Information Systems Fundamentals: Social Media Risks in Healthcare
VerifiedAdded on 2022/08/19
|10
|2297
|18
Report
AI Summary
This research report, submitted as part of the Information Systems Fundamentals course (BN110), investigates the risks associated with social media technologies (SMT) within the healthcare industry. The report begins with an overview of private medical practices and the integration of SMT like Facebook, YouTube, and Twitter, highlighting potential privacy concerns. It identifies key risks such as poor-quality information, data breaches, and human errors, providing a risk assessment table to evaluate severity, likelihood, and mitigation strategies. The report discusses examples of real-world security breaches, including incidents at Hollywood Presbyterian Medical Center, Kalispell Regional Healthcare, and University of Washington Medicine. It concludes with a discussion on various encryption techniques, security policies, and employee training programs to address these risks. The report emphasizes the importance of risk assessment tables to identify and manage threats, ultimately offering practical solutions for improving data security within healthcare organizations.
Running head: RISKS IN SOCIAL MEDIA
Assessment Cover Sheet
BN110 Student Declaration
I declare that:
1. the work contained in this assignment is my own work, except where
acknowledgement of sources is made;
2. certify that this assessment has not been submitted previously for academic credit in
this or any other course;
3. I have read the MIT’s Plagiarism and Academic Misconduct Policy Procedure, and I
understand the consequences of engaging in plagiarism;
I have not plagiarized the work of others or participated in unauthorized collaboration when
preparing this assignment.
MIT ID: Signature: Date:
Executive Summary
Student ID Number: Student Surname: Given name:
Course: Bachelor of Networking, Bachelor of Business School of IT and Engineering
Unit code: BN110 Unit title: Information Systems Fundamentals (Assignment 2)
Due date: Date submitted: Campus: Sydney/Melbourne
Lecturer: Tutor:
Assessment Cover Sheet
BN110 Student Declaration
I declare that:
1. the work contained in this assignment is my own work, except where
acknowledgement of sources is made;
2. certify that this assessment has not been submitted previously for academic credit in
this or any other course;
3. I have read the MIT’s Plagiarism and Academic Misconduct Policy Procedure, and I
understand the consequences of engaging in plagiarism;
I have not plagiarized the work of others or participated in unauthorized collaboration when
preparing this assignment.
MIT ID: Signature: Date:
Executive Summary
Student ID Number: Student Surname: Given name:
Course: Bachelor of Networking, Bachelor of Business School of IT and Engineering
Unit code: BN110 Unit title: Information Systems Fundamentals (Assignment 2)
Due date: Date submitted: Campus: Sydney/Melbourne
Lecturer: Tutor:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1RISKS IN SOCIAL MEDIA
Growth and development of the healthcare industries depends hugely on the protection of the
organizational data as well as the sensitive data. These data are some sometimes compromised by
social engineers for their personal benefit. There are numerous categories of data which are
circulated across diverse business units of a healthcare industry. This research report shall be
identifying the few of the threats which occurs due to the deployment of SMT like Facebook. Risk
Assessment table will be an integral part of this report which will be identifying the contingency plan
of each of the identified risks. The report will be concluding with the examples of the key risks.
Growth and development of the healthcare industries depends hugely on the protection of the
organizational data as well as the sensitive data. These data are some sometimes compromised by
social engineers for their personal benefit. There are numerous categories of data which are
circulated across diverse business units of a healthcare industry. This research report shall be
identifying the few of the threats which occurs due to the deployment of SMT like Facebook. Risk
Assessment table will be an integral part of this report which will be identifying the contingency plan
of each of the identified risks. The report will be concluding with the examples of the key risks.

