Wireless Sensor Networks: Analysis of LEACH and PEGASIS Protocols
VerifiedAdded on 2022/09/22
|11
|2650
|22
Report
AI Summary
This report provides a comprehensive analysis of two prominent routing protocols used in wireless sensor networks (WSNs): LEACH (Low Energy Adaptive Clustering Hierarchy) and PEGASIS (Power-Efficient Gathering Sensor Information System). The study delves into the technical details, routing analysis, and performance metrics of each protocol, focusing on their energy efficiency and network lifetime. A significant portion of the report is dedicated to the security concerns and potential attacks that can exploit vulnerabilities within these protocols, including denial-of-service, masquerading, and eavesdropping. Furthermore, the report proposes and evaluates various mitigation strategies, such as authentication, authorization, and integrity checks using cryptography and digital certificates, to counter these attacks. A comparative analysis highlights the strengths and weaknesses of each protocol, concluding that PEGASIS generally outperforms LEACH in terms of network lifetime and energy efficiency. The report underscores the importance of selecting the appropriate routing protocol to optimize network performance and security in WSN deployments.

Computer networking and application 1
Computer networking and application
By Name
Course
Instructor
Institution
Location
Date
Computer networking and application
By Name
Course
Instructor
Institution
Location
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Computer networking and application 2
Table of Content
Introduction 2
Motivation 3
Routing protocol analysis 3
LEACH (Low Energy Adaptive Clustering Hierarchy) 3
PEGASIS (Power-Efficient Gathering Sensor Information System) 5
Feedback report 5
Security issues and attacks 7
LEACH 7
PEGASIS 7
Attack countermeasures 8
LEACH 8
PEGASIS 8
Comparative analysis 8
Conclusion 9
References 10
1. Introduction
Routing protocols are generally involved in the network process of select the best suitable path
for which the packets are supposed to use to travel from the source node to the destination node on the
network. The whole process of evaluating and selecting the best route is always a set of rules which the
Table of Content
Introduction 2
Motivation 3
Routing protocol analysis 3
LEACH (Low Energy Adaptive Clustering Hierarchy) 3
PEGASIS (Power-Efficient Gathering Sensor Information System) 5
Feedback report 5
Security issues and attacks 7
LEACH 7
PEGASIS 7
Attack countermeasures 8
LEACH 8
PEGASIS 8
Comparative analysis 8
Conclusion 9
References 10
1. Introduction
Routing protocols are generally involved in the network process of select the best suitable path
for which the packets are supposed to use to travel from the source node to the destination node on the
network. The whole process of evaluating and selecting the best route is always a set of rules which the

Computer networking and application 3
nodes use while exchanging packets on the network. This process often is marred with a lot of
challenges and difficulties since the best rout normally is a factor of network type, the medium used and
network key performance metrics. This paper details some of the protocols used in the wireless sensor
networks with more focus on the technical details of the protocols, their general routing analysis and
performance metrics, a deep dive into the security concerns and attacks that can be designed to exploit
vulnerabilities, mitigation strategies for these attacks will be among the key concepts covered. The
paper focuses mainly on the following prominent wireless sensor network
● LEACH
● PEGIS
2. Motivation
The knowledge of the underlying wireless sensor networks routing protocols is important in the
day to day life of a wireless sensor network design as the practical knowledge gained from
understanding the mechanism of the wireless sensor networks will be critical in designing networks and
applications that are efficient in terms of energy consumption. Energy shortages have always been a
major issue in the design of wireless sensor networks especially those deployed in intensive
environments such as the battlefields. This paper will provide the mechanism to make your network
efficient by choosing the best and efficient routing protocol. The complexity of a sensor network again is
a key challenge which affects the performance of the network. Through this paper, we will learn the best
protocol to choose that reduce the complexity of the network hence better performance. This key topic
among other likes robustness is deeply discussed in this paper
3. Routing protocol analysis
This section deep dives into the technical details of the two wireless routing protocols. The
analysis focus on their internal workings and the general performance rating in a different stress
environment [1].
