Risk Treatment and Implementation Plan: A Comprehensive Analysis
VerifiedAdded on 2023/06/10
|5
|523
|106
Report
AI Summary
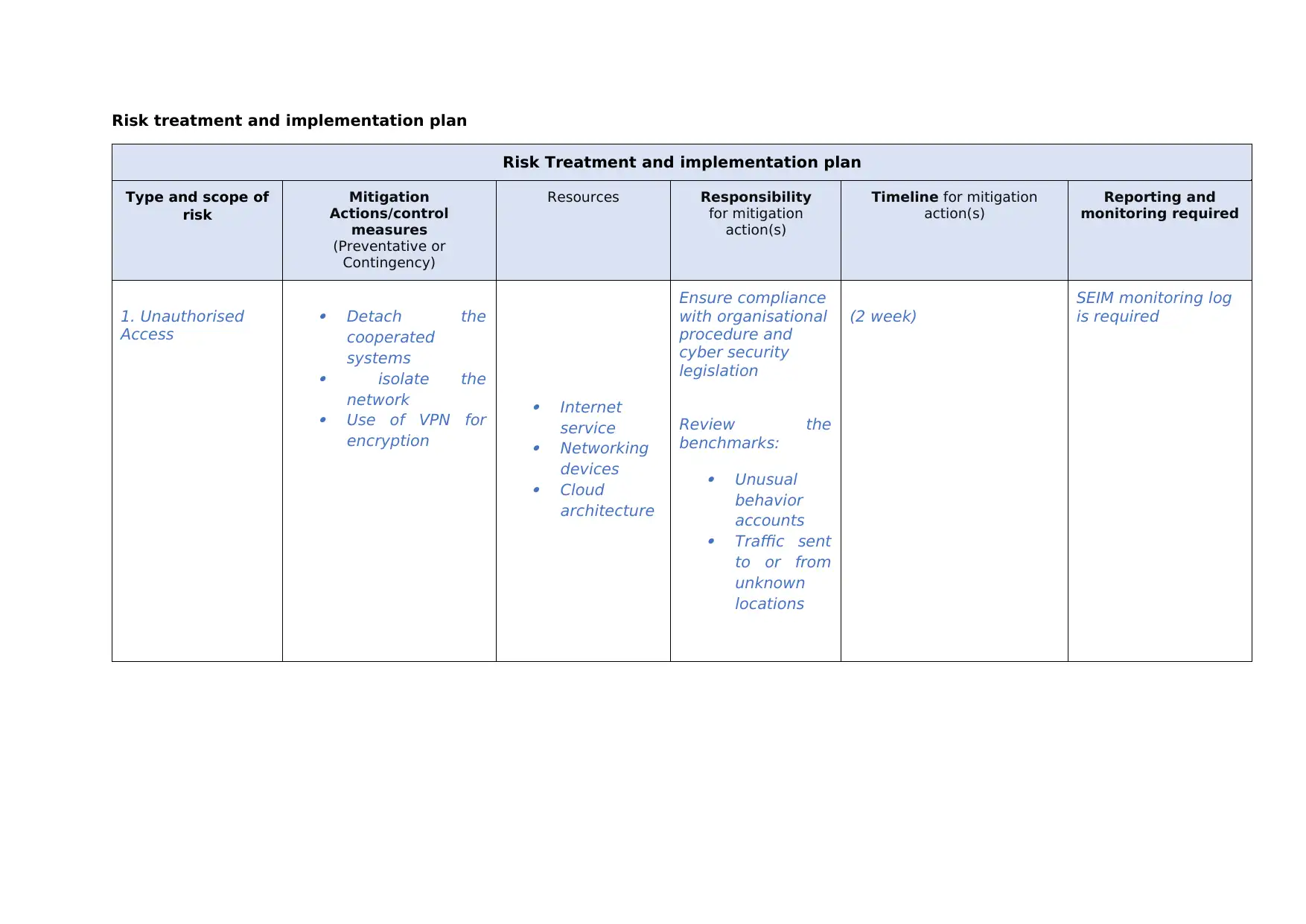
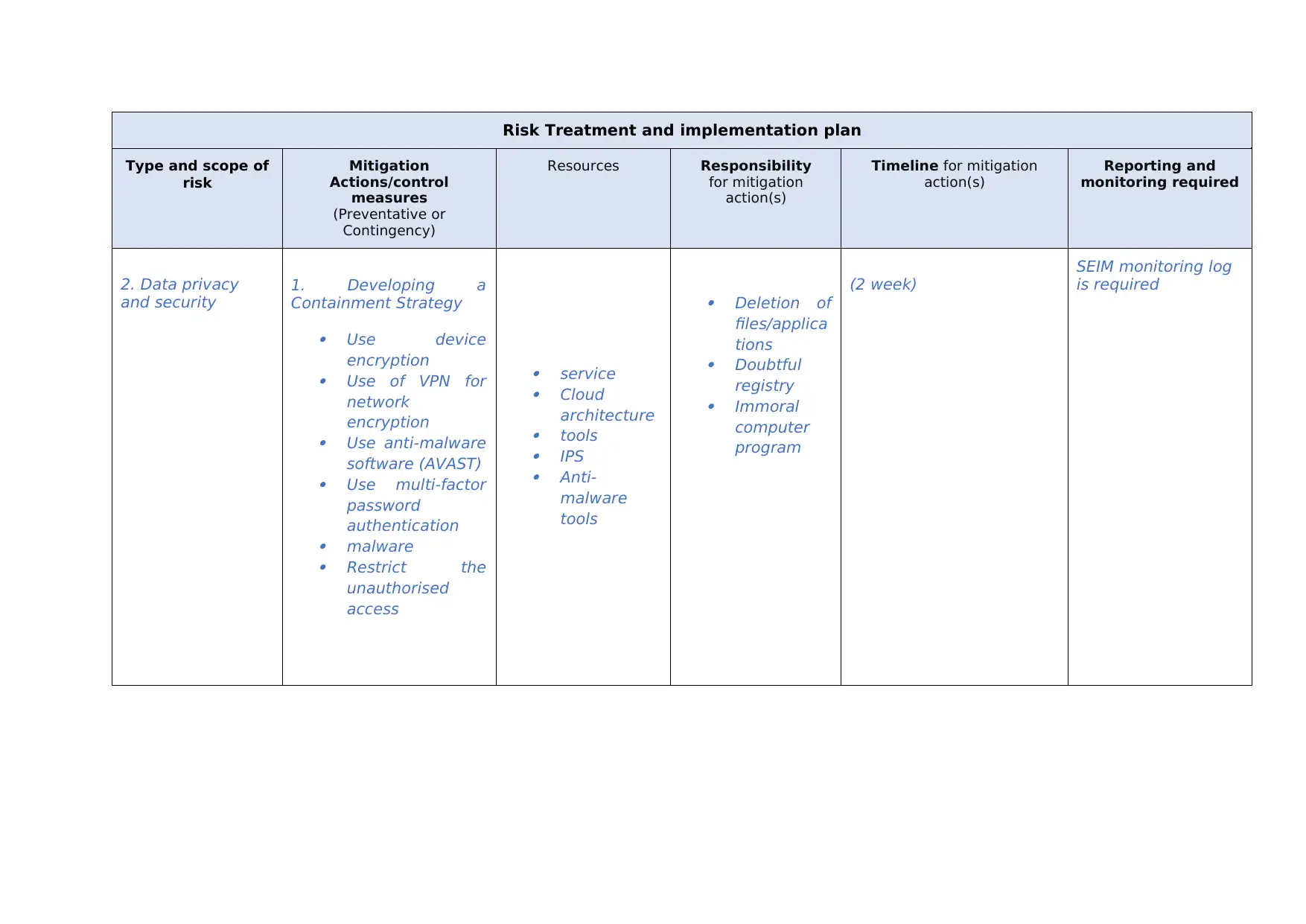
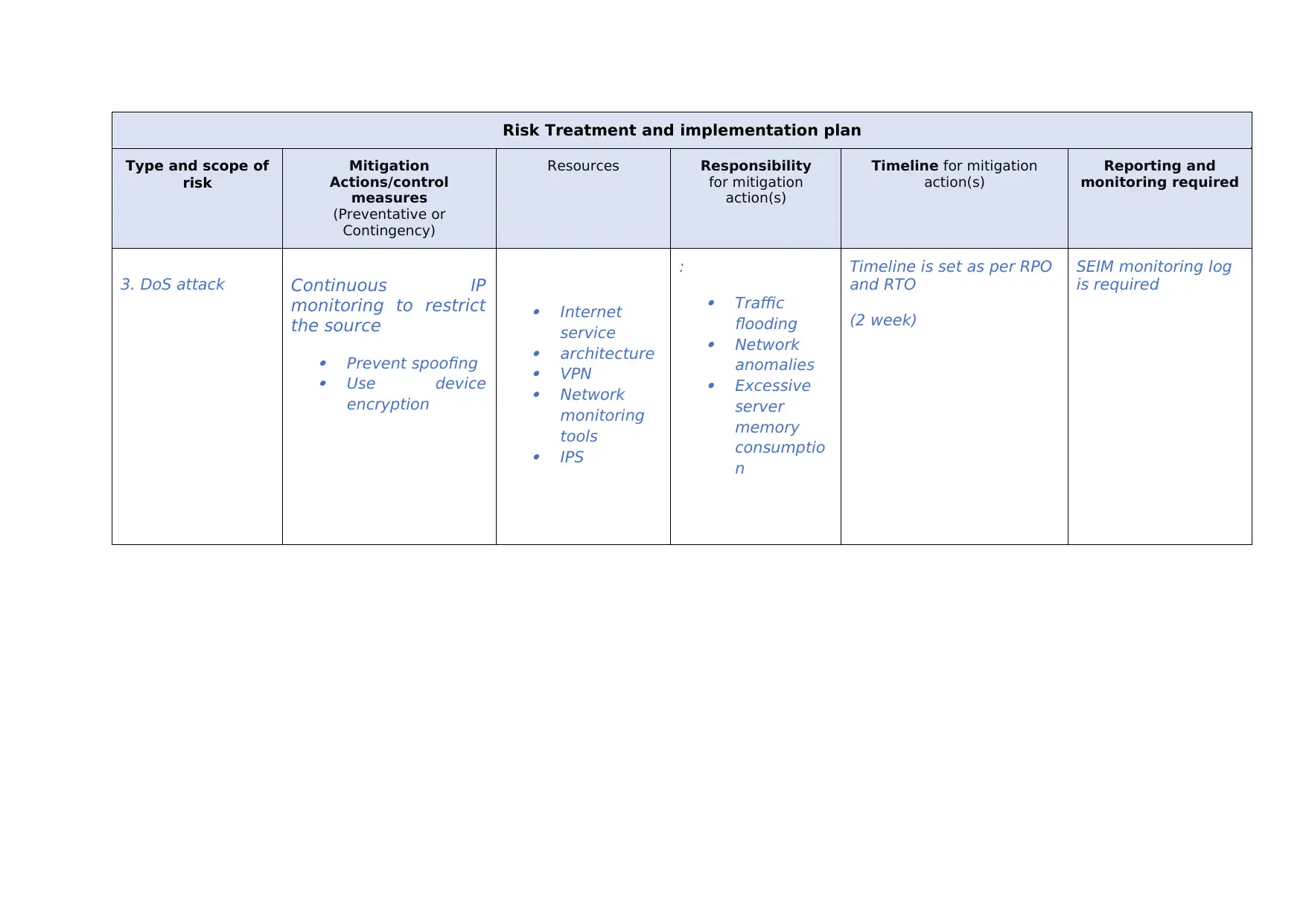