2RISKS IN SOCIAL MEDIA
Table of Contents
1. Introduction.......................................................................................................................................3
2.1 Overview of private medical practise..............................................................................................3
2.2 Social media risk in medical practise...............................................................................................3
2.3 Evaluation of social media risk in medical practise..........................................................................3
2.4 Risks assessment table....................................................................................................................4
3.1 Discussion of key risks.....................................................................................................................5
3.2 Supporting discussion......................................................................................................................6
4. Conclusion.........................................................................................................................................6
5. Reference..........................................................................................................................................8
Table of Contents
1. Introduction.......................................................................................................................................3
2.1 Overview of private medical practise..............................................................................................3
2.2 Social media risk in medical practise...............................................................................................3
2.3 Evaluation of social media risk in medical practise..........................................................................3
2.4 Risks assessment table....................................................................................................................4
3.1 Discussion of key risks.....................................................................................................................5
3.2 Supporting discussion......................................................................................................................6
4. Conclusion.........................................................................................................................................6
5. Reference..........................................................................................................................................8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3RISKS IN SOCIAL MEDIA
1. Introduction
Risk assessment can be defined as the procedure by which risks can be identified in a project
or a business [4]. This technique is very much useful for the creation of the risk mitigation strategy
for numerous risks. There are diverse categories of Social Media Technologies (SMT) which are used
across the health care organizations such as YouTube, Facebook and Twitter [5]. Considering the use
of these SMT it can be said that there are numerous privacy concerns related with each of these
technologies such as maintaining the security of the medical health records, and violation of the
federal law.
The notable determination of this research report is to focus on the assessment of risks
which occurs due to the use of SMT across the healthcare organizations of Australia. The report will
be having numerous sections such as the risk assessment table. and each one of them will be very
much beneficial to understand the exact contingency plan which required to be taken in order to
deal with the identified risks.
2.1 Overview of private medical practise
In most of the healthcare organizations in Australia there are diverse categories of clinical
data which travels from one department to another using social media platforms such as the
electronic health records, administrative data, and clinical trials data [6]. The use of SMT is very
much significant across the healthcare organizations in Australia as it helps them to identify new
opportunities of their existing systems, build a connection with the consumers, developing
credibility.
2.2 Social media risk in medical practise
The risks coming from SMT across the healthcare organizations in Australia includes
distribution of poor quality information, breaches of business data and licensing issues [7]. The other
risk includes the human errors, imposter accounts and unsecured mobile phones. There are other
reasons behind the security issues of SMTs such as the lack of effective training sessions.
2.3 Evaluation of social media risk in medical practise
Poor quality information has a reputation impact on the healthcare industries of Australia as
the net profitability of this business depends upon the quality of data which are transferred across
each business units. Breaches of business data can have impact on the customer base of these
healthcare industries [12]. The degree of competencies of the healthcare industries depends upon
1. Introduction
Risk assessment can be defined as the procedure by which risks can be identified in a project
or a business [4]. This technique is very much useful for the creation of the risk mitigation strategy
for numerous risks. There are diverse categories of Social Media Technologies (SMT) which are used
across the health care organizations such as YouTube, Facebook and Twitter [5]. Considering the use
of these SMT it can be said that there are numerous privacy concerns related with each of these
technologies such as maintaining the security of the medical health records, and violation of the
federal law.
The notable determination of this research report is to focus on the assessment of risks
which occurs due to the use of SMT across the healthcare organizations of Australia. The report will
be having numerous sections such as the risk assessment table. and each one of them will be very
much beneficial to understand the exact contingency plan which required to be taken in order to
deal with the identified risks.
2.1 Overview of private medical practise
In most of the healthcare organizations in Australia there are diverse categories of clinical
data which travels from one department to another using social media platforms such as the
electronic health records, administrative data, and clinical trials data [6]. The use of SMT is very
much significant across the healthcare organizations in Australia as it helps them to identify new
opportunities of their existing systems, build a connection with the consumers, developing
credibility.
2.2 Social media risk in medical practise
The risks coming from SMT across the healthcare organizations in Australia includes
distribution of poor quality information, breaches of business data and licensing issues [7]. The other
risk includes the human errors, imposter accounts and unsecured mobile phones. There are other
reasons behind the security issues of SMTs such as the lack of effective training sessions.
