while working to identify potential risks.
Figure 1: What is risk?

c) How does risk assessment work?
The depth of the risk assessment models is influenced by factors such as scale, growth rate, capital, and asset
portfolio. When facing budget or time constraints, organizations may carry out generalized evaluations.
Generalized evaluation; however, do not generally include comprehensive mapping of properties, related hazards,
defined risks, effects, and control mitigation.
A more in-depth evaluation is required if generalized evaluation results do not provide adequate correlation
between these areas.
Figure 2: IT risk assessment
d) Steps to risk assessment:
There are 5 steps to risk assessment that you have to know:
Just find the details of steps in this RISK ASSESSMENT PROCEDURE (P5) in the third title before the RISK
IDENTIFICATION STEPS
1st step: Identify hazards (Anything that may cause harm)
The depth of the risk assessment models is influenced by factors such as scale, growth rate, capital, and asset
portfolio. When facing budget or time constraints, organizations may carry out generalized evaluations.
Generalized evaluation; however, do not generally include comprehensive mapping of properties, related hazards,
defined risks, effects, and control mitigation.
A more in-depth evaluation is required if generalized evaluation results do not provide adequate correlation
between these areas.
Figure 2: IT risk assessment
d) Steps to risk assessment:
There are 5 steps to risk assessment that you have to know:
Just find the details of steps in this RISK ASSESSMENT PROCEDURE (P5) in the third title before the RISK
IDENTIFICATION STEPS
1st step: Identify hazards (Anything that may cause harm)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
2nd step: Decide who might be harm and tell how
3rd step: Assess the risks and take actions
4th step: Make a record of the findings
5th step: Review risk assessment
2. Asset and threatidentification procedures:
Figure 3: Asset and threat identification
2.1. Asset and threat:
a) Definition of asset:
An asset is any data, system, or other component of the environment that supports information-related activities
in information protection, computer security, and network security. Hardware (e.g. servers and switches),
software (e.g. mission critical applications and support systems) and sensitive information are usually included in
3rd step: Assess the risks and take actions
4th step: Make a record of the findings
5th step: Review risk assessment
2. Asset and threatidentification procedures:
Figure 3: Asset and threat identification
2.1. Asset and threat:
a) Definition of asset:
An asset is any data, system, or other component of the environment that supports information-related activities
in information protection, computer security, and network security. Hardware (e.g. servers and switches),
software (e.g. mission critical applications and support systems) and sensitive information are usually included in
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
the properties. Assets should be protected against unauthorized entry, use, disclosure, modification, damage
and/or theft, resulting in the organization's loss.
b) Definition of threat:
A security threat is a possible negative behavior or event facilitated by a weakness in computer security that
resulting in an unintended effect on a computer system or application.
A danger can be either a negative "intentional" event (i.e. hacking: a person cracker or a criminal organization) or
an "accidental" negative event (e.g. the possibility of a computer failure or the possibility of an event of a natural
disaster such as an earthquake, a fire, or a tornado) or a condition, ability, behavior, or event otherwise.
This is distinct from a threat actor who is a person or group that can perform the action of the threat, such as
leveraging a vulnerability to have a negative effect.
2.2. Threat identification procedures:
The method of identifying threats is a way of collecting data on possible threats that can assist management in
identifying information security risks. A systematic methodology that helps an organization to aggregate and
measure possible threats is threat modeling. Institutions should consider using threat modeling to better
understand the existence, frequency, and complexity of threats; determine the institution's vulnerability to
information security; and apply this awareness to the information security program of the institution.
The identification of threats involves the sources of threats, their capabilities, and their objectives. By giving
actions:
Identify and assess threats.
Use threat knowledge to drive risk assessment and response.
Design policies to allow immediate and consequential threats to be dealt with expeditiously.
3. Risk assessment procedure:
Risk assessment procedures are audit procedures carried out in order to gain an understanding of the
organization and its environment, including internal monitoring of the entity, to recognize and determine the risks
of material misrepresentation, whether due to fraud or mistake, at the level of the financial statements and at the
level of the related claim.
The Risk Assessment divides 5 steps:
1st step: Identify the hazards
and/or theft, resulting in the organization's loss.
b) Definition of threat:
A security threat is a possible negative behavior or event facilitated by a weakness in computer security that
resulting in an unintended effect on a computer system or application.
A danger can be either a negative "intentional" event (i.e. hacking: a person cracker or a criminal organization) or
an "accidental" negative event (e.g. the possibility of a computer failure or the possibility of an event of a natural
disaster such as an earthquake, a fire, or a tornado) or a condition, ability, behavior, or event otherwise.