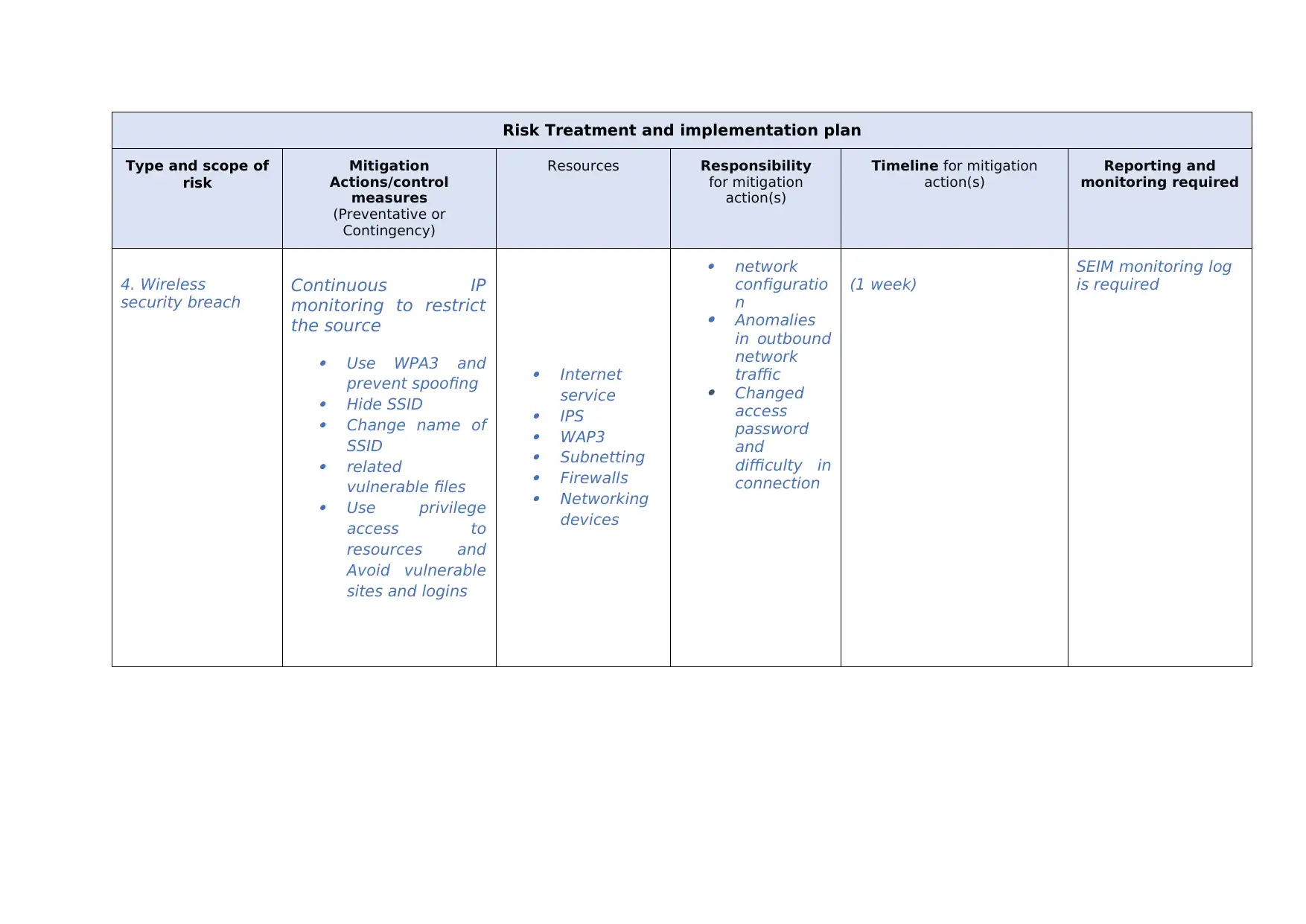
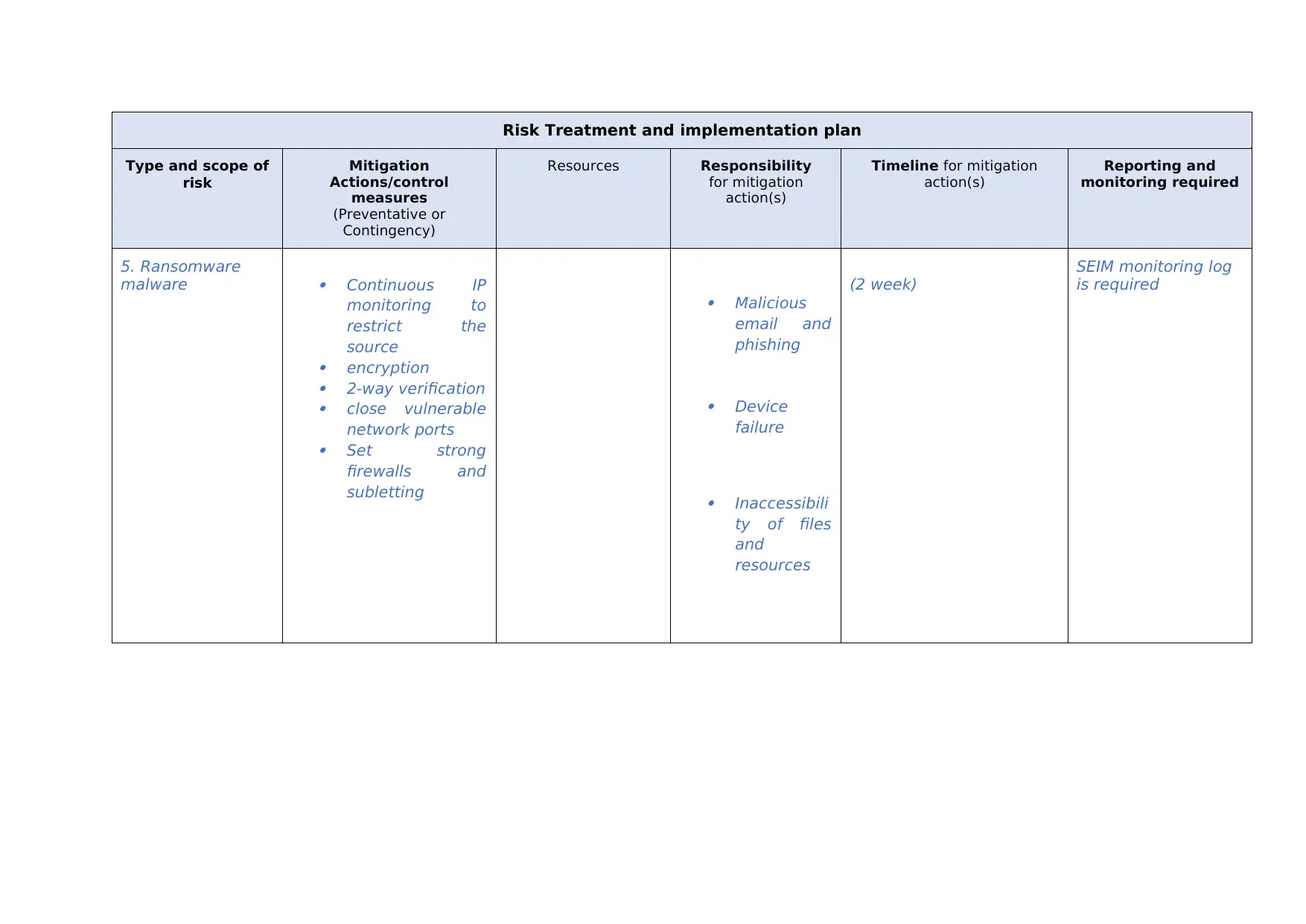
This report presents a risk treatment and implementation plan, outlining strategies to address various cybersecurity threats. It covers several types of risks, including unauthorized access, data privacy breaches, DoS attacks, wireless security vulnerabilities, and ransomware. For each risk, the report details mitigation actions, including the use of encryption, anti-malware software, and network monitoring tools. It also identifies responsible parties, required resources, and timelines for implementation. The report emphasizes the importance of continuous monitoring, the use of firewalls, and the implementation of strong security protocols to safeguard against potential threats, ensuring the confidentiality, integrity, and availability of data and systems.
1 out of 5



![[object Object]](/_next/static/media/star-bottom.7253800d.svg)