nodes use while exchanging packets on the network. This process often is marred with a lot of
challenges and difficulties since the best rout normally is a factor of network type, the medium used and
network key performance metrics. This paper details some of the protocols used in the wireless sensor
networks with more focus on the technical details of the protocols, their general routing analysis and
performance metrics, a deep dive into the security concerns and attacks that can be designed to exploit
vulnerabilities, mitigation strategies for these attacks will be among the key concepts covered. The
paper focuses mainly on the following prominent wireless sensor network
● LEACH
● PEGIS
2. Motivation
The knowledge of the underlying wireless sensor networks routing protocols is important in the
day to day life of a wireless sensor network design as the practical knowledge gained from
understanding the mechanism of the wireless sensor networks will be critical in designing networks and
applications that are efficient in terms of energy consumption. Energy shortages have always been a
major issue in the design of wireless sensor networks especially those deployed in intensive
environments such as the battlefields. This paper will provide the mechanism to make your network
efficient by choosing the best and efficient routing protocol. The complexity of a sensor network again is
a key challenge which affects the performance of the network. Through this paper, we will learn the best
protocol to choose that reduce the complexity of the network hence better performance. This key topic
among other likes robustness is deeply discussed in this paper
3. Routing protocol analysis
This section deep dives into the technical details of the two wireless routing protocols. The
analysis focus on their internal workings and the general performance rating in a different stress
environment [1].
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Computer networking and application 4
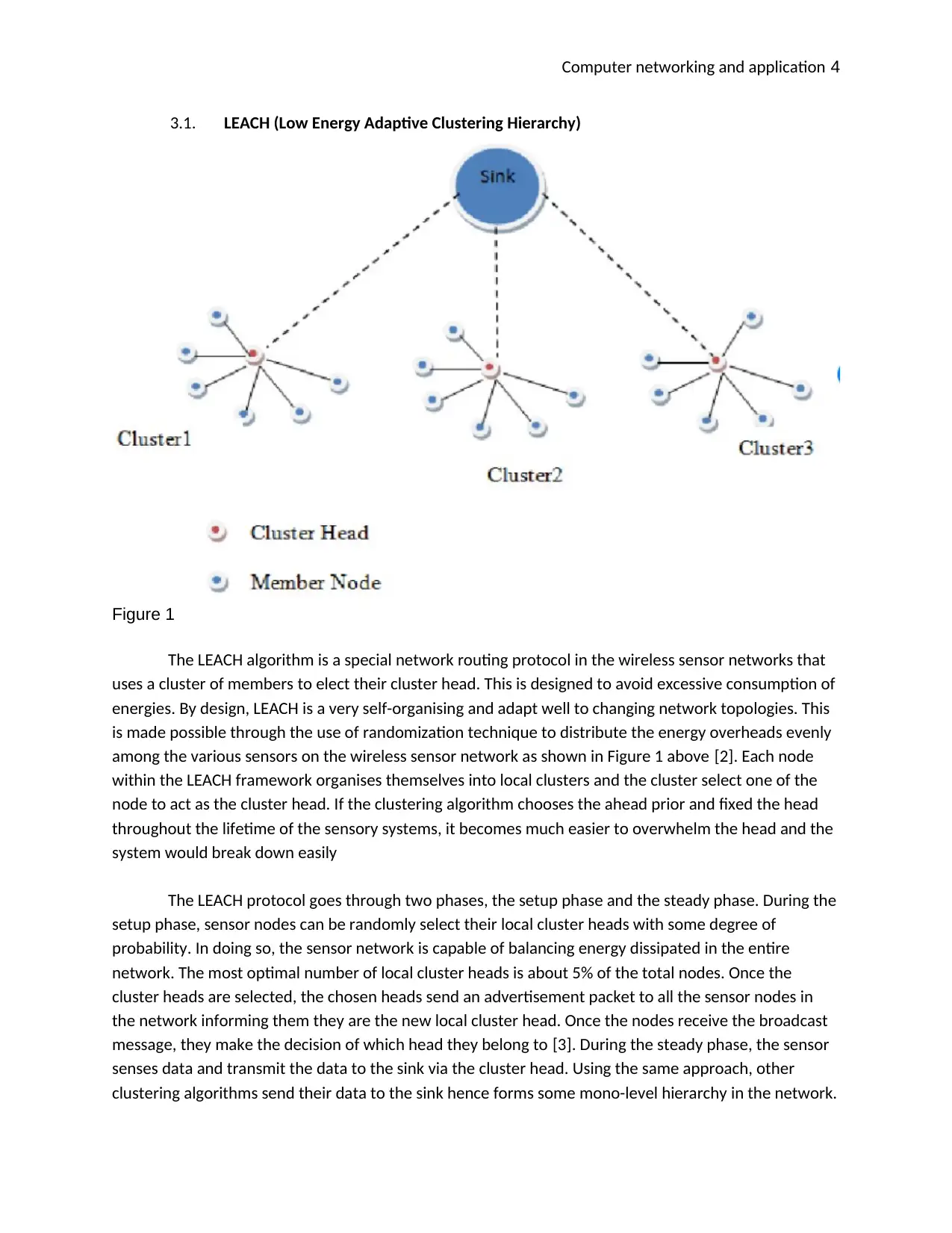
3.1. LEACH (Low Energy Adaptive Clustering Hierarchy)
Figure 1
The LEACH algorithm is a special network routing protocol in the wireless sensor networks that
uses a cluster of members to elect their cluster head. This is designed to avoid excessive consumption of
energies. By design, LEACH is a very self-organising and adapt well to changing network topologies. This
is made possible through the use of randomization technique to distribute the energy overheads evenly
among the various sensors on the wireless sensor network as shown in Figure 1 above [2]. Each node
within the LEACH framework organises themselves into local clusters and the cluster select one of the
node to act as the cluster head. If the clustering algorithm chooses the ahead prior and fixed the head
throughout the lifetime of the sensory systems, it becomes much easier to overwhelm the head and the
system would break down easily
The LEACH protocol goes through two phases, the setup phase and the steady phase. During the
setup phase, sensor nodes can be randomly select their local cluster heads with some degree of
probability. In doing so, the sensor network is capable of balancing energy dissipated in the entire
network. The most optimal number of local cluster heads is about 5% of the total nodes. Once the
cluster heads are selected, the chosen heads send an advertisement packet to all the sensor nodes in
the network informing them they are the new local cluster head. Once the nodes receive the broadcast