This is distinct from a threat actor who is a person or group that can perform the action of the threat, such as
leveraging a vulnerability to have a negative effect.
2.2. Threat identification procedures:
The method of identifying threats is a way of collecting data on possible threats that can assist management in
identifying information security risks. A systematic methodology that helps an organization to aggregate and
measure possible threats is threat modeling. Institutions should consider using threat modeling to better
understand the existence, frequency, and complexity of threats; determine the institution's vulnerability to
information security; and apply this awareness to the information security program of the institution.
The identification of threats involves the sources of threats, their capabilities, and their objectives. By giving
actions:
Identify and assess threats.
Use threat knowledge to drive risk assessment and response.
Design policies to allow immediate and consequential threats to be dealt with expeditiously.
3. Risk assessment procedure:
Risk assessment procedures are audit procedures carried out in order to gain an understanding of the
organization and its environment, including internal monitoring of the entity, to recognize and determine the risks
of material misrepresentation, whether due to fraud or mistake, at the level of the financial statements and at the
level of the related claim.
The Risk Assessment divides 5 steps:
1st step: Identify the hazards

The first step in developing your risk assessment plan is to decide what risks are facing your employees and your
company, including:
Natural disaster
Biological hazards
Workplace accidents
Intentional acts
Technological hazards
Chemical hazards
Mental hazards
Supply chains interruption
Take a look around your workplace to see what processes or operations could potentially affect your business.
Include all facets of employment, including remote staff and tasks such as repair and maintenance that are not
routine. To assess what risks have affected your business in the past, you can also look at accident/incident
records.
2nd step: Determine who might be harmed and how
Think about how your workers could be affected by company practices or external influences when you look at
your organization. Think about who would be affected if the danger takes place with any hazard that you find in
phasing one.
3rd step: Evaluate the risks and take precautions
Now that a list of possible hazards has been compiled, you need to know how likely it is that the danger will occur
and how serious the consequences will be if that hazard happens. This assessment will help you decide where the
risk level should be minimized and which hazards you should first prioritize.
4th step: Record your findings
You are required by law to write down the risk management process if you have more than five employees in your
office. The dangers you have discovered, the persons they impact, and how you plan to minimize them should be
included in your plan. The document or the risk management plan should explain that you:
Conducted a proper check of your workspace
company, including:
Natural disaster
Biological hazards
Workplace accidents
Intentional acts
Technological hazards
Chemical hazards
Mental hazards
Supply chains interruption
Take a look around your workplace to see what processes or operations could potentially affect your business.
Include all facets of employment, including remote staff and tasks such as repair and maintenance that are not
routine. To assess what risks have affected your business in the past, you can also look at accident/incident
records.
2nd step: Determine who might be harmed and how
Think about how your workers could be affected by company practices or external influences when you look at
your organization. Think about who would be affected if the danger takes place with any hazard that you find in
phasing one.
3rd step: Evaluate the risks and take precautions
Now that a list of possible hazards has been compiled, you need to know how likely it is that the danger will occur
and how serious the consequences will be if that hazard happens. This assessment will help you decide where the
risk level should be minimized and which hazards you should first prioritize.
4th step: Record your findings
You are required by law to write down the risk management process if you have more than five employees in your
office. The dangers you have discovered, the persons they impact, and how you plan to minimize them should be
included in your plan. The document or the risk management plan should explain that you:
Conducted a proper check of your workspace
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Determined who would be affected
Controlled and dealt with obvious hazards
Initiated precautions to keep risks low
Kept your staff involved in the process
5th step: Review assessment and update if necessary
Your workplace is always changing, so your organization's threats are also changing. Each brings the risk of a new
danger as new equipment, procedures, and individuals are implemented. To keep on top of these new risks,
constantly evaluate and upgrade the risk management process.
4. Risk identification steps:
There are five core steps within the risk identification and management process. These steps include risk
identification, risk analysis, risk evaluation, risk treatment, and risk monitoring.
1st step: Risk identification
The goal of risk identification is to expose what where, where, why and how anything could affect the ability of an
organization to work. A business in central California; for example, may include the possibility of wildfire" as an
occurrence that could interfere with business operations.
2nd step: Risk analysis
This step includes determining the likelihood of a risk event occurring and the likely outcome of each event. Using
the example of the California wildfire, safety managers may determine how much rainfall has occurred in the last
12 months and the degree of harm that the organization could face if a fire occurs.