2.3 Evaluation of social media risk in medical practise
Poor quality information has a reputation impact on the healthcare industries of Australia as
the net profitability of this business depends upon the quality of data which are transferred across
each business units. Breaches of business data can have impact on the customer base of these
healthcare industries [12]. The degree of competencies of the healthcare industries depends upon
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4RISKS IN SOCIAL MEDIA
its ability to deal with the licensing issues. Human error can be lead to serious accidents both in the
operation theatres and the research laboratories. Healthcare organizations in Australia faces huge
amount of threat due to presence of imposter accounts. Unsecured mobile devices which are
deployed in the business environment of the healthcare can lead to unintentional data leakage and
network spoofing.
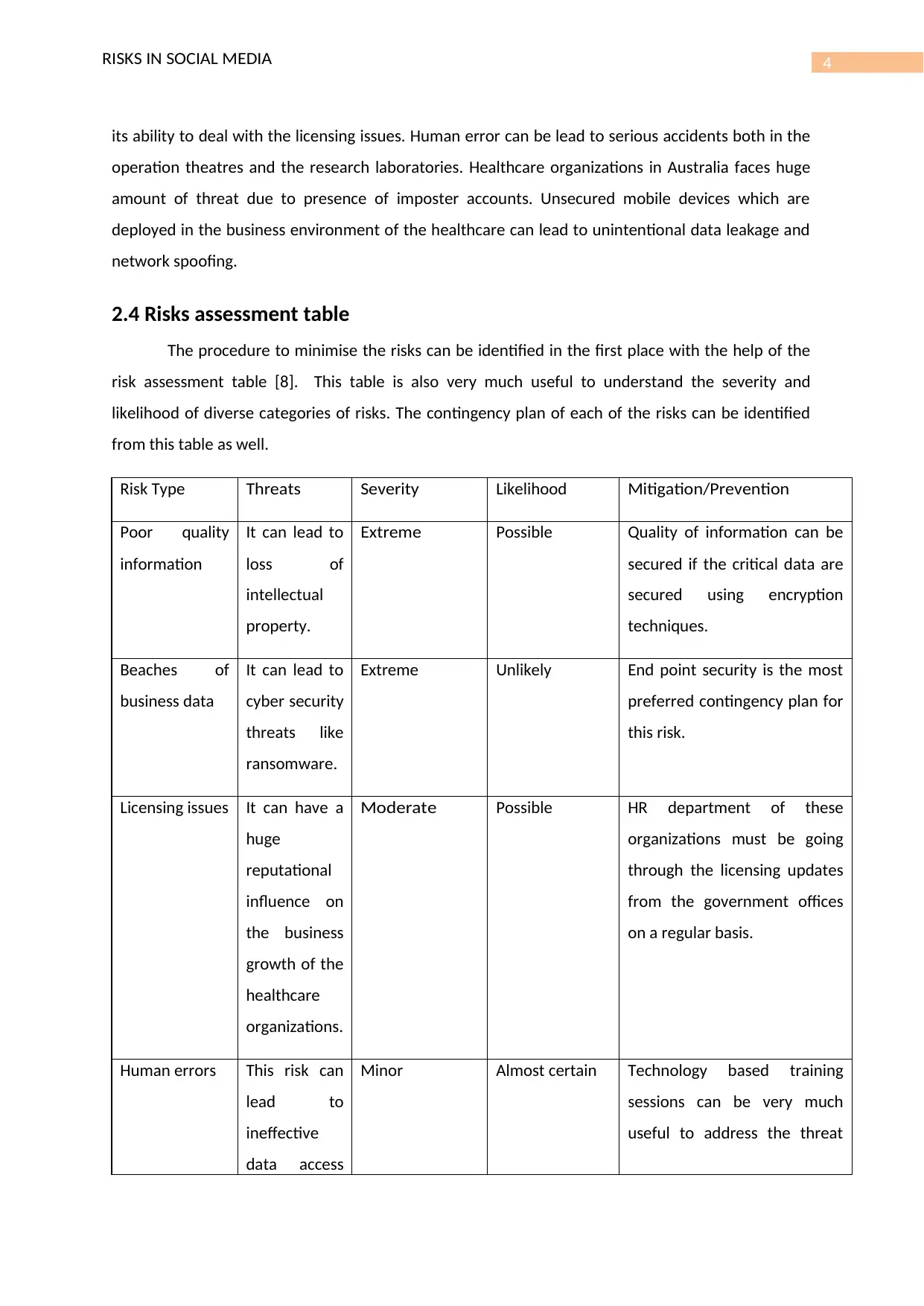
2.4 Risks assessment table
The procedure to minimise the risks can be identified in the first place with the help of the
risk assessment table [8]. This table is also very much useful to understand the severity and
likelihood of diverse categories of risks. The contingency plan of each of the risks can be identified
from this table as well.