message, they make the decision of which head they belong to [3]. During the steady phase, the sensor
senses data and transmit the data to the sink via the cluster head. Using the same approach, other
clustering algorithms send their data to the sink hence forms some mono-level hierarchy in the network.
3.1. LEACH (Low Energy Adaptive Clustering Hierarchy)
Figure 1
The LEACH algorithm is a special network routing protocol in the wireless sensor networks that
uses a cluster of members to elect their cluster head. This is designed to avoid excessive consumption of
energies. By design, LEACH is a very self-organising and adapt well to changing network topologies. This
is made possible through the use of randomization technique to distribute the energy overheads evenly
among the various sensors on the wireless sensor network as shown in Figure 1 above [2]. Each node
within the LEACH framework organises themselves into local clusters and the cluster select one of the
node to act as the cluster head. If the clustering algorithm chooses the ahead prior and fixed the head
throughout the lifetime of the sensory systems, it becomes much easier to overwhelm the head and the
system would break down easily
The LEACH protocol goes through two phases, the setup phase and the steady phase. During the
setup phase, sensor nodes can be randomly select their local cluster heads with some degree of
probability. In doing so, the sensor network is capable of balancing energy dissipated in the entire
network. The most optimal number of local cluster heads is about 5% of the total nodes. Once the
cluster heads are selected, the chosen heads send an advertisement packet to all the sensor nodes in
the network informing them they are the new local cluster head. Once the nodes receive the broadcast
message, they make the decision of which head they belong to [3]. During the steady phase, the sensor
senses data and transmit the data to the sink via the cluster head. Using the same approach, other
clustering algorithms send their data to the sink hence forms some mono-level hierarchy in the network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Computer networking and application 5
After a given period of time elapse in the steady phase, the network is programmed to go into another
setup phase where they undergo the process of selecting the local cluster heads
LEACH uses a distributed algorithm to form a cluster in which the local nodes makes an
autonomous decision without the need of central governing control. In the formation of round r +
1(which begin at time (t) with some probability of T(n), given each sensor n select itself to be the cluster
head CH. T(n) is arrived at such that the expected number of CH for the round is k). For N nodes, the
algorithm is as shown below [4]
The probability of a node being selected CH is given below
This setup ensures all the nodes have a generally equal amount of energy, making it more efficient. The
distributed nature of the setup makes it very self-sustaining as it eliminates the central point of failure in
the network making it very robust [5]
The LEACH routing protocol rotational basis for the CH ensures no sensor is over drained in terms of
energy. The local clusters know its members hence uses TDMA to schedule transmission of data within
the cluster hence avoiding intra-cluster collisions
3.2. PEGASIS (Power-Efficient Gathering Sensor Information System)
PEGASIS is an improvement on the LEACH routing protocol by improving efficiency. The main