3rd step: Risk evaluation
Risk evaluation compares and rates the severity of each risk according to prominence and consequences. For
example, it is possible to balance the effects of a possible wildfire against the effects of a possible mudslide. It will
rank higher regardless of which event is calculated to have a higher likelihood of occurring and causing harm.
4th step: Risk treatment
Risk treatment is often referred to as Preparation for risk response. Risk reduction techniques, preventive
treatment, and contingency measures are built in this process based on the measured importance of each risk.
Risk managers can opt to house additional network servers offsite, using the wildfire example, so business
Controlled and dealt with obvious hazards
Initiated precautions to keep risks low
Kept your staff involved in the process
5th step: Review assessment and update if necessary
Your workplace is always changing, so your organization's threats are also changing. Each brings the risk of a new
danger as new equipment, procedures, and individuals are implemented. To keep on top of these new risks,
constantly evaluate and upgrade the risk management process.
4. Risk identification steps:
There are five core steps within the risk identification and management process. These steps include risk
identification, risk analysis, risk evaluation, risk treatment, and risk monitoring.
1st step: Risk identification
The goal of risk identification is to expose what where, where, why and how anything could affect the ability of an
organization to work. A business in central California; for example, may include the possibility of wildfire" as an
occurrence that could interfere with business operations.
2nd step: Risk analysis
This step includes determining the likelihood of a risk event occurring and the likely outcome of each event. Using
the example of the California wildfire, safety managers may determine how much rainfall has occurred in the last
12 months and the degree of harm that the organization could face if a fire occurs.
3rd step: Risk evaluation
Risk evaluation compares and rates the severity of each risk according to prominence and consequences. For
example, it is possible to balance the effects of a possible wildfire against the effects of a possible mudslide. It will
rank higher regardless of which event is calculated to have a higher likelihood of occurring and causing harm.
4th step: Risk treatment
Risk treatment is often referred to as Preparation for risk response. Risk reduction techniques, preventive
treatment, and contingency measures are built in this process based on the measured importance of each risk.
Risk managers can opt to house additional network servers offsite, using the wildfire example, so business
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
operations may still continue if an onsite server is destroyed. Evacuation plans for staff can also be created by the
risk manager.
5th: Risk monitoring
Risk management is a non-stop process which, over time, adapts and changes. It will help to ensure optimum
coverage of known and unknown threats by repeating and constantly tracking the processes.
II. Data protection processes and regulations as applicable to an
organization (P6):
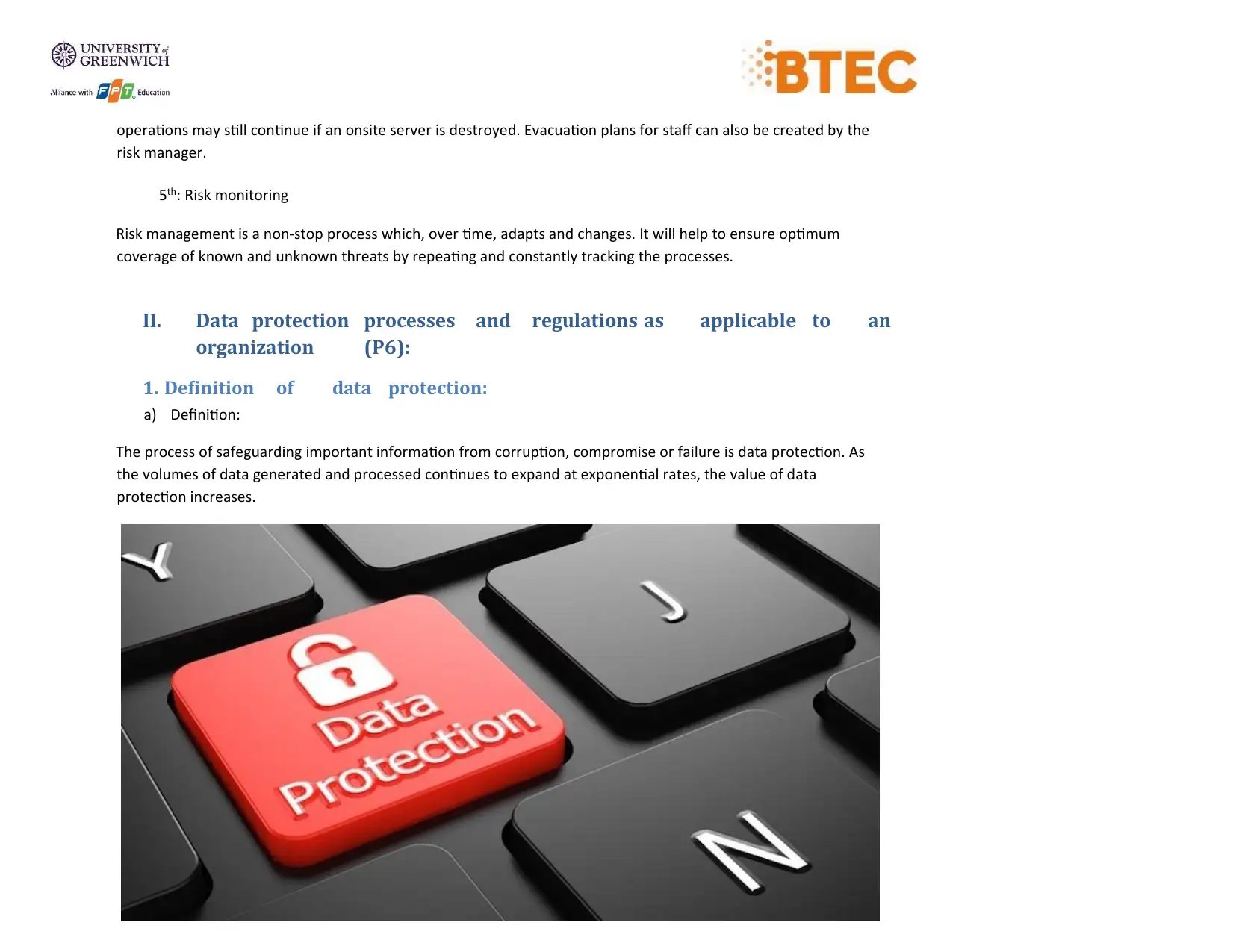
1. Definition of data protection:
a) Definition:
The process of safeguarding important information from corruption, compromise or failure is data protection. As
the volumes of data generated and processed continues to expand at exponential rates, the value of data
protection increases.
risk manager.