Risk Type Threats Severity Likelihood Mitigation/Prevention
Poor quality
information
It can lead to
loss of
intellectual
property.
Extreme Possible Quality of information can be
secured if the critical data are
secured using encryption
techniques.
Beaches of
business data
It can lead to
cyber security
threats like
ransomware.
Extreme Unlikely End point security is the most
preferred contingency plan for
this risk.
Licensing issues It can have a
huge
reputational
influence on
the business
growth of the
healthcare
organizations.
Moderate Possible HR department of these
organizations must be going
through the licensing updates
from the government offices
on a regular basis.
Human errors This risk can
lead to
ineffective
data access
Minor Almost certain Technology based training
sessions can be very much
useful to address the threat
its ability to deal with the licensing issues. Human error can be lead to serious accidents both in the
operation theatres and the research laboratories. Healthcare organizations in Australia faces huge
amount of threat due to presence of imposter accounts. Unsecured mobile devices which are
deployed in the business environment of the healthcare can lead to unintentional data leakage and
network spoofing.
2.4 Risks assessment table
The procedure to minimise the risks can be identified in the first place with the help of the
risk assessment table [8]. This table is also very much useful to understand the severity and
likelihood of diverse categories of risks. The contingency plan of each of the risks can be identified
from this table as well.
Risk Type Threats Severity Likelihood Mitigation/Prevention
Poor quality
information
It can lead to
loss of
intellectual
property.
Extreme Possible Quality of information can be
secured if the critical data are
secured using encryption
techniques.
Beaches of
business data
It can lead to
cyber security
threats like
ransomware.
Extreme Unlikely End point security is the most
preferred contingency plan for
this risk.
Licensing issues It can have a
huge
reputational
influence on
the business
growth of the
healthcare
organizations.
Moderate Possible HR department of these
organizations must be going
through the licensing updates
from the government offices
on a regular basis.