theme behind the PEGASIS protocol is that for each node in the network to send and receive data the
closest neighbours, the node takes a turn for being the leader for the given transmission to the base
station. During the construction of the chain, it is very likely that some nodes will have some relative
distant neighbours in the chain. Such nodes generally will use relatively more energy compared to other
sensors in the node. In an event a node dies, the chain gets reconstructed and the threshold
reconfigured to determine which of the nodes in the network can be leaders [6]
After a given period of time elapse in the steady phase, the network is programmed to go into another
setup phase where they undergo the process of selecting the local cluster heads
LEACH uses a distributed algorithm to form a cluster in which the local nodes makes an
autonomous decision without the need of central governing control. In the formation of round r +
1(which begin at time (t) with some probability of T(n), given each sensor n select itself to be the cluster
head CH. T(n) is arrived at such that the expected number of CH for the round is k). For N nodes, the
algorithm is as shown below [4]
The probability of a node being selected CH is given below
This setup ensures all the nodes have a generally equal amount of energy, making it more efficient. The
distributed nature of the setup makes it very self-sustaining as it eliminates the central point of failure in
the network making it very robust [5]
The LEACH routing protocol rotational basis for the CH ensures no sensor is over drained in terms of
energy. The local clusters know its members hence uses TDMA to schedule transmission of data within
the cluster hence avoiding intra-cluster collisions
3.2. PEGASIS (Power-Efficient Gathering Sensor Information System)
PEGASIS is an improvement on the LEACH routing protocol by improving efficiency. The main
theme behind the PEGASIS protocol is that for each node in the network to send and receive data the
closest neighbours, the node takes a turn for being the leader for the given transmission to the base
station. During the construction of the chain, it is very likely that some nodes will have some relative
distant neighbours in the chain. Such nodes generally will use relatively more energy compared to other
sensors in the node. In an event a node dies, the chain gets reconstructed and the threshold
reconfigured to determine which of the nodes in the network can be leaders [6]
Computer networking and application 6
4. Feedback report
PEGASIS is seen as an improvement on the LEACH protocol as it saves relatively much energy at
various stages. First, the distance covered in the local gatherings is much less hence energy dissipated in
relatively less compared to what would have been covered in the LEACH protocol. Second, the relative
amount of data that the leader can receive is at most 2 messages compared to 20 i.e 20 nodes per
cluster in LEACH given 100 nodes. Finally, at any transmission instance, only one base station transmits
per each round of data transfer. The aggregation of data occurs at all the various nodes in the sensory
network. This is done to pervade all the key information on the network. In the PEGASIS framework,
despite the fact that it has multiple nodes in the chain, only one of the nodes in the chain can actually
transmit data at every given instance of time. This increases the general lifespan of the network due to