5th: Risk monitoring
Risk management is a non-stop process which, over time, adapts and changes. It will help to ensure optimum
coverage of known and unknown threats by repeating and constantly tracking the processes.
II. Data protection processes and regulations as applicable to an
organization (P6):
1. Definition of data protection:
a) Definition:
The process of safeguarding important information from corruption, compromise or failure is data protection. As
the volumes of data generated and processed continues to expand at exponential rates, the value of data
protection increases.

Figure 4: Data protection
b) How does it works:
The Data Protection Act was designed to provide protection and set down guidelines for how to use data about
individuals. The Act of 1998 protects information or data about living persons stored on a computer or a
structured paper filing system. The fundamental way it functions is through: getting a Commissioner of
Information to follow the laws.
2. Data protection processes with relations to organization:
The Data Protection Laws grant certain rights over their personal data to individuals (known as 'data subjects')
while enforcing certain responsibilities on the organizations that process their data. The organization gathers and
processes both personal data and confidential personal data as a recruiting enterprise.
Data protection process relates to the availability and management of data:
Data availability ensures that consumers have the information they need to conduct business, even if the
information is compromised or lost.
For reporting, testing, enabling growth, analytics and other purposes, data management has come to
include seeking ways to unlock business value from otherwise dormant copies of data.
The data protection process establishes and retains a full copy of the protected data and periodically constructs
modified copy recovery points. The copy distributes the protected data as an entire backup. The points recovered
allow you to recover earlier versions of the secured data.
b) How does it works:
The Data Protection Act was designed to provide protection and set down guidelines for how to use data about
individuals. The Act of 1998 protects information or data about living persons stored on a computer or a
structured paper filing system. The fundamental way it functions is through: getting a Commissioner of
Information to follow the laws.
2. Data protection processes with relations to organization:
The Data Protection Laws grant certain rights over their personal data to individuals (known as 'data subjects')
while enforcing certain responsibilities on the organizations that process their data. The organization gathers and
processes both personal data and confidential personal data as a recruiting enterprise.
Data protection process relates to the availability and management of data:
Data availability ensures that consumers have the information they need to conduct business, even if the
information is compromised or lost.
For reporting, testing, enabling growth, analytics and other purposes, data management has come to
include seeking ways to unlock business value from otherwise dormant copies of data.
The data protection process establishes and retains a full copy of the protected data and periodically constructs
modified copy recovery points. The copy distributes the protected data as an entire backup. The points recovered
allow you to recover earlier versions of the secured data.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 46
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