Human errors This risk can
lead to
ineffective
data access
Minor Almost certain Technology based training
sessions can be very much
useful to address the threat
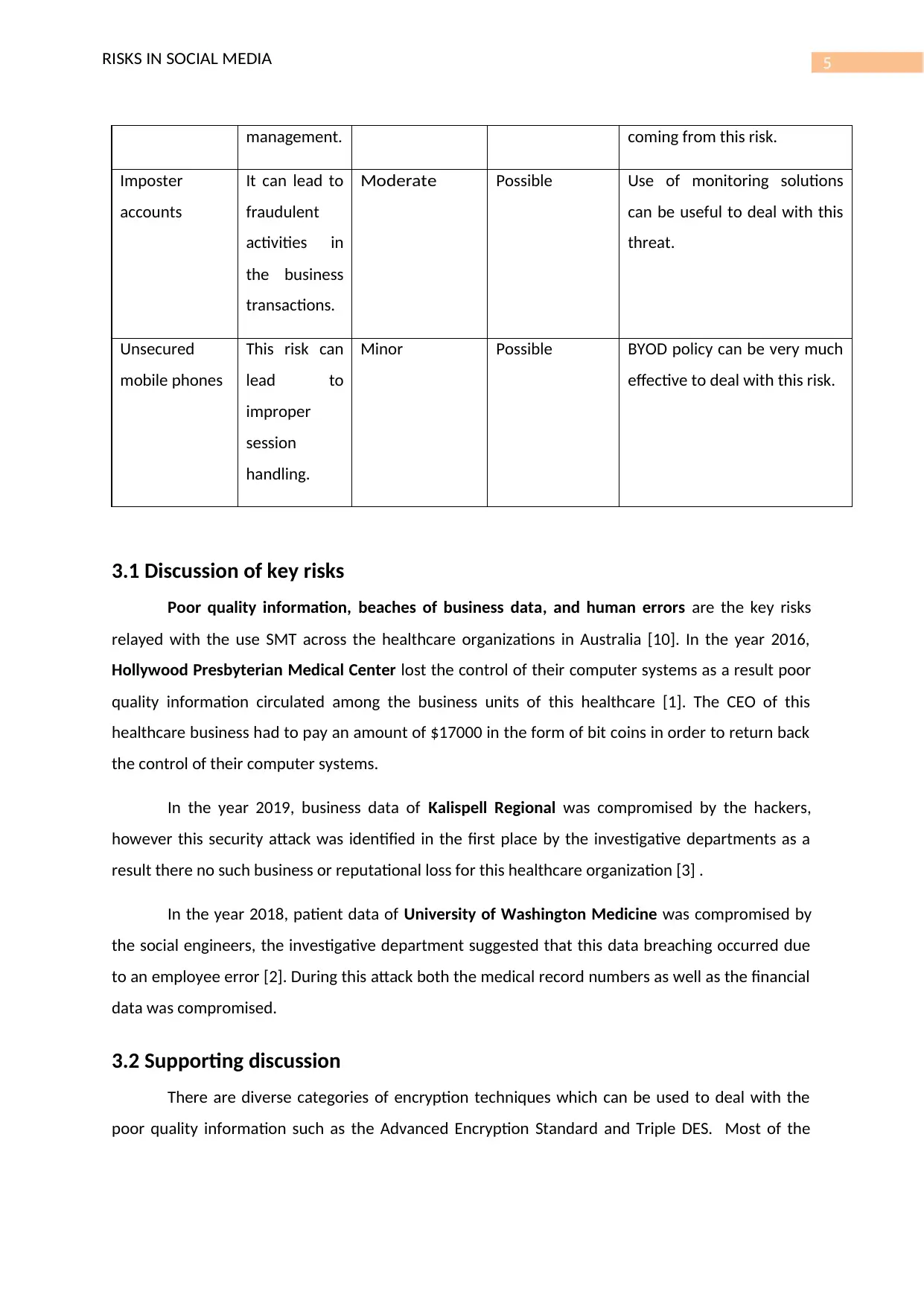
5RISKS IN SOCIAL MEDIA
management. coming from this risk.
Imposter
accounts
It can lead to
fraudulent
activities in
the business
transactions.
Moderate Possible Use of monitoring solutions
can be useful to deal with this
threat.
Unsecured
mobile phones
This risk can
lead to
improper
session
handling.
Minor Possible BYOD policy can be very much
effective to deal with this risk.
3.1 Discussion of key risks
Poor quality information, beaches of business data, and human errors are the key risks
relayed with the use SMT across the healthcare organizations in Australia [10]. In the year 2016,
Hollywood Presbyterian Medical Center lost the control of their computer systems as a result poor
quality information circulated among the business units of this healthcare [1]. The CEO of this
healthcare business had to pay an amount of $17000 in the form of bit coins in order to return back
the control of their computer systems.
In the year 2019, business data of Kalispell Regional was compromised by the hackers,
however this security attack was identified in the first place by the investigative departments as a
result there no such business or reputational loss for this healthcare organization [3] .