turn-taking in the communication between the base station and the nodes in the chain. The PEGASIS
protocol thus reduces the required power to send the data for any given round since the energy
dissipation is spread equally among the nodes. The conservation of energy is thus achieved in PEGASIS in
the following two ways;
● The head receives at most 2 messages
● The distance covered to transmit data to the closest neighbour is much smaller
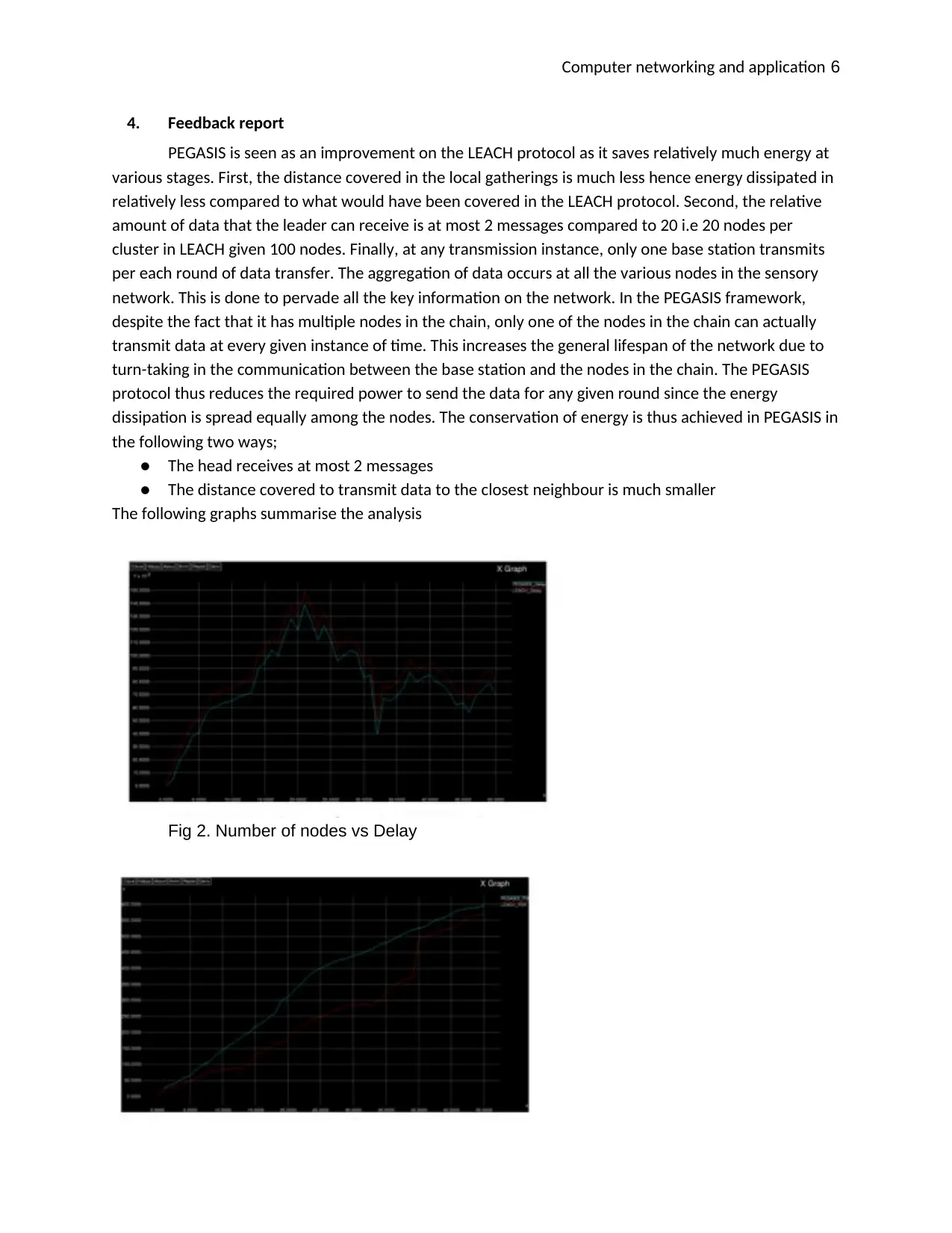
The following graphs summarise the analysis
Fig 2. Number of nodes vs Delay
4. Feedback report
PEGASIS is seen as an improvement on the LEACH protocol as it saves relatively much energy at
various stages. First, the distance covered in the local gatherings is much less hence energy dissipated in
relatively less compared to what would have been covered in the LEACH protocol. Second, the relative
amount of data that the leader can receive is at most 2 messages compared to 20 i.e 20 nodes per
cluster in LEACH given 100 nodes. Finally, at any transmission instance, only one base station transmits
per each round of data transfer. The aggregation of data occurs at all the various nodes in the sensory
network. This is done to pervade all the key information on the network. In the PEGASIS framework,
despite the fact that it has multiple nodes in the chain, only one of the nodes in the chain can actually
transmit data at every given instance of time. This increases the general lifespan of the network due to
turn-taking in the communication between the base station and the nodes in the chain. The PEGASIS
protocol thus reduces the required power to send the data for any given round since the energy
dissipation is spread equally among the nodes. The conservation of energy is thus achieved in PEGASIS in
the following two ways;
● The head receives at most 2 messages
● The distance covered to transmit data to the closest neighbour is much smaller
The following graphs summarise the analysis
Fig 2. Number of nodes vs Delay
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Computer networking and application 7
Fig 3. Number of nodes vs Latency
Fig 4. Number of nodes vs packet delivery ratio
Fig 5. Number of nodes vs throughput
The analysis shows that the PEGASIS generally performs much better than LEACH in terms of the
general network lifetime and various connectivity overheads and the death of nodes. The PEGASIS offers
much better and longer network life due to its inherent energy efficiency from the design
5. Security issues and attacks
Security is one of the main problems with the wireless sensor network routing protocols as
attacks can be launched against these protocols. This section details some of the vulnerabilities and
attacks than can be done on the two protocols
5.1. LEACH
The following attacks can be launched against the LEACH protocol
● A very malicious node may declare itself as the CH by sending the advertisement packet
● An attacker can join some clusters together or worse preven some nodes from joining a cluster
● An attacker can gather information about the nodes during the cluster formation process
Fig 3. Number of nodes vs Latency
Fig 4. Number of nodes vs packet delivery ratio
Fig 5. Number of nodes vs throughput
The analysis shows that the PEGASIS generally performs much better than LEACH in terms of the
general network lifetime and various connectivity overheads and the death of nodes. The PEGASIS offers
much better and longer network life due to its inherent energy efficiency from the design
5. Security issues and attacks
Security is one of the main problems with the wireless sensor network routing protocols as
attacks can be launched against these protocols. This section details some of the vulnerabilities and
attacks than can be done on the two protocols
5.1. LEACH
The following attacks can be launched against the LEACH protocol
● A very malicious node may declare itself as the CH by sending the advertisement packet
● An attacker can join some clusters together or worse preven some nodes from joining a cluster
● An attacker can gather information about the nodes during the cluster formation process
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Computer networking and application 8
● An attacker may use the DDOS attack to disrupt the cluster formation process
● An attacker can create a false membership list for CH and schedule TDMA
● A passive attacker can eavesdrop on the traffic transmitted between the CH and the members of
the cluster.
● An active attack can be manifested by using the time slot of an idle node and use the time slot to
send false data
The above attacks are possible because of the vulnerabilities in the LEACH protocol. It relies
heavily on the CH for most operations that include data aggregation and the routing of packets hence
the election of unauthorised CH will have a much devastating impact on the network security
5.2. PEGASIS
Attacks on the PEGASIS includes
● Denial of service attack at the physical layer
● Network jamming
● Traffic manipulation
● Packet injection
6. Attack countermeasures
Each countermeasure is applicable to the different protocols at different stages of the
framework formation. This section summarises the countermeasures for the above attacks.
6.1. LEACH
Securing the LEACH protocol involves security the integrity, trustworthiness and the freshness of
the CH as it is the central point of failure. The following proposed solution can help mitigate the attacks
mentioned above
● The authenticity, integrity and freshness of the broadcast advertising message should be
authenticated by the cluster members [7]
● The members of the cluster should be authenticated by the CH
● The authenticity, integrity and the freshness of the TDMA broadcasted should be authenticated
by all nodes [8]
● The CH should authenticate the members of the node before it receives data from them
● Continous header selection
● Obedience of TDMA schedules
● No transmission of any header metadata
● No transmission of member metadata
● An attacker may use the DDOS attack to disrupt the cluster formation process
● An attacker can create a false membership list for CH and schedule TDMA
● A passive attacker can eavesdrop on the traffic transmitted between the CH and the members of
the cluster.
● An active attack can be manifested by using the time slot of an idle node and use the time slot to
send false data
The above attacks are possible because of the vulnerabilities in the LEACH protocol. It relies
heavily on the CH for most operations that include data aggregation and the routing of packets hence
the election of unauthorised CH will have a much devastating impact on the network security
5.2. PEGASIS
Attacks on the PEGASIS includes
● Denial of service attack at the physical layer
● Network jamming
● Traffic manipulation
● Packet injection
6. Attack countermeasures
Each countermeasure is applicable to the different protocols at different stages of the
framework formation. This section summarises the countermeasures for the above attacks.