In the year 2018, patient data of University of Washington Medicine was compromised by
the social engineers, the investigative department suggested that this data breaching occurred due
to an employee error [2]. During this attack both the medical record numbers as well as the financial
data was compromised.
3.2 Supporting discussion
There are diverse categories of encryption techniques which can be used to deal with the
poor quality information such as the Advanced Encryption Standard and Triple DES. Most of the
management. coming from this risk.
Imposter
accounts
It can lead to
fraudulent
activities in
the business
transactions.
Moderate Possible Use of monitoring solutions
can be useful to deal with this
threat.
Unsecured
mobile phones
This risk can
lead to
improper
session
handling.
Minor Possible BYOD policy can be very much
effective to deal with this risk.
3.1 Discussion of key risks
Poor quality information, beaches of business data, and human errors are the key risks
relayed with the use SMT across the healthcare organizations in Australia [10]. In the year 2016,
Hollywood Presbyterian Medical Center lost the control of their computer systems as a result poor
quality information circulated among the business units of this healthcare [1]. The CEO of this
healthcare business had to pay an amount of $17000 in the form of bit coins in order to return back
the control of their computer systems.
In the year 2019, business data of Kalispell Regional was compromised by the hackers,
however this security attack was identified in the first place by the investigative departments as a
result there no such business or reputational loss for this healthcare organization [3] .
In the year 2018, patient data of University of Washington Medicine was compromised by
the social engineers, the investigative department suggested that this data breaching occurred due
to an employee error [2]. During this attack both the medical record numbers as well as the financial
data was compromised.
3.2 Supporting discussion
There are diverse categories of encryption techniques which can be used to deal with the
poor quality information such as the Advanced Encryption Standard and Triple DES. Most of the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6RISKS IN SOCIAL MEDIA
sensitive data of healthcare organizations can be secured in the first place using different encryption
techniques.
The security of the business data can be maintained in the first place with the help of the
email encryption method. On the other hand, it can also be said that the establishment of the
security policy is beneficial to deal with the security glitches which can lead to data security attacks
[9]. Effective training sessions can also be beneficial to deal with the data security threats.
Creation of a right work culture and making the employees understand the significance of
data security can be convenient to minimise the data security threats coming the employees [10].
The creation of a governance plan is the other way to address the threats coming from the
employees of an organization.
4. Conclusion
Risk assessment is practised to deal with the security issues of a commercial establishment
or a business. The SMT’s which are used in the healthcare organizations of Australia are YouTube,
Twitter and Facebook. There are diverse categories of data which ate circulated in the business units
of healthcare organisations such as the financial data and the electronic health records. The
circulation of each of these essential data can lead to security risks such as distribution of poor
quality information, licensing issues mode and breaches of business data. Risk assessment table can
be very much useful to identify the severity and likelihood of each of the risks of the healthcare
organizations of Australia. The risk of poor quality information can be prevented using encryption
methods such as Triple DES, breaches of business data can be secured using end point security, most
of the licensing issues can be resolved using the pro-activeness of the HR departments of
commercial establishments. Technology based training sessions can be very much useful to deal with
the human errors which causes ineffective data access management. The risk coming from the
imposter accounts which are created using SMT can be addressed using monitoring solutions.
The threats coming from the unsecured mobile devices can be resolved in the first place
with the help of the BYOD policy. The research report highlights few examples of security breaches
which occurred due to lack of effective security measures such as the data security attack of
Hollywood Presbyterian Medical Center which occurred in the year 2016. Business data of Kalispell
Regional was compromised in the year 2019 by the hackers; however, there were no such business
or reputational loss due to this security attack. Sensitive data from University of Washington
Medicine was compromised due to the threats coming from the inside the organization. Thus, this
research report was very much useful to understand the significance of risk assessment table which
sensitive data of healthcare organizations can be secured in the first place using different encryption
techniques.
The security of the business data can be maintained in the first place with the help of the
email encryption method. On the other hand, it can also be said that the establishment of the
security policy is beneficial to deal with the security glitches which can lead to data security attacks
[9]. Effective training sessions can also be beneficial to deal with the data security threats.