6.1. LEACH
Securing the LEACH protocol involves security the integrity, trustworthiness and the freshness of
the CH as it is the central point of failure. The following proposed solution can help mitigate the attacks
mentioned above
● The authenticity, integrity and freshness of the broadcast advertising message should be
authenticated by the cluster members [7]
● The members of the cluster should be authenticated by the CH
● The authenticity, integrity and the freshness of the TDMA broadcasted should be authenticated
by all nodes [8]
● The CH should authenticate the members of the node before it receives data from them
● Continous header selection
● Obedience of TDMA schedules
● No transmission of any header metadata
● No transmission of member metadata

Computer networking and application 9
6.2. PEGASIS
● Cryptographic measures at the Application layer
● Packet authentication at the transport layer
● Provides means of network authentication, authorisation and digital certificates
● Apply the error correction codes at the data link layer
● Hiding encryption, tamper-proofing and packet prioritization
7. Comparative analysis
In comparison, the PEGASIS generally performs much better than LEACH in terms of the general
network lifetime and various connectivity overheads and the death of nodes. The PEGASIS offers much
better and longer network life due to its inherent energy efficiency from the design [9]
8. Conclusion
In conclusion, the paper provided a deep dive analysis into the two main wireless sensor
networks routing protocols i.e the LEACH and the PEGASIS. It is evident that the choice of the routing
protocol will directly impact on the performance of the network in general. The PEGASIS framework
generally performs much better than the LEACH protocol due to its ability to efficiently and effectively
utilise the energy in each node to ensure maximum network life cycle. despite the good designs put in
place to ensure reliable routing protocols, their practical implementation brings about serious security
vulnerabilities which threat can exploit. The key among the attacks includes DDOS attack, Masquerading,
Spoofing attacks, Man in the middle attacks, Eavesdropping, Jamming. This attacks when successful
could bring serious security issues to the network. To mitigate against this attack, the paper has
recommended mechanisms such as the use of authentification, authorisation and integrity checking
mechanism such as cryptography, digital certificates and authentification codes in the design of the
application and network nodes messages. This shall ensure theirs is some level of authentication and
authorization of all the critical network actions. Use of cryptography tools will ensure the man in the
eavesdropping which is a form of passive attacks won’t reveal any details about the nodes in the
network. Authentification between the nodes and the CH in case of the LEACH protocol will be done
securely. The authorization ensures the right action is done by the authenticated node to avoid
compromising the integrity of the network and other nodes as a whole
6.2. PEGASIS
● Cryptographic measures at the Application layer
● Packet authentication at the transport layer
● Provides means of network authentication, authorisation and digital certificates
● Apply the error correction codes at the data link layer
● Hiding encryption, tamper-proofing and packet prioritization
7. Comparative analysis
In comparison, the PEGASIS generally performs much better than LEACH in terms of the general
network lifetime and various connectivity overheads and the death of nodes. The PEGASIS offers much
better and longer network life due to its inherent energy efficiency from the design [9]
8. Conclusion
In conclusion, the paper provided a deep dive analysis into the two main wireless sensor
networks routing protocols i.e the LEACH and the PEGASIS. It is evident that the choice of the routing
protocol will directly impact on the performance of the network in general. The PEGASIS framework
generally performs much better than the LEACH protocol due to its ability to efficiently and effectively
utilise the energy in each node to ensure maximum network life cycle. despite the good designs put in
place to ensure reliable routing protocols, their practical implementation brings about serious security
vulnerabilities which threat can exploit. The key among the attacks includes DDOS attack, Masquerading,
Spoofing attacks, Man in the middle attacks, Eavesdropping, Jamming. This attacks when successful
could bring serious security issues to the network. To mitigate against this attack, the paper has
recommended mechanisms such as the use of authentification, authorisation and integrity checking
mechanism such as cryptography, digital certificates and authentification codes in the design of the
application and network nodes messages. This shall ensure theirs is some level of authentication and
authorization of all the critical network actions. Use of cryptography tools will ensure the man in the
eavesdropping which is a form of passive attacks won’t reveal any details about the nodes in the
network. Authentification between the nodes and the CH in case of the LEACH protocol will be done
securely. The authorization ensures the right action is done by the authenticated node to avoid
compromising the integrity of the network and other nodes as a whole
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Computer networking and application 10
9. References
[1] M. R. Jafri, N. Javaid, A. Javaid, and Z. A. Khan, “Maximizing the lifetime of multi-chain pegasis using
sink mobility,” ArXiv Prepr. ArXiv13034347, 2013.
[2] Z. Han, J. Wu, J. Zhang, L. Liu, and K. Tian, “A general self-organized tree-based energy-balance
routing protocol for wireless sensor network,” IEEE Trans. Nucl. Sci., vol. 61, no. 2, pp. 732–740,
2014.
[3] M. Gupta and L. Saraswat, “Energy aware data collection in wireless sensor network using chain
based PEGASIS,” in International Conference on Recent Advances and Innovations in Engineering
(ICRAIE-2014), 2014, pp. 1–5.
[4] Y. A. N. Ying, G. U. O. Li, and X. U. Jianzhen, “Linking of Delamination Based LEACH and PERASIS [J],”
9. References
[1] M. R. Jafri, N. Javaid, A. Javaid, and Z. A. Khan, “Maximizing the lifetime of multi-chain pegasis using
sink mobility,” ArXiv Prepr. ArXiv13034347, 2013.
[2] Z. Han, J. Wu, J. Zhang, L. Liu, and K. Tian, “A general self-organized tree-based energy-balance
routing protocol for wireless sensor network,” IEEE Trans. Nucl. Sci., vol. 61, no. 2, pp. 732–740,
2014.
[3] M. Gupta and L. Saraswat, “Energy aware data collection in wireless sensor network using chain
based PEGASIS,” in International Conference on Recent Advances and Innovations in Engineering
(ICRAIE-2014), 2014, pp. 1–5.
[4] Y. A. N. Ying, G. U. O. Li, and X. U. Jianzhen, “Linking of Delamination Based LEACH and PERASIS [J],”
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Computer networking and application 11
Chin. J. Sens. Actuators, vol. 9, 2011.
[5] I. Sharma, R. Singh, and M. Khurana, “Comparative study of LEACH, LEACH-C and PEGASIS routing
protocols for wireless sensor network,” in 2015 International Conference on Advances in Computer
Engineering and Applications, 2015, pp. 842–846.
[6] E. Selem, A. M. Khedr, and H. Nassar, “M-PEGASIS: Energy Efficient Pegasis for Mobile Wireless
Sensor Networks,” Egypt. Comput. Sci. J., vol. 37, no. 6, 2013.
[7] I. Boulhares and M. Omari, “Hybridizing PEGASIS with LEACH-1R protocols in wireless sensor
networks,” in 2016 8th International Conference on Modelling, Identification and Control (ICMIC),
2016, pp. 1037–1042.
[8] Z. ZHANG, L. YAN, W. PAN, B. LUO, J. LIU, and X. LI, “Routing protocol based on cluster-head-
chaining incorporating LEACH and PEGASIS [J],” Chin. J. Sens. Actuators, vol. 8, pp. 027–31, 2010.
[9] P. Jain and A. Chaudhary, “The comparison between leach protocol and pegasis protocol based on
lifetime of wireless sensor networks,” Int. J. Comput. Sci. Mob. Comput., vol. 6, no. 12, pp. 15–19,
2017.
Chin. J. Sens. Actuators, vol. 9, 2011.
[5] I. Sharma, R. Singh, and M. Khurana, “Comparative study of LEACH, LEACH-C and PEGASIS routing
protocols for wireless sensor network,” in 2015 International Conference on Advances in Computer
Engineering and Applications, 2015, pp. 842–846.
[6] E. Selem, A. M. Khedr, and H. Nassar, “M-PEGASIS: Energy Efficient Pegasis for Mobile Wireless
Sensor Networks,” Egypt. Comput. Sci. J., vol. 37, no. 6, 2013.
[7] I. Boulhares and M. Omari, “Hybridizing PEGASIS with LEACH-1R protocols in wireless sensor
networks,” in 2016 8th International Conference on Modelling, Identification and Control (ICMIC),
2016, pp. 1037–1042.
[8] Z. ZHANG, L. YAN, W. PAN, B. LUO, J. LIU, and X. LI, “Routing protocol based on cluster-head-
chaining incorporating LEACH and PEGASIS [J],” Chin. J. Sens. Actuators, vol. 8, pp. 027–31, 2010.
[9] P. Jain and A. Chaudhary, “The comparison between leach protocol and pegasis protocol based on
lifetime of wireless sensor networks,” Int. J. Comput. Sci. Mob. Comput., vol. 6, no. 12, pp. 15–19,
2017.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