Creation of a right work culture and making the employees understand the significance of
data security can be convenient to minimise the data security threats coming the employees [10].
The creation of a governance plan is the other way to address the threats coming from the
employees of an organization.
4. Conclusion
Risk assessment is practised to deal with the security issues of a commercial establishment
or a business. The SMT’s which are used in the healthcare organizations of Australia are YouTube,
Twitter and Facebook. There are diverse categories of data which ate circulated in the business units
of healthcare organisations such as the financial data and the electronic health records. The
circulation of each of these essential data can lead to security risks such as distribution of poor
quality information, licensing issues mode and breaches of business data. Risk assessment table can
be very much useful to identify the severity and likelihood of each of the risks of the healthcare
organizations of Australia. The risk of poor quality information can be prevented using encryption
methods such as Triple DES, breaches of business data can be secured using end point security, most
of the licensing issues can be resolved using the pro-activeness of the HR departments of
commercial establishments. Technology based training sessions can be very much useful to deal with
the human errors which causes ineffective data access management. The risk coming from the
imposter accounts which are created using SMT can be addressed using monitoring solutions.
The threats coming from the unsecured mobile devices can be resolved in the first place
with the help of the BYOD policy. The research report highlights few examples of security breaches
which occurred due to lack of effective security measures such as the data security attack of
Hollywood Presbyterian Medical Center which occurred in the year 2016. Business data of Kalispell
Regional was compromised in the year 2019 by the hackers; however, there were no such business
or reputational loss due to this security attack. Sensitive data from University of Washington
Medicine was compromised due to the threats coming from the inside the organization. Thus, this
research report was very much useful to understand the significance of risk assessment table which
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7RISKS IN SOCIAL MEDIA
are used to identify risks coming from the use of SMT across the healthcare establishments in
Australia.
are used to identify risks coming from the use of SMT across the healthcare establishments in
Australia.

8RISKS IN SOCIAL MEDIA
5. Reference
[1]"Hollywood hospital pays $17,000 in bitcoin to hackers; FBI investigating", Los Angeles Times,
2020. [Online]. Available: https://www.latimes.com/business/technology/la-me-ln-hollywood-
hospital-bitcoin-20160217-story.html. [Accessed: 28- Jan- 2020].
[2]"Health Data of 974,000 UW Medicine Patients Exposed for 3 Weeks", HealthITSecurity, 2020.
[Online]. Available: https://healthitsecurity.com/news/health-data-of-974000-uw-medicine-
patients-exposed-for-3-weeks. [Accessed: 28- Jan- 2020].
[3]"Kalispell Regional Healthcare reports data breach", KPAX, 2020. [Online]. Available:
https://www.kpax.com/news/community/vista-semanal/local/kalispell-regional-healthcare-reports-
data-breach. [Accessed: 28- Jan- 2020].
[4]"Social Media Policy Template - GPSA - GP Supervisors Australia", GPSA - GP Supervisors Australia,
2020. [Online]. Available: https://gpsupervisorsaustralia.org.au/social-media-policy-template/.
[Accessed: 28- Jan- 2020].
[5]"Medical Board of Australia - Social media: How to meet your obligations under the National
Law", Medicalboard.gov.au, 2020. [Online]. Available: https://www.medicalboard.gov.au/Codes-
Guidelines-Policies/Social-media-guidance.aspx. [Accessed: 28- Jan- 2020].
[6]"Social media", Australian Government Department of Health, 2020. [Online]. Available:
https://www.health.gov.au/using-our-websites/social-media?
utm_source=health.gov.au&utm_medium=callout-auto-
custom&utm_campaign=digital_transformation. [Accessed: 28- Jan- 2020].
[7] S.P. Williams, and V. Hausman. Categorizing the business risks of social media. Procedia computer
science, 121, pp.266-273, 2017.
[8] C. V. Baccarella, T.F. Wagner, J.H. Kietzmann, I.P. and McCarthy. Social media? It's serious!
Understanding the dark side of social media. European Management Journal, 36(4), pp.431-438,
2018
[9] I. Rodella, Madau, M. Mazzanti, C. Corbau, D. Carboni, K. Utizi, and U. Simeoni. Data for the
analysis of willingness to pay for Italian beaches. Data in brief, 23, p.103815, 2019
[10] D. Zhang. Big data security and privacy protection. In 8th International Conference on
Management and Computer Science (ICMCS 2018). Atlantis Press, 2018
5. Reference
[1]"Hollywood hospital pays $17,000 in bitcoin to hackers; FBI investigating", Los Angeles Times,
2020. [Online]. Available: https://www.latimes.com/business/technology/la-me-ln-hollywood-
hospital-bitcoin-20160217-story.html. [Accessed: 28- Jan- 2020].
[2]"Health Data of 974,000 UW Medicine Patients Exposed for 3 Weeks", HealthITSecurity, 2020.
[Online]. Available: https://healthitsecurity.com/news/health-data-of-974000-uw-medicine-
patients-exposed-for-3-weeks. [Accessed: 28- Jan- 2020].
[3]"Kalispell Regional Healthcare reports data breach", KPAX, 2020. [Online]. Available:
https://www.kpax.com/news/community/vista-semanal/local/kalispell-regional-healthcare-reports-
data-breach. [Accessed: 28- Jan- 2020].
[4]"Social Media Policy Template - GPSA - GP Supervisors Australia", GPSA - GP Supervisors Australia,
2020. [Online]. Available: https://gpsupervisorsaustralia.org.au/social-media-policy-template/.
[Accessed: 28- Jan- 2020].
[5]"Medical Board of Australia - Social media: How to meet your obligations under the National
Law", Medicalboard.gov.au, 2020. [Online]. Available: https://www.medicalboard.gov.au/Codes-
Guidelines-Policies/Social-media-guidance.aspx. [Accessed: 28- Jan- 2020].
[6]"Social media", Australian Government Department of Health, 2020. [Online]. Available:
https://www.health.gov.au/using-our-websites/social-media?
utm_source=health.gov.au&utm_medium=callout-auto-
custom&utm_campaign=digital_transformation. [Accessed: 28- Jan- 2020].
[7] S.P. Williams, and V. Hausman. Categorizing the business risks of social media. Procedia computer
science, 121, pp.266-273, 2017.
[8] C. V. Baccarella, T.F. Wagner, J.H. Kietzmann, I.P. and McCarthy. Social media? It's serious!
Understanding the dark side of social media. European Management Journal, 36(4), pp.431-438,
2018
[9] I. Rodella, Madau, M. Mazzanti, C. Corbau, D. Carboni, K. Utizi, and U. Simeoni. Data for the
analysis of willingness to pay for Italian beaches. Data in brief, 23, p.103815, 2019
[10] D. Zhang. Big data security and privacy protection. In 8th International Conference on
Management and Computer Science (ICMCS 2018). Atlantis Press, 2018
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9RISKS IN SOCIAL MEDIA
[11] C. Esposito, A. De Santis, G. Tortora, H. Chang and K.K.R. Choo. Blockchain: A panacea for
healthcare cloud-based data security and privacy?. IEEE Cloud Computing, 5(1), pp.31-37, 2018
[12] P.R. Kumar, P.H. Raj, P. and Jelciana. Exploring data security issues and solutions in cloud
computing. Procedia Computer Science, 125, pp.691-697, 2018
[11] C. Esposito, A. De Santis, G. Tortora, H. Chang and K.K.R. Choo. Blockchain: A panacea for
healthcare cloud-based data security and privacy?. IEEE Cloud Computing, 5(1), pp.31-37, 2018
[12] P.R. Kumar, P.H. Raj, P. and Jelciana. Exploring data security issues and solutions in cloud
computing. Procedia Computer Science, 125, pp.691-697, 2018
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